Article Directory
| Server name | IP Address | Explain |
|---|---|---|
| Server 200 | 192.168.1.200 | docker private warehouse |
| Server 210 | 192.168.2.210 | docker client |
| Software | version number | Query Command |
|---|---|---|
| docker | Docker version 18.09.1, build 4c52b90 | docker -v |
| centos8 | CentOS Linux release 8.0.1905 (Core) | cat /etc/redhat-release |
1. Private Warehouse Server 200 Create Certificate
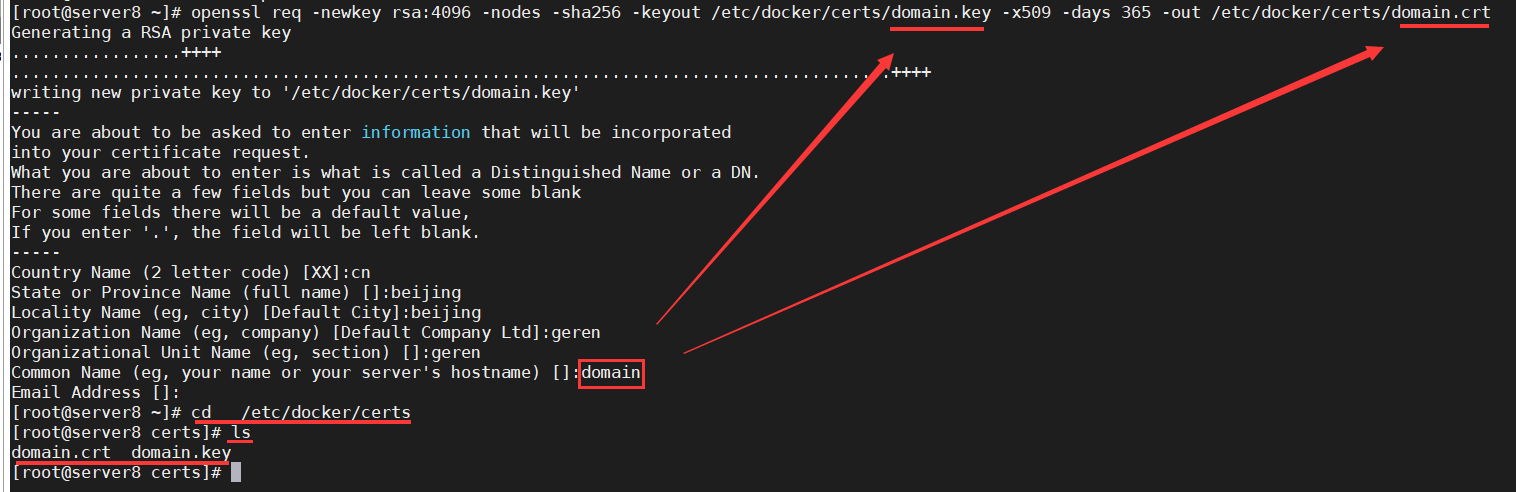
1. Private Warehouse Server 200 creates a certificate store directory/etc/docker/certs and creates certificates (the content you need to enter can be customized, but the domain name must match the command line, as shown below).
mkdir -p /etc/docker/certs openssl req -newkey rsa:4096 -nodes -sha256 -keyout /etc/docker/certs/domain.key -x509 -days 365 -out /etc/docker/certs/domain.crt cd /etc/docker/certs ls
2. Private warehouse server 200 uses certificates to create containers
1. Stop and delete the container registry.
docker ps -a docker stop registry docker rm registry
2. Use certificates to create container registries.
docker run -d \ -p 5000:5000 \ --restart=always \ --name registry \ -v /etc/docker/certs:/certs \ -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \ -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \ registry:latest
-v Mount local certs directory
- - restart: Set container restart policy
-e REGISTRY_HTTP_ADDR: Set the warehouse host address format.
-e REGISTRY_HTTP_TLS_CERTIFICATE: Set the environment variable to tell the container where the certificate is located.
3. Server 200 Local Test Upload and Download Mirrors
1. Copy the certs certificate into the new docker data directory.
mkdir -p /etc/docker/certs.d/domain/ cp /etc/docker/certs/domain.crt /etc/docker/certs.d/domain/ca.crt
2. Create a new label for the registry image. When the first part of the label is the host name and port, docker interprets the image as the location of the mirror warehouse when uploading it.
docker images docker tag registry:latest 192.168.1.200:5000/server-registry:latest
3. Upload a mirror of the new label to the private repository.
docker push 192.168.1.200:5000/server-registry
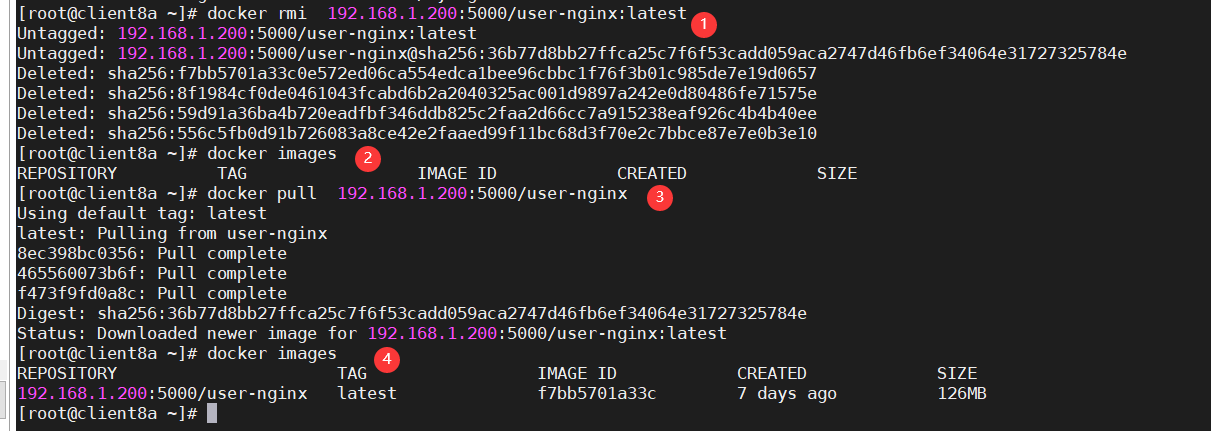
4. Test the download mirroring process: view and delete the local image of docker client server 210, confirm that there is no local image, download the private warehouse server 200 image, and view the downloaded local image.
docker images docker rmi 192.168.1.200:5000/server-registry docker images docker pull 192.168.1.200:5000/server-registry docker images
IV. Client 210 Test Upload and Download Mirrors
1. Client 210 copies the certs certificate of server 200 to the new docker data directory.
mkdir -p /etc/docker/certs.d/domain/ scp root@192.168.1.200:/etc/docker/certs/domain.crt /etc/docker/certs.d/domain/ca.crt
2. Create a new tag for the nginx image. When the first part of the tag is the host name and port, docker will interpret the image as the location of the mirror warehouse when uploading it.
docker images docker tag nginx:latest 192.168.1.200:5000/client-nginx:latest
3. Upload a mirror of the new label to the private repository.
docker push 192.168.1.200:5000/client-nginx
4. Test the download mirroring process: view and delete the local image of docker client server 210, confirm that there is no local image, download the private warehouse server 200 image, and view the downloaded local image.
docker images docker rmi 192.168.1.200:5000/client-nginx docker images docker pull 192.168.1.200:5000/client-nginx docker images

5. docker Private Warehouse Server 200 upload mirror error: x509: cannot validate certificate for 192.168.1.200 because it doesn't contain any IP SANs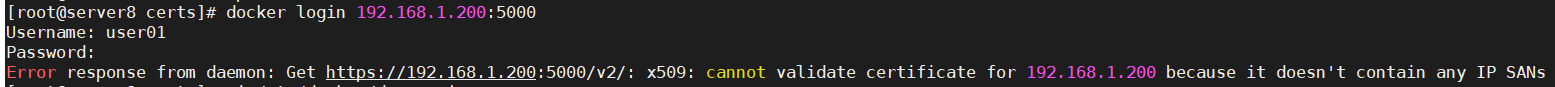
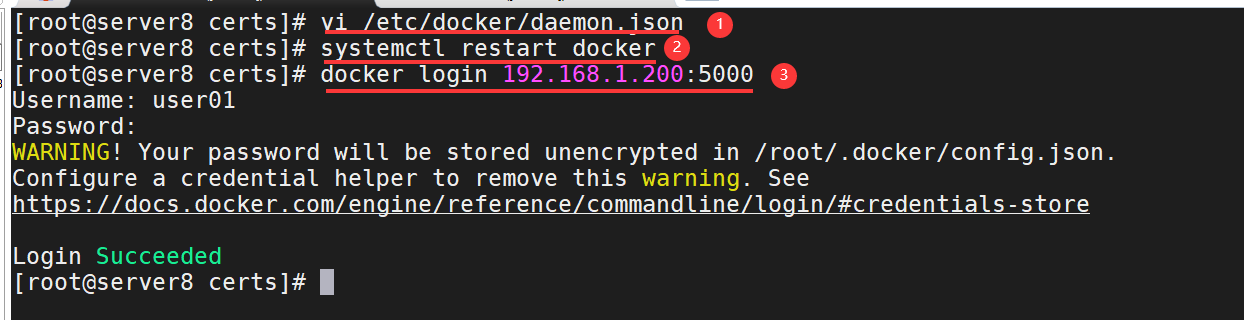
Solution: docker private warehouse server 200, edit configuration file/etc/docker/daemon.json, add content "private warehouse IP: port number", save configuration file, restart docker service.
vi /etc/docker/daemon.json
{ "registry-mirrors": ["https://njrds9qc.mirror.aliyuncs.com"], "insecure-registries": ["192.168.1.200:5000"] }
systemctl restart docker