- Dashboard is the official WEB UI of kubernetes.
- Heapster adds usage statistics and monitoring functions for clusters and dashboards for Dashboard. Use InfluxDB as the back-end storage for Heapster.
Dashboard Installation
kubernetes dashboard official Resource Definition Document: https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes-dashboard.yaml
Note:
- Service definitions in the default resource definition document do not use NodePort and cannot be accessed outside the server
- The permission definition in the default resource definition document contains only the minimum permissions required by dashboard. It does not support access other than local access. Create An Authentication Token is needed to provide access independently.
By looking at the definition document of dashboard, the required image is k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.0. We pull the image on all node nodes:
docker pull mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.0 docker tag mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.0 k8s.gcr.io/kubernetes-dashboard:v1.10.0
Using anbile-playbook, the script is as follows:
--- - hosts: slave remote_user: root tasks: - name: copy pull-images-nodes-dashboard.sh to remote nodes copy: src=../pull-images-nodes-dashboard.sh dest=/tmp/pull-images-nodes-dashboard.sh - name: pull images for node shell: sh /tmp/pull-images-nodes-dashboard.sh
Since there was no - adm64 suffix when using kubeadm to install kubernetes before, in order to maintain uniformity, it is necessary to modify the image name used in the kubernetes-dashboard.yaml document.
Image PullPolicy: IfNotPresent, a pull strategy for adding mirrors to the image, guarantees that you do not pull on the network if you have mirrors locally.
containers: - name: kubernetes-dashboard image: k8s.gcr.io/kubernetes-dashboard:v1.10.0 imagePullPolicy: IfNotPresent
Here, the mirror can also be downloaded and stored in the local warehouse, and then the configured mirror address can be changed to the address of the private warehouse.
Service Extranet Access
Modify the definition of Service, type NodePort, as follows:
kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system spec: type: NodePort ports: - port: 443 targetPort: 8443 nodePort: 8443 selector: k8s-app: kubernetes-dashboard
dashboard External access is supported only https Agreement.
Modify permission configuration
When the default role permissions are logged in, the following problems arise:
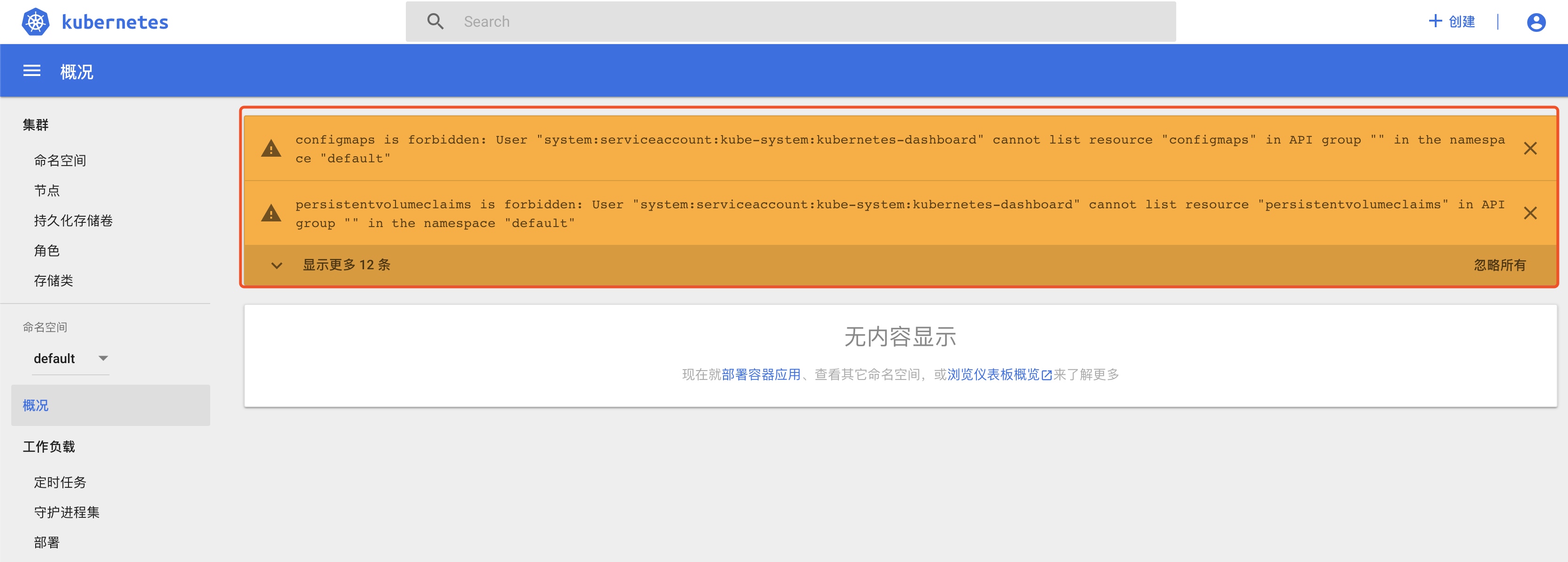
The authority of kubernetes-dashboard can be adjusted according to actual usage.
It mainly modifies Role and Role Binding.
Annotation kubernetes-dashboard.yml In the Role and Role Binding section.
The original RBAC authorization is based on namespace authorization (using Role and RoleBinding), instead of cluster-based authorization (using Cluster Role and Cluster RoleBinding). After the cluster authorizes admin to login, it can manage the resources under each namespace of the whole cluster. However, in actual production use, it should still distinguish between user and namespace authorization.
Detailed RBAC instructions, refer to kubernetes official website: Using RBAC Authorization
The allocation of authorized resources should be changed to:
kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kube-system roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io
Deploy kubernetes dashboard using kubectl apply-f dashboard/ with new configuration.
Visit dashboard: login https://10.20.13.24:30443.
You can view the resources of various kubernetes clusters.
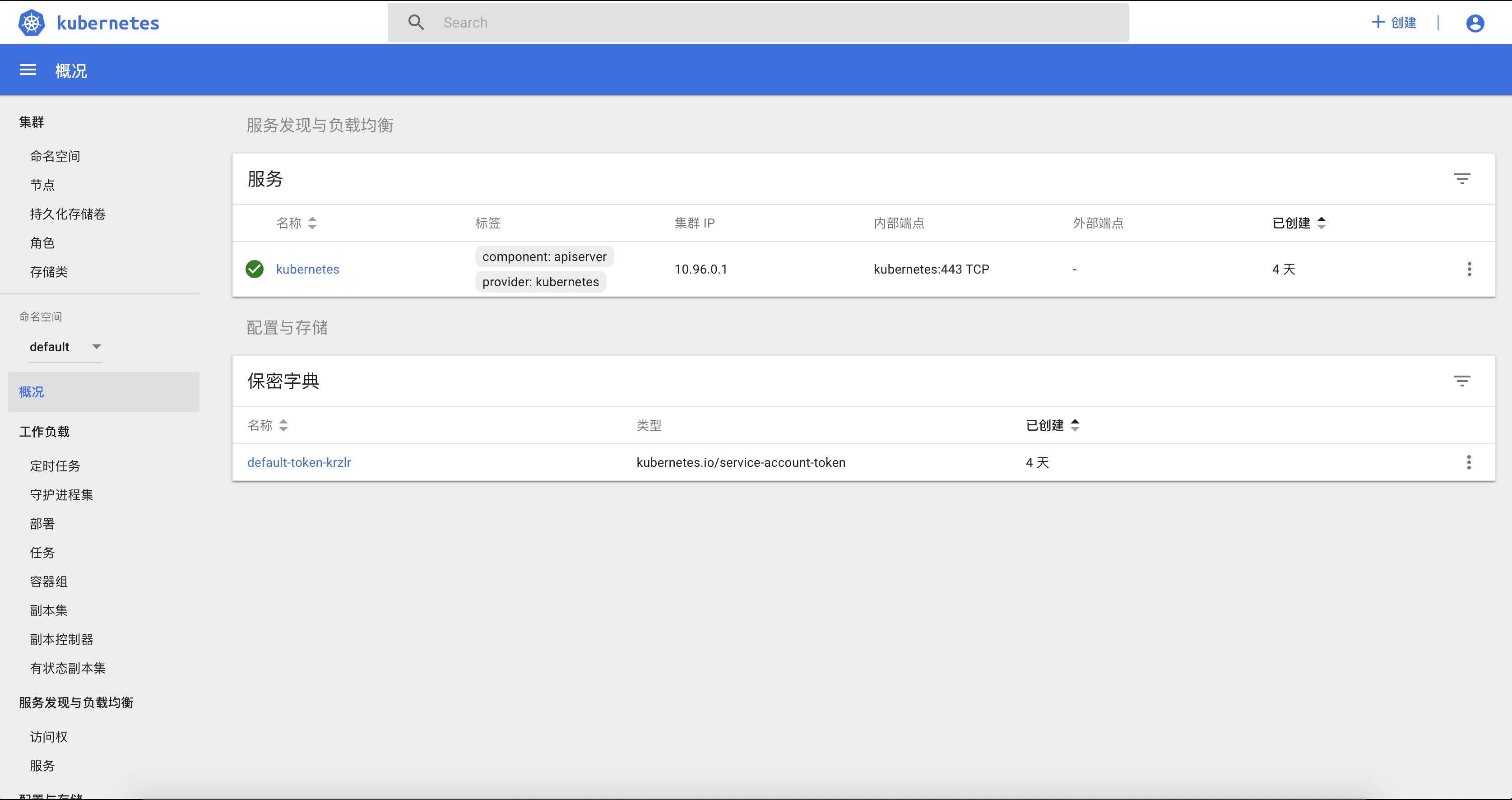
The load of kube-system space: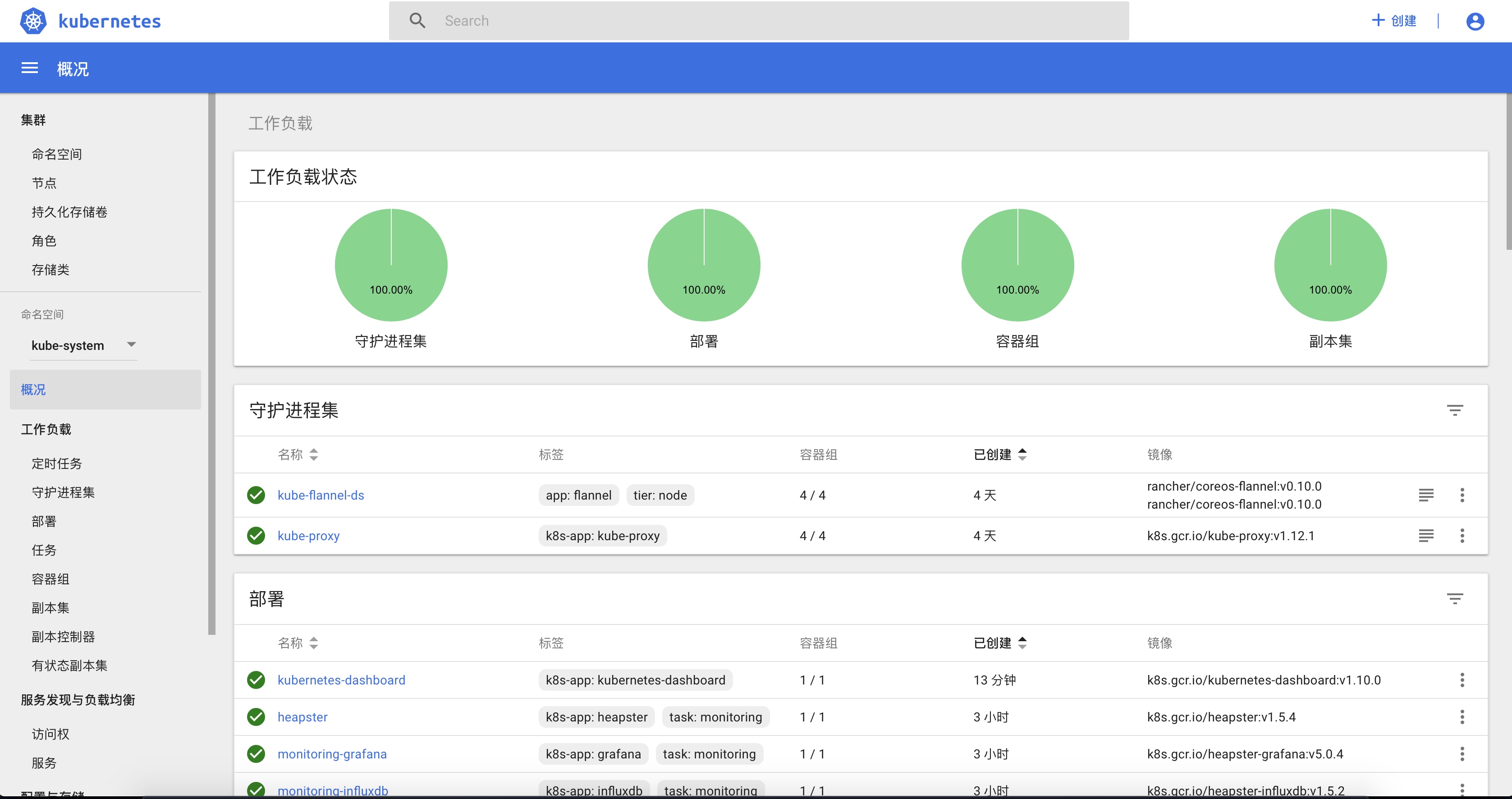
Complete kubernetes dashboard configuration reference at the end of the article.
Start dashboard
Start dashboard: kubectl apply-f kubernetes-dashboard.yaml
View the running status of the pod:
[root@kuber24 dashboard]# kubectl get pods --all-namespaces -o wide NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE kube-system coredns-576cbf47c7-75gcc 1/1 Running 0 4d19h 10.1.0.3 kuber24 <none> kube-system coredns-576cbf47c7-v242w 1/1 Running 0 4d19h 10.1.0.2 kuber24 <none> kube-system etcd-kuber24 1/1 Running 2 4d19h 10.20.13.24 kuber24 <none> kube-system kube-apiserver-kuber24 1/1 Running 1 4d19h 10.20.13.24 kuber24 <none> kube-system kube-controller-manager-kuber24 1/1 Running 2 4d19h 10.20.13.24 kuber24 <none> kube-system kube-flannel-ds-6hqc4 1/1 Running 0 3d19h 10.20.13.25 kuber25 <none> kube-system kube-flannel-ds-bs4b7 1/1 Running 0 3d19h 10.20.13.27 kuber27 <none> kube-system kube-flannel-ds-gwcj5 1/1 Running 0 4d16h 10.20.13.24 kuber24 <none> kube-system kube-flannel-ds-tmsbc 1/1 Running 0 3d19h 10.20.13.26 kuber26 <none> kube-system kube-proxy-fqm89 1/1 Running 0 3d19h 10.20.13.27 kuber27 <none> kube-system kube-proxy-nd875 1/1 Running 2 4d19h 10.20.13.24 kuber24 <none> kube-system kube-proxy-qsf9z 1/1 Running 0 3d19h 10.20.13.25 kuber25 <none> kube-system kube-proxy-ww8x7 1/1 Running 0 3d19h 10.20.13.26 kuber26 <none> kube-system kube-scheduler-kuber24 1/1 Running 2 4d19h 10.20.13.24 kuber24 <none> kube-system kubernetes-dashboard-68bbb49dc-kl5gn 1/1 Running 0 16s 10.1.3.2 kuber27 <none>
The access address of dashboard is: https://<master-ip>: <dashboard-nodeport>.
If ErrImagePull occurs, first check whether the physical node deployed by pod has a dashboard image, and then determine whether the image name and version information are consistent with the yml definition.
Use kubectl to get secret -- all-namespaces | grep dashboard to view the dashboard associated identity token.
[root@kuber24 dashboard]# kubectl get Secret --all-namespaces|grep dashboard kube-system kubernetes-dashboard-certs Opaque 0 152m kube-system kubernetes-dashboard-key-holder Opaque 2 75m kube-system kubernetes-dashboard-token-9msgn kubernetes.io/service-account-token 3 152m [root@kuber24 dashboard]# kubectl describe secret/kubernetes-dashboard-token-9msgn -n kube-system Name: kubernetes-dashboard-token-9msgn Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: kubernetes-dashboard kubernetes.io/service-account.uid: 43b5fdcf-d67d-11e8-8f15-00259029d7a2 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1025 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi05bXNnbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjQzYjVmZGNmLWQ2N2QtMTFlOC04ZjE1LTAwMjU5MDI5ZDdhMiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.LjBwNW93Gn-XRmJvkpHpPkpYhE3v7CB3Vm5GE1VvXRDSMtme7q7K-E522BS__I6BCqLTtmncN1rSkEYtBKgmfhUf6UhABL3vW8zoPYneFZINrcWA1wrlLx5TlIIcdDLVGrWQUbv3X5NYVfP-yhCuLMv7K3glXa01-B6L8Mgm8EiuMJqZ6ypiGUySl3dLld0vu4reT5fIHgipziuChZWLrYd2mPHXNesVv4UHw_UGASD0-CCEtMvTZ5Bgvs3IP278qOw8AyAioBDNMjPTqri4MDBbkzuXjmXhBiknA6yBDYD4piBt_cjVWq6diTwV2veFCiGMxfetz36AkgMFSSQjKA
The preceding one is the default installation token of kubernetes dashboard.
Heapster installation
Heapster relies on influxdb to download the configuration resource definition document and authorization definition document run by heapster.
mkdir heapster cd heapster wget https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/grafana.yaml wget https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/heapster.yaml wget https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/influxdb/influxdb.yaml wget https://raw.githubusercontent.com/kubernetes/heapster/master/deploy/kube-config/rbac/heapster-rbac.yaml
Prepare the mirror
Look at the resource definition document and find the image you need to use, as follows:
k8s.gcr.io/heapster-grafana-amd64:v5.0.4 k8s.gcr.io/heapster-amd64:v1.5.4 k8s.gcr.io/heapster-influxdb-amd64:v1.5.2
Use scripts to pull images on node s:
#!/bin/bash images=(kube-proxy-amd64:v1.12.1 pause-amd64:3.1 kubernetes-dashboard-amd64:v1.10.0 heapster-grafana-amd64:v5.0.4 heapster-amd64:v1.5.4 heapster-influxdb-amd64:v1.5.2) for imageName in ${images[@]} ; do docker pull mirrorgooglecontainers/$imageName if [[ $imageName =~ "amd64" ]]; then docker tag mirrorgooglecontainers/$imageName "k8s.gcr.io/${imageName//-amd64/}" else docker tag mirrorgooglecontainers/$imageName k8s.gcr.io/$imageName fi # docker rmi mirrorgooglecontainers/$imageName done
Since there was no - adm64 suffix when using kubeadm to install kubernetes before, in order to maintain uniformity, it is necessary to modify the image name used in the kubernetes-dashboard.yaml document.
In the heapster folder directory created above, run:
kubectl apply -f ./heapster/
Delete resources related to kubernetes dashboard
After using the official kubernetes dashboard configuration, the login system does not have any permissions and needs to be changed. Before changing, clean up the resources that were configured and run before.
- Delete secret: kubectl delete secret $(kubectl get secret-n kube-system | grep dashboard | awk'{print $1}') - n kube-system
- Delete Service Account: kubectl delete Service Account $(kubectl get Service Account - n kube-system | grep dashboard | awk'{print $1}') - n kube-system
- Delete Role: kubectl delete role $(kubectl get role - n kube-system | grep dashboard | awk'{print $1}') - n kube-system
- Delete RoleBinding: kubectl delete RoleBinding $(kubectl get RoleBinding-n kube-system | grep dashboard | awk'{print $1}') - n kube-system
- Delete Deployment: kubectl delete Deployment $(kubectl get Deployment - n kube-system | grep dashboard | awk'{print $1}') - n kube-system
- Delete Service: kubectl delete Service $(kubectl get service-n kube-system | grep dashboard | awk'{print $1}') - n kube-system
Clear:
kubectl delete secret $(kubectl get secret -n kube-system|grep dashboard| awk '{print $1}') -n kube-system kubectl delete ServiceAccount $(kubectl get ServiceAccount -n kube-system|grep dashboard| awk '{print $1}') -n kube-system kubectl delete Role $(kubectl get Role -n kube-system|grep dashboard| awk '{print $1}') -n kube-system kubectl delete RoleBinding $(kubectl get RoleBinding -n kube-system|grep dashboard| awk '{print $1}') -n kube-system kubectl delete RoleBinding $(kubectl get RoleBinding -n kube-system|grep dashboard| awk '{print $1}') -n kube-system kubectl delete Deployment $(kubectl get Deployment -n kube-system|grep dashboard| awk '{print $1}') -n kube-system kubectl delete Service $(kubectl get Service -n kube-system|grep dashboard| awk '{print $1}') -n kube-system
Complete kubernetes dashboard configuration
# Copyright 2017 The Kubernetes Authors. # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. # ------------------- Dashboard Secret ------------------- # apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kube-system type: Opaque --- # ------------------- Dashboard Service Account ------------------- # apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system --- # # ------------------- Dashboard Role & Role Binding ------------------- # # # kind: Role # apiVersion: rbac.authorization.k8s.io/v1 # metadata: # name: kubernetes-dashboard-minimal # namespace: kube-system # rules: # # Allow Dashboard to create 'kubernetes-dashboard-key-holder' secret. # - apiGroups: [""] # resources: ["secrets"] # verbs: ["create"] # # Allow Dashboard to create 'kubernetes-dashboard-settings' config map. # - apiGroups: [""] # resources: ["configmaps"] # verbs: ["create"] # # Allow Dashboard to get, update and delete Dashboard exclusive secrets. # - apiGroups: [""] # resources: ["secrets"] # resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"] # verbs: ["get", "update", "delete"] # # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. # - apiGroups: [""] # resources: ["configmaps"] # resourceNames: ["kubernetes-dashboard-settings"] # verbs: ["get", "update"] # # Allow Dashboard to get metrics from heapster. # - apiGroups: [""] # resources: ["services"] # resourceNames: ["heapster"] # verbs: ["proxy"] # - apiGroups: [""] # resources: ["services/proxy"] # resourceNames: ["heapster", "http:heapster:", "https:heapster:"] # verbs: ["get"] # # --- # apiVersion: rbac.authorization.k8s.io/v1 # kind: RoleBinding # metadata: # name: kubernetes-dashboard-minimal # namespace: kube-system # roleRef: # apiGroup: rbac.authorization.k8s.io # kind: Role # name: kubernetes-dashboard-minimal # subjects: # - kind: ServiceAccount # name: kubernetes-dashboard # namespace: kube-system # --- # ---------- Dashboard ClusterRole & ClusterRoleBinding --------- # kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kube-system roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io --- # ------------------- Dashboard Deployment ------------------- # kind: Deployment apiVersion: apps/v1beta2 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard image: k8s.gcr.io/kubernetes-dashboard:v1.10.0 imagePullPolicy: IfNotPresent ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule --- # ------------------- Dashboard Service ------------------- # kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system spec: type: NodePort ports: - port: 443 targetPort: 8443 nodePort: 30443 selector: k8s-app: kubernetes-dashboard
Reference resources
Last
Thank you for your reading. If you have any questions, please leave a message.
Welcome to our company. My github See more about kubernetes'personal experience and make progress together.