First, some basic routines for installing Opnstack services are described.
1. Database Creation
2. Install packages of corresponding services and modify configuration files
3. Create corresponding services and register api
I. Database
Official Documents https://docs.openstack.org/keystone/stein/install/keystone-install-rdo.html
Creating databases and keystone users
mysql -uroot -p123456 MariaDB [(none)]> CREATE DATABASE keystone; GRANT ALL PRIVILEGES ON keystone.* TO 'keystone'@'%' IDENTIFIED BY 'keystone123';
2. Testing the connection at the control end
mysql -ukeystone -pkeystone123 -hopenstack-mysql.heng.net
2. Installing packages of corresponding services and modifying configuration files
1. Installation of keystone software package on the control side
yum install openstack-keystone httpd mod_wsgi #mod_wsgi for httpd calling python service
2. Modify keystone configuration file
vi /etc/keystone/keystone.conf
[database] Search the database section connection = mysql+pymysql://keystone:keystone123@openstack-mysql.heng.net/keystone [token] # ... provider = fernet Remove comments
3. Generating tables of keystone database
su -s /bin/sh -c "keystone-manage db_sync" keystone
4. Generating fernet validation file
keystone-manage fernet_setup --keystone-user keystone --keystone-group keystone keystone-manage credential_setup --keystone-user keystone --keystone-group keystone
5. Edit apache configuration file
vi /etc/httpd/conf/httpd.conf
ServerName 192.168.12.17:80
6. Create a soft connection to / usr/share/keystone/wsgi-keystone.conf, which is a configuration file for apache calling python and listening on port 5000
ln -s /usr/share/keystone/wsgi-keystone.conf /etc/httpd/conf.d/ systemctl start httpd.service systemctl enable httpd.service
3. Create corresponding services and register api
1. Because Openstack has no account and password, keystone can't provide authentication service. The purpose of authentication service is to get a token, so we can define a token directly to bypass authentication.
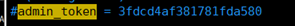
openssl rand -hex 10 3fdcd4af381781fda580
vi /etc/keystone/keystone.conf
admin_token = 3fdcd4af381781fda580
Synchronize the database again after modification and write to the database
su -s /bin/sh -c "keystone-manage db_sync" keystone
2. Check the log for errors
Kestone log file:
ll /var/log/keystone/keystone.log
3. Defining environmental variables
export OS_TOKEN=3fdcd4af381781fda580 export OS_URL=http://192.168.12.17:5000/v3 export OS_IDENTITY_API_VERSION=3
echo $OS_TOKEN confirms that the setup was successful
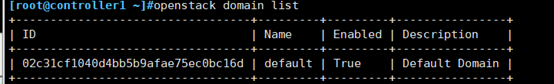
4. Create default domains
openstack domain create --description "Default Domain" default
5. Create an admin project
openstack project create --domain default --description "Admin Project" admin
6. Create admin user and set password to admin:
[root@controller1 ~]#openstack user create --domain default --password-prompt admin User Password: Repeat User Password:
7. Create admin roles and authorize amdin users
openstack role create admin openstack role add --project admin --user admin admin
8. Create demo projects and users
openstack project create --domain default --description "Demo Project" demo openstack user create --domain default --password-prompt demo User Password: Repeat User Password: openstack role create user openstack role add --project demo --user demo user
9. Create a service project
openstack project create --domain default --description "Service Project" service
10. Creating authentication services
openstack service create --name keystone --description "OpenStack Identity" identity [root@controller1 ~]#openstack service list #View the current service
11. Registration api to certification service
openstack endpoint create --region RegionOne identity admin http://openstack-vip.heng.net:5000/v3 openstack endpoint create --region RegionOne identity public http://openstack-vip.heng.net:5000/v3 openstack endpoint create --region RegionOne identity internal http://openstack-vip.heng.net:5000/v3
12. Test whether keystone can do user authentication to open a new terminal
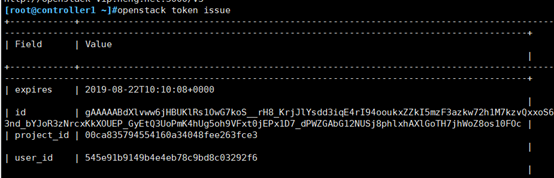
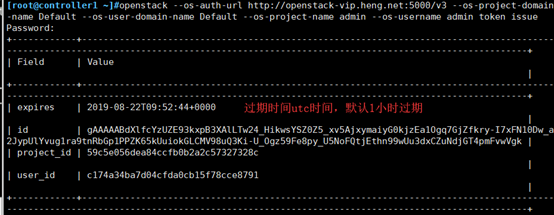
[root@controller1 ~]#export OS_IDENTITY_API_VERSION=3 [root@controller1 ~]#openstack --os-auth-url http://openstack-vip.heng.net:5000/v3 --os-project-domain-name Default --os-user-domain-name Default --os-project-name admin --os-username admin token issue
# Enter this command to display the result without entering a password, which indicates success.
13. It is no longer necessary to specify token manually after user authentication. The token in the file is no longer used and deleted.
vi /etc/keystone/keystone.conf
14. A script that defines two environment variables by which variables are defined and the corresponding api is invoked
vi scripts/admin-stein.sh
export OS_PROJECT_DOMAIN_NAME=Default export OS_USER_DOMAIN_NAME=Default export OS_PROJECT_NAME=admin export OS_USERNAME=admin export OS_PASSWORD=admin export OS_AUTH_URL=http://openstack-vip.heng.net:5000/v3 export OS_IDENTITY_API_VERSION=3 export OS_IMAGE_API_VERSION=2
vi scripts/demo-stein.sh
export OS_PROJECT_DOMAIN_NAME=Default export OS_USER_DOMAIN_NAME=Default export OS_PROJECT_NAME=demo export OS_USERNAME=demo export OS_PASSWORD=demo export OS_AUTH_URL=http://openstack-vip.heng.net:5000/v3 export OS_IDENTITY_API_VERSION=3 export OS_IMAGE_API_VERSION=2
15. The script is used and this result indicates that the keystone service has been successfully installed.
source demo-stein.sh openstack token issue