1, Concept
1.1,TLS
Transport Layer Security protocol
As the successor of SSL protocol, it has become the next generation network security and data integrity security protocol
1.2,SSL
Secure Socket Layer
The network transport layer, located in TCP/IP, is a security protocol that provides security and data integrity for network communication
1.3,HTTPS
HTTP+SSL (secure socket layer) / TLS(Transport Layer Security) protocol and HTTPS protocol provide the best application environment for digital certificates
1.4,OpenSSL
It is equivalent to an implementation of SSL. If the SSL specification is regarded as an interface in OO, OpenSSL is regarded as an implementation of the interface. The interface specification itself is safe, but the specific implementation may be imperfect. For example, the previous "bleeding heart" vulnerability is a bug in OpenSSL
1.5,CA
Digital Certification authority
Contains a variety of cryptographic algorithms:
- Message digest algorithm: MD5, and SHA (digest the digital certificate in the province to verify the data integrity server)
- Symmetric encryption algorithm: RC2, RC4, IDEA, DES, AES (encrypt / decrypt data to ensure data confidentiality service)
- Asymmetric encryption algorithm: RSA and DH (encrypt / decrypt data to ensure data confidentiality)
- Digital signature algorithm: RSA, DSA (sign / verify data to ensure data integrity and anti repudiation).
1.6,KEY
Usually refers to the private key
1.7,CSR
The abbreviation of Certificate Signing Request is Certificate Signing Request. This is not a certificate. It can be simply understood as a public key. When generating a certificate, it should be submitted to an authoritative certification authority.
1.8,CRT
Certificate is the abbreviation of certificate.
1.9,X.509
A certificate format. For an X.509 certificate, the authenticator is always the CA or the person designated by the ca. an X.509 certificate is a collection of standard fields that contain information about the user or device and its corresponding public key.
10. 509 certificate file generally ends with. crt. According to the content coding format of the file, it can be divided into the following two formats:
-
PEM - Privacy Enhanced Mail, which starts with "----- BEGIN..." and ends with "----- END..." and contains BASE64 encoding. Apache and * NIX servers prefer this encoding format
-
DER - Distinguished Encoding Rules, which is binary and unreadable when opened. Java and Windows servers prefer this encoding format
2, Certificate issuing process
The certificate tool OpenSSL: win64openssl is used here_ Light-3_ 0_ 0.exe
After installation, enter the installation bin directory and enter the command line operation (or configure environment variables for command line operation)
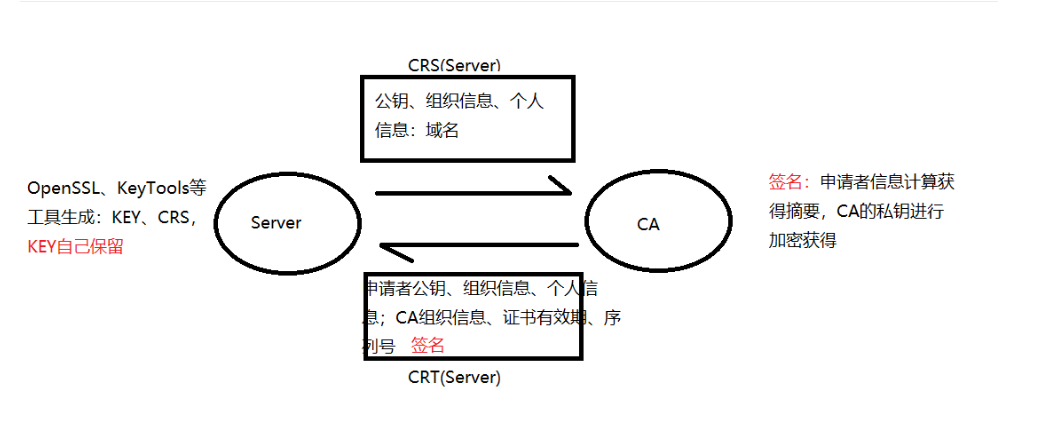
2.1 certificate application process
2.2. The applicant prepares csr and key
- Generate key:
openssl genrsa -out D:\keys\cloudweb.key 4096
- Generate crs
openssl req -new -sha256 -out D:\keys\cloudweb.csr -key D:\keys\cloudweb.key -config ssl.conf
It contains the configuration file ssl.conf
[ req ] default_bits = 4096 distinguished_name = req_distinguished_name req_extensions = req_ext [ req_distinguished_name ] countryName = Country Name (2 letter code) countryName_default = cn stateOrProvinceName = State or Province Name (full name) stateOrProvinceName_default = sc localityName = Locality Name (eg, city) localityName_default = cd organizationName = Organization Name (eg, company) organizationName_default = my organizationalUnitName = Organizational Unit Name (eg, section) organizationalUnitName_default = as commonName = Common Name (e.g. server FQDN or YOUR name) commonName_max = 64 commonName_default = www.baidu.com [ req_ext ] subjectAltName = @alt_names [alt_names] IP.1 = 192.168.11.112 DNS.1 = www.baidu.com DNS.2 = map.baidu.com
3. View crs
openssl req -text -noout -verify -in D:\keys\cloudweb.csr
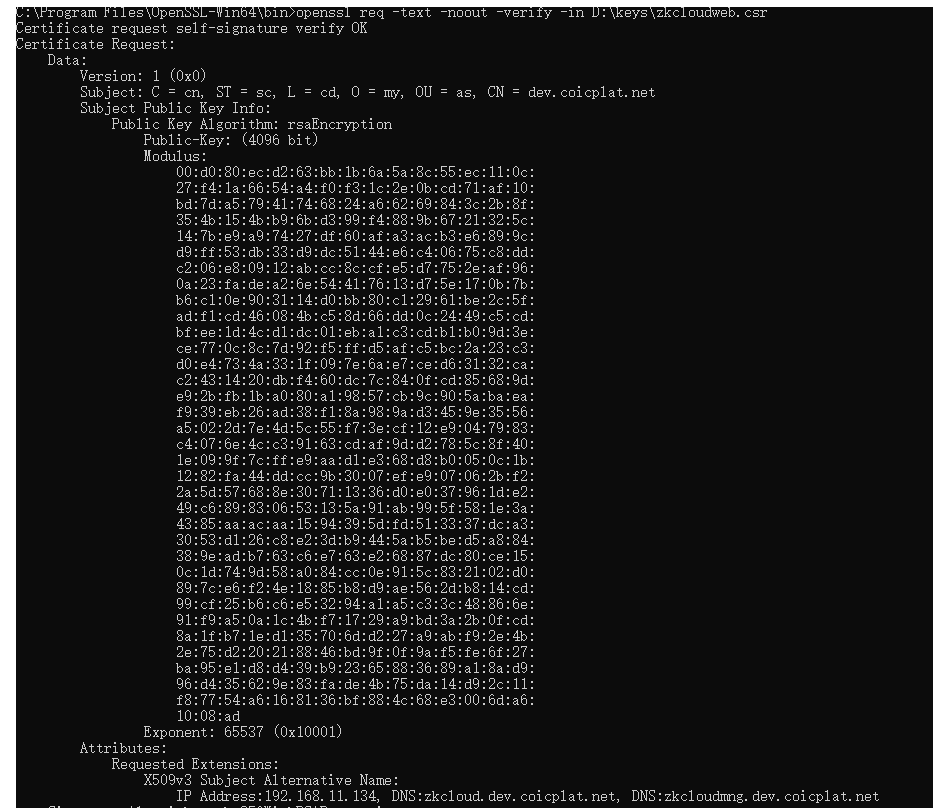
2.3 CA organization generates crt for applicant
CA institution obtains the applicant crs and relevant applications, verifies the applicant's information online and offline, and makes certificates for the applicant.
Signature in certificate: the summary is calculated by using the applicant's public information, and the signature is obtained by encrypting the CA's private key.
- Generate crt
openssl x509 -req -days 3650 -in D:\keys\cloudweb.csr -signkey D:\keys\cagroup.key -out D:\keys\cloudweb.crt -extensions req_ext -extfile cassl.conf
Special note: if cagroup.key is cloudweb.key and cassl.conf is ssl.conf, you will issue a certificate to yourself, that is, a self signed certificate.
- View crt
openssl x509 -in D:\keys\cloudweb.crt -text -noout
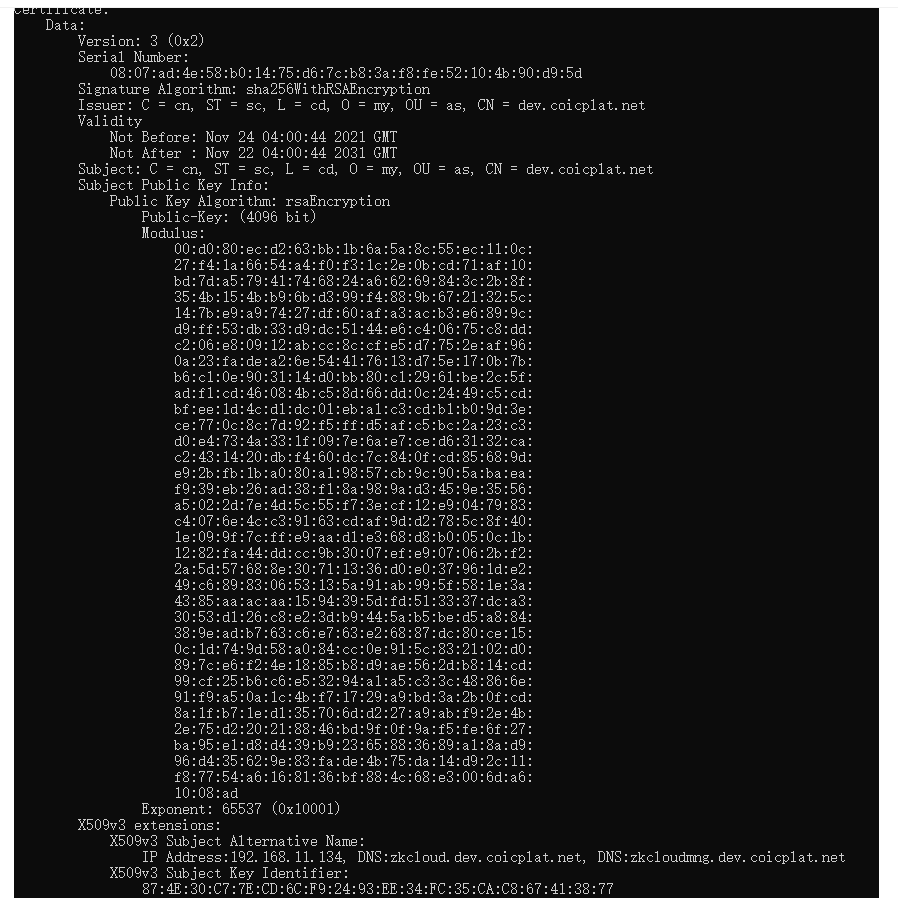
matters needing attention:
- There is no need to provide a private key to apply for a certificate. Ensure that the private key can only be mastered by the server
- . certificate = public key + applicant and issuer information + signature
3, HTTPS request
3.1 one way certificate process
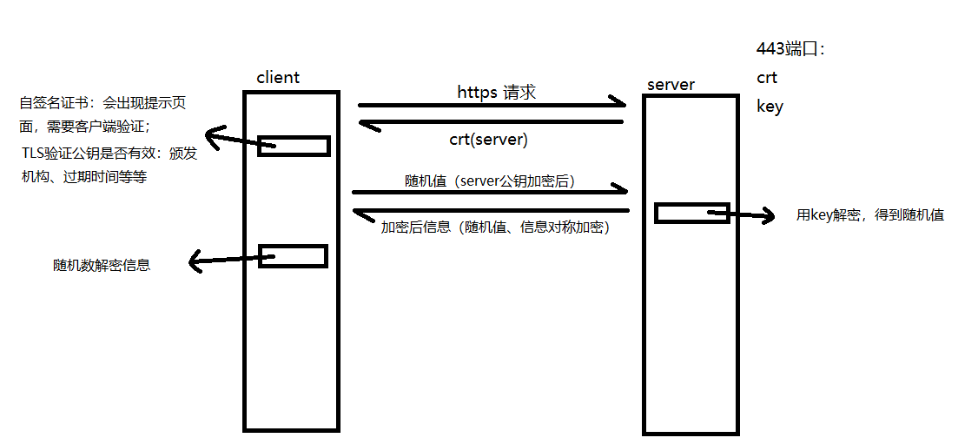
3.2. nginx server configuration
- The server needs to install the SSL module
./configure --prefix=/usr/local/nginx --with-http_stub_status_module --with-http_ssl_module
make
- Modify the nginx.conf configuration file as follows:
server {
listen 443 ssl;
server_name www.myweb.com; #The domain name to be accessed does not need https
ssl on;
ssl_certificate D://keys//myweb.crt; # This is the absolute path where ssl crt files are stored
ssl_certificate_key D://keys//myweb.key; # This is the absolute path where the ssl key file is stored
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://192.168.6.45:8343/; # Jump path
}
}
server {
listen 80;
server_name www.myweb.com;
rewrite ^(.*)$ https://$host$1 permanent;
}
3.3. Tomcat server configuration
Modify the server.xml file and add the following under the Service node:
<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true" clientAuth="true"
sslProtocol="TLS" keystoreFile="D:\keys\myweb.crt"
truststoreFile="D:\keys\myweb.keystore" truststorePass="jsonliu@123" />
Attribute description:
- clientAuth: set whether to two-way authentication. The default value is false. Setting to true means two-way authentication
- keystoreFile: server certificate file path
- truststoreFile: the root certificate used to verify the client certificate. In this case, it is the server certificate
- truststorePass: root certificate password
last:
- To access https requests, you need to access port 8443. To access http requests, you can access the Tomcat default port (the port you set yourself, the default is 8080).
3.4 browser installation CA certificate
If it is a recognized CA organization, the browser generally has installed the certificate. If it is a self signed certificate, you need to manually install the CA certificate to the trusted root certification authority.