Python 3 Baidu cloud disk resources auto transfer
Python 3 realizes the automatic transfer of Baidu cloud disk resources, solves the automatic transfer of shared links with passwords, and the automatic transfer of resources without passwords. At the same time, it realizes the transfer of post request and selenium transfer
Preface
Recently, I saw a free animation website. As soon as the resources came out, there were a lot of online resources, so I thought
So I wrote a piece of code and crawled all the resources of the website
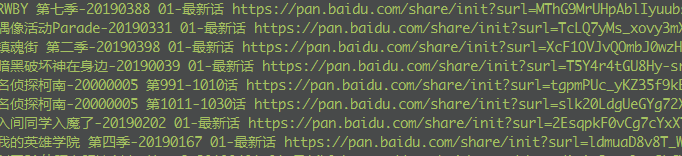
Then it's time to save them to my cloud disk one by one. The problem is that more than 1900 are very tiring if you use them manually, so you plan to do it through Python
At first, the idea was to use selenium to operate, but I was curious about whether I could do it through common crawler thinking, so I added the exploration process as well
Analysis & code
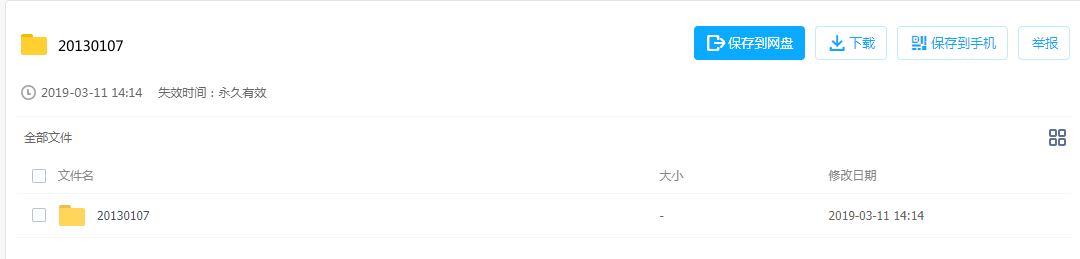
Analyze the target, construct and send the request through the resource link and password taken from the database, then enter the resource saving page, and click the operation through selenium
First, the extraction link with password is as follows
https://pan.baidu.com/share/init?surl=xxx
Instead of password, you can extract the link of resources directly
https://pan.baidu.com/s/1xxx
It's similar to the extraction page that jumps after entering the password. Note that the contents of the above two xxx are the same. One is the intrinsic parameter accessed from the web side, which will be mentioned later
After entering the password, we can go in. The key is how to submit the password. Press f12 to open the developer tool according to the general principle. After entering the password on the password input page, click extract file
There is a possibility that you will see a 404 page where you can't find the resources. Of course, you can use fiddler to grab the package and you can definitely catch it
We found key requests
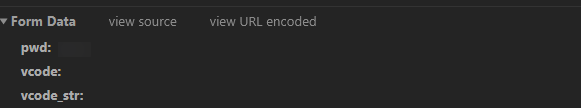
The post request is sent with a series of parameters and a password
The following is the jump resource page, which is a get request without any other parameters, but if you just take it out and visit it directly (when you have never entered a password), it will jump directly to the page where you enter the password. So the question is why
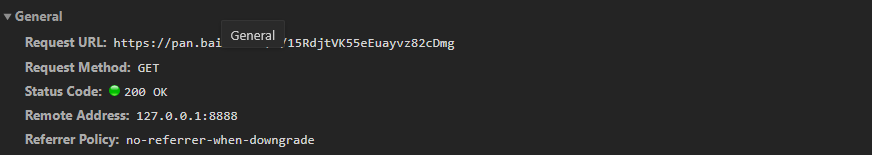
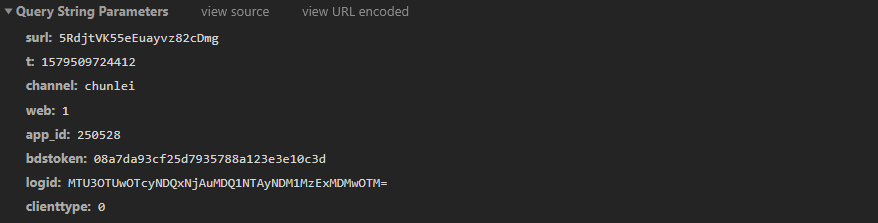
An experienced and accurate guess may be that there is a difference between the cookies of the two requests, because logically, the post request after I input the password will return a parameter, which is neither reflected in the url of the second request nor carried formdata, so there can be a difference in the cookie
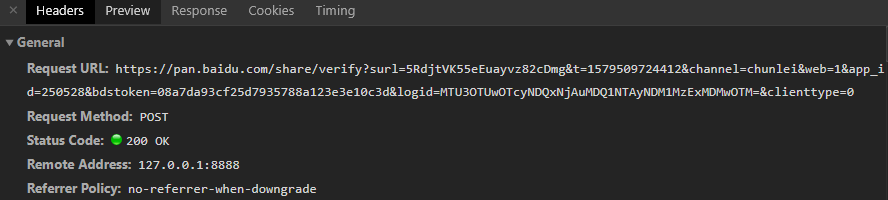
It turns out that the cookie s of the two requests are different. The key is https://pan.baidu.com/s/1xxx
The BDCLND in the cookie of is exactly https://pan.baidu.com/share/verify?surl=5RdjtVK55eEuayvz82cDmg&t=1579432835477&channel=chunlei&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d&logid=MTU3OTQzMjgzNTQ3OTAuNjM2MDg4OTgzOTY3MzU0OQ==&clienttype=0 One of the returned parameters, as shown in the figure:
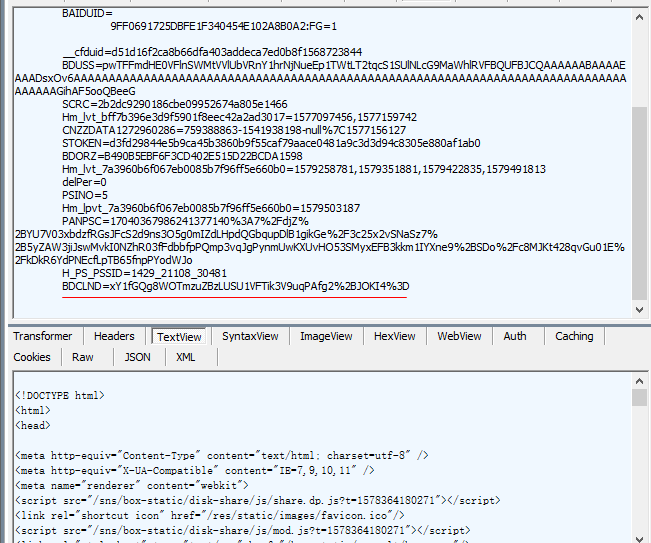
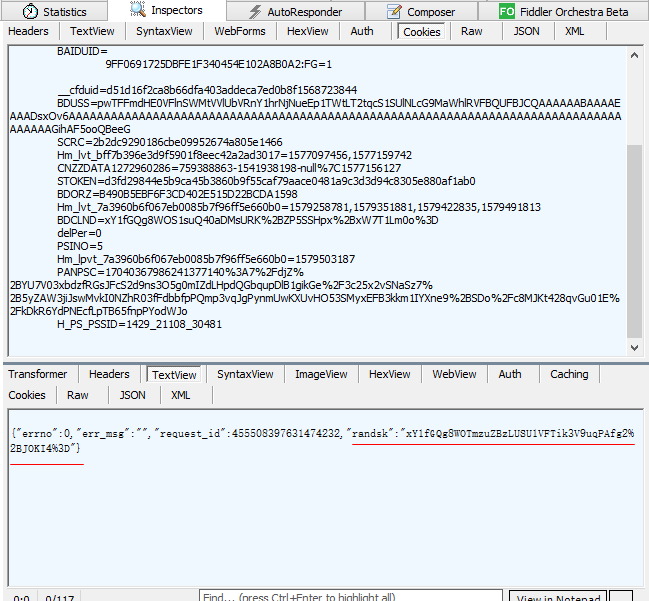
That is to say, we need to obtain this parameter before accessing https://pan.baidu.com/s/1xxx Only with this cookie can you not return to the password input page
So the next question is how to get this parameter. I'll make a long story short
It can be seen from the comparative analysis of multiple post links that
https://pan.baidu.com/share/verify?surl=5RdjtVK55eEuayvz82cDmg&t=1579432835477&channel=chunlei&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d&logid=MTU3OTQzMjgzNTQ3OTAuNjM2MDg4OTgzOTY3MzU0OQ==&clienttype=0
| parameter | value | state |
|---|---|---|
| surl | 5RdjtVK55eEuayvz82cDmg | Equivalent to the ID of the resource, known |
| t | 1579432835477 | 13 bit time stamp |
| channel | chunlei | It's fixed anyway |
| web | 1 | Fixed, as mentioned earlier |
| app_id | 250528 | fixed |
| bdstoken | 08a7da93cf25d7935788a123e3e10c3d | fixed |
| logid | MTU3OTQzMjgzNTQ3OTAuNjM2MDg4OTgzOTY3MzU0OQ== | change |
| clienttype | 0 | fixed |
Only the logid is changed. Then I found it. It should be generated in js. Finally, it's here
[failed to transfer the pictures in the external link. The source station may have anti-theft chain mechanism. It is recommended to save the pictures and upload them directly (img-s0rp42yw-1579682702660) (http://image.joelyings.com/2020-01-20_. PNG))
Find the js generation code as follows:
var u = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/~!@#¥%......&" , l = String.fromCharCode , d = function(e) { if (e.length < 2) { var n = e.charCodeAt(0); return 128 > n ? e : 2048 > n ? l(192 | n >>> 6) + l(128 | 63 & n) : l(224 | n >>> 12 & 15) + l(128 | n >>> 6 & 63) + l(128 | 63 & n) } var n = 65536 + 1024 * (e.charCodeAt(0) - 55296) + (e.charCodeAt(1) - 56320); return l(240 | n >>> 18 & 7) + l(128 | n >>> 12 & 63) + l(128 | n >>> 6 & 63) + l(128 | 63 & n) } , f = /[\uD800-\uDBFF][\uDC00-\uDFFFF]|[^\x00-\x7F]/g , g = function(e) { return (e + "" + Math.random()).replace(f, d) } , h = function(e) { var n = [0, 2, 1][e.length % 3] , t = e.charCodeAt(0) << 16 | (e.length > 1 ? e.charCodeAt(1) : 0) << 8 | (e.length > 2 ? e.charCodeAt(2) : 0) , o = [u.charAt(t >>> 18), u.charAt(t >>> 12 & 63), n >= 2 ? "=" : u.charAt(t >>> 6 & 63), n >= 1 ? "=" : u.charAt(63 & t)]; return o.join("") } , m = function(e) { return e.replace(/[\s\S]{1,3}/g, h) } , p = function() { return m(g((new Date).getTime())) } , w = function(e, n) { return n ? p(String(e)).replace(/[+\/]/g, function(e) { return "+" == e ? "-" : "_" }).replace(/=/g, "") : p(String(e)) }; !function() { r(document).ajaxSend(function(e, n, t) { var i = w(s.getCookie("BAIDUID")); ... }) }(),
It's mainly about this content. logid is generated by a series of methods. Due to the complexity, it's decided to call the third-party library execjs to slightly adjust this section of js
var u = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/~!@#¥%......&", l = String.fromCharCode, d = function(e) { if (e.length < 2) { var n = e.charCodeAt(0); return 128 > n ? e : 2048 > n ? l(192 | n >>> 6) + l(128 | 63 & n) : l(224 | n >>> 12 & 15) + l(128 | n >>> 6 & 63) + l(128 | 63 & n) } var n = 65536 + 1024 * (e.charCodeAt(0) - 55296) + (e.charCodeAt(1) - 56320); return l(240 | n >>> 18 & 7) + l(128 | n >>> 12 & 63) + l(128 | n >>> 6 & 63) + l(128 | 63 & n) }, f = /[\uD800-\uDBFF][\uDC00-\uDFFFF]|[^\x00-\x7F]/g, g = function(e) { return (e + "" + Math.random()).replace(f, d) }, h = function(e) { var n = [0, 2, 1][e.length % 3], t = e.charCodeAt(0) << 16 | (e.length > 1 ? e.charCodeAt(1) : 0) << 8 | (e.length > 2 ? e.charCodeAt(2) : 0), o = [u.charAt(t >>> 18), u.charAt(t >>> 12 & 63), n >= 2 ? "=" : u.charAt(t >>> 6 & 63), n >= 1 ? "=" : u.charAt(63 & t)]; return o.join("") }, m = function(e) { return e.replace(/[\s\S]{1,3}/g, h) }, p = function() { return m(g((new Date).getTime())) }, w = function(e, n) { return n ? p(String(e)).replace(/[+\/]/g, function(e) { return "+" == e ? "-" : "_" }).replace(/=/g, "") : p(String(e)) }; function getLogId(data){ var logid = w(data); return logid; }
Then when we call, just input the BAIDUID, which can be obtained from the cookie of the earliest password input page
When installing execjs, please note that the command is pyexecjs:
pip install pyexecjs
Because Node.js is a Javascript language server-side running environment, you also need to Install nodejs
After installation, you can see that
Python 3.6.3 (v3.6.3:2c5fed8, Oct 3 2017, 17:26:49) [MSC v.1900 32 bit (Intel)] on win32 Type "help", "copyright", "credits" or "license" for more information. >>> import execjs >>> execjs.get().name 'Node.js (V8)'
Then call
# Read in the modified js code file def get_logid(self, baidu_id): with open('boot.js', encoding='utf-8') as f: bootjs = f.read() # Compiling js code js_obj = execjs.compile(bootjs) # Call the getLogId method, give the parameter Baidu? ID, that is, BAIDUID, and get the output res = js_obj.call('getLogId', baidu_id) return res
This is the code to test sending the request
def __init__(self): # Take the list of resource links and passwords from the database self.row_lists = [] # Link with format required for password request self.pan_post = 'https://pan.baidu.com/share/verify?surl={}&t={}&channel=chunlei' \ '&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d' \ '&logid={}&clienttype=0' # 13 bit time stamp self.t = int(round(time.time() * 1000)) # Make a random ua by yourself self.user_agent = FaUa.get_ua() def get_logid(self, baidu_id): with open('boot.js', encoding='utf-8') as f: bootjs = f.read() js_obj = execjs.compile(bootjs) res = js_obj.call('getLogId', baidu_id) return res def test(self): # Keep conversation session = requests.session() # Resource links to extract s_url = 'https://pan.baidu.com/share/init?surl=5RdjtVK55eEuayvz82cDmg' # verify=False to some extent, it can avoid multiple accesses that cause the other server to seal you, but there will be a warning. This is to add a request. Packages. Urlib3. Disable_warnings () in front, that is, disable the security request warning r_bid = session.get(s_url, headers={'user-agent': self.user_agent}, verify=False) # Get the BAIDUID in the cookie baiduid = r_bid.cookies['BAIDUID'] # Get the returned logid according to the BAIDUID logid = self.get_logid(baiduid) # Get the next part of the link ID of the resource surl = s_url.split('surl=')[1] # Parameter of post request, with password, the last two are empty data = { 'pwd': 'xxx', 'vcode': '', 'vcode_str': '', } # Request header headers = { 'user-agent':self.user_agent, 'Referer': 'https://pan.baidu.com/share/init?surl=5RdjtVK55eEuayvz82cDmg', 'Accept':'*/*', 'Content-Type':'application/x-www-form-urlencoded; charset=UTF-8', 'X-Requested-With':'XMLHttpRequest', 'Accept-Language':'zh-CN', 'Accept-Encoding':'gzip, deflate', 'Host':'pan.baidu.com', 'DNT':'1', 'Connection': 'Keep-Alive', 'Cache-Control': 'no-cache', } # Send post request r = session.post(self.pan_post.format(surl, self.t, logid), data=data, headers=headers, verify=False) print(r.url, r.text) # Get the returned BDCLND, which is brought in the cookie of the next request BDCLND = r.json()['randsk'] headers['Cookie'] = 'BDCLND=' + BDCLND print(headers) r2 = session.get('https://pan.baidu.com/s/15RdjtVK55eEuayvz82cDmg', headers=headers, verify=False) r2.encoding = 'utf-8' print(r2.text)
This is the result of the returned page
<!DOCTYPE html> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8" /> <meta http-equiv="X-UA-Compatible" content="IE=7,9,10,11" /> <meta name="renderer" content="webkit"> <script src="/sns/box-static/disk-share/js/share.dp.js?t=1578364180271"></script> <link rel="shortcut icon" href="/res/static/images/favicon.ico"/> <script src="/sns/box-static/disk-share/js/mod.js?t=1578364180271"></script> <link rel="stylesheet" type="text/css" href="/box-static/consult/base.css"/> <link rel="stylesheet" type="text/css" href="/box-static/consult/system-core.css"/> <script src="/box-static/consult/base.js"></script> <script src="/box-static/consult/system-core.js"></script> <link rel="stylesheet" type="text/css" href="/box-static/consult/function.css"/> ... <div class="slide-show-left"> <h2 class="file-name" title="file name"> <em class="global-icon-16"></em>file name</h2> </div> <div class="slide-show-right"> <span class="slide-header-funcs"> </span> <div class="module-share-top-bar g-clearfix"> <div class="bar"></div> </div> </div> <div class="cb"></div> <div class="slide-show-other-infos"> <div class="share-file-info"> <span>2020-01-15 19:22</span> </div> <div class="share-valid-check"> Expiration time: permanent </div> <div class="slide-show-other-cns clearfix"> <span class="title-funcs"> <span class="funcs-share-area"> </span> </span> </div> <div class="cb"></div> </div> </div> </div> <div class="share-list" id="shareqr"> <div class="module-toolbar g-clearfix"> <div class="default-dom"> <div class="list-grid-switch list-switched-on"> <a class="list-switch" href="javascript:void(0)" node-type="kyzmAM0B" style="display:none"></a> <a class="grid-switch" href="javascript:void(0)" node-type="xgcvwQNp"></a> </div> </div> <div class="after-dom"></div> <div class="user-dom"> </div> </div> <!--[if IE]><iframe id="historyIFrameEmulator" style="display: none"></iframe><![endif]--> <div node-type="KPDwCE" class="KPDwCE"> </div> </div> <div class="ad-platform-tips ad-multi-tips" node-type="share-mutil-bottom" id="web-multi-bottom" node-id="web-sharemultibanner"> <div style="margin: 0 auto; width: 960px;" id="cpro_u2164871"></div> </div> </div> </div> <div class="bd-aside"> <div node-type="module" class="module-share-person-info"> <div class="share-person-inner global-clearfix haha"> <div class="share-person-avatar"> <a href="//yun.baidu.com/buy/center?tag=1&from=sicon" class="vip-icon sicon" target="_blank"><em></em></a> <a href="javascript:void(0)" title="go Ta Share home page for" class="person-icon"><img alt="fci****re2" src="https://ss0.bdstatic.com/7Ls0a8Sm1A5BphGlnYG/sys/portrait/item/netdisk.1.46160ad.44gPu69hQcgfXwSxAB1nrQ.jpg"></a> </div> <div class="share-person-data self"> <div class="share-person-data-top"> <a href="/share/home?uk=3821724077&suk=euEHLsAO_SkKFFGZ7JnePA" target="_blank" title="go Ta Share home page for" class="share-person-username global-ellipsis">fci****re2</a> <a href="//yun.baidu.com/buy/center?tag=8&from=sicon" class="svip-icon sicon"> <em></em> ...
ok, that's what we're trying to figure out. We're trying to figure out how to get the logid after entering the password https://pan.baidu.com/share/init?surl=xxx With such links and passwords, you can access the resource file page after entering passwords in batches through the code
How to create a new folder and transfer it by request
We capture the operation of transferring a resource to our own disk (the first step is to create a folder, and then the second step is to save the resource to this folder)
In this way, we can see that there are two obvious requests:
# Request to create a folder https://pan.baidu.com/api/create?a=commit&channel=chunlei&app_id=250528&bdstoken=undefined&channel=chunlei&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d&logid=MTU3OTYwNDg1NTE3ODAuNTkxMDExODM4OTIwNDg1Mw==&clienttype=0
# Request to transfer resources https://pan.baidu.com/share/transfer?shareid=3153250388&from=3821724077&ondup=newcopy&async=1&channel=chunlei&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d&logid=MTU3OTYwNDg1NTE3ODAuNTkxMDExODM4OTIwNDg1Mw==&clienttype=0
First, let's look at the post request in the folder creation section:
https://pan.baidu.com/api/create?a=commit&channel=chunlei&app_id=250528&bdstoken=undefined&channel=chunlei&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d&logid=MTU3OTYwNDg1NTE3ODAuNTkxMDExODM4OTIwNDg1Mw==&clienttype=0
querystring is similar to the above. Only the logid needs to be changed, mainly the data carried
| parameter | value | state |
|---|---|---|
| isdir | 1 | fixed |
| size | empty | fixed |
| method | post | fixed |
| dataType | json | fixed |
| path | /Animation / Douluo mainland-20180062 01-latest | custom |
It can be seen that other things need not be moved. When we send a post request, we just need to bring a custom path
self.create_dir_post = 'https://pan.baidu.com/api/create?a=commit&channel=chunlei' \ '&app_id=250528&bdstoken=undefined&channel=chunlei&web=1' \ '&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d' \ '&logid={}&clienttype=0' self.headers = { 'User-Agent': self.user_agent, 'Host': 'pan.baidu.com', 'Connection': 'keep-alive', 'Accept': 'application/json, text/javascript, */*; q=0.01', 'Origin': 'https://pan.baidu.com', 'X-Requested-With': 'XMLHttpRequest', 'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8', 'Sec-Fetch-Site': 'same-origin', 'Sec-Fetch-Mode': 'cors', 'Accept-Encoding': 'gzip, deflate, br', 'Accept-Language': 'zh-CN,zh;q=0.9', } logid = self.get_logid(baiduid) create_path = '/Comic/' + source_filename # data parameters required for new folder request self.create_dir_data['path'] = create_path self.headers['Referer'] = s_url self.headers['Cookie'] = bdclnd + ';' + self._stoken_bduss r_create_dir = requests.post(self.create_dir_post.format(logid), data=self.create_dir_data, headers=self.headers, verify=False) print(r_create_dir.json())
After the request is successful, you can see that you have created a folder named by yourself in your network disk
And the next post is to implement the content transfer
https://pan.baidu.com/share/transfer?shareid=3153250388&from=3821724077&ondup=newcopy&async=1&channel=chunlei&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d&logid=MTU3OTYwNDg1NTE3ODAuNTkxMDExODM4OTIwNDg1Mw==&clienttype=0
| parameter | value | state |
|---|---|---|
| shareid | 3153250388 | change |
| from | 3821724077 | change |
| logid | MTU3OTYwNDg1NTE3ODAuNTkxMDExODM4OTIwNDg1Mw== | change |
In addition to these three other querystring s, the parameters are fixed. Let's look at the data carried by post
| parameter | value | state |
|---|---|---|
| fsidlist | [597498773956140] | change |
| path | /Animation / Douluo mainland-20180062 01-latest | change |
path needs to be constructed by yourself. logid, we have talked about the generation method before, and the key is the remaining three parameters: shareid, from, fsidlist
Where can I find this parameter
In fact, think about it carefully. These three parameters must be in the previous page source code or Js code. Before that, we could successfully visit a page like https://pan.baidu.com/s/1xxx, but we didn't pay attention to the content of the page source code of this page. Think again that these three parameters are used in the process of transferring, and the transferred page is exactly in this https://pa n. Baidu.com/s/1xxx page
So it's not hard to find that the source code of this page has such contents
yunData.SHAREPAGETYPE = "multi_file";
yunData.MYUK = "4503602932392500";
yunData.SHARE_USER_NAME = "fci****re2";
// This is share? ID-----------------------------------
yunData.SHARE_ID = "3151703641";
yunData.SIGN = "8e9fc93e128935d2b43ed0cb267c8bca964e33af";
yunData.sign = "8e9fc93e128935d2b43ed0cb267c8bca964e33af";
yunData.TIMESTAMP = "1579608010";
// This is from-----------------------------------
yunData.SHARE_UK = "3821724077";
yunData.SHARE_PUBLIC = 0;
yunData.SHARE_TIME = "1579087633";
yunData.SHARE_DESCRIPTION = "";
yunData.MYSELF = +false;
yunData.MYAVATAR = "https:\/\/ss0.bdstatic.com\/7Ls0a8Sm1A5BphGlnYG\/sys\/portrait\/item\/netdisk.1.c8d8ac7b.54y40Nw_2ayb-Pg7hPetiA.jpg";
yunData.NOVELID = "";
// This is fsidlist-----------------------------------
yunData.FS_ID = "540067849856680";
yunData.FILENAME = "20190069 Scientific super electromagnetic gun T";
yunData.PATH = "\/sharelink3821724077-540067849856680\/20190069 Scientific super electromagnetic gun T";
yunData.PATH_MD5 = "10451130099679229426";
yunData.CTIME = "1579087633";
yunData.CATEGORY = "6";
So as long as you can visit this page, extract these three parameters with regular, and then construct the url to send the request, it will be solved
This is the final code:
self._stoken_bduss = 'This part of the browser cookie Copy paste in' self.pan_post = 'https://pan.baidu.com/share/verify?surl={}&t={}&channel=chunlei' \ '&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d' \ '&logid={}&clienttype=0' self.create_dir_post = 'https://pan.baidu.com/api/create?a=commit&channel=chunlei' \ '&app_id=250528&bdstoken=undefined&channel=chunlei&web=1' \ '&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d' \ '&logid={}&clienttype=0' self.transfer_post = 'https://pan.baidu.com/share/transfer?shareid={}' \ '&from={}&ondup=newcopy&async=1&channel=chunlei' \ '&web=1&app_id=250528&bdstoken=08a7da93cf25d7935788a123e3e10c3d' \ '&logid={}&clienttype=0' self.pan_s_url = 'https://pan.baidu.com/s/1{}' self.create_dir_data = { 'isdir': '1', 'size': '', 'block_list': [], 'method': 'post', 'dataType': 'json' } self.pwd_data = { 'vcode': '', 'vcode_str': '', } self.headers = { 'User-Agent': self.user_agent, 'Host': 'pan.baidu.com', 'Connection': 'keep-alive', 'Accept': 'application/json, text/javascript, */*; q=0.01', 'Origin': 'https://pan.baidu.com', 'X-Requested-With': 'XMLHttpRequest', 'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8', 'Sec-Fetch-Site': 'same-origin', 'Sec-Fetch-Mode': 'cors', 'Accept-Encoding': 'gzip, deflate, br', 'Accept-Language': 'zh-CN,zh;q=0.9', } self.t = int(round(time.time() * 1000)) def get_logid(self, baidu_id): with open('boot.js', encoding='utf-8') as f: bootjs = f.read() js_obj = execjs.compile(bootjs) res = js_obj.call('getLogId', baidu_id) # print(res) return res def enter_pwd(self, source_filename, pan_url, pan_pwd): """ //Run the code generating the logid through execjs, obtain the parameter followed by the password and send the post request together, and add the BDCLND parameter returned as a cookie to get 'https://In the request header of pan.baidu.com/s/1xxx ', you can normally access the resource file page """ session = requests.session() # Request the url of the network disk resource that requires a password; verify=False to avoid frequent attempts to block and disconnect SSL, but this request is not secure r_baiduid = session.get(pan_url, headers={'user-agent': self.user_agent}, verify=False) # Get the current BAIDUID to generate the logid baiduid = r_baiduid.cookies['BAIDUID'] logid = self.get_logid(baiduid) surl = pan_url.split('surl=')[1] self.pwd_data['pwd'] = pan_pwd self.headers['Referer'] = pan_url # post request with password, you can visit 'https://pan.baidu.com/s/1xxx' page successfully r = session.post(self.pan_post.format(surl, self.t, logid), data=self.pwd_data, headers=self.headers, verify=False) # Return json data with randsk to get bdclnd bdclnd = 'BDCLND=' + r.json()['randsk'] # Visit the request header of 'https://pan.baidu.com/s/1xxx' self.headers['Cookie'] = bdclnd # 'https://pan.baidu.com/s/1xxx' s_url = self.pan_s_url.format(surl) r_s_url = session.get(s_url, headers=self.headers, verify=False) r_s_url.encoding = 'utf-8' # Three parameters needed to obtain post request of transfer resources by regular params = re.findall(r'yunData\.SHARE_ID = "(.*?)";.*?yunData\.SHARE_UK = "(.*?)";.*?yunData\.FS_ID = "(.*?)";', r_s_url.text, re.S)[0] # Call new folder and transfer request self.create_dir(baiduid, s_url, source_filename, params, bdclnd) def create_dir(self, baiduid, s_url, source_filename, params, bdclnd): logid = self.get_logid(baiduid) shareid, from_id, fsidlist = params[0], params[1], params[2] transfer_url = self.transfer_post.format(shareid, from_id, logid) create_path = '/Comic/' + source_filename # data parameters required for new folder request self.create_dir_data['path'] = create_path self.headers['Referer'] = s_url self.headers['Cookie'] = bdclnd + ';' + self._stoken_bduss # Two parameters BDUSS and STOKEN are required r_create_dir = requests.post(self.create_dir_post.format(logid), data=self.create_dir_data, headers=self.headers, verify=False) print(r_create_dir.json()) # Three parameters BDUSS, BDCLND and STOKEN are required r_transfer = requests.post(transfer_url, data={'fsidlist': '[' + str(fsidlist) + ']', 'path': create_path}, headers=self.headers, verify=False) print(r_transfer.text)
Explain that the three parameters, source filename, pan URL and pan PWD, are part of path, link of resources and password of resources
In addition, there is the operation version of selenium, so I put the code directly
Selenium operation
def s_enter_pwd(self, source_filename, pan_url, pan_pwd): """ selenium Input password for operation """ browser = webdriver.Chrome() browser.get(pan_url) time.sleep(3) if '404' in browser.current_url: print('404,Page not found') self.update_status(pan_url) time.sleep(10) browser.close() # print(browser.page_source) # Enter password automatically browser.find_element_by_id("wkwj9A").send_keys(pan_pwd) time.sleep(2) # Auto CR browser.find_element_by_id("wkwj9A").send_keys(Keys.ENTER) time.sleep(5) print(browser.current_url) # Click Save to online disk to open the login box browser.find_element_by_css_selector('.g-button.g-button-blue').click() time.sleep(5) # Enter account password browser.find_element_by_id("TANGRAM__PSP_10__footerULoginBtn").click() time.sleep(3) browser.find_element_by_id("TANGRAM__PSP_10__userName").send_keys(self.username) browser.find_element_by_id("TANGRAM__PSP_10__password").send_keys(self.password) browser.find_element_by_id("TANGRAM__PSP_10__submit").click() # If rotation verification code appears try: slid_ing = browser.find_element_by_class_name('vcode-spin-button') if slid_ing: while True: ActionChains(browser).click_and_hold(on_element=slid_ing).perform() time.sleep(0.2) for track in [0, 0, 0, 1, 1, 1, 1, 2, 2, 2, 3, 3, 3, 3, 3, 4, 4, 4, 4]: ActionChains(browser).move_by_offset(xoffset=track, yoffset=0).perform() try: ActionChains(browser).release(on_element=slid_ing).perform() except: break except NoSuchElementException as e: print(e) time.sleep(10) browser.find_element_by_css_selector('.Qxyfvg.fydGNC').click() time.sleep(2) # Click Save to online disk again browser.find_element_by_css_selector('.g-button.g-button-blue').click() time.sleep(2) browser.find_element_by_xpath('//*[@id="fileTreeDialog"]/div[2]/div/ul/li/ul/li[4]/div/span').click() time.sleep(2) browser.find_element_by_css_selector('.icon.icon-newfolder').click() time.sleep(3) browser.find_element_by_css_selector('.input.shareFolderInput').clear() browser.find_element_by_css_selector('.input.shareFolderInput').send_keys(source_filename) browser.find_element_by_css_selector('.input.shareFolderInput').send_keys(Keys.ENTER) time.sleep(2) browser.find_element_by_css_selector('.treeview-node.treenode-empty.treeview-node-on').click() browser.find_element_by_xpath('//*[@id="fileTreeDialog"]/div[3]/a[2]').click() time.sleep(30) browser.close()
Memo
import time import datetime t = time.time() print (t) #Original time data 1552267863.7501628 print (int(t)) #Second time stamp 1552267863 print (int(round(t * 1000))) #Millisecond time stamp 1552267863750 nowTime = lambda:int(round(t * 1000)) print (nowTime()); #Millisecond timestamps based on lambda 1552267863750 print (datetime.datetime.now().strftime('%Y-%m-%d %H:%M:%S')) #Date format 2019-03-11 09:31:03
Reference resources
python3 crawler (5) Baidu cloud disk violent cracking attempt
OpenSSL.SSL.Error: [('SSL routes',' TLS \ process \ server \ certificate ',' certificate verify failed ')] (SSL certificate problem)
Python 3 + selenium common syntax summary
https://www.52pojie.cn/thread-1059883-1-1.html
Insert a code slice here

