Download official yaml file
The latest configuration file v2.0.0-beta 8, recommended.yaml, UI address
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta8/aio/deploy/recommended.yaml
Original document:
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
Revised to:
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort #Newly added
ports:
- port: 443
nodePort: 30001 #Newly added
targetPort: 8443
selector:
k8s-app: kubernetes-dashboardContents of the original document
spec:
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.0.0-beta8
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCPRevised to:
spec:
# nodeName: master.node is specified to the master node, which means not to specify as required
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.0.0-beta8
# imagePullPolicy: Always
imagePullPolicy: IfNotPresent #No more downloads
ports:
- containerPort: 8443
protocol: TCPDownload Image and start
Execute on the master node
docker pull kubernetesui/dashboard:v2.0.0-beta8
implement
kubectl apply -f recommended.yaml
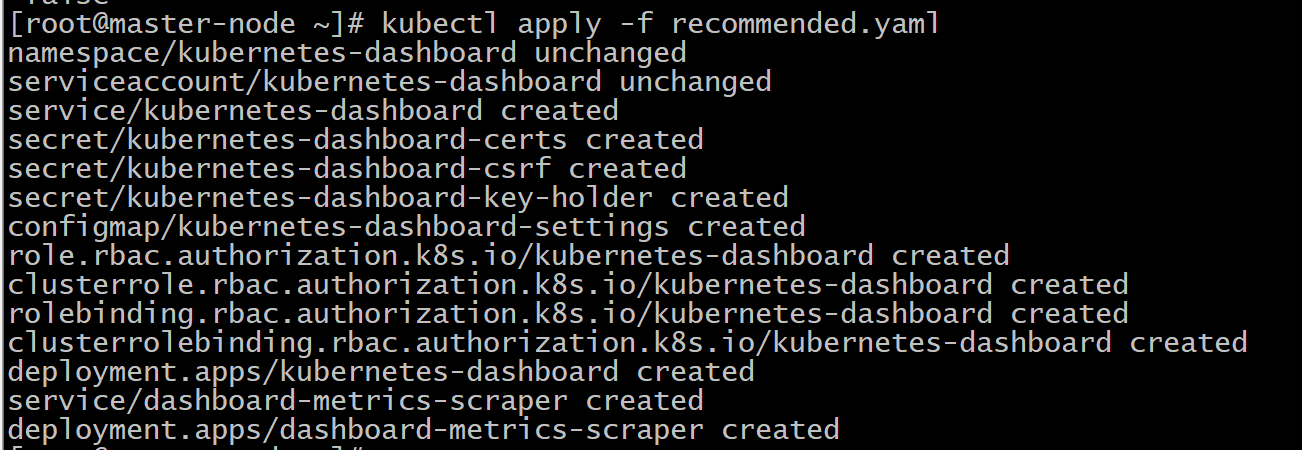
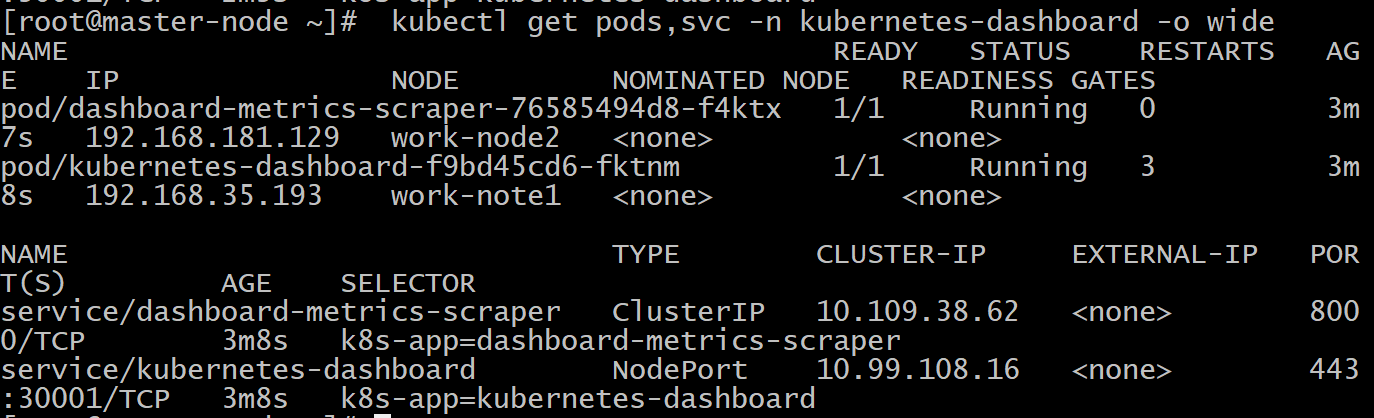
View pod and service status
kubectl get pods,svc -n kubernetes-dashboard -o wide
kubectl describe po kubernetes-dashboard --namespace=kubernetes-dashboard
If found
kubernetes-dashboard crashloopbackoff
kubectl get pods --all-namespaces
systemctl stop kubelet systemctl stop docker iptables --flush iptables -tnat --flush systemctl start kubelet systemctl start docker
kubectl delete -f recommended.yaml
List all nodes: kubectl get node s
Delete node: kubectl delete node node3
View the pods information on the corresponding node: kubectl get Pods - O width | grep node3
Rejoin
Execute: kubeadm reset on the server corresponding to the deleted node3
iptables -P INPUT ACCEPT iptables -P FORWARD ACCEPT iptables -F iptables -L -n
mkdir cert cd cert/ openssl genrsa -out dashboard.key 2048 openssl req -days 36000 -new -out dashboard.csr -key dashboard.key -subj '/CN=**192.168.56.106**' openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kubernetes-dashboard
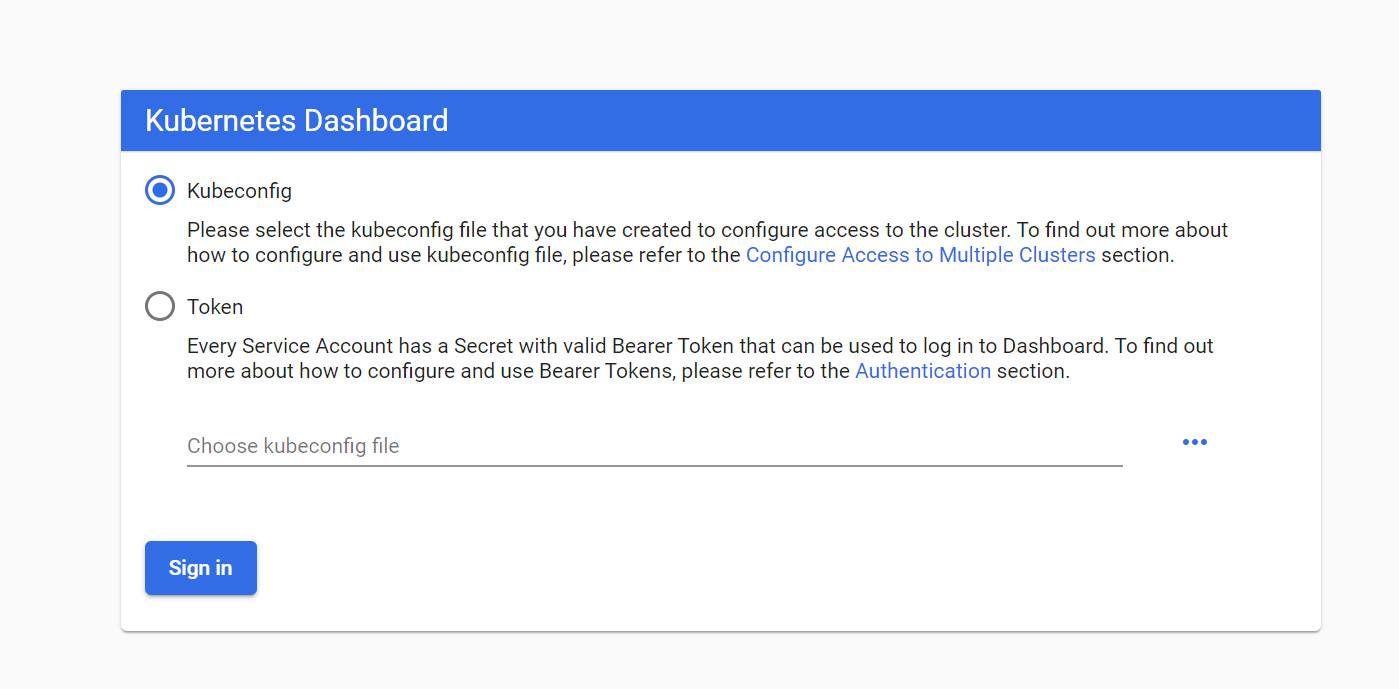
New create-admin.yaml
apiVersion: v1 kind: ServiceAccount metadata: name: admin-user namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: admin-user roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: admin-user namespace: kubernetes-dashboard
Function
kubectl apply -f create-admin.yaml
View sa and secret
kubectl get sa,secrets -n kubernetes-dashboard
kubectl describe secret admin-user-token-t79xh -n kubernetes-dashboard
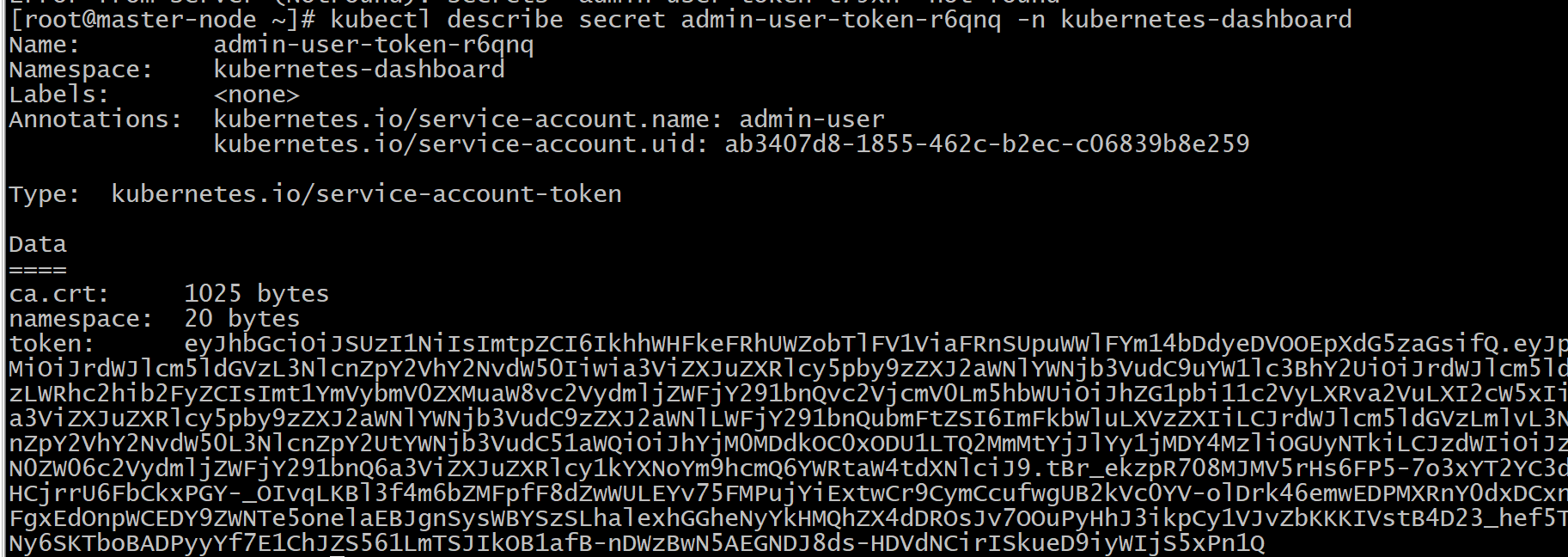
Get token login succeeded:
This article is based on the platform of blog one article multiple sending OpenWrite Release!