ssh command; key authentication; service management in linux
Keywords:
ssh
openssh
Linux
vim
1.openssh
When the openssh service is enabled in the host, the remote connection interface is opened to the public. The service end of openssh service is open to the public, and the remote connection is open to the public
sshd ා server software, open an interface for others to connect through other ways
2. How to connect sshd on the client
ssh server user @ server ip address
For example:
ssh root@172.25.254.138 use ssh command to connect the root user of 172.25.254.138 host on the client
Specific display information:
[kiosk@foundation78 Desktop]$ ssh root@172.25.254.138
The authenticity of host '172.25.254.138 (172.25.254.138)' can't be established.ECDSA key fingerprint is eb:24:0e:07:96:26:b1:04:c2:37:0c:78:2d:bc:b0:08.
Are you sure you want to continue connecting (yes / no)
root@172.25.254.138's password: enter password to connect successfully
Last login: Sun Sep 23 11:35:10 2018 from 172.25.254.78
[root @ desktop ~] "exit" means to exit the current connection logoutConnection to 172.25.254.138 closed
Note: the above connection mode cannot open the graphic function of the remote host. If you need to open the graphic function of the remote host, you need to enter - X
For example:
ssh -X root@172.25.254.138
3. Add a new authentication method to ssh service, KEY authentication
(1) Generate locks and keys
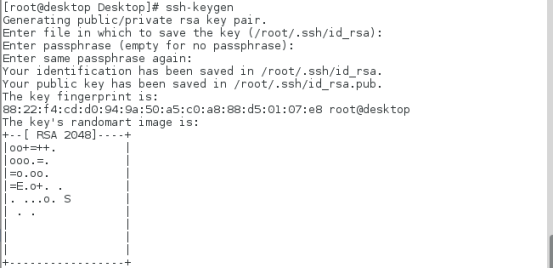
[root @ desktop desktop] ා SSH keygen ා command to generate a key, press enter until the password pattern appears
(2)encryption ssh User authentication
#On the server side
[root@desktop Desktop]# ls /root/.ssh/
authorized_keys id_rsa id_rsa.pub known_h
[root@desktop Desktop]# ssh-copy-id -i /root/.ssh/id_rsa.pub root@172.25.254.138 #Encryption command
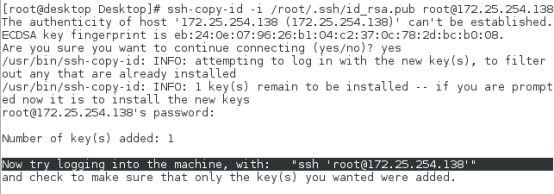
ssh-copy-id # Encryption command
-i # Designated key
/root/.ssh/id_rsa.pub # Key, lock
/root/.ssh/id_rsa # Key
root # Encrypted users
172.25.254.238 # Host ip
(3)Verify (decrypt file transfer to client)
[root@desktop Desktop]# scp /root/.ssh/id_rsa root@172.25.254.238:/root/.ssh/ #No password is required for client connection after executing this command
id_rsa 100% 1679 1.6KB/s 00:00
[root@desktop Desktop]# ssh root@172.25.254.238 # No password required to connect
Last login: Mon Sep 24 08:49:34 2018 from 172.25.254.78
[root@server ~]# logoutConnection to 172.25.254.238 closed.
# Test on client
[root@server Desktop]# ssh root@172.25.254.138
Last login: Mon Sep 24 10:49:16 2018 from 172.25.254.238
[root@desktop ~]# logoutConnection to 172.25.254.138 closed.
# On the server side
[root@desktop Desktop]# rm -fr /root/.ssh/authorized_keys #When this file is deleted, the decryption file of the client is invalid. At this time, the client cannot log in without password
# Test on client:
[root@server Desktop]# ssh root@172.25.254.138
root@172.25.254.138's password:
# On the server side
[root@desktop Desktop]# cp /root/.ssh/id_rsa.pub /root/.ssh/authorized_keys #Regenerate lock file, decrypt file function recovery
# Test on client:
[root@server Desktop]# ssh root@172.25.254.138
Last login: Mon Sep 24 10:53:17 2018 from 172.25.254.238
//Note: first, check whether there is / root/.ssh / directory on the desktop
ls -l /root/
//If not, log in to a virtual machine at will, and now a / root/.ssh / directory has been created
4.sshd Security configuration for
[root@desktop ssh]# pwd
/etc/ssh
[root@desktop ssh]# vim sshd_config
78 PasswordAuthentication no|yes # The default authentication mode to turn on or off ssh
48 PermitRootLogin no|yes # Turn on or off the login permission of root user
79 AllowUsers westos # User white list. Currently, only westos is allowed to log in
80 DenyUsers linux # User blacklist. Currently, only linux is not allowed to log in
//Note: only one white list and one black list can appear
5.linux Service management in
//Format: systemctl Action Service
systemctl start sshd #Opening service
systemctl stop sshd #Out of Service
systemctl status sshd #View service status
systemctl restart sshd #Restart service
systemctl reload sshd #Let service load configuration from New
systemctl enable sshd #Set service startup
systemctl disable sshd #Set the service not to start
systemct list-unit-files #View the startup status of all services in the system
systemctl list-units #View all open services in the system
systemctl set-default graphical.target #Turn on graphics at power on
systemctl set-default multi-user.targe #No graphics on
Posted by ldmccla on Thu, 26 Dec 2019 10:47:17 -0800

