Introduction to Harbor
Deploying the Docker Compose service on which Harbor depends
Deploy Harbor Service
Harbor Daily Operations Management
Harbor Management Life Cycle
Harbor is an open source enterprise Docker Registry project for VMware
Advantages of Harbor
Role-based Control Mirror-based replication strategies Support for LDAP/AD Image deletion and garbage collection Graphic UI audit RESTful API Proxy Unified acceptance of browser, Docker client requests through a front-end reverse proxy and forwarding requests to different services on the back-end Registry Responsible for storing Docker images and handling docker push/pull commands Core services Core features of Harbor, including UI,webhook,token services Database Provide database services for core service Log collector Responsible for collecting log s for other components for future analysis
Docker Private Warehouse Architecture Topology
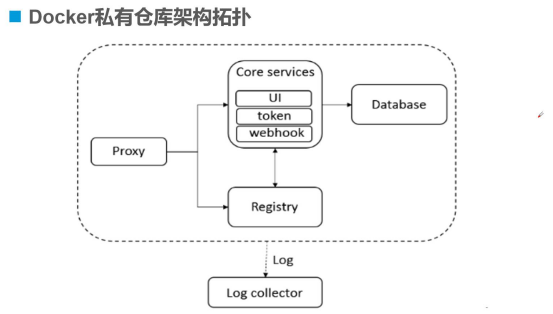
Users request access to Core services through the Proxy reverse proxy. The UI provides a web interface, token token. The server will give you a serial number after your first login. Next time you log in directly, you need to download the image information, attributes, all stored in the later database, and then retrieve the image from the registry private repository through the webhook callback.This series of operations is stored in the log.
------------------------------------------ Build harbor private warehouse-----------------------------------
harbor is deployed as multiple docker containers, so it can be deployed on any distribution of linux that supports docker We also need the docker-compose orchestration tool, which performs operations on multiple docker containers
[root@localhost ~]# mount.cifs //192.168.100.25/compose /abc/ Password for root@//192.168.100.25/compose: [root@localhost ~]# cd /abc/ [root@localhost abc]# ls consul_0.9.2_linux_amd64.zip consul-template_0.19.3_linux_amd64.zip docker-compose [root@localhost abc]# cp docker-compose /usr/local/bin/ [root@localhost abc]# tar zxvf harbor-offline-installer-v1.2.2.tgz -C /usr/local/ [root@localhost abc]# cd /usr/local/ [root@localhost local]# ls bin etc games harbor include lib lib64 libexec sbin share src [root@localhost local]# cd harbor/ [root@localhost harbor]# ls common docker-compose.yml harbor.v1.2.2.tar.gz NOTICE docker-compose.clair.yml harbor_1_1_0_template install.sh prepare docker-compose.notary.yml harbor.cfg LICENSE upgrade hostname = 192.168.136.185 #Open Private Warehouse [root@localhost harbor]# sh /usr/local/harbor/install.sh [root@localhost harbor]# docker-compose ps #If everything works, you can open a browser to access the administration page at http://192.168.136.185 //The default username password is admin, Harbor12345
Let's start by creating a project where our type of mirror can be placed
#We upload images locally [root@localhost harbor]# docker login -u admin -p Harbor12345 http://127.0.0.1 [root@localhost harbor]# docker pull cirros [root@localhost harbor]# docker tag cirros 127.0.0.1/chen/cirros:v1 [root@localhost harbor]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE 127.0.0.1/chen/cirros v1 bc94bceaae77 12 months ago 10.3MB cirros latest bc94bceaae77 12 months ago 10.3MB [root@localhost harbor]# docker push 127.0.0.1/chen/cirros:v1 The push refers to repository [127.0.0.1/chen/cirros] abbd6d6ac643: Pushed 75b99987219d: Pushed 0cc237193a30: Pushed v1: digest: sha256:96137d51e0e46006243fa2403723eb47f67818802d1175b5cde7eaa7f19446bd size: 943
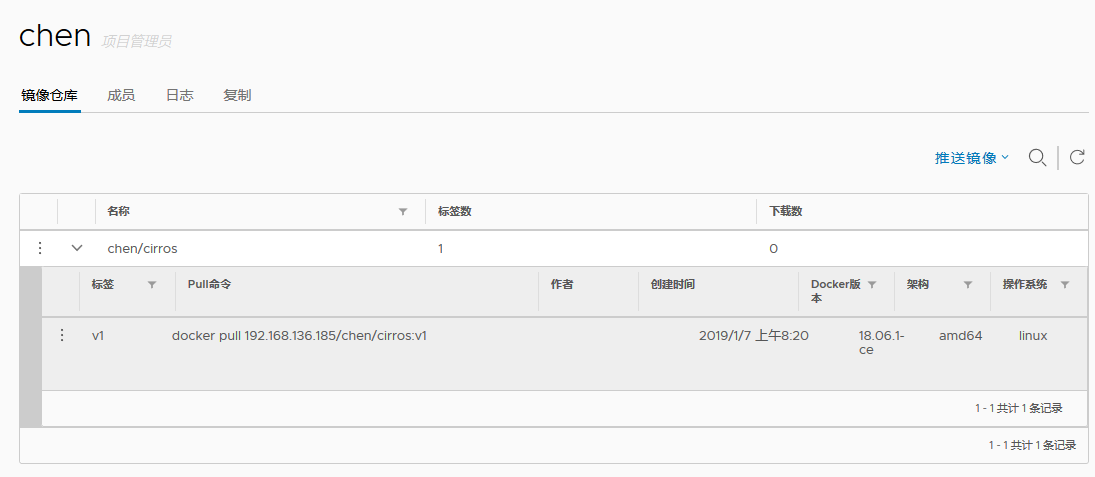
We check the web interface to see if the image was uploaded successfully
#Remote client uploads mirror to private repository #Remote login error [root@localhost ~]# docker login -u admin -p Harbor12345 http://192.168.136.185 WARNING! Using --password via the CLI is insecure. Use --password-stdin. Error response from daemon: Get https://192.168.136.185/v2/: dial tcp 192.168.136.185:443: connect: connection refused #We want to specify the private warehouse columns [root@localhost ~]# vim /usr/lib/systemd/system/docker.service 14 ExecStart=/usr/bin/dockerd -H fd:// --insecure-registry 192.168.136.185 --containerd=/run/contai nerd/containerd.sock [root@localhost ~]# systemctl daemon-reload [root@localhost ~]# systemctl restart docker [root@localhost ~]# docker login -u admin -p Harbor12345 http://192.168.136.185 #Remote download of mirror for private repository [root@localhost ~]# docker pull 192.168.136.185/chen/cirros:v1 #Remote upload mirror to private repository [root@localhost ~]# docker push 192.168.136.185/chen/cirros:v2 The push refers to repository [192.168.136.185/chen/cirros] abbd6d6ac643: Layer already exists 75b99987219d: Layer already exists 0cc237193a30: Layer already exists v2: digest: sha256:96137d51e0e46006243fa2403723eb47f67818802d1175b5cde7eaa7f
Web page validation
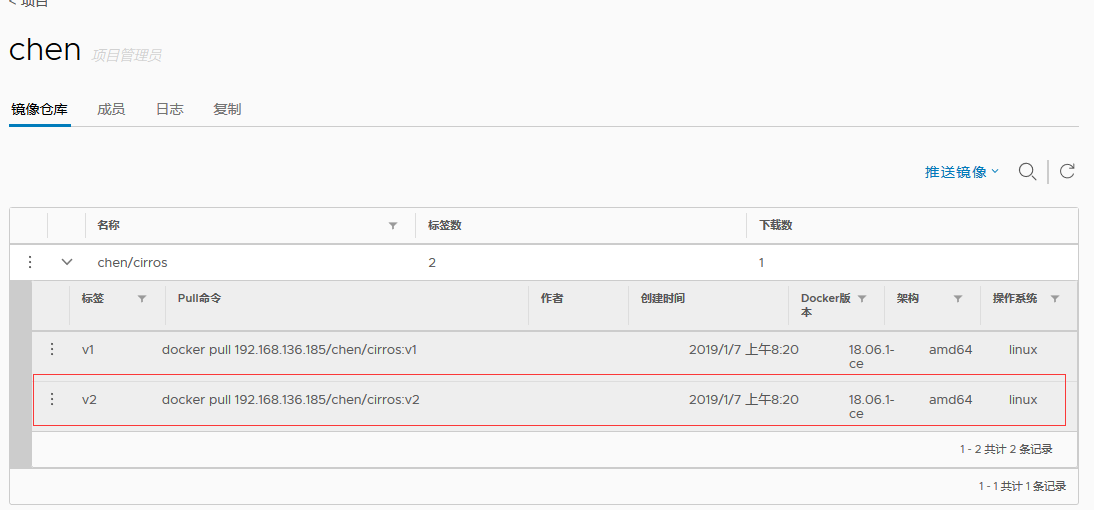
#Close harbor private warehouse [root@localhost harbor]# docker-compose down -v [root@localhost harbor]# ./prepare #Open Private Warehouse [root@localhost harbor]# docker-compose up -d
Create User
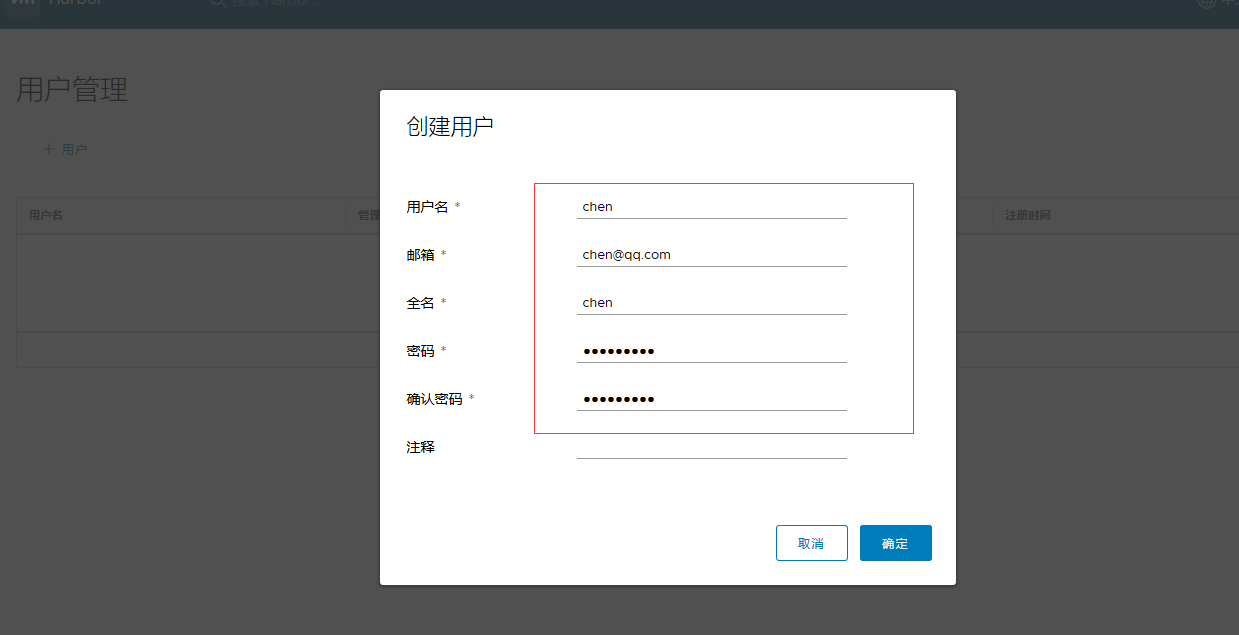
#We use the user we just created to log in to the private repository [root@localhost harbor]# docker login http://192.168.136.185 Username: chen Password:
We joined a user in the project
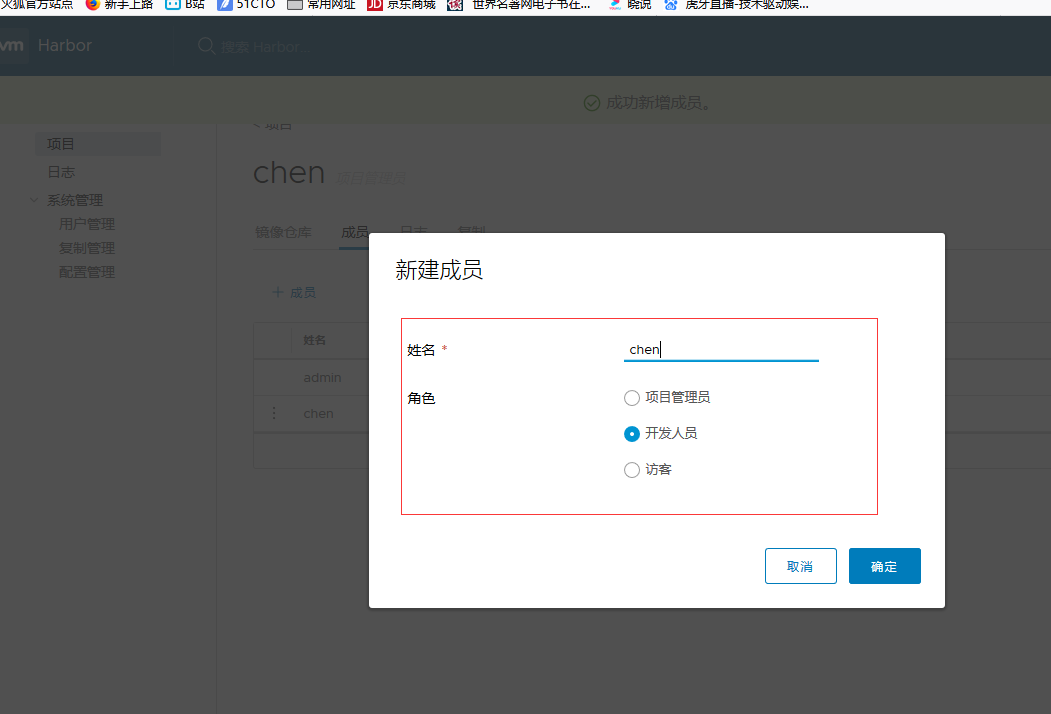
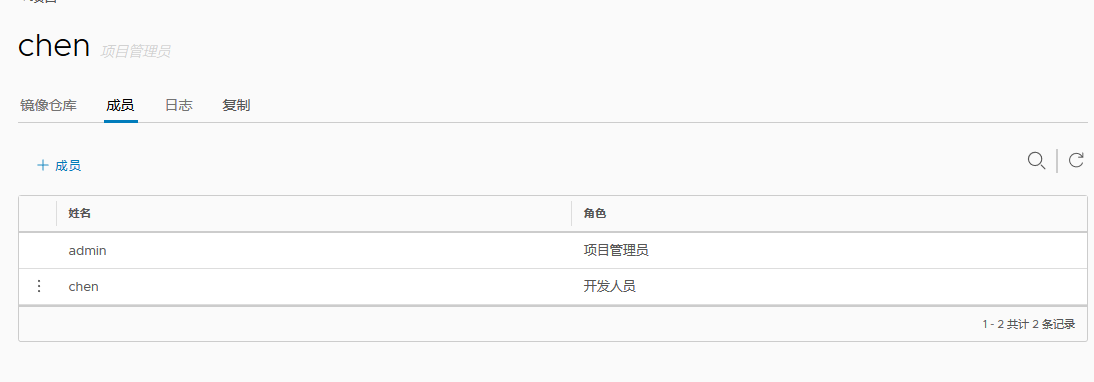
If you want to remove the service container while preserving the mirror database/database
docker-compose down -v
To redeploy, remove all data from the harbor service container
/var/log/Harbor/Catalog rm-rf /data/database/ /data/registry/