Article directory
- 1, Kali virtual machine installation
- 2, Domain name introduction
- 3, Collect subdomain information
- 4, Port information collection
- 5, Collect sensitive information
1, Kali virtual machine installation
There are two main steps:
(1) Install virtual machines such as VMware:
For specific installation process, please refer to https://blog.csdn.net/qq_40950957/article/details/80467513.
(2) To install Kali on VMware:
For specific installation process, please refer to https://blog.csdn.net/qq_40950957/article/details/80468030.
Or direct reference https://blog.csdn.net/chaootis1/article/details/84137460 Complete steps (1) and (2).
2, Domain name introduction
1. Domain name introduction
Domain name is the name of a computer or computer group on the Internet, which is composed of a series of names separated by dots. It is used to identify the electronic orientation of the computer during data transmission.
Browser browsing process:
(1) The client uploads the domain name to the DNS server;
(2) The DNS server returns the IP address corresponding to the specified domain name to the client;
(3) The client accesses the target server according to IP;
(4) The target server returns the access content to the client.
As follows: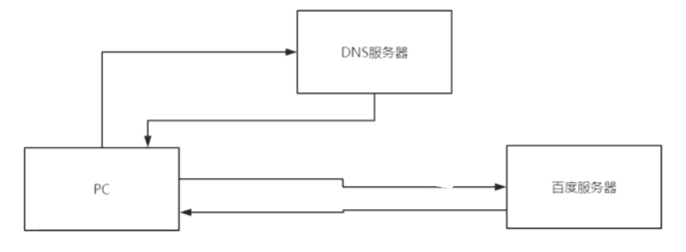
Because IP address is not easy to remember and can not display the name and nature of address organization, people have designed a domain name.
And through the Domain Name System (DNS), the domain name and IP address are mapped to each other, making it easier for people to access the Internet without remembering the IP address string that can be read directly by the machine.
2. Domain name query method whois
whois is a database used to query whether a domain name has been registered and the details of the registered domain name (such as domain name owner, domain name registrar, etc.).
Whois information with different domain name suffixes needs to be queried in different whois databases, such as. com's Whois database and. edu's. At present, the websites that provide whois inquiry service in China include wanwang, the home of stationmaster, etc. Whois information of each domain name or IP is saved by the corresponding management organization. For example, whois information of domain names ending in. com is managed by VeriSign, the domain name operator of. com, and the domain name of China's national top-level domain. cn is managed by CNNIC.
The whois query method is as follows:
web interface query
- Wan Wan https://whois.aliyun.com
Example is shown.
-
https://www.whois365.com/cn
Example is shown.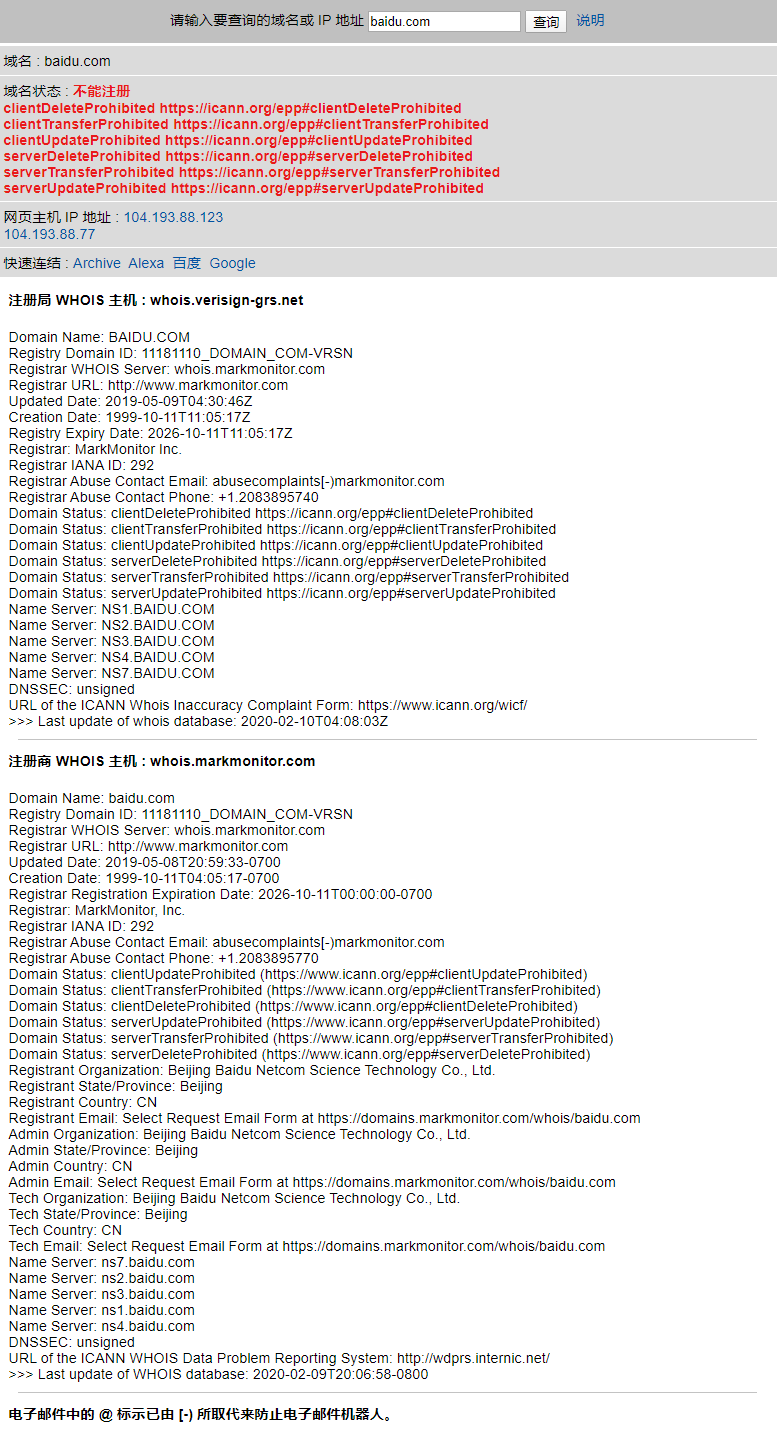
- Stationmaster's home http://whois.chinaz.com
Example is shown.
Obviously is blocked, inquires not to come out, namely Baidu has blocked the stationmaster 's home. -
https://whois.aizhan.com
Example is shown.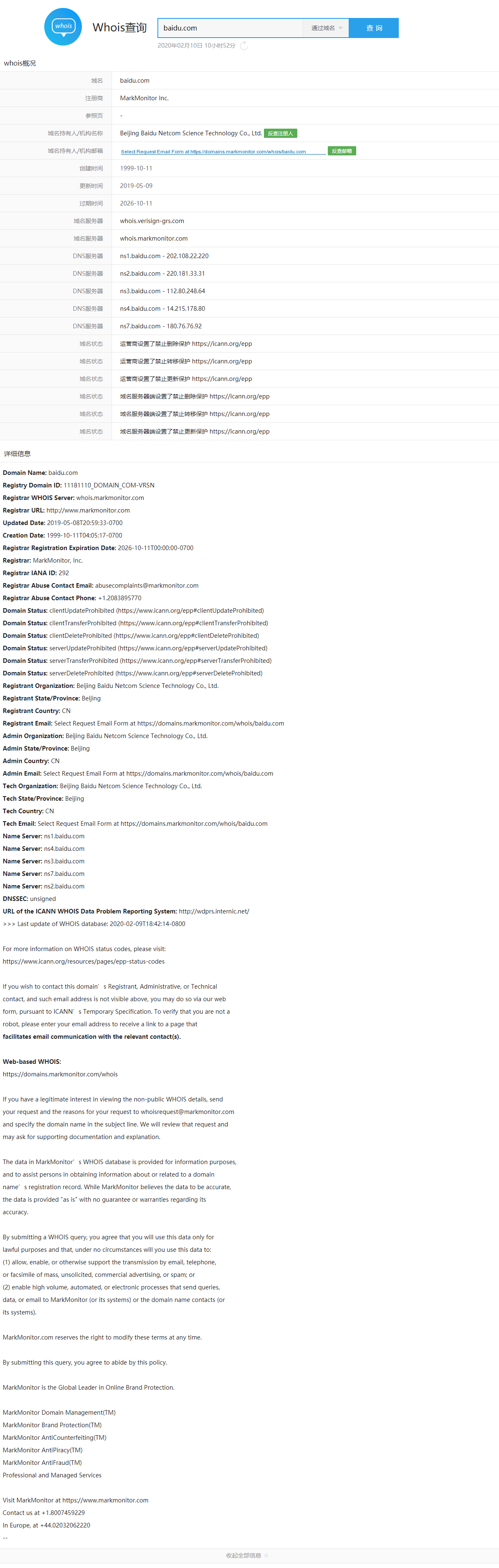
Query through whois command line
as
whois baidu.com
Show: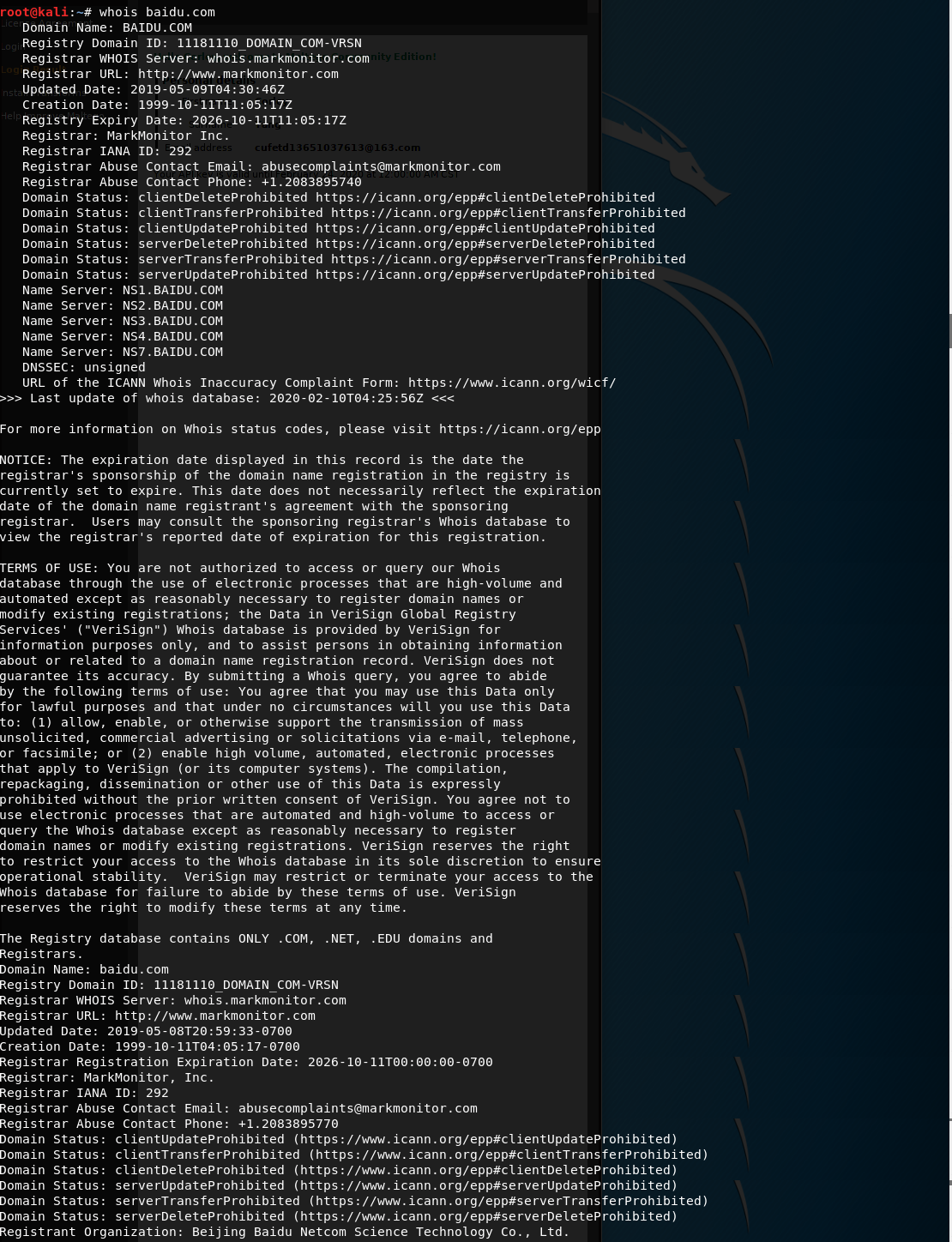
3.ICP filing
English full name: Internet Content Provider, Chinese full name: network content provider.
ICP can be understood as a telecom operator providing Internet information services and value-added services to users, and it is a formal operation enterprise or department approved by the competent national department.
The measures for the administration of Internet information services points out that Internet information services can be divided into two categories: operational and non operational. The State implements a licensing system for business Internet information services and a filing system for non business Internet information services. Those who have not obtained permission or fulfilled the filing procedures shall not engage in Internet information services.
Can pass http://www.beianbeian.com To view the website filing information, an example is as follows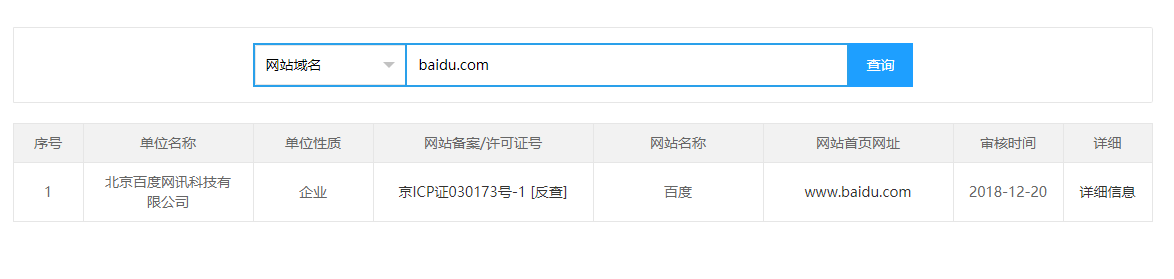
3, Collect subdomain information
1. Domain name and subdomain name
Top level domain names include. com,. net,. org,. cn, etc.
Subdomain name:
All top-level domain names are prefixed with sub domain names of the top-level domain name, and sub domain names are divided into two-level sub domain names, three-level sub domain names and multi-level sub domain names according to the number of technologies.
The collection of subdomain name is due to a large number of protection of a main domain name, the difficulty of mobile phone is relatively large, the difficulty of starting from the secondary domain name is relatively low, and the subdomain name is close to the main domain name and relevant information.
2. Sub domain name mining tool
- Maltego CE
Kali comes with it. If you can't receive the verification code when you register your account, you can register in Windows or other platforms, and then log in directly in Kali.
For the use of Maltego CE, please refer to https://www.cnblogs.com/zh2000/p/11199492.html
The results framework is shown in the figure below
The test results of Baidu are as follows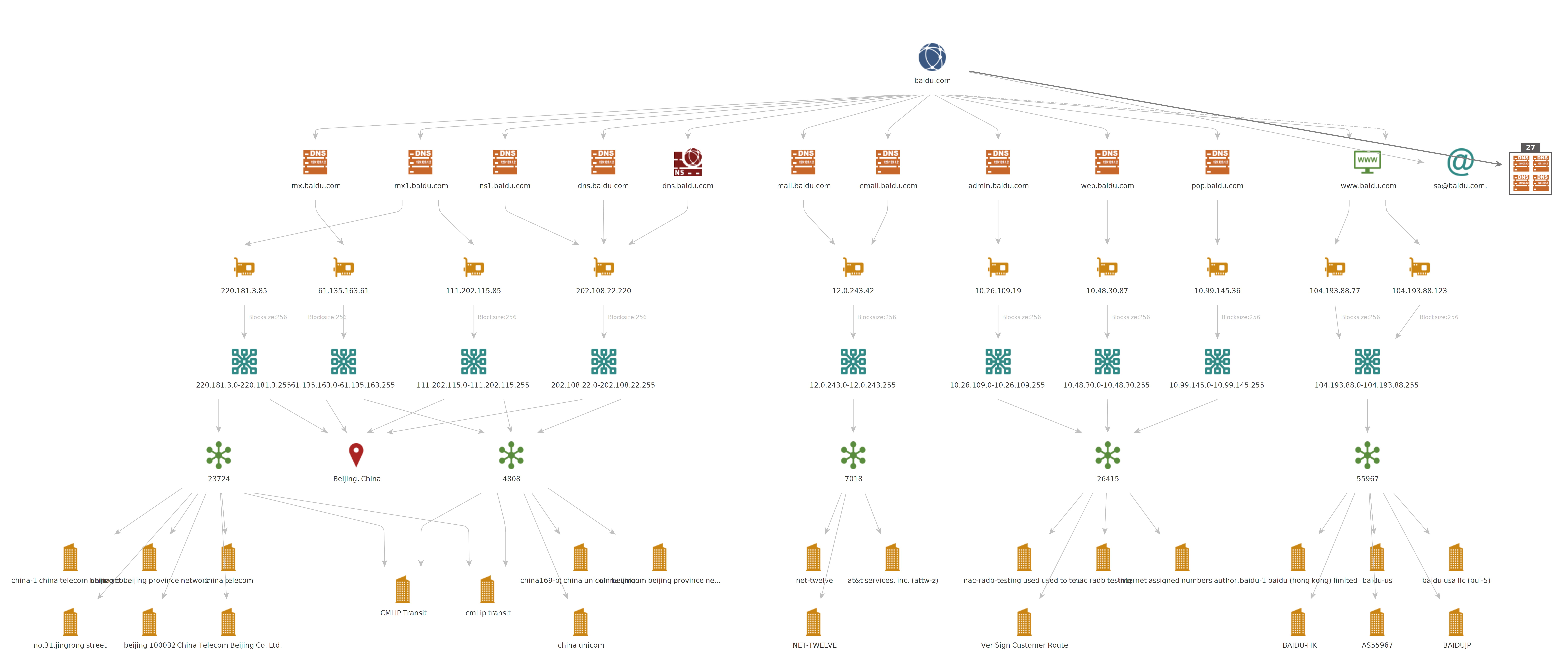
- wydomain
GitHub address: https://github.com/ring04h/wydomain.
Download and install commands (in Kali)
git clone https://github.com/ring04h/wydomain cd wydomain/ cat requirements.txt pip3 install -r requirements.txt
View parameters:
python dnsburte.py -h
Show:
usage: dnsburte.py [-h] [-t] [-time] [-d] [-f] [-o] wydomian v 2.0 to bruteforce subdomains of your target domain. optional arguments: -h, --help show this help message and exit -t , --thread thread count -time , --timeout query timeout -d , --domain domain name -f , --file subdomains dict file name -o , --out result out file
Use:
python dnsburte.py -d baidu.com
Show:
2020-02-10 10:15:41,739 [INFO] starting bruteforce threading(16) : baidu.com 2020-02-10 10:15:48,653 [INFO] dns bruteforce subdomains(100) successfully... 2020-02-10 10:15:48,653 [INFO] result save in : /root/wydomain/bruteforce.log
View results:
cat /root/wydomain/bruteforce.log
Show:
[ "m.baidu.com", "www.baidu.com", "wap.baidu.com", "pop.baidu.com", "bbs.baidu.com", ... "u.baidu.com", "sp.baidu.com", "svn.baidu.com", "hb.baidu.com", "vc.baidu.com" ]
- Search engine mining
For example:
Enter in Google
site:sina.com
Example results: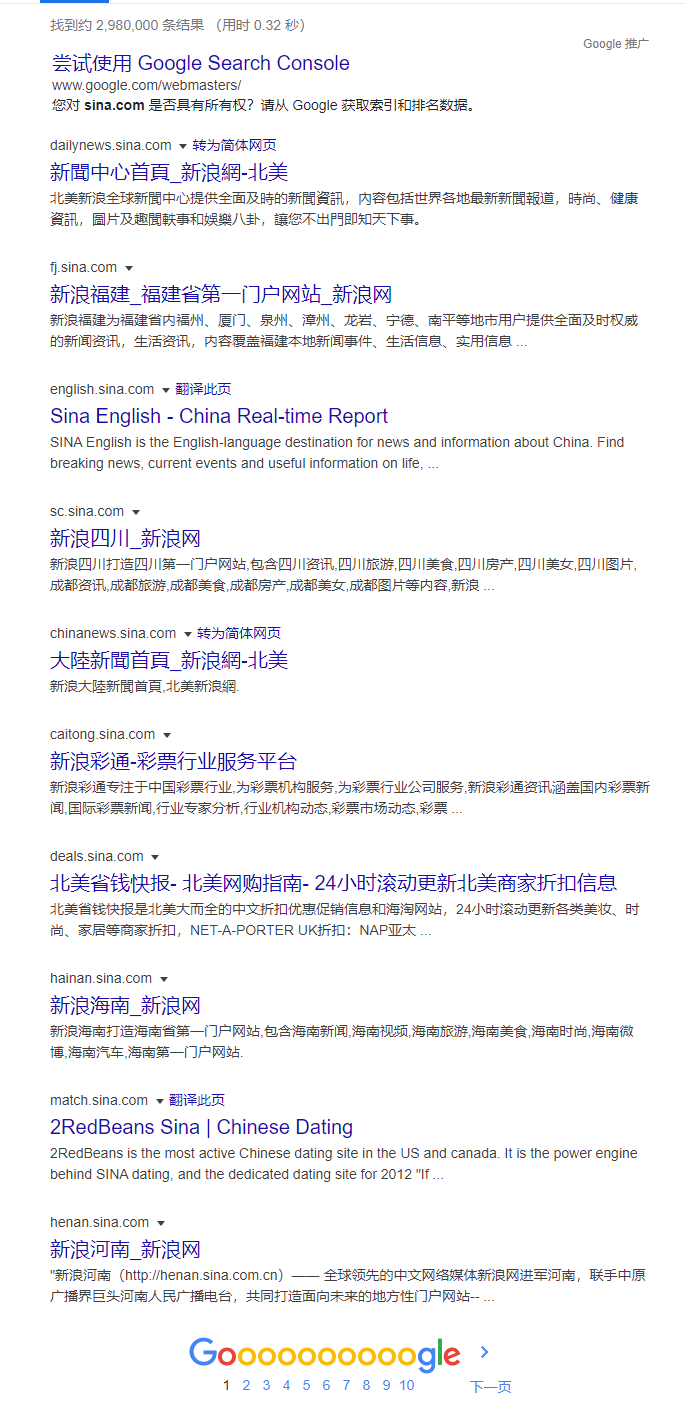
If you can't access Google, you can also enter it in Baidu
site:sina.com
Example results: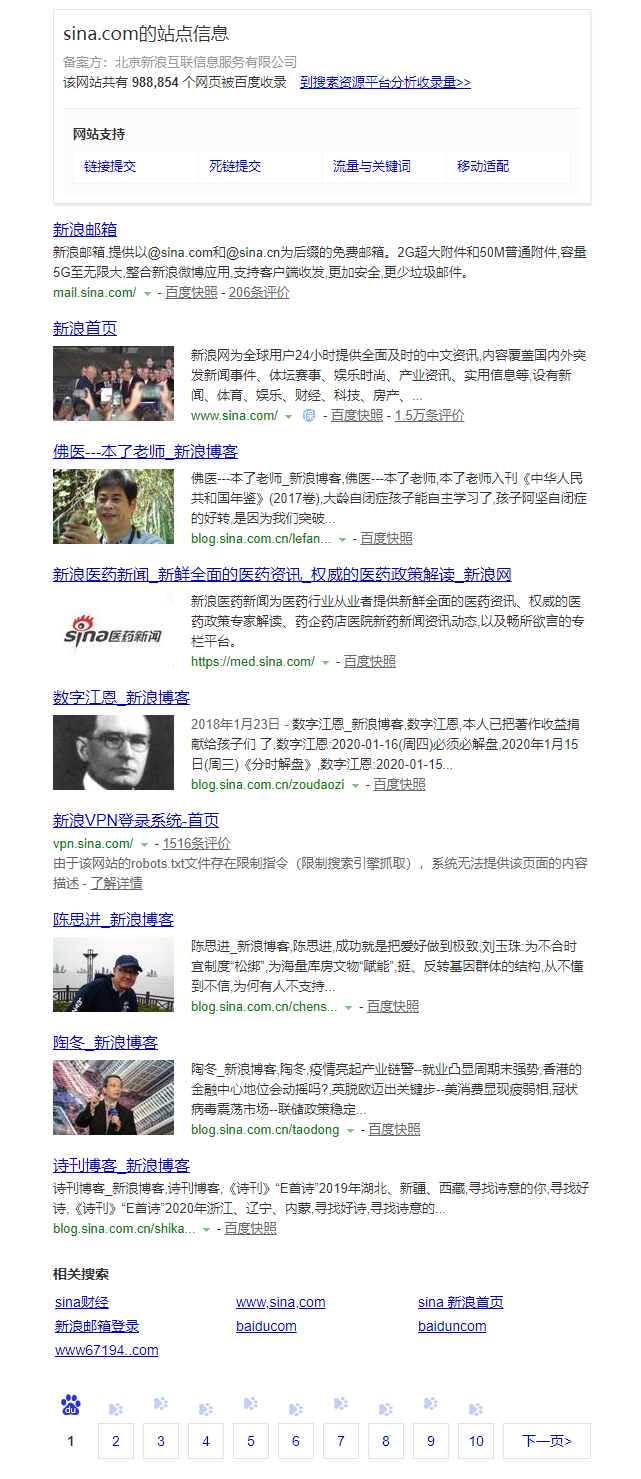
- Third party website query
-
http://tool.chinaz.com/subdomain
Examples are as follows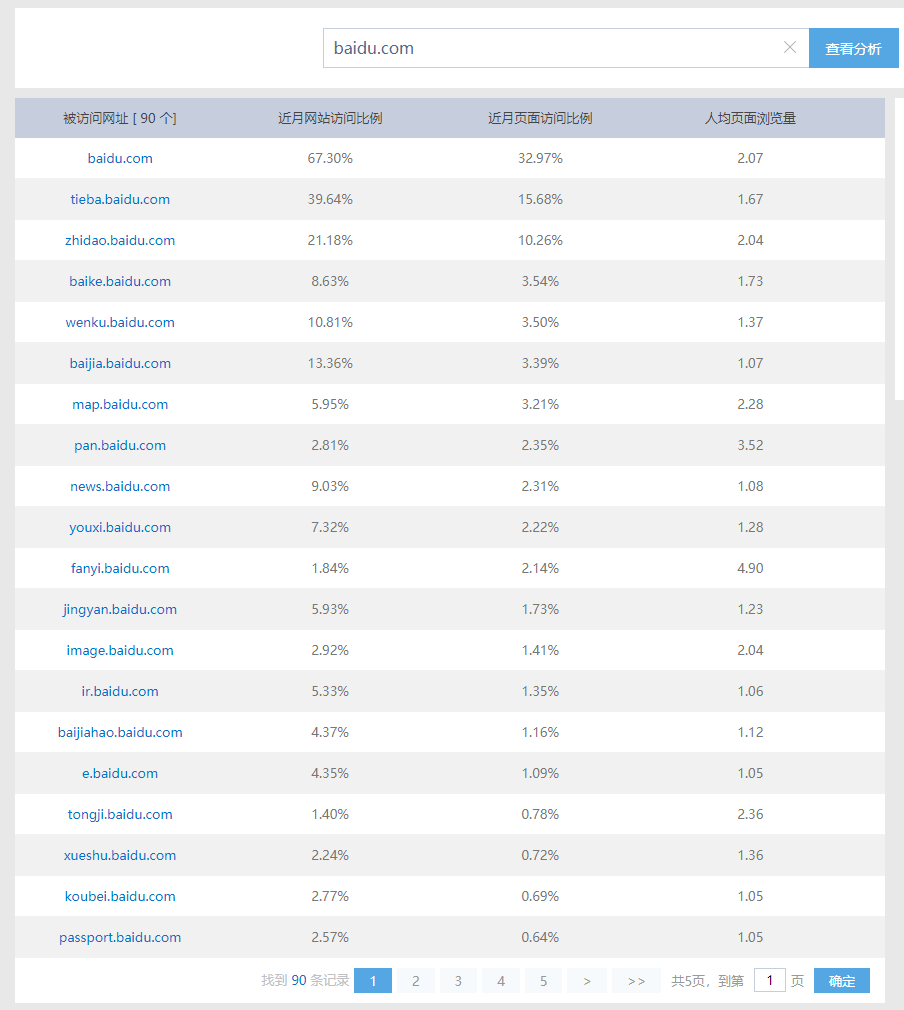
-
https://dnsdumpster.com
Examples are as follows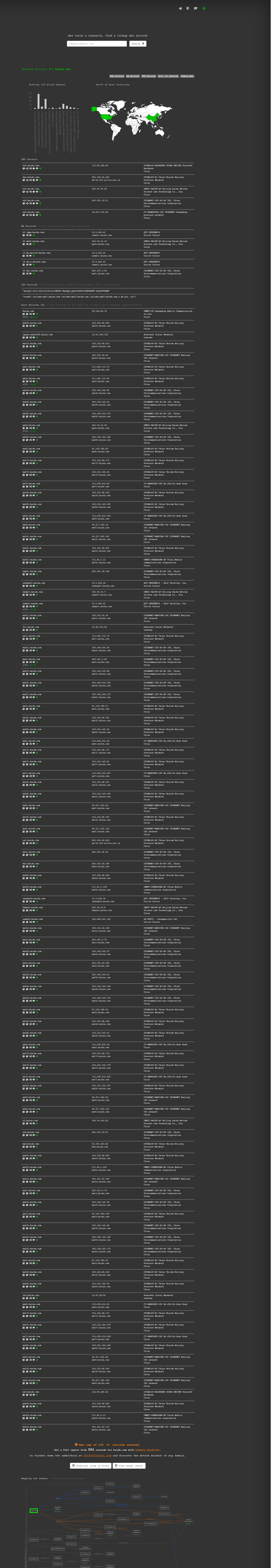
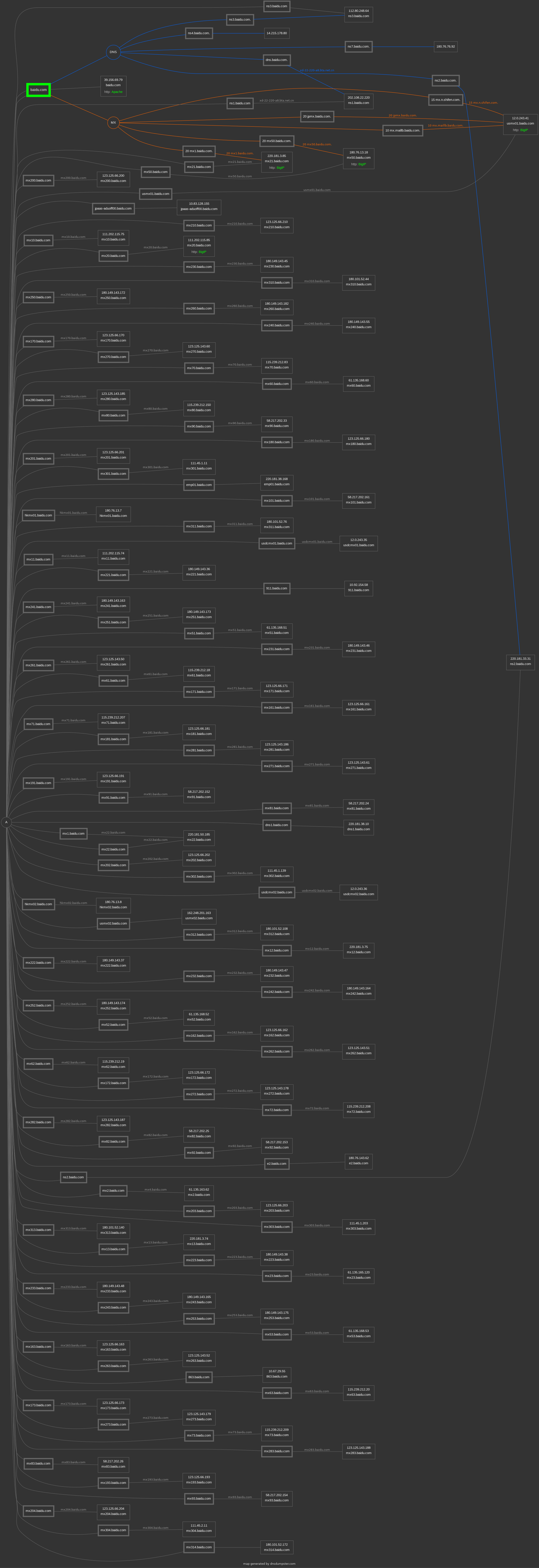
-
https://phpinfo.me/domain/
Examples are as follows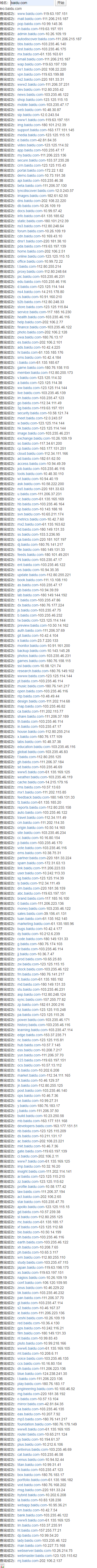
-
http://tool.chinaz.com/subdomain
4, Port information collection
1. Port introduction
If the IP address is compared to a house, the port is the door to the house. The real house has only a few doors, but an IP address can have 65536 ports.
The port is marked by the port number, which is only an integer and ranges from 0 to 65535.
Each port in the computer represents a service.
Open the command line as administrator in Windows view port to execute:
netstat -anbo
Printing
Active connection
//Protocol local address external address status PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 1032
RpcSs
[svchost.exe]
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 26800
[vmware-hostd.exe]
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
//Unable to get ownership information
TCP 0.0.0.0:902 0.0.0.0:0 LISTENING 19200
[vmware-authd.exe]
TCP 0.0.0.0:912 0.0.0.0:0 LISTENING 19200
[vmware-authd.exe]
...
UDP [fe80::e908:14c9:dc52:d1d5%5]:2177 *:* 4836
QWAVE
[svchost.exe]
UDP [fe80::e908:14c9:dc52:d1d5%5]:52240 *:* 7608
SSDPSRV
[svchost.exe]
UDP [fe80::f55a:3b0f:f090:458%14]:1900 *:* 7608
SSDPSRV
[svchost.exe]
UDP [fe80::f55a:3b0f:f090:458%14]:2177 *:* 4836
QWAVE
[svchost.exe]
UDP [fe80::f55a:3b0f:f090:458%14]:52242 *:* 7608
SSDPSRV
[svchost.exe]
2. Port information collection
Tools can be used to test the collection of target machine port status.
Tool principle:
Use TCP or UDP and other protocols to send packets with specified flags to the destination port, wait for the destination to return packets, so as to judge the port status.
Using nmap detection
The nmap symbol is like an eye, called the eye of God.
Order:
nmap -A -v -T4 baidu.com
Print:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-10 10:26 CST NSE: Loaded 151 scripts for scanning. NSE: Script Pre-scanning. Initiating NSE at 10:26 Completed NSE at 10:26, 0.00s elapsed Initiating NSE at 10:26 Completed NSE at 10:26, 0.00s elapsed Initiating NSE at 10:26 Completed NSE at 10:26, 0.00s elapsed Initiating Ping Scan at 10:26 Scanning baidu.com (220.181.38.148) [4 ports] Completed Ping Scan at 10:26, 0.04s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 10:26 Completed Parallel DNS resolution of 1 host. at 10:26, 0.01s elapsed Initiating SYN Stealth Scan at 10:26 Scanning baidu.com (220.181.38.148) [1000 ports] Discovered open port 443/tcp on 220.181.38.148 Discovered open port 80/tcp on 220.181.38.148 Completed SYN Stealth Scan at 10:26, 5.00s elapsed (1000 total ports) TRACEROUTE (using port 80/tcp) HOP RTT ADDRESS 1 ... 30 NSE: Script Post-scanning. Initiating NSE at 10:27 Completed NSE at 10:27, 0.00s elapsed Initiating NSE at 10:27 Completed NSE at 10:27, 0.00s elapsed Initiating NSE at 10:27 Completed NSE at 10:27, 0.00s elapsed Read data files from: /usr/bin/../share/nmap OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 44.19 seconds Raw packets sent: 2168 (98.008KB) | Rcvd: 5 (208B)
Explain:
Ports 443 and 80 are open, corresponding to https and http respectively.
Use online website detection
Address:
http://tool.chinaz.com/port/.
Test example: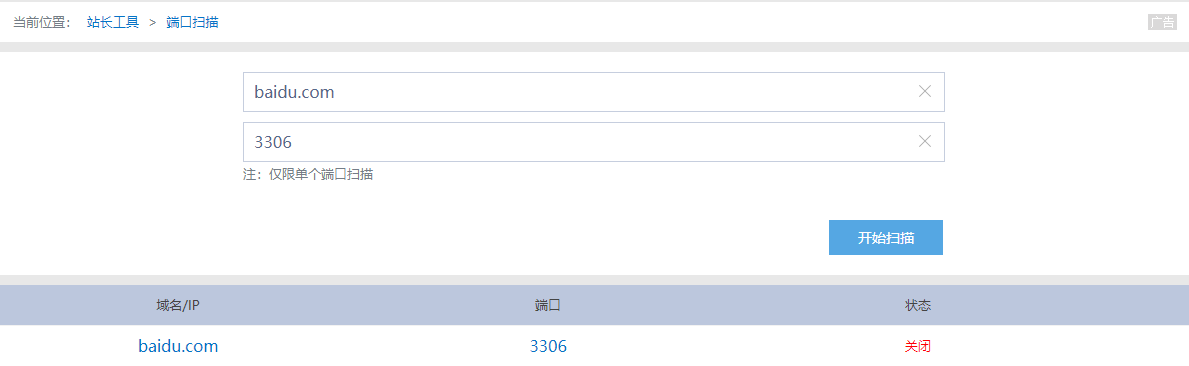
This method can't detect the local.
3. Port attack
There are different attack methods for different ports.
Attack method
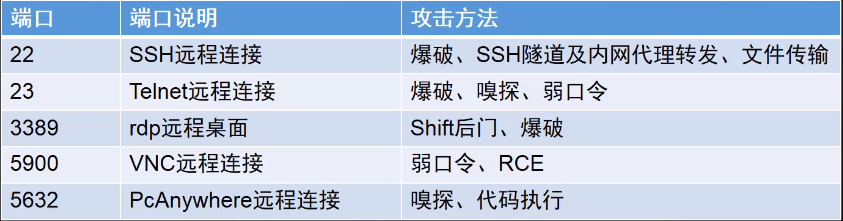
Defensive measures
- Turn off unnecessary ports
- Set up firewall for service port of important business
- Change user password frequently
- Frequently update software and patch
5, Collect sensitive information
1. Importance of sensitive information collection
For some good goals of security, it is impossible to complete penetration test directly through technical level.
In this case, search engine can be used to search the association information exposed on the Internet.
For example, database files, SQL injection, server configuration information, even through Git to find site disclosure source code, and Redis unauthorized access, so as to achieve the purpose of penetration test.
2.Google hacking syntax
Google hacking refers to the use of search engines such as Google to search for vulnerabilities of certain network hosts, in order to quickly find vulnerabilities of vulnerable hosts or specific hosts.
Intext: - search for body content e.g. intext: website management Intitle: - Search title content such as intitle: background management Filetype: - search the specified file format, for example, filetype:txt inurl: - search for a specific URL. For example. php?id Site: - make a search for a specific site, for example: site:baidu.com info: - specify search page information, for example: info:baidu.com
Example:
Enter in Google
Intel background management
As shown in the picture: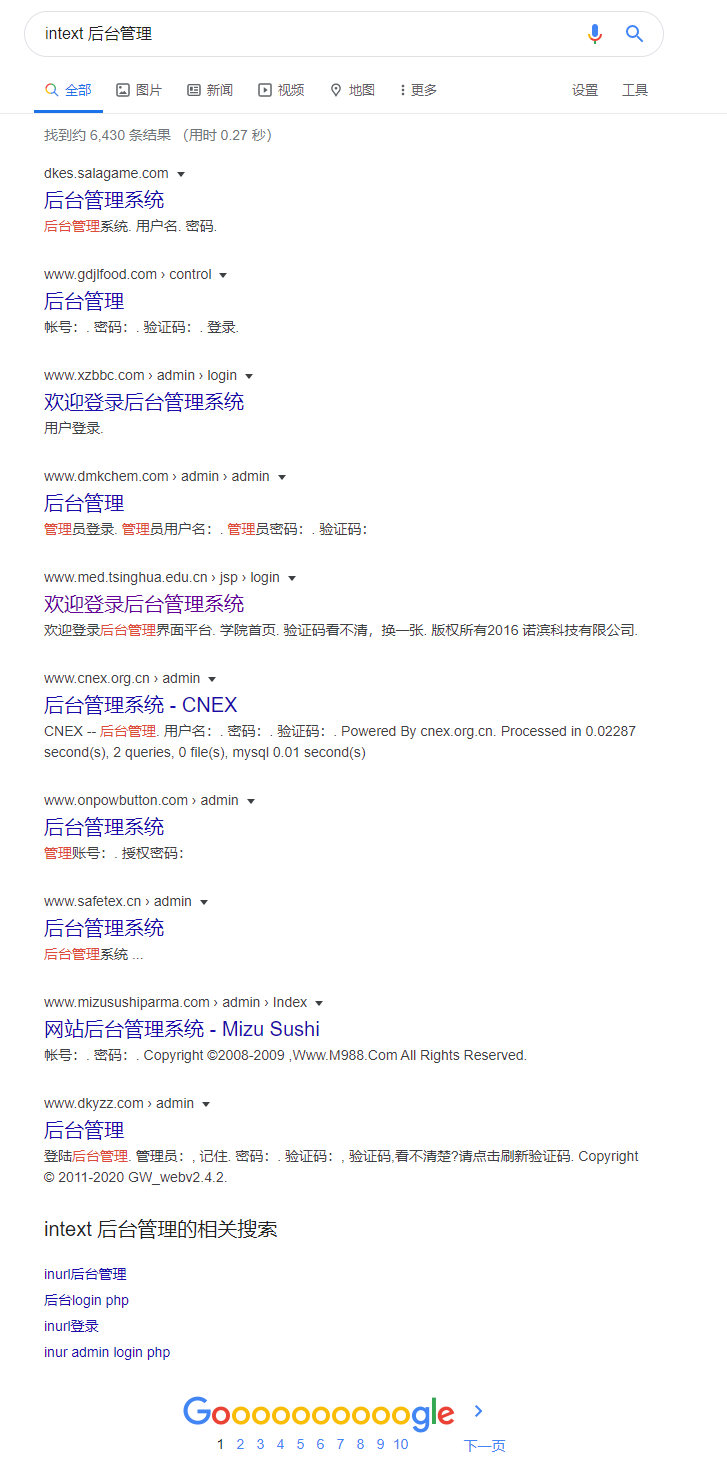
Obviously, there are many back office management systems exposed. You can easily click in one to see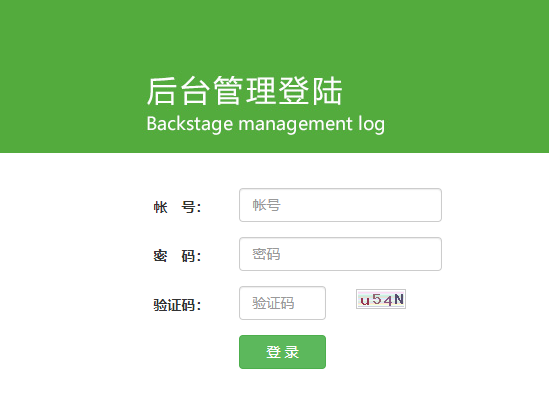
Obviously, this is extremely dangerous.
For another example, input in Baidu
intitle background management
Pictured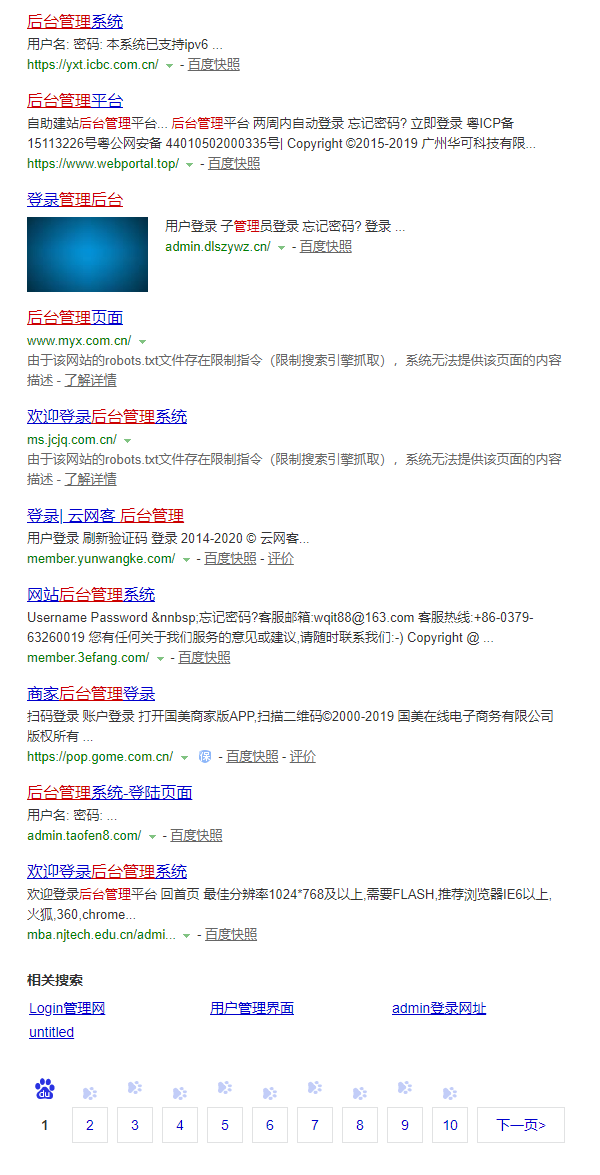
Similarly, there are a lot of background management system exposures. Try any one of them to display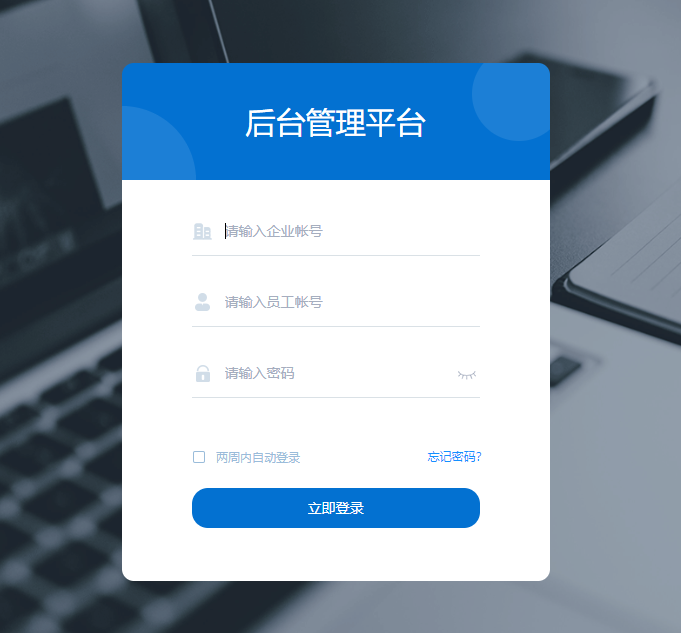
Obviously, there is a great threat to network security.
More about Google hacking's syntax, usage and latest news can be found here
https://www.exploit-db.com/google-hacking-database.
3.HTTP response collects server information
The service header and X-Powered-By header in the message that the target responds to in the communication with the target site through HTTP or HTTPS will expose the information of the target serve r and the programming language used. Through these information, we can have targeted exploit attempts.
To get an HTTP response:
Using browser audit tools
Click F12, select Network, and click F5 to refresh, as follows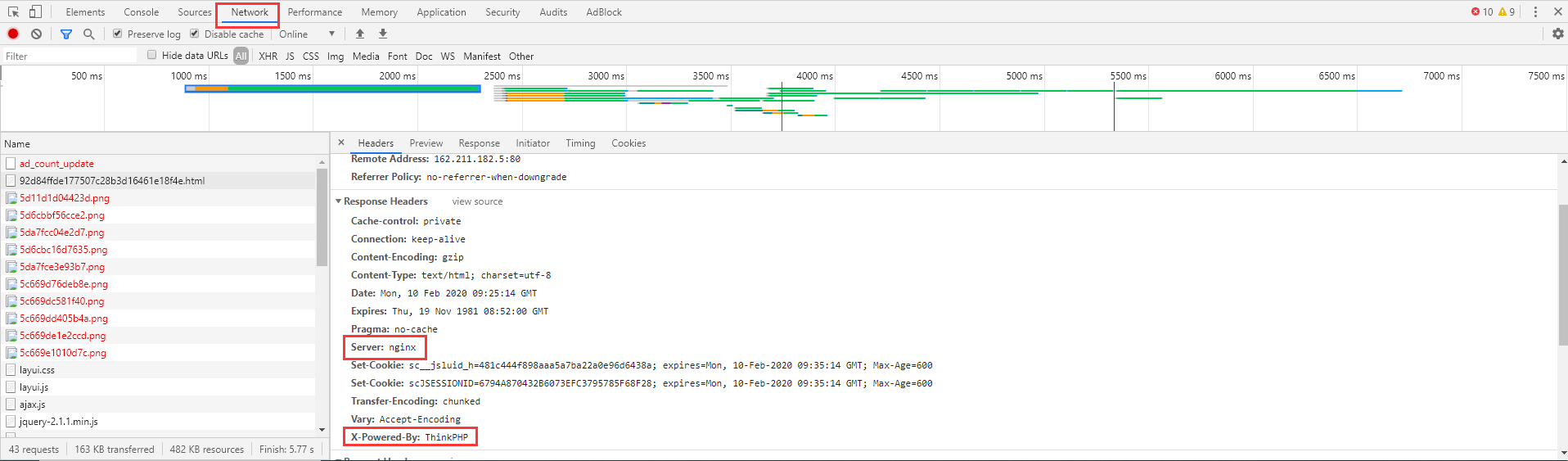
Obviously, Server middleware is nginx, and X-Powered-By is ThinkPHP, which is a framework of PHP language.
Writing Python scripts (using the requests Library)
Simple test:
import requests r = requests.get('http://www.beianbeian.com') print(r.headers)
Print:
{'Server': 'nginx', 'Date': 'Mon, 10 Feb 2020 03:08:34 GMT', 'Content-Type': 'text/html; charset=utf-8', 'Transfer-Encoding': 'chunked', 'Connection': 'keep-alive', 'Vary': 'Accept-Encoding', 'Expires': 'Thu, 19 Nov 1981 08:52:00 GMT', 'Pragma': 'no-cache', 'Cache-control': 'private', 'X-Powered-By': 'ThinkPHP', 'Set-Cookie': 'PHPSESSID=v0ee5tiumr3pat5kpnltdvnbh4; path=/, sc__jsluid_h=43c68abd9efb5d2ebed43d88a1ab550c; expires=Mon, 10-Feb-2020 03:18:34 GMT; Max-Age=600, scJSESSIONID=04D2B6C6538CDD8A48003405C29F52B0; expires=Mon, 10-Feb-2020 03:18:34 GMT; Max-Age=600', 'Content-Encoding': 'gzip'}
As the result of the first method, the Server middleware is nginx, and X-Powered-By is ThinkPHP.

