1, Openssh features
1. Purpose of sshd service
- effect:
You can open the secure shell in the remote host through the network
Secure shell > > > SSH ## client
Secure shell daemon > > > sshd ## server
2. Installation package
openssh-server
3. Master profile
/etc/ssh/sshd_conf
4. Default port
port 22
5. Client commands
ssh
2, ssh
1. Basic usage
ssh [-l remote host user] < ip|hostname >
ssh -l root 172.25.254.72 ##Open the remote shell as root in the 72 host through ssh command First connection or deletion/root/.ssh/The following occurs [lee@westos_lee ~]$ ssh -l root 172.25.254.105 The authenticity of host '172.25.254.105 (172.25.254.105)' can't be established. ECDSA key fingerprint is SHA256:1uLJ3EuYzt16BrtDrGdbjOY6wxCZcfppTLSwTI3BuCs. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes ##Identification generation process confirmation
#Function:
-
When yes is received, the 72 host will send the identity public key to the current host and save the public key to / root/.ssh/know_hosts,72 the host holds the private key. When the client connects again, it will authenticate the client
-
If the authentication changes, the effect of rejecting the connection is as follows:
[lee@westos_lee ~]$ ssh -l root 172.25.254.72 @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that a host key has just been changed. The fingerprint for the ECDSA key sent by the remote host is SHA256:1uLJ3EuYzt16BrtDrGdbjOY6wxCZcfppTLSwTI3BuCs. Please contact your system administrator. Add correct host key in /home/lee/.ssh/known_hosts to get rid of this message. Offending ECDSA key in /home/lee/.ssh/known_hosts:1 ECDSA host key for 172.25.254.72 has changed and you have requested strict checking. Host key verification failed.
#Solution when connection is rejected due to authentication problem
vim ~/.ssh/know_hosts ## delete the corresponding line of error prompt in this file
2. ssh common parameters
| parameter | effect |
|---|---|
| -l | Specify login user |
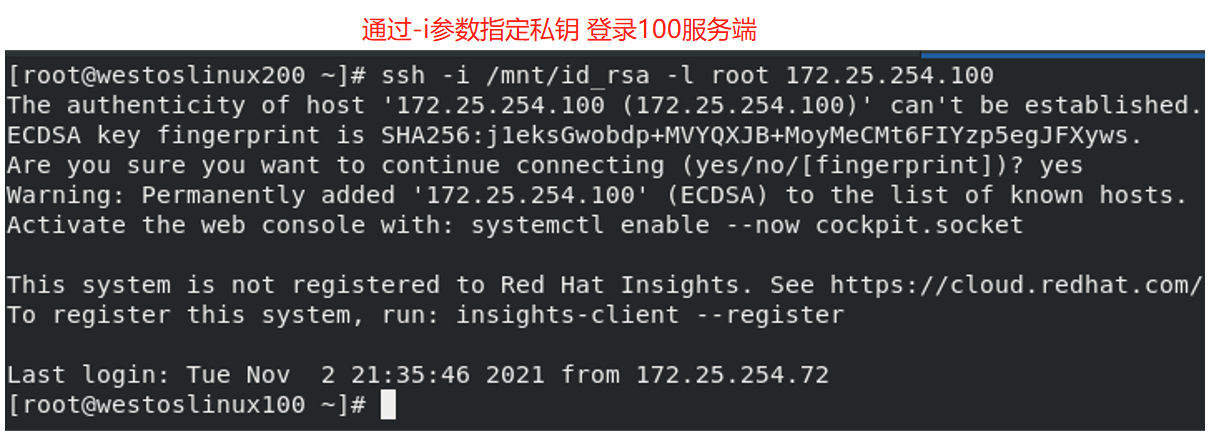
| -i | Specify private key |
| -X | Get the opening permission of the graphics software of the server |
| -f | Background operation |
| -0 | Specify connection parameters |
| -t | Specify connection springboard |
-l this parameter is already familiar
-i will be used below
Look at the - o and - t parameters
ssh -l root 172.25.254.100 -o "StrictHostKeyChecking=no" No input is required for the first connection yes ssh -l root 172.25.254.72 -t ssh -l root 172.25.254.100 Specify the connection springboard as 100 hosts
3, sshd key authentication
1. Type of certification
1) Symmetric encryption
Encryption and decryption are the same string of characters
Easy to leak
Brute force cracking
Easy to forget
2) Asymmetric encryption
Public key for encryption and private key for decryption
Will not be stolen
An attacker cannot log on to the server without a key
2. Generate asymmetric encryption key
Delete / root/.ssh / before doing the experiment
The experiment uses two virtual machines, westosa and westosb
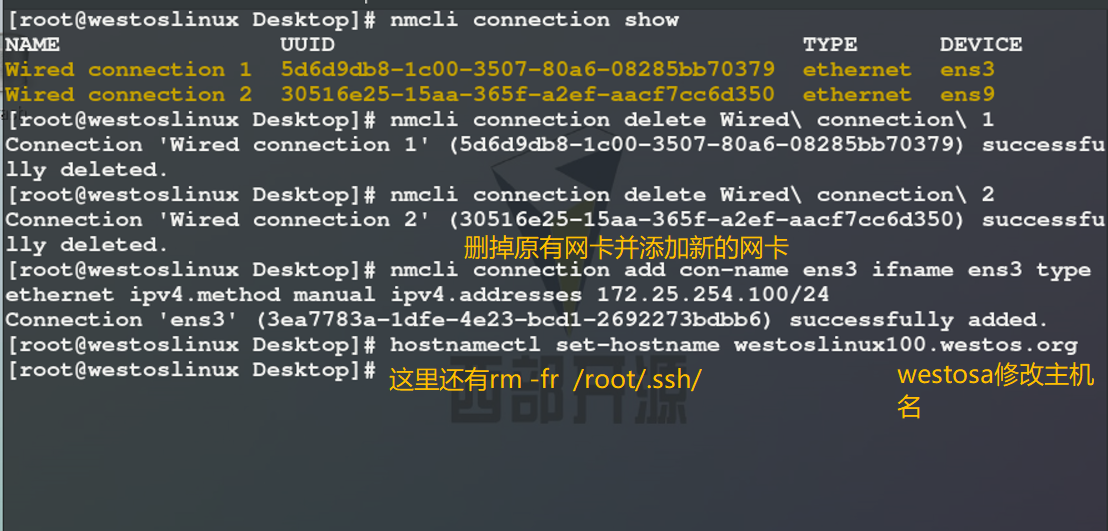
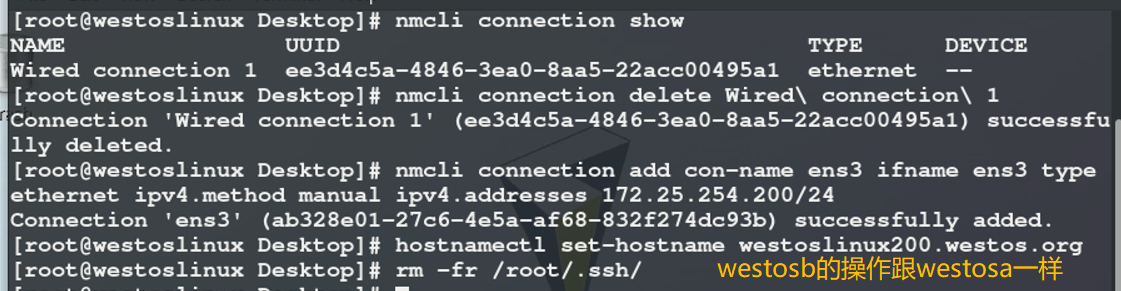
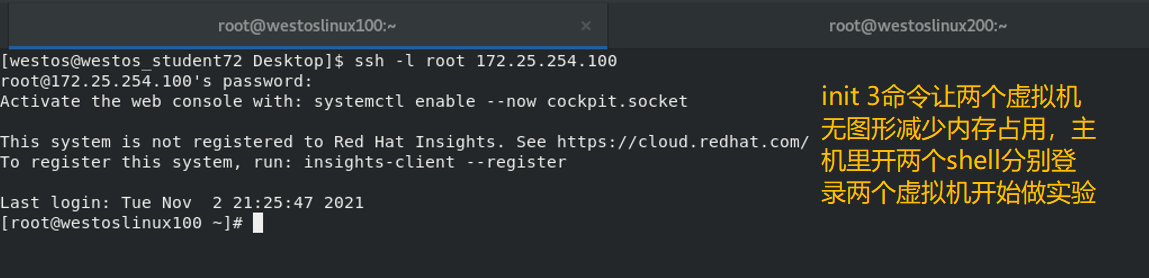
1) Interactive generation
ssh-keygen
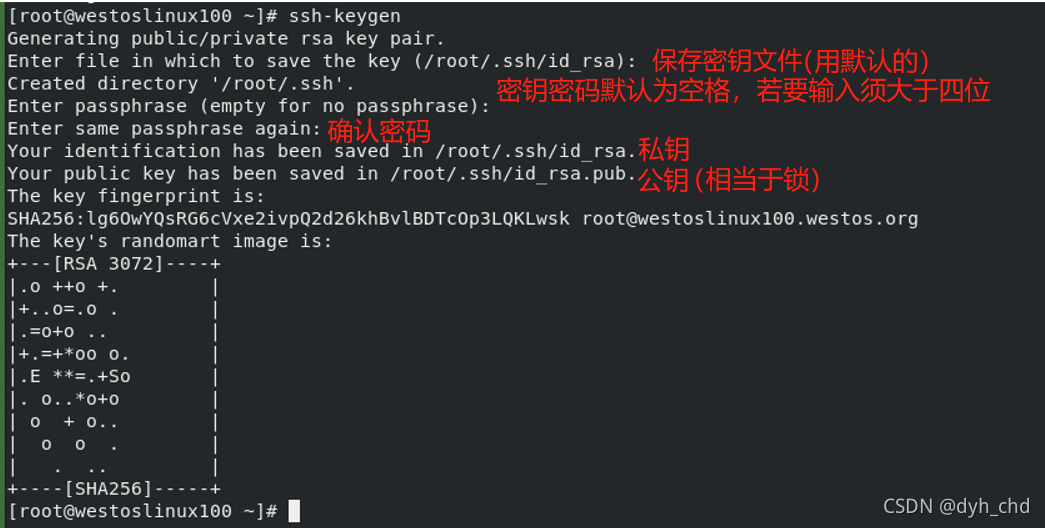
2) Non interactive generation
The purpose is the same as that of the method in 1), but no interaction is required
ssh-keygen -f /root/.ssh/id_isa -P "" ""The setting password is blank
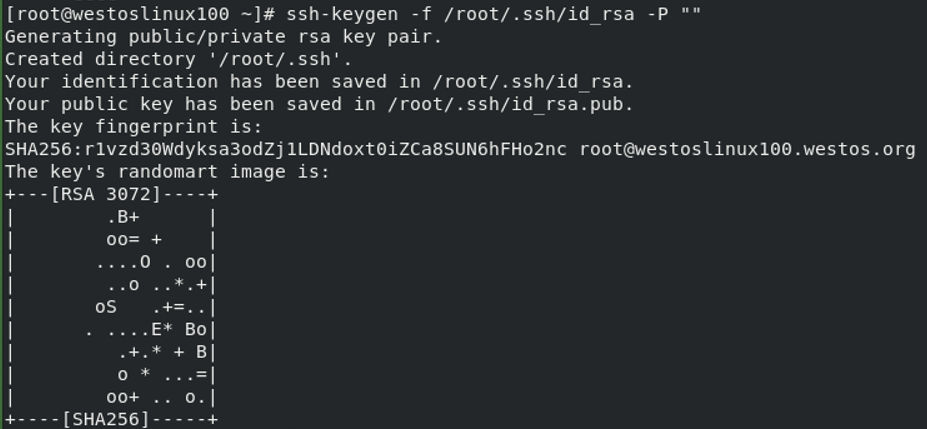
3. Encrypt server
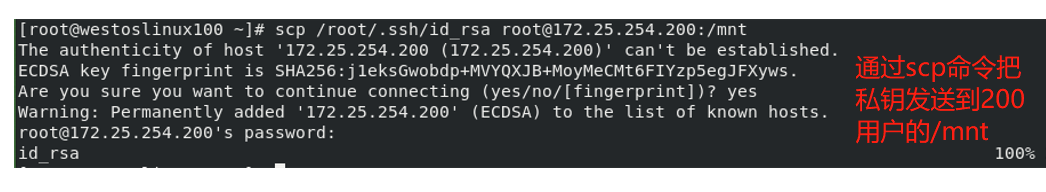
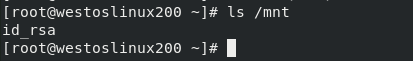
ssh-copy-id -i /root/.ssh/id_rsa.pub username@serverip
After generating the asymmetric key, you can view the corresponding file
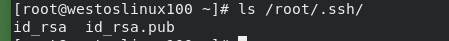
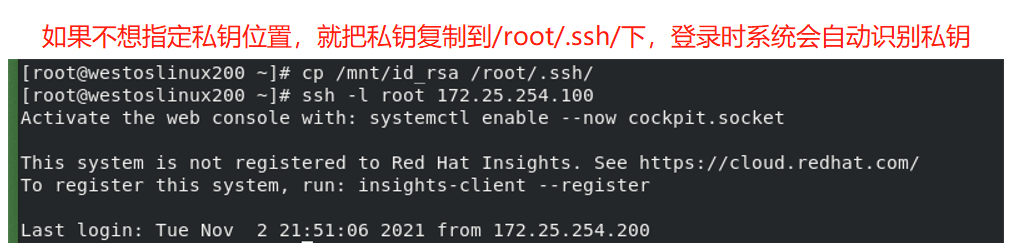
- Note: it is not a safe way to log in to other users by entering the user password. Now another lock, namely the public key, is set for the server. Without the server user password, the client can open this lock through the private key distributed by the server and enter the server.
We just generated an asymmetric key, that is, a lock and a key. Now we need to "lock" to determine which door to lock
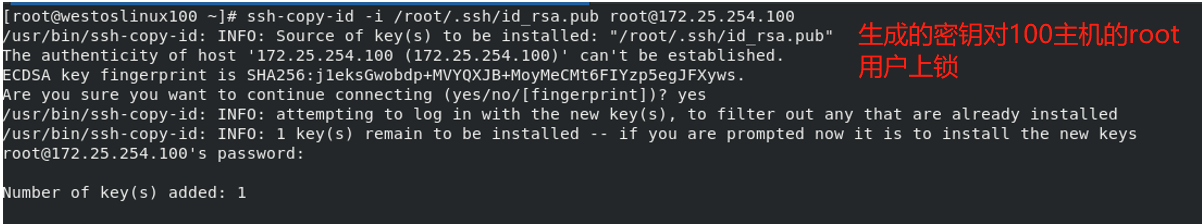
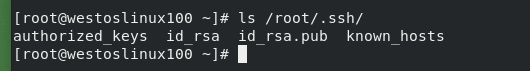
4, Detailed explanation of sshd security optimization parameters
- configuration file
/etc/ssh/sshd_config
Preparation before experiment
setenforce 0 #Turn off selinux firewall
1. Port (can be regarded as physical password)
The default port in the configuration file is port22
When logging in to a user with ssh, the default port is 22
vim /etc/ssh/sshd_config Enter the file and modify the port to 2222
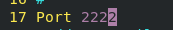
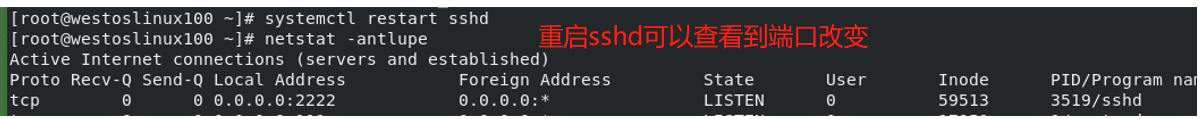
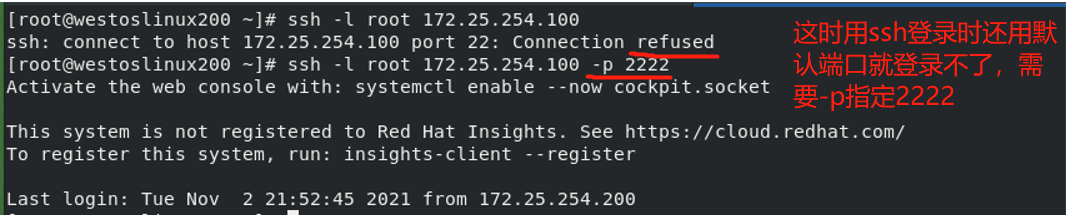
2. Enable the original password authentication method
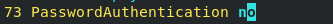
PasswordAuthentication yes|no defaults to yes
Once the modified file is changed to no, you cannot log in with the original password authentication
3. User blacklist
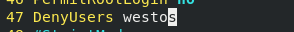
The client does not have permission to log in to the westos user of the server
4. User whitelist
There is no white list in the document, so you need to add it yourself
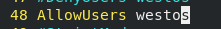
After adding the white list, the client will not be able to log in to other users on the server except the white list. Only users on the white list can log in. At the same time, the black list will also become invalid.