Passive information collection using Recon ng
Full feature web information search framework, developed based on Python.
Note: when reading this article, pay attention to reading the comments in the code at the same time.
1. Enter Recon ng environment
1.1 welcome interface
_/_/_/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/
_/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/
_/_/_/ _/_/_/ _/ _/ _/ _/ _/ _/ _/_/_/_/ _/ _/ _/ _/ _/_/_/
_/ _/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/
_/ _/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/
/\
/ \\ /\
Sponsored by... /\ /\/ \\V \/\
/ \\/ // \\\\\ \\ \/\
// // BLACK HILLS \/ \\
www.blackhillsinfosec.com
____ ____ ____ ____ _____ _ ____ ____ ____
|____] | ___/ |____| | | | |____ |____ |
| | \_ | | |____ | | ____| |____ |____
www.practisec.com
[recon-ng v5.1.1, Tim Tomes (@lanmaster53)]
[84] Recon modules
[14] Disabled modules
[8] Reporting modules
[4] Import modules
[2] Exploitation modules
[2] Discovery modules
[recon-ng][default] > # Command prompt, where you enter interactive mode
1.2 help interface
1.2.1 view commands available in interactive mode
[recon-ng][default] > help Commands (type [help|?] <topic>): --------------------------------- back Exits the current context dashboard Displays a summary of activity db Interfaces with the workspace's database exit Exits the framework help Displays this menu index Creates a module index (dev only) keys Manages third party resource credentials marketplace Interfaces with the module marketplace modules Interfaces with installed modules options Manages the current context options pdb Starts a Python Debugger session (dev only) script Records and executes command scripts shell Executes shell commands show Shows various framework items snapshots Manages workspace snapshots spool Spools output to a file workspaces Manages workspaces
1.2.2 viewing Recon ng command
$ recon-ng -h
usage: recon-ng [-h] [-w workspace] [-r filename] [--no-version] [--no-analytics]
[--no-marketplace] [--stealth] [--accessible] [--version]
recon-ng - Tim Tomes (@lanmaster53)
optional arguments:
-h, --help show this help message and exit
-w workspace load/create a workspace
-r filename load commands from a resource file
--no-version disable version check. Already disabled by default in Debian
--no-analytics disable analytics reporting. Already disabled by default in Debian
--no-marketplace disable remote module management
--stealth disable all passive requests (--no-*)
--accessible Use accessible outputs when available
--version displays the current version
2 work area
If you do not create a workspace, you will work in the default workspace of Recon ng. However, for the convenience of management, it is best to create an independent partition for independent tasks, and the data between partitions does not affect each other.
2.1 view existing workspace
[recon-ng][default] > workspaces list # List workspaces +----------------------------------+ | Workspaces | Modified | +----------------------------------+ | default | 2021-09-25 11:24:00 | | test1 | 2021-09-27 09:06:49 | | test2 | 2021-09-27 09:50:58 | +----------------------------------+
2.2 adding a new workspace
[recon-ng][default] > workspaces create demo # Create workspace [recon-ng][demo] > # After creation, it will automatically enter the workspace
2.3 entering a work area
Recon ng has two ways to enter a workspace.
In the interactive interface:
[recon-ng][demo] > workspaces load default # Import workspace [recon-ng][default] >
On the command line:
$ recon-ng -w demo
_/_/_/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/
_/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/
_/_/_/ _/_/_/ _/ _/ _/ _/ _/ _/ _/_/_/_/ _/ _/ _/ _/ _/_/_/
_/ _/ _/ _/ _/ _/ _/ _/_/ _/ _/_/ _/ _/
_/ _/ _/_/_/_/ _/_/_/ _/_/_/ _/ _/ _/ _/ _/_/_/
/\
/ \\ /\
Sponsored by... /\ /\/ \\V \/\
/ \\/ // \\\\\ \\ \/\
// // BLACK HILLS \/ \\
www.blackhillsinfosec.com
____ ____ ____ ____ _____ _ ____ ____ ____
|____] | ___/ |____| | | | |____ |____ |
| | \_ | | |____ | | ____| |____ |____
www.practisec.com
[recon-ng v5.1.1, Tim Tomes (@lanmaster53)]
[84] Recon modules
[14] Disabled modules
[8] Reporting modules
[4] Import modules
[2] Exploitation modules
[2] Discovery modules
[recon-ng][demo] >
2.4 working area parameters
2.4.1 display workspace parameters
[recon-ng][demo] > options list Name Current Value Required Description ---------- ------------- -------- ----------- NAMESERVER 8.8.8.8 yes default nameserver for the resolver mixin PROXY no proxy server (address:port) THREADS 10 yes number of threads (where applicable) TIMEOUT 10 yes socket timeout (seconds) USER-AGENT Recon-ng/v5 yes user-agent string VERBOSITY 1 yes verbosity level (0 = minimal, 1 = verbose, 2 = debug)
2.4.2 setting work area parameters
The workspace parameters here can also be skipped directly without setting and will not affect the results; But if you don't set parameters, it's easy for the other party to find that you scan him with Recon ng. Therefore, it is better to set it, and the scanning will be more hidden.
[recon-ng][demo] > options set USER-AGENT Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 # Set option values USER-AGENT => Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 [recon-ng][demo] > options list Name Current Value Required Description ---------- ------------- -------- ----------- NAMESERVER 8.8.8.8 yes default nameserver for the resolver mixin PROXY no proxy server (address:port) THREADS 10 yes number of threads (where applicable) TIMEOUT 10 yes socket timeout (seconds) USER-AGENT Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 yes user-agent string VERBOSITY 1 yes verbosity level (0 = minimal, 1 = verbose, 2 = debug)
3 DNS query
3.1 querying hosts
3.1.1 query process
[recon-ng][demo] > modules search brute # You can also search bing, baidu, shodan and other search engines
[*] Searching installed modules for 'brute'...
Exploitation
------------
exploitation/injection/xpath_bruter
Recon
-----
recon/domains-domains/brute_suffix
recon/domains-hosts/brute_hosts
[recon-ng][demo] > modules load recon/domains-hosts/brute_hosts # Introduce corresponding module
[recon-ng][demo][brute_hosts] > options list # Enumerate options
Name Current Value Required Description
-------- ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
WORDLIST /home/parallels/.recon-ng/data/hostnames.txt yes path to hostname wordlist
[recon-ng][demo][brute_hosts] > options set SOURCE nju.edu.cn # Set source
SOURCE => nju.edu.cn
[recon-ng][demo][brute_hosts] > run # Operation module
----------
NJU.EDU.CN
----------
...... # The specific query results are omitted
-------
SUMMARY
-------
[*] 92 total (92 new) hosts found.
3.1.2 display results
The query results will be saved in the database host table. You can view or obtain these data by using the show command or db query followed by SQL statements.
Using show:
[recon-ng][demo][brute_hosts] > show hosts +-----------------------------------------------------------------------------------------------------------------+ | rowid | host | ip_address | region | country | latitude | longitude | notes | module | +-----------------------------------------------------------------------------------------------------------------+ | 1 | access.nju.edu.cn | 210.28.130.5 | | | | | | brute_hosts | ...... # The detailed results are omitted | 92 | www.nju.edu.cn | 202.119.32.7 | | | | | | brute_hosts | +-----------------------------------------------------------------------------------------------------------------+ [*] 92 rows returned
Using db query SQL:
db query select host, ip_address from hosts +-----------------------------------------+ | host | ip_address | +-----------------------------------------+ | access.nju.edu.cn | 210.28.130.5 | ...... # The detailed results are omitted | www.nju.edu.cn | 202.119.32.7 | +-----------------------------------------+ [*] 92 rows returned
3.1.3 if you are not familiar with the module
You can use the info command to print the details of the current module, including various functions and the meaning of each option.
[recon-ng][demo][brute_hosts] > info
Name: DNS Hostname Brute Forcer
Author: Tim Tomes (@lanmaster53)
Version: 1.0
Description:
Brute forces host names using DNS. Updates the 'hosts' table with the results.
Options:
Name Current Value Required Description
-------- ------------- -------- -----------
SOURCE nju.edu.cn yes source of input (see 'info' for details)
WORDLIST /home/parallels/.recon-ng/data/hostnames.txt yes path to hostname wordlist
Source Options:
default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL
<string> string representing a single input
<path> path to a file containing a list of inputs
query <sql> database query returning one column of inputs
3.2 hosts analysis
Parse the existing host to find a new host, as follows.
[recon-ng][demo][brute_hosts] > back
[recon-ng][demo] > modules search resolve
[*] Searching installed modules for 'resolve'...
Recon
-----
recon/hosts-hosts/resolve
recon/hosts-hosts/reverse_resolve
recon/netblocks-hosts/reverse_resolve
[recon-ng][demo] > modules load recon/hosts-hosts/resolve
[recon-ng][demo][resolve] > options list
Name Current Value Required Description
------ ------------- -------- -----------
SOURCE default yes source of input (see 'info' for details)
[recon-ng][demo][resolve] > options set SOURCE query select host from hosts
SOURCE => query select host from hosts # The hosts just queried are parsed here
[recon-ng][demo][resolve] > run
...... # The detailed results are omitted
-------
SUMMARY
-------
[*] 12 total (12 new) hosts found.
3.3 query ports according to hosts
3.3.1 query process
[recon-ng][demo][resolve] > back
[recon-ng][demo] > modules search shodan
[*] Searching installed modules for 'shodan'...
Recon
-----
recon/companies-multi/shodan_org
recon/domains-hosts/shodan_hostname
recon/hosts-ports/shodan_ip
recon/locations-pushpins/shodan
recon/netblocks-hosts/shodan_net
[recon-ng][demo] > modules load recon/hosts-ports/shodan_ip
[recon-ng][demo][shodan_ip] > options list
Name Current Value Required Description
------ ------------- -------- -----------
LIMIT 1 yes limit number of api requests per input source (0 = unlimited)
SOURCE default yes source of input (see 'info' for details)
options set SOURCE query select ip_address from hosts
SOURCE => query select ip_address from hosts
[recon-ng][demo][shodan_ip] > run
...... # The detailed results are omitted. It may take a while here
-------
SUMMARY
-------
[*] 2499 total (263 new) ports found.
[recon-ng][demo][shodan_ip] > show ports
+----------------------------------------------------------------------------------------------------------------------------+
| rowid | ip_address | host | port | protocol | banner | notes | module |
+----------------------------------------------------------------------------------------------------------------------------+
| 1 | 202.119.32.7 | nsc2017.nju.edu.cn | 443 | tcp | | | shodan_ip |
...... # The detailed results are omitted. You can also query the results by querying the database as mentioned earlier
+----------------------------------------------------------------------------------------------------------------------------+
[*] 263 rows returned
4 generate report
4.1 generation process
Recon ng supports generating reports in multiple formats. The following is an example of html.
[recon-ng][demo][shodan_ip] > back
[recon-ng][demo] > modules search report
[*] Searching installed modules for 'report'...
Reporting
---------
reporting/csv
reporting/html
reporting/json
reporting/list
reporting/proxifier
reporting/pushpin
reporting/xlsx
reporting/xml
[recon-ng][demo] > modules load reporting/html
[recon-ng][demo][html] > options list
Name Current Value Required Description
-------- ------------- -------- -----------
CREATOR yes use creator name in the report footer
CUSTOMER yes use customer name in the report header
FILENAME /home/parallels/.recon-ng/workspaces/demo/results.html yes path and filename for report output
SANITIZE True yes mask sensitive data in the report
[recon-ng][demo][html] > options set FILENAME /home/parallels/results.html
FILENAME => /home/parallels/results.html
[recon-ng][demo][html] > options set CREATOR 201220014@smail.nju.edu.cn
CREATOR => 201220014@smail.nju.edu.cn
[recon-ng][demo][html] > options set CUSTOMER a dingle dog
CUSTOMER => a dingle dog
[recon-ng][demo][html] > run
[*] Report generated at '/home/parallels/results.html'.
4.2 generation effect
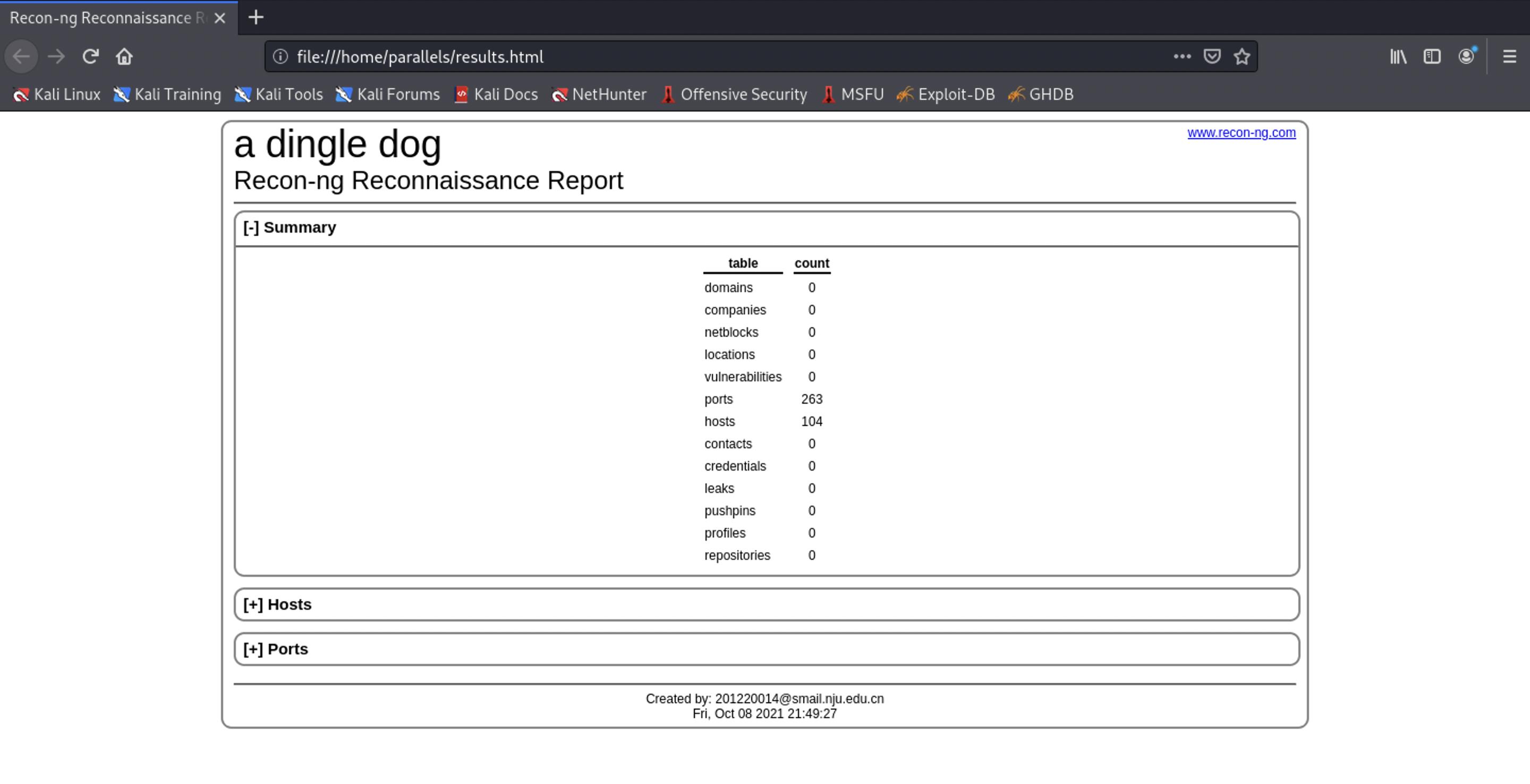
Click the hosts and ports section to expand all the specific search results.