Foreword: API gateway is actually a very interesting product, just started, tried some new things, it feels fun.
A friend saw me studying and said it was fun to have a gateway on his weekend. Is that the difference?
1. Introduction to API Gateway
API gateways are products of traffic management on Tencent's cloud, and generally play the role of hosting traffic entrances. It provides API hosting services and provides full life cycle management of APIs, including creation, maintenance, publishing, running, offline, and so on.
For ease of understanding, put a picture on it. When introducing to customers, I usually use the following picture as an introduction to the overall scheme of micro services. The gateway rushes ahead.
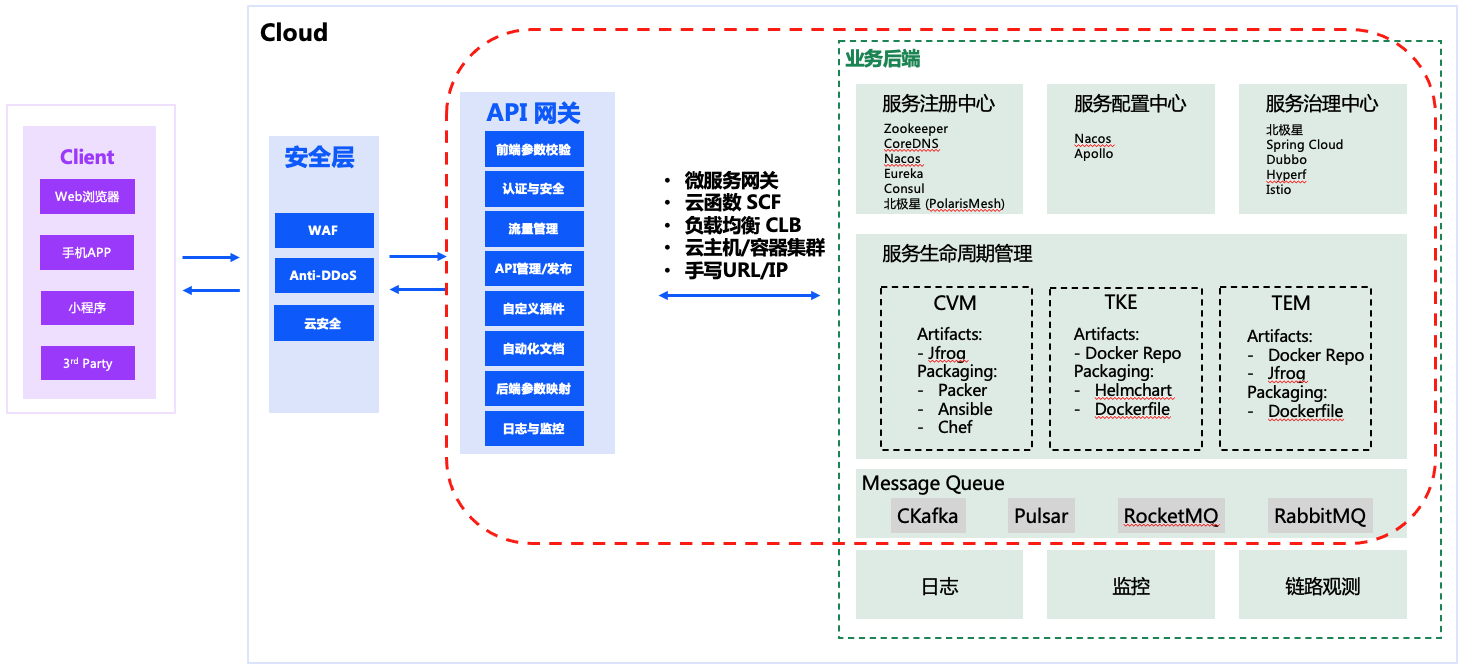
Because today's topic is not about API gateways, but about Oauth, students with other questions can leave a message or contact me directly.
2. Requirements for Oauth integration
2.1 What is AoP
According to the design concept of AoP (aspect-oriented programming), we need to continuously refine reusable capabilities to modularize and form facets. For example, what we commonly use in Java code is that only those with Admin privileges in the privilege can perform the following deletion.
@Scope(role="Admin")
public void deleteRecord(String recordId){
deleteById(recordId);
}In fact, there may be such a facet behind it
@Before("execution(* com.yourpackage..*.*(..))")
public void checkScope(JoinPoint proceedingJoinPoint) throws Throwable {
String scope = getCurrentScope(proceedingJoinPoint);
isAllow(proceedingJoinPoint, scope);
}Based on this design concept, abstracting authentication becomes an inevitable choice. In the process of daily customer communication, the vast majority still very approve of this design concept.
2.2 Why Authentication in API Gateway
First, traffic should be managed as far as possible at the top level, as well as safety protection. We will not configure the defense of WAF in a micro-service system for each service, nor will we expect the business code to keep doing authentication and handling the Exception that results from authentication. Therefore, a well-established scheme is to do authentication at the entrance of traffic. Are there any other options? Certainly, there are different solutions for different needs. But it's good to put the authentication on top, roughly if allowed.
This elicits the customer's need to authenticate in the API gateway.
2.3 Implementation
API gateways currently in the cloud support authentication methods such as API Key / Oauth 2.0 / EIAM. EIAM is essentially Oauth 2.0 + token. Customers can choose to use their own Oauth services or integrate EIAM in the cloud. Most of the customers you are currently encountering are planning to use direct integration of products on the cloud. So EIAM is the first choice.
3. How to configure APIGW+EIAM
3.1 Interface Configuration EIAM Authentication
API gateways are deeply integrated with EIAM, so instead of selecting a standard Oauth authentication method, EIAM can be selected directly. The API Gateway documentation is detailed Introduction to configuration . The documentation describes how to create an API, choose to create a new one or use an existing EIAM application as an object of authentication. Each step is described in detail and the operation is documented. The general content is as follows:
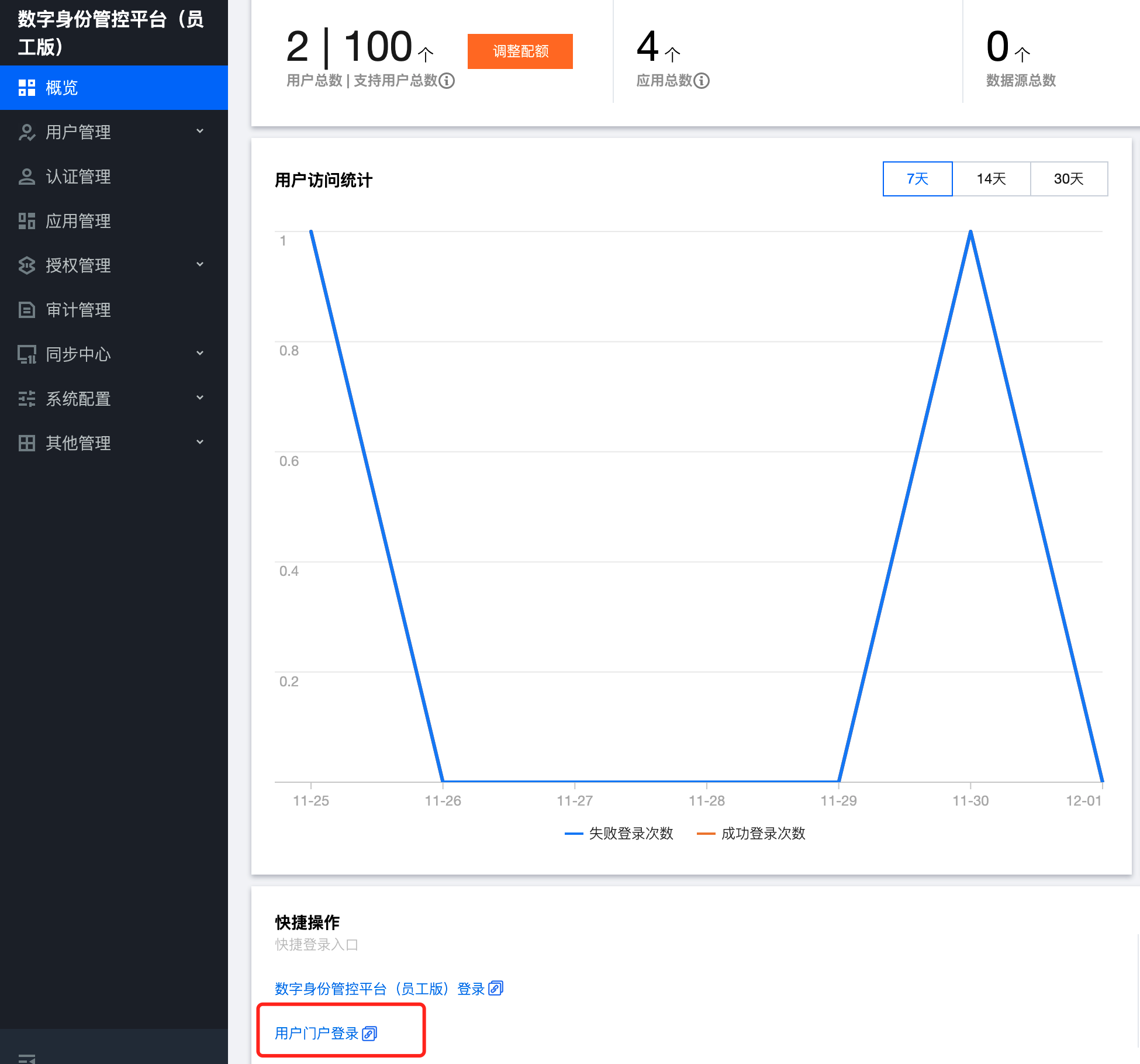
- Confirm that EIAM is on, create a user, configure username/password, and log in to the user portal to ensure that the customer is activated.
- Create an API and configure a front-end access. Select the EIAM authentication type and use the new EIAM application to select the mock on the back end.
- Access the EIAM service and authorize users to access new applications.
- To test with Postman or similar tools, the first step is to get token, and the second step is to pass authentication.
It is important to note that there are differences between the two options of Authentication without Authentication and Authentication, as well as between Non-Web Customer and Web Customer. It is also described in detail in the document.
Users can't find a way to log in to the portal, so I intentionally took a picture.
3.2 Interface Configuration Oauth Type Using EIAM
"How can I prove that EIAM integration is Oauth authentication?". There is only one other way to configure something almost identical, but the API gateway uses Oauth as the authentication method, not EIAM, but still interacts with EIAM.
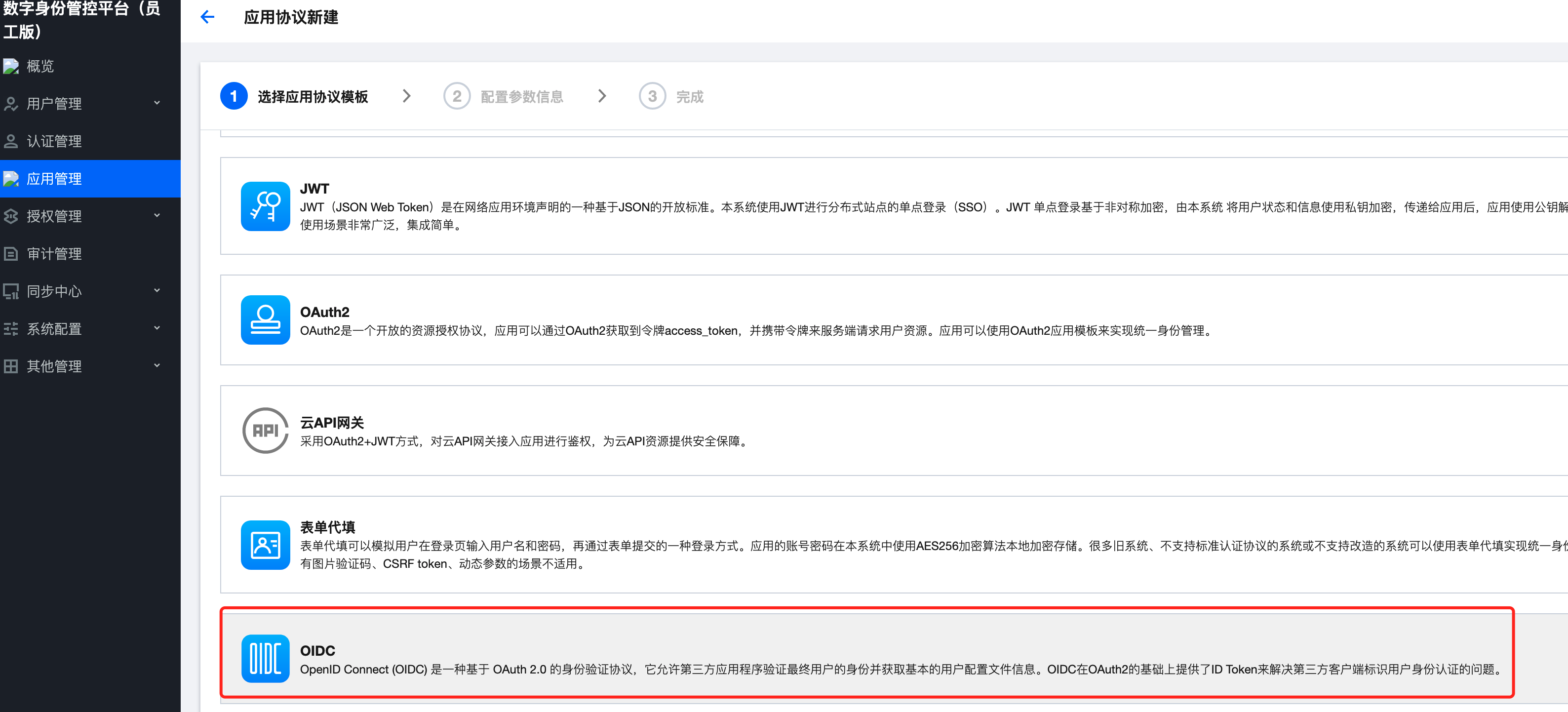
Then the complexity comes in. The first application to create EIAM needs to select OIDC, which is based on OAuth2.0 and provides id_ The application type of token.
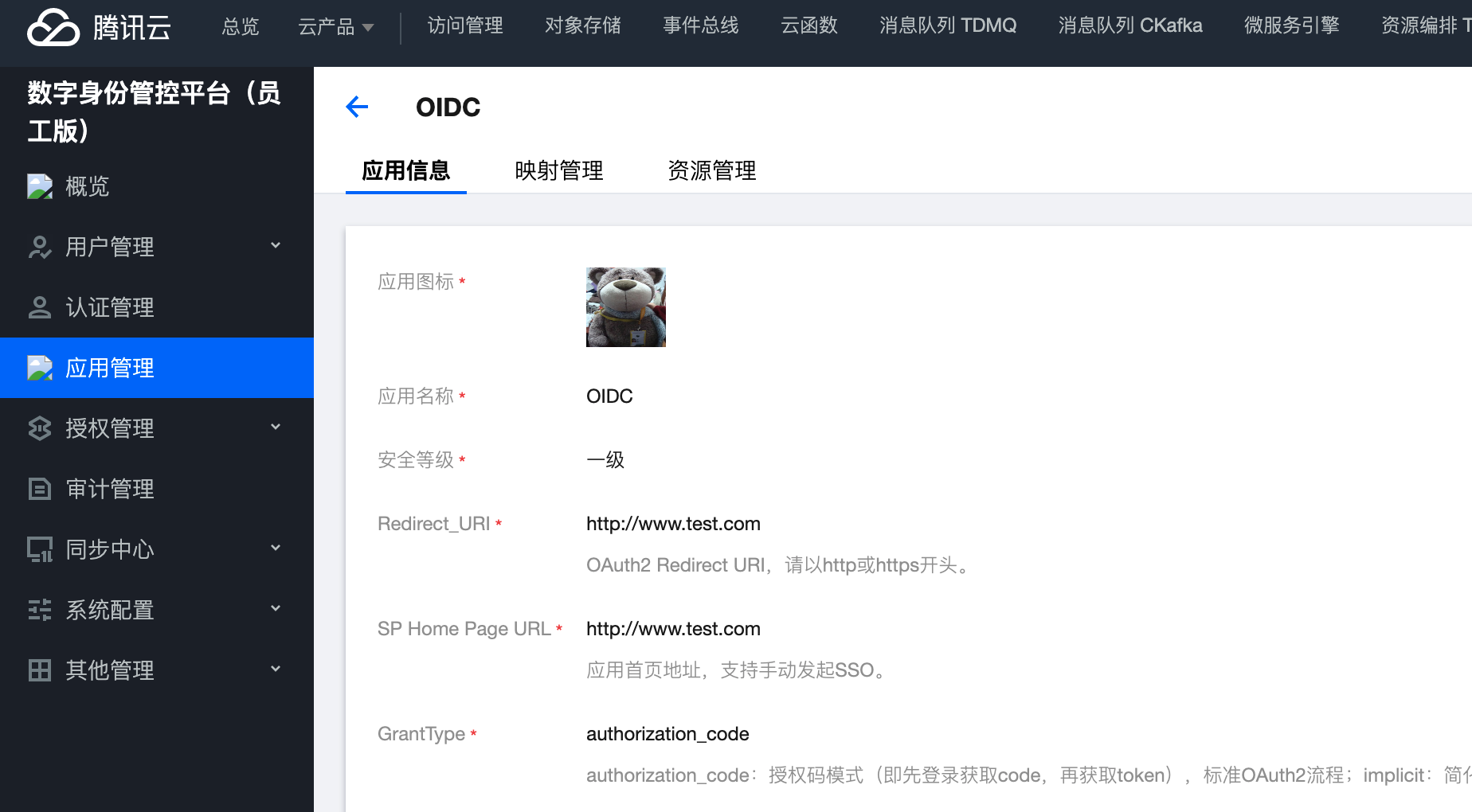
The configuration in the API gateway can then be found in EIAM's Application Management - > Application Information. User authorization can be done in Authorization Management - > Application Authorization.
The configuration of the API gateway authentication interface is not complicated. Refer to the screenshots below for the front-end and back-end configurations, which are authorized APIs of type OAuth 2.0. Business APIs only need to be bound to authorization APIs.
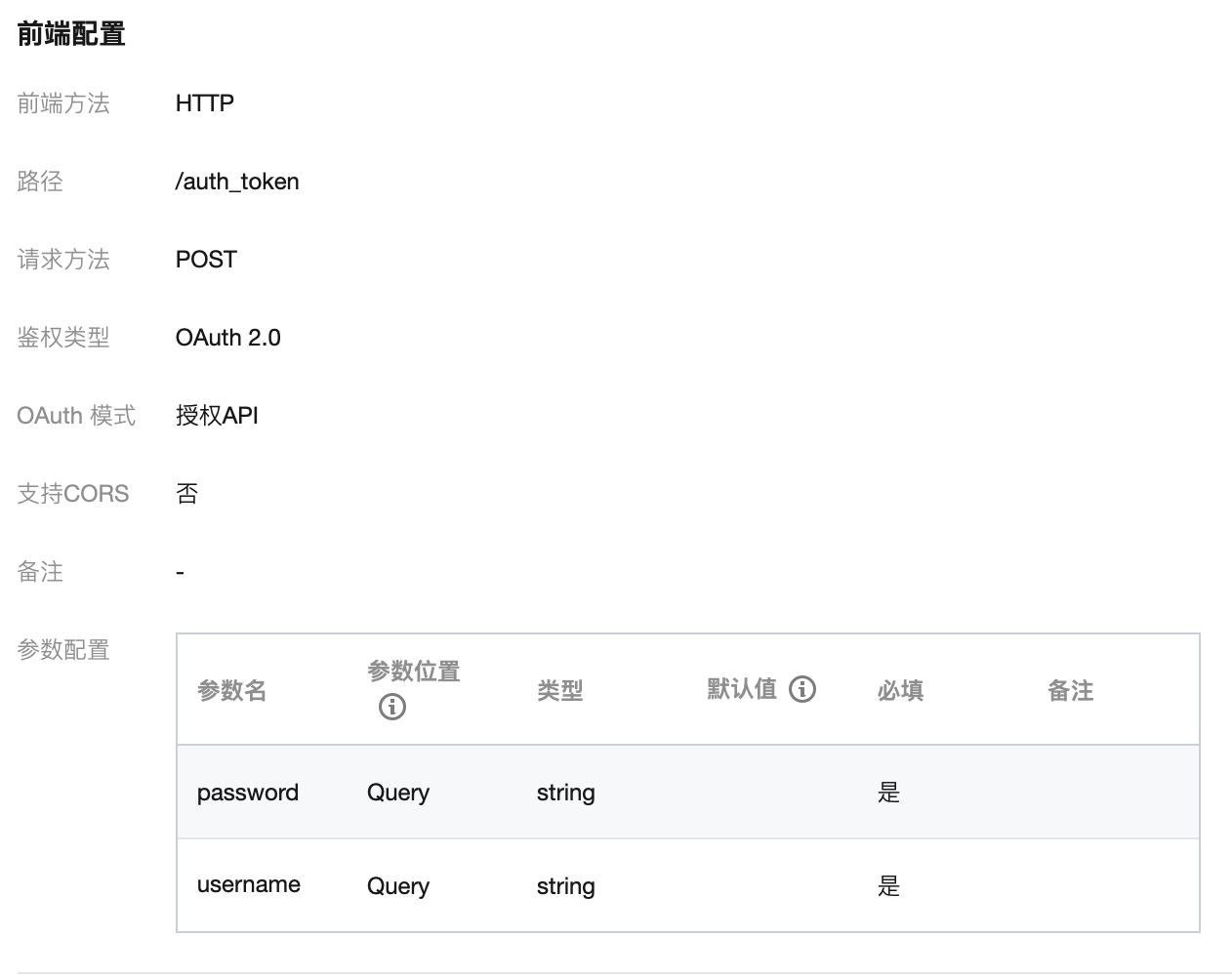
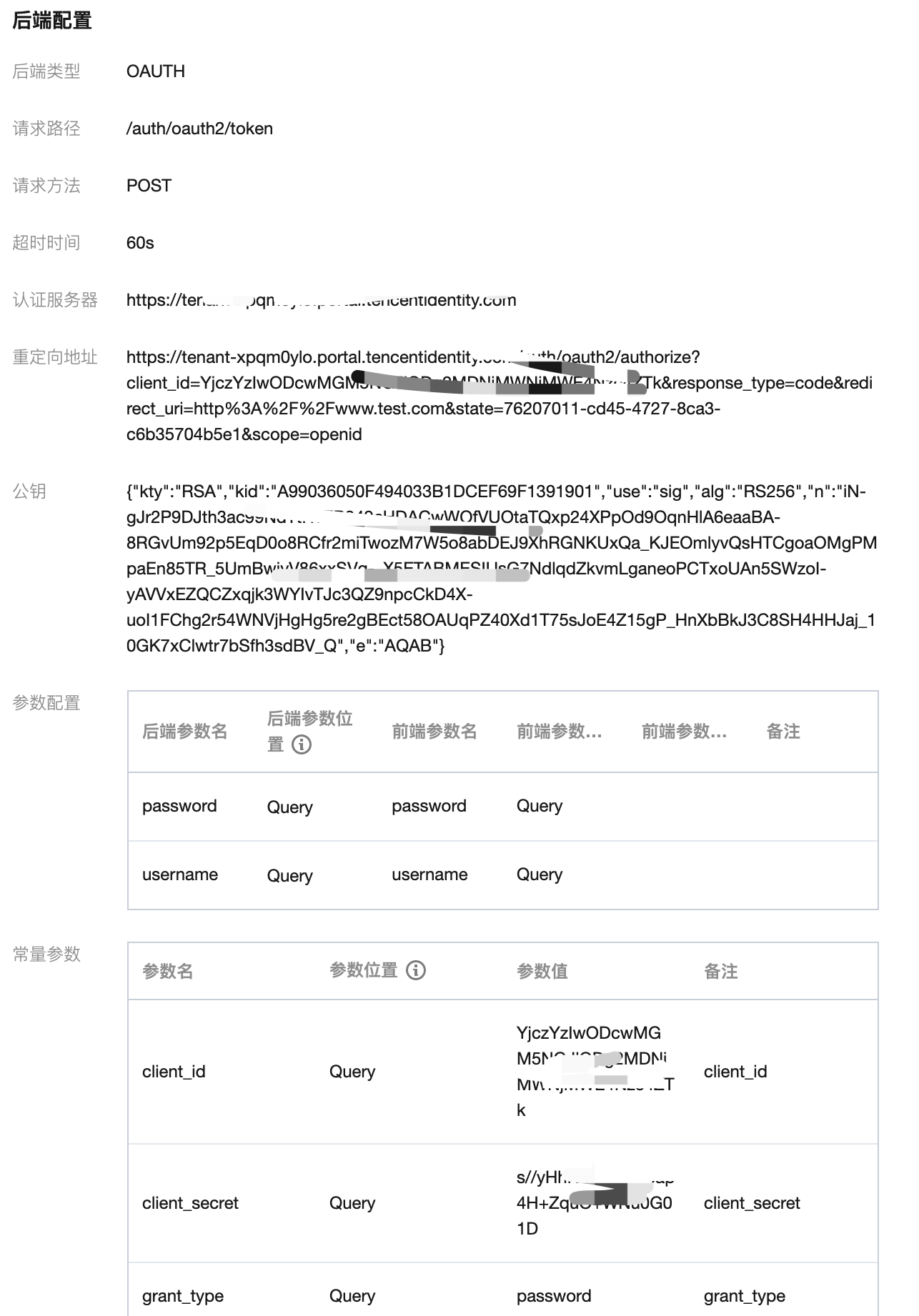
3.3 Cmd Configure EIAM Authentication and Oauth Authentication
Anyone who knows me knows that I won't log in to the console if it's not necessary. There is absolutely no interface that can be solved with code. In fact, this is in line with the usage habits of the general IT industry, but our products are not always able to do it. Terraform is not integrated yet, so I debug the command line through tccli and share it with you here. It's just that the command line can't store state, which is the most basic support for automation.
The first part is Authentication of EIAM - not supported at this time
The second part is Oauth's authorization API creation
export APIGW_SERVICE_ID=service-xxxx export APIGW_SERVICE_API_NAME=yagr-demo export EIAM_APP_ID=6f209a8d-xxxx-xxxx-xxxx-ada444f0976c # create auth-api tccli apigateway CreateApi --cli-unfold-argument \ --ServiceId `echo $APIGW_SERVICE_ID` \ --ApiName $APIGW_SERVICE_API_NAME \ --ApiType NORMAL \ --AuthType OAUTH \ --ApiBusinessType OAUTH \ --Protocol HTTP \ --RequestConfig.Path /auth_token \ --RequestConfig.Method POST \ --ServiceType HTTP \ --RequestParameters.0.Name password \ --RequestParameters.0.Position QUERY \ --RequestParameters.0.Type string \ --RequestParameters.0.Required true \ --RequestParameters.1.Name username \ --RequestParameters.1.Position QUERY \ --RequestParameters.1.Type string \ --RequestParameters.1.Required true \ --ConstantParameters.0.Name client_id \ --ConstantParameters.0.Position QUERY \ --ConstantParameters.0.Desc client_id \ --ConstantParameters.0.DefaultValue `tccli eiam DescribeApplication --ApplicationId $EIAM_APP_ID | jq .ClientId -r` \ --ConstantParameters.1.Name client_secret \ --ConstantParameters.1.Position QUERY \ --ConstantParameters.1.Desc client_secret \ --ConstantParameters.1.DefaultValue `tccli eiam DescribeApplication --ApplicationId $EIAM_APP_ID | jq .ClientSecret -r` \ --ConstantParameters.2.Name grant_type \ --ConstantParameters.2.Position QUERY \ --ConstantParameters.2.Desc grant_type \ --ConstantParameters.2.DefaultValue password \ --ServiceParameters.0.Name username \ --ServiceParameters.0.Position QUERY \ --ServiceParameters.0.RelevantRequestParameterPosition QUERY \ --ServiceParameters.0.RelevantRequestParameterName username \ --ServiceParameters.1.Name password \ --ServiceParameters.1.Position QUERY \ --ServiceParameters.1.RelevantRequestParameterPosition QUERY \ --ServiceParameters.1.RelevantRequestParameterName password \ --ServiceConfig.Url `tccli eiam DescribeApplication --ApplicationId $EIAM_APP_ID | jq .AuthorizeUrl -r | sed -e "s/https:\/\///g" | cut -d '/' -f 1 | sed 's/^/https:\/\//g'` \ --ServiceConfig.Path "/auth/oauth2/token" \ --ServiceConfig.Method POST \ --OauthConfig.PublicKey `tccli eiam DescribeApplication --ApplicationId $EIAM_APP_ID | jq .PublicKey -r` \ --OauthConfig.TokenLocation "method.req.header.authorization" \ --OauthConfig.LoginRedirectUrl `tccli eiam DescribeApplication --ApplicationId $EIAM_APP_ID | jq .AuthorizeUrl -r` \ --ServiceTimeout 60 # release service - this must be done to see the change available tccli apigateway ReleaseService --ServiceId $APIGW_SERVICE_ID --EnvironmentName release --ReleaseDesc test
It took me about 5-6 hours to complete (including a lot of learning costs, of course) and I thank several experts in the team for their dedicated guidance. How to say, I hope it will help everyone