Preface
Last article Spring Cloud advanced Road 15: service gateway integrated circuit breaker (zuul + hystrix) In, describes how the service gateway integrates the circuit breaker. However, like other service integrated circuit breakers before, we still can't see the relevant information of circuit breakers intuitively. Therefore, it is necessary to integrate circuit breaker monitoring components to display circuit breaker information in a graphical and friendly way.
Preparation
Reuse previous article Spring Cloud advanced Road 15: service gateway integrated circuit breaker (zuul + hystrix) All projects in: xmall auth, xmall product, xmall zuul.
Transformation of zuul
Add dependency
Just as other services add breaker monitoring components, add spring cloud starter Netflix hystrix dashboard dependencies.
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>com.luas.cloud</groupId>
<artifactId>java-boot-parent-2.1</artifactId>
<version>1.0.0-SNAPSHOT</version>
<relativePath>../../java-boot-parent-2.1</relativePath>
</parent>
<groupId>com.luas.xmall</groupId>
<artifactId>xmall-zuul</artifactId>
<version>1.0.0-SNAPSHOT</version>
<name>xmall-zuul</name>
<description>Gateway service</description>
<properties>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-netflix-zuul</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-openfeign</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-oauth2</artifactId>
</dependency>
<!-- nacos cloud -->
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-nacos-config</artifactId>
</dependency>
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-nacos-discovery</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-netflix-hystrix</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-netflix-hystrix-dashboard</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-configuration-processor</artifactId>
<optional>true</optional>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
<exclusions>
<exclusion>
<groupId>org.junit.vintage</groupId>
<artifactId>junit-vintage-engine</artifactId>
</exclusion>
</exclusions>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
Open circuit breaker monitoring
Add @ EnableHystrixDashboard annotation to the startup class.
package com.luas.xmall.gateway;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.cloud.client.circuitbreaker.EnableCircuitBreaker;
import org.springframework.cloud.netflix.hystrix.dashboard.EnableHystrixDashboard;
import org.springframework.cloud.netflix.zuul.EnableZuulProxy;
import org.springframework.cloud.openfeign.EnableFeignClients;
@EnableHystrixDashboard
@EnableFeignClients
@EnableCircuitBreaker
@EnableZuulProxy
@SpringBootApplication
public class XmallZuulApplication {
public static void main(String[] args) {
SpringApplication.run(XmallZuulApplication.class, args);
}
}
To configure
Modify zuul hystrix's default isolation policy to thread.
zuul:
prefix: /gateway
sensitive-headers:
routes:
auth:
path: /auth/**
service-id: xmall-auth
strip-prefix: true
product:
path: /product/**
service-id: xmall-product
strip-prefix: true
ribbon-isolation-strategy: threadRelease the hystrix.stream endpoint
management:
endpoints:
web:
exposure:
include: '*'The complete application.yml file is as follows.
server:
port: 5566
zuul:
prefix: /gateway
sensitive-headers:
routes:
auth:
path: /auth/**
service-id: xmall-auth
strip-prefix: true
product:
path: /product/**
service-id: xmall-product
strip-prefix: true
ribbon-isolation-strategy: thread
security:
oauth2:
resource:
user-info-uri: http://localhost:7777/oauth/user
prefer-token-info: false
feign:
hystrix:
enabled: true
management:
endpoints:
web:
exposure:
include: '*'
Resource server security policy
Modify the security policy of resource server and release the endpoint related to hystrix monitoring.
package com.luas.xmall.gateway.configuration;
import com.luas.xmall.gateway.oauth2.endpoint.AuthorizationServerEndpoints;
import org.apache.commons.lang3.StringUtils;
import org.springframework.cloud.netflix.zuul.filters.ZuulProperties;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableResourceServer;
import org.springframework.security.oauth2.config.annotation.web.configuration.ResourceServerConfigurerAdapter;
@Configuration
@EnableResourceServer
public class ResourceServerConfiguration extends ResourceServerConfigurerAdapter {
private String prefixAntPattern;
public ResourceServerConfiguration(ZuulProperties zuulProperties) {
this.prefixAntPattern = StringUtils.isBlank(zuulProperties.getPrefix()) ? "/*" : zuulProperties.getPrefix() + "/*";
}
@Override
public void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers(this.prefixAntPattern + AuthorizationServerEndpoints.TOKEN_ENDPOINT).permitAll()
.antMatchers(this.prefixAntPattern + AuthorizationServerEndpoints.TOKEN_KEY_ENDPOINT).permitAll()
.antMatchers(this.prefixAntPattern + AuthorizationServerEndpoints.CHECK_TOKEN_ENDPOINT).permitAll()
.antMatchers("/favicon.ico").permitAll()
.antMatchers("/proxy.stream").permitAll()
.antMatchers("/hystrix.stream").permitAll()
.antMatchers("/actuator/**").permitAll()
.antMatchers("/webjars/**").permitAll()
.antMatchers("/hystrix/**").permitAll()
.anyRequest().authenticated()
;
}
}/favicon.ico, / proxy.stream, / hystrix.stream, / Actor / * *, / hystrix / * *, / webjars / *, and other endpoints must be open as public endpoints, otherwise, the circuit breaker monitoring interface will not display normally and will be blocked by Spring Security.
Verification
Start xmall product, xmall auth, and xmall zuul projects successively, with ports of 8080, 7777, and 5566 respectively.
Apply for authorization.
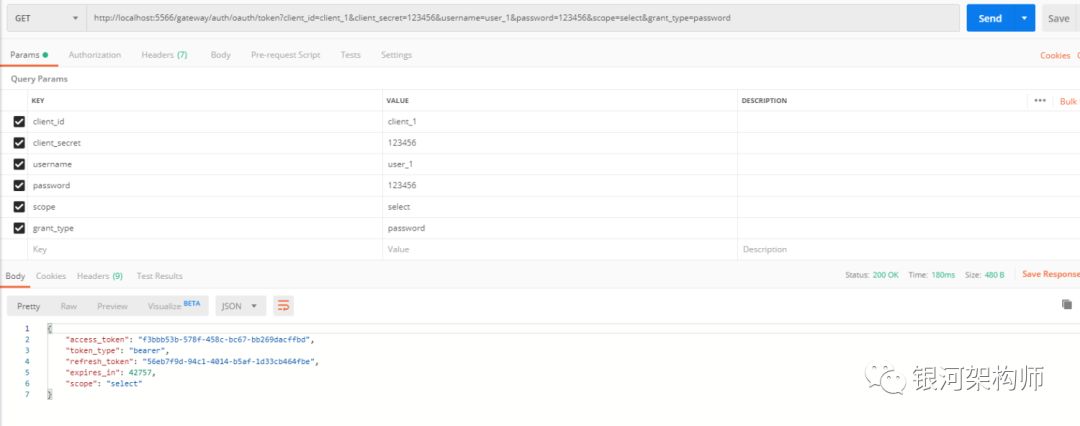
Visit http://localhost: 5566/actor/hystrix.stream. As expected, it must be ping all the time.
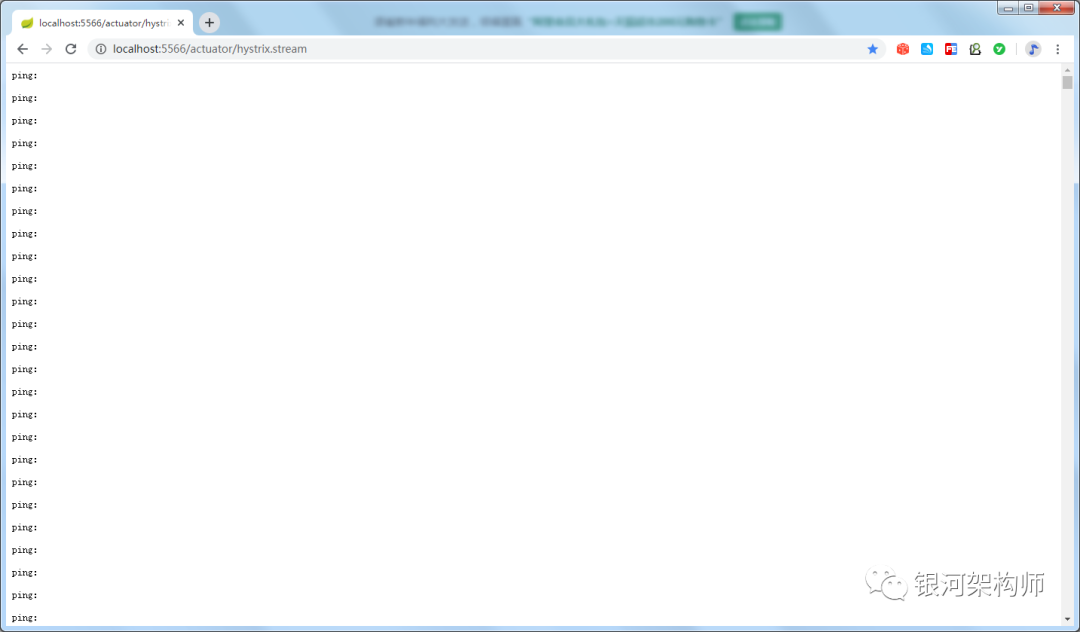
At the same time, accessing the hystrix monitoring interface must be in the loading state. Next, access the relevant interface to generate monitoring data.
Use the authorization applied in the previous step to access the sku interface http://localhost:5566/gateway/product/sku/1122.
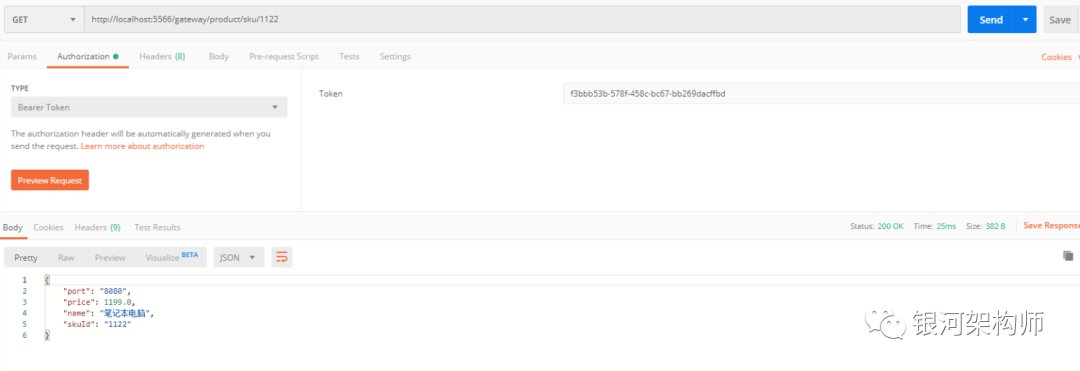
At this point, hystrix.stream already has data returned.
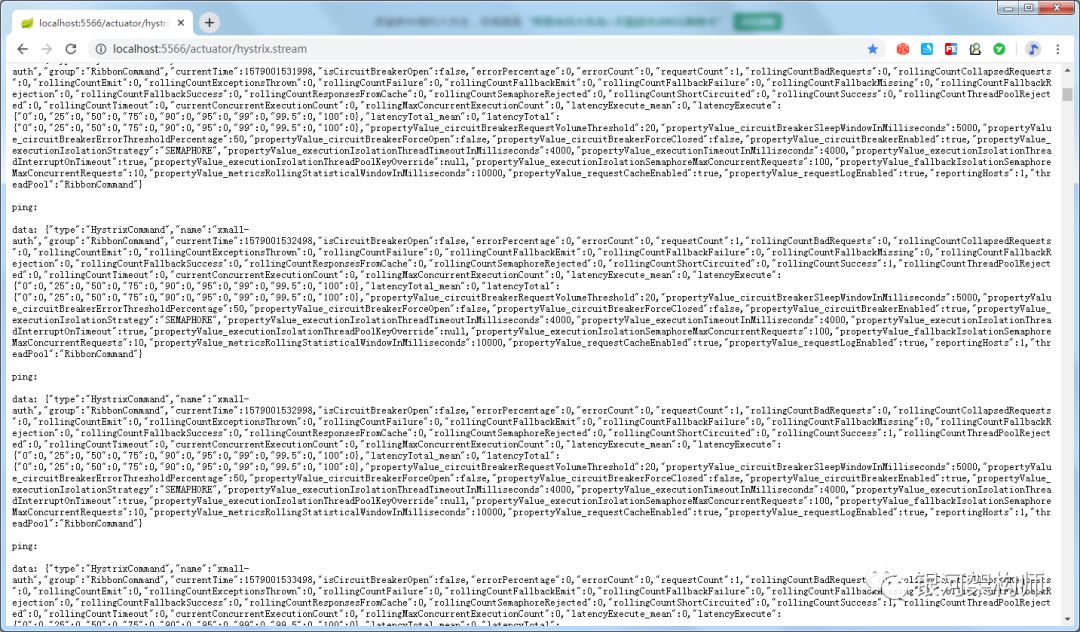
At the same time, the graphic display of hystrix monitoring page is normal.
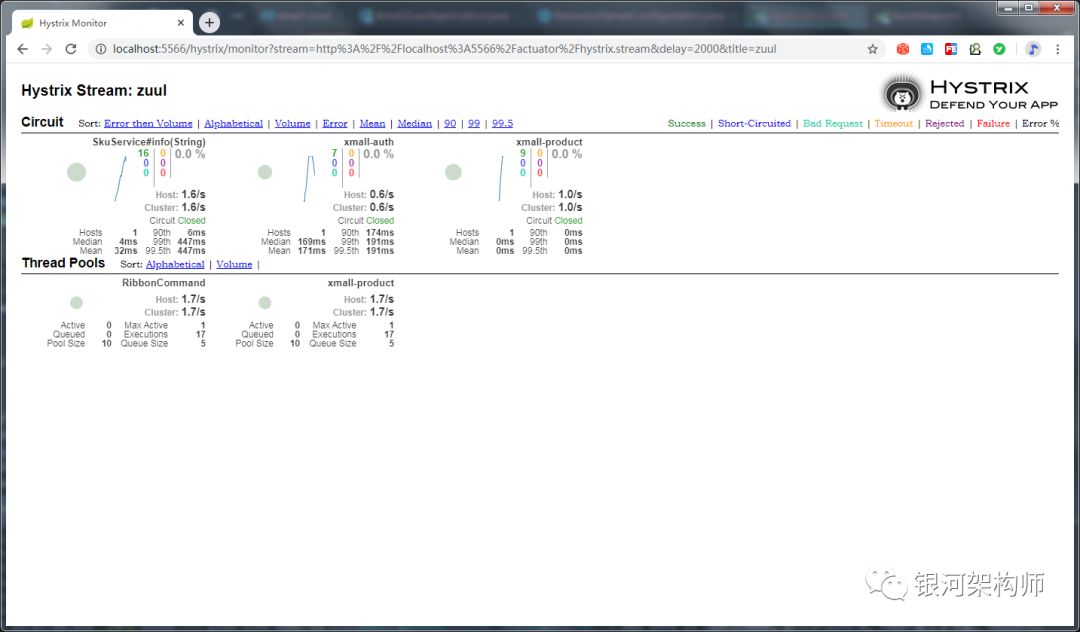
Among them, RibbonCommand is the thread pool name, which is created by zuul's default hystrix, which corresponds to the modification of zuul hystrix isolation policy to thread in the previous configuration item. As for xmall product, it is the default thread pool created by hystrix, which generates data through the remote call of feign client.
problem
If there is no remote call logic in the gateway project, such as rest + ribbon, or feign, at this time, the hystrix monitoring interface does not display the thread pool information, but has been in the loading state, as shown in the figure.
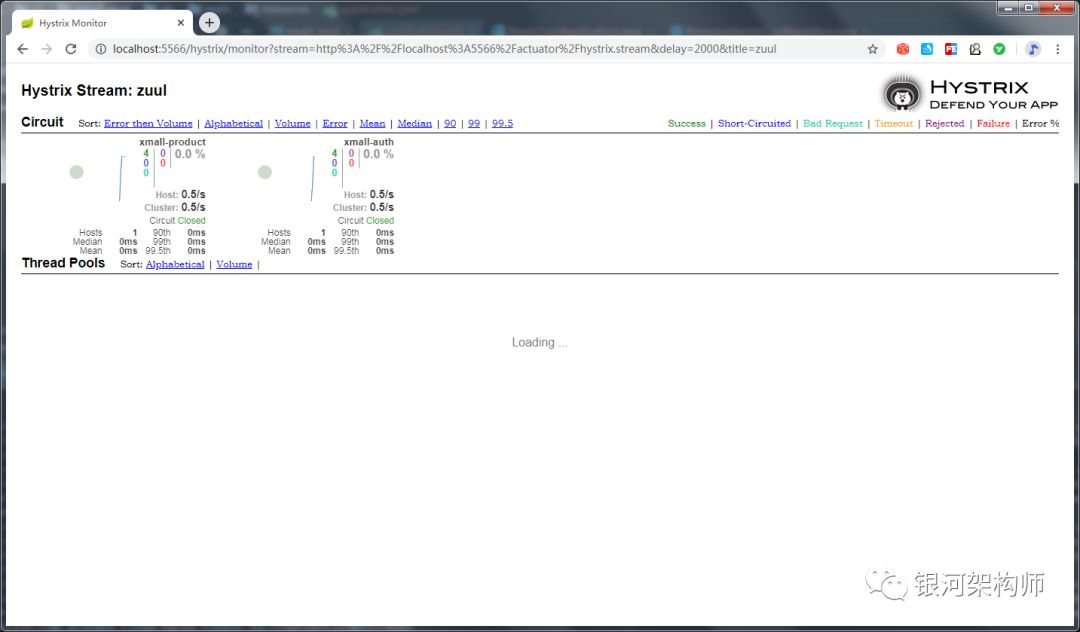
The reason for this is that zuul hystrix's default isolation policy is semaphore, not thread.
If there is remote call logic in the gateway project, no matter rest + ribbon or feign, the hystrix monitoring interface does not display the situation. In addition to the above reasons for the absence of remote call logic, there may be the problem of the default isolation strategy of hystrix. The default isolation policy of hystrix is thread. If it is configured as semaphore, the thread pool of the remote call part will not be created.
hystrix:
command:
default:
execution:
isolation:
strategy: THREAD
You can also configure isolation policies for a service separately.
hystrix:
command:
default:
execution:
isolation:
strategy: THREAD
xmall-product:
execution:
isolation:
strategy: SEMAPHORE
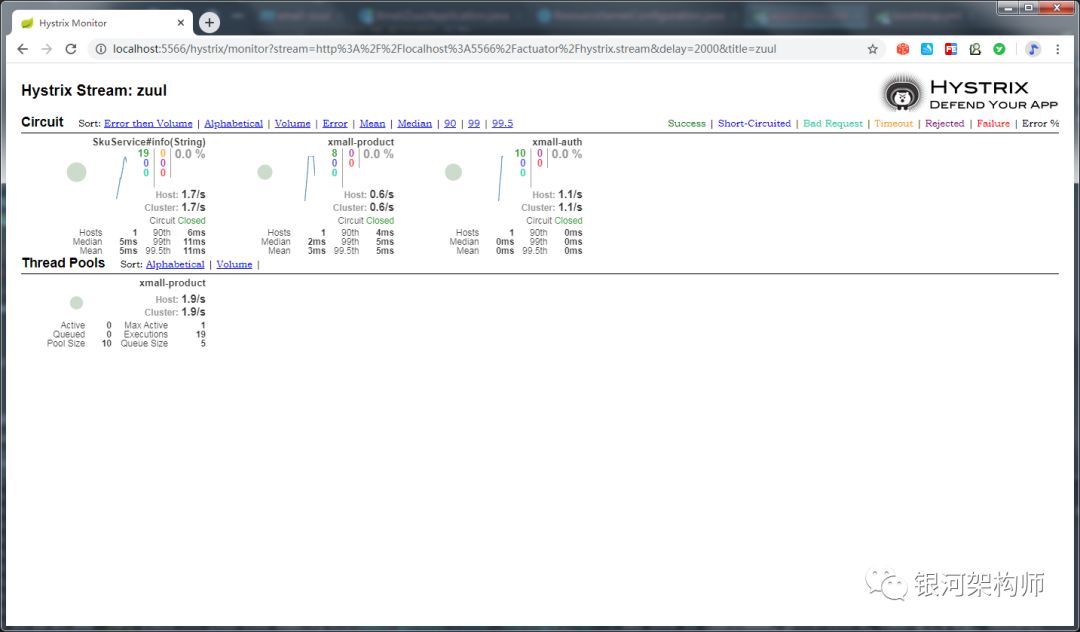
As shown in the following figure, the reason is that zuul hystrix's default isolation policy is not configured as thread, while hystrix's default isolation policy is thread.
As shown in the following figure, the reason is that the default isolation policy of zuul hystrix is thread, while the default isolation policy of hystrix is SEMAPHORE.
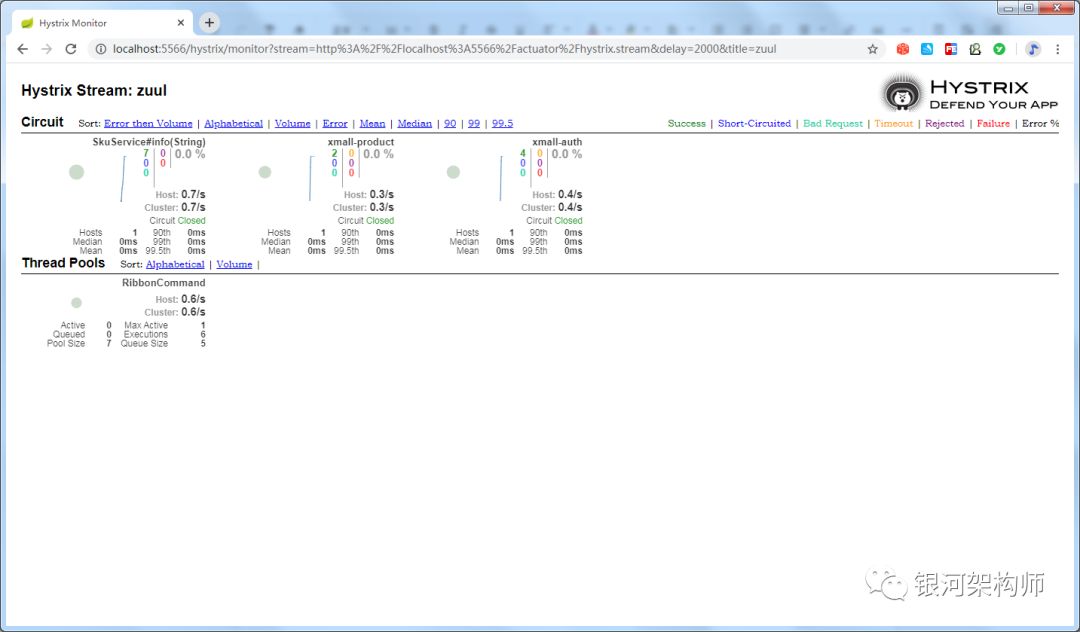
In the above two exceptions, feign remote call exists in the project.
Source code
github
https://github.com/liuminglei/SpringCloudLearning/tree/master/16/
gitee
https://gitee.com/xbd521/SpringCloudLearning/tree/master/16/
This article is the original of Galaxy architect. If you need to reprint it, please indicate the author and source clearly in the article.
Wechat search [Galaxy architect] to find more exciting content.


