catalog
1, What is a warehouse
2, Install and configure Docker Hub
3, Configure image accelerator
4, How Registry works
5, CONTENTS
6, Build private warehouse
1, What is a warehouse
What is a warehouse?
The docker warehouse is used to contain images. Docker provides a registration server
(Register) to save multiple warehouses. Each warehouse can contain multiple images with different tag s.
• the default warehouse used in Docker operation is the Docker Hub public warehouse.
2, Introduction to Docker Hub
Docker Hub
docker hub is a public warehouse maintained by docker company. Users can use it for free or purchase a private warehouse
3, Installation and configuration of docker
First of all https://hub.docker.com/ Sign up for an account
• create a new public warehouse on the docker hub
3.1 installing docker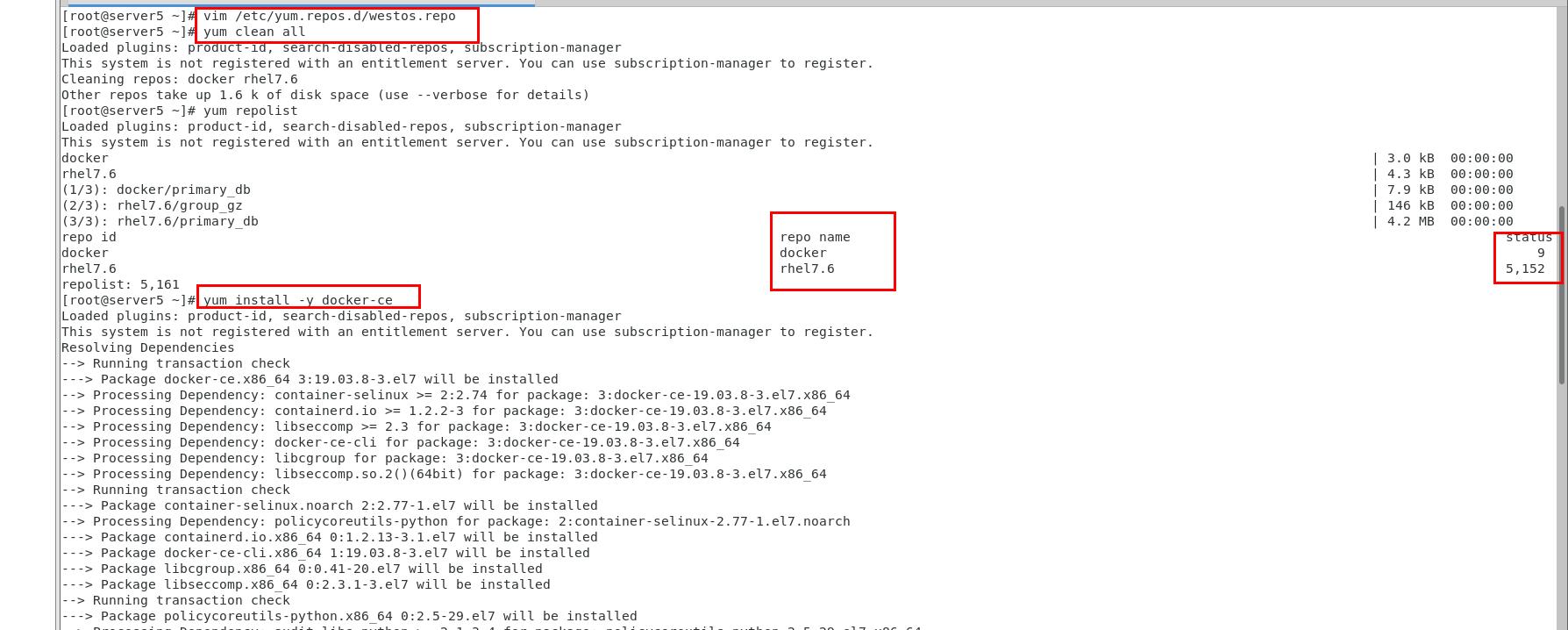
[root@server1 ~]# systemctl enable --now docker start docker Created symlink from /etc/systemd/system/multi-user.target.wants/docker.service to /usr/lib/systemd/system/docker.service.
decompression [root@server1 ~]# tar zxf harbor-offline-installer-v1.10.1.tgz [root@server1 ~]# ls anaconda-ks.cfg harbor harbor-offline-installer-v1.10.1.tgz [root@server1 ~]# cd harbor/ [root@server1 harbor]# ls common.sh harbor.v1.10.1.tar.gz harbor.yml install.sh LICENSE prepare //Edit profile [root@server1 harbor]# vim harbor.yml 5 hostname: reg.westos.org 15 #port: 443 17 #certificate: /your/certificate/path 18 #private_key: /your/private/key/path 27 harbor_admin_password: westos //Run docker-compose-Linux-x86_64-1.24.1 [root@server1 ~]# mv docker-compose-Linux-x86_64-1.24.1 /usr/local/bin/docker-compose [root@server1 ~]# chmod +x /usr/local/bin/docker-compose //analysis [root@server1 ~]# Cat / etc / hosts add resolution 172.25.254.5 server1 reg.westos.org //function [root@server1 harbor]# / install.sh A file will be generated when finished [root@server1 harbor]# ls common common.sh (New) docker-compose.yml harbor.v1.10.1.tar.gz harbor.yml install.sh LICENSE prepare

3.2 create certificate and secret key
cd /data/ [root@server1 data]# mkdir -p certs //Only 365 days [root@server1 data]# openssl req -newkey rsa:4096 -nodes -sha256 -keyout certs/westos.org.key -x509 -days 365 -out certs/westos.org.crt
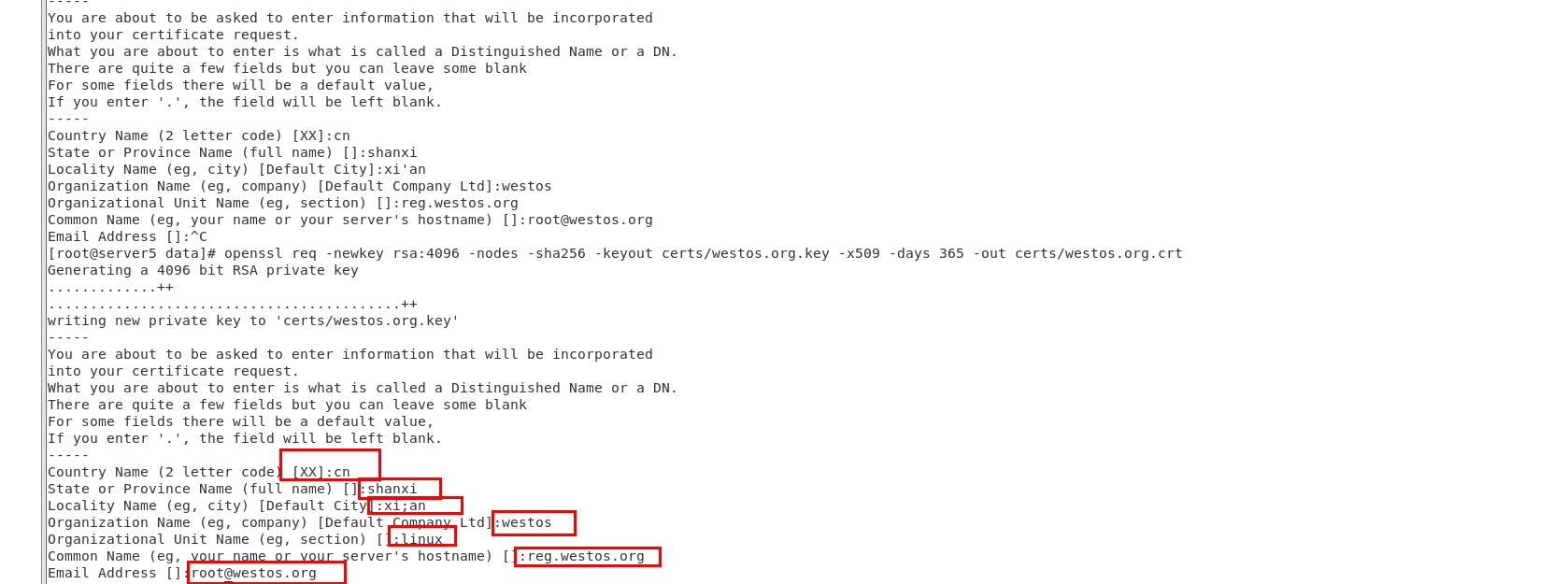
[root@server1 data]# cd certs/ [root@server1 certs]# ls westos.org.crt westos.org.key
3.3 setting encryption
[root@server1 harbor]# pwd /root/harbor [root@server1 harbor]# vim harbor.yml 17 certificate: /data/certs/westos.org.crt 18 private_key: /data/certs/westos.org.key
3.4 change configuration file, update
[root@server1 ~]# cd harbor/ [root@server1 harbor]# ls common common.sh docker-compose.yml harbor.v1.10.1.tar.gz harbor.yml install.sh LICENSE prepare [root@server1 harbor]# . / prepare clear the original configuration prepare base dir is set to /root/harbor Clearing the configuration file: /config/log/logrotate.conf Clearing the configuration file: /config/log/rsyslog_docker.conf Clearing the configuration file: /config/nginx/nginx.conf Clearing the configuration file: /config/core/env Clearing the configuration file: /config/core/app.conf Clearing the configuration file: /config/registry/config.yml Clearing the configuration file: /config/registry/root.crt Clearing the configuration file: /config/registryctl/env Clearing the configuration file: /config/registryctl/config.yml Clearing the configuration file: /config/db/env Clearing the configuration file: /config/jobservice/env Clearing the configuration file: /config/jobservice/config.yml Generated configuration file: /config/log/logrotate.conf Generated configuration file: /config/log/rsyslog_docker.conf Generated configuration file: /config/nginx/nginx.conf Generated configuration file: /config/core/env Generated configuration file: /config/core/app.conf Generated configuration file: /config/registry/config.yml Generated configuration file: /config/registryctl/env Generated configuration file: /config/db/env Generated configuration file: /config/jobservice/env Generated configuration file: /config/jobservice/config.yml loaded secret from file: /secret/keys/secretkey Generated configuration file: /compose_location/docker-compose.yml Clean up the input dir [root@server1 harbor]# / install.sh Restart [root@server2harbor]# Netstat - tnpl 443 port is open Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:1514 0.0.0.0:* LISTEN 19178/docker-proxy tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 7510/sshd tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 7677/master tcp6 0 0 :::80 :::* LISTEN 19826/docker-proxy tcp6 0 0 :::22 :::* LISTEN 7510/sshd tcp6 0 0 ::1:25 :::* LISTEN 7677/master tcp6 0 0 :::443 :::* LISTEN 19806/docker-proxy
3.5 browser directly accesses host IP after adding certificate
4, Upload the image remotely to the built private warehouse
install docker Process and server5 identical [root@server5 ~]# cat /etc/hosts add resolution 172.25.254.1 server1 reg.westos.org //Get Nginx image [root@server5 ~]# docker load -i nginx.tar Import image in container [root@server5 ~]# docker images view REPOSITORY TAG IMAGE ID CREATED SIZE nginx latest e548f1a579cf 2 years ago 109MB [root@server5 reg.westos.org]# mkdir -p /etc/docker/certs.d/reg.westos.org Create directory note domain name //Upload the certificate to the new directory and rename it ca.crt This path is the default setting and does not need to be restarted docker service [root@server1 certs]# scp westos.org.crt server5:/etc/docker/certs.d/reg.westos.org/ca.crt [root@server5 reg.westos.org]# pwd /etc/docker/certs.d/reg.westos.org [root@server5 reg.westos.org]# ls ca.crt
[root@server5 ~]# docker tag nginx:latest reg.westos.org/library/nginx : latest label specifies the path [root@server5 reg.westos.org]# docker login reg.westos.org You must log in the authentication domain name before uploading the image [root@server5 reg.westos.org]# docker push reg.westos.org/library/nginx Upload again successfully
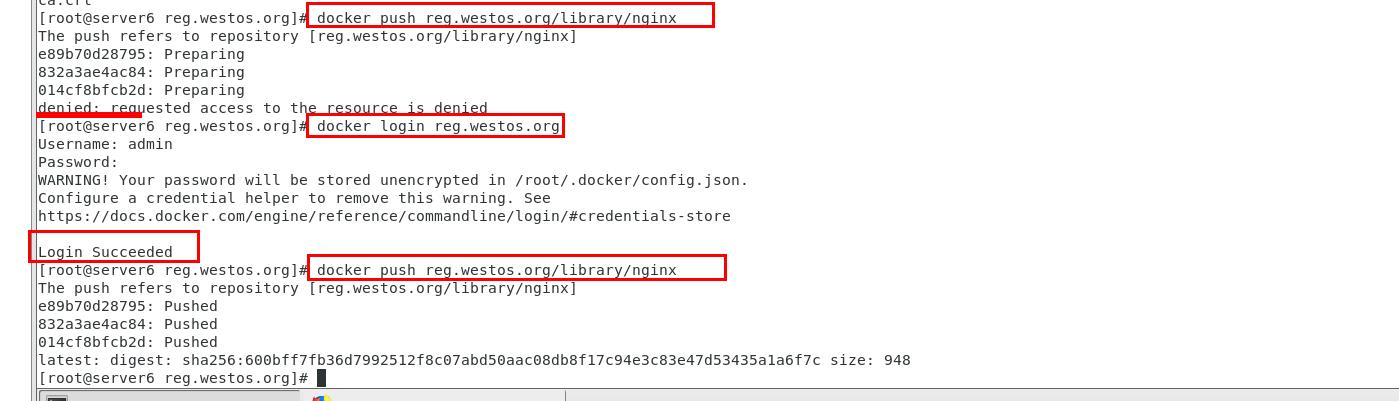
Enter the host IP of server: 1172.25.254.1 to view that the image has been uploaded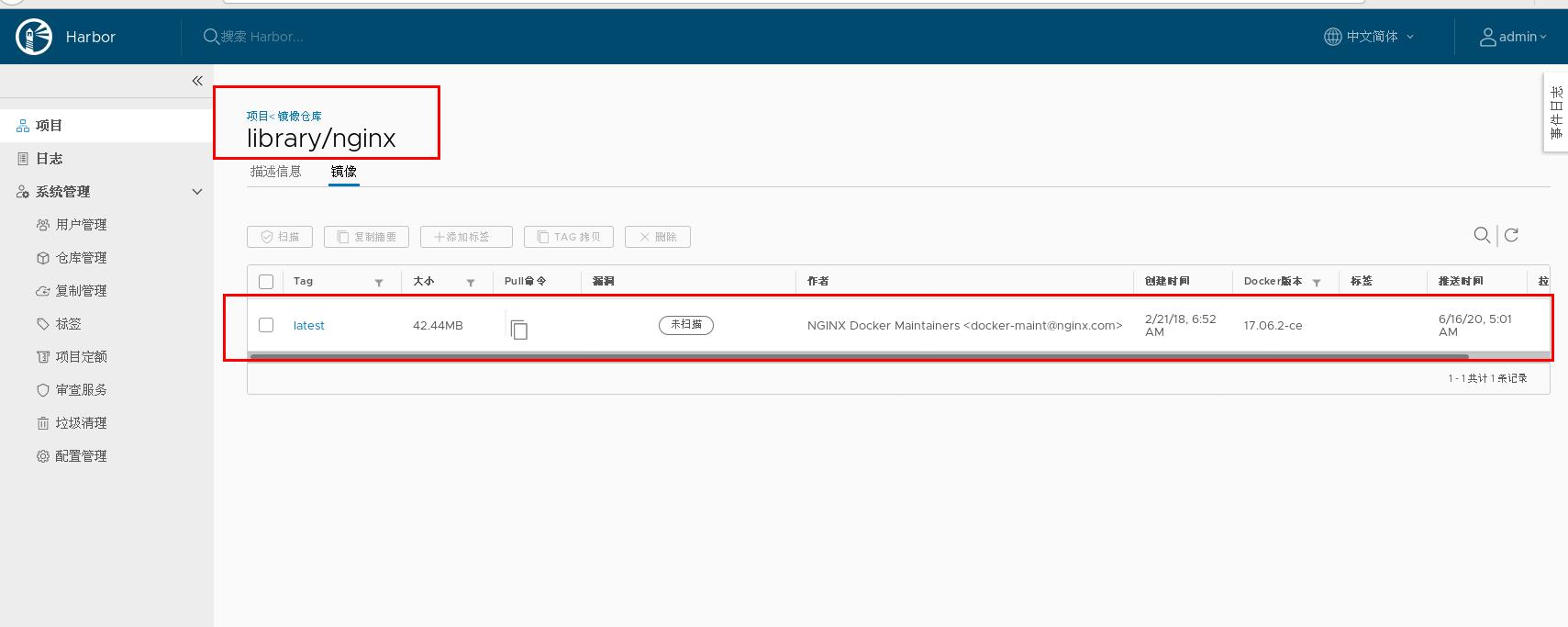
Note: you do not need to authenticate docker pull to download the image reg.westos.org/library/nginx
3, Configure image accelerator
Downloading images from the docker hub is too slow. You need to configure the image accelerator
Take Alibaba cloud as an example: (Alibaba cloud account needs to be registered in advance)
To configure the docker daemon file:
vim /etc/docker/daemon.json { "registry-mirrors": ["https://reg.westos.org"] } [root@server5 docker]# systemctl restart docker restart service
[root@server5 docker]# docker rmi nginx delete image Untagged: nginx:latest [root@server5 docker]# docker rmi reg.westos.org/library/nginx:latest [root@server5 docker]# docker images view REPOSITORY TAG IMAGE ID CREATED SIZE [root@server5 ~]# docker pull nginx sets the image accelerator to pull the image directly without specifying a long path
Test the image accelerator
Upload the game2048 image on server1, and then pull the image on server2
Authentication is required for uploading image: server1 Create certificate store directory [root@server1 docker]# mkdir -p certs.d/reg.westos.org/ [root@server1 docker]# ls certs.d key.json [root@server1 docker]# cd certs.d/reg.westos.org/ [root@server1 reg.westos.org]# scp /data/certs/westos.org.crt ca.crt [root@server1 reg.westos.org]# ls ca.crt [root@server1 reg.westos.org]# pwd /etc/docker/certs.d/reg.westos.org
[root@server1 reg.westos.org]# docker login reg.westos.org Authentication login Username: admin Password: WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded [root@server1 reg.westos.org]# cd [root@server1 ~]# ls anaconda-ks.cfg game2048.tar harbor harbor-offline-installer-v1.10.1.tgz [root@server1 ~]# docker load -i game2048.tar import image Loaded image: game2048:latest [root@server1 ~]# docker push reg.westos.org/library/game2048 Upload image to indicate warehouse Path The push refers to repository [reg.westos.org/library/game2048] 88fca8ae768a: Pushed 6d7504772167: Pushed 192e9fad2abc: Pushed 36e9226e74f8: Pushed 011b303988d2: Pushed latest: digest: sha256:8a34fb9cb168c420604b6e5d32ca6d412cb0d533a826b313b190535c03fe9390 size: 1364
server2 pull game2048
[root@server2 docker]# docker pull game2048 Using default tag: latest latest: Pulling from library/game2048 534e72e7cedc: Pull complete f62e2f6dfeef: Pull complete fe7db6293242: Pull complete 3f120f6a2bf8: Pull complete 4ba4e6930ea5: Pull complete Digest: sha256:8a34fb9cb168c420604b6e5d32ca6d412cb0d533a826b313b190535c03fe9390 Status: Downloaded newer image for game2048:latest docker.io/library/game2048:latest The pull address is pulled from the private warehouse //If there is no image in the private warehouse, it will be pulled from the official website, but it must be connected to the Internet
4, How Registry works
What happens behind a docker pull or push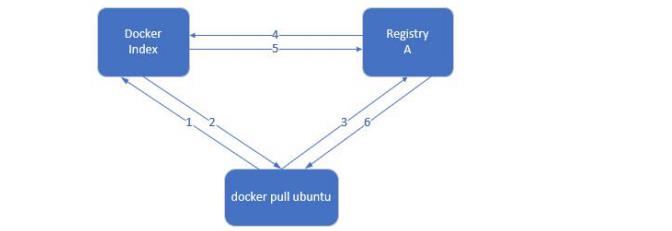
Index service mainly provides the function of image index and user authentication. When downloading an image, you will first go to the index service for authentication, then find the address of the registry where the image is located and put it back to the docker client. The docker client then downloads the image from the registry during the download process Registry will check the validity of the client token by index. Different images can be saved in different registry services, and the index information is put in the index service.
Docker Registry has three roles: index, registry and registry client.
• index • be responsible for and maintain information about user accounts, image validation, and public namespaces. • Web UI • metadata storage • certification services • symbolization
registry: it is a warehouse for images and charts. It does not have a local database or provide user authentication. It is authenticated by Token of Index Auth service.
• Registry Client • Docker acts as a registry client to maintain push and pull, as well as client authorization.
New harbor warehouse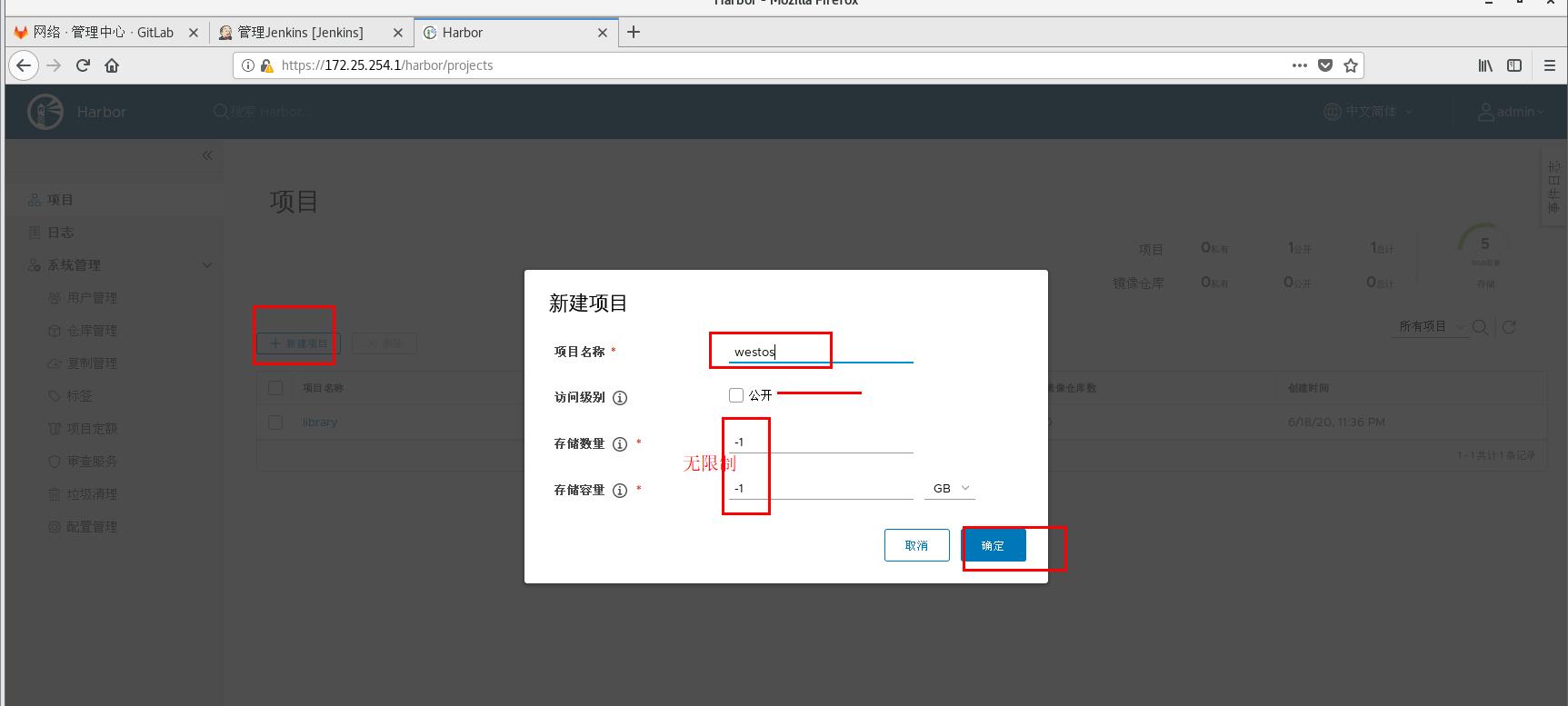
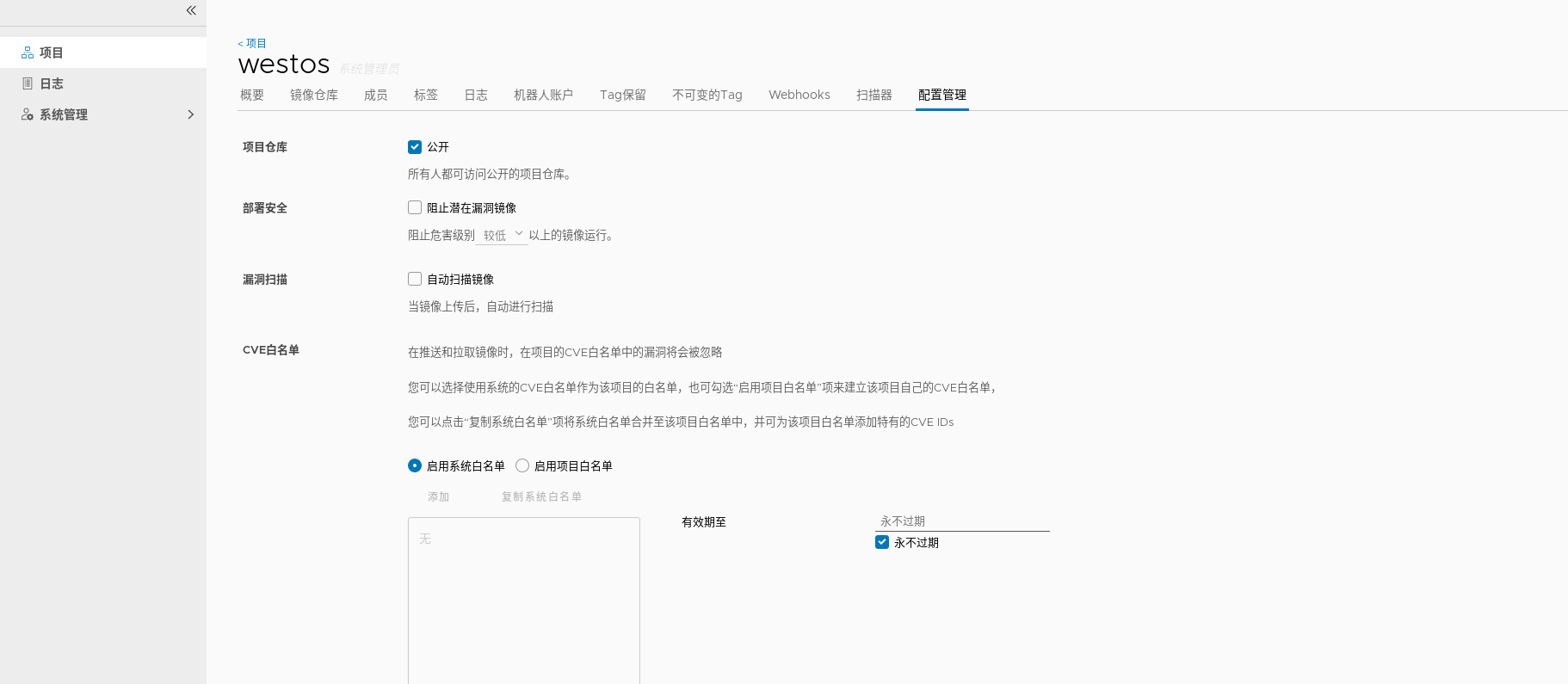
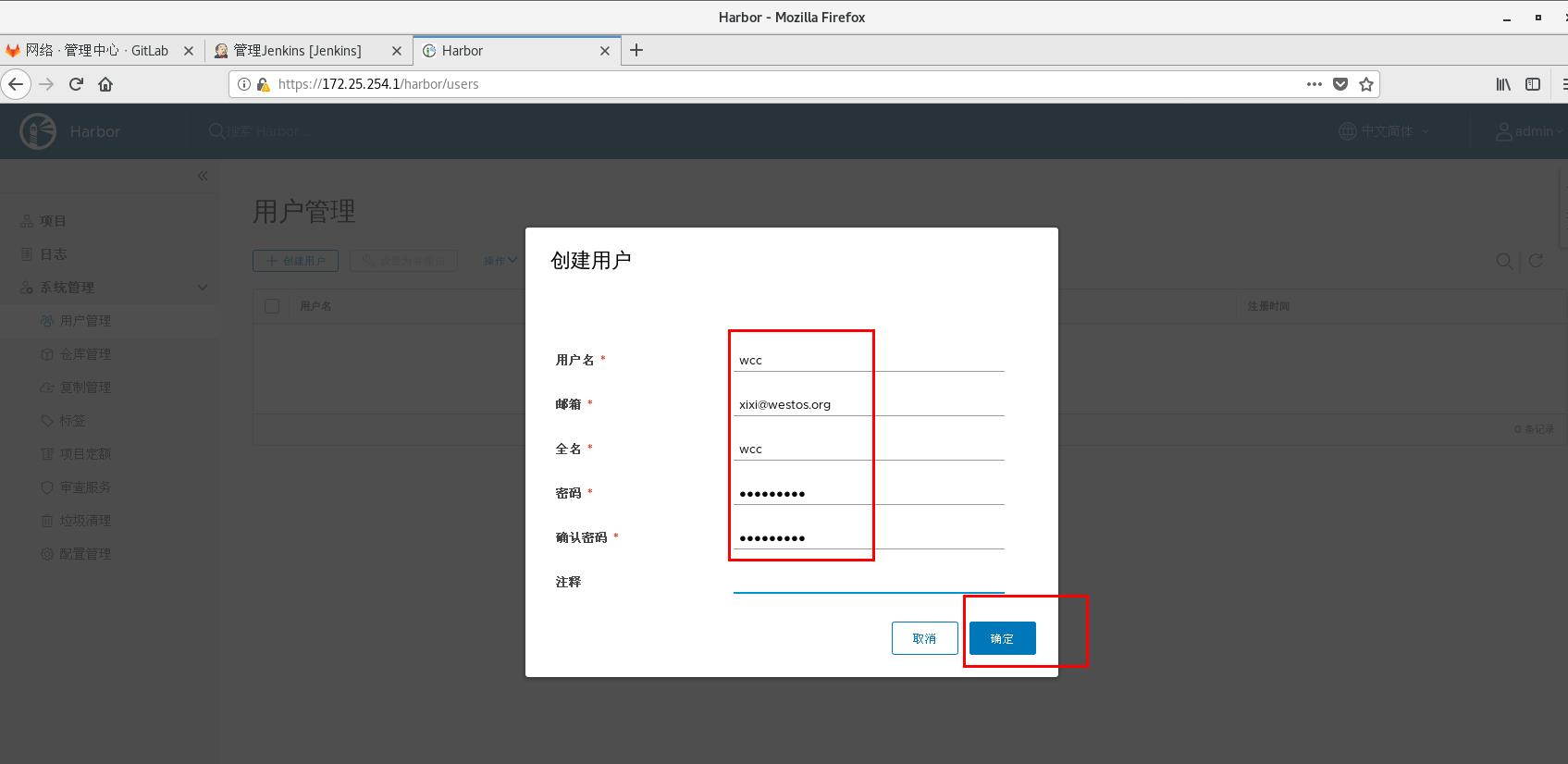
Developers can image but not manage deletion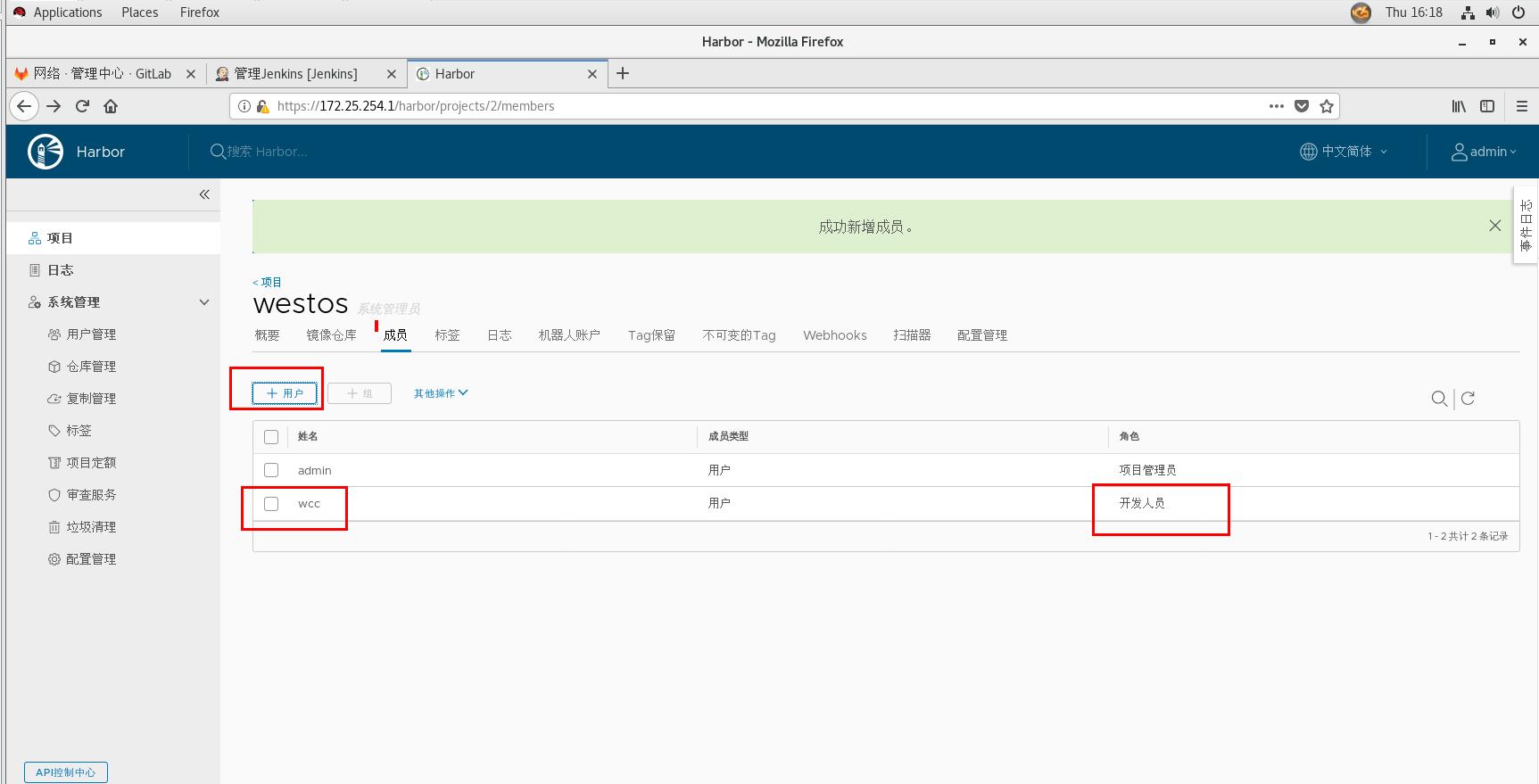
The warehouse is set to be public, and the image can be downloaded directly without login and authentication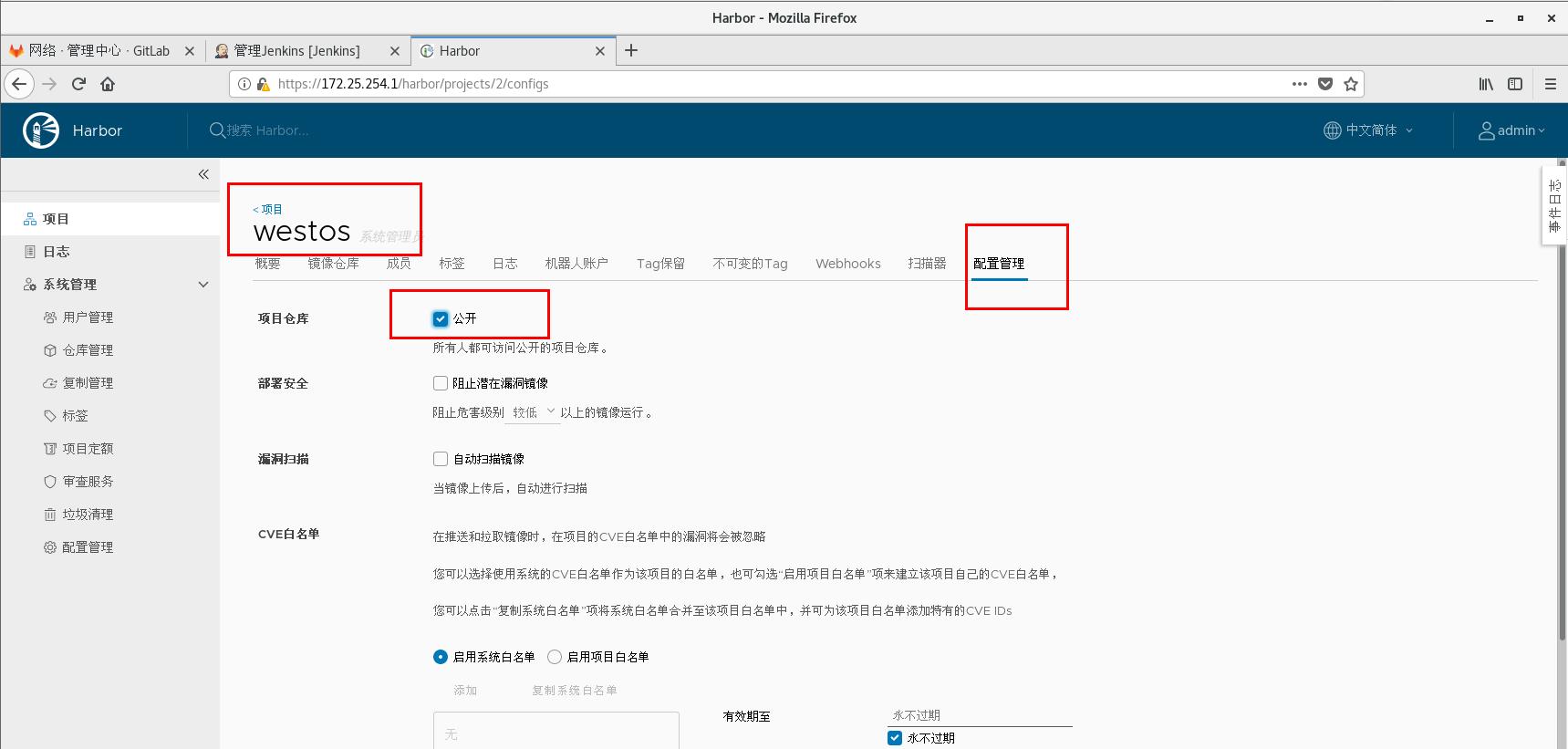
Add some components of dockhub
[root@server1 ~]# cd harbor / must be executed in the directory [root@server1 harbor]# docker-compose stop Stopping harbor-jobservice ... done Stopping nginx ... done Stopping harbor-core ... done Stopping harbor-db ... done Stopping redis ... done Stopping harbor-portal ... done Stopping registryctl ... done Stopping registry ... done Stopping harbor-log ... done [root@server1 harbor]# / install.sh --help view help Note: Please set hostname and other necessary attributes in harbor.yml first. DO NOT use localhost or 127.0.0.1 for hostname, because Harbor needs to be accessed by external clients. Please set --with-notary(Mirror trust) if needs enable Notary in Harbor, and set ui_url_protocol/ssl_cert/ssl_cert_key in harbor.yml bacause notary must run under https. Please set --with-clair(Image security scan) if needs enable Clair in Harbor Please set --with-chartmuseum(support chake) if needs enable Chartmuseum in Harbor [root@server1 harbor]# ./install.sh --with-notary --with-clair --with-chartmuseum
Sign out and sign in again
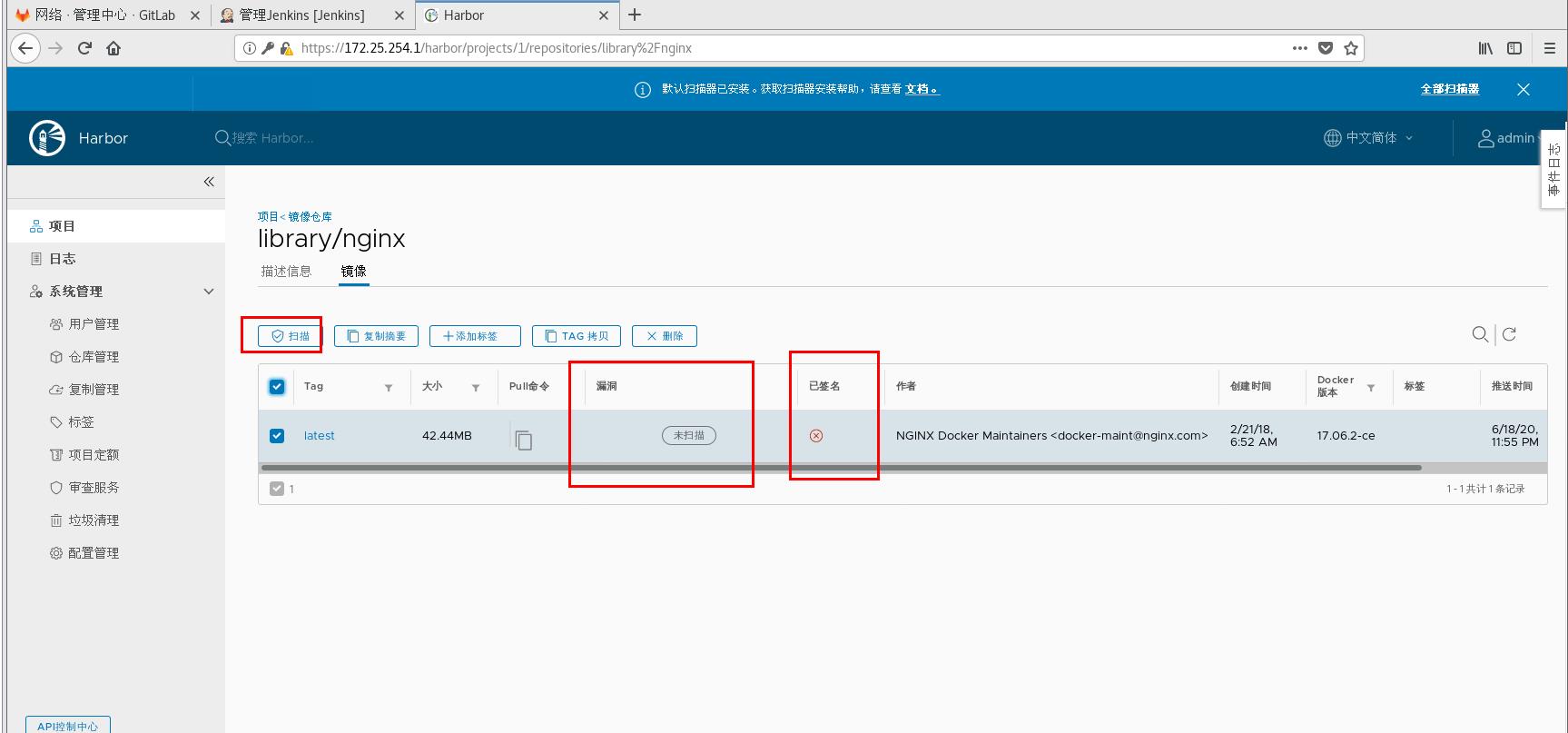
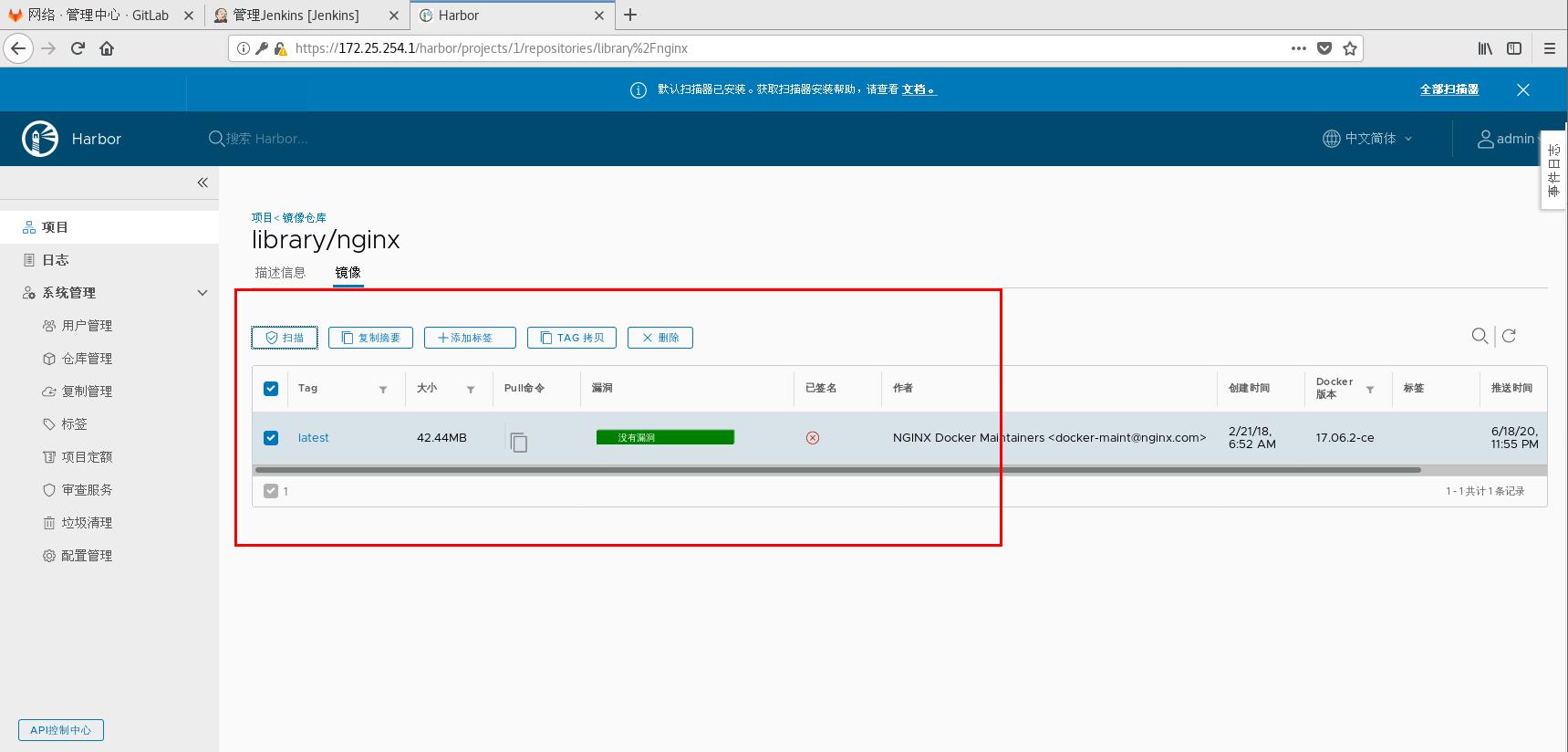
You can also turn on the autoscanner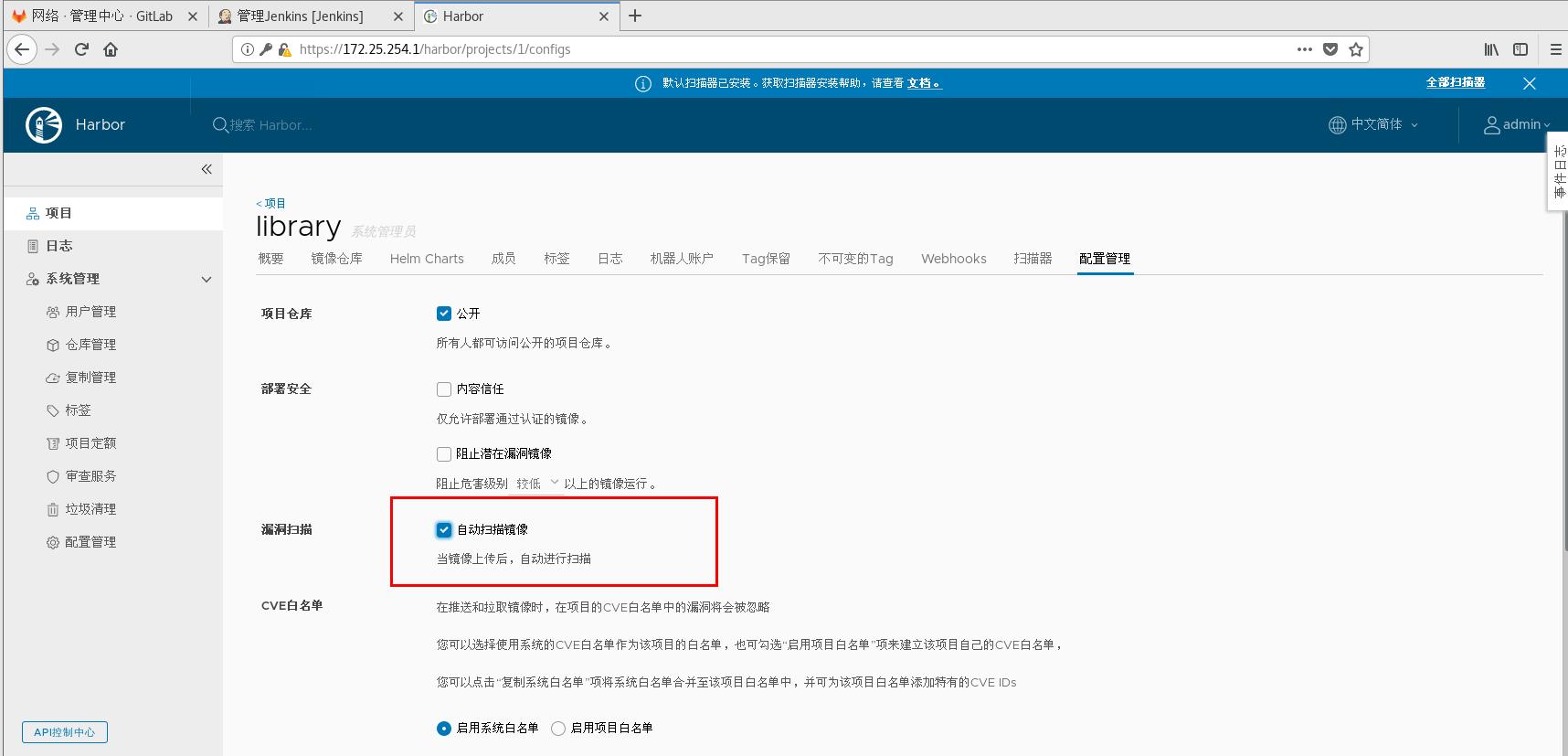
Test Auto Scanner
[root@server1 ~]# docker load -i busybox.tar Image import container 8a788232037e: Loading layer [==================================================>] 1.37MB/1.37MB Loaded image: busybox:latest [root@server1 ~]# mkdir -p /etc/docker/certs.d/reg.westos.org/ Create certification directory [root@server1 ~]# scp /data/certs/westos.org.crt /etc/docker/certs.d/reg.westos.org/ca.crt get recertification file [root@server1 ~]# docker tag busybox:latest reg.westos.org/library/busybox Label [root@server1 ~]# docker login reg.westos.org Login authentication Password: WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded [root@server1 ~]# docker push reg.westos.org/library/busybox Upload image The push refers to repository [reg.westos.org/library/busybox] 8a788232037e: Pushed latest: digest: sha256:915f390a8912e16d4beb8689720a17348f3f6d1a7b659697df850ab625ea29d5 size: 527
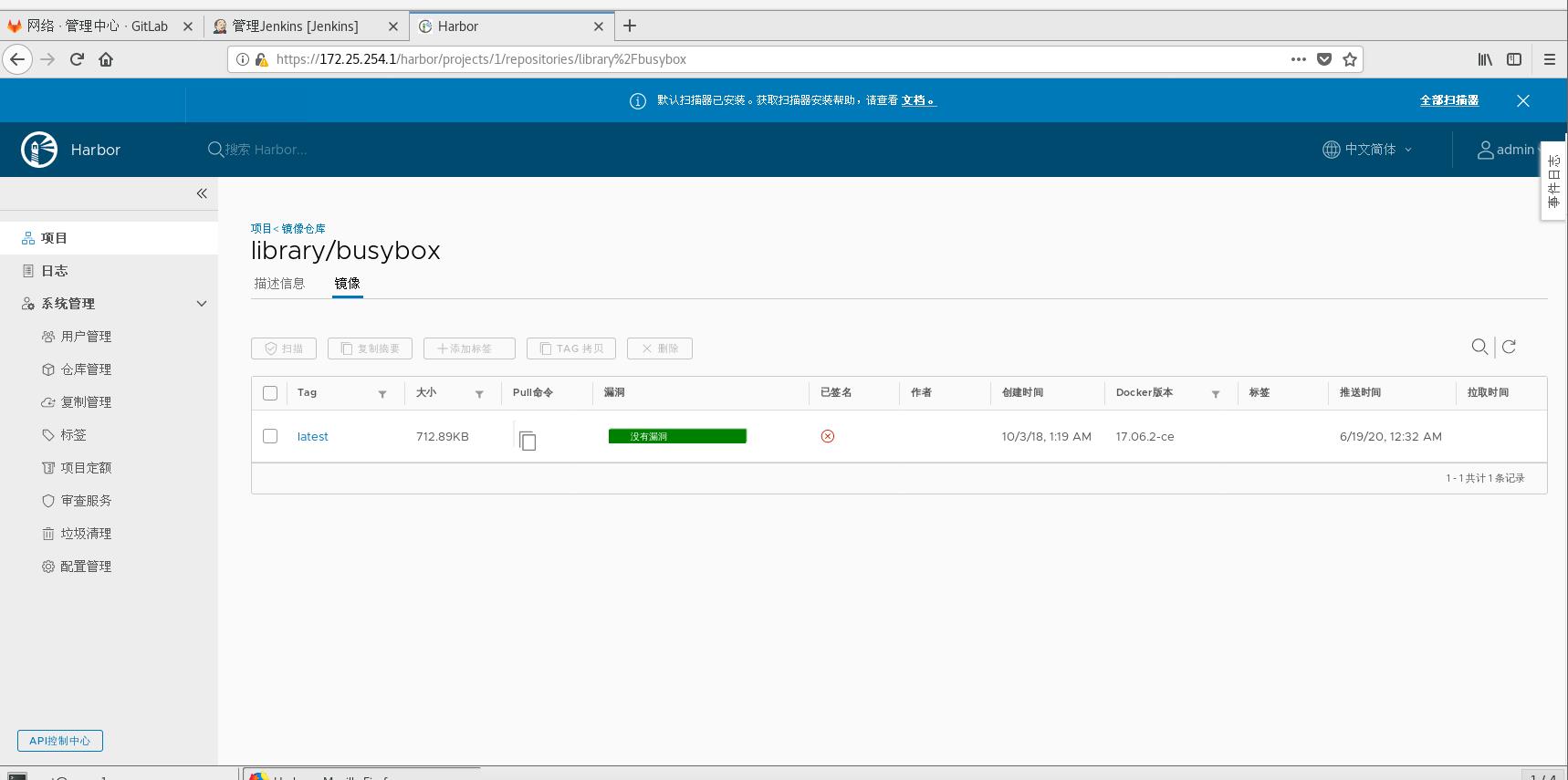
Next, cancel the automatic scanner and start the automatic trust test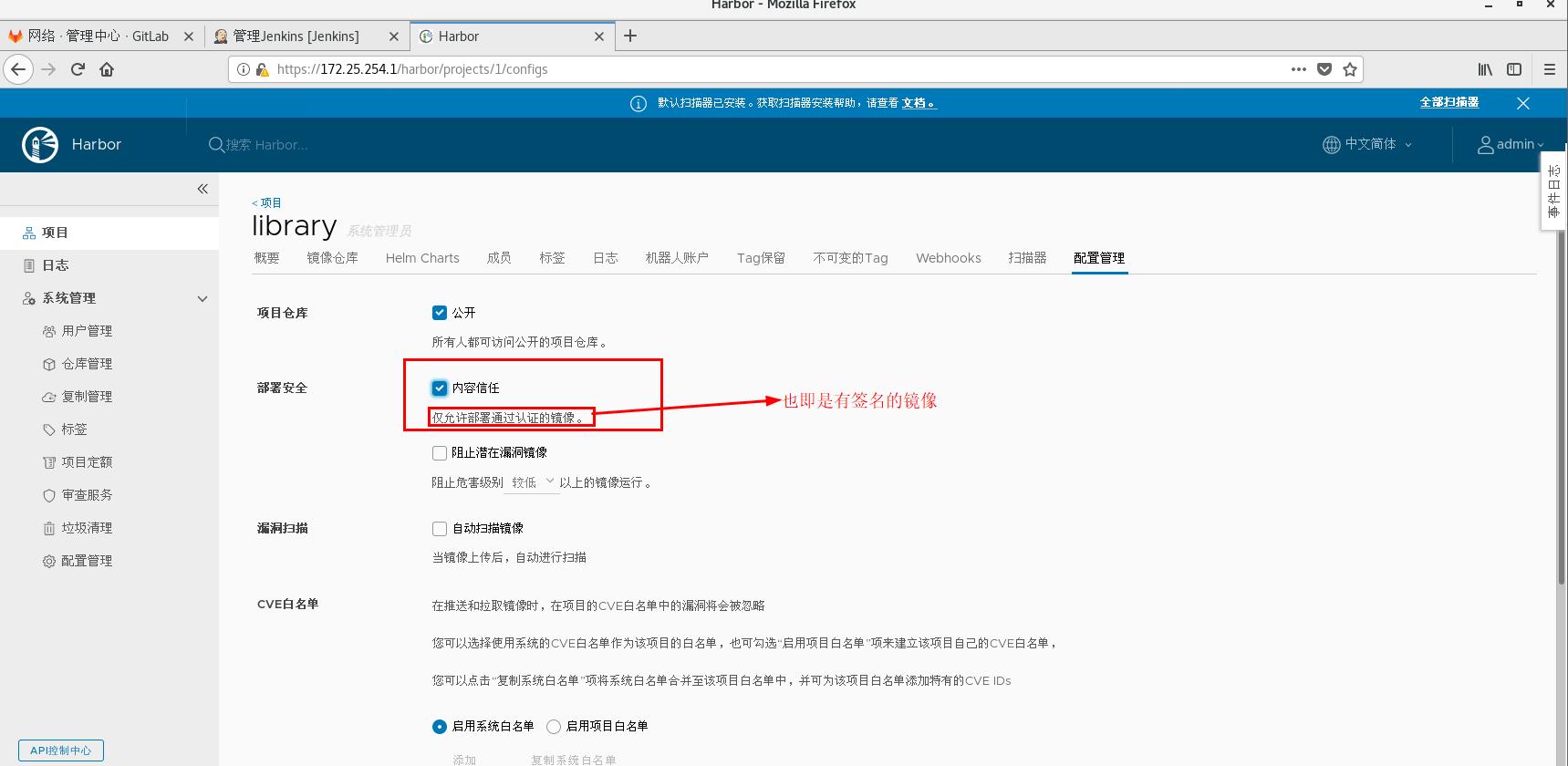
[ root@server1 ~]# docker pull reg.westos.org/library/nginx Login without authentication is public Using default tag: latest Error response from daemon: unknown: The image is not signed in Notary. Image not signed in notarization
• image signature: https://goharbor.io/docs/1.10/working-with-projects/workingwith-images/pulling-pushing-images/
Deploy root certificate
[root@server1 .docker]# mkdir -p tls/reg.westos.org\:4443/ [root@server1 .docker]# cd tls/reg.westos.org\:4443/ [root@server1 reg.westos.org:4443]# ls //This file can be used by docker engine and operating system [root@server1 reg.westos.org:4443]# cp /etc/docker/certs.d/reg.westos.org/ca.crt . [root@server1 reg.westos.org:4443]# ls ca.crt
To enable docker content trust:
[root@server1 reg.westos.org:4443]# export DOCKER_CONTENT_TRUST=1 [root@server1 reg.westos.org:4443]# export DOCKER_CONTENT_TRUST_SERVER=https://reg.westos.org:4443
[root@server1 ~]# docker load -i myapp.tar [root@server1 ~]# docker tag ikubernetes/myapp:v1 reg.westos.org/library/myapp:v1
[root@server1 ~]# docker load -i myapp.tar [root@server1 ~]# docker tag ikubernetes/myapp:v1 reg.westos.org/westos/myapp:v1 //Set the password for the first time. Second pass direct = authentication upload [root@server1 ~]# docker push reg.westos.org/westos/myapp:v1 The push refers to repository [reg.westos.org/westos/myapp] a0d2c4392b06: Layer already exists 05a9e65e2d53: Layer already exists 68695a6cfd7d: Layer already exists c1dc81a64903: Layer already exists 8460a579ab63: Layer already exists d39d92664027: Layer already exists v1: digest: sha256:9eeca44ba2d410e54fccc54cbe9c021802aa8b9836a0bcf3d3229354e4c8870e size: 1569 Signing and pushing trust metadata Enter passphrase for repository key with ID 5433f54: Westos123 Passphrase incorrect. Please retry. Enter passphrase for repository key with ID 5433f54: QQ123456 Successfully signed reg.westos.org/westos/myapp:v1
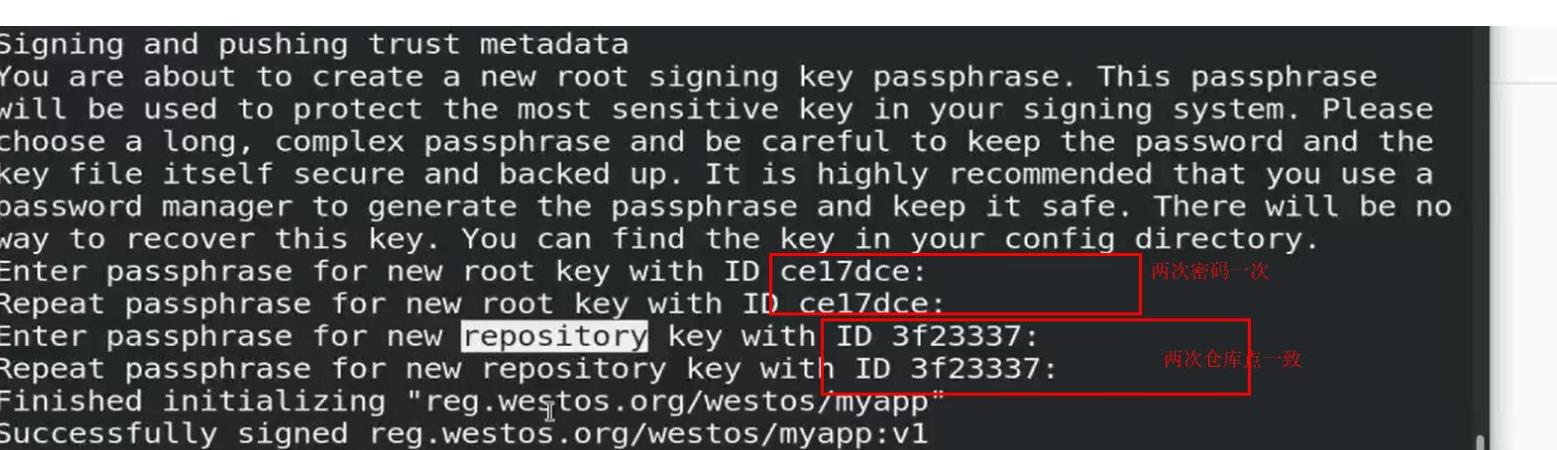
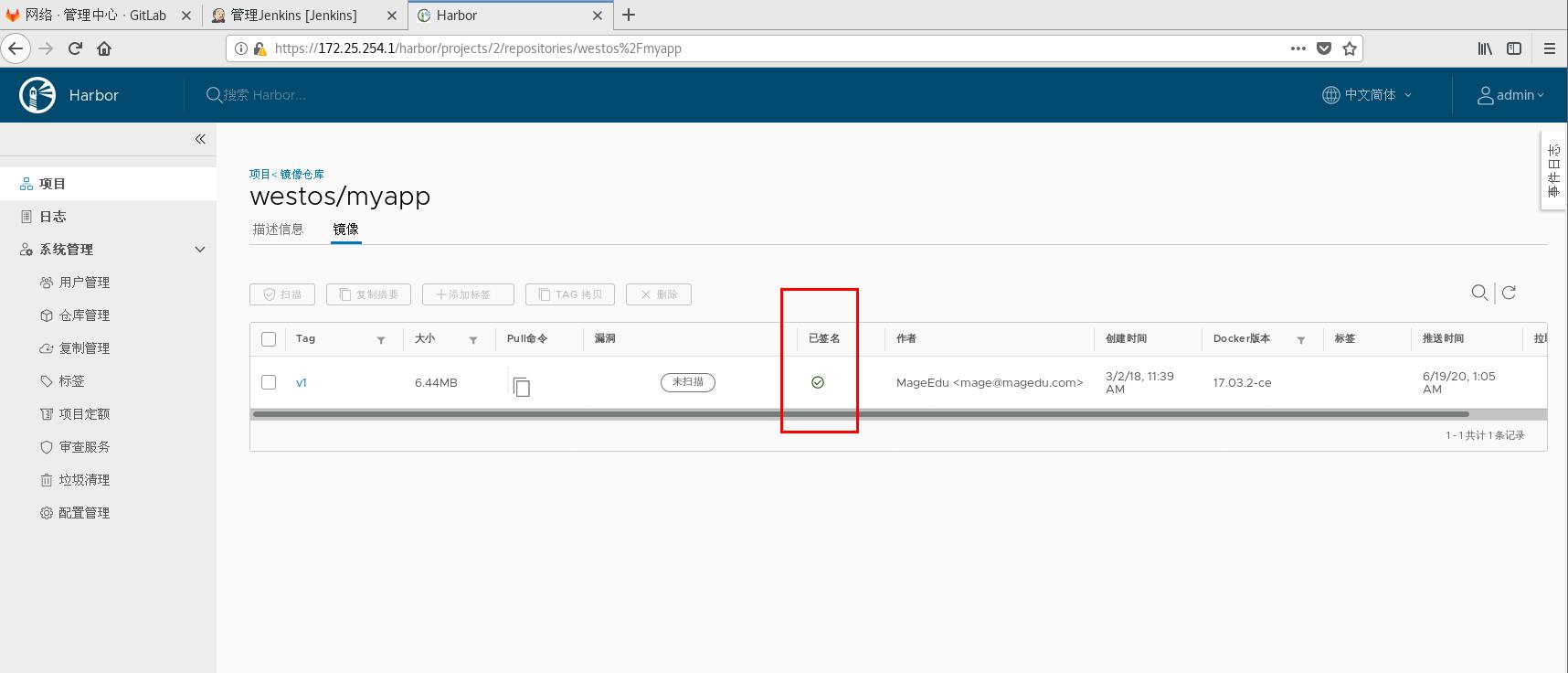
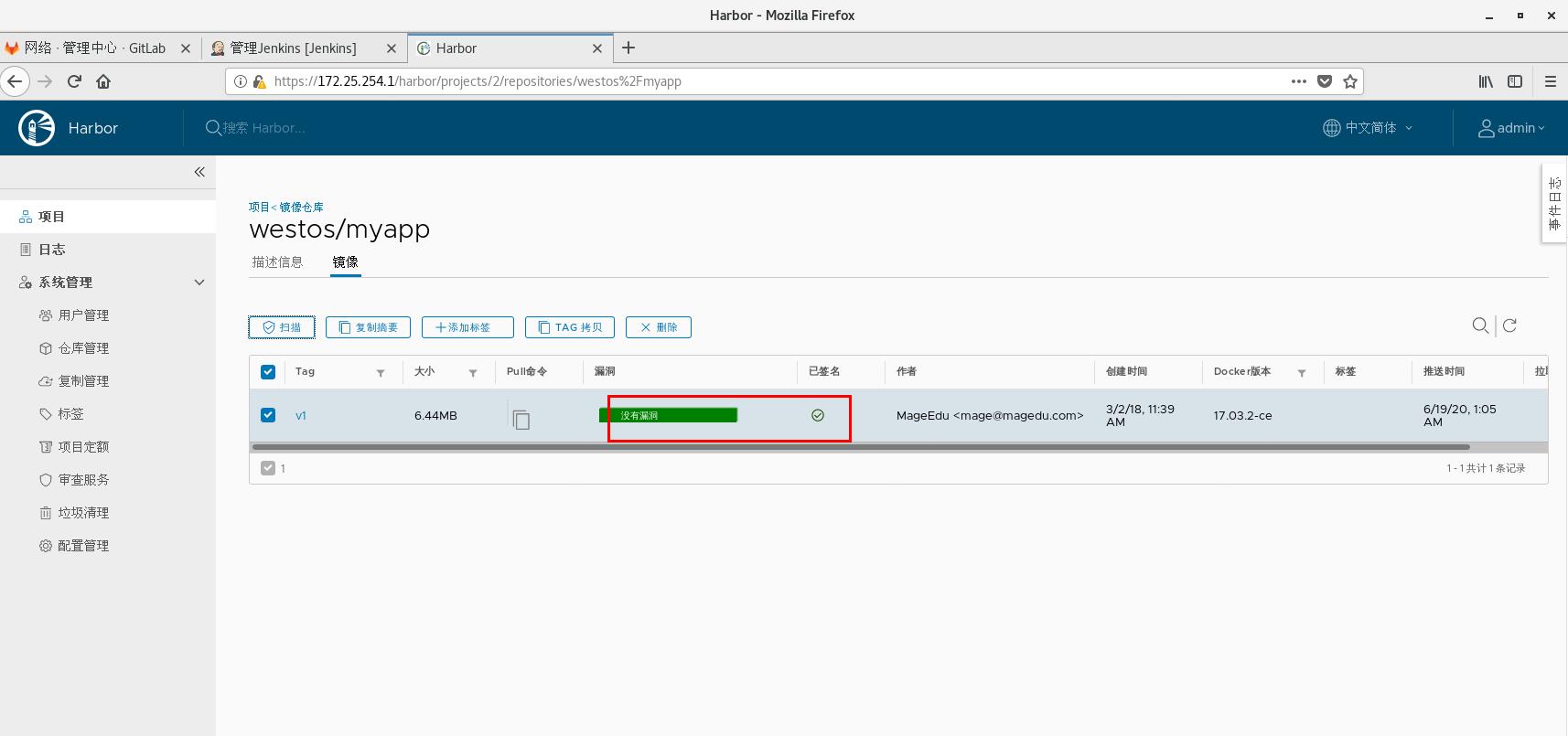
Retest: upload successfully as long as you input correct password free
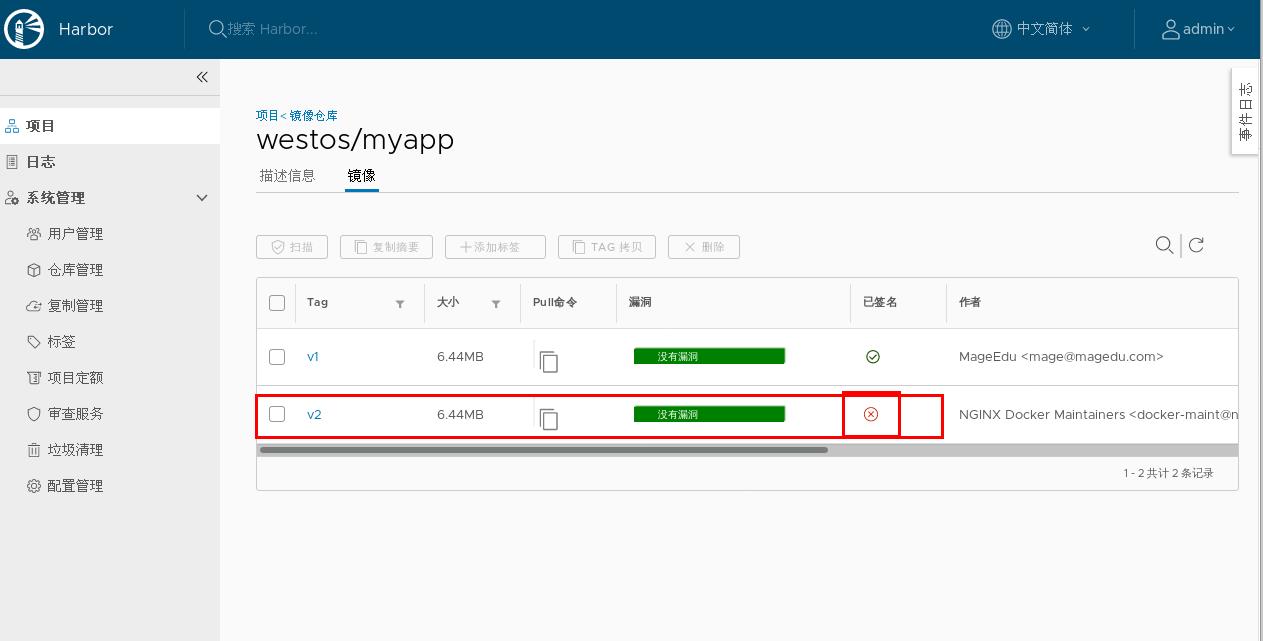
[root@server1 ~]# docker tag ikubernetes/myapp:v2 reg.westos.org/westos/myapp:v2 [root@server1 ~]# docker push reg.westos.org/westos/myapp:v2 The push refers to repository [reg.westos.org/westos/myapp] 05a9e65e2d53: Layer already exists 68695a6cfd7d: Layer already exists c1dc81a64903: Layer already exists 8460a579ab63: Layer already exists d39d92664027: Layer already exists v2: digest: sha256:5f4afc8302ade316fc47c99ee1d41f8ba94dbe7e3e7747dd87215a15429b9102 size: 1362 Signing and pushing trust metadata Enter passphrase for repository key with ID 5433f54: Passphrase incorrect. Please retry. Enter passphrase for repository key with ID 5433f54: Successfully signed reg.westos.org/westos/myapp:v2
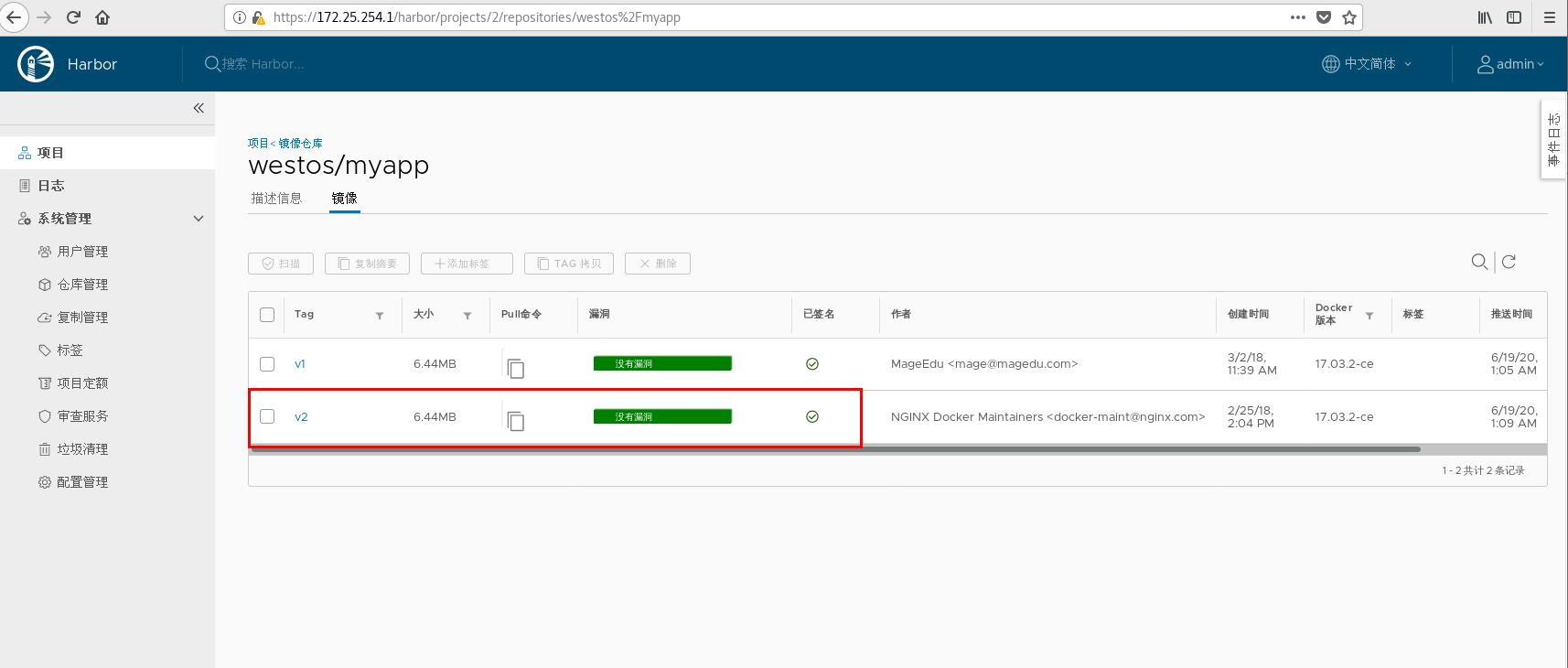
Remote pull image test
[root@server5 ~]# docker pull reg.westos.org/westos/myapp : V2 pull v2: Pulling from westos/myapp Digest: sha256:5f4afc8302ade316fc47c99ee1d41f8ba94dbe7e3e7747dd87215a15429b9102 Status: Downloaded newer image for reg.westos.org/westos/myapp:v2 reg.westos.org/westos/myapp:v2
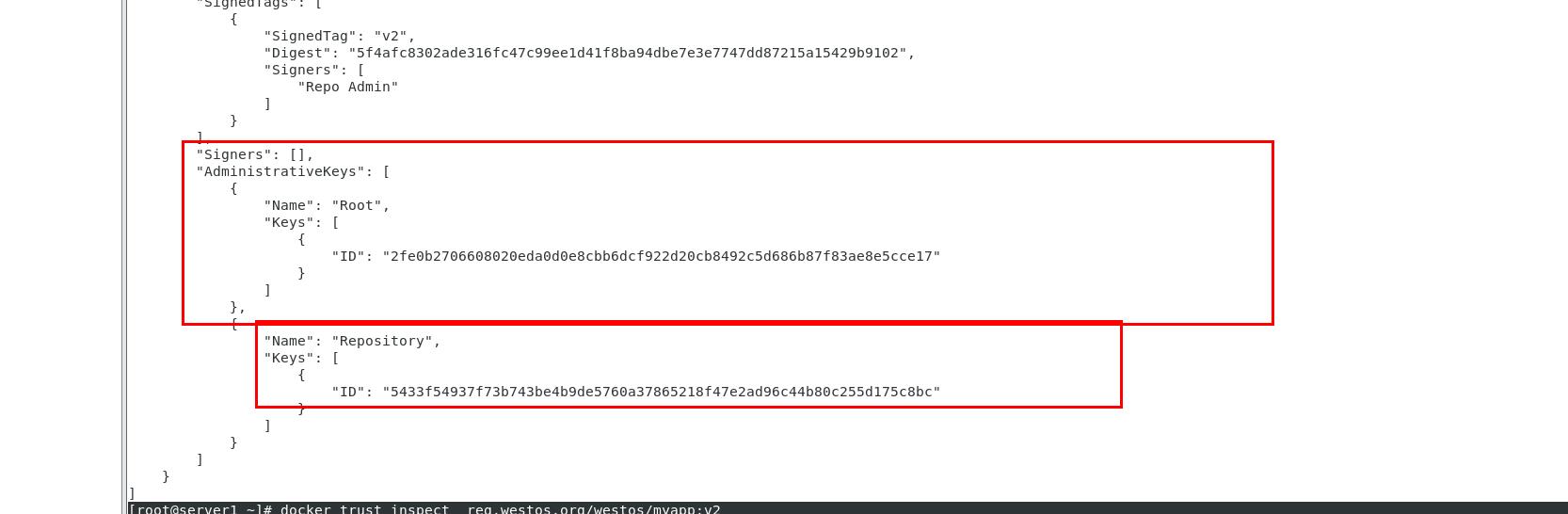
[root@server1 ~]# docker trust inspect reg.westos.org/westos/myapp : V2 viewing signature information [root@server1 ~]# docker trust revoke reg.westos.org/westos/myapp : V2 deleting signature information Enter passphrase for repository key with ID 5433f54: Successfully deleted signature for reg.westos.org/westos/myapp:v2