Use and configuration of HTTPS on SL/TLS (IIS8 and iOS client)
CA certificate
1. Domain Name Type SSL Certificate (DV SSL): The trust level is ordinary, only need to verify the authenticity of the website can issue certificates to protect the website; generally free.
2. Enterprise-type SSL Certificate (OV SSL): Strong trust level, need to verify the identity of the enterprise, strict audit, higher security; charging
3. Enhanced SSL Certificate (EV SSL): The highest level of trust, generally used in financial institutions such as banks and securities, strict audit, the highest security, and can activate the green web site bar. It's more expensive than the OV certificate.
4. Self-Signed Cert: There are many tools created. For example, keystrings in Mac can be created, and server certificates in IIS can be created.
https://help.aliyun.com/knowledge_detail/42216.html
Public Key and Private Key are a pair of keys (i.e. a public key and a private key) obtained by an algorithm. The public key is the public part of the key pair and the private key is the non-public part. Public keys are usually used to encrypt session keys, verify digital signatures, or encrypt data that can be decrypted with the corresponding private key. The key pair obtained by this algorithm can be guaranteed to be unique in the world. When using this key pair, if one key is used to encrypt a piece of data, another key must be used to decrypt it. For example, data encrypted with public key must be decrypted with private key, and if it is encrypted with private key, it must be decrypted with public key, otherwise decryption will not succeed.
x509 is the specification of digital certificate, P7 and P12 are two packaging forms. For example, some of the same movies are in avi format and some are in mpg format.
Differences between SSL/TLS/HTTPS
There are currently three versions of Secure Socket Layer: 1.0, 2.0, and 3.0.
TLS (Transport Layer Security) Transport Layer Security Protocol is a standardized product of SSL, which currently has 1.0, Versions 1.1, 1.2
HTTPS (Hyper Text Transfer Protocol over Secure Socket Layer) is HTTP plus SSL/TLS
SSL Digital Certificate for HTTPS-based Web Sites, currently mainly divided into DV There are three types of certificates: SSL, OV SSL and EV SSL.
symantec Certificate Detection
https://cryptoreport.websecurity.symantec.com/checker/views/certCheck.jsp
When you configure https on your website, if IE browser prompts certificate configuration errors, chrome browser prompts unsafe connections, that is, because IIS does not open TLS by default, so we need to manually open SSL/TLS, the specific steps are as follows
https://social.technet.microsoft.com/Forums/forefront/en-US/ec033ff6-091d-441d-8ad3-7ea411100009/ssl-with-256bit-strength
The most important step in this link is
In order to get IIS7 to do 256 bit encryption, we have to ensure the cipher suit that is listed first is the following: TLS_RSA_WITH_AES_256_CBC_SHA
In order to change the Cipher Suite order we can do the following:
- Run gpedit.msc from the command line
- within the Group Policy Object Editor, expand Computer Configuration, Administrative Templates, Network.
- Under Network, select SSL Configuration and then double click on SSL Cipher Suite Order
- By Default the SSL Cipher Suite Order is set to "Not Configured"
- To enable 256-bit encryption, select the "enabled" radio button
- Within the SSL Cipher Suites text box, remove TLS_RSA_WITH_AES_128_CBC_SHA or at least place it behind TLS_RSA_WITH_AES_256_CBC_SHA.
TLS_RSA_WITH_AES_256_CBC_SHA has to be the first cpiher suite listed in order for us to connect with 256-bith encryption.
Once the steps above have been completed, restart the server for the changes to take effect. Now we can browse a page served on the IIS7 server and confirm it is using 256 bit encryption. To do this, right click on the page, select properties and you should see the following:
TLS 1.0, AES with 256 bit encryption (High); RSA with 1024 bit exchange
Creation process of self-signed certificate
1. KeyChain: KeyChain Access - > Certificate Assistant - > Create a Certificate - > Enter a name and select a certificate type - > Create - > generates a self-signed certificate and automatically joins KeyChain
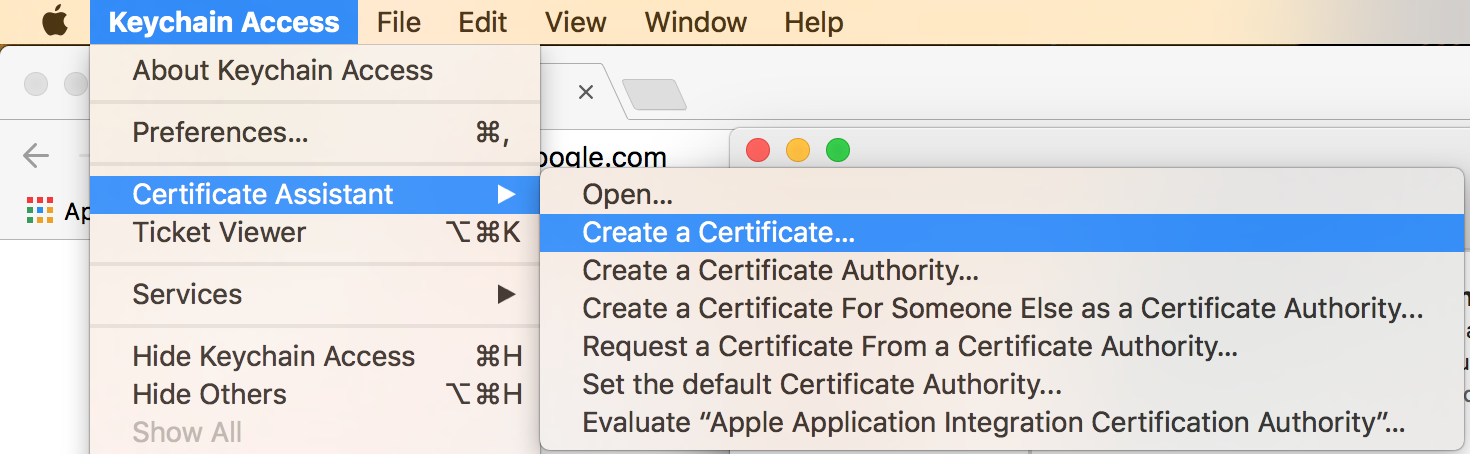
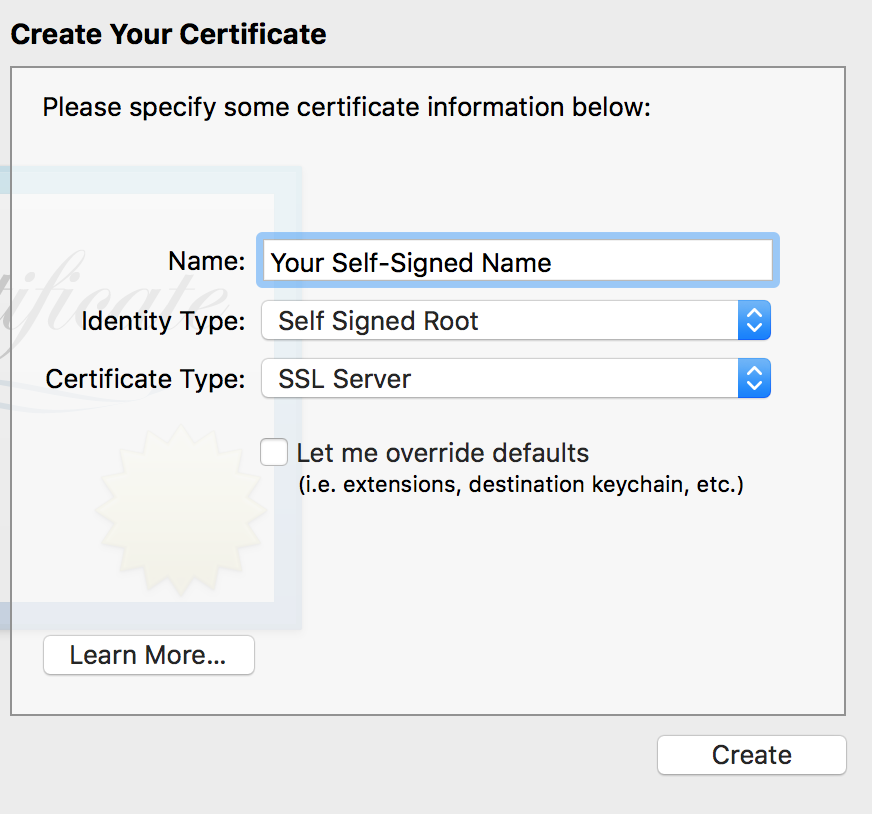

IIS creates self-signed certificates. Look here
http://jingyan.baidu.com/article/48206aeaa60a65216bd6b353.html
Other ways of creation
1.Free https://letsencrypt.org
2. Introduction to XCA http://xca.hohnstaedt.de/
Download address https://sourceforge.net/projects/xca/files/?source=navbar
3. in www.net.cn Apply for DV (domain) verified) Certificate
Okay, the certificate above is finished, and then the iOS client is used and configured.
1.Info.plist is configured as follows. This step is decided according to the situation. If all the requests of your project are HTTPS, this configuration is not needed. If some requests of your project are HTTP, you can configure the domain name of HTTP request here. There are many domain names.
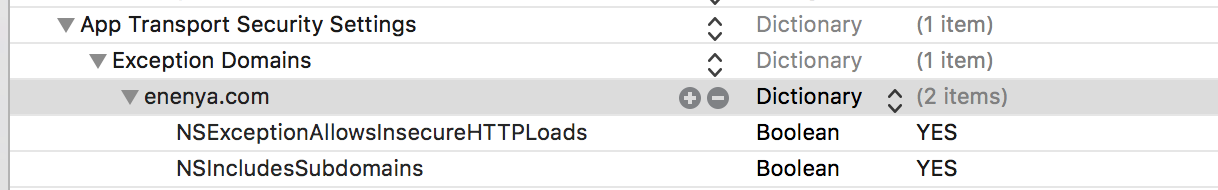
2. Focus on the following, Objective-C code
#import "ViewController.h"
@interface ViewController ()<NSURLSessionDelegate>
@end
@implementation ViewController
- (void)viewDidLoad {
[super viewDidLoad];
}
- (void)touchesBegan:(NSSet<UITouch *> *)touches withEvent:(UIEvent *)event
{
NSURLSessionConfiguration *configuration = [NSURLSessionConfiguration defaultSessionConfiguration];
NSURLSession *session = [NSURLSession sessionWithConfiguration:configuration delegate:self delegateQueue:[NSOperationQueue mainQueue]];
NSURL *url = [NSURL URLWithString:@"https://www.domain.com/Home/LoginWithPass"];
NSMutableURLRequest *request = [NSMutableURLRequest requestWithURL:url];
[request setHTTPMethod:@"POST"];
NSURLSessionDataTask *data = [session dataTaskWithRequest:request completionHandler:^(NSData * _Nullable data, NSURLResponse * _Nullable response, NSError * _Nullable error) {
NSHTTPURLResponse *httpResponse = (NSHTTPURLResponse *)response;
NSString *str = [[NSString alloc] initWithData:data encoding:NSUTF8StringEncoding];
NSLog(@"%@ %ld", str, (long)httpResponse.statusCode);
}];
[data resume];
}
/*
ABSTRACT: For self-signed certificates, DV,OV,EV type certificates
Role: 1. One-way Authentication
This delegate method will be called once, NSURLAuthentication Method Server Trust.
2.Bidirectional Authentication, or Mutual Authentication, or Two-way Authentication
This delegate method will be called twice, namely NSURLAuthentication Method Server Trust and NSURLAuthentication Method Client Certificate.
*/
- (void)URLSession:(NSURLSession *)session didReceiveChallenge:(NSURLAuthenticationChallenge *)challenge completionHandler:(void (^)(NSURLSessionAuthChallengeDisposition, NSURLCredential * _Nullable))completionHandler
{
//Certificate Processing
NSURLSessionAuthChallengeDisposition disposition = NSURLSessionAuthChallengePerformDefaultHandling;
NSURLCredential *credential = nil;
//Determine whether the certificate returned by the server is trusted by the server?
if ([challenge.protectionSpace.authenticationMethod isEqualToString:NSURLAuthenticationMethodServerTrust]) { //Trusted
//Get the certificate returned by the server
credential = [NSURLCredential credentialForTrust:challenge.protectionSpace.serverTrust];
if (credential) {
disposition = NSURLSessionAuthChallengeUseCredential;
} else {
disposition = NSURLSessionAuthChallengePerformDefaultHandling;
}
} else {
//Read the private key of the certificate
NSString *thePath = [[NSBundle mainBundle] pathForResource:@"webtest_ssl_Certificates" ofType:@"p12"];
NSData *PKCS12Data = [[NSData alloc] initWithContentsOfFile:thePath];
CFDataRef inPKCS12Data = (CFDataRef)CFBridgingRetain(PKCS12Data);
SecIdentityRef identity = nil;
//Read the private key content of the p12 certificate
OSStatus result = [self extractP12Data:inPKCS12Data toIdentity:&identity];
if(result != errSecSuccess){
completionHandler(NSURLSessionAuthChallengeCancelAuthenticationChallenge, nil);
return;
}
SecCertificateRef certificate = NULL;
SecIdentityCopyCertificate(identity, &certificate);
const void *certs[] = {certificate};
CFArrayRef certArray = CFArrayCreate(kCFAllocatorDefault, certs, 1, NULL);
credential = [NSURLCredential credentialWithIdentity:identity certificates:(NSArray*)CFBridgingRelease(certArray) persistence:NSURLCredentialPersistencePermanent];
disposition = NSURLSessionAuthChallengeUseCredential;
}
//Installation Certificate (KeyChain imported to the iPhone)
if (completionHandler) {
completionHandler(disposition, credential);
}
}
- (OSStatus)extractP12Data:(CFDataRef)inP12Data toIdentity:(SecIdentityRef *)identity {
OSStatus securityError = errSecSuccess;
CFStringRef password = CFSTR("Your cert password");
const void *keys[] = { kSecImportExportPassphrase };
const void *values[] = { password };
CFDictionaryRef options = CFDictionaryCreate(NULL, keys, values, 1, NULL, NULL);
CFArrayRef items = CFArrayCreate(NULL, 0, 0, NULL);
securityError = SecPKCS12Import(inP12Data, options, &items);
if (securityError == errSecSuccess) {
CFDictionaryRef ident = CFArrayGetValueAtIndex(items, 0);
const void *tempIdentity = NULL;
tempIdentity = CFDictionaryGetValue(ident, kSecImportItemIdentity);
*identity = (SecIdentityRef)tempIdentity;
}
if (options) CFRelease(options);
if (password) CFRelease(password);
return securityError;
}
@end
<script src="https://gist.github.com/VictorZhang2014/1d4903b1c5f260d9cae6a007fb53bebe.js"></script>
Okay, that's it. If you have any questions, please reply in the comments.