Notes on iOS reverse learning: LLDB dynamic debugging target program
- Configure debugserver
1. Copy the debugserver in the mobile phone to the Mac (provided that the mobile phone has been used as a test machine)
scp root@192.168.0.15:/Developer/usr/bin/debugserver /Users/mac/Desktop/dump 2. Check the debugserver architecture and slim down to remove other architectures
macdeiMac:dump mac$ lipo -info debugserver
Architectures in the fat file: debugserver are: armv7 armv7s arm64
// Keep the required architecture (4S here)
lipo -thin armv7 debugserver -output /Users/mac/Desktop/debugserver3. Sign debugserver
Add task for PID permission with codesign
1. Download the file ent.plist (address: http://iosre.com/ent.plist)
2. Put ent.plist and debugserver in the same directory for signature
macdeiMac:dump mac$ cd /Users/mac/Desktop/sign
macdeiMac:sign mac$ codesign -s - --entitlements ent.plist -f debugserver
debugserver: replacing existing signature
// View signature information
macdeiMac:sign mac$ ldid -e debugserver
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/ PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>com.apple.springboard.debugapplications</key>
<true/>
<key>run-unsigned-code</key>
<true/>
<key>get-task-allow</key>
<true/>
<key>task_for_pid-allow</key>
<true/>
</dict>
</plist>3. Copy the processed debugserver back to the jailbreaking iOS device
scp /Users/mac/Desktop/sign/debugserver root@192.168.2.122:/usr/bin/debugserverNote: copying to "/ usr/bin /" directory has global permission. The original directory / Developer/usr/bin/debugserver is not writable and cannot be overwritten.
- Use of lldb (iOS devices and computers are on the same LAN)
1. ssh to mobile phone to enable debugserver monitoring
debugserver *:9999 -a "caipudaquan"2. Using lldb on the computer
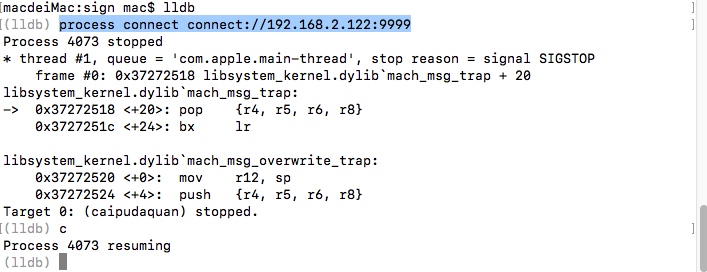
lldb
process connect connect://192.168.2.122:9999The effect is as follows: 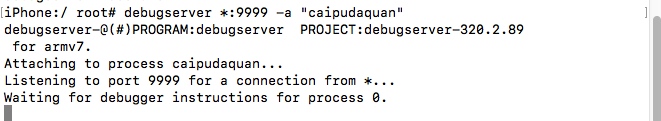
Common commands:
See ASLR deviation
image list -o -f
br s -a '0x0000000000054000+0x0000000101dcbb0c'
//Set breakpoints
b function
br s –a address
br s –a 'ASLROffset+address'
// View all breakpoints
br list
// Delete breakpoint 1
br delete 1
// Program continues
c
// View function call stack
bt
// Disable breakpoint 1
br dis 1
// Make breakpoint 1 effective
br enable 1
x/s $x1 // Display the memory at register x1 as a string
register read // Read the value of all registers
register read $x0 // Read the value of a register
register write $x5 1 // Modify the value of a register
si // Jump inside the current instruction
ni // Skip current instruction
finish // Return to upper call stack
thread return // The following code is no longer executed, returning a value directly from the current call stack.
br list // View the current breakpoint list
br del // Delete all current breakpoints
help // View all LLDB commands
apropos name // Search command related command with name
memory read -force -f A $sp $fp // Print the value of the stack in memory
x/10xg address // Display the contents of 10 64 bit elements in the address space in hexadecimal
// Add a command to the breakpoint. When the breakpoint is triggered, the command you added will be executed. For example, there is a breakpoint 1 at this time
br com add 1
> po $r0
> po $r1
> c
> DONE