I got back an industrial control board with J2900 double Gigabit ports (odd model) for soft routing, but I wanted to use all kinds of skins, install a desktop environment with VNC, and I didn't have a cold on the virtual machine (and this U doesn't support through yet), so I had to give up all the router systems.As an Arch iron powder, in pursuit of no customization and pure origin, you decide to install Archlinux and turn it into a router.Installation of Archlinux goes away, just about the title.The steps are simple and beautiful, and other Linux distributions need to understand them if they want to eat them.
First, you need a dual-port computer (single-port trying to get WiFi's own experience), minimize the installation of Archlinux (it doesn't matter what else has been installed, just the network configuration section needs to adjust itself), and recommend operating in ArchISO to avoid network problems without installing packages (<?).
There are several things you can do to build a router: one network card uses DHCP to access the Internet, the other network card sets a static address and configures DHCP services on it, sets up DNS services (optional), and finally configures iptables to forward traffic and act as a firewall.
(Optional) Before configuring the network, I changed the name of the network interface to lan and wan for the sake of aesthetics.Simply edit/etc/udev/rules.d/10-network.rules to add the following:
SUBSYSTEM=="net", ACTION=="add", ATTR{address}=="00:e0:b5:90:09:1a", NAME="lan"
SUBSYSTEM=="net", ACTION=="add", ATTR{address}=="00:e0:b5:90:09:19", NAME="wan"Replace the MAC address with your own.
Install the necessary packages (iptables come with Archlinux if you don't want to swap with netctl):
pacman -S netctl dhcpcd dhcp
Then configure the network, I choose netctl, and as to why I don't use NetworkManager, it may cause me to lose control of the network card.
Configure the WAN port, edit/etc/netctl/extern-profile (name taken), and then add the following:
Description='Public Interface' Interface=wan Connection=ethernet IP='dhcp'
This is online via DHCP, please check ArchWiki for dial-up.
Then configure the LAN port, edit/etc/netctl/intern-profile (name of your choice), and add the following:
Description='Private Interface'
Interface=lan
Connection=ethernet
IP='static'
Address=('192.168.0.1/24')Description s are just descriptions. If you haven't changed the name of the Interface, you need to replace the Interface with your own (e.g. eth0, enp0s0, etc.). Address is.
Then enable these things:
netctl enable intern-profile netctl enable extern-profile
Now configure the DHCP service, edit/etc/dhcpd.conf, delete everything, and add the following:
option domain-name-servers 8.8.8.8;
option subnet-mask 255.255.255.0;
option routers 192.168.0.1;
subnet 192.168.0.0 netmask 255.255.255.0 {
range 192.168.0.2 192.168.0.255;
}domain-name-servers are DNS server addresses, which can be configured in multiple ways. If a local DNS server is set up, it can be replaced. subnet-mask is a subnet mask, basically not used. routers are gateway addresses. Note that they match Addresses of previous netctl s. Subnet must be x.x.0, and range surfaces can be assigned Address intervals.
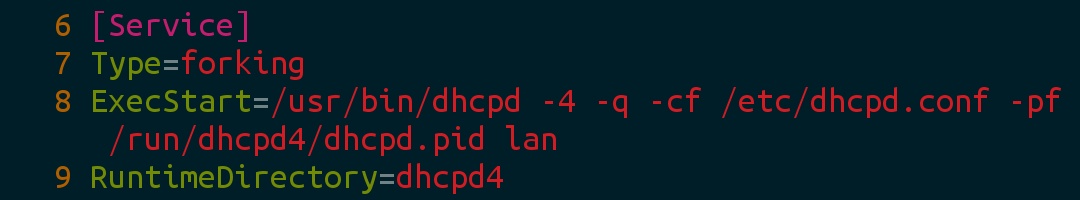
Edit/usr/lib/systemd/system/dhcpd4.service and add the name of the listening network card at the end of ExecStart.
Then set the startup auto-boot, and by the way, let iptables auto-boot:
systemctl enable dhcpd4 systemctl enable iptables
I omitted it because I can't use ipv6.
Exit chroot to restart and enter the system operation. If you remotely operate ArchISO, half of the line will be disconnected and the previously configured service will not be started (although it can be started manually).
Now the WAN port is connected to the Internet, but it can't access the Internet through the LAN port, so it begins to configure forwarding and firewalls.
Turn on Forwarding first (I only turn on ipv4):
echo 'net.ipv4.ip_forward=1' > /etc/sysctl.d/30-ipforward.conf
Arch is written to a separate file, and other distributions are written directly to/etc/sysctl.conf.
Then configure iptables to clear all rules:
iptables -F iptables -t nat -F
Then set the default policy to handle mismatched traffic:
iptables -P INPUT ACCEPT iptables -P OUTPUT ACCEPT iptables -P FORWARD DROP
Then set the variable name for subsequent commands (if you do not modify the name of the network interface you need to modify it to your own):
export LAN=lan export WAN=wan
(Optional) Lock the service so that it only works for the LAN port:
iptables -I INPUT 1 -i ${LAN} -j ACCEPT
iptables -I INPUT 1 -i lo -j ACCEPT
iptables -A INPUT -p UDP --dport bootps ! -i ${LAN} -j REJECT
iptables -A INPUT -p UDP --dport domain ! -i ${LAN} -j REJECT(Optional) Drop TCP/UDP packets for privileged ports:
iptables -A INPUT -p TCP ! -i ${LAN} -d 0/0 --dport 0:1023 -j DROP
iptables -A INPUT -p UDP ! -i ${LAN} -d 0/0 --dport 0:1023 -j DROPFinally, add the NAT rule (be careful to modify it yourself):
iptables -I FORWARD -i ${LAN} -d 192.168.0.0/16 -j DROP
iptables -A FORWARD -i ${LAN} -s 192.168.0.0/16 -j ACCEPT
iptables -A FORWARD -i ${WAN} -d 192.168.0.0/16 -j ACCEPT
iptables -t nat -A POSTROUTING -o ${WAN} -j MASQUERADENow the device connected through the LAN port should be able to connect to the Internet, save the iptables rules:
rm -rf /etc/iptables/iptables.rules iptables-save > /etc/iptables/iptables.rules
With great success, enjoy!(Finally skin ready)