1 MD5 encryption
MD5 message digest algorithm (English: MD5 message digest algorithm), a widely used cryptographic hash function, can generate a 128 bit (16 byte) hash value to ensure complete and consistent information transmission. MD5 was designed by American Cryptologist Ronald Linn Rivest and published in 1992 to replace MD4 algorithm. The program of this algorithm is standardized in RFC 1321 standard. After 1996, the algorithm was proved to have weaknesses and can be cracked. For data requiring high security, experts generally recommend to use other algorithms, such as SHA-2. In 2004, it was confirmed that MD5 algorithm can not prevent collision, so it is not suitable for security authentication, such as SSL public key authentication or digital signature.
MD5 features:
1. It can only be encrypted from plaintext to ciphertext, irreversible and unbreakable
2. The current crack can only crack some functions or reverse queries
3. md5 upgrade md5hash = plaintext + salt, almost unbreakable
example:
md5(123) = xxxxxxxx
md5(123 + lyj) = yyyyyyyyy
md5(123lyj+lyj) = zzzzzzzz
//Gets the password in the object
byte[] bytes = user.getPassword().getBytes();
//Encrypt password using MD5
String md5Pass = DigestUtils.md5DigestAsHex(bytes);
//Put the encrypted password back to the original object
user.setPassword(md5Pass);
2 cookies and Session
2.1 business description
The user sends a request to the server to obtain the results of the server. However, the life cycle of the request is a request and a response. If the request ends, all the response data will be cleared
In order to save the response data of the server, you should find a way to persist the server data!!!
2.2 Session description
Session: in computers, especially in network applications, it is called "session control". The session object stores the properties and configuration information required for a specific user session. In this way, when the user jumps between the Web pages of the application, the variables stored in the session object will not be lost, but will exist throughout the user session. When a user requests a Web page from an application, if the user does not have a session, the Web server will automatically create a session object. When a session expires or is abandoned, the server terminates the session. One of the most common uses of the session object is to store user preferences. For example, if you indicate that you don't like viewing drawings, you can store this information in the session object. For more information about using session objects, see "managing sessions" in the ASP applications section. Note that session state is reserved only in browsers that support cookie s.
summary: 1. Session Called session control" 2. Session User information can be stored. 3. Session The lifecycle of data is the entire session,If the session is closed, the data is cleared. 4. Session The data structure is key-value structure. 5. Session Store in browser
2.3 Cookie description
Cookie s, sometimes in the plural form. The type is "small text file", which is the data (usually encrypted) stored on the user's local terminal by some websites in order to identify the user's identity and track the Session, and the information temporarily or permanently saved by the user's client computer
summary: 1. Cookie Is a small text file,Store on local terminal. 2. Cookie User information can be stored. 3. Cookie Data type for key-value 4. Cookie The data in is generally saved by encryption 5. Cookie Your data can"permanent"preservation.
2.4 Session and Cookie selection
characteristic:
1. If the data needs to be saved temporarily, select Session. If the data needs to be stored for a long time, select Cookie
2. Select Session for data with high security requirements and Cookie for data with low security requirements
Question: what technology does the financial system user use to save information? session
3. Global exception handling
3.1 exception description
explain: When an exception occurs in the background server,The front-end user cannot get exception information,Poor user experience
Exception handling:
@DeleteMapping("/{id}")
public SysResult deleteById(@PathVariable Integer id){
//To prevent conflicts with MP methods, it is best to add a business name to the business method
try {
userService.deleteUserById(id);
return SysResult.success();
}catch (Exception e){
e.printStackTrace();
return SysResult.fail();
}
}
explain:
If a large number of try catches are added to the business code, it will lead to high business complexity and inconvenient maintenance
3.2 Spring's global exception handling mechanism
Using in AOP slice programming
package com.jt.exe;
import com.jt.vo.SysResult;
import org.springframework.web.bind.annotation.ControllerAdvice;
import org.springframework.web.bind.annotation.ExceptionHandler;
import org.springframework.web.bind.annotation.RestControllerAdvice;
import java.sql.SQLException;
//1. Identify that this class is a global exception handling mechanism. The return values are JSON strings
// Notification: Technology in AOP to solve specific problems
// Features: this exception handling mechanism only intercepts exceptions thrown by the Controller layer
@RestControllerAdvice
public class SystemExe {
/**
* Description: you need to define a method for global exception
* Requirement: returned unified business data SysResult
* Intercept: Specifies that an exception is encountered to implement AOP processing
* Note: do not add try catch in the business method at will
*/
@ExceptionHandler({RuntimeException.class})
public SysResult fail(Exception e){
e.printStackTrace();
return SysResult.fail();
}
}
4 transaction control in spring
4.1 transaction characteristics
- Atomicity: both success and failure (indivisible)
- Isolation: multiple transactions are independent and do not interfere with each other
- Consistency: ensure data consistency (dirty reading / unreal reading / non repeatable reading)
- Persistence: once the transaction is committed, it should be persisted
4.2 default transaction strategy in spring
Note: after Spring integrates Mybatis, the business layer does not support transaction execution. If the business is executed in this way, there must be a problem
//Question: is the data really deleted? A deleted
@Override
public void deleteUserById(Integer id) {
userMapper.deleteUserById(id);
int a = 1/0;
}
4.3 add transaction @ Transactional in spring
/**
* Question: is the data really deleted?????
* Solution: @ Transactional
* effect:
* 1.By default, only runtime exceptions are intercepted
* 2.rollbackFor: Specify the type of exception rollback rollbackFor = RuntimeException.class
* 3.noRollbackFor: Specifies that the exception is not rolled back. noRollbackFor = RuntimeException.class
*/
@Transactional
@Override
public void deleteUserById(Integer id) {
userMapper.deleteUserById(id);
}
5. Automatic data filling function
Requirement Description: if the user needs his own manual operation time every time, the code is relatively cumbersome
Optimization means:
- When adding an operation, the creation time / modification time needs to be filled in the insert
- Operation modification time during update operation
package com.jt.pojo;
import com.baomidou.mybatisplus.annotation.FieldFill;
import com.baomidou.mybatisplus.annotation.TableField;
import lombok.Data;
import lombok.experimental.Accessors;
import java.io.Serializable;
import java.util.Date;
@Data
@Accessors(chain=true)
public class BasePojo implements Serializable{
//Auto fill when adding
@TableField(fill = FieldFill.INSERT)
private Date created;
//Auto fill when adding and modifying
@TableField(fill = FieldFill.INSERT_UPDATE)
private Date updated;
}
Need to add time pojo Inherit this class
6. Agency mechanism
6.1 reverse proxy
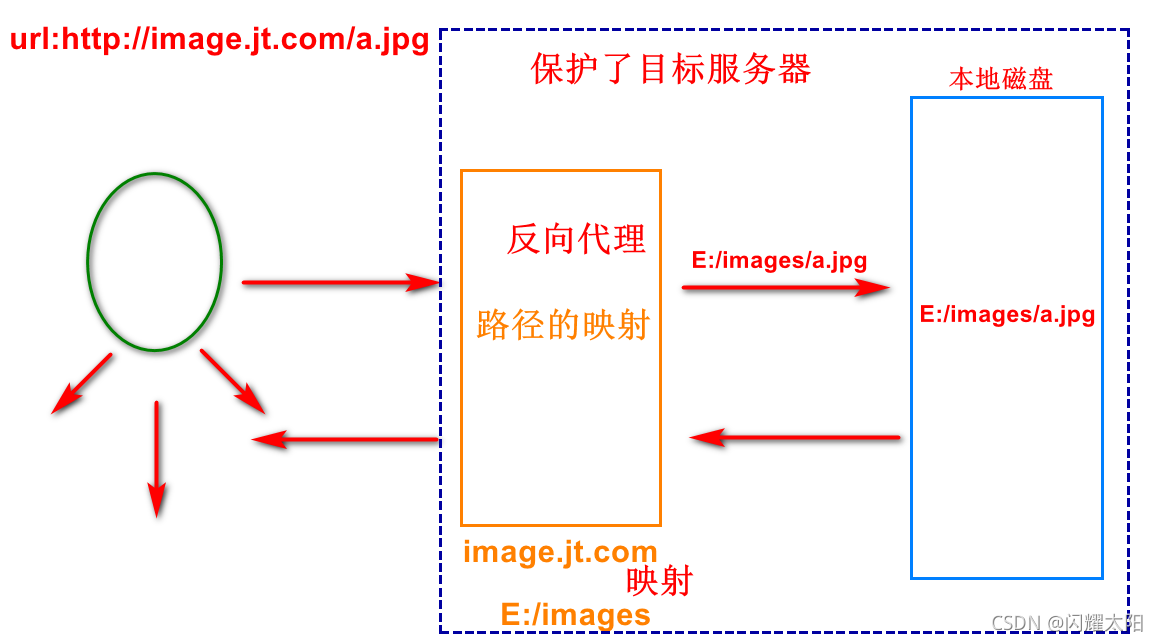
6.1.1 reverse agent concept
The reverse proxy server is located between the user and the target server, but for the user, the reverse proxy server is equivalent to the target server, that is, the user can obtain the resources of the target server by directly accessing the reverse proxy server. At the same time, the user does not need to know the address of the target server or make any settings on the client. The reverse proxy server usually can It is used as Web acceleration, that is, using reverse proxy as the front-end machine of Web server to reduce the load of network and server and improve access efficiency
6.1.2 reverse proxy features
- The proxy server is between the user and the server
- The user thinks that the reverse proxy server is the target server
- Users don't know who the real server is!
- The reverse proxy server protects the information of the target server, so it is also called "server - side proxy"
6.1.3 reverse agency cases
6.2 forward agency
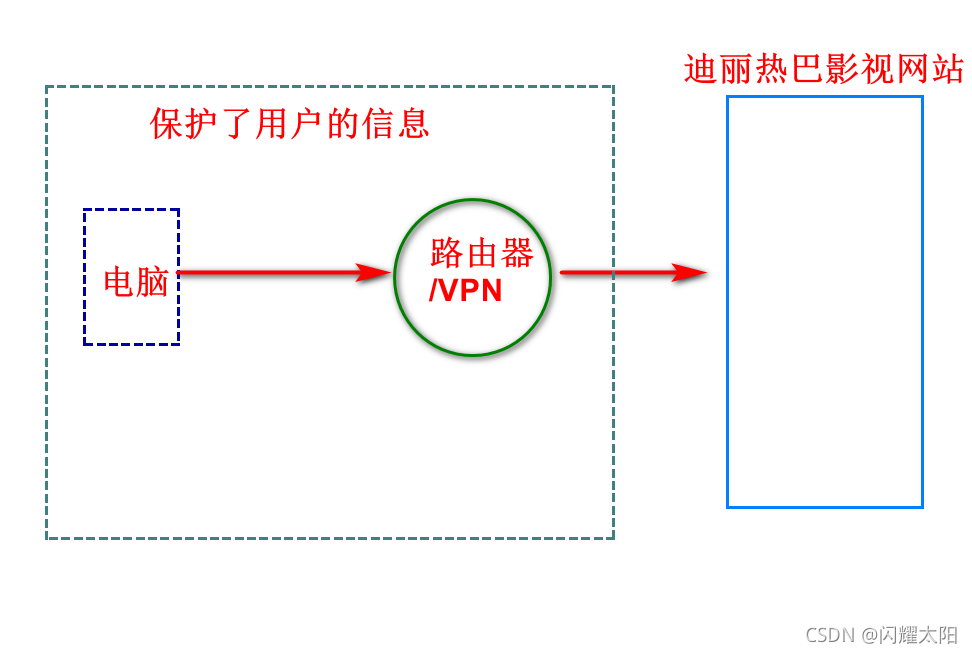
6.2.1 forward agency concept
Forward proxy means a server located between the client and the original server. In order to obtain content from the original server, the client sends a request to the proxy and specifies the target (original server), and then the proxy forwards the request to the original server and returns the obtained content to the client. Only clients can use forward proxy.
6.2.2 characteristics of forward agency
- The forward proxy server is between the user and the server
- The user sends the request to the proxy server and specifies the target server
- The target server thinks it is accessed by a proxy server and protects the user's information, so it is also called "client agent"
6.2.3 forward agency cases
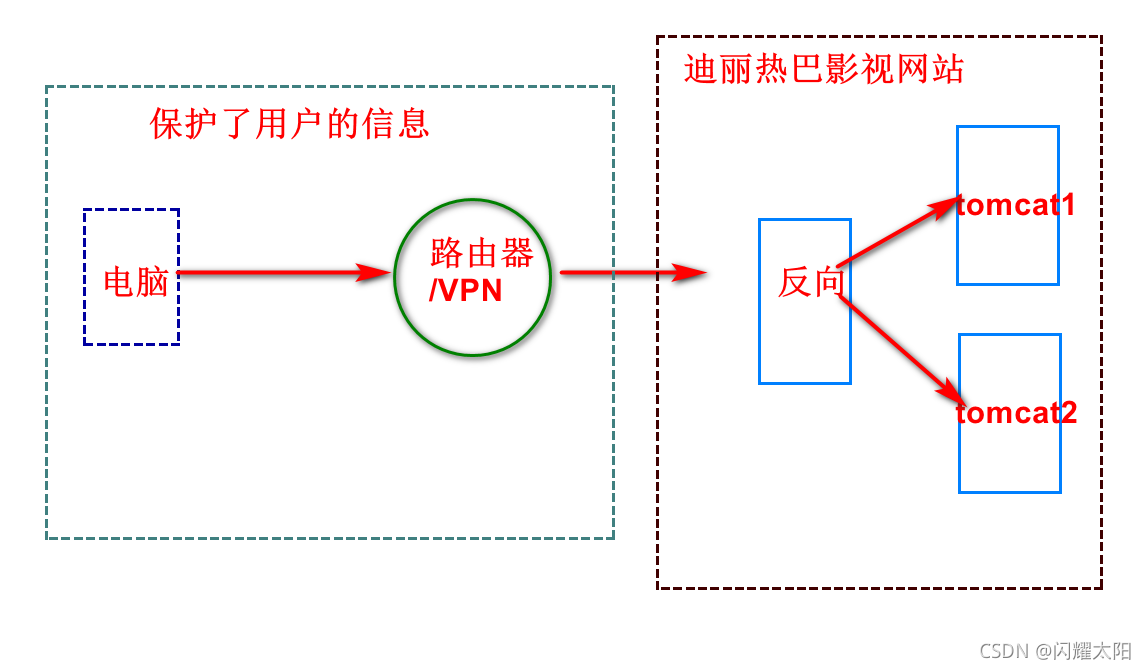
6.3 forward and reverse proxy features
Every request includes forward proxy and reverse proxy mechanism
7 Nginx
Role: reverse proxy to achieve load balancing
7.1 introduction to nginx server
Nginx (engine x) is a high-performance HTTP and reverse proxy web server
Nginx is a lightweight Web server / reverse proxy server and e-mail (IMAP/POP3) proxy server, which is distributed under BSD like protocol. Its characteristics are less memory and concurrent capability. In fact, nginx's concurrent capability is better in the same type of Web server. Chinese mainland users use Baidu website: Baidu, Jingdong, Sina, NetEase, Tencent, Taobao, etc.
7.2 Nginx features
- It occupies less memory, no more than 2m, and the Tomcat server is 200M
- Strong concurrency capacity: 30000-50000 / S; tomcat server: 220-250 / S
- Nginx is the c language and tomcat is the java language
7.3 Nginx Download
7.4 Nginx installation instructions
7.4.1 nginx path description
Path problem:
nginx is developed in c language, so it is not friendly to Chinese. Extra attention should be paid to spaces
Port problem:
1. The running port of nginx is 80. Port 80 cannot be occupied by other services
2. If port 80 is occupied by other services, kill the process with dos command
Occupied port:
The default port number of http protocol is port 80
https protocol default port number 443
7.4.2 nginx process item description
Every time nginx starts, there will be two processes. One is the main process and the other is the daemon process
Main process: it mainly provides reverse proxy service. It occupies a large memory space
Daemon: a process that prevents the main process from shutting down unexpectedly
If nginx needs to be shut down, shut down the daemon first and then the main process
7.4.3 nginx command (key)
Note: the execution of nginx commands needs to be run in the root directory of nginx
- Start: nginx start nginx
- Restart: nginx nginx -s reload
- Close: nginx nginx -s stop
Note: nginx can only be started once. If it is started multiple times, redundant items will be generated, affecting the normal operation of the program