What is SELinux
selinux(security enhanced linux) is a security enhanced linux system. It is not only a linux kernel module, but also a security subsystem of linux.
Role of SELinux
The main function of selinux is to minimize the resources accessible by the service process in the system (the principle of minimum permission)
SELinux's permission management mechanism
DAC (autonomous access control)
In the operating system without SELinux, the factor that determines whether a resource can be accessed is whether a resource has the permissions (read, write, execute) of the corresponding user.
As long as the process accessing this resource meets the above conditions, it can be accessed.
The most fatal problem is that the root user is not subject to any control, and any resources on the system can be accessed unrestricted.
The main body of this authority management mechanism is the user
MAC (mandatory access control)
In the operating system using SELinux, in addition to the above factors, it is also necessary to judge whether each type of process has access to a certain type of resources.
In this way, even if the process is running as root, you need to judge the type of the process and the type of resources allowed to access before deciding whether to allow access to a resource. The active space of the process can also be compressed to a minimum.
Http root
Even the service process running as root can only access the resources it needs. Even if the program has a vulnerability, the scope of impact is only within the range of resources it allows access to. The security is greatly increased.
The main body of this permission management mechanism is the process
MAC is divided into two ways
- Category safety (MCS) mode
- Multilevel security (MLS) mode
Operating mode of SELinux
The change mode is set in / etc/selinux/config, and the restart can take effect
If you only need to change permission and enforceing, you only need to use the command setenforce0 or 1
- enforcing
In forced mode, violations of SELinux rules will be blocked and logged - permissive
In tolerant mode, violations of SELinux rules will only be recorded in the log. It is generally used for commissioning. - disabled
Close SELinux.
Basic concept of SELinux (process file label matches target file label)
Subject
Can be completely equivalent to a process.
Note: for the convenience of understanding, unless otherwise specified, the process is regarded as the main body below.
Object
The resource accessed by the principal. It can be files, directories, ports, devices, etc.
Note: for ease of understanding, unless otherwise specified, the following documents or directories are regarded as objects.
Policy & rule
There are usually a large number of files and processes in the system. In order to save time and cost, we usually only selectively regulate some processes.
What processes need to be regulated and how to regulate them are determined by policy.
There are multiple rules in a set of policies. Some rules can be enabled or disabled as required (hereinafter, this type of rule is called Boolean rule).
Rules are modular and extensible. When installing a new application, the application can add rules by adding new modules. Users can also add or delete rules manually.
In redhat 7 system, there are three sets of policies:
- targeted: regulate most network service processes. This is the default policy used by the system (this policy is used below).
- minimum: Based on targeted, it only controls the selected network service process. Generally not.
- mls: multilevel security protection. Control all processes. This is the most stringent policy, and the configuration is very difficult. Generally not, unless there are high requirements for safety.
The policy can be set in / etc/selinux/config.
Security Context
Security context is the core of SELinux.
Security context is divided into:
- Process security context
- File security context
A process security context generally corresponds to multiple file security contexts.
Only when the security context of the two corresponds, the process can access the file. Their correspondence is determined by the rules in the policy.
The file security context is determined by the location where the file is created and the process in which the file is created. Moreover, the system has a set of default values, which can also be set by the user.
It should be noted that simply moving a file does not change the security context of the file.
Structure and meaning of security context
The security context has four fields separated by colons. Form: system_u:object_r:admin_home_t:s0.
Detailed explanation of common commands and SELinux statements
SELINUX configuration file
/etc/selinux/config
#View level
[root@web ~]# getenforce
#Switch levels using the command line
setenforce 0
setenforce 1
#Modification level
#Edit / etc/selinux/config directly
SELINUX=enforcing
#After modification, restart to take effect
#Viewing selinux status
[root@web ~]# sestatus
#View selinux values
[root@web ~]# ll -Z
#View the change of context value
[root@web ~]# touch 1
[root@web ~]# cp 1 /tmp
[root@web ~]# ll -Z /tmp
#The context value of the file will change with the role of the directory and the environment. This value will inherit the context value ll -Z of the previous directory
system_u:object_r:admin_home_t:s0
User identity: role: type (label): security level
This statement is divided into four sections by: the first section is system_u represents the user, and the second paragraph is object_r represents the role. The third paragraph is the most important information in SELinux, admin_home indicates the type. The last paragraph s0 is related to MLS and MCS. It doesn't need to be managed for the time being
①system_u refers to the SElinux user, root refers to the root account identity, user_u means ordinary user, unprivileged user, system_u indicates the system user. The user can confirm the identity type. It is generally used with roles. Identity and different roles have different permissions. Although the su command can be used to switch users, it has not changed for SElinux users. This user identity remains unchanged during account switching. In the targeted policy environment, user identity has no substantive effect.
②object_r is generally the role and system of the file directory_ R is generally the role of the process. In the targeted policy environment, the role of the user is generally system_r. User roles are similar to the concept of user groups. Different roles have different identity permissions. A user can have multiple roles, but only one role can be used at the same time. In the targeted policy environment, the role has no substantive role. In the targeted policy environment, the role of all process files is system_r role.
③admin_ Both home files and processes have a type. SElinux restricts access permissions according to the relevant combination of types
In the Touch /.autorelabel system, selinux is enabled by default to read a file, and he has to read whether there is content in the file. After reading, it will set the security value for these system default files
#Modify the context value, so if you don't take this step, the system can't take this step, so the system won't start normally
④s0 mls
Change the label value of the file
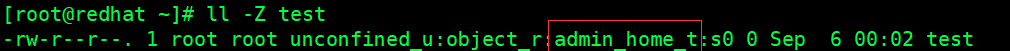
Create a new file test in the home directory
[root@redhat ~]# touch test
View label values
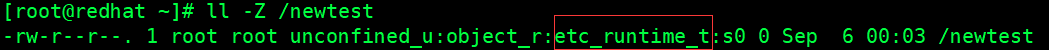
Create a file newtest in the root directory
[root@redhat ~]# touch /newtest
View label values
Method 1:
Using the chcon command
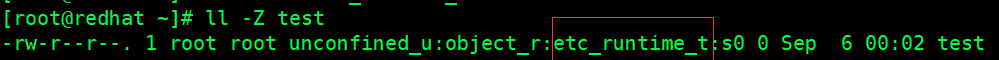
Now change the label value of the home directory file to the label value of the root directory file
[root@redhat ~]# chcon -t etc_runtime_t test
Check whether the change is successful
If you want to reply to the previous tag value
[root@redhat ~]# restorecon -v test Relabeled /root/test from unconfined_u:object_r:etc_runtime_t:s0 to unconfined_u:object_r:admin_home_t:s0 [root@redhat ~]# ll -Z test -rw-r--r--. 1 root root unconfined_u:object_r:admin_home_t:s0 0 Sep 6 00:02 test
Method 2:
Using the semanage command
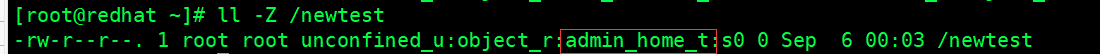
Change the value of the newtest tag of the root directory to admin_home_t
[root@redhat ~]# semanage fcontext -a -t admin_home_t /newtest
see
At this time, only the default value is modified, which has not yet taken effect
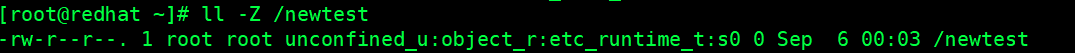
Execute restorecon
[root@redhat ~]# restorecon -v /newtest Relabeled /newtest from unconfined_u:object_r:etc_runtime_t:s0 to unconfined_u:object_r:admin_home_t:s0
see
How to access custom web services when SELinux is turned on
New web service directory
[root@redhat ~]# mkdir -p /www/openlab
Add page information accessed
[root@redhat ~]# echo this is openlab > /www/openlab/index.html
to configure
[root@redhat ~]# vim /etc/httpd/conf.d/vhost.conf
//Add as follows
<VirtualHost 192.168.159.128:80>
DocumentRoot /www/openlab
ServerName 192.168.159.128
</VirtualHost>
<Directory /www>
AllowOverride none
Require all granted
</Directory>
Restart the service and turn off the firewall
[root@redhat ~]# systemctl restart httpd [root@redhat ~]# systemctl stop firewalld
View current selinux status
[root@redhat ~]# getenforce Enforcing //Enforcement ----- on status
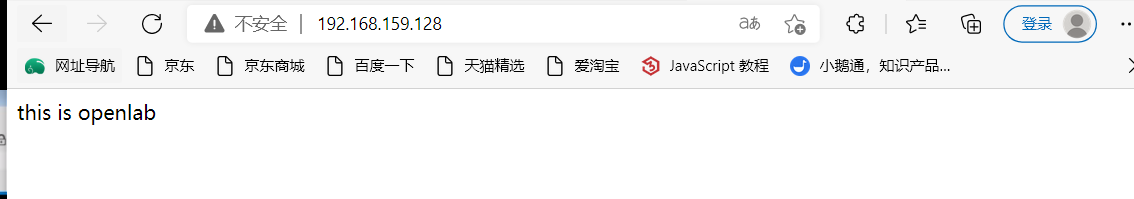
visit
[root@redhat ~]# curl http://192.168.159.128
This is the welcome interface, and we did not successfully access the customized resource file information

Modify the currently customized resource file label value
View the tag value of the resource file accessed by the default web service
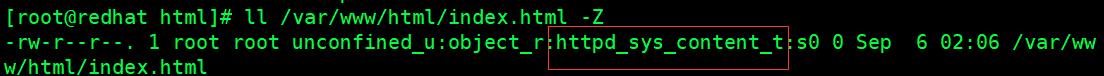
Modify the label value of the current custom resource file
[root@redhat html]# chcon -t httpd_sys_content_t /www/openlab/index.html [root@redhat html]# ll -Z /www/openlab/index.html -rw-r--r--. 1 root root unconfined_u:object_r:httpd_sys_content_t:s0 16 Sep 6 01:30 /www/openlab/index.html
see
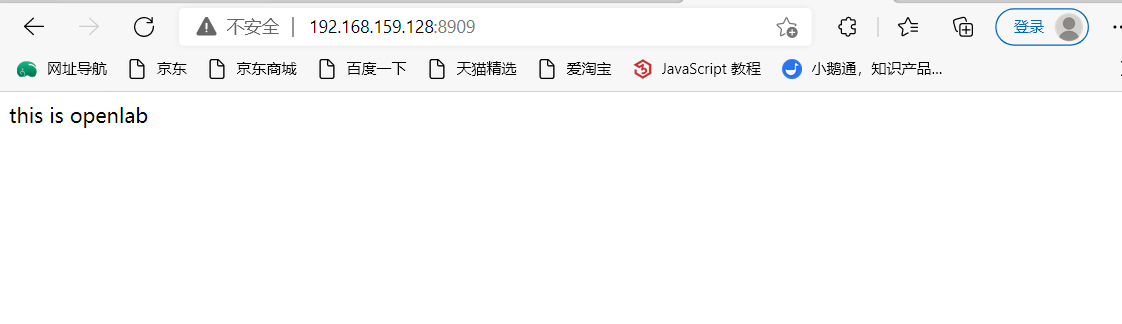
Access the custom port of the web service when seLinux is turned on
Modify and configure custom ports and listen
[root@redhat html]# vim /etc/httpd/conf.d/vhost.conf
LISTEN 8909 //monitor
<VirtualHost 192.168.159.128:8909> //Custom port
DocumentRoot /www/openlab
ServerName 192.168.159.128
</VirtualHost>
<Directory /www>
AllowOverride none
Require all granted
</Directory>
Restart service
Error report found
[root@redhat html]# systemctl restart httpd Job for httpd.service failed because the control process exited with error code. See "systemctl status httpd.service" and "journalctl -xe" for details.
View reason
[root@redhat html]# systemctl status httpd Cannot open this port Sep 06 02:18:31 redhat httpd[5987]: (13)Permission denied: AH00072: make_sock: could not bind to address [::]:8909 Sep 06 02:18:31 redhat httpd[5987]: (13)Permission denied: AH00072: make_sock: could not bind to address 0.0.0.0:8909
View the tag value of the web service port
[root@redhat ~]# semanage port -l | grep -w 80 http_port_t tcp 80, 81, 443, 488, 8008, 8009, 8443, 9000
Modify the port type that your web service is currently accessing
[root@redhat html]# semanage port -a -t http_port_t -p tcp 8909 [root@redhat html]# semanage port -l | grep -w 8909 http_port_t tcp 8909, 8090, 80, 81, 443, 488, 8008, 8009, 8443, 9000
Restart service
[root@redhat html]# systemctl restart httpd
Access the test through the specified port