Permission management under Linux
Permission management under Linux
1. How to view and read permission information
[1]ls
| ls -l file | Enter the specified directory |
|---|---|
| ls -d dir | View catalog itself |
| ls -a dir | All files contain hidden |
| ls -S dir | View and sort by size |
| ls -s dir | View file size |
This part has also appeared in linux command line operation and file management. To master more commands and their functions, please see the previous blog linux command line operation and file management
L l will be used below, so I inquired the following information: ll will list all file information under the file, including hidden files, while ls -l will only list display files, and the information listed by ll command is more detailed, with time, whether it is readable or writable, etc
[2] View file properties
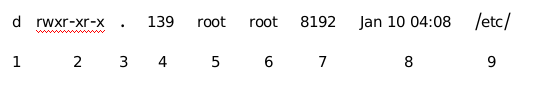
//How to view file properties [root@workstation Desktop]# ls -l /etc/shadow ----------. 1 root root 1338 Jan 10 02:48 /etc/shadow //How to view catalog properties [root@workstation Desktop]# ls -ld /etc/ drwxr-xr-x. 139 root root 8192 Jan 10 04:08 /etc/
Note that we need to remember the function of ls parameters in [1]
[3] Understanding of each field of property
- Understand the fields of file properties

| field | attribute |
|---|---|
| 1 | type |
| 2 | file right |
| 3 | SELinux Context |
| 4 | Number of file hard links |
| 5 | File owner |
| 6 | File ownership group |
| 7 | file size |
| 8 | Last time the file was modified |
| 9 | File name |
- Understand the fields of catalog properties
| field | attribute |
|---|---|
| 1 | type |
| 2 | directory right |
| 3 | SELinux Context |
| 4 | Number of subdirectories in the directory |
| 5 | File owner |
| 6 | File ownership group |
| 7 | Metadata size of self file or subdirectory in directory |
| 8 | Last time directory was modified |
| 9 | Directory name |
-
Field 1 is a special case.
-Represents directory or link file, etc., d represents directory, such as drwx ------. l indicates the linked file, such as lrwxrwxrwx; if it is indicated by a "-" column, it indicates that it is a file. -
Field 2, representing the properties of the file.
Linux files are basically divided into three attributes: readable (r), writable (w), and executable (x). The grid of this part is one unit for every three grids. Because Linux is a multi-user and multi task system, a file may be used by many people at the same time, so we must set the permissions of each file. The order of the permissions of the file is (take - rwxrxrxrxrx as an example): rwx(Owner)r-x(Group)r-x(Other)
– this example shows the permissions: users can read, write, and execute; users in the same group can read, write, and execute; other users can read, write, and execute.
– in addition, the execution part of some program attributes is not X, but S, which means that the user executing the program can temporarily have the same authority as the owner to execute the program. Generally appear in the system management and other instructions or programs, so that the user has root identity when executing. -
Field 4 indicates the number of files.
- if it's a file, the number is 1. If it's a directory, the number is the number of files in the directory. For example, the code in the following section explains the number of directories.
(Note: in the following example, you can see that we did not create new files and subdirectories under the directory "westos", but the number is 2 at this time, because it contains the hidden directories "." and " ", so it's 2.)
[root@workstation Desktop]# mkdir westos [root@workstation Desktop]# ls -l /mnt/ total 0 drwx------. 2 1001 linux 6 Jan 10 01:26 westos
- Field 5, indicating the owner of the file or directory.
– if the user is currently in his / her own Home, this column is probably his / her account name.
-
Field 6, indicating the group to which it belongs.
– each user can have more than one group, but most users should belong to only one group. Only when the system administrator wants to give a user special permission, can another group be given to him. -
Field 7, representing the file size.
– the file size is expressed in bytes, while the empty directory is generally 1024byte. You can use other parameters to make the file display in different units, such as ls
- k is to display the size unit of a file in kb, but generally we still use byte as the main unit.
Note: for example, the code in the following section explains the size of the file installed when it is a directory. Create a new directory "westos". At this time, no new files or directories are created in "westos", but the number represented by field 3 is already 6. The reasons are as follows: the original is 6, because it contains [". [3] and" "[3]] there are 6 in total, so 6 represents the original ownership and (3+3)]
[root@workstation Desktop]# mkdir westos [root@workstation Desktop]# ls -l /mnt/ total 0 drwx------. 2 1001 linux 6 Jan 10 01:26 westos
-
Field 8, representing the creation date.
– in the format of "month, day, time", for example, Jan 10 01:26 means 1:26 a.m. on January 10. -
Field 9 for the file name.
– we can use ls – a to show hidden filenames.
[3] Practice
Why 63 (for example)
[root@workstation mnt]# ls -Rl /mnt/
/mnt/:
total 0
drwxr-xr-x. 2 root root 63 Jan 8 22:41 westos
/mnt/westos:
total 0
-rw-r–r--. 1 root root 0 Jan 8 22:41 file
-rw-r–r--. 1 root root 0 Jan 8 22:11 redhat1
-rw-r–r--. 1 root root 0 Jan 8 22:11 redhat2
-rw-r–r--. 1 root root 0 Jan 8 22:11 redhat3
63 = 8 (8 bits before the name) * 4 lines + 4 (file) + 21 (redhat{1) 3} ) + 6 (. And...)
2. Set the owner and ownership group of the file
[1] Division of identity
- Because Linux is a multi-user and multi task system, a file may be used by many people at the same time. In order to consider everyone's privacy and everyone's favorite working environment, users are classified. (take - rwxrxrxrx as an example): rwx(Owner)r-x(Group)r-x(Other)
This example shows permissions: users can read, write, and execute; users in the same group can read, write, and execute; other users can read, write, and execute. - File owner and ownership group can only be modified by root
[2] Change method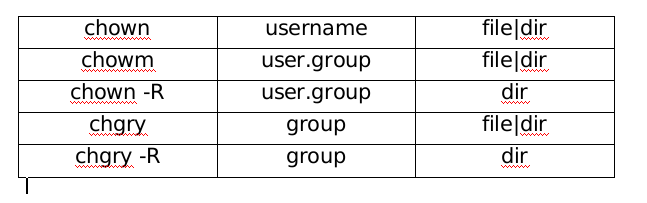 Practice
Practice
[root@workstation ~]# chown haha /mnt/file1 [user] [root@workstation ~]# chown student:haha /mnt/file2 [user] [root@workstation ~]# chown haha.student /mnt/file3 [user] [root@workstation ~]# chgrp student /mnt/westos [group] [root@workstation ~]# Chown. Student / MNT / file1 [group] [root@workstation ~]# Chown: student / MNT / File2 [group] /mnt: total 0 -rw-r--r--. 1 haha student 0 Jan 8 20:40 file1 -rw-r--r--. 1 student student 0 Jan 8 20:40 file2 -rw-r--r--. 1 haha student 0 Jan 8 20:40 file3 drwxr-xr-x. 2 root student 51 Jan 8 20:40 westos [2 Because there are hidden directories . and..]
3. Understand the impact of various permission types on files
[1] File permission read
- Linux files are basically divided into three attributes: readable (r), writable (w), and executable (x). The grid of this part is one unit for every three grids. Because Linux is a multi-user and multi task system, a file may be used by many people at the same time, so we must set the permissions of each file. The order of the permissions of the files is (take - rwxrxrxrx-x as an example):
rwx(Owner)r-x(Group)r-x(Other)
– this example shows the permissions: users can read, write, and execute; users in the same group can read, write, and execute; other users can read, write, and execute. - – in addition, the execution part of some program attributes is not X, but S, which means that the user executing the program can temporarily have the same authority as the owner to execute the program. Generally appear in the system management and other instructions or programs, so that the user has root identity when executing.
Permission type
- "-" permission closed: this bit of permission is not opened
- "r" (read view permission):
For files, you can view the contents of the files;
For a directory, list the file names in the directory. - "w" (writeable permission):
For the document, the contents of the document record can be changed;
Create a new file or directory in the new directory, delete the existing files and directories (regardless of the permissions of the sub files or sub directories), modify the name of the existing files or directories, and move the location of the files and directories in this directory. - "x" (execute permission):
Indicates that the user can switch paths to the current directory
4. Skillfully set authority
[1] Setting file permissions in character mode
Chmod < U / g / O / a > < R / w / x > target
Practice
chmod u+x /mnt/file chmod g-w /mnt/file1 chmod uo-x /mnt/file2 chmod g-x,o-w /mnt/file3 chmod o=rw- /mnt/file4
[2] Set file permissions in digital mode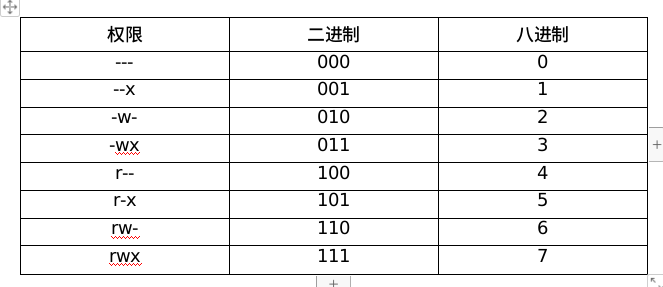
Practice
chmod 777 /mnt/file chmod 645 /mnt/file1 [at this time, the permission is rw-r--r-x]
[3] Permission copy
chmod --reference=Property source file TAG chmod --reference=/mnt/file westos
Compared with the command CP learned before, it can be found that cp-p will copy the permissions and the contents of the source file, and overwrite the contents of the target file. chmod --reference only copies the permissions
5. Permission reservation threshold umask
[1] Temporary changes
- Use umask to reserve permission in the system
- In the shell, you can use umask to view and set the reserved permission threshold [that is, umask reserved threshold]
- sudo delegation of power (it can be simply understood that it gives certain power to ordinary users, such as the example "haha workstation.lab.example.com = (root) NOPASSWD: / user/sbin/useradd" in the user management section, which means that in terms of creating new users, the power of root is given to ordinary users. But what umask modifies is permissions, that is, the permissions of file owners, file organizers and others.
In short: sudo is what we can do after devolution. umask is what ugo can do to files or directories after modifying permissions.
Practice
[root@workstation Desktop]# umask [View reserved permission threshold] 0022 [root@workstation Desktop]# umask 077 [set reserved permission threshold] [root@workstation Desktop]# umask 0077
[2] Permanent change
- shell configuration file / etc/bashrc
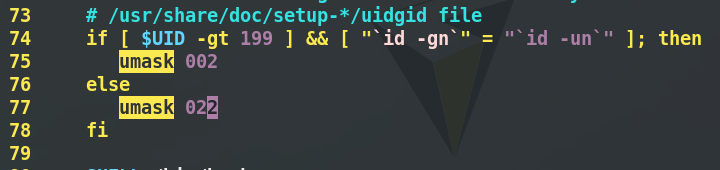
- System environment configuration file / etc/profile
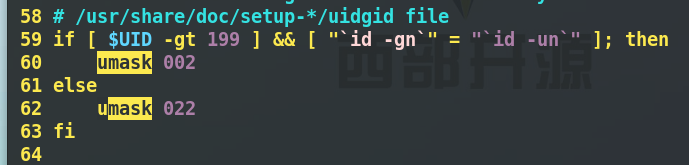
- Modification steps
[root@workstation Desktop]# vim /etc/bashrc [after entering the environment shown in Figure 1, / umask, change 022 to 077] [root@workstation Desktop]# vim /etc/profile [root@workstation Desktop]# source /etc/profile. ] [root@workstation Desktop]# umask 0077
6. Special permissions in the system
[1] . sticky
- Effect
Only valid for directory. When a directory has sticky permission, files in this directory can only be deleted by the owner of the file - Setting method (special permission o+t effect is equivalent to 1 original file)
chmod o+t dir
chmod 1xxx dir
[Command] watch -n 1 ls -l /mnt/ [Monitoring command] [root@workstation mnt]# cd /mnt/ [root@workstation mnt]# ls westos [root@workstation mnt]# chmod 777 /mnt/westos [root@workstation mnt]# chmod 1777 /mnt/westos / [o+t limit permission, operation verification user A can't delete files created by user B] [root@workstation mnt]# su student (process:20759): dconf-CRITICAL **: 00:48:36.215: unable to create directory '/run/user/0/dconf': Permission denied. dconf will not work properly. (process:20759): dconf-CRITICAL **: 00:48:36.215: unable to create directory '/run/user/0/dconf': Permission denied. dconf will not work properly. (process:20759): dconf-WARNING **: 00:48:36.221: failed to commit changes to dconf: Could not connect: Permission denied [student@workstation Desktop]$ exit exit [root@workstation mnt]# su - student [switch to student user] [student@workstation mnt]$ cd westos [student@workstation westos]$ touch studentfile [student User created a file] [student@workstation westos]$ exit exit [root@workstation mnt]# su - westos [switch to the user of weatos, which does not exist at this time] su: user westos does not exist [root@workstation mnt]# User add westos [root@workstation mnt]# su - westos [switch to westos user] [westos@workstation ~]$ cd /mnt/westos [westos@workstation westos]$ touch westosfile [Set up documents] [westos@workstation westos]$ rm -fr westosfile [Delete self created documents] [westos@workstation westos]$ rm -fr studentfile rm: cannot remove 'studentfile': Operation not permitted [westos Users can delete their own files, but in the chmod 1777 westos Can't delete student User created documents]>>>[Verify that under the set permission, A User cannot delete B User created files. Files in this directory can only be deleted by the owner of the file]
[2] sgid (mandatory bit)
- Effect
For files: only for binary executable files, when there is sgid on the file, the process generated by anyone executing the file belongs to the file group
For a directory: when there is sgid permission on the directory, the files created by anyone in the directory belong to all groups of the directory
In short: what I have made should belong to Xiaomi company. When I create a file or directory, the owner of the file and the owning group are all me. But at this time, the identity of the group must be changed to the company to meet the reality. Therefore, it needs to be set to change the group of newly created files into the group of the original directory - Setting mode (g+s has the same effect as 2777)
chmod g+s file|dir
chmod 2xxx file|dir
g+s is the same as 2777
[Command] [root@workstation mnt]# chmod 2777 westos [root@workstation mnt]# su - student Last login: Thu Jan 9 01:38:01 EST 2020 on pts/2 [student@workstation ~]$ cd /mnt/westos [student@workstation westos]$ touch file1 [student@workstation westos]$ cd .. [student@workstation mnt]$ mkdir haha [student@workstation mnt]$ cd haha [student@workstation haha]$ touch redhat1 [student@workstation haha]$ chmod 2777 /mnt/haha [student@workstation haha]$ exit logout [root@workstation mnt]# touch redhat5 /mnt/haha [root@workstation mnt]# rm -f redhat5 [root@workstation mnt]# su - westos Last login: Thu Jan 9 00:51:44 EST 2020 on pts/2 [westos@workstation ~]$ cd /mnt/haha [westos@workstation haha]$ touch file5
[Monitoring command] watch -n 1 ls -Rl /mnt /mnt: total 0 drwxrwsrwx. 2 student student 34 Jan 9 01:48 haha drwxrwsrwx. 2 root root 50 Jan 9 01:40 westos /mnt/haha: total 0 -rw-rw-r--. 1 westos student 0 Jan 9 01:48 file5 [Another one, student Set permissions under westos Created users belong to haha Original group of catalog student] -rw-rw-r--. 1 student student 0 Jan 9 01:46 redhat1 /mnt/westos: total 0 -rw-rw-r--. 1 student student 0 Jan 9 01:38 file -rw-rw-r--. 1 student root 0 Jan 9 01:40 file1 [student Created, but inherited under special permission settings root Group] -rw-rw-r--. 1 student student 0 Jan 9 00:49 studentfile
[3] suid (Adventure bit)
-
Effect
For and binary executables only. When there is a suid on the file, the process generated by anyone executing the program recorded in the file belongs to the owner of the file -
Setting mode
chmod u+s file
chmod 4xxx file
[Command] [root@workstation mnt]# ls -l /bin/cat -rwxr-xr-x. 1 root root 51856 Jan 11 2019 /bin/cat [root@workstation mnt]# cat ^C [root@workstation mnt]# chmod 2777 /bin/cat [root@workstation mnt]# su - student Last login: Thu Jan 9 01:39:24 EST 2020 on pts/2 [student@workstation ~]$ cat ^C [student@workstation ~]$ exit logout [root@workstation mnt]# chmod u+s /bin/cat [root@workstation mnt]# su - student Last login: Thu Jan 9 02:05:19 EST 2020 on pts/1 [student@workstation ~]$ cat ^C [student@workstation ~]$ exit logout [root@workstation mnt]# chmod 777 /bin/cat [root@workstation mnt]# su - student Last login: Thu Jan 9 02:06:23 EST 2020 on pts/1 [student@workstation ~]$ cat
7.ACL permission list
[1] Overview and notes of facel
- There are only three identities (owner, group, othe r) with three permissions (r,w,x),
There is no way to set specific permission requirements only for a user or a group. At this time, ACL (file Access control list, Access) must be used
Control List). - ==Note: = = so ACL has been added to all common Linux file system mount parameters by default, such as ext2/ext3/ext4/xfs, etc.), but RHEL 6.0 and earlier versions do not support ACL by default.
[2] acl list view
| getfacl file | Permission to view files opened by acl |
|---|---|
| # file: file | File name |
| # owner: root | File owner |
| # group: root | File ownership group |
| user::rw- | Authority of document owner |
| user:kiosk:rwx | Specify permissions for users |
| group::r– | File has group power |
| mask::rwx | The maximum power value that can be given to users |
| other::r– | Rights of others |
[3] Management of acl list
getfacl file
| setfacl -m u:username:rwx file | Set username to have rwx permission on file |
|---|---|
| setfacl -m g:group:rwx file | Set group members to have rwx permission on file |
| setfacl -x u:username file | Remove usernam from acl list |
| setfacl -b file | Close acl list on file |

