
1, New user access
[avoid using names such as sshd that conflict with service built-in accounts]
In general, for the sake of system access security, the system administrator account will not be directly used for remote access.
2.1 creating users
With administrator privileges, execute cmd, execute user addition instructions, and create users as standard users, as follows:
# net user username password /add >net user ggcyuser ggcyadmin@@ /add Command completed successfully. >net user ggcyuser user name ggcyuser full name notes User comments country/Area code 000 (System default) Account enable Yes Account expiration never Last set password two thousand and twenty-one/10/5 16:54:17 Password expiration two thousand and twenty-one/11/16 16:54:17 The password can be changed two thousand and twenty-one/10/5 16:54:17 Password required Yes The user can change the password Yes Allowed workstations All Login script User profile home directory Last login two thousand and twenty-one/10/6 2:04:23 Allowed logon hours All Local group members *Users global group membership *None Command completed successfully.
2.2 allow new users ssh access
Edit% programdata% \ ssh \ sshd as Administrator_ Config, add AllowUsers configuration at the end of the file. For relevant information, please see the official document: https://github.com/PowerShell/Win32-OpenSSH/wiki/sshd_config and Microsoft official documents: https://docs.microsoft.com/zh-cn/windows-server/administration/openssh/openssh_server_configuration: the following configuration enables the ordinary user ggcyuser to access ssh remotely:
# Example of overriding settings on a per-user basis #Match User anoncvs # AllowTcpForwarding no # PermitTTY no # ForceCommand cvs server AllowUsers ggcyuser
After adding, restart the sshd service.
2.3 remote test connection
When the port is the default 22, the port parameter configuration can be ignored. The operations are as follows:
> ssh -p [port] [username]@[ip] Connecting to [ip]:[port]... Connection established. To escape to local shell, press 'Ctrl+Alt+]'. Microsoft Windows [Version 10.0.19043.1165] (c) Microsoft Corporation. All rights reserved. [username]@[Host name] C:\Users\[username]>
Sometimes when remote access encounters problems, you can check the information by viewing the connection output log. The output results are as follows:
> ssh -p [port] [username]@[ip] -v OpenSSH_for_Windows_7.7p1, LibreSSL 2.6.5
2.4 access with ssh key
Execute the SSH keygen command to generate the public key and private key according to the actual needs. The encryption algorithm is rsa and there is an encryption key. If it is not set here, it will be empty. Although this will be unsafe, it is recommended not to use an empty password in the production environment. After confirming that the path is correct, there is no next step.
Generate public and private keys:
>ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (C:\Users\[username]/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in C:\Users\[username]/.ssh/id_rsa. Your public key has been saved in C:\Users\[username]/.ssh/id_rsa.pub. The key fingerprint is: SHA256:nr3jdbOpRaSZ2FOgqtOF68YMG5WvEuJEVF+jn7cbUqE [username]@[Host name] The key's randomart image is: +---[RSA 3072]----+ | .. o . | | . . o o . | | . o.. . o | | . o+ = B | | . .S.E O . | | o ++ =.o + | | o .oB=.o + + | | . oo= .+ = + | | o..o.o.o | +----[SHA256]-----+
The file directory is as follows, with *. pub as the public key and vice versa as the private key:
>dir
2021/08/20 18:38 <DIR> .
2021/08/20 18:38 <DIR> ..
2021/08/20 18:38 2,610 id_rsa
2021/08/20 18:38 579 id_rsa.pub
2 File(s) 3,189 bytes
2 Dir(s) 29,674,840,064 bytes free
2.4.1 standard users and management users
For standard users and management users, the corresponding public keys are stored in different locations on the server where sshd is located.
If the account is a standard user, create a non suffix file authorized in the directory C:\Users\[username]/.ssh /_ Keys, used to store the generated public key content;
If the account is an administrative user, create a non suffix file administrators in the directory C:\Users\[username]/.ssh /_ authorized_ In keys,
Taking the standard user as an example, the private key is reserved locally for logging in and accessing the sshd service remotely.
2.4.2 restart sshd service
xshell is used for testing. The selection method is Public Key. The user name is consistent with the account name ggcyuser generated in the remote. The local corresponding private key is introduced. The configuration is as follows:
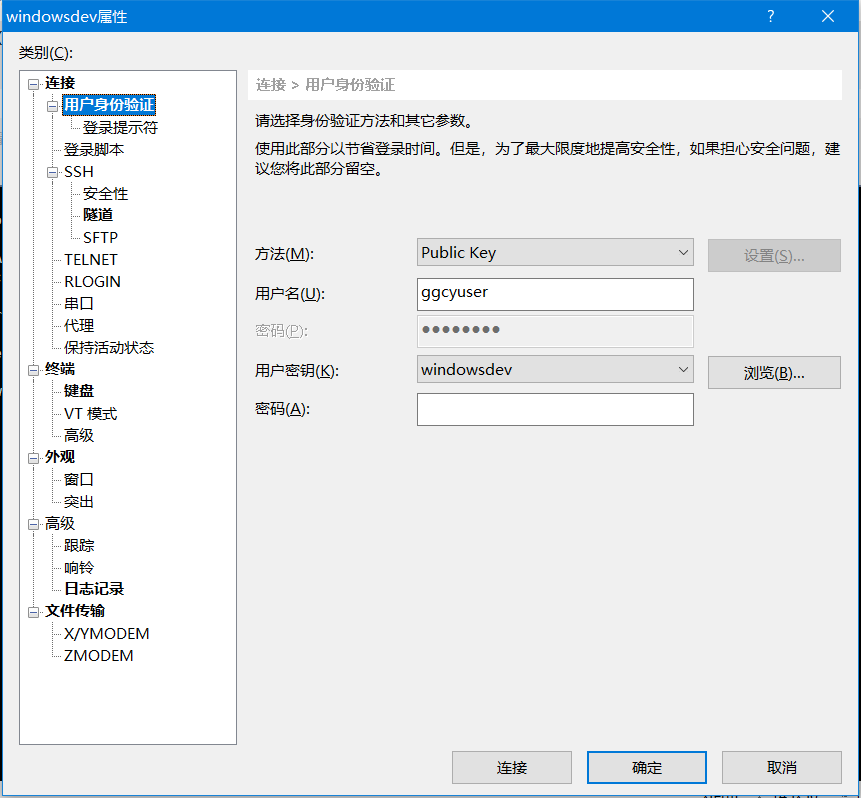
Test connection login

2.4.3 disable user name and password login
Modify sshd_config, start certificate authentication, restart the service and test again
#LoginGraceTime 2m #PermitRootLogin prohibit-password #StrictModes yes #MaxAuthTries 6 #MaxSessions 10 # Enable certificate authentication PubkeyAuthentication yes # Disable password remote login PasswordAuthentication no # The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2 # but this is overridden so installations will only check .ssh/authorized_keys AuthorizedKeysFile .ssh/authorized_keys
Switch to user name and password login, and prompt user name and password login, indicating that login has been disabled,
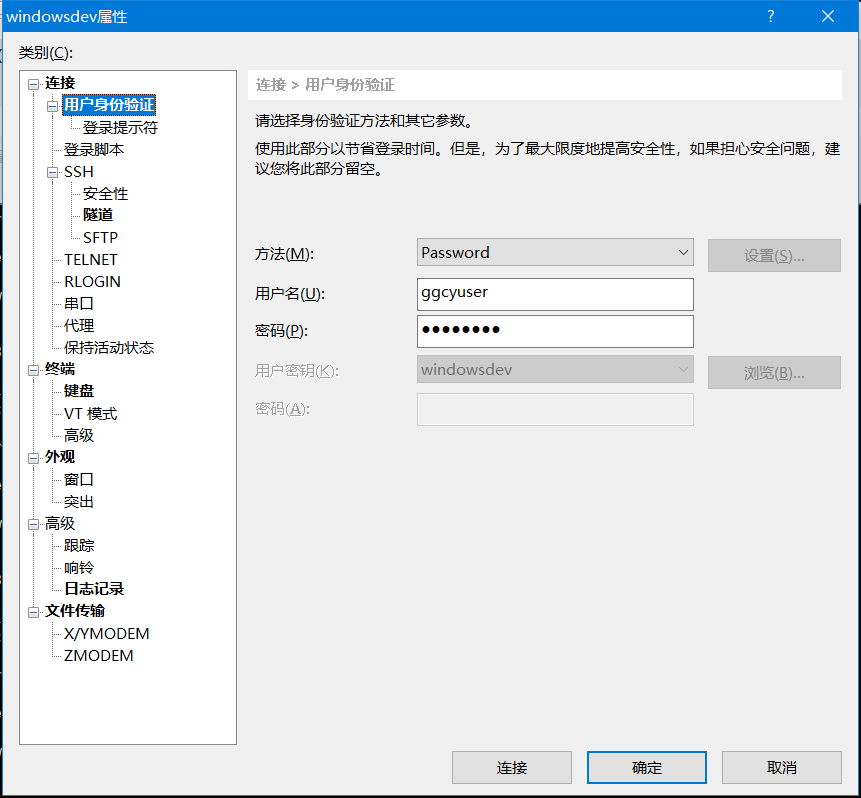
Prompt SSH user authentication, and the feedback is as follows:
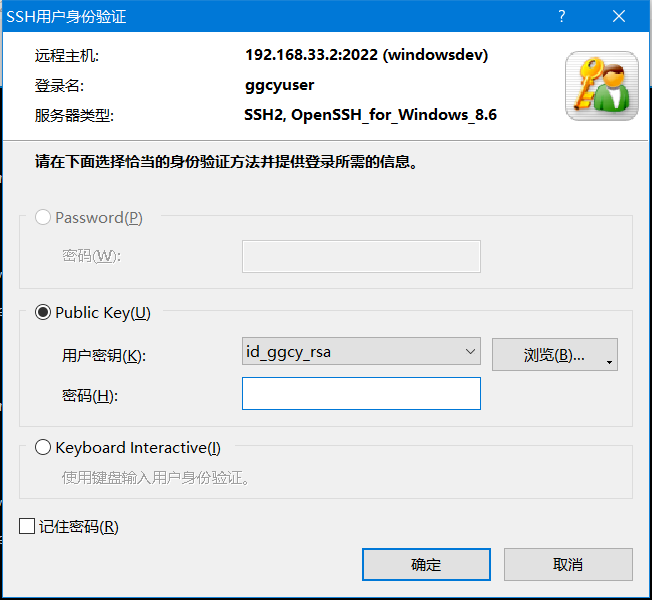
2.4.4 precautions
For remote access, open the default access port 22 of the sshd corresponding to the firewall, and try whether the configuration is effective. It is best to test step by step,
2, Log view
By default, the OpenSSH log is output to the system log, which can be viewed in the event viewer - Application and service logs.
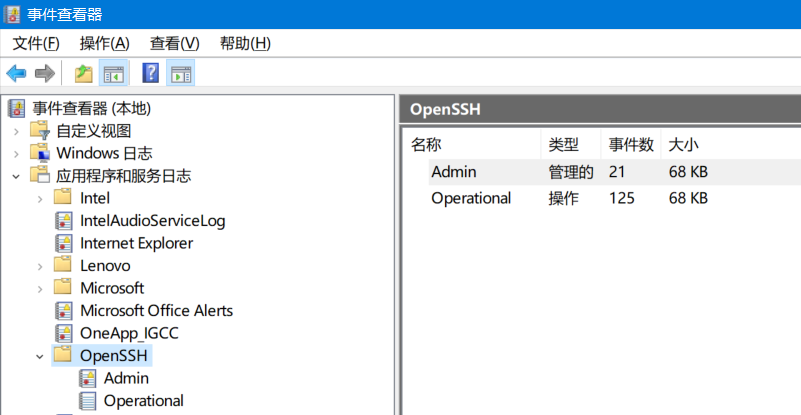
If file based logging is required, set sshd_ SyslogFacility LOCAL0 in the config file, and the log file will be input into the% programdata%\ssh\logs file directory.
3, Frequently asked questions
After ssh key login is configured, remote login cannot be performed
Use xshell to prompt that the current key is registered in the server. The actual reason is that the author keeps trying and checking the log. It can be found that the problem lies in the retention of the file authorized on the public key server_ For the access permissions corresponding to keys, the troubleshooting method is to enable the local log output of sshd instead of using the default log system output. Modify sshd_ SyslogFacility LOCAL0 is configured in the config file. At the same time, in order to further refine the output content, adjust the log output level LogLevel to Debug3, and the log output file is in the% programdata%\ssh\logs directory.
The abnormal output is as follows:
18900 2021-10-06 01:55:28.475 debug3: mm_answer_keyallowed: key_from_blob: 0000026DC6958130 18900 2021-10-06 01:55:28.475 debug1: trying public key file C:\\Users\\ggcyuser\\.ssh/authorized_keys 18900 2021-10-06 01:55:28.476 debug3: Bad permissions. Try removing permissions for user: S-1-5-21-1185597859-3763637221-3021501666-1006 on file C:/Users/ggcyuser/.ssh/authorized_keys. 18900 2021-10-06 01:55:28.476 Authentication refused. 18900 2021-10-06 01:55:28.476 debug3: mm_answer_keyallowed: publickey authentication test: RSA key is not allowed 18900 2021-10-06 01:55:28.476 Failed publickey for ggcyuser from 127.0.0.1 port 49820 ssh2: RSA SHA256:eEUla5p9V1RSHNCTP0dItkf6XRfnnsJObR3saOdkDv0 18900 2021-10-06 01:55:28.476 debug3: mm_request_send entering: type 23
The core problem lies in Bad permissions. Try removing permissions for user. After thinking about it, consider whether it is a file access permission problem, so delete the redundant user permissions sshd, and then use xshell to access again. The above problems will not be prompted, and the remote access can be successful.
The normal output is as follows:
2300 2021-10-06 01:43:28.775 debug3: mm_answer_keyallowed: key_from_blob: 0000016A572D2450 2300 2021-10-06 01:43:28.775 debug1: trying public key file C:\\Users\\ggcyuser\\.ssh/authorized_keys 2300 2021-10-06 01:43:28.775 debug1: C:\\Users\\ggcyuser\\.ssh/authorized_keys:1: matching key found: RSA SHA256:eEUla5p9V1RSHNCTP0dItkf6XRfnnsJObR3saOdkDv0 2300 2021-10-06 01:43:28.775 debug1: C:\\Users\\ggcyuser\\.ssh/authorized_keys:1: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding 2300 2021-10-06 01:43:28.775 Accepted key RSA SHA256:eEUla5p9V1RSHNCTP0dItkf6XRfnnsJObR3saOdkDv0 found at C:\\Users\\ggcyuser\\.ssh/authorized_keys:1 2300 2021-10-06 01:43:28.775 debug3: mm_answer_keyallowed: publickey authentication test: RSA key is allowed
The above problems lead the author to think that the problem of permissions in Windows is often not as obvious as that in Linux. It is necessary to further track the specific operation output of assembly and runtime. It can be seen that a mature log output in a system can bring benefits to users and troubleshooting problems, and can point out the direction for confused people.
4, Reference link
[1] OpenSSH For Windows official documentation:
https://github.com/PowerShell/Win32-OpenSSH/wiki/sshd_config
[2] Microsoft official documents:
https://docs.microsoft.com/zh-cn/windows-server/administration/openssh/openssh_server_configuration