10.12 firewalld and netfilter
selinux temporarily closed
[root@arslinux-01 ~]# setenforce 0 [root@arslinux-01 ~]# getenforce Permissive
selinux permanently closed
[root@arslinux-01 ~]# vi /etc/selinux/config

permissive doesn't block, it reminds, it doesn't show, it just records information.
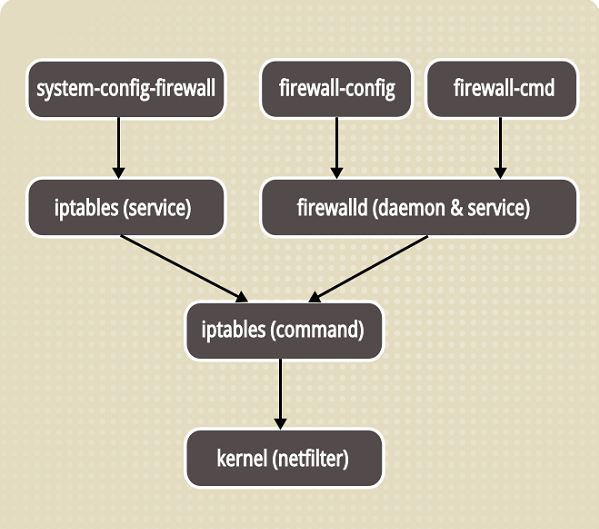
· CentOS 7 used netfilter firewalls before, and CentOS 7 started using firewalld firewalls.
But the use of the iptables tool is the same
Close netfilter and open firewalld
[root@arslinux-01 ~]# systemctl disable firewalld Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service. Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service. [root@arslinux-01 ~]# systemctl stop firewalld
[root@arslinux-01 ~]# yum install -y iptables-services //Passing slightly [root@arslinux-01 ~]# systemctl enable iptables Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service. [root@arslinux-01 ~]# systemctl start iptables
[root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 29 1924 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 16 packets, 1488 bytes) pkts bytes target prot opt in out source destination
10.13 Netfilter 5 Table 5 Chain Introduction
Five tables of netfilter: filter, nat, mangle, raw, security
filter has three chains: INPUT acts on packets entering the machine
FORWARD acts on native-independent packages
OUTPUT acts on the packages that send out the machine
nat has three chains: the PREROUTING packet changes the destination address of the packet just when it reaches the firewall
OUTPUT changes the destination address of locally generated packages
POSTROUTING is used to change the source address of a package as it leaves the firewall.
managle, raw, security tables are basically unused, so you don't need to pay attention to them, just filter and nat.
The process of iptables transmitting data packets

Reference resources: http://www.cnblogs.com/metoy/p/4320813.html
· The packet enters the network card, first enters the PREROUTING chain to judge the target IP. If it is not local, then it is forwarded to the network card. It must go through the FORWARD chain and output to the POSTROUTING chain.
· If PREOUTING judges that IP is local, it will enter the INPUT chain, enter the local kernel, after processing, send out, through the OUTPUT chain, and finally output to the POSTROUTING chain.
Conclusion:
If it's native PREROUTING - > INPUT - > OUTPUT - > POSTROUTING
If not native PREROUTING --> FORWARD --> POSTROUTING
10.14 iptables grammar
Iptables-nvL) View iptables rules
[root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 93 6690 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 14 1877 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 85 packets, 7970 bytes) pkts bytes target prot opt in out source destination
Iptables rules are stored in / etc/sysconfig/iptables
[root@arslinux-01 ~]# cat /etc/sysconfig/iptables # sample configuration for iptables service # you can edit this manually or use system-config-firewall # please do not ask us to add additional ports/services to this default configuration *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT -A INPUT -j REJECT --reject-with icmp-host-prohibited -A FORWARD -j REJECT --reject-with icmp-host-prohibited COMMIT
Clear the iptables rules
[root@arslinux-01 ~]# iptables -F [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 34 packets, 2244 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 18 packets, 1688 bytes) pkts bytes target prot opt in out source destination
Rules are only temporarily cleared, not from the configuration file. If the service is restarted, the rules will also be loaded and take effect.
If you want to take effect permanently, you need to write to the configuration file to execute service iptables save
Save iptables rules
[root@arslinux-01 ~]# service iptables save
Restarting the server or restarting the service will reload the iptables rule
[root@arslinux-01 ~]# service iptables restart Redirecting to /bin/systemctl restart iptables.service [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 14 924 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 1 229 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 8 packets, 864 bytes) pkts bytes target prot opt in out source destination
Restarting the server or restarting the iptables rules loads the rules in the configuration file / etc/sysconfig/iptables
· Rule iptables -t netfilter -nvL (filter table without - t)
Iptables-t nat-nvL) Rules for viewing NAT tables
[root@arslinux-01 ~]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
Iptables-Z Clear Counter
[root@arslinux-01 ~]# iptables -Z;iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
After a while, the data in the first line will increase again.
[root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 10 660 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 6 packets, 1736 bytes) pkts bytes target prot opt in out source destination
After a while, the data in the first line will be added again.
iptables:
- A Add a rule INPUT: For the chain
- s Specified Source ip (source)
- p Specified Protocol (tcp, udp, icmp)
Sportt Source Port
- d target ip
-- dport target port
- j operation (DROP throw / REJECT reject, DROP throw away directly; REJECT looks at him and tells him no)
- I insert
- i Designated Network Card
Iptables-A Increase iptables rules (queue to the end)
[root@arslinux-01 ~]# iptables -A INPUT -s 192.168.188.1 -p tcp --sport 1234 -d 192.168.188.128 --dport 80 -j DROP[root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 413 28732 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 4 946 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 13 packets, 1228 bytes) pkts bytes target prot opt in out source destination
Iptables-I Insertion Rules (equivalent to queue jumping)
[root@arslinux-01 ~]# iptables -I INPUT -p tcp --dport 80 -j DROP [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 524 36068 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 4 946 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 4 packets, 464 bytes) pkts bytes target prot opt in out source destination
Once matched, the latter will not be matched again.
Iptables-D Delete Rules
[root@arslinux-01 ~]# iptables -D INPUT -p tcp --dport 80 -j DROP [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 584 40828 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 4 946 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 4 packets, 464 bytes) pkts bytes target prot opt in out source destination
If the rules need to be deleted are long, the rules are not clear, and iptables-D is not easy to delete.
So you can delete it in a simple way.
iptables deletion rule (simple method)
1. Give the rule a rule number first; 2. Delete the rule corresponding to the rule number.
[root@arslinux-01 ~]# iptables -nvL --line-number Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 2 654 45448 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 6 5 1175 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 7 0 0 DROP tcp -- * * 192.168.188.1 192.168.188.128 tcp spt:1234 dpt:80 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 32 packets, 4368 bytes) num pkts bytes target prot opt in out source destination
[root@arslinux-01 ~]# iptables -D INPUT 7 [root@arslinux-01 ~]# iptables -nvL --line-number Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 2 717 49616 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 5 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 6 5 1175 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 10 packets, 2232 bytes) num pkts bytes target prot opt in out source destination
Iptables-i) Specify a network card
[root@arslinux-01 ~]# iptables -I INPUT -s 192.168.1.0/24 -i eth0 -j ACCEPT
· Default Rules: If there are no specific rules to match the data packet, then go to the default policy policy.
· Change the default policy: iptables -P OUTPUT DROP (remote connection will be disabled if running, only to the host to modify the rules)
[root@arslinux-01 ~]# iptables -P OUTPUT DROP
C. Change back to policy: iptables-P OUTPUT ACCEPT (release)
[root@arslinux-01 ~]# iptables -P OUTPUT ACCEPT
DROP / REJECT / ACCEPT
10.15 iptables filter table case
iptables small case
[root@arslinux-01 ~]# vi /usr/local/sbin/iptables.sh
#!/bin/bash ipt="/usr/sbin/iptables" $ipt -F $ipt -P INPUT DROP $ipt -P OUTPUT ACCEPT $ipt -P FORWARD ACCEPT $ipt -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT $ipt -A INPUT -s 192.168.194.0/24 -p tcp --dport 22 -j ACCEPT $ipt -A INPUT -p tcp --dport 80 -j ACCEPT $ipt -A INPUT -p tcp --dport 21 -j ACCEPT :wq
Interpretation:
ipt="/usr/sbin/iptables"
Define a variable ipt. It's easy and easy to write a global path.
$ipt -F
Clear away the original rules
$ipt -P INPUT DROP
Define default policy INPUT DROP out
$ipt -P OUTPUT ACCEPT
$ipt -P FORWARD ACCEPT
All ACCEPT of OUTPUT and FORWARD
$ipt -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
Add Rules: - m state specifies state, specifies let RELATED, ESTABLISHED state release
$ipt -A INPUT -s 192.168.194.0/24 -p tcp --dport 22 -j ACCEPT
Additional Rules: 192.168.194.0/24 network segment, 22 port data packet release
$ipt -A INPUT -p tcp --dport 80 -j ACCEPT
$ipt -A INPUT -p tcp --dport 21 -j ACCEPT
Packet Release on Ports 80 and 21
Actual operation:
[root@arslinux-01 ~]# sh /usr/local/sbin/iptables.sh [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 32 2112 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT tcp -- * * 192.168.194.0/24 0.0.0.0/0 tcp dpt:22 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 17 packets, 1596 bytes) pkts bytes target prot opt in out source destination
Restore the default state:
[root@arslinux-01 ~]# service iptables restart Redirecting to /bin/systemctl restart iptables.service [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 40 2640 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 21 packets, 1964 bytes) pkts bytes target prot opt in out source destination
icmp example:
Ping local ip can ping through
Extranet can also be ping-connected
[root@arslinux-01 ~]# ping www.baidu.com PING www.baidu.com (192.168.194.150) 56(84) bytes of data. 64 bytes from www.baidu.com (192.168.194.150): icmp_seq=1 ttl=64 time=0.030 ms 64 bytes from www.baidu.com (192.168.194.150): icmp_seq=2 ttl=64 time=0.042 ms ^C --- www.baidu.com ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1000ms rtt min/avg/max/mdev = 0.030/0.036/0.042/0.006 ms
After adding rules, you can't Ping the local machine, but you can ping the external network.
[root@arslinux-01 ~]# iptables -I INPUT -p icmp --icmp-type 8 -j DROP
iptables -I INPUT -p icmp --icmp-type 8 -j DROP
10.16/10.17/10.18 iptables nat table application
Demand:
A: Two network cards, one can access the external network and the other can use the internal network.
B: Only one intranet card
Let B Machine Connect to External Network
Add a Network Card to Machine A
Virtual Machine Settings - > Add - > Add Network Adapter - > Default - > In LAN Section, create a new custom Section Name - > Select Section
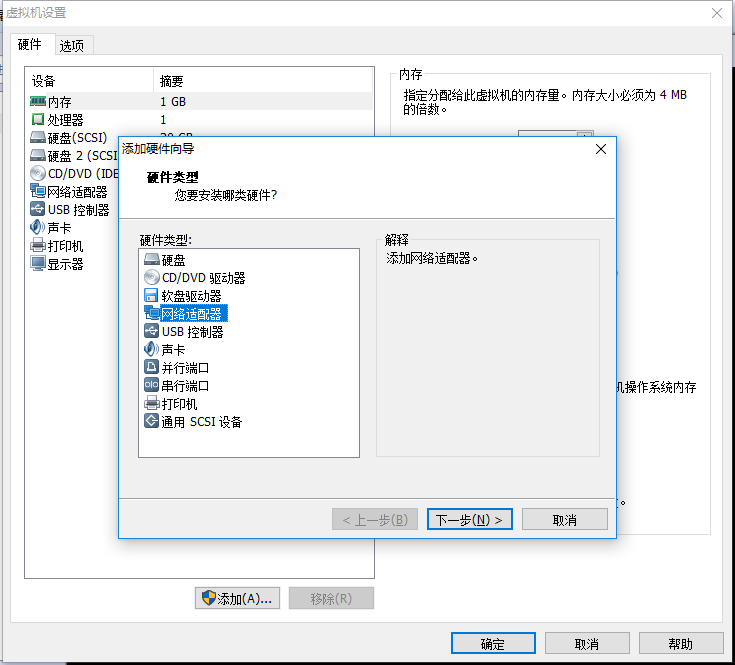



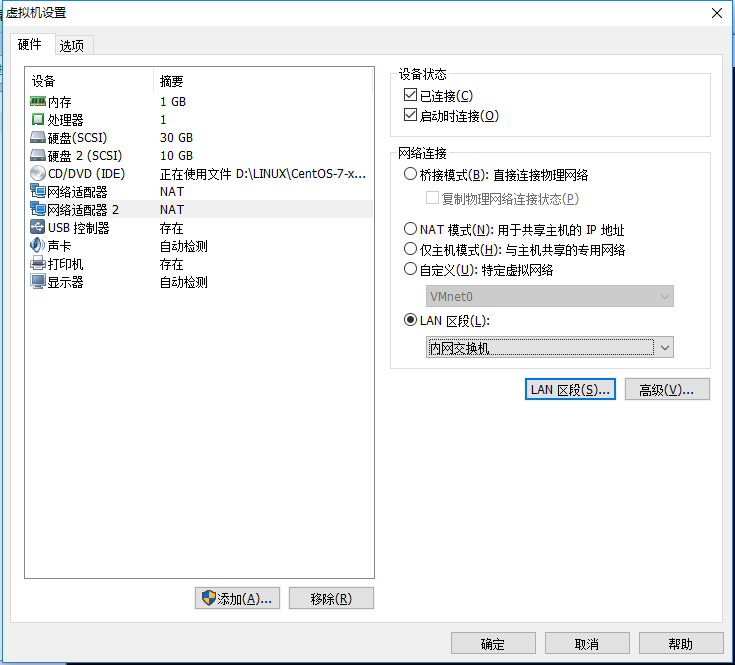
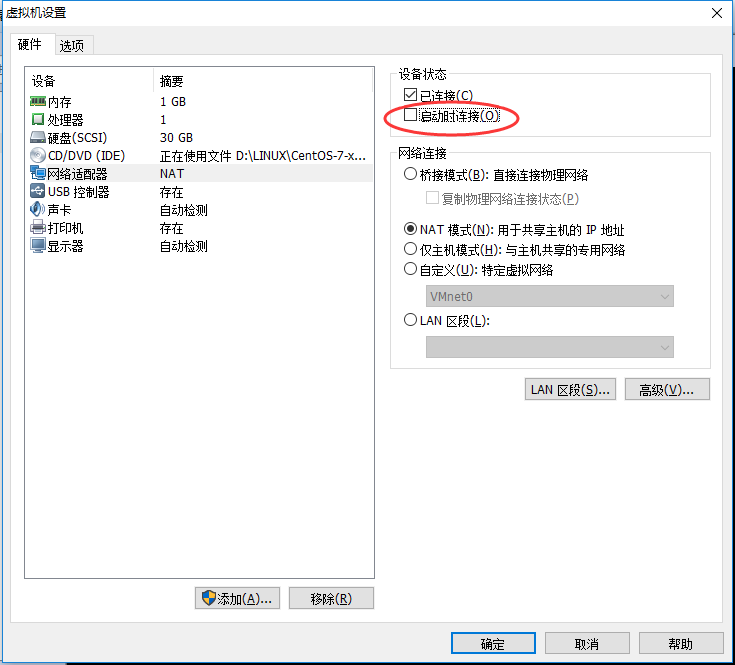
Machine B adds network card and disconnects the original network card connection
Add a network card with machine A, select LAN section, select intranet switch
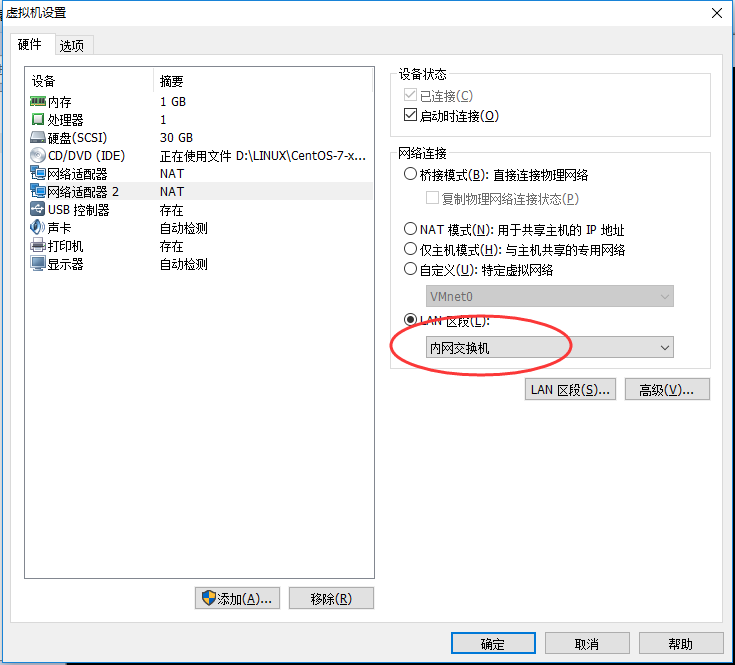
A and B, two machines choose the same section, the same switch
Machine A can continue to use remote connections, while Machine B thinks it has disabled the original network card, so it can only operate the virtual machine directly.
A machine:
[root@arslinux-01 ~]# ifconfig ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.194.130 netmask 255.255.255.0 broadcast 192.168.194.255 inet6 fe80::c905:5e78:b916:41da prefixlen 64 scopeid 0x20<link> ether 00:0c:29:24:ea:f2 txqueuelen 1000 (Ethernet) RX packets 102 bytes 11545 (11.2 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 115 bytes 15471 (15.1 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ens33:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.194.150 netmask 255.255.255.0 broadcast 192.168.194.255 ether 00:0c:29:24:ea:f2 txqueuelen 1000 (Ethernet) ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 ether 00:0c:29:24:ea:fc txqueuelen 1000 (Ethernet) RX packets 23 bytes 7866 (7.6 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 64 bytes 10952 (10.6 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens37 is a new network card
ifconfig ens37 192.168.100.1/24 Manual command line setting IP, restart to restore default
Adding configuration files directly will take effect permanently
Add IP to ens37 and create configuration network card file
[root@arslinux-01 ~]# cd /etc/sysconfig/network-scripts/ [root@arslinux-01 network-scripts]# cp ifcfg-ens33 ifcfg-ens37 [root@arslinux-01 network-scripts]# vim ifcfg-37
TYPE=Ethernet PROXY_METHOD=none BROWSER_ONLY=no BOOTPROTO=static DEFROUTE=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=ens37 DEVICE=ens37 ONBOOT=yes IPADDR=192.168.100.1 NETMASK=255.255.255.0 :wq
Just set IP and subnet masks and delete UUID and MAC addresses
Restart the network and you can see that ens37 has a successful range
[root@arslinux-01 network-scripts]# systemctl restart network [root@arslinux-01 network-scripts]# ifconfig ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.194.130 netmask 255.255.255.0 broadcast 192.168.194.255 inet6 fe80::c905:5e78:b916:41da prefixlen 64 scopeid 0x20<link> ether 00:0c:29:24:ea:f2 txqueuelen 1000 (Ethernet) RX packets 678 bytes 62503 (61.0 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 506 bytes 86900 (84.8 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ens33:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.194.150 netmask 255.255.255.0 broadcast 192.168.194.255 ether 00:0c:29:24:ea:f2 txqueuelen 1000 (Ethernet) ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.100.1 netmask 255.255.255.0 broadcast 192.168.100.255 inet6 fe80::f41:9da7:d8e3:10ba prefixlen 64 scopeid 0x20<link> ether 00:0c:29:24:ea:fc txqueuelen 1000 (Ethernet) RX packets 42 bytes 14364 (14.0 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 156 bytes 25698 (25.0 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Log on to B machine, set ens37 network card in the same way, ip 192.168.100.100/24
[root@arslinux-02 ~]# cd /etc/sysconfig/network-scripts/ [root@arslinux-02 network-scripts]# cp ifcfg-ens33 ifcfg-ens37 [root@arslinux-02 network-scripts]# vim ifcfg-37
TYPE=Ethernet PROXY_METHOD=none BROWSER_ONLY=no BOOTPROTO=static DEFROUTE=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=ens37 DEVICE=ens37 ONBOOT=yes IPADDR=192.168.100.100 NETMASK=255.255.255.0 :wq
[root@arslinux-02 network-scripts]# ifdown end33 Device 'ens33' successfully disconnected. [root@arslinux-02 network-scripts]# systemctl restart network [root@arslinux-02 network-scripts]# ifconfig ens33: flags=4099<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 ether 00:0c:29:14:4f:d9 txqueuelen 1000 (Ethernet) RX packets 0 bytes 0 (0.0 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.100.100 netmask 255.255.255.0 broadcast 192.168.100.255 inet6 fe80::3771:e1f:d792:b669 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:14:4f:e3 txqueuelen 1000 (Ethernet) RX packets 47 bytes 15228 (14.8 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 233 bytes 35912 (35.0 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@arslinux-02 network-scripts]# ping 192.168.100.1 PING 192.168.100.1 (192.168.100.1) 56(84) bytes of data. 64 bytes from 192.168.100.1: icmp_seq=1 ttl=64 time=1.31 ms 64 bytes from 192.168.100.1: icmp_seq=2 ttl=64 time=0.337 ms 64 bytes from 192.168.100.1: icmp_seq=3 ttl=64 time=0.296 ms 64 bytes from 192.168.100.1: icmp_seq=4 ttl=64 time=0.304 ms ^C --- 192.168.100.1 ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3003ms rtt min/avg/max/mdev = 0.296/0.562/1.312/0.433 ms [root@arslinux-01 network-scripts]#
A and B have been successfully connected
Completion of preparatory work
Requirement 1: B machines can be connected to the external network
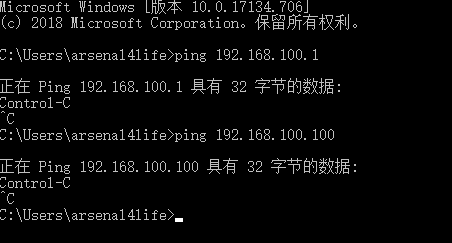
In windows, the host can't ping the network cards of two virtual machines
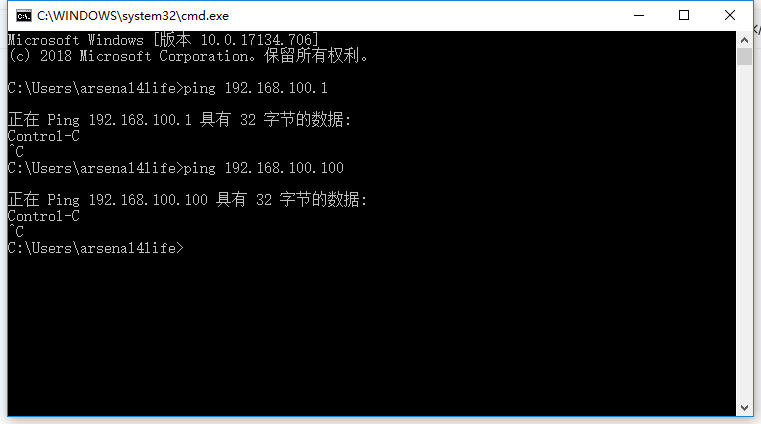
Machine B can't connect with A's first network card, and it can't connect to the Internet at the same time.

1. Open port forwarding on machine A
Echo "1" >/proc/sys/net/ipv4/ip_forward (0 is closed, 1 is open, default is 0)
[root@arslinux-01 network-scripts]# cat /proc/sys/net/ipv4/ip_forward 0 [root@arslinux-01 network-scripts]# echo "1" > !$ echo "1" > /proc/sys/net/ipv4/ip_forward [root@arslinux-01 network-scripts]# !cat cat /proc/sys/net/ipv4/ip_forward 1
2.A Machine Add a Rule
iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -o ens33 -j MASQUERADE
[root@arslinux-01 network-scripts]# iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -o ens33 -j MASQUERADE [root@arslinux-01 network-scripts]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 MASQUERADE all -- * ens33 192.168.100.0/24 0.0.0.0/0
3.B Machine Sets Gateway 192.168.100.1 to enable data packets from B to A
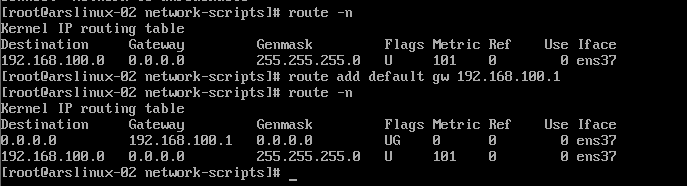
Machine B has been able to ping the first network card of Machine A.
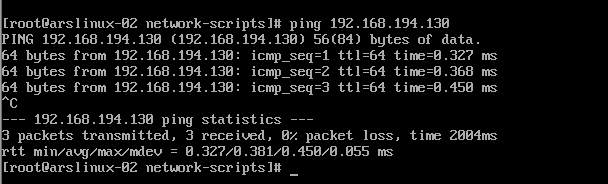
Edit the public DNS configuration file/etc/resolve.conf

At first, ping was different from 119.29.29.29, and it was not working. www.qq.com
Return to machine A, add the iptables rules again, and then return to machine B to connect.
A machine
[root@arslinux-01 network-scripts]# iptables -F [root@arslinux-01 network-scripts]# iptables -t nat -F [root@arslinux-01 network-scripts]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
[root@arslinux-01 network-scripts]# iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -o ens33 -j MASQUERADE [root@arslinux-01 network-scripts]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 MASQUERADE all -- * ens33 192.168.100.0/24 0.0.0.0/0
B machine
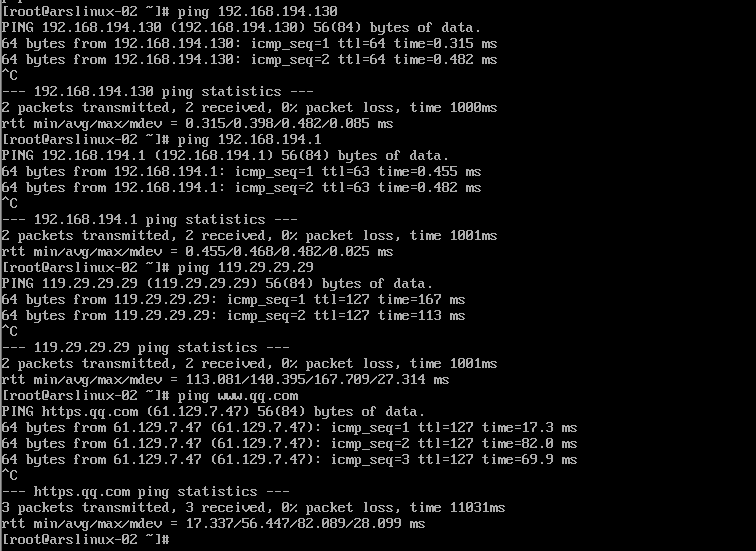
You can connect to the outside network, but you still can't connect to the inside network.
Machine A is the router and Machine B is the terminal connecting the router.
Requirement 2: C machine can only communicate with A, so that C machine can directly connect to port 22 of B machine (port mapping)
Although 192.168.100.100 can not be connected, but can connect A machine 192.168.194.130, can do a jump to B machine 192.168.100.100, this is called port mapping.
· A port of machine A 192.168.65.128 (we set it to 1122) is mapped to port 22 of machine B 192.168.100.100.
· Accessing port 112 of A machine 192.168.194.130 is actually accessing port 22 of B machine 192.168.100.100.
1. Open Port Forwarding
[root@arslinux-01 network-scripts]# echo "1" > /proc/sys/net/ipv4/ip_forward
2. Delete the original iptables rule
[root@arslinux-01 network-scripts]# iptables -t nat -D POSTROUTING -s 192.168.100.0/24 -o ens33 -j MASQUERADE [root@arslinux-01 network-scripts]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
3. Adding new iptables rules
All bags in and out of Machine A should be specified.
Output: iptables - t NAT - A PREROUTING - D 192.168.194.130 - P TCP -- dport 1122 - J DNA T -- to 192.168.100.100:22
Enter: iptables -t nat -A POSTROUTING -s 192.168.100.100 -j SNAT --to 192.168.194.130
[root@arslinux-01 network-scripts]# iptables -t nat -A PREROUTING -d 192.168.194.130 -p tcp --dport 1122 -j DNAT --to 192.168.100.100:22 [root@arslinux-01 network-scripts]# iptables -t nat -A POSTROUTING -s 192.168.100.100 -j SNAT --to 192.168.194.130[root@arslinux-01 network-scripts]# iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 DNAT tcp -- * * 0.0.0.0/0 192.168.194.130 tcp dpt:1122 to:192.168.100.100:22 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 SNAT all -- * * 192.168.100.100 0.0.0.0/0 to:192.168.194.130
4. Gateway for B Machine
It was done before Demand 1.
Create a new session with port 1122 of machine A

Has successfully entered the B machine

Successful connection to external network
Reference resources: http://man.linuxde.net/iptables
http://blog.chinaunix.net/uid-26495963-id-3279216.html
Extension: (selinux understands)
selinux tutorial http://os.51cto.com/art/201209/355490.htm
selinux pdf e-book http://pan.baidu.com/s/1jGGdExK
Application of iptables in a network segment http://www.aminglinux.com/bbs/thread-177-1-1.html
sant,dnat,masquerade http://www.aminglinux.com/bbs/thread-7255-1-1.html
iptables limit syn rate http://www.aminglinux.com/bbs/thread-985-1-1.html
http://jamyy.us.to/blog/2006/03/206.html
0416 Classroom Notes
Extension:

1 for network segments
iptables -I INPUT -m iprange --src-range 61.4.176.0-61.4.191.255 -j DROP
192.168.1.0/24
iptables -I INPUT -p tcp --dport 80 -s 192.168.1.0/24 -j ACCEPT
- m is followed by the module name, iprange is a module name to support a network segment
- ip range of src-range specified source
- dst-range specifies the target ip range
2. sant dnat masquerade http://ask.apelearn.com/question/7255
3 There are four states on iptables: NEW, ESTABLISHED, INVALID and RELATED.
NEW: NEW says this package is the first one we see. This means that this is the first package of a connection seen by the conntrack module, and it will soon be matched. For example, we see a SYN package, which is the first package of the connection we've noticed, and we need to match it.
ESTABLISHED: ESTABLISHED has noticed data transfers in both directions and will continue to match the packages of this connection. Connections in the ESTABLISHED state are very easy to understand. As long as the response is sent and received, the connection is ESTABLISHED. To change a connection from NEW to ESTABLISHED, you only need to receive a reply packet, whether it is sent to the firewall or forwarded by the firewall. Packets such as ICMP errors and redirections are also considered ESTABLISHED as long as they are responses to the messages we send out.
RELATED: RELATED is a troublesome state. When a connection is related to a connection that is already in the ESTABLISHED state, it is considered RELATED. In other words, if a connection is to be RELATED, it must first have an ESTABLISHED connection. This ESTABLISHED connection produces a connection other than a primary connection. This new connection is RELATED, provided that the conntrack module understands RELATED. FTP is a good example. FTP-data connection is related to FTP-control. If RELATED status is not configured in the iptables policy, FTP-data connection can not be established correctly. There are other examples, such as DCC connection through IRC. With this state, ICMP response, FTP transmission, DCC and so on can work properly through the firewall. Note that most UDP protocols rely on this mechanism. These protocols are very complex. They put connection information in data packets and require that it be understood correctly.
INVALID: INVALID indicates that a packet cannot be identified as belonging to which connection or without any state. There are several reasons for this, such as memory overflow and receiving ICMP error messages that do not know which connection they belong to. Generally, anything in our DROP state, because firewalls think it's unsafe.
4 speed limit
http://ask.apelearn.com/question/985
http://jamyy.us.to/blog/2006/03/206.html
iptables -N syn-flood
iptables -A syn-flood -m limit --limit 5/s --limit-burst 500 -j RETURN
iptables -A syn-flood -j DROP
iptables -I INPUT -j syn-flood
5. limit module of iptables
https://www.centos.bz/2018/10/iptables-%E7%9A%84limit%E6%A8%A1%E5%9D%97/