preface
IpRateLimitMiddleware(Github: AspNetCoreRateLimit )It is a flow limiting middleware of ASPNETCore, which is used to control the frequency of API calls by the client. If the client frequently accesses the server, it can limit its frequency and reduce the pressure of accessing the server. Or if a crawler is crawling key data, it can also limit the number of calls of a certain API or IP every day, so as to limit its crawling speed.
Of course, what I want to solve is another problem. Sometimes there are some APIs in the WebApi we write. We only want other internal applications to call it. For example, the HealthCheck of WebApi. We hope that only our middle console can call it regularly to obtain information, but the front-end cannot call it. In this way, we can put the internal IP address into the IpWhitelist configuration item, and limit the number of specific API calls to 0, so that only the addresses in the white list can access the corresponding endpoints, as shown below.
use
NuGet installation: install package aspnetcoreratelimit
Startup configuration
public Startup(IConfiguration configuration)
{
Configuration = configuration;
}
public IConfiguration Configuration { get; }
public void ConfigureServices(IServiceCollection services)
{
//Add IP current limit
//services.AddMvc().SetCompatibilityVersion(CompatibilityVersion.Latest);
//services.AddOptions();
//services.AddMemoryCache();
//services.Configure<IpRateLimitOptions>(App.Configuration.GetSection("IpRateLimit"));
//services.AddSingleton<IProcessingStrategy, AsyncKeyLockProcessingStrategy>();
//services.AddSingleton<IIpPolicyStore, MemoryCacheIpPolicyStore>();
//services.AddSingleton<IRateLimitCounterStore, MemoryCacheRateLimitCounterStore>();
//services.AddSingleton<IRateLimitConfiguration, RateLimitConfiguration>();
//services.AddHttpContextAccessor();
}
Configure call middleware UseIpRateLimiting
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
//Enable current limiting
//app.UseIpRateLimiting();
}
appsettings.json configuration
"IpRateLimit": {
"EnableEndpointRateLimiting": true,
"StackBlockedRequests": false,
"RealIPHeader": "X-Real-IP",
"ClientIdHeader": "X-ClientId",
"HttpStatusCode": 429,
"GeneralRules": [
{
"Endpoint": "*:/file/multipart/upload",
"Period": "1s",
"Limit": 20
},
{
"Endpoint": "*",
"Period": "1s",
"Limit": 2
},
{
"Endpoint": "*",
"Period": "15m",
"Limit": 300
},
{
"Endpoint": "*",
"Period": "12h",
"Limit": 3000
},
{
"Endpoint": "*",
"Period": "7d",
"Limit": 50000
}
]
}
Configuration description
If enableendpointratelinimiting is set to false, global restrictions are applied and only rules with as endpoints * are applied. For example, if you set a limit of 5 calls per second, any HTTP calls to any endpoint will count towards that limit.
If enableendpointratelinimiting is set to true, restrictions will be applied to each endpoint, such as {HTTP_Verb}{PATH}. For example, if you set a limit of 5 calls per second for the *: / api/values client, you can GET /api/values calls 5 times per second, but you can also call PUT /api/values 5 times.
If StackBlockedRequests is set to false, rejected API calls are not added to the call count. For example, if the client sends three requests per second and you set the limit of one call per second, other limits such as the per minute or daily counter will only record the first call, that is, the successful API call. If you want rejected API calls to count into the display of other times (minutes, hours, etc.), you must set StackBlockedRequests to true.
When RealIpHeader is used, there is a reverse proxy behind your Kestrel server. If your proxy server uses different headers and extracts the client IP X-Real-IP, use this option to set it.
The ClientIdHeader is used to extract the client ID of the whitelist. If a client ID exists in this header and matches the value specified in ClientWhitelist, no rate limit is applied.
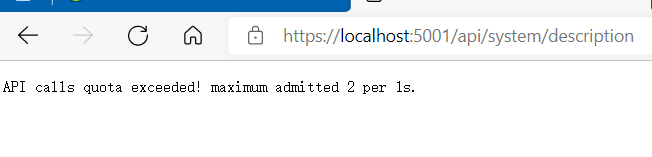
test