CIS security scanning is one of the heavyweight functions introduced by Rancher 2.4, which aims to help users quickly and effectively enhance the security of clusters. This article will introduce the CIS security scanning function in detail, including the detailed operation demo.

This article comes from Rancher Labs
Cluster security is a critical part of any successful Kubernetes strategy. Recently, a survey released by AimPoint showed that 44% of the respondents said that due to the security problem of Kubernetes container, application access to the production environment was delayed.
Kubernetes security, however, is a complex machine with many moving parts, integrations, and knobs and levers. This will make the already challenging security work more difficult.
Rancher Labs, the creator of the most widely used Kubernetes management platform in the industry, has been looking for various efficient ways for users, so we are very pleased to launch CIS security scanning function in Rancher 2.4. This new function of rancher managed cluster allows you to run ad-hoc security scan and regular scan of RKE cluster for more than 100 CIS benchmarks published by Internet Security Center. With CIS security scan, you can create custom test configurations and generate reports containing pass / fail information. According to the report, you can take various measures to ensure that your cluster meets all security requirements.
CIS benchmark has been widely accepted as the factual standard to ensure the security of Kubernetes cluster. It provides an industry recognized indicator that can be used to measure the security of the Kubernetes cluster. It combines knowledge of the information security community with a deep understanding of the API, interaction, and overall control path in Kubernetes. When engineers try to understand all the locations they need to protect the cluster, they can learn from the benchmark the possibilities of dozens of kinds of * * * and how to mitigate them.
Why does IT Ops need CIS security scanning?
It is a time-consuming and failure prone process to evaluate clusters manually according to CIS Benchmark. In reality, our system is constantly changing, so we need to re evaluate it frequently. That's what Kube bench has done. This is an open source tool created by Aqua to automatically evaluate clusters based on CIS Benchmark.
Rancher 2.4 uses Kube bench as the security engine and supplements it. With the CIS security scan in rancher 2.4, you can organize cluster scans with one click. Rancher is responsible for getting the Kube bench tool and connecting it to the cluster. Then, rancher will summarize an easy to read report from the results of all nodes, which will show the areas where the cluster passed or failed. In addition, rancher allows you to schedule periodic scans at the cluster level. This setting can be enabled at the cluster template level and, by default, allows administrators to configure templates for scheduled scans to run scans for each new cluster created by any user in the rancher settings. Finally, rancher provides custom alarms and notifications for CIS security scanning. Security administrators are notified by email, wechat, etc. when the configuration of the cluster is changed, or the configuration of the cluster itself is not compliant.
Hands on CIS cluster in Rancher 2.4
Let's start a Rancher RKE cluster.
Pre preparation: CentOS VM (at least 2 cores) and Docker installed
Step 1: run Rancher Server
[root@rancher-rke ~]# sudo docker run -d --restart=unless-stopped -p 80:80 -p 443:443 rancher/rancher:v2.4.0-rc3 Unable to find image 'rancher/rancher:v2.4.0-rc3' locally Trying to pull repository docker.io/rancher/rancher ... v2.4.0-rc3: Pulling from docker.io/rancher/rancher 423ae2b273f4: Pull complete de83a2304fa1: Pull complete f9a83bce3af0: Pull complete b6b53be908de: Pull complete b365c90117f7: Pull complete c939267bea55: Pull complete 7669306d1ae0: Pull complete 25e0f5e123a3: Pull complete d6664495480f: Pull complete 99f55ceed479: Pull complete edd7d0bc05aa: Pull complete 77e4b172baa4: Pull complete 48f474afa2cd: Pull complete 2270fe22f735: Pull complete 44c4786f7637: Pull complete 45e3db8be413: Pull complete 6be735114771: Pull complete dfa5473bfef3: Pull complete Digest: sha256:496bd1d204744099d70f191e86d6a35a5827f86501322b55f11c686206010b51 Status: Downloaded newer image for docker.io/rancher/rancher:v2.4.0-rc3 a145d93e8fa66a6a08b4f0e936dafc4b9717a93c59013e78118a4c5af8209a53
[root@rancher-rke ~]# docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES a145d93e8fa6 rancher/rancher:v2.4.0-rc3 "entrypoint.sh" About a minute ago Up About a minute 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp distracted_albattani
Step 2: visit the Rancher URL and install RKEhttp://{hostIP}
Set password and URL
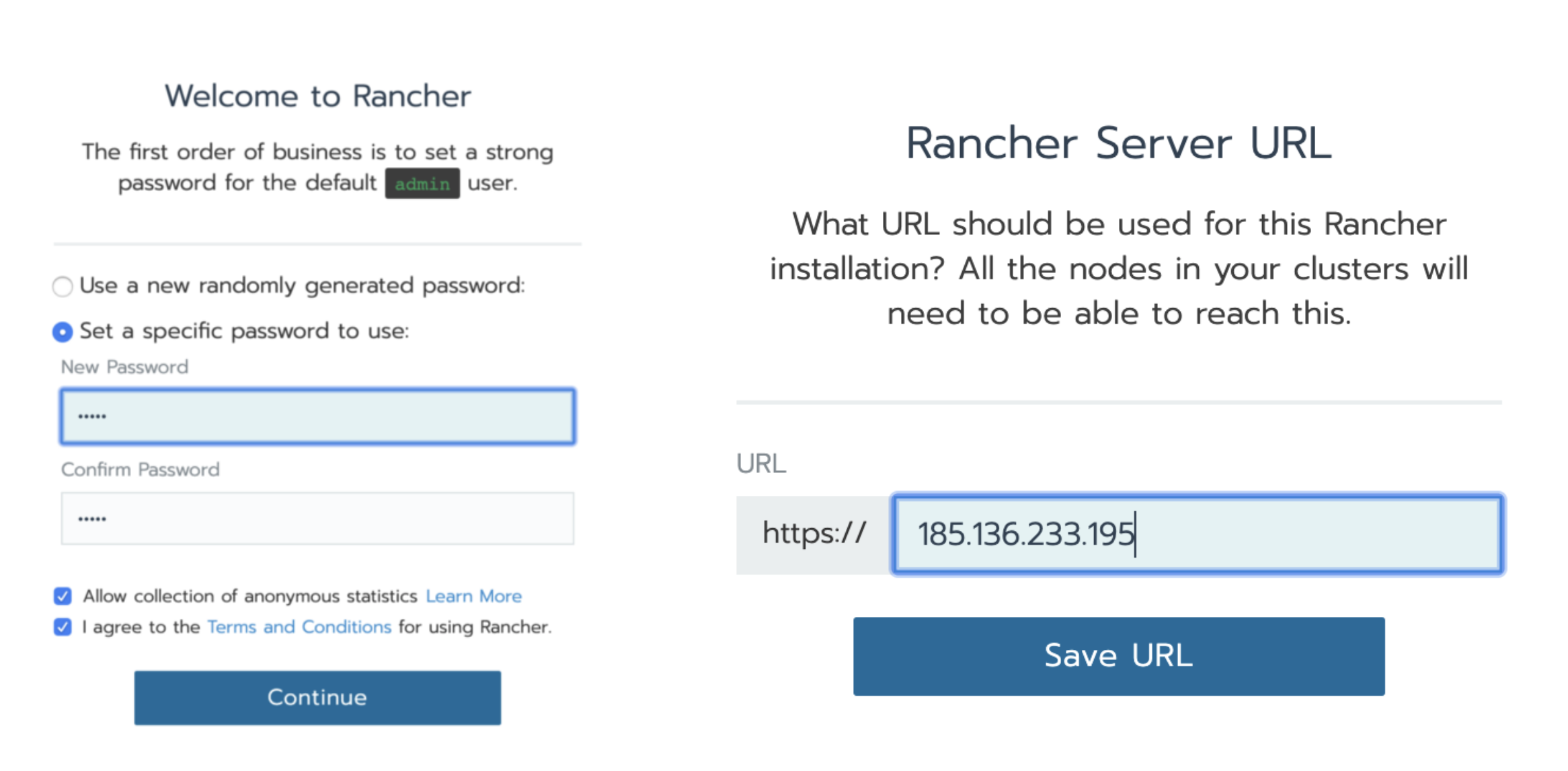
Set the Rancher password and URL as the host IP
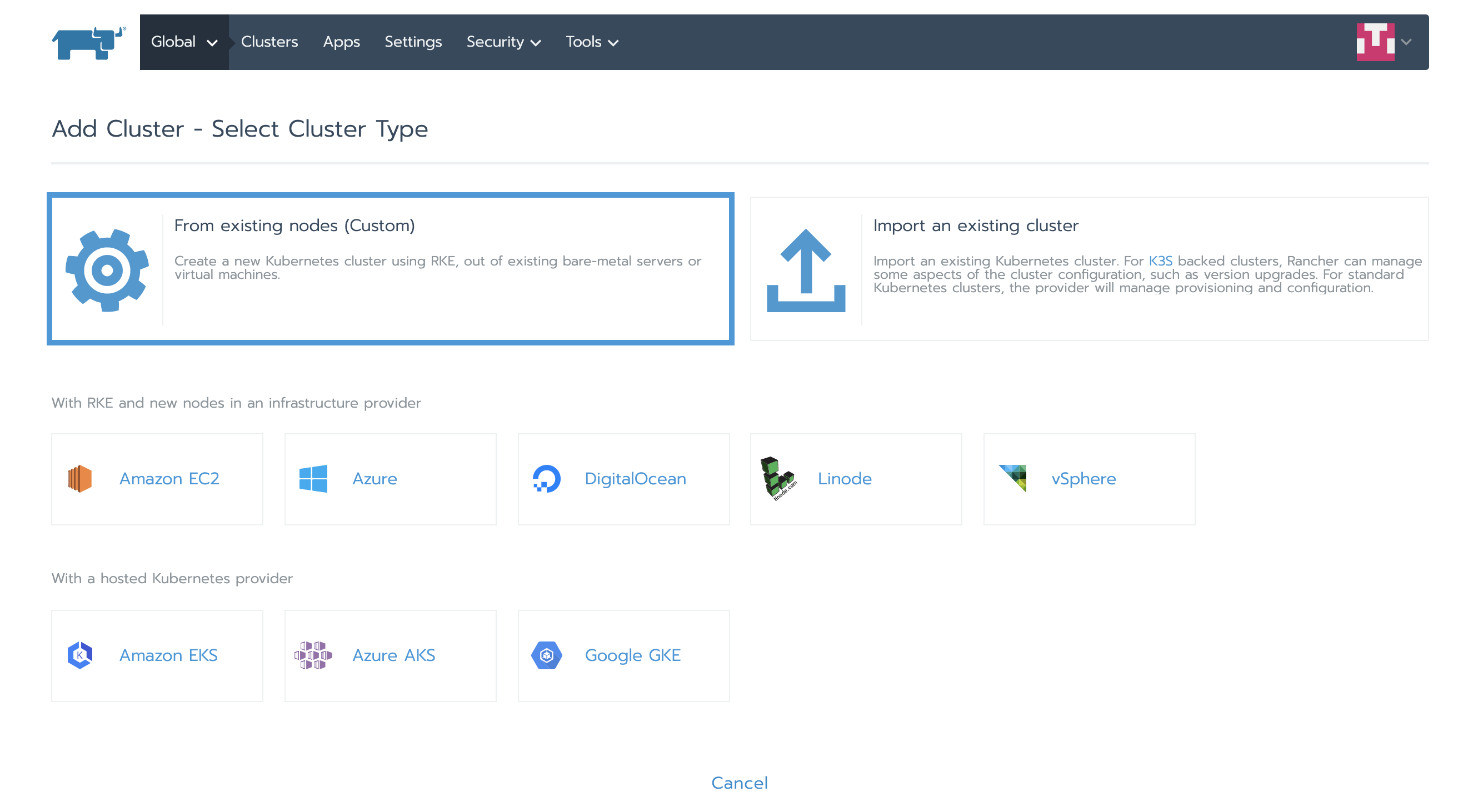
Add a new cluster and select From existing nodes (Custom)
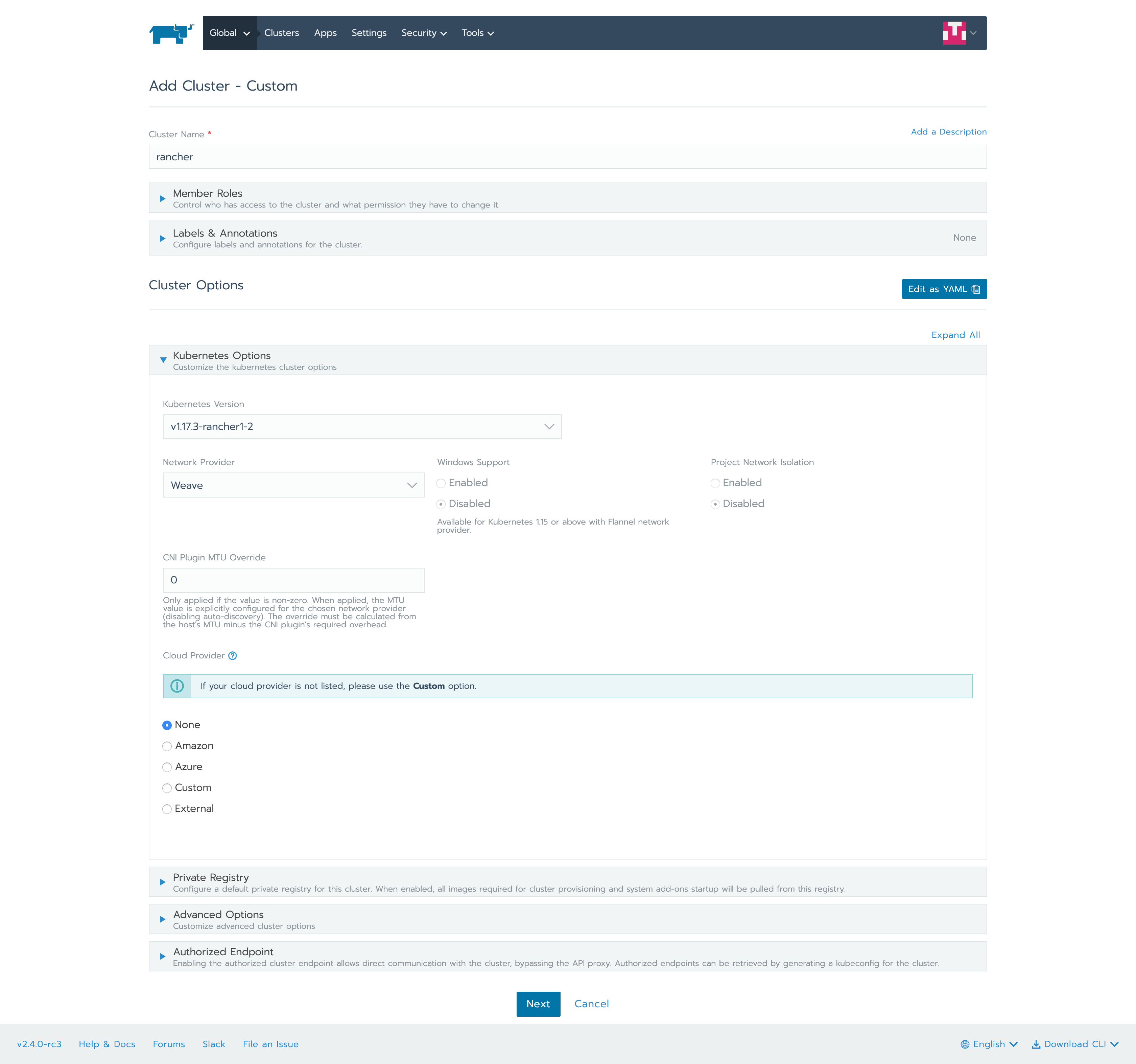
Select the default options and select etcd, control plane, and worker because we will install all of these on a VM.
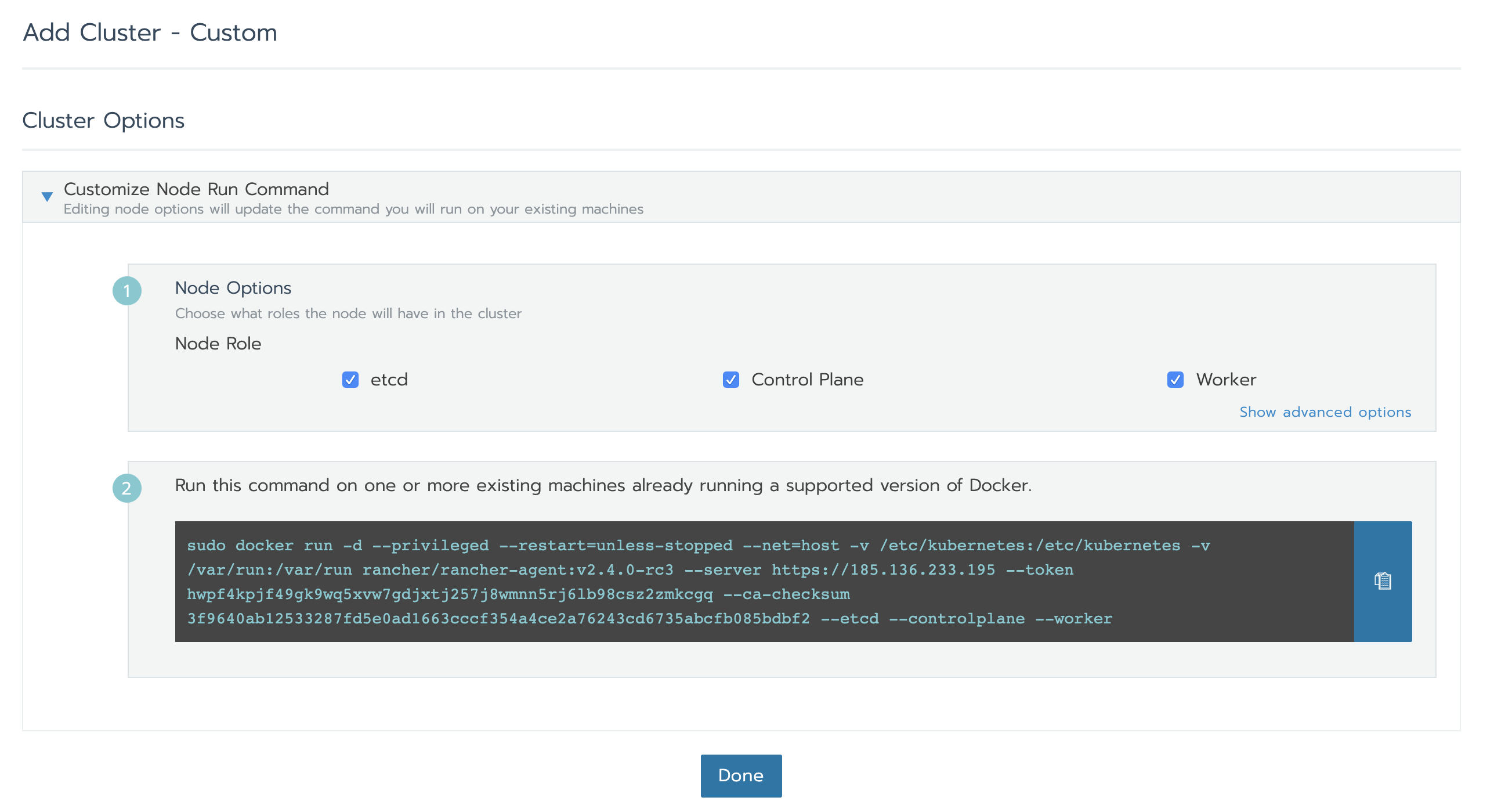
Copy the above command and run it on VM instance
[root@rancher-rke ~]# **sudo docker run -d --privileged --restart=unless-stopped --net=host -v /etc/kubernetes:/etc/kubernetes -v /var/run:/var/run rancher/rancher-agent:v2.4.0-rc3 --server https://185.136.233.195 --token** hwpf4kpjf49gk9wq5xvw7gdjxtj257j8wmnn5rj6lb98csz2zmkcgq --ca-checksum 3f9640ab12533287fd5e0ad1663cccf354a4ce2a76243cd6735abcfb085bdbf2 --etcd --controlplane --worker Unable to find image 'rancher/rancher-agent:v2.4.0-rc3' locally Trying to pull repository docker.io/rancher/rancher-agent ... v2.4.0-rc3: Pulling from docker.io/rancher/rancher-agent 423ae2b273f4: Already exists de83a2304fa1: Already exists f9a83bce3af0: Already exists b6b53be908de: Already exists 931af2228ddf: Pull complete 94b51e50d654: Pull complete 7e7961efe32b: Pull complete 85725dc92c8d: Pull complete 5a82c6e509a6: Pull complete 3b675e73aee3: Pull complete Digest: sha256:89017bd846a8cc597186f41eb17cfe1520aa0f7e6d86b48d8c32a5490c588f1e Status: Downloaded newer image for docker.io/rancher/rancher-agent:v2.4.0-rc3 5aaa9fab48db4557c84b7ce0c61816384075570ed3e593446795bf8443610b64
When importing a cluster in the Rancher UI, we can see that the status of the cluster is active:

Now click cluster and select CIS security scan from the [tools] menu bar.
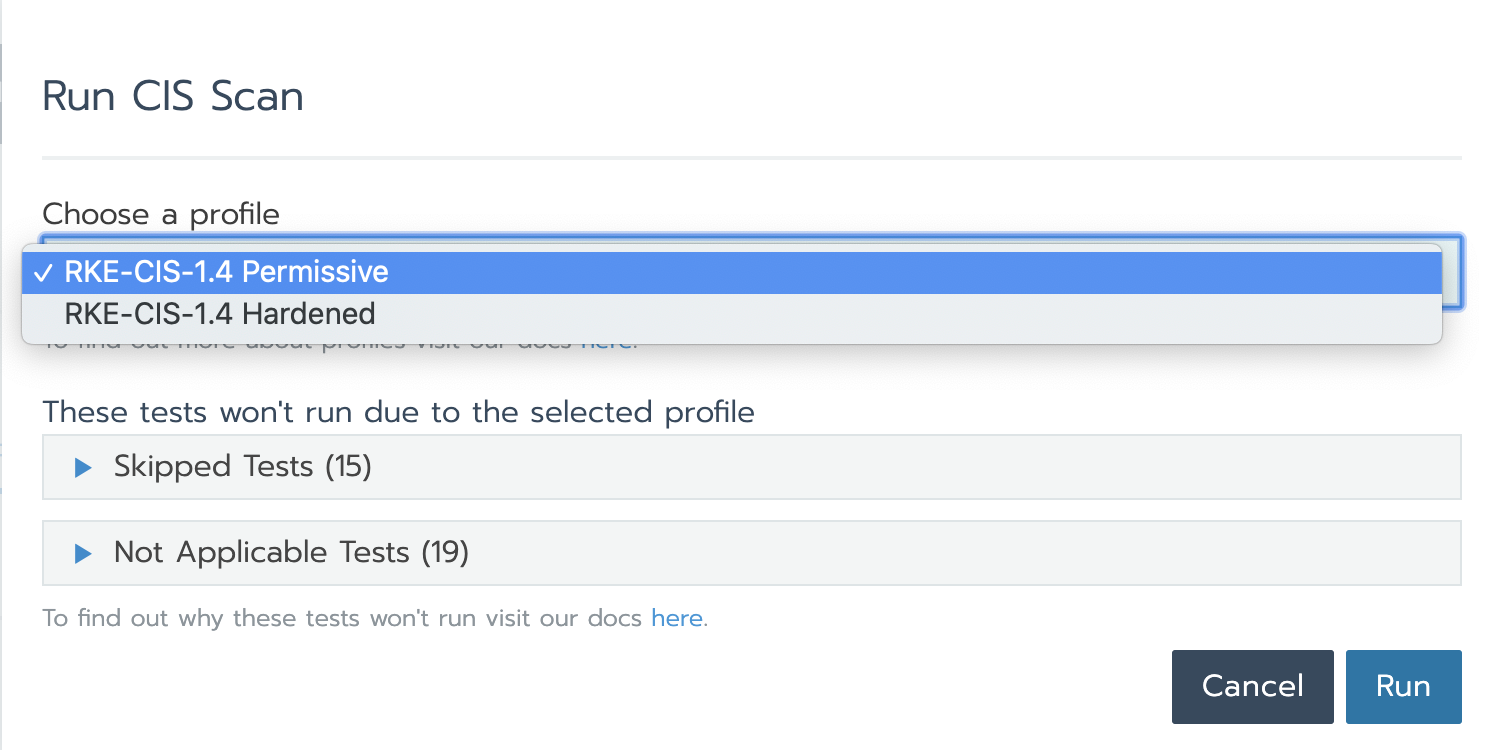
Currently, CIS security scanning is only for RKE cluster, and there are two scanning configuration files: Permissive and Hardened.
- Permissive: this profile has a set of tests that will be skipped because they are not necessary for users who are just starting to use Kubernetes.
- Hardened: this profile will not skip any tests. This configuration is for advanced users and security experts.
For each configuration type, some of these tests are marked as not applicable because they are not applicable to RKE clusters.
Now let's select the "loose" profile and run the scan. The result is that all standard RKE clusters pass.
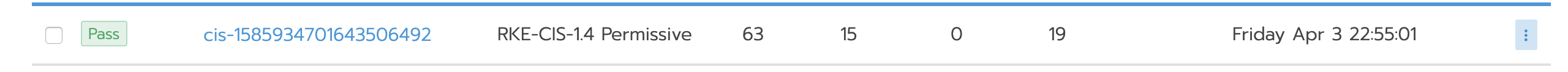
To see more details about test execution, click on the test and the entire list of tests will be displayed, including failure / skip / pass information.
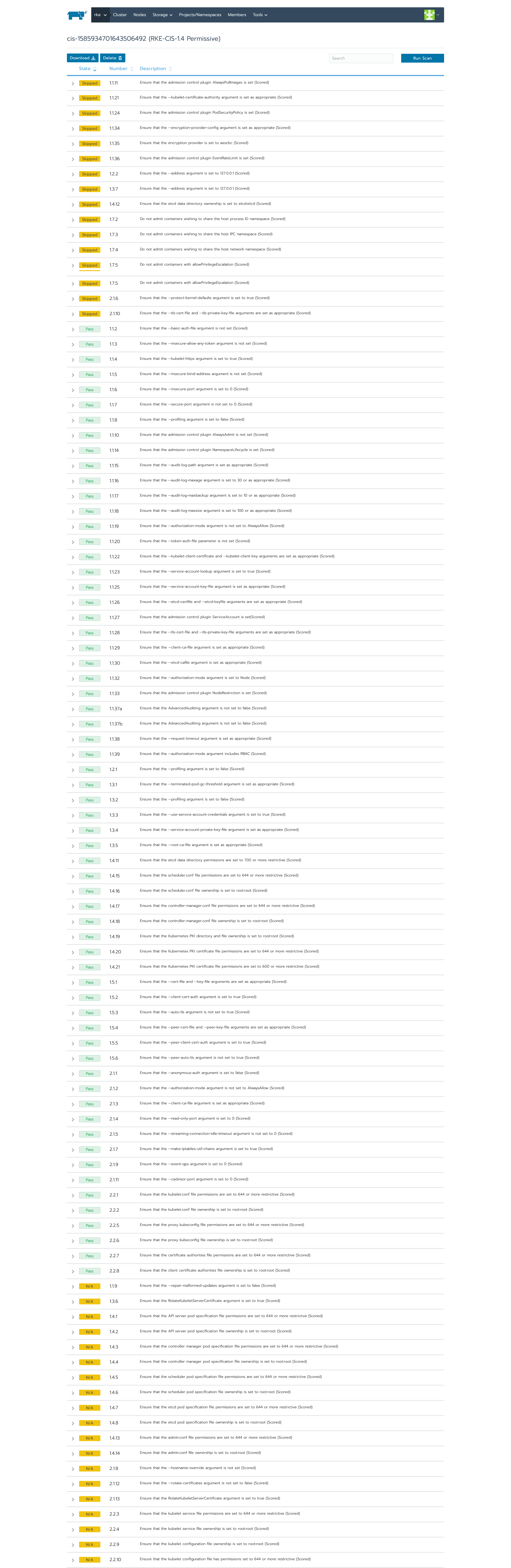
Now, we use the "strict" configuration file to perform the same test, and we'll see that the last skipped test failed.
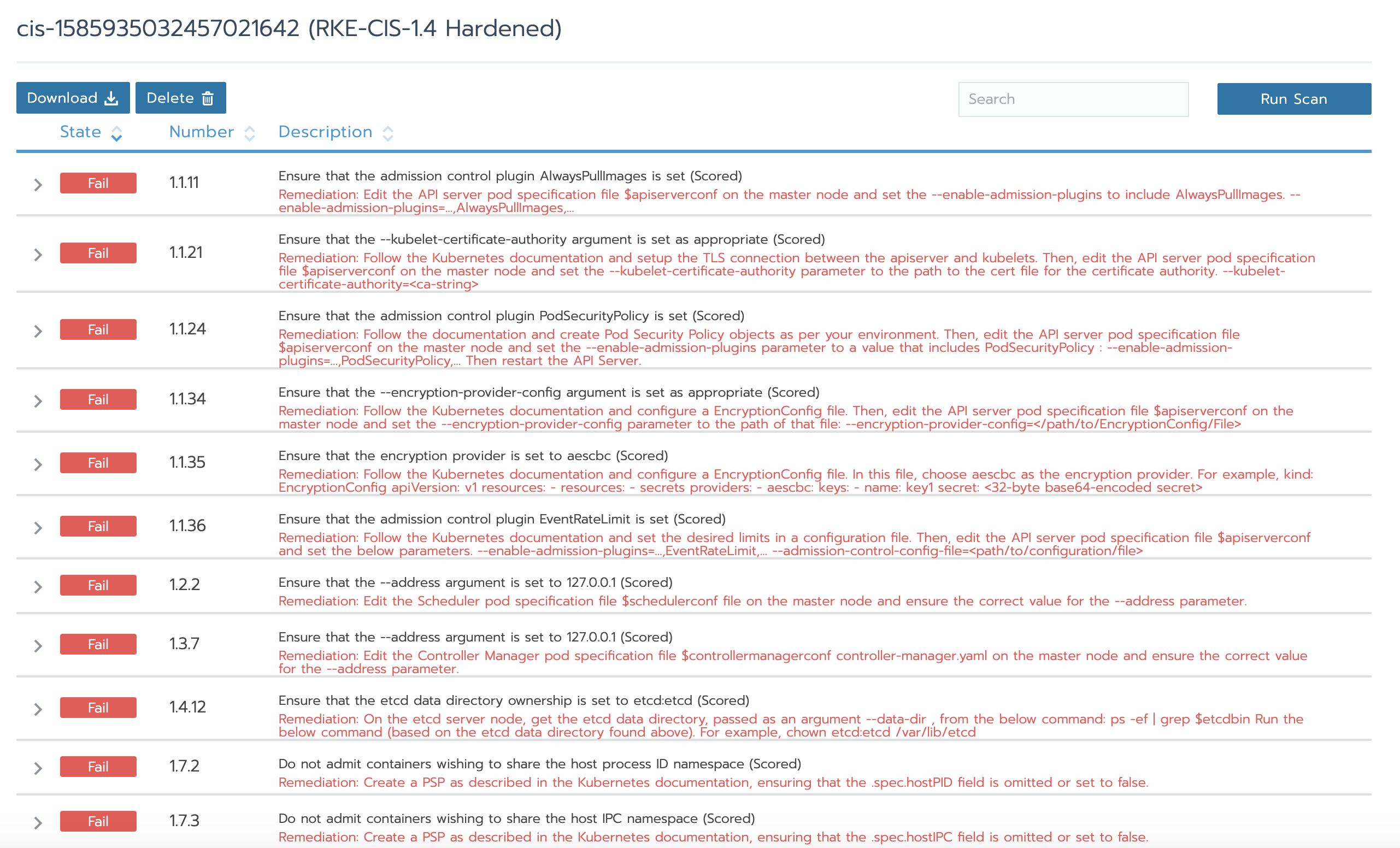
As you can see, according to the CIS benchmark, the failure results provide a description and remedial steps. This is very effective because you can not only understand what will crash in the cluster according to the CIS benchmark, but also repair the cluster according to the suggestions.
Next steps to enhance cluster security
Although CIS security scan can be run with one click, it is better to be able to perform it automatically. It can also be configured in Rancher. Regular security scans are a reassuring and reassuring tool for your team. If there are some non conformances in the cluster, you can find it faster.
Now, what if there are some non conformances in the cluster? The solution is simple: View Rancher security hardening Guide . This guide provides rancher specific steps to make your cluster meet the requirements of each CIS check. Rancher's world-class support team is also proficient in solving such problems. You are welcome to buy our subscription service. For details, please add a small assistant (wechat: lancher3) for consultation.