Proficient in Office 365 Cloud Computing Management Exchange Online
Chapter 1 Beginning with Office 365
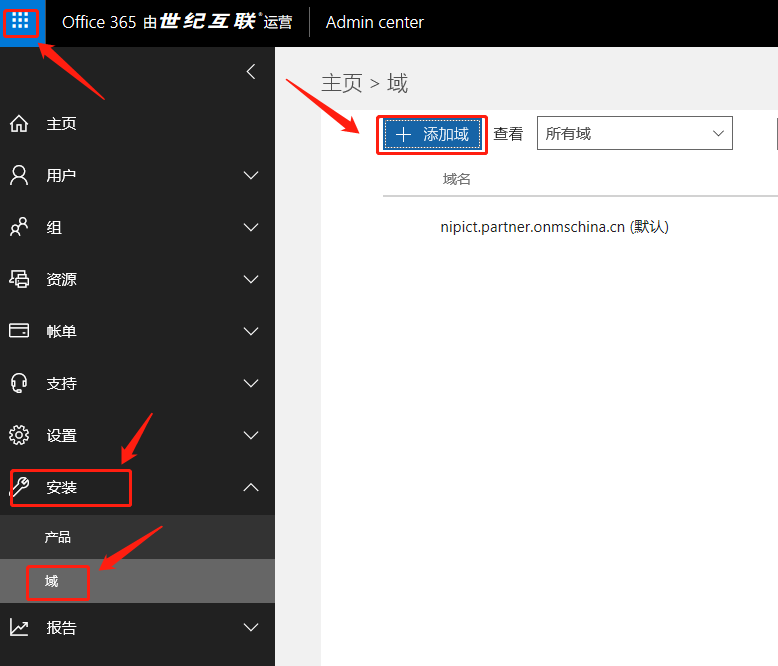
1.1 Domain Name Management
Registering Century Interconnected Office 365 will result in an initial Office 365 domain name: XXX.partner.onmschina.cn
Administrator login office 365 portal: left "navigation bar" -- "installation" -- "domain" -- "add domain":
https://portal.partner.microsoftOnline.cn
2. Manage OFfice 365 through PowerShell:
2.1 Install Azure AD Module:
Install-Module AzureAD
Install-Module Msonline
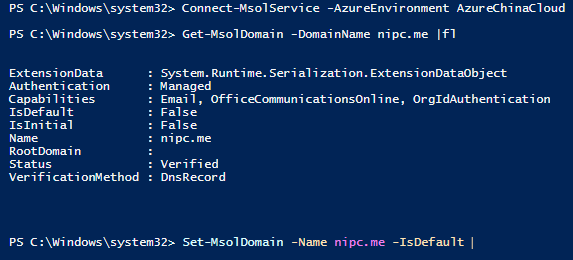
Connect-MsolService -AzureEnvironment AzureChinaCloud
Get-MsolDomain -DomainName nipc.me |fl
Set default domain:
Set-MsolDomain -Name nipc.me -IsDefault
Get-MsolDomain
Delete Domain:
Remove-MsolDomain -DomainName nipc.me
If a custom domain name is bound to the Office 365 Global Edition, even if it is added to the Office 365 Chinese Edition, the domain name will be missing from the Accepted Domain of the Exchange Administration Center in the Chinese Edition, resulting in malfunctioning of the mailbox.
1.2 User Management
Create user:
Required properties for creating users:
DisplayName Display Name
UserPrincipalName username eg for login to Office 365 service: XXX@nipict.partner.onmschina.cn
New-MsolUser -DisplayName "Gan Zhiyan" -UserPrincipalName ganzy@nipc.me -FirstName Gan -LastName Zhiyan -UsageLocation CN -LicenseAssignment reseller-account:O365_BUSINESS_PREMIUM
Query licenses for subscriptions:
Get-MsolAccountSku
AccountSkuId ActiveUnits WarningUnits ConsumedUnits
------------ ----------- ------------ -------------
reseller-account:O365_BUSINESS_ESSENTIALS 0 0 2
reseller-account:O365_BUSINESS_PREMIUM 2 0 2
Create users in bulk:
Prepare a CSV file with the appropriate properties: DisplayName, UserPrincipalName, FirstName, LastName, UsageLocation, LicenseAssignment(AccountSkuId)
Create users in bulk through Powershell:
Import-Csv -Path "C:\users.csv" | foreach {New-MsolUser -DisplayName $_.DisplayName -UserPrincipalName $_.UserPrincipalName -FirstName $_.FirstName -LastName $_.LastName -UsageLocation $_.UsageLocation -LicenseAssignment $_.AccountSkuId} | Export-Csv -Path "C:\Results.csv"
Administrator privilege role:
Get-MsolUser | where Displayname -Like "gan*" | sort displayname | select Displayname | more
Get the administrator role name and description:
Get-MsolRole | sort name | select Name,Description
Name Description
---- -----------
Application Administrator Can create and manage all aspects of app registrations and enterprise apps.
Application Developer Can create application registrations independent of the 'Users can register applications' setting.
Authentication Administrator Allowed to view, set and reset authentication method information for any non-admin user.
Azure DevOps Administrator Can manage Azure DevOps organization policy and settings.
Azure Information Protection Administrator Can manage all aspects of the Azure Information Protection product.
B2C IEF Keyset Administrator Can manage secrets for federation and encryption in the Identity Experience Framework (IEF).
B2C IEF Policy Administrator Can create and manage trust framework policies in the Identity Experience Framework (IEF).
B2C User Flow Administrator Can create and manage all aspects of user flows.
B2C User Flow Attribute Administrator Can create and manage the attribute schema available to all user flows.
Billing Administrator Can perform common billing related tasks like updating payment information.
Cloud Application Administrator Can create and manage all aspects of app registrations and enterprise apps except App Proxy.
Cloud Device Administrator Full access to manage devices in Azure AD.
Company Administrator Can manage all aspects of Azure AD and Microsoft services that use Azure AD identities.
Compliance Administrator Can read and manage compliance configuration and reports in Azure AD and Office 365.
Compliance Data Administrator Creates and manages compliance content.
Conditional Access Administrator Can manage conditional access capabilities.
CRM Service Administrator Can manage all aspects of the Dynamics 365 product.
Customer LockBox Access Approver Can approve Microsoft support requests to access customer organizational data.
Desktop Analytics Administrator Can access and manage Desktop management tools and services.
Device Administrators Device Administrators
Device Join Device Join
Device Managers Deprecated - Do Not Use.
Device Users Device Users
Directory Readers Can read basic directory information. Commonly used to grant directory read access to applications and guests.
Directory Synchronization Accounts Only used by Azure AD Connect service.
Directory Writers Can read and write basic directory information. For granting access to applications, not intended for users.
Exchange Service Administrator Can manage all aspects of the Exchange product.
External Identity Provider Administrator Can configure identity providers for use in direct federation.
Global Reader Can read everything that a global admin can read but not update anything.
Groups Administrator Members of this role can create/manage groups, create/manage groups settings like naming and expiration policies, and view ...
Guest Inviter Can invite guest users independent of the 'members can invite guests' setting.
Helpdesk Administrator Can reset passwords for non-administrators and Helpdesk Administrators.
Intune Service Administrator Can manage all aspects of the Intune product.
Kaizala Administrator Can manage settings for Microsoft Kaizala.
License Administrator Can manage product licenses on users and groups.
Lync Service Administrator Can manage all aspects of the Skype for Business product.
Message Center Privacy Reader Can read security messages and updates in Office 365 Message Center only.
Message Center Reader Can read messages and updates for their organization in Office 365 Message Center only.
Office Apps Administrator Can manage Office apps cloud services, including policy and settings management, and manage the ability to select, unselect...
Partner Tier1 Support Do not use - not intended for general use.
Partner Tier2 Support Do not use - not intended for general use.
Password Administrator Can reset passwords for non-administrators and Password Administrators.
Power BI Service Administrator Can manage all aspects of the Power BI product.
Printer Administrator Can manage all aspects of printers and printer connectors.
Printer Technician Can manage all aspects of printers and printer connectors.
Privileged Authentication Administrator Allowed to view, set and reset authentication method information for any user (admin or non-admin).
Privileged Role Administrator Can manage role assignments in Azure AD, and all aspects of Privileged Identity Management.
Reports Reader Can read sign-in and audit reports.
Search Administrator Can create and manage all aspects of Microsoft Search settings.
Search Editor Can create and manage the editorial content such as bookmarks, Q and As, locations, floorplan.
Security Administrator Security Administrator allows ability to read and manage security configuration and reports.
Security Operator Creates and manages security events.
Security Reader Can read security information and reports in Azure AD and Office 365.
Service Support Administrator Can read service health information and manage support tickets.
SharePoint Service Administrator Can manage all aspects of the SharePoint service.
Teams Communications Administrator Can manage calling and meetings features within the Microsoft Teams service.
Teams Communications Support Engineer Can troubleshoot communications issues within Teams using advanced tools.
Teams Communications Support Specialist Can troubleshoot communications issues within Teams using basic tools.
Teams Service Administrator Can manage the Microsoft Teams service.
User Account Administrator Can manage all aspects of users and groups, including resetting passwords for limited admins.
Workplace Device Join Workplace Device Join
Assign roles to accounts:
Add-MsolRoleMember -RoleMemberEmailAddress gan@nipc.me -RoleName "Exchange Service Administrator"
Assign roles to multiple users:
Create a CSV file that includes the display name DisplayName and the role name RoleName
DisplayName,RoleName
"Gan Zhiyan","Exchange Service Administrator"
"Joe Xiao","SharePoint Service Administrator "
"Eric Yan","Helpdesk Administrator"
Next, run the following command:
Import-Csv -Path "C:\RoleAdd.csv" | foreach {Add-MsolRoleMember -RoleMemberEmailAddress (Get-MsolUser | Where DisplayName -eq $_.DisplayName).UserPrincipalName -RoleName $_.RoleName } | Export-Csv -Path "C:\RoleAddResults.csv"
Note: Users can only be assigned administrator roles, not groups.
1.2.2 Delete users:
Delete single user:
Remove-MsolUser -UserPrincipalName gan@nipc.me
No prompt to confirm:
Remove-MsolUser -UserPrincipalName gan@nipc.me -Force
If it is a directory synchronization account, the next synchronization after deletion will be restored to the active user, so for directory synchronization users, the best way is to delete or not synchronize this user object locally.
Delete all users at once:
$users=get-msoluser
$users | Remove-MsolUser –Force
$users=Get-MsolUser -All -ReturnDeletedUsers
$users | Remove-MsolUser -RemoveFromRecycleBin -force
Remove user licenses:
Get-MsolAccountSku
Get-MsolUser -All | select UserPrincipalName,Licenses
Remove licenses from existing users and use Set-MsolUserLicense with parameters-RemoveLicenses multiple licenses separated by commas.
Set-MsolUserLicense -UserPrincipalName gan@nipc.me -RemoveLicenses "reseller-account:O365_BUSINESS_PREMIUM","reseller-account:O365_BUSINESS_ESSENTIALS"
Soft and hard delete users
Soft Delete Users are stored in Deleted Users. Within 30 days before permanently deleting user data, licenses can also be restored and assigned, and users can still access data and services normally.
Hard deletion is when a user's mailbox has been soft deleted for more than 30 days and the associated Office 365 user has been hard deleted.All mailbox content, such as e-mail, contacts, and files, will be permanently deleted.
Connect to Exchange Online with the following Powershell:
$USerCredential = Get-Credential
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://partner.outlook.cn/PowerShell-LiveID/ -Credential $USerCredential -Authentication Basic -AllowRedirection
Import-PSSession $Session
Get information about soft delete mailboxes:
Get-Mailbox -SoftDeletedMailbox | Select-Object Name, ExchangeGuid
Restore mailbox:
New-MailboxRestoreRequest -SourceMailbox <ExchangeGuid> -TargetMailbox <Guid from new Target mailbox>
View the recovery results:
Get-MailboxRestoreRequest
Manage user licenses
Obtain the licensing plans in the current organization and the services and order contained in each plan (index number)
(Get-MsolAccountSku | where {$_.AccountSkuid -eq 'reseller-account:O365_BUSINESS_PREMIUM' }).ServiceStatus
ServicePlan ProvisioningStatus
----------- ------------------
Microsoft Bookings Success
SHAREPOINTWAC Success
SHAREPOINTSTANDARD Success
OFFICE_BUSINESS Success
MCOSTANDARD Success
EXCHANGE_S_STANDARD Success
If you only want users to disable using other Exchange Online services, then assign them.
First, define a license variable.
$LO = New-MsolLicenseOptions -AccountSkuId 'reseller-account:O365_BUSINESS_PREMIUM' -DisabledPlans 'Microsoft Bookings','SHAREPOINTWAC','SHAREPOINTSTANDARD','MCOSTANDARD'
New-MsolUser -UserPrincipalName gan@nipc.me -DisplayName "Gan" -LicenseAssignment "reseller-account:O365_BUSINESS_PREMIUM" -LicenseOptions $LO -UsageLocation CN
If you have multiple users, you can create a txt file with one user account on each line:
The batch operations are as follows:
Get-Content "C:\Accounts.txt" | foreach {Set-MsolUserLicense -UserPrincipalName $_ -LicenseOptions $LO}
Multiple Authentication (MFA) in 1.2.4 Office 365:
Active Users select Multiple Authentication Settings from the More drop-down list
New authentication needs to be enabled in Exchange Online as well when the user has MFA.Exchange Online PowerShell:
Get-OrganizationConfig | ft -Auto Name,OAuth*
See if OAuth2ClientProfileEnabled is Ture
If the result is False, change to Ture with the following command:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
Chapter 2 Exchange Online Management
2.1 Recipients
The recipient is any enabled mail object to which the message can be delivered or routed.
Each recipient type has a unique value in the RecipientTypeDetails property of Exchange Online PowerShell
2.1.1 User Mailbox
1. Create user mailboxes:
Active users automatically create user mailboxes when assigning Exchange online licenses.
2. Delete mailbox
Remove-Mailbox -Identity gan@nipc.me
Permanently delete the user's mailbox, which cannot be recovered after deletion:
Remove-MsolUser -UserPrincipalName gan@nipc.me -RemoveFromRecycleBin
After the mailbox has been deleted, it can be verified by Get-Mailbox <identity>. When an error is returned and the mailbox cannot be found, it means it has been deleted.
When a mailbox is deleted, Exchange Online will retain the mailbox and all content for 30 days if litigation or in-place retention is not enabled. After 30 days, permanent deletion cannot be restored.
If the mailbox was deleted by revoking the Exchange Online license, you can redistribute the license within 30 days to restore the mailbox.
If deleted through Active User, you can restore the user from Deleted User within 30 days to restore the mailbox.
3. Manage e-mail addresses:
Administrators can add a "primary SMTP address" and "proxy address" with multiple "aliases" for the same user's mailbox (up to 400).