
Dead work
1. Enabling the ingress plug-in of minikube
minikube addons enable ingress
2. Complete the mirroring required by the ingress plug-in
minikube ssh
export image=nginx-ingress-controller:0.14.0 docker pull registry.cn-hangzhou.aliyuncs.com/anoy/${image} docker tag registry.cn-hangzhou.aliyuncs.com/anoy/${image} quay.io/kubernetes-ingress-controller/${image} docker rmi registry.cn-hangzhou.aliyuncs.com/anoy/${image}
Note: This step can be ignored if the network is good.
3. Create two services
Create blog-anoyi: Anoyi's Personal Blog
apiVersion: apps/v1 kind: Deployment metadata: name: blog-anoyi labels: app: blog spec: selector: matchLabels: blog-name: anoyi template: metadata: labels: blog-name: anoyi spec: containers: - image: registry.cn-hangzhou.aliyuncs.com/anoy/blog name: blog env: - name: JIANSHU_ID value: 7b7ec6f2db21 ports: - containerPort: 8080 --- apiVersion: v1 kind: Service metadata: name: blog-anoyi labels: app: blog spec: ports: - port: 8080 selector: blog-name: anoyi clusterIP: None
Creating Service blog-science: Science Jia's Personal Blog
apiVersion: apps/v1 kind: Deployment metadata: name: blog-science labels: app: blog spec: selector: matchLabels: blog-name: science template: metadata: labels: blog-name: science spec: containers: - image: registry.cn-hangzhou.aliyuncs.com/anoy/blog name: blog env: - name: JIANSHU_ID value: 66a89bc4d1b3 ports: - containerPort: 8080 --- apiVersion: v1 kind: Service metadata: name: blog-science labels: app: blog spec: ports: - port: 8080 selector: blog-name: science clusterIP: None
Ingress type
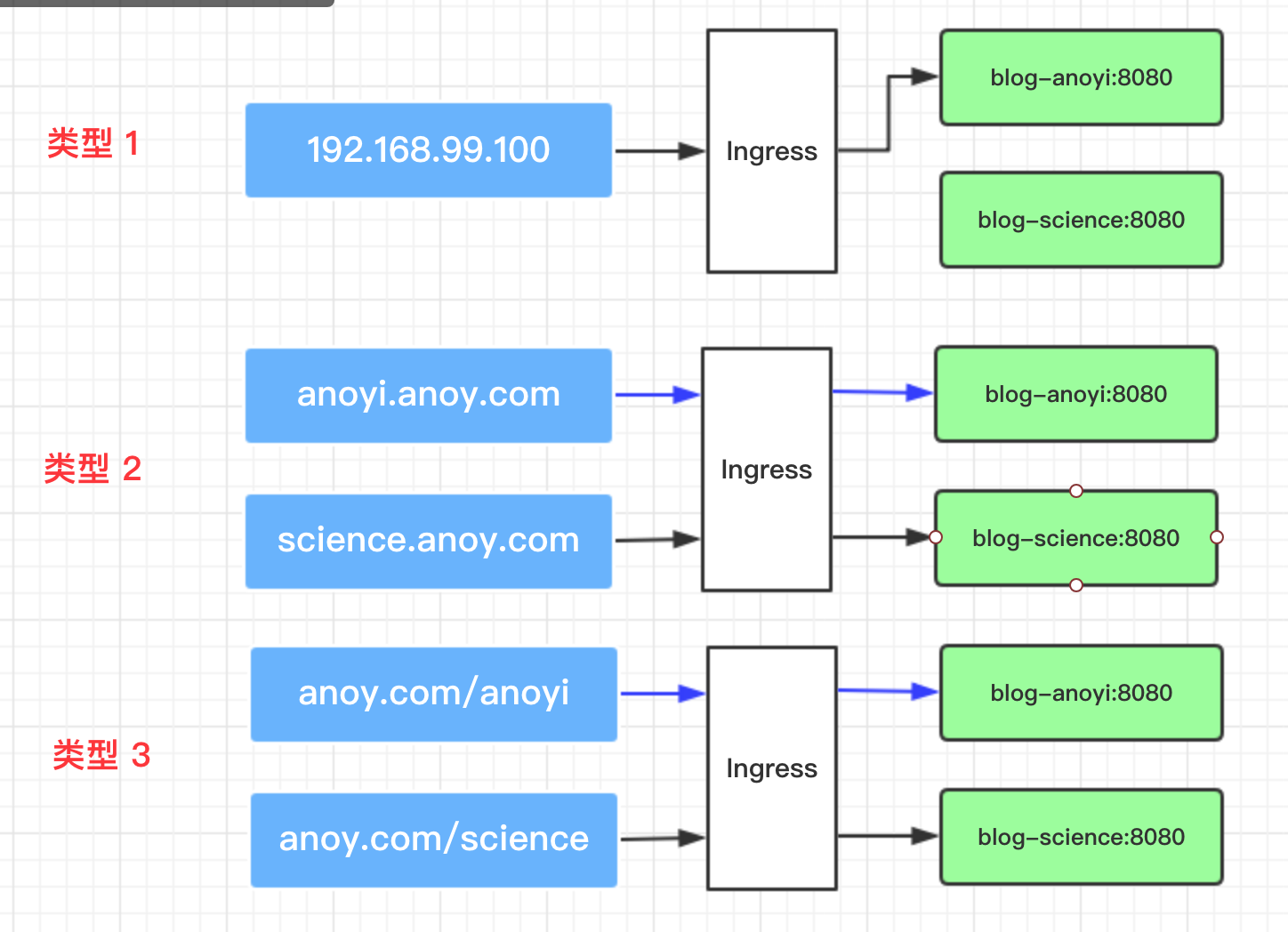
1,Single Service Ingress
apiVersion: extensions/v1beta1 kind: Ingress metadata: name: blog-ingress spec: backend: serviceName: blog-anoyi servicePort: 8080
Simple service routing, forwarding Node's inbound traffic from port 80 to service blog-anoyi, checking ingress rules:
kubectl describe ing
Name: blog-ingress Namespace: default Address: 192.168.99.100 Default backend: blog-anoyi:8080 (172.17.0.3:8080) Rules: Host Path Backends ---- ---- -------- * * blog-anoyi:8080 (172.17.0.3:8080) Annotations: Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal CREATE 18m nginx-ingress-controller Ingress default/blog-ingress Normal UPDATE 17m nginx-ingress-controller Ingress default/blog-ingress
That is to say, visiting http://192.168.99.100/is equal to visiting http://172.17.0.3:8080/, and visiting Anoyi's blog in browser will display.
2,Name based virtual hosting
apiVersion: extensions/v1beta1 kind: Ingress metadata: name: blog-ingress spec: rules: - host: anoyi.anoy.com http: paths: - backend: serviceName: blog-anoyi servicePort: 8080 - host: science.anoy.com http: paths: - backend: serviceName: blog-science servicePort: 8080
Name-based virtual host forwarding, forwarding requests under anoyi.anoy.com domain name to service blog-anoyi, science.anoy.com domain name to service blog-science, ingress rules are as follows:
Name: test Namespace: default Address: 192.168.99.100 Default backend: default-http-backend:80 () Rules: Host Path Backends ---- ---- -------- anoyi.anoy.com blog-anoyi:8080 (<none>) science.anoy.com blog-science:8080 (<none>) Annotations: Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal CREATE 3m nginx-ingress-controller Ingress default/test Normal UPDATE 2m nginx-ingress-controller Ingress default/test
Configuration Host is accessed separately as shown in the following figure http://anoyi.anoy.com and http://science.anoy.com
Note: 192.168.99.100 is Address in Ingress
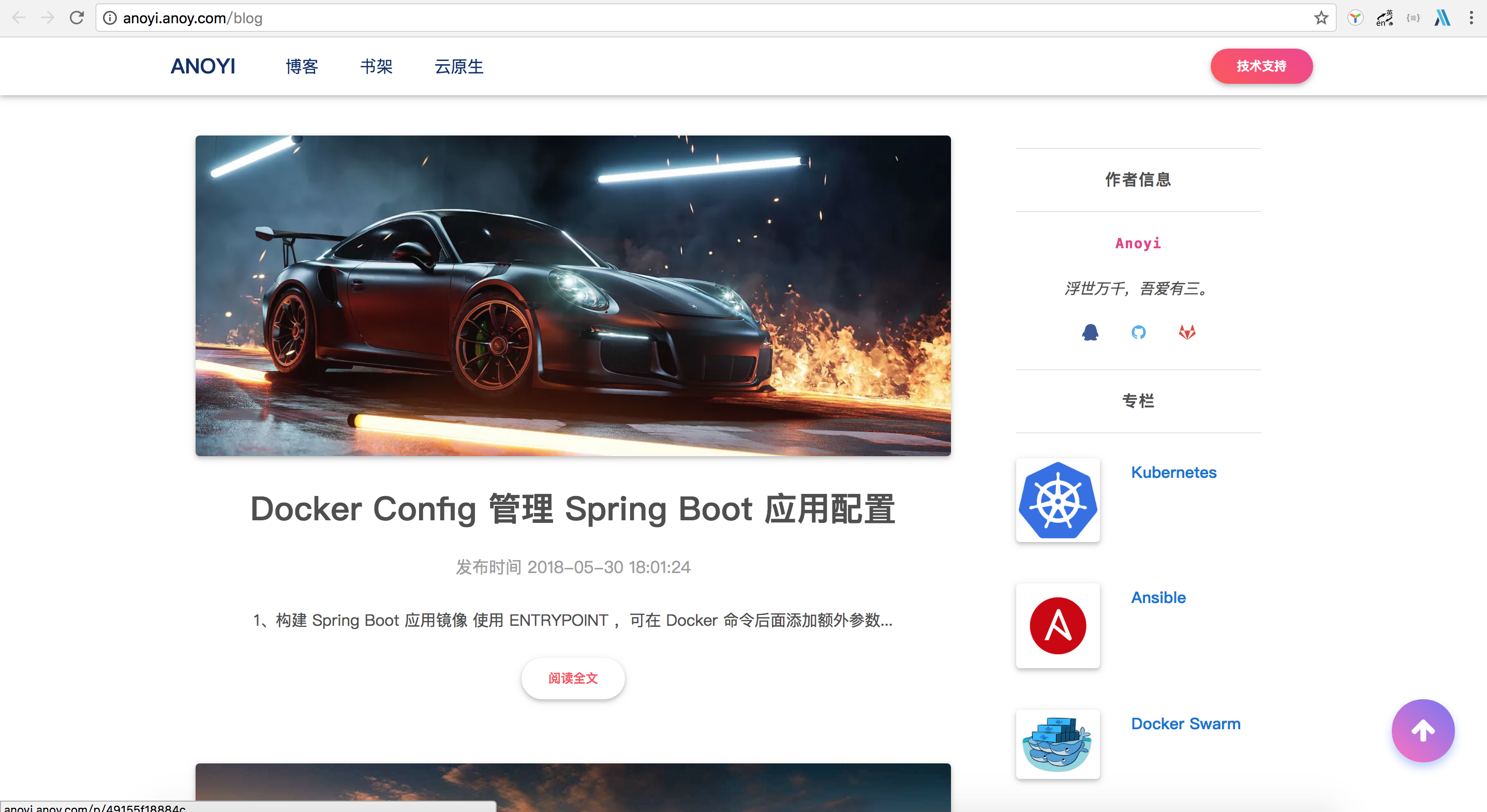
3,Simple fanout
apiVersion: extensions/v1beta1 kind: Ingress metadata: name: blog-ingress annotations: nginx.ingress.kubernetes.io/rewrite-target: / spec: rules: - host: anoy.com http: paths: - path: /anoyi backend: serviceName: blog-anoyi servicePort: 8080 - path: /science backend: serviceName: blog-science servicePort: 8080
Simple path forwarding http://anoy.com/anoyi The request for the path is forwarded to the service blog-anoyi, which forwards the request for the path to the service blog-anoyi. http://anoy.com/science Forwarding to service blog-science, the ingress rule is as follows:
Name: blog-ingress Namespace: default Address: 192.168.99.100 Default backend: default-http-backend:80 () Rules: Host Path Backends ---- ---- -------- anoy.com /anoyi blog-anoyi:8080 (<none>) /science blog-science:8080 (<none>) Annotations: nginx.ingress.kubernetes.io/rewrite-target: / Events: Type Reason Age From Message ---- ------ ---- ---- ------- Normal CREATE 26s nginx-ingress-controller Ingress default/blog-ingress Normal UPDATE 4s nginx-ingress-controller Ingress default/blog-ingress
Because the path jump of the blog mirror is not suitable for this scenario, there is no screenshot here.
TLS
You can protect Ingress by specifying a Secure that contains the TLS private key and certificate. Currently, Ingress supports only one TLS port 443. If different hosts are specified in the configuration part of TLS in Ingress, they are multiplexed on the same port according to the host name specified through the SNI TLS extension (in the case of Ingress Controller supporting SNI). TLS keys must contain keys named tls.crt and tls.key, which contain certificates and private keys for TLS.
Example: Adding TLS to Ingress of "Name based virtual hosting" type
Generating CA Private Key and Certificate
openssl genrsa -out tls.key 2048
openssl req -x509 -new -key tls.key -out tls.crt
View the base64 values of tls.key and tls.crt:
cat tls.key | base64
cat tls.crt | base64
Create Secret with tls.key and tls.crt
apiVersion: v1 kind: Secret metadata: name: ingress-tls type: Opaque data: tls.key: <Above tls.key Of Base64 value> tls.crt: <Above tls.crt Of Base64 value>
Create Ingress with TLS
apiVersion: extensions/v1beta1 kind: Ingress metadata: name: blog-ingress spec: tls: - secretName: ingress-tls rules: - host: anoyi.anoy.com http: paths: - backend: serviceName: blog-anoyi servicePort: 8080 - host: science.anoy.com http: paths: - backend: serviceName: blog-science servicePort: 8080
Visit https://anoyi.anoy.com/ Discovered that the browser showed "unsafe" because the certificate did not pass tripartite authentication.
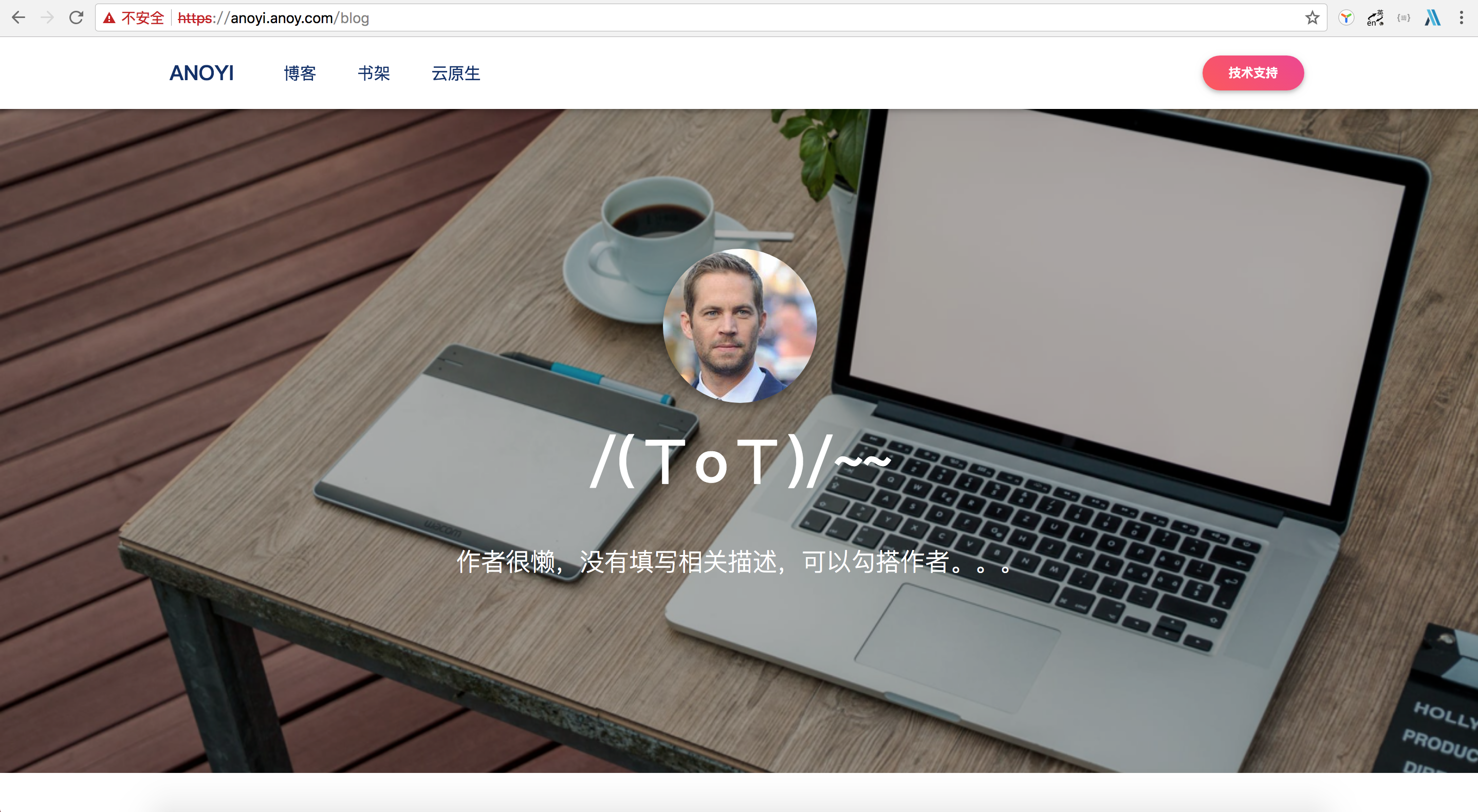
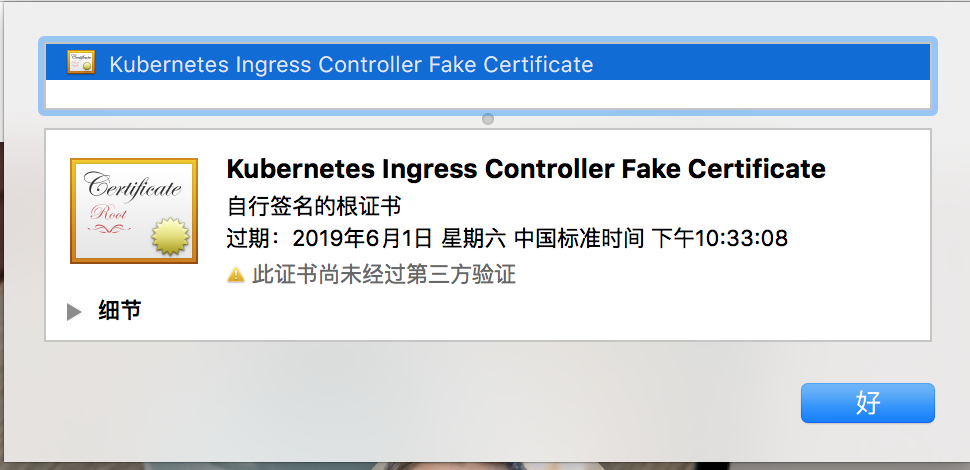
How to solve it? Simply add tls.crt to the system's trusted certificate list.