Brief answer
1. Count the number of files under / var/log.
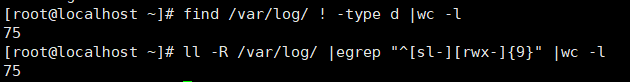
find /var/log/ ! -type d |wc -l
//Or l l - R / var / log / | egrep "^ [SL -] [RWX -] {9}" | WC - L
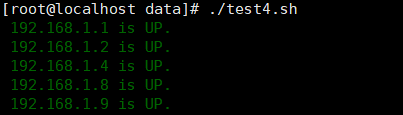
3. Write a script to judge which ip address is currently online in the 192.168.1.0/24 network, and which ip address can be ping ed according to the general rule
#!/bin/bash
#
while true; do
for I in {1..255};do
ping -c 2 -w 2 192.168.1.$I &>/dev/null
if [ $? -eq 0 ]; then
echo -e "\033[32;40m 192.168.1.$I is UP.\033[0m"
fi
done
break
done
4. Based on the following information:
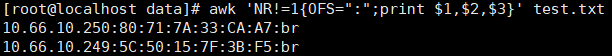
IP_Address MAC_Address Interface Static 10.66.10.250 80:71:7A:33:CA:A7 br on 10.66.10.249 5C:50:15:7F:3B:F5 br on
Add the above file name test.txt IP in file_ Address,MAC_ The contents under address and interface are extracted, and the values are divided by ":" and displayed in format. Note:
10.66.10.250:80:71:7A:33:CA:A7:br
10.66.10.249:5C:50:15:7F:3B:F5:br
awk 'NR!=1{OFS=":";print $1,$2,$3}' test.txt
5. There are four ways to assign variables in the shell, in which name is used= oupeng.com Direct assignment uses the read command to use command line parameters to use command output
Direct assignment
6. Write a script, check the log once in 5 minutes, if there is violent SSH cracking, extract such IP address, de duplicate it, and sort it in descending order.
Requirements: when the same IP is brutally cracked more than 10 times, the IP address will be automatically masked. The designated office IP address (192.168.100.100) is a trusted IP address, which is not limited by the shielding rules. The following is the log format:
May 4 03:43:07 tz-monitor sshd{14003}: Failed password for root from 124.232.135.84 port 25251 ssh2 Myy 4 03:43:07 tz-monitor sshd{14082}: invalid user postgres from 124.232.135.84
vim /server/scripts/fairban.sh
#!/bin/bash
awk '/Failed password/{count[$(NF-3)]++}END{for (ip in count) if(count[ip]>=10){print count[ip],ip}}' /var/log/secure > /tmp/count_ip.txt
while read line
do
IP=$(echo $line |awk '{print $2}')
if [ "$IP" != "192.168.100.100" ];then
if ! grep -w $IP /tmp/drop_ip.txt &> /dev/null;then
iptables -I INPUT -s $IP -j DROP
echo $IP >> /tmp/drop_ip.txt
fi
fi
done < /tmp/count_ip.txt
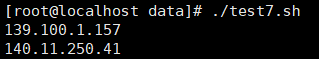
7. To check IP address compliance, write code in shell and list IP addresses that do not start with 199 or 200, such as 199.x.x.x or 200.x.x.x
Address file:
Interface Physical Protocol IP Adderss Eth1/0/1 up up 199.11.250.1 Eth1/0/2 up up 200.11.250.5 Loop0 up up(s) 199.11.250.1 Vlan1 *down down unassigned Vlan500 down down 139.100.1.157 Vlan900 up up 140.11.250.41
#!/bin/bash
while read line
do
isnum=$(echo $line | awk -F "[ .]+" '{print $(NF-3)}')
if [[ $isnum =~ ^[0-9]+$ ]];then
if [ $isnum -ne 199 ] && [ $isnum -ne 200 ];then
echo $line | awk '{print $NF}'
fi
fi
done < /tmp/config.txt
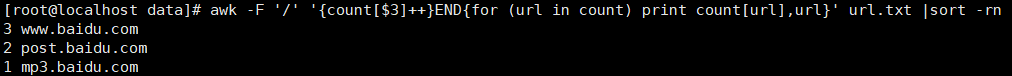
8. Process the following file contents, extract and count the domain name, such as processing:
http://www.baidu.com/index.html http://www.baidu.com/1.html http://post.baidu.com/index.html http://mp3.baidu.com/index.html http://www.baidu.com/3.html http://post.baidu.com/2.html
awk -F '/' '{count[$3]++}END{for (url in count) print count[url],url}' url.txt |sort -rn
9. Under the Linux operating system environment of a single server, write a line of command, and set all the data of the machine as "" log.bak "It is the suffix file. It is packed, compressed and uploaded to FTP. The FTP address is 123.234.25.130 in the / home/bak folder
cd / find -type f -name "*.log.bak" |xargs tar zcf /tmp/all.tar.gz ftp -i -n <<FTPIT open 123.234.25.130 user username_xxx password_xxx bin passive hash cd /home/bak lcd /tmp put all.tar.gz quit FTPIT
10. Linux script: now you want to delete some files in this machine, / root/file.list The absolute path of these files is recorded in. Please implement it with script. /root/file.list Content example / tmp/1.file
#!/bin/bash while read line do rm $line -f done < /root/file.list