Preface
gitlab 11.1 has built-in CI/CD, which has been available since gitlab 8+, but the configuration is trivial.
After several large versions of iterations, it has now simplified the way to use, and also repaired some pits, which attracted me greatly.
Sorry for not using the good stuff, we started a long way to climb the pit.
Things are deployed in the company, so access is not open, but you can refer to my general configuration;
As for why docker is used for deployment, easy migration and easy upgrade (because data and configuration files are independent)
Prefix Foundation
Basic environment
- Debian Linux 9
-
Docker 18.06, Official gitlab for gitlab Mirror gitlab-ce The benefits are as follows
- Officially, with assurance, the frequency of updates is high (keeping pace with the times) - This tutorial uses the latest 11.1
- One-click installation (because basic environments like postgresql,ruby,nginx) are included
- Expose only the main configuration file/database location/logs.
- Upgrading does not take data into account; for companies with less complex business, they can deploy quickly........................................... .
If you want to build from 0 to 1 (which can be more detailed for business configuration), but there are many things to consider;
Big guys with professional peacekeeping companies who don't lack money can toss around.
Essential knowledge
Linux/Docker && Docker Compose / Nginx
Design sketch
Anything that doesn't show a picture is a hooligan, so you say it's a hooligan. If there's a picture, there's the truth, there's no plan, there's no pure bullshit!!!
As you can see, LOGO, introductory language, global broadcasting, the administrator's account will be found after login.
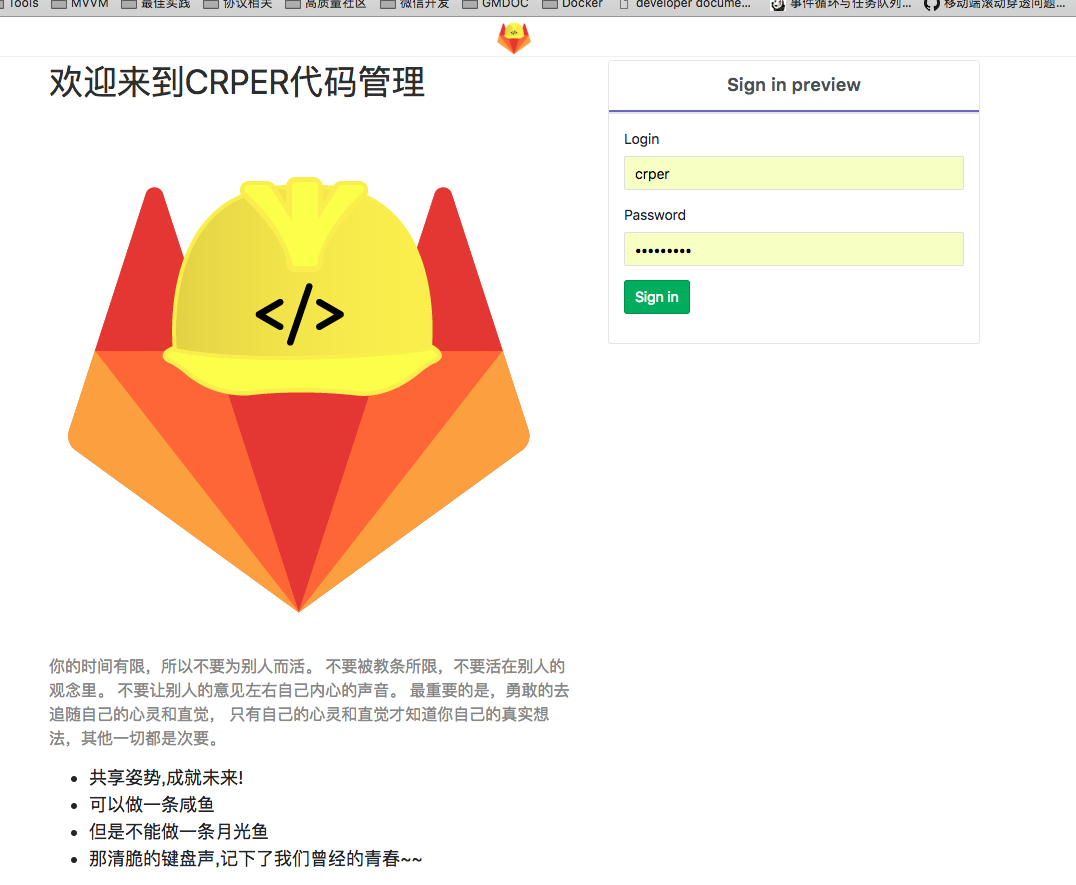
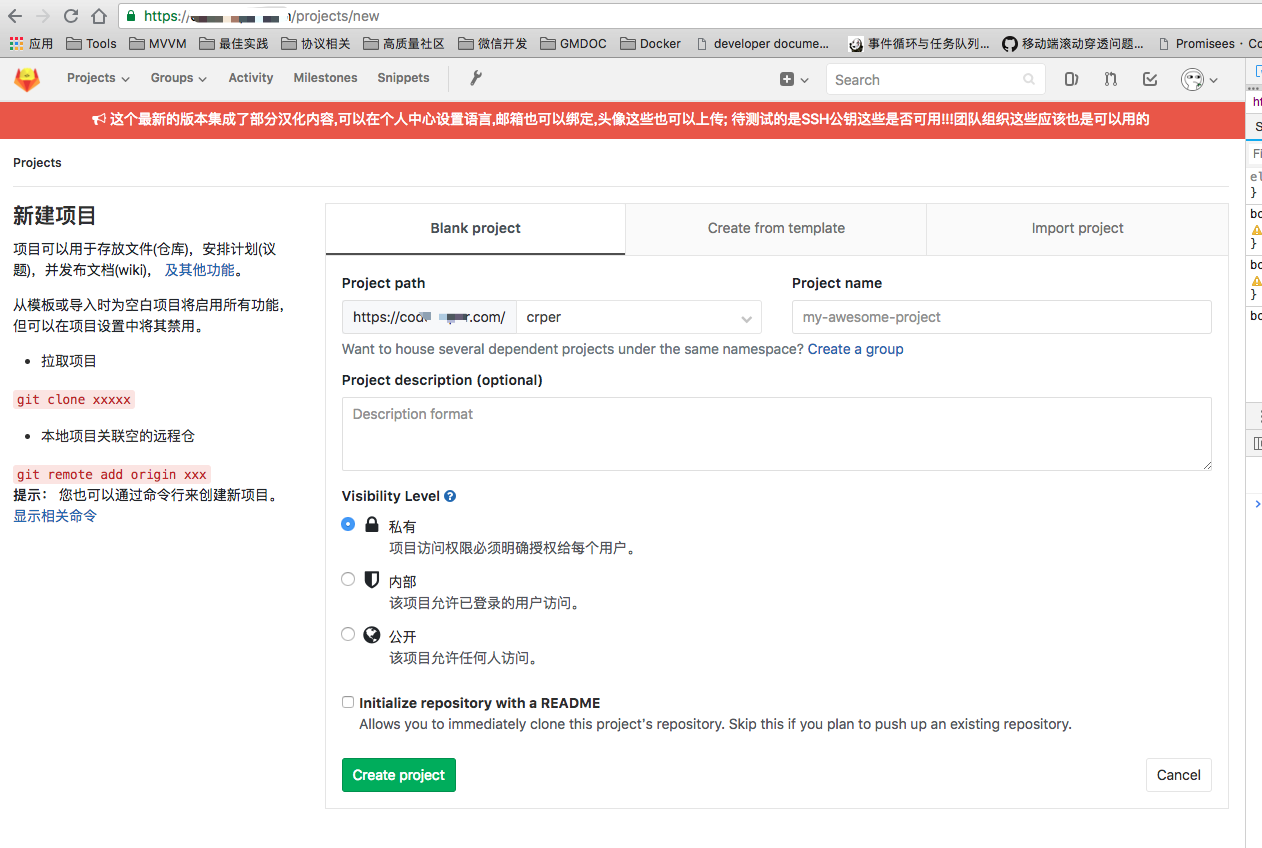
Construction initiation
This piece of knowledge is not gitlab, or docker's
- The basic starting posture of the official course:
- detack: The container runs in the background and outputs the container ID
- Push: Exposure port, abbreviated - p
- Name: Container name
- Restart: When will the container restart trigger, in all cases
- Volume: Mapping volume, basically for persistent data
# Official basic posture, docker starts directly
sudo docker run --detach \
--hostname gitlab.example.com \
--publish 443:443 --publish 80:80 --publish 22:22 \
--name gitlab \
--restart always \
--volume /srv/gitlab/config:/etc/gitlab \
--volume /srv/gitlab/logs:/var/log/gitlab \
--volume /srv/gitlab/data:/var/opt/gitlab \
gitlab/gitlab-ce:latest
Three volume s are the exposed locations.
| Local location | Container location | Effect |
|---|---|---|
| /srv/gitlab/data | /var/opt/gitlab | gitlab data storage, including nginx,postgresql |
| /srv/gitlab/logs | /var/log/gitlab | Log storage |
| /srv/gitlab/config | /etc/gitlab | gitlab master configuration file |
Transmission initiation
- hostname: domain name accessed
-
env: This is where the provisional right of suffrage comes into effect.
- This is to pass in some parameters to gitlab so that the build process reads the values you set (gitlab.rb) and takes effect.
- Officials say this will not be written to gitlab. RB (gitlab configuration file), but will take effect temporarily (container lifetime).
sudo docker run --detach \
--hostname gitlab.example.com \
--env GITLAB_OMNIBUS_CONFIG="external_url 'http://my.domain.com/'; gitlab_rails['lfs_enabled'] = true;" \
--publish 443:443 --publish 80:80 --publish 22:22 \
--name gitlab \
--restart always \
--volume /srv/gitlab/config:/etc/gitlab \
--volume /srv/gitlab/logs:/var/log/gitlab \
--volume /srv/gitlab/data:/var/opt/gitlab \
gitlab/gitlab-ce:latest
docker-compose startup
I prefer this, so I write a build rule as follows
First edition
version: '3.6'
services:
gitlab:
container_name: gitlab
image: gitlab/gitlab-ce:latest
restart: always
environment:
GITLAB_OMNIBUS_CONFIG: |
external_url 'https://Domain name
ports:
- "80:80"
- "443:443"
- "2224:22"
volumes:
- "/srv/gitlab/config:/etc/gitlab"
- "/srv/gitlab/logs:/var/log/gitlab"
- "/srv/gitlab/data:/var/opt/gitlab"
The whole initialization process, I waited here for about two minutes, because the server configuration is not very high ~~
For Gitlab configurations, you can configure either the containers or the mapped areas.
The former can be revalidated with gitlab-ctl reconfigure, while the latter needs to restart the container
- In Container: /etc/gitlab
- Mapping: / srv/gitlab/config
Mailbox configuration
Mailbox push is one of the most basic functions, such as registration, which is generally used.
Here is Ali Yun's mailbox, of course, personal mailbox. Enough is enough.
# https://mailhelp.aliyun.com/freemail/detail.vm?knoId=5869705
gitlab_rails['smtp_enable'] = true
gitlab_rails['smtp_address'] = "smtpdm.aliyun.com"
gitlab_rails['smtp_port'] = 465
gitlab_rails['smtp_user_name'] = "crperx@aliyun.com"
gitlab_rails['smtp_password'] = "xxxxxxxx"
gitlab_rails['smtp_domain'] = "smtp.aliyun.com"
gitlab_rails['smtp_authentication'] = "login"
gitlab_rails['smtp_enable_starttls_auto'] = true
gitlab_rails['smtp_tls'] = true
gitlab_rails['gitlab_email_enabled'] = true
gitlab_rails['gitlab_email_from'] = 'crperx@aliyun.com'
gitlab_rails['gitlab_email_display_name'] = 'noreply@aliyun.com'
# Other mailboxes are much the same (QQ,163, etc.), as long as they support the smtp protocol, port is not necessary.
# Gitlab_rails ['smtp_address']= "smtp.aliyun.com": mailbox interactive server
# Gitlab_rails ['smtp_user_name']= "crperx@aliyun.com": mailbox login account
# Gitlab_rails ['smtp_password']= "xxxxxxxx": mailbox login password
#gitlab_rails['gitlab_email_enabled'] = true: Start the mailbox push function
# Gitlab_rails ['gitlab_email_from']='crperx@aliyun.com': Who will act as an e-mail sender?
# Gitlab_rails ['gitlab_email_display_name']='noreply@aliyun.com': The name of the sender seen by others
Effect
Common mailboxes can be received basically. .
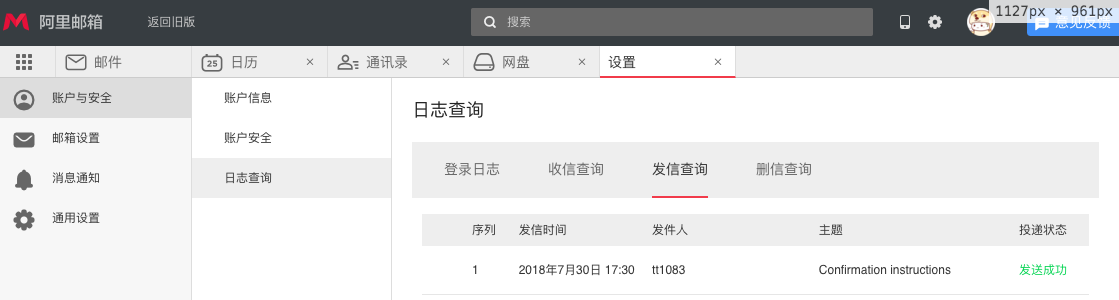
Gitlab HTTPS
My slag server currently doesn't have much service, so I don't consider nginx as a reflection agent (gitlab supports reflection proxy)
With gitlab built-in nginx, use the default port directly
- I applied for a certificate. I applied for Aliyun's free certificate.
The application process is very simple, as long as you have a well-documented domain name, you can basically approve it, this process needn't be said.
After approval, we need to download the certificate.
After downloading and decompressing, there are two files.
- 1533582000680.key: Certificate Private Key!!!! Certificate Private Key!!!! Certificate Private Key!!!!
- 1533582000680.pem: Public key, Aliyun provides PEM format
I went to see that gitlab.rb(gitlab's main configuration file) requires crt format.
###############################################################################
## GitLab NGINX
##! Docs: https://docs.gitlab.com/omnibus/settings/nginx.html
################################################################################
# nginx['enable'] = true
# nginx['client_max_body_size'] = '250m'
# nginx['redirect_http_to_https'] = false
# nginx['redirect_http_to_https_port'] = 80
##Most root CA's are included by default default default root certificate
# nginx['ssl_client_certificate'] = "/etc/gitlab/ssl/ca.crt"
##enable/disable 2-way SSL client authentication two-step verification to verify whether the certificate is proofread, see the requirements open
# nginx['ssl_verify_client'] = "off"
##If ssl_verify_client, verification depth in the depth of the client certificates chain check
# nginx['ssl_verify_depth'] = "1"
# nginx['ssl_certificate'] = "/etc/gitlab/ssl/#{node['fqdn']}.crt "certificate location
# nginx['ssl_certificate_key'] = "/etc/gitlab/ssl/#{node['fqdn']}.key"
# nginx['ssl_ciphers'] = "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256"
# nginx['ssl_prefer_server_ciphers'] = "on"
##! **Recommended by: https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html
##! https://cipherli.st/**
# nginx['ssl_protocols'] = "TLSv1.1 TLSv1.2"
At this point, we need to switch on and open the terminal.
# I renamed the number gitlab
# This order means
# Generate certificates with x509 specification and output bit-readable text format.
# - in is the standard input, which one to accept?
# out standard output, why output file format
openssl x509 -outform PEM -in gitlab.pem -out gitlab.crt
# If a binary stream (DER) is used to roll out the format, this problem will be output.
# SSL: error:0906D06C:PEM routines:PEM_read_bio:no start line:Expect
Next, we use scp to transfer the corresponding certificate to the server and modify the configuration file.
- Transfer certificate
# - r recursive delivery, because the entire directory is being transferred
# Pass in the container mapped directory so that restarting the container takes effect.
scp -r ./ssl root@xxxxx:/srv/gitlab/config
- Modify configuration and highlight screenshots
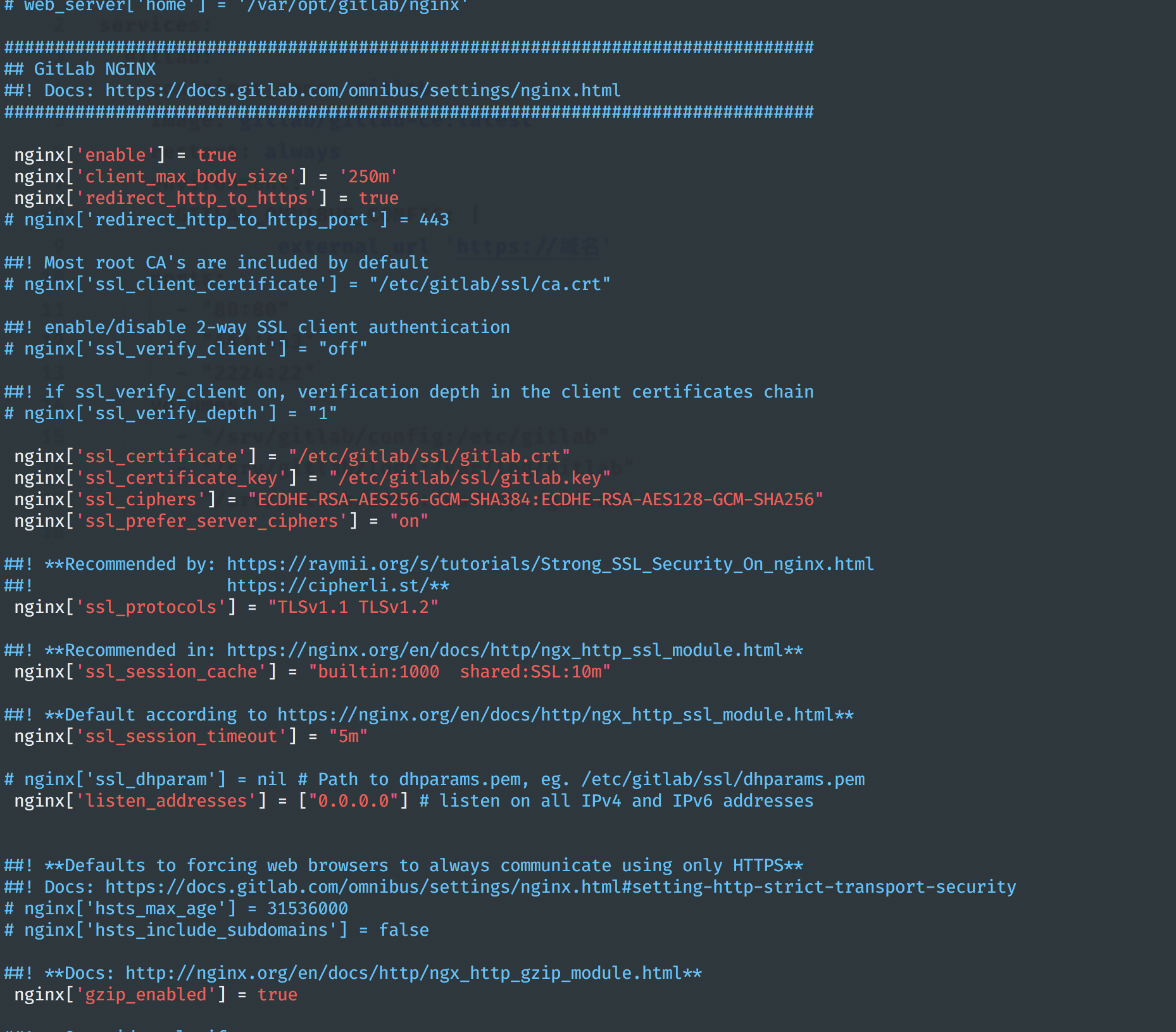
Overtime configuration
Because the server is not strong enough, so the default is not enough.
# This is for the request hook, and this is for Git.
gitlab_rails['webhook_timeout'] = 60 #The default is 10s.
# If you need to extend in general, you can configure the global, which is the number of processes.
unicorn['worker_timeout'] = 60
unicorn['worker_processes'] = 2
Configuration effective
There are two modifications to the gitlab configuration. One is to start the container with reference to the above.
A configuration file for direct mapping; there are two ways to take effect;
First: gitlab-ctl => gitlab-ctl reconfigure overload configuration file takes effect
For one thing, we must enter the container to operate.
- docker ps-a: Find examples of gitlab containers, docker-compose ps and docker ps are much the same.
- Docker exec-it gitlab bash: Enter the container and use the bash shell
It should be said that the command line of docker-compose is basically encapsulated for docker.
It's not surprising that docker can also interfere with instances generated by compse.
gitlab-ctl has other commands, such as pausing, stopping gitlab, output configuration files, etc.
Second: Restart the container!
The second edition
gitlab.rb has many configurations, the whole configuration file is close to 1800 lines at present.
It covers all the configurations of logs, security, nginx, databases, etc.
Most configurations have default values, so there are many things you need to turn on.
We don't need to open too many things here, e-mail and https, timeout configuration, and everything else is default (such as logging, database initialization, etc.).
Certificate must be duplicated in advance!!!!, new directory will be built if there is a directory.
# Write the configuration file in the container build, which takes effect directly when the container starts, eliminating many restarts or command line operations.
# Pay attention to replacing the contents of Chinese area
version: '3.6'
services:
gitlab:
container_name: gitlab
image: gitlab/gitlab-ce:latest
restart: always
environment:
GITLAB_OMNIBUS_CONFIG: |
external_url 'https://Domain name
unicorn['worker_timeout'] = 60
unicorn['worker_processes'] = 2
gitlab_rails['smtp_enable'] = true
gitlab_rails['smtp_address'] = "Mailbox smtp The server"
gitlab_rails['smtp_port'] = 465
gitlab_rails['smtp_user_name'] = "Send mailbox"
gitlab_rails['smtp_password'] = "Password"
gitlab_rails['smtp_domain'] = "mailbox smtp field"
gitlab_rails['smtp_authentication'] = "login"
gitlab_rails['smtp_enable_starttls_auto'] = true
gitlab_rails['smtp_tls'] = true
gitlab_rails['gitlab_email_enabled'] = true
gitlab_rails['gitlab_email_from'] = 'Who Sends Mail'
gitlab_rails['gitlab_email_display_name'] = 'User name displayed by sender'
user['git_user_email'] = "Who Sends Mail"
nginx['enable'] = true
nginx['client_max_body_size'] = '250m'
nginx['redirect_http_to_https'] = true
nginx['ssl_certificate'] = "Certificate location"
nginx['ssl_certificate_key'] = "Certificate location"
nginx['ssl_ciphers'] = "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256"
nginx['ssl_prefer_server_ciphers'] = "on"
nginx['ssl_protocols'] = "TLSv1.1 TLSv1.2"
nginx['ssl_session_cache'] = "builtin:1000 shared:SSL:10m"
nginx['listen_addresses'] = ["0.0.0.0"]
nginx['http2_enabled'] = true
ports:
- "80:80"
- "443:443"
- "2224:22"
volumes:
- "/srv/gitlab/config:/etc/gitlab"
- "/srv/gitlab/logs:/var/log/gitlab"
- "/srv/gitlab/data:/var/opt/gitlab"
Official resources:
- Mainstream STMP Service Configuration
- gitlab nginx configuration
- Global configuration file (gitlab.rb)
Error summary
- [emerg] SSL_CTX_use_PrivateKey_file("/etc/gitlab/ssl/gitla.key") failed (SSL: error:02001002:system library:fopen:No such file or directory
This is a mismatch between the path you mapped or the name of the file.
- 443 failed (97: Address family not supported by protocol)
Official Writing
# gitlab Official Textbook
nginx['listen_addresses'] = ["0.0.0.0", "[::]"] # listen on all IPv4 and IPv6 addresses
# Manual change to
nginx['listen_addresses'] = ["0.0.0.0"]
# [:] On behalf of IPV6, I use the Aliyun server. It is estimated that my security policy is not open, but it is not used. It is not so important to delete it directly.
# Aliyun's security strategy has the highest priority, such as the opening of inbound and outbound ports, which can't be accessed without opening them.
summary
- The latest edition of Gitlab (11) integrates some Chinese (Simplified Chinese with the change of user center)
- Certificate services do not necessarily use Ali's, but can also use some websites that offer free certificates.
- Lets Encrypt
- Free SSL
- Of course, the security of payment is higher than that of free.
Gitlab requires a lot of resources. My single core | 2G storage | 1M bandwidth does not respond from time to time. When several people use it together, they hang up.
Soundly, as for CI/CD, we can only wait for the free money to upgrade the server to reconsider. .
Because the initial consideration is to container some commonly used services and unify nginx proxy services.
For example, yapi,gitlab, test site.. ..
If there is something wrong, please leave a message. It will be amended in time. Thank you for reading.