Preface:
Last week, in the essence of 52, I saw a big guy using Python to make a modifier of 5 of devil's tears. After reading it, I knew that the original Python could also operate on memory. After inquisitive about technology, I decided to try it myself.
Tools to use:
CE,Ollybdg,
With Python, read the blood volume of the characters in this game.
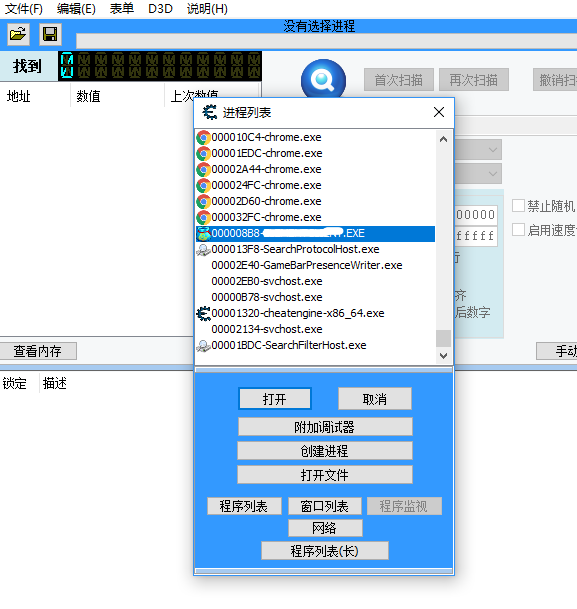
Open the game first, open CE, attach to the game.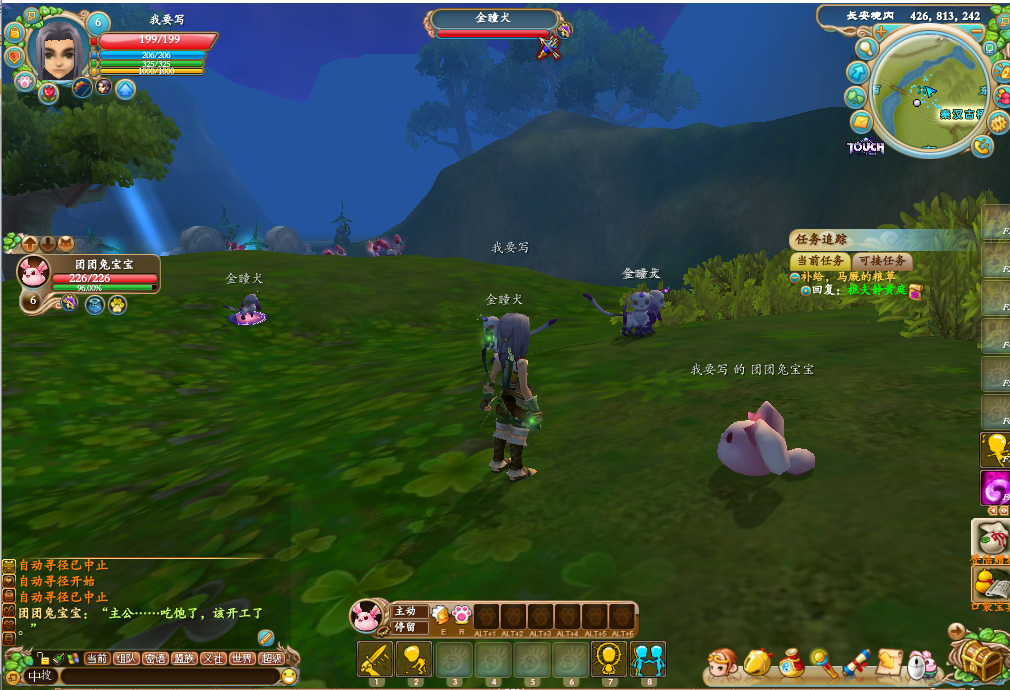
Input 199 in the input box, scan first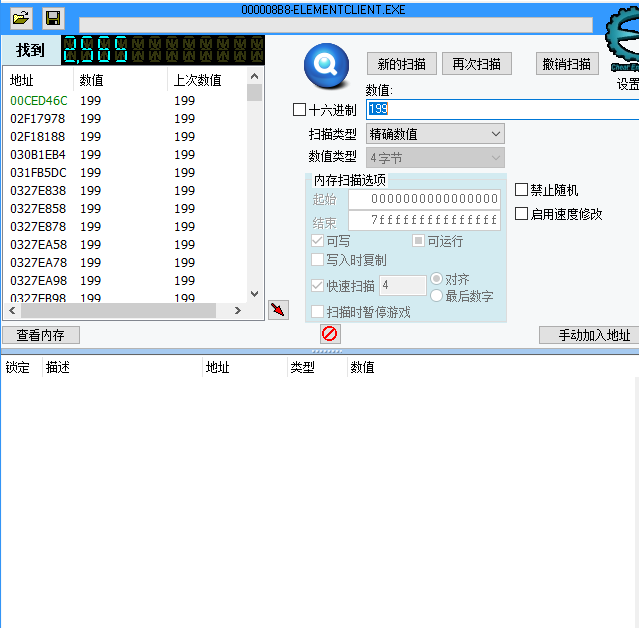
Then I'm going to fight monsters. I'm going to have a scan after I've got my blood cut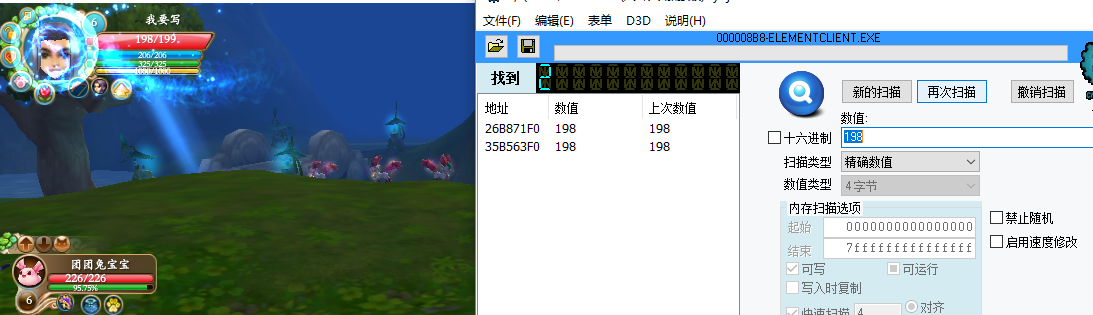
Wait a moment, the character will automatically return blood, and then you will find that one of the two data will become 199, and where the last value is 198, that is the data we are looking for
26B871F0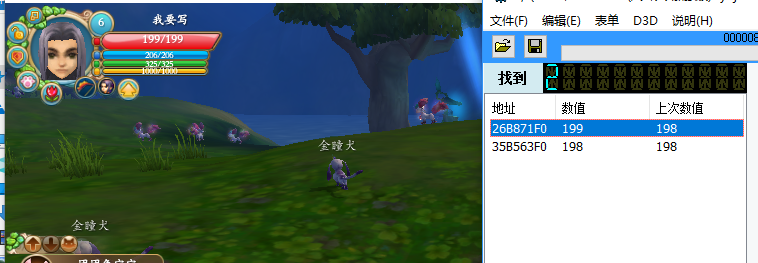
Open OD, put the address in it, search for the breakpoint, and then use bharara's magic power to find the offset
[[[[D0DF1C]+1C]+28]+288]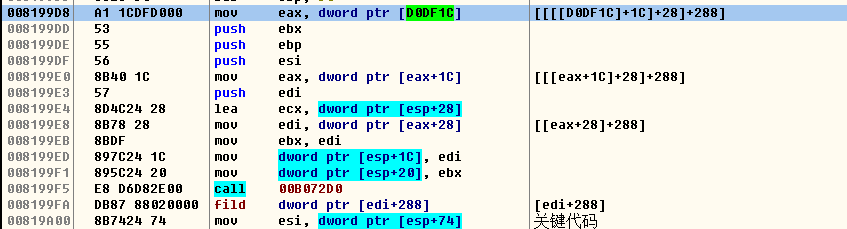
.................................................................................................................................................................................
Now let's get into Python
For 32-bit reading and writing, first of all, we need to understand several functions to be used. Most of the functions found through Baidu are C/C + + data.
FindWindowA is FindWindow in Python
FindWindow this function retrieves the string specified to match the class name and window name of the processing top-level window. This function does not search for child windows.
HWND FindWindowA( LPCSTR lpClassName,//Window class name LPCSTR lpWindowName//Window name, such as calculator );
GetWindowThreadProcessId
After getting the window handle, we can get the process ID and thread ID of the window through the GetWindowThreadProcessId function, so as to judge the process and thread of creating the window.
DWORD GetWindowThreadProcessId( HWND hWnd, //Incoming window handle LPDWORD lpdwProcessId //The process ID address returned. );
OpenProcess
The OpenProcess function is used to open an existing process object and return a handle to the process.
HANDLE OpenProcess( DWORD dwDesiredAccess, //Access to the process you want to have BOOL bInheritHandle,//Indicates whether the resulting process handle can be inherited DWORD dwProcessId//PID of the opened process );
ReadProcessMemory
Is a memory operation function, which reads in a memory space of the process according to the process handle. The function prototype is BOOL. When the function reads successfully, it returns 1, and if it fails, it returns 0
BOOL ReadProcessMemory( HANDLE hProcess, //process handle LPCVOID lpBaseAddress,//Address of read data LPVOID lpBuffer,//Address where read data is stored SIZE_T nSize,//Read data size SIZE_T *lpNumberOfBytesRead//Actual size of data );
Import module first
# -*- coding: utf-8 -*-
import win32process#Process module
from win32con import PROCESS_ALL_ACCESS #Opencress permission
import win32api#Call system module
import ctypes#C language type
from win32gui import FindWindow#Interface
//A read operation of the game to read the blood volume.
def GetProcssID(address,bufflength):
pid = ctypes.c_ulong() // Set pid to unsigned single precision type
kernel32 = ctypes.windll.LoadLibrary("kernel32.dll")//Load dynamic link library
hwnd = FindWindow("XYElementClient Window", u"Pocket tour westward")//Get window handle
hpid, pid = win32process.GetWindowThreadProcessId(hwnd)//Get window ID
hProcess = win32api.OpenProcess(PROCESS_ALL_ACCESS, False, pid)//Get process handle
ReadProcessMemory = kernel32.ReadProcessMemory
addr = ctypes.c_ulong()
ReadProcessMemory(int(hProcess), address, ctypes.byref(addr), bufflength, None)//Read memory
win32api.CloseHandle(hProcess)//Closing handle
return addr.value
def main():
addr = ctypes.c_long()
ret = addr + 0x1C
ret2 = GetProcssID(ret, 4)
ret3 = ret2 + 0x28
ret4 = GetProcssID(ret3, 4)
ret5 = ret4 + 0x288
ret6 = GetProcssID(ret5, 4) // Incoming offset address
print ("Hp:%d" % ret6)
if __name__ == '__main__':
main()
ReadProcessMemory(int(hProcess), address, ctypes.byref(addr), bufflength, None)
Parameter resolution: 1. Pass in process handle 2. Address, which is the address of blood volume. 3. The third one is to pass in pointer. 4. length
Operation result: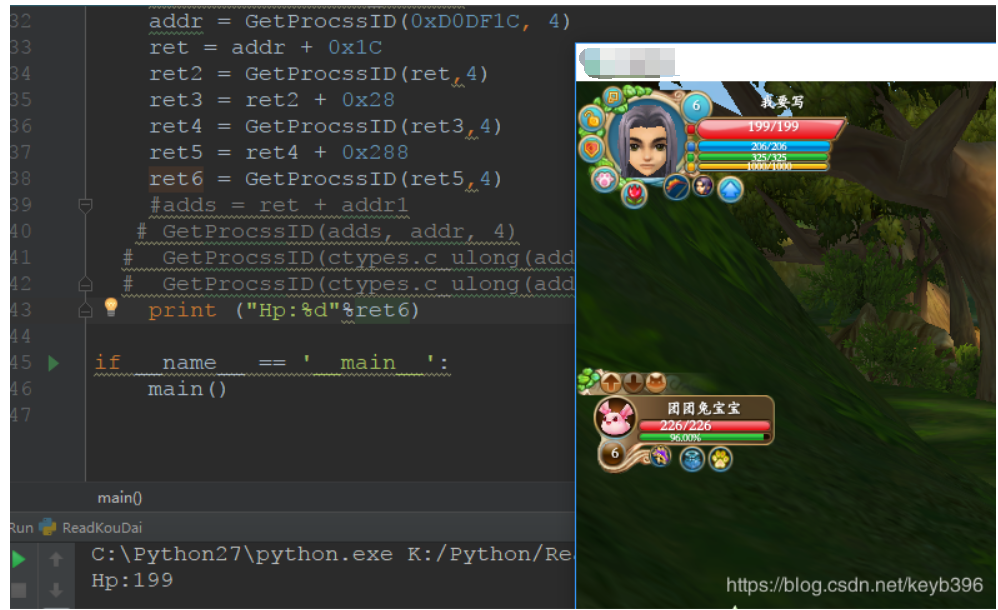
Personal blog: www.wrpzkb.cn

