To enable https access to the website, first of all, an ssl certificate issued by a certification authority is needed. At present, a certification authority is free for individuals. The better thing is: let's encrypt . Let's Encrypt is a public free SSL project initiated by Mozilla, Cisco, Akamai, IdenTrust and EFF. It is free, easy to install, simple to configure and trustworthy. At present, more than 100 million websites have been encrypted with certificates issued, and it is expected to reach 150 million + by the end of 2018. AMCE V2 released by Let's Encrypt in 2018 has officially supported wildcard certificates, which can support certificates like *.xx.com, making it easier to use.
The certificate of let's encrypt now supports automatic issuance and installation. The client tool is certbot. The official website: https://certbot.eff.org/ Different operating systems, certbot program name is different, my server is ubuntu, the corresponding program is: letsencrypt
Create certificate
Install let's encrypt client
sudo apt-get update sudo apt-get install letsencrypt
Using letsencrypt to create certificates, you can specify multiple domain names as shown below
letsencrypt certonly --webroot -w /var/www/blog -d blog.xxx.org -w /var/www/thing -d thing.is -d m.thing.is
The generated domain name is stored in the directory: / etc/letsencrypt/live/blog.xxx.org/:
- cert.pem: Domain Name Certificate
- chain.pem: Let's Encrypt chain certificate
- Fulchain.pem: cert.pem and chain.pem combination certificates
- privkey.pem: Certificate Private Key
Generate Strong Diffie-Hellman Group (optional)
sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048
Configure nginx
Modify the nginx configuration file, change the corresponding domain name to https access, and modify the server configuration as follows
server { listen 443 ssl http2 default_server; root /var/www/blog; # Here is a list of files, such as index.html, under the path of your website. index index.html index.htm; server_name blog.hutang.us; ssl_certificate /etc/letsencrypt/live/blog.hutang.us/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/blog.hutang.us/privkey.pem; ssl_ciphers "EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5"; ssl_ecdh_curve secp384r1; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_session_cache shared:SSL:10m; ssl_session_tickets off; ssl_stapling on; ssl_stapling_verify on; ssl_dhparam /etc/ssl/certs/dhparam.pem; #Allow access to let's encrypt's webroot plug-in directory location ~ /.well-known { allow all; } }
http access rewritten to https
server { listen 80; server_name blog.xxx.org; rewrite ^(.*)$ https://$host$1 permanent; }
Other domain name redirection
server { server_name xxx.org; return 301 https://blog.xxx.org$request_uri; }
When the configuration is complete, restart nginx: sudo system CTL restart nginx
Then you can access your website through https, as shown in the figure:
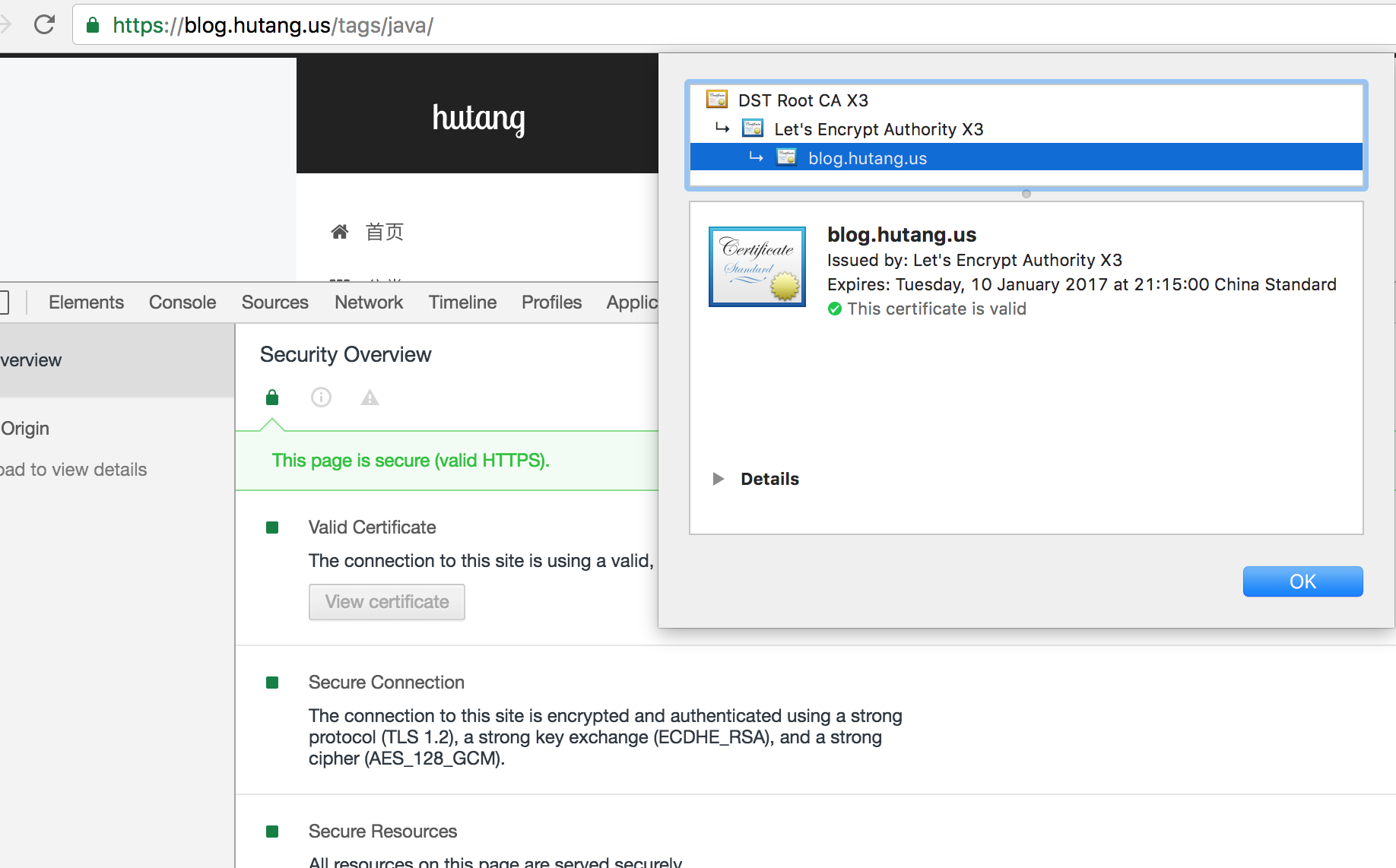
Certificate renewal
let's encrypt's certificate is valid for 3 months. Before it expires, it needs to be regenerated before it can continue to use. The certificate can be regenerated by following commands:
letsencrypt renew
Scheduled tasks can be configured to update certificates regularly to avoid forgetting.
Configuring System D Scheduled Tasks
- Create the letsencrypt service and create a new file: / etc/systemd/system/letsencrypt.service. Enter the following:
[Unit] Description=letsencrypt renew [Service] Type=simple ExecStart=/usr/bin/letsencrypt renew ExecStop=
- Enable service
sudo systemctl enable letsencrypt.service - Create a timer and create a new file: / etc/systemd/system/letsencrypt.timer, enter the following:
[Unit] Description=run letsencrypt renew every day [Timer] OnBootSec=10min OnUnitActiveSec=12h Unit=letsencrypt.service [Install] WantedBy=multi-user.target
OnBootSec represents the execution of the system after boot
The official proposal is to execute every 12 hours. In fact, the renew program will not do anything until the certificate expires.
- Turn on the timer and start
sudo systemctl enable letsencrypt.timer - Turn on the timer
sudo systemctl start letsencrypt.timer