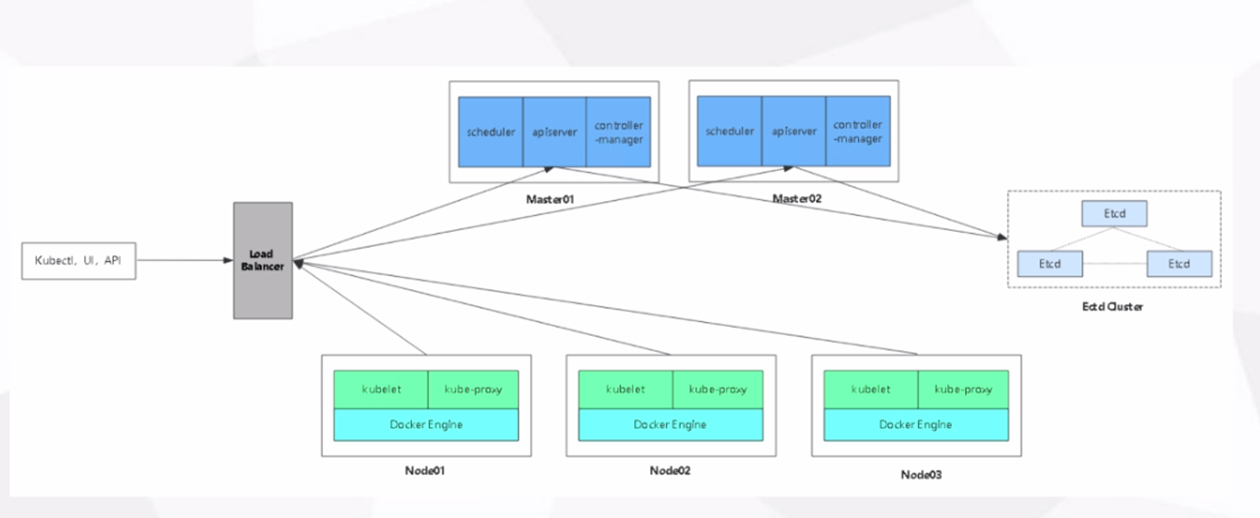
k8s general environmental plan
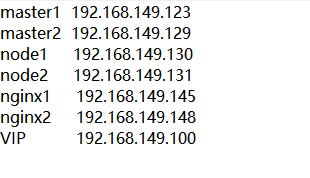
Environmental equipment
Two master nodes, two node nodes and two node nodes are installed with nginx for load balancing, failover and floating address vip
Deployment process
Turn off firewall and security functions
systemctl stop firewalld.service
setenforce 0
Copy the kubernetes directory to master2 (last experiment k8s directory)
scp -r /opt/kubernetes/ root@192.168.149.129:/opt
Copy etcd directory to master2
scp -r /opt/etcd/ root@192.168.149.129:/opt
Replication service script
scp /usr/lib/systemd/system/{kube-apiserver,kube-controller-manager,kube-scheduler}.service root@192.168.149.129:/usr/lib/systemd/system/
Modify the configuration file to change the ip address to the local address
vim /opt/kubernetes/cfg/kube-apiserver
--bind-address=192.168.149.129
--advertise-address=192.168.149.129
Append and modify environment variables and execute them to take effect
vim /etc/profile
export PATH=$PATH:/opt/kubernetes/bin/
source /etc/profile
Deploy keepalive service and prepare script
vim keepalive.conf
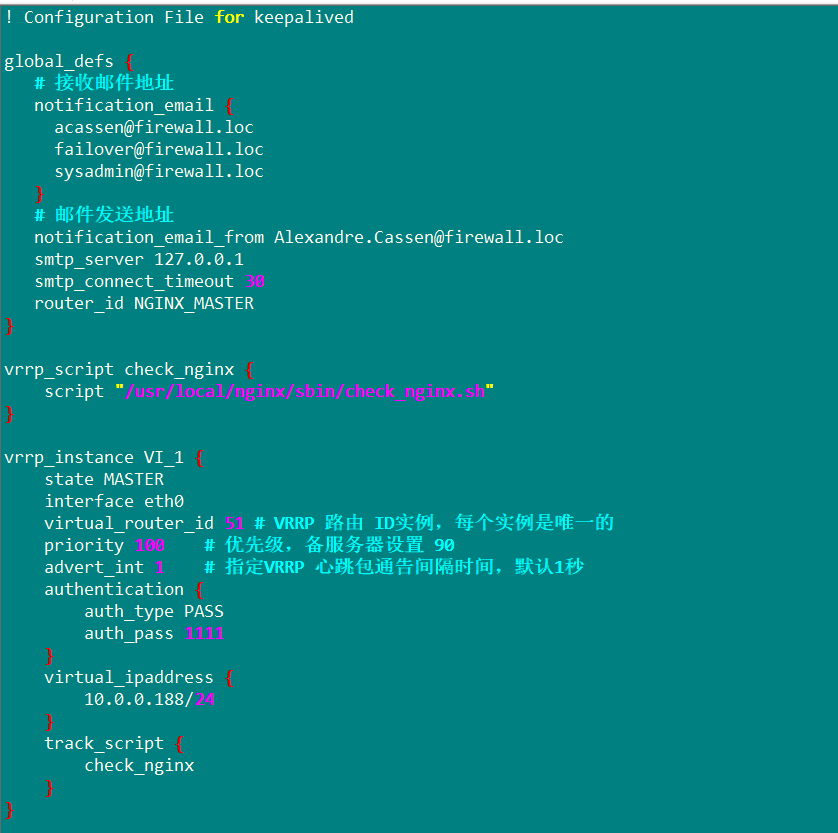
After putting the script into the home directory, build the yum warehouse
vim /etc/yum.repos.d/nginx.repo
[nginx]
name=nginx repo
baseurl=http:/ /nginx.org/packages/centos/7/$basearch/
gpgcheck=0
After completion, refresh the yum warehouse and download nginx
yum list
yum install nginx -y
Add four layer forwarding module and start the service
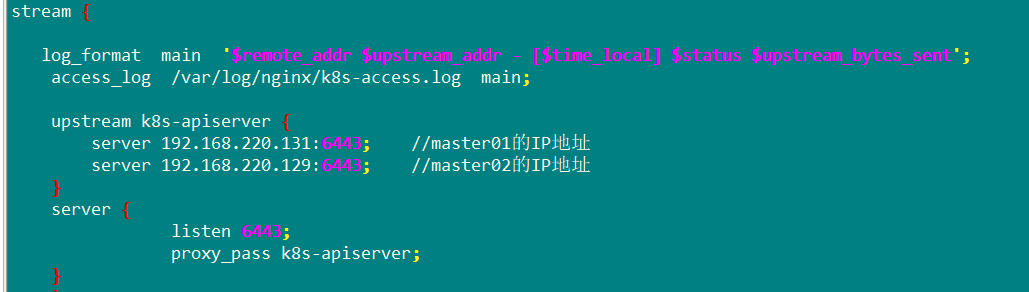
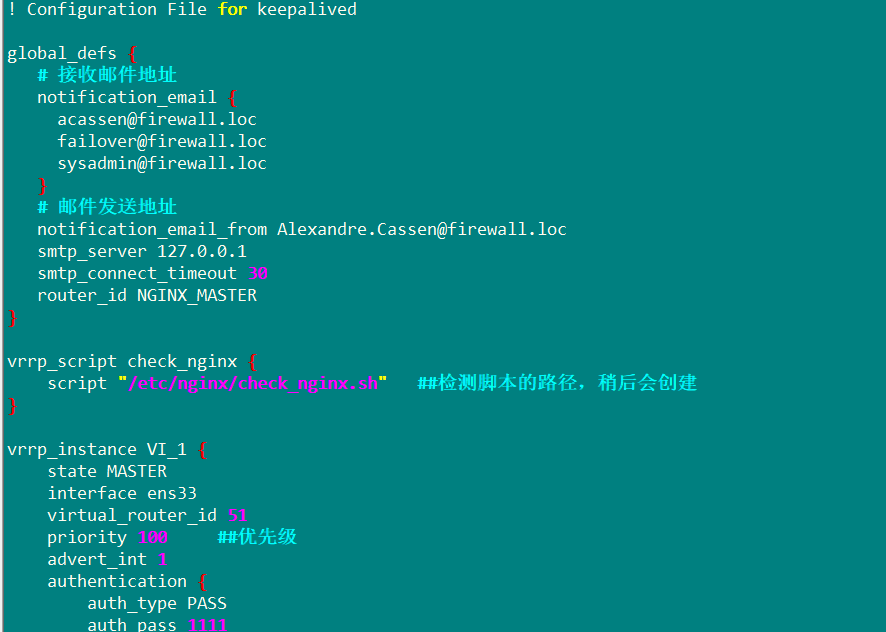
Install the keepalive service, overwrite the prepared configuration file and modify it
yum install keepalived -y
cp keepalived.conf /etc/keepalived/keepalived.conf
vim /etc/keepalived/keepalived.conf
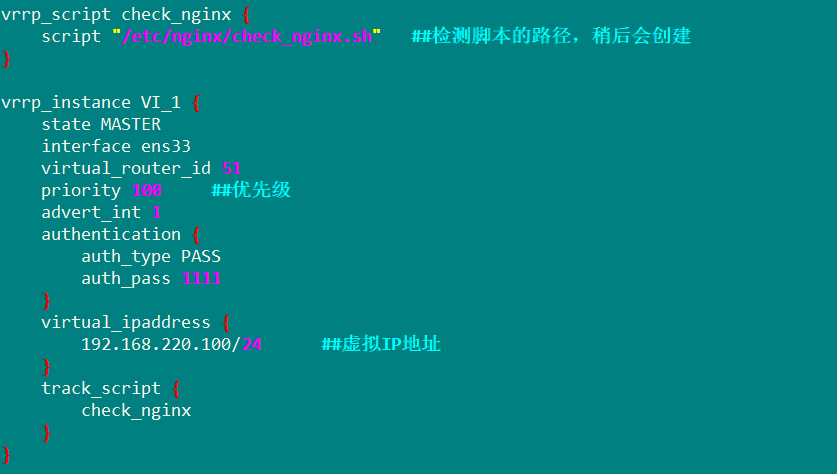
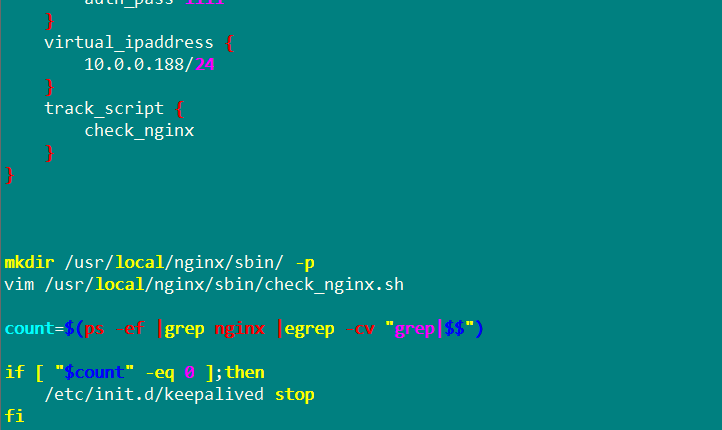
Create nginx script and detect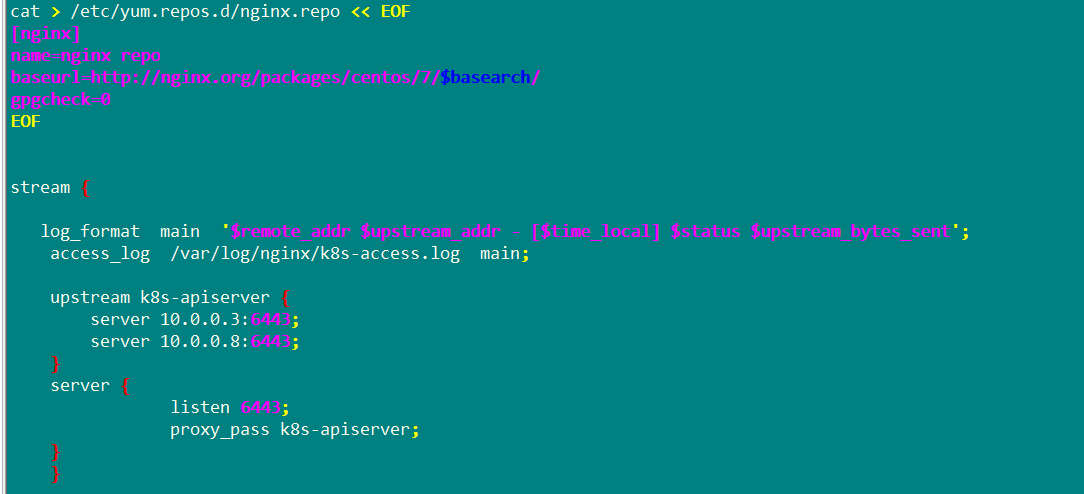
vim /etc/nginx/check_nginx.sh
count=$(ps -ef |grep nginx |egrep -cv "grep|$$")
if [ "$count" -eq 0 ];then
systemctl stop keepalived
fichmod +x /etc/nginx/check_nginx.sh
systemctl start keepalived.service
ip aens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:eb:11:2a brd ff:ff:ff:ff:ff:ff
inet 192.168.149.140/24 brd 192.168.142.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::53ba:daab:3e22:e711/64 scope link
valid_lft forever preferred_lft forever
Node node modify configuration file
cd /opt/kubernetes/cfg/
#Change the profile to VIP
vim /opt/kubernetes/cfg/bootstrap.kubeconfigserver: https:/ /192.168.149.20:6443
#Change line 5 to the address of Vipvim /opt/kubernetes/cfg/kubelet.kubeconfig
server: https:/ /192.168.149.20:6443
#Change line 5 to the address of Vipvim /opt/kubernetes/cfg/kube-proxy.kubeconfig
server: https:/ /192.168.149.20:6443
#Change line 5 to the address of Vip
Self test after replacement
grep 20 *
bootstrap.kubeconfig: server: https:/ /192.168.142.20:6443
kubelet.kubeconfig: server: https:/ /192.168.142.20:6443
kube-proxy.kubeconfig: server: https:/ /192.168.142.20:6443
View the k8s log of nginx on lb01
tail /var/log/nginx/k8s-access.log
192.168.142.140 192.168.142.129:6443 - [08/Feb/2020:19:20:40 +0800] 200 1119
192.168.142.140 192.168.142.120:6443 - [08/Feb/2020:19:20:40 +0800] 200 1119
192.168.142.150 192.168.142.129:6443 - [08/Feb/2020:19:20:44 +0800] 200 1120
192.168.142.150 192.168.142.120:6443 - [08/Feb/2020:19:20:44 +0800] 200 1120
Create Pod
Test create Pod
kubectl run nginx --image=nginx
View state
kubectl get pods
Bind anonymous users in cluster to give administrator rights
kubectl create clusterrolebinding cluster-system-anonymous --clusterrole=cluster-admin --user=system:anonymous
Create UI display interface
Create dashborad working directory on master1
mkdir /k8s/dashboard
cd /k8s/dashboard
Upload official documents to the directory
Authorized access api
kubectl create -f dashboard-rbac.yaml
encryption
kubectl create -f dashboard-secret.yaml
Configuration application
kubectl create -f dashboard-configmap.yaml
Controller
kubectl create -f dashboard-controller.yaml
Publish access
kubectl create -f dashboard-service.yaml
After completion, check that the creation is under the specified Kube system namespace
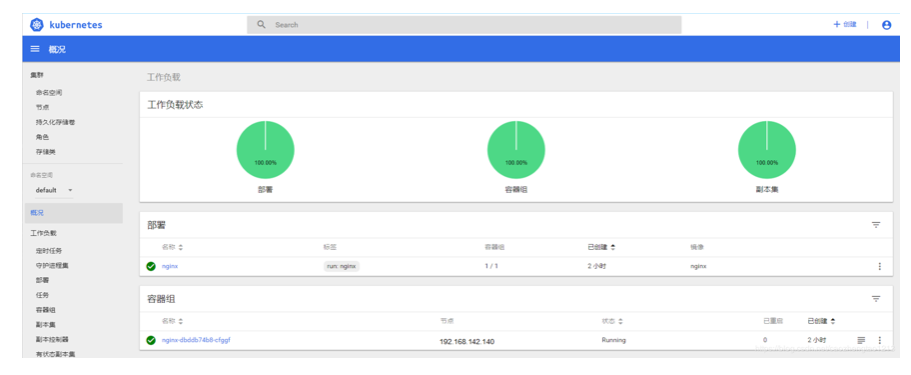
kubectl get pods -n kube-system
See how to access
kubectl get pods,svc -n kube-system
On the master side, write a certificate for self signing
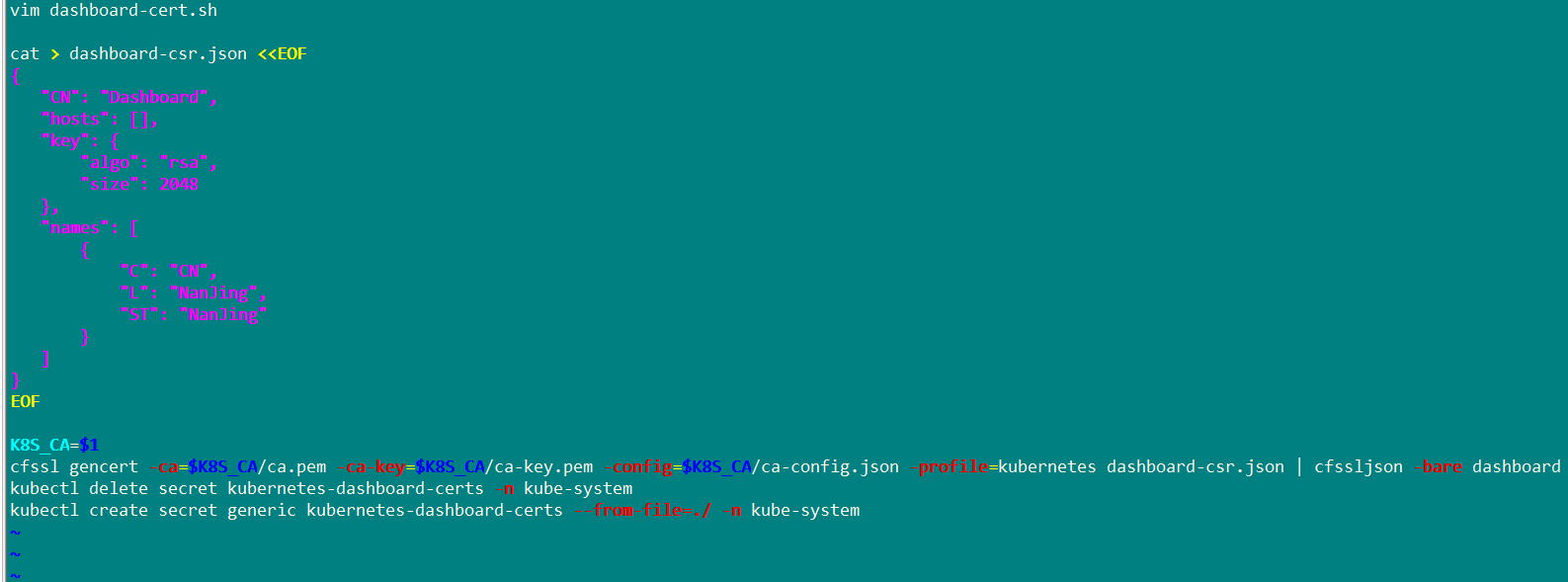
Reapply new self signed certificate
bash dashboard-cert.sh /root/k8s/apiserver/
Modify yaml file
vim dashboard-controller.yaml
- --tls-key-file=dashboard-key.pem
- --tls-cert-file=dashboard.pemRedeploy
kubectl apply -f dashboard-controller.yaml
Generate token
kubectl create -f k8s-admin.yaml
Save token
kubectl get secret -n kube-system
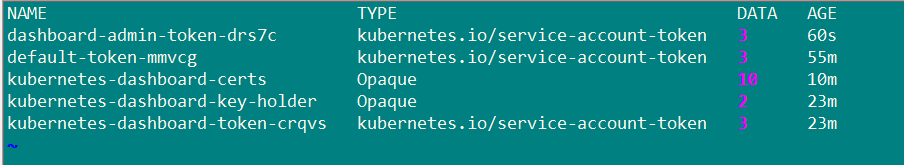
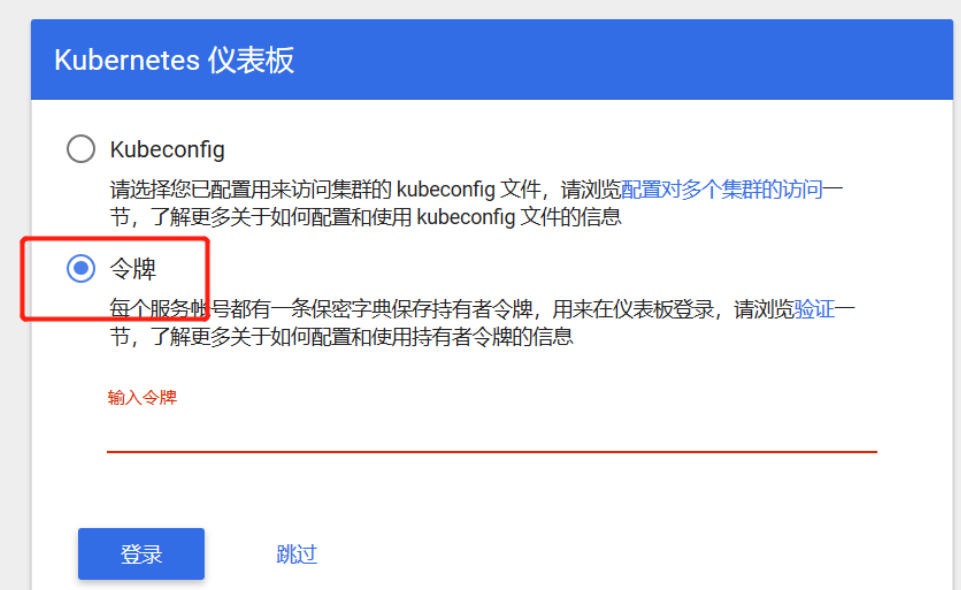
Copy paste token login