Hello, I'm jock.
Some people may not be familiar with traifik, but they should be familiar with Nginx.
For the time being, we regard Traefik as a kind of software similar to Nginx. After reading the whole article, you will have a different understanding of Traefik.
This article mainly takes you to have a comprehensive understanding of Traefik. I will introduce it from the following aspects.

This article is based on traifik 2.5.3.
What is Traefik
Traefik is an open source edge routing gateway, which is easy to use and fully functional. The official [1] introduction is: traefik is an [open source]( https://github.com/traefik/traefik ) _ Edge Router_ that makes publishing your services a fun and easy experience.
Traifik supports a variety of clusters, such as Kubernetes, Docker, Docker Swarm, AWS, Mesos, Marathon, etc; And can handle many clusters at the same time.

image.png
Traifik's core concepts and capabilities
Traefik is an edge router. It will intercept external requests and choose different operation modes according to logical rules. These rules determine how to deal with these requests. Traefik provides automatic discovery capability, which will detect services in real time and automatically update routing rules.
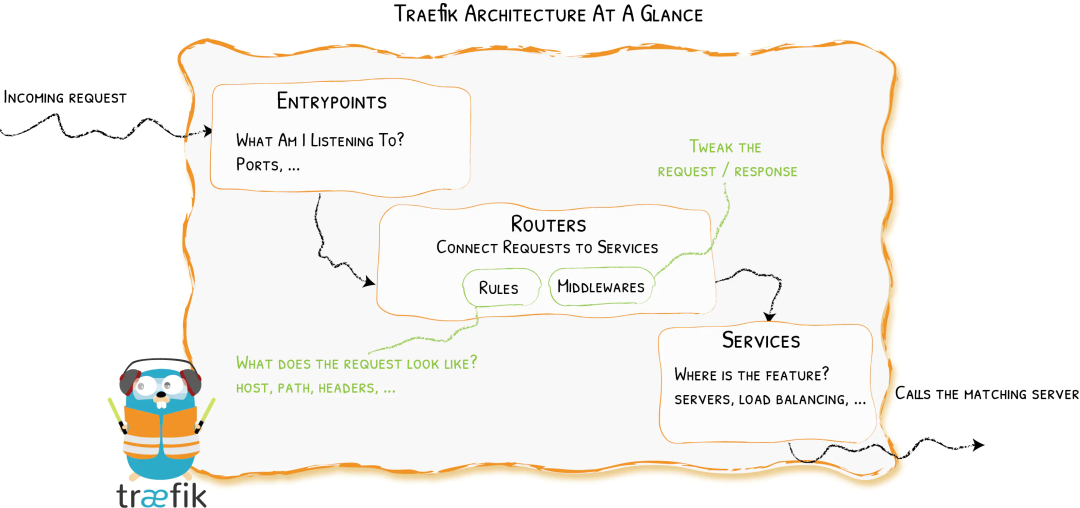
As can be seen from the above figure, the requests will first be connected to the entry points, and then analyze whether these requests match the defined rules. If they match, they will pass through a series of middlewares and then to the corresponding services.
This involves the following important core components.
- Providers
- Entrypoints
- Routers
- Services
- Middlewares
Providers
Providers is the basic component through which the configuration discovery of Traefik is realized. It can be a coordinator, container engine, cloud provider or key value storage.
Traefik queries the relevant information of the route through the API of Providers. Once a change is detected, it will dynamically update the route.
Entrypoints
Entrypoints is the network portal of Traefik. It defines the interface to receive requests and whether to listen to TCP or UDP.
Routers
Routers is mainly used to analyze requests and connect them to corresponding services. In this process, routers can also use Middlewares to update requests, such as adding some Headers before sending requests to services.
Services
Services is responsible for configuring how to reach the actual service that will eventually process incoming requests.
Middlewares
Middlewares are used to modify the request or make some judgments according to the request (authentication, rate limiting, headers,...). Middleware is attached to the route. It is a method to adjust the request before the request is sent to your service (or before the service response is sent to the client).
Deploy traifik
There are many ways to deploy traifik. Here, Helm is mainly used for deployment management.
Helm deployment
Environment: kubernetes: 1.22.3 helm: 3.7.1
1. Add traefik helm warehouse
$ helm repo add traefik https://helm.traefik.io/traefik $ helm repo update
2. Download the traefik package locally for management
$ helm search repo traefik NAME CHART VERSION APP VERSION DESCRIPTION traefik/traefik 10.6.0 2.5.3 A Traefik based Kubernetes ingress controller $ helm pull traefik/traefik
3. Deploy traifik
The default value.yaml[2] configuration file has many configurations, which may take some time to sort out, but it can be understood quickly according to the relevant comments.
Here you can customize a configuration file, my-value.yaml, as follows:
service:
type: NodePort
ingressRoute:
dashboard:
enabled: false
ports:
traefik:
port: 9000
expose: true
web:
port: 8000
expose: true
websecure:
port: 8443
expose: true
persistence:
enabled: true
name: data
accessMode: ReadWriteOnce
size: 5G
storageClass: "openebs-hostpath"
path: /data
additionalArguments:
- "--serversTransport.insecureSkipVerify=true"
- "--api.insecure=true"
- "--api.dashboard=true"
To deploy, the command is as follows:
$ kubectl create ns traefik-ingress $ helm install traefik -n traefik-ingress -f my-value.yaml .
The default value.yaml[2] configuration file is not used here.
Then you can see the deployment results as follows:
# kubectl get all -n traefik-ingress NAME READY STATUS RESTARTS AGE pod/traefik-77ff894bb5-qqszd 1/1 Running 0 6m26s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/traefik NodePort 10.108.170.22 <none> 9000:32271/TCP,80:31728/TCP,443:30358/TCP 6m26s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/traefik 1/1 1 1 6m26s NAME DESIRED CURRENT READY AGE replicaset.apps/traefik-77ff894bb5 1 1 1 6m26s
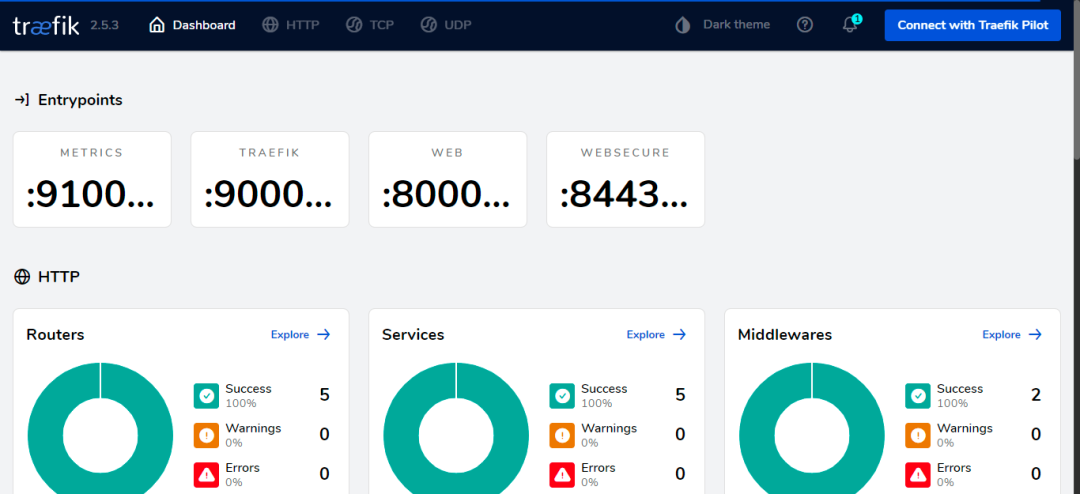
Then you can access the Dashboard page through NodePort, as follows:
Using traifik
Create first routing rule
We use the NodePort method to access the Dashboard. Now that Traefik has been deployed, why not use the routing gateway method?
Let's create the first routing gateway to access the Dashboard.
There are many ways for Traefik to create routing rules, such as:
- Native Ingress writing
- Use CRD ingresroute mode
- How to use the gateway API
The first two methods are briefly introduced here. The gateway API methods will be introduced later.
Native Ingress routing rules
The routing rules of the native Ingress are relatively simple, as follows.
# cat traefik-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: traefik-dashboard-ingress
annotations:
kubernetes.io/ingress.class: traefik
traefik.ingress.kubernetes.io/router.entrypoints: web
spec:
rules:
- host: traefik-web.coolops.cn
http:
paths:
- pathType: Prefix
path: /
backend:
service:
name: traefik
port:
number: 9000
To create a routing rule, the command is as follows:
# kubectl apply -f traefik-ingress.yaml -n traefik-ingress ingress.networking.k8s.io/traefik-dashboard-ingress created
Now you can use the domain name http://traefik-web.coolops.cn:31728/dashboard/#/ Accessed (31728 is the mapped port of port 80), as follows:

Configure routing rules in CRD mode
In earlier versions, Traefik only provided kubernetes ingress to configure routing rules. The community believed that developing a custom CRD type could better provide Kubernetes access configuration [3].
The configuration method of ingresroute is also relatively simple, as follows:
# cat traefik-ingressRoute.yaml
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: traefik-dashboard-route
spec:
entryPoints:
- web
routes:
- match: Host(`traefik-web2.coolops.cn`)
kind: Rule
services:
- name: traefik
port: 9000
The deployment command is as follows:
# kubectl apply -f traefik-ingressRoute.yaml -n traefik-ingress ingressroute.traefik.containo.us/traefik-dashboard-route created
Then you can pass http://traefik-web2.coolops.cn:31728/dashboard/#/ Visited.

Expose HTTP services
First, deploy a simple whoami[4] application. The YAML file is as follows:
---
apiVersion: v1
kind: Pod
metadata:
name: whoami
labels:
app: whoami
spec:
containers:
- name: whoami
image: traefik/whoami:latest
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: whoami
spec:
ports:
- port: 80
protocol: TCP
targetPort: 80
selector:
app: whoami
type: ClusterIP
After successful deployment, create a routing rule so that external users can access it.
# cat ingressroute.yaml
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami-route
spec:
entryPoints:
- web
routes:
- match: Host(`whoami.coolops.cn`)
kind: Rule
services:
- name: whoami
port: 80
After creation, you can access it as follows:
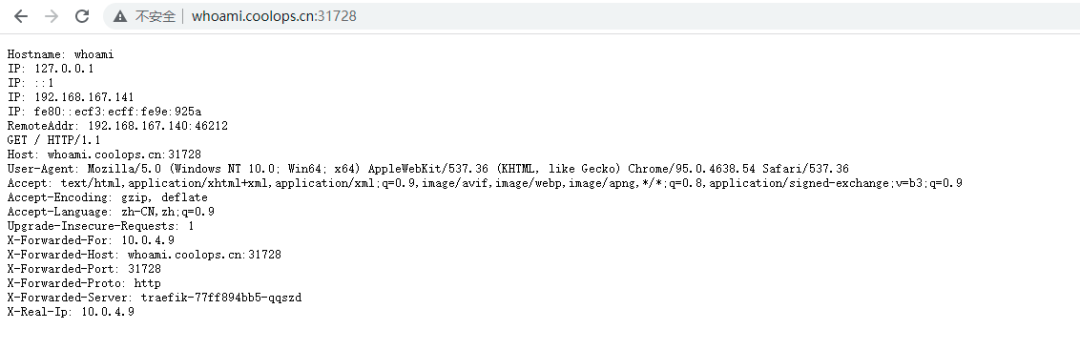
Expose HTTPS services
The whoami application above is accessed through HTTP. If you want to access through HTTPS, how should you configure it?
Traifik supports HTTPS and TLS. For certificates, you can select your own certificate or use Let's Encrypt [5] to automatically generate certificates. These two methods will be introduced here.
Own certificate configuration HTTPS
Now the company will basically purchase more secure certificates by itself, so HTTPS will be used more frequently for its own certificate configuration. This configuration method is mainly introduced here.
1. Apply for or purchase certificates
Here is the free certificate I applied for in Tencent cloud.
Then download the corresponding certificate and upload it to the server.
2. Save the certificate file as Secret
# kubectl create secret tls whoami-tls --cert=1_whoami.coolops.cn_bundle.crt --key=2_whoami.coolops.cn.key
3. Create an ingresroute object so that it can be accessed through TLS
# cat ingressroutetls.yaml
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami-route-tls
spec:
entryPoints:
- websecure
routes:
- match: Host(`whoami.coolops.cn`)
kind: Rule
services:
- name: whoami
port: 80
tls:
secretName: whoami-tls
Once created, you can https://whoami.coolops.cn:30358/ Accessed (30358 is the port mapped by 443).
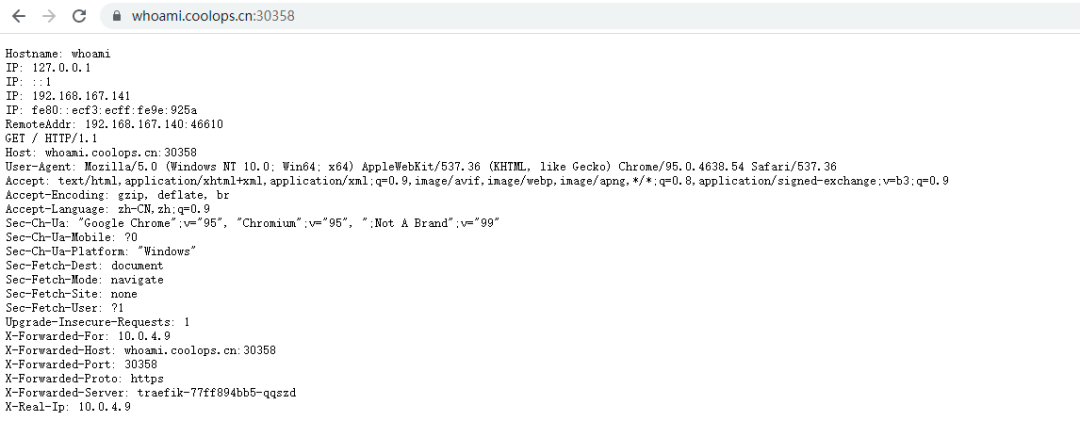
Automatically generate HTTPS certificate
In addition to using its own certificates, traifik also supports Let's Encrypt to automatically generate certificates [6].
To automatically generate a certificate using Let's Encrypt, you need to use ACME. The "certificate parser" needs to be defined in the static configuration, and Traefik is responsible for retrieving the certificate from the ACME server.
Then, each "router" is configured to enable TLS and is associated with a certificate parser through the tls.certresolver configuration option.
Traifik's ACME verification methods mainly include the following three types:
- tlsChallenge
- httpChallenge
- dnsChallenge
If tlsChallenge is used, Let's Encrypt to Traefik 443 port must be reachable. If httpChallenge is used, Let's Encrypt to traifik 80 port must be reachable. If you use dnsChallenge, you need the corresponding providers[7].
However, ports 80 and 443 were not exposed when we deployed Traefik above. To test tlsChallenge and httpChallenge, we must expose them. Let's change my-value.yaml as follows:
service:
type: NodePort
ingressRoute:
dashboard:
enabled: false
ports:
traefik:
port: 9000
expose: true
web:
port: 8000
hostPort: 80
expose: true
websecure:
port: 8443
hostPort: 443
expose: true
persistence:
enabled: true
name: data
accessMode: ReadWriteOnce
size: 5G
storageClass: "openebs-hostpath"
path: /data
additionalArguments:
- "--serversTransport.insecureSkipVerify=true"
- "--api.insecure=true"
- "--api.dashboard=true"
Then update Traefik again. The command is as follows:
helm upgrade traefik -n traefik-ingress -f my-value.yaml .
Now we can access it directly through port 80 or 443.
1,tlsChallenge
As mentioned above, to use tlsChallenge, you must be able to access port 443 of the portal. Now that the portal has been opened, we will modify the my-value.yaml configuration of Traefik, as follows:
......
deployment:
initContainers:
- name: volume-permissions
image: busybox:1.31.1
command: ["sh", "-c", "chmod -Rv 600 /data/*"]
volumeMounts:
- name: data
mountPath: /data
additionalArguments:
- "--serversTransport.insecureSkipVerify=true"
- "--api.insecure=true"
- "--api.dashboard=true"
- "--certificatesresolvers.coolops.acme.email=coolops@163.com"
- "--certificatesresolvers.coolops.acme.storage=/data/acme.json"
- "--certificatesresolvers.coolops.acme.tlschallenge=true"
PS: here, you need to change the permission of / data directory. The default is 0660. If the permission is too large, it is not allowed.
Then we create an ingress route as follows:
# cat ingressrouteautotls.yaml
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami-route-auto-tls
spec:
entryPoints:
- websecure
routes:
- match: Host(`whoami3.coolops.cn`)
kind: Rule
services:
- name: whoami
port: 80
tls:
certResolver: coolops
This is when we visit https://whoami3.coolops.cn The certificate can be used normally, as follows:

2,httpChallenge
Next, use httpChallenge to test. Modify the my-value.yaml configuration file as follows:
......
deployment:
initContainers:
- name: volume-permissions
image: busybox:1.31.1
command: ["sh", "-c", "chmod -Rv 600 /data/*"]
volumeMounts:
- name: data
mountPath: /data
additionalArguments:
- "--serversTransport.insecureSkipVerify=true"
- "--api.insecure=true"
- "--api.dashboard=true"
- "--certificatesresolvers.coolops.acme.email=coolops@163.com"
- "--certificatesresolvers.coolops.acme.storage=/data/acme.json"
- "--certificatesresolvers.coolops.acme.httpchallenge=true"
- "--certificatesresolvers.coolops.acme.httpchallenge.entrypoint=web"
After updating traifik, create an ingressRoute for testing. The YAML file is as follows:
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami-route-auto-tls-http
spec:
entryPoints:
- websecure
routes:
- match: Host(`whoami4.coolops.cn`)
kind: Rule
services:
- name: whoami
port: 80
tls:
certResolver: coolops
Then use https://whoami4.coolops.cn , the effect is as follows:
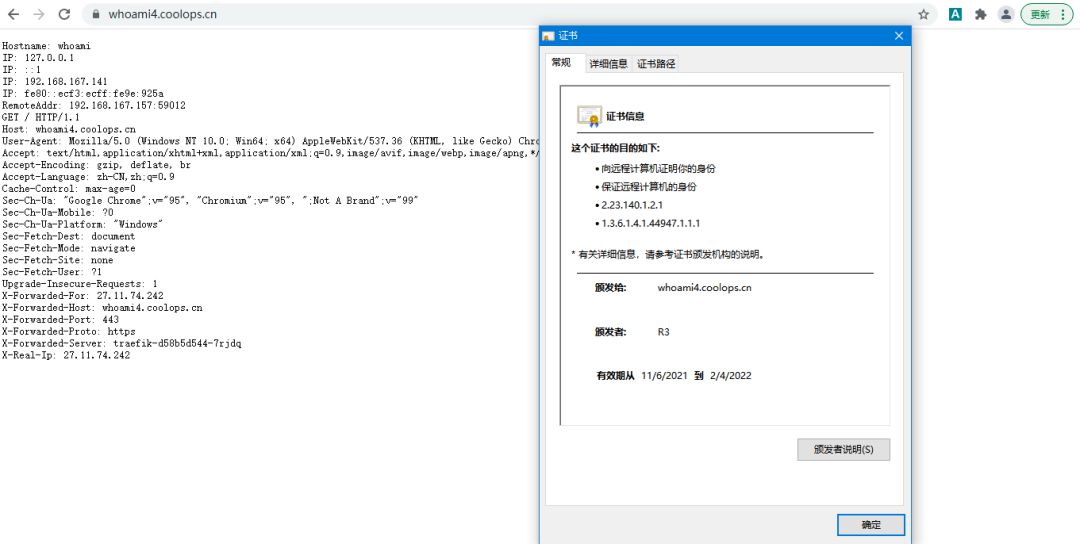
3,dnsChallenge
dnsChallenge is relatively troublesome to use because the corresponding provider needs to be configured, but it can generate wildcard certificates. Here, take alicloud DNS [8] as an example.
The premise of using Alibaba DNS is that your domain name is on Alibaba cloud, otherwise an error will be reported when signing the certificate, as follows:
Unable to obtain ACME certificate for domains \"*.coolops.cn\" : unable to generate a certificate for the domains [*.coolops.cn]: error: one or more domains had a problem:\n[*.coolops.cn] [*.coolops.cn] acme: error presenting token: alicloud: zone coolops.cn. not found in AliDNS for domain coolops.cn\n" providerName=coolops.acme
Three environment variables need to be configured for alicloud DNS verification: ALICLOUD_ACCESS_KEY,ALICLOUD_SECRET_KEY,ALICLOUD_REGION_ID, which respectively corresponds to the key we use when developing Alibaba cloud applications, can be obtained by logging in to the Alibaba cloud background. Because this is relatively private information, we use the Secret object to create:
$ kubectl create secret generic traefik-alidns --from-literal=ALICLOUD_ACCESS_KEY=<aliyun ak> --from-literal=ALICLOUD_SECRET_KEY=<aliyun sk>--from-literal=ALICLOUD_REGION_ID=cn-beijing -n traefik-ingress
Modify my-value.yaml of Traefik as follows:
......
additionalArguments:
- "--serversTransport.insecureSkipVerify=true"
- "--api.insecure=true"
- "--api.dashboard=true"
- "--certificatesresolvers.coolops.acme.email=coolops@163.com"
- "--certificatesresolvers.coolops.acme.storage=/data/acme.json"
- "--certificatesresolvers.coolops.acme.dnschallenge=true"
- "--certificatesResolvers.coolops.acme.dnsChallenge.provider=alidns"
envFrom:
- secretRef:
name: traefik-alidns
After updating the traifik, create an ingressRoute for testing. The YAML file is as follows (because coolops.cn is not on alicloud, a domain name is changed):
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami-route-auto-tls-dns
spec:
entryPoints:
- websecure
routes:
- match: Host(`whoami6.coolops.cn`)
kind: Rule
services:
- name: whoami
port: 80
tls:
certResolver: coolops
domains:
- main: "*.coolops.cn"
After accessing the domain name, you can see that the certificate is signed successfully, as follows:
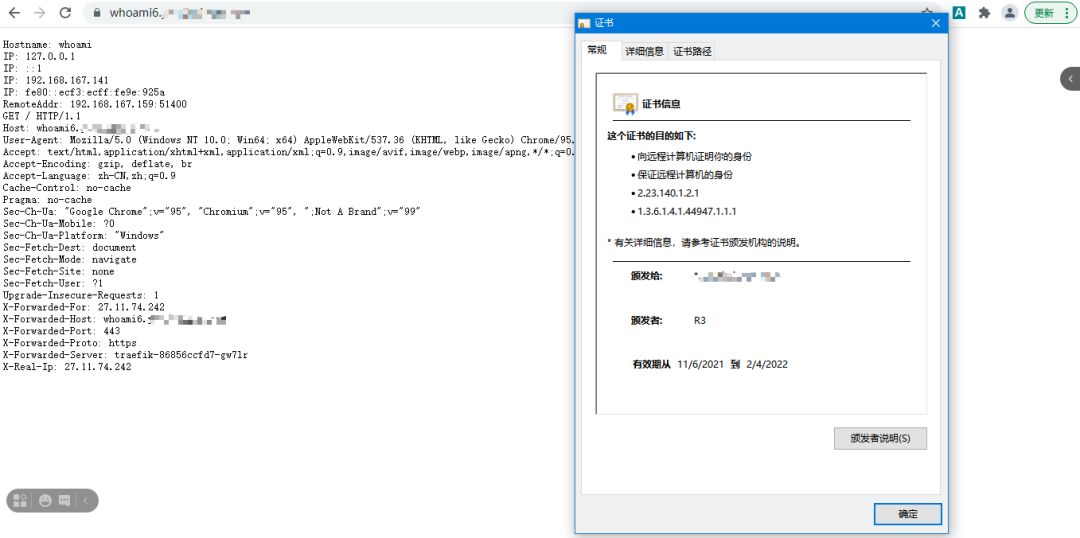
Use of Middleware
When introducing the core concept of Traefik, it was mentioned that after a request matches Rules, it will go through a series of Middleware and then to the specific Services. What is this Middleware?

image.png
Middleware is a new function after Traefik 2.0. Users can choose different middleware to meet the service according to their unreasonable needs, which improves the customization ability.
Traifik has built-in Middleware with many different functions, mainly for HTTP and TCP. HTTP accounts for the majority [9]. Here are some commonly used ones for demonstration.
Force a jump to HTTPS
Forced jump to HTTPS is a frequently configured function. Here is the whoami application not mentioned above as an example.
1. Create an HTTPS ingressRoute
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami-route-auto-tls
spec:
entryPoints:
- websecure
routes:
- match: Host(`whoami3.coolops.cn`)
kind: Rule
services:
- name: whoami
port: 80
tls:
certResolver: coolops
2. Define a middleware that jumps to HTTPS
The built-in middleware of RedirectScheme will be used here. The configuration is as follows:
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: redirect-https-middleware
spec:
redirectScheme:
scheme: https
3. Define an HTTP ingressRoute and use Middleware
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami3-route
spec:
entryPoints:
- web
routes:
- match: Host(`whoami3.coolops.cn`)
kind: Rule
services:
- name: whoami
port: 80
middlewares:
- name: redirect-https-middleware
Then visit http://whoami3.coolops.cn Will be forced to jump to https://whoami3.coolops.cn .
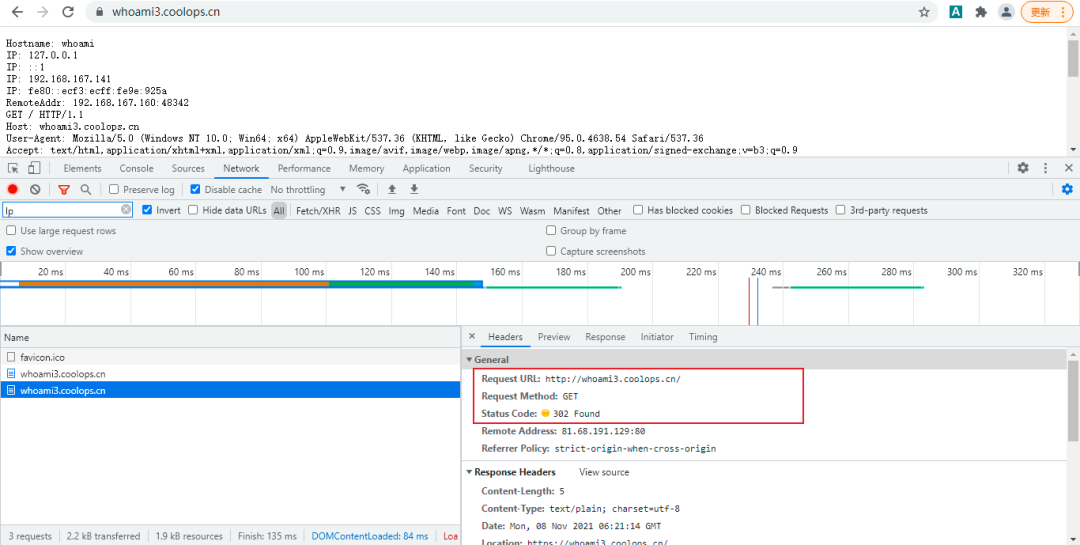
Remove request path prefix
Sometimes there is a need:
- Only one domain name
- You can access different applications through this domain name
This requirement is very common. In NGINX, we can configure multiple locations to customize rules, and Traefik can also do so.
However, after customizing different prefixes, because the application itself does not have these prefixes, the request returns 404. At this time, we need to process the requested path, or take whoami application as an example.
1. Create an ingressRoute with a prefix
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami7-route
spec:
entryPoints:
- web
routes:
- match: Host(`whoami7.coolops.cn`) && PathPrefix('/coolops')
kind: Rule
services:
- name: whoami
port: 80
Our current access will return 404 status.

2. Define prefixed Middleware
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: prefix-coolops-url-middleware
spec:
stripPrefix:
prefixes:
- /coolops
3. Modify the above ingressRoute to apply middleware
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: whoami7-route
spec:
entryPoints:
- web
routes:
- match: Host(`whoami7.coolops.cn`) && PathPrefix('/coolops')
kind: Rule
services:
- name: whoami
port: 80
middlewares:
- name: prefix-coolops-url-middleware
Then you can access it normally.
Add IP whitelist
In our work, we do not want to expose some URLs, such as prometheus, grafana, etc. at this time, we want to meet the requirements through the white list IP, so we can use the ipWhiteList Middleware in Traefik.
1. Middleware for defining whitelist IP
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: ip-white-list-middleware
spec:
ipWhiteList:
sourceRange:
- 127.0.0.1/32
- 192.168.100.180
Then apply the middleware to the corresponding Rules to complete the whitelist function.
In addition to the above functions, the built-in Middleware in Traefik also supports many other functions, such as current limiting, authentication, etc., which can be viewed by referencing [9].
Expose TCP services
Traefik 2.0 supports TCP exposure. Take Redis as an example.
1. Deploy a Redis service
apiVersion: apps/v1
kind: Deployment
metadata:
name: redis
spec:
selector:
matchLabels:
app: redis
template:
metadata:
labels:
app: redis
spec:
containers:
- name: redis
image: redis:5.0.14
ports:
- containerPort: 6379
protocol: TCP
---
apiVersion: v1
kind: Service
metadata:
name: redis
spec:
ports:
- port: 6379
targetPort: 6379
selector:
app: redis
2. Expose Redis port
The exposed TCP port uses SNI [10], and SNI depends on TLS, so we need to configure the certificate. However, if there is no certificate, we can use the wildcard * for configuration.
(1) . add an entry point for redis
Modify the deployment file my-value.yaml of Traefik and add the following:
ports:
traefik:
port: 9000
expose: true
web:
port: 8000
hostPort: 80
expose: true
websecure:
port: 8443
hostPort: 443
expose: true
redis:
port: 6379
containerPort: 6379
hostPort: 6379
additionalArguments:
- "--entryPoints.redis.address=:6379"
- "--serversTransport.insecureSkipVerify=true"
- "--api.insecure=true"
- "--api.dashboard=true"
- "--certificatesresolvers.coolops.acme.email=coolops@163.com"
- "--certificatesresolvers.coolops.acme.storage=/data/acme.json"
- "--certificatesresolvers.coolops.acme.httpchallenge=true"
- "--certificatesresolvers.coolops.acme.httpchallenge.entrypoint=web"
Add -- entryPoints.redis.address=:6379 to the startup parameters to specify the entrypoint.
(2) Create ingressRoute for external exposure
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRouteTCP
metadata:
name: redis-traefik-tcp
spec:
entryPoints:
- redis
routes:
- match: HostSNI(`*`)
services:
- name: redis
port: 6379
Then you can use the client tool to perform Redis operations.
# redis-cli -h redis.coolops.cn redis.coolops.cn:6379> set a b OK redis.coolops.cn:6379> get a "b" redis.coolops.cn:6379>
Grayscale Publishing
A more powerful function after traefik 2.0 is gray-scale publishing. Gray-scale publishing is sometimes called Canary publishing, which mainly allows some tested services to participate in the online. After testing, observe whether the symbol is required to go online.
Suppose an application is running V1 and the new V2 version needs to go online. At this time, we need to deploy the V2 version in the cluster, and then realize this function through weighted polling (WRR) provided by Traefik.
1. Deploy appv1 and appv2 applications
appv1.yaml
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: appv1
spec:
selector:
matchLabels:
app: appv1
template:
metadata:
labels:
use: test
app: appv1
spec:
containers:
- name: nginx
image: nginx
imagePullPolicy: IfNotPresent
lifecycle:
postStart:
exec:
command: ["/bin/sh", "-c", "echo Hello v1 > /usr/share/nginx/html/index.html"]
ports:
- containerPort: 80
name: portv1
---
apiVersion: v1
kind: Service
metadata:
name: appv1
spec:
selector:
app: appv1
ports:
- name: http
port: 80
targetPort: portv1
appv2.yaml
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: appv2
spec:
selector:
matchLabels:
app: appv2
template:
metadata:
labels:
use: test
app: appv2
spec:
containers:
- name: nginx
image: nginx
imagePullPolicy: IfNotPresent
lifecycle:
postStart:
exec:
command: ["/bin/sh", "-c", "echo Hello v2 > /usr/share/nginx/html/index.html"]
ports:
- containerPort: 80
name: portv2
---
apiVersion: v1
kind: Service
metadata:
name: appv2
spec:
selector:
app: appv2
ports:
- name: http
port: 80
targetPort: portv2
2. Create traifikservice
After traefik 2.1, a CRD resource of traefik service is added. We can directly use this object to configure WRR.
apiVersion: traefik.containo.us/v1alpha1
kind: TraefikService
metadata:
name: app-wrr
spec:
weighted:
services:
- name: appv1
weight: 3
port: 80
kind: Service
- name: appv2
weight: 1
port: 80
kind: Service
3. Create ingressRoute
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: app-ingressroute-canary
spec:
entryPoints:
- web
routes:
- match: Host(`app.coolops.cn`)
kind: Rule
services:
- name: app-wrr
kind: TraefikService
Note: the Service type is not configured here, but the traifikservice.
Then you can access http://app.coolops.cn To verify the results.
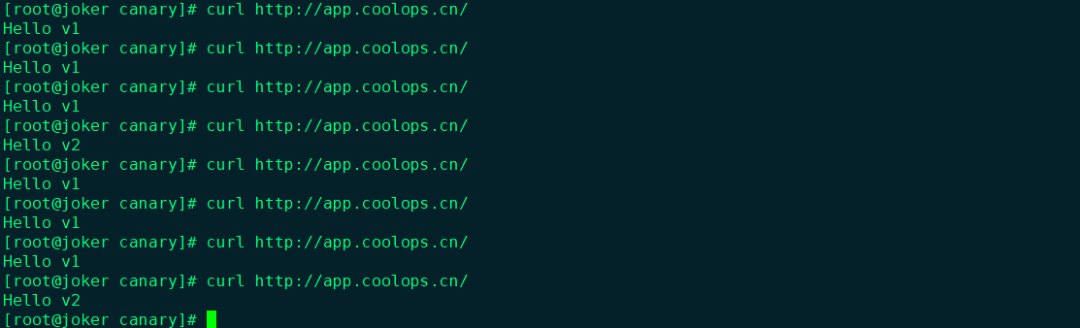
After the V2 test is OK, you can switch the flow to v2.
Traffic replication
After Traefik 2.0, the image service [11] is also introduced. It can copy the requested traffic and send it to other services according to rules, and will ignore the response of these requests.
This function is still very useful when doing some pressure measurement or problem recurrence.
Here is still a simple demonstration of the above-mentioned appv1 and appv2.
1. Create a traifikservice and define replication rules
apiVersion: traefik.containo.us/v1alpha1
kind: TraefikService
metadata:
name: app-mirror
spec:
mirroring:
name: appv1
port: 80
mirrors:
- name: appv2
percent: 50
port: 80
The above definition means that 50% of the requests to appv1 are copied to appv2.
2. Create ingressRoute and demonstrate the effect
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: app-ingressroute-mirror
spec:
entryPoints:
- web
routes:
- match: Host(`mirror.coolops.cn`)
kind: Rule
services:
- name: app-mirror
kind: TraefikService
Then test, the effect is as follows:
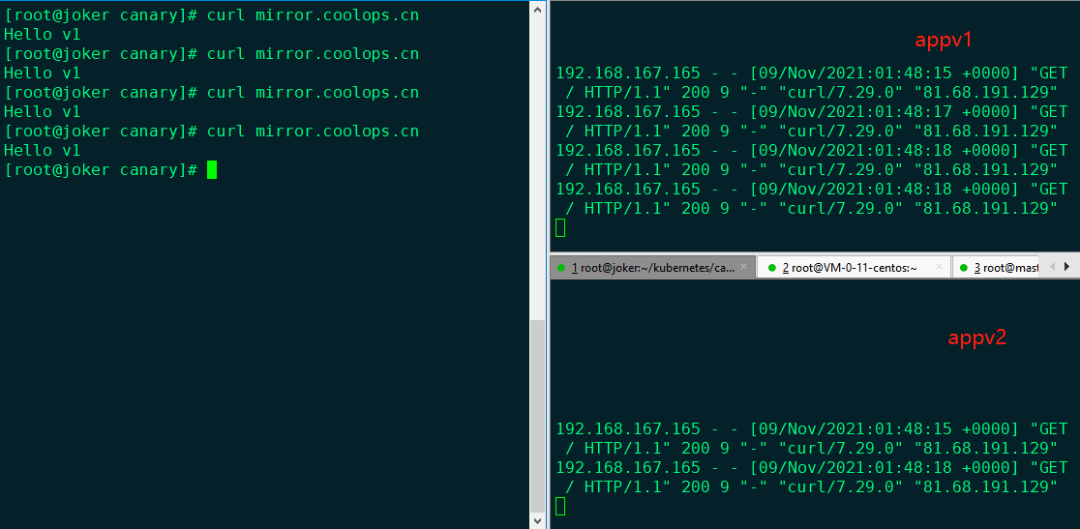
After four requests, appv1 can normally receive four requests, and appv2 can receive two requests. The received response is from appv1, but there is no response from appv2.
Kubernetes Gateway API
We create routing rules using either ingress or ingresroute. In fact, after Traefik 2.4, we support the CRD method provided by kubernets gateway API [12] to create routing rules.
What is the Gateway API?
Gateway API [13] is an open source project managed by SIG-NETWORK community. It is a collection of resources for the Service network model in Kubernetes. These resources (GatewayClass, gateway, HTTPRoute, tcroute, Service) aim to develop Kubernetes Service network through expressive, extensible and role-oriented interfaces. These interfaces are implemented by many suppliers and have been widely supported by the industry.
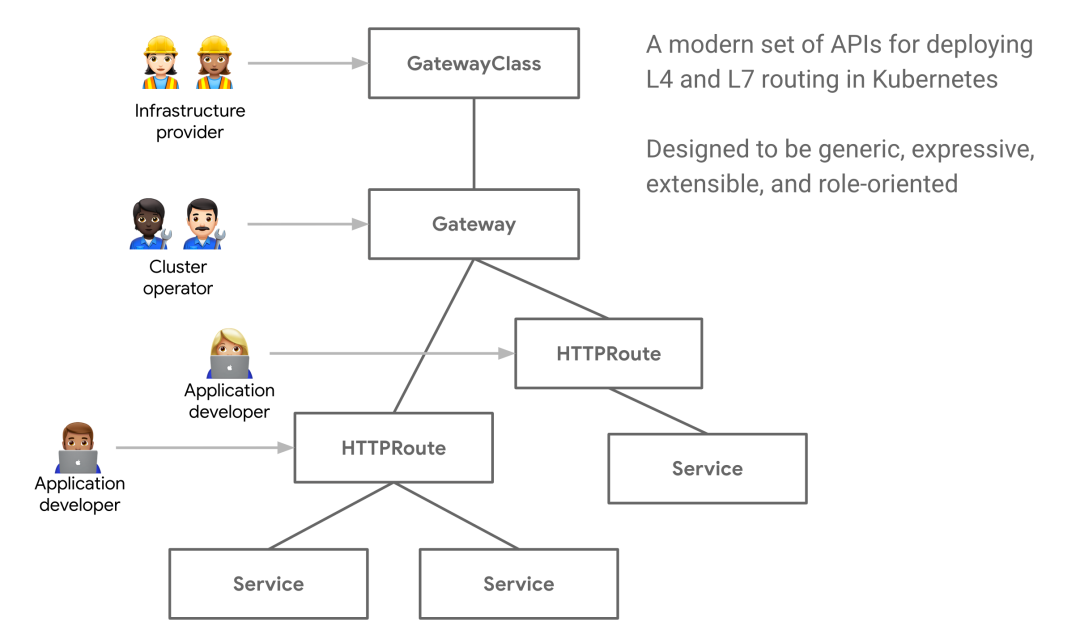
image.png
- Gateway class: gateway class is a cluster wide resource defined by the infrastructure provider. This resource represents the gateway class that can be instantiated. Generally, this resource is used to support multiple infrastructure providers. Here, we only need to deploy one.
- Gateway: the lifecycle of gateway and infrastructure configuration is 1:1. When a user creates a gateway, the gateway class controller provides or configures some load balancing infrastructure.
- HTTPRoute: HTTPRoute is a gateway API type that specifies the routing behavior of HTTP requests from gateway listeners to API objects (i.e. services).
Using the Gateway API
1. Install CRD for Gateway API
Traifik gateway provider only supports v0.3.0 (v1alpha1)
kubectl kustomize "github.com/kubernetes-sigs/gateway-api/config/crd?ref=v0.3.0" \ | kubectl apply -f -
2. Create rbac and authorize traefik
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: gateway-role
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- networking.x-k8s.io
resources:
- gatewayclasses
- gateways
- httproutes
- tcproutes
- tlsroutes
verbs:
- get
- list
- watch
- apiGroups:
- networking.x-k8s.io
resources:
- gatewayclasses/status
- gateways/status
- httproutes/status
- tcproutes/status
- tlsroutes/status
verbs:
- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: gateway-controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: gateway-role
subjects:
- kind: ServiceAccount
name: traefik
namespace: traefik-ingress
2. Traefik enables gateway api support
Modify the my-value.yaml file as follows:
...... additionalArguments: - "--entryPoints.redis.address=:6379" - "--serversTransport.insecureSkipVerify=true" - "--api.insecure=true" - "--api.dashboard=true" - "--certificatesresolvers.coolops.acme.email=coolops@163.com" - "--certificatesresolvers.coolops.acme.storage=/data/acme.json" - "--certificatesresolvers.coolops.acme.httpchallenge=true" - "--certificatesresolvers.coolops.acme.httpchallenge.entrypoint=web" - "--experimental.kubernetesgateway" - "--providers.kubernetesgateway"
Update traifik with the following command:
helm upgrade traefik -n traefik-ingress -f my-value.yaml .
4. Expose the traefik dashboard application through the Gateway api
(1) , create GatewayClass
apiVersion: networking.x-k8s.io/v1alpha1 kind: GatewayClass metadata: name: traefik spec: controller: traefik.io/gateway-controller
(2) , create a gateway
apiVersion: networking.x-k8s.io/v1alpha1
kind: Gateway
metadata:
name: http-gateway
namespace: traefik-ingress
spec:
gatewayClassName: traefik
listeners:
- protocol: HTTP
port: 8000
routes:
kind: HTTPRoute
namespaces:
from: All
selector:
matchLabels:
app: traefik
(3) , create HTTPRoute
apiVersion: networking.x-k8s.io/v1alpha1
kind: HTTPRoute
metadata:
name: whoami-gateway-api-route
namespace: traefik-ingress
labels:
app: traefik
spec:
hostnames:
- "traefik1.coolops.cn"
rules:
- matches:
- path:
type: Prefix
value: /
forwardTo:
- serviceName: traefik
port: 9000
weight: 1
(4) Now you can access it directly in the browser

image.png
Only one Gateway class can be created in the cluster, and then the Gateway and HTTPRoute need to be corresponding.
For example, if I want to expose the whoami application under the default namespace here, YAML should be as follows:
apiVersion: networking.x-k8s.io/v1alpha1
kind: Gateway
metadata:
name: http-gateway
spec:
gatewayClassName: traefik
listeners:
- protocol: HTTP
port: 8000
routes:
kind: HTTPRoute
namespaces:
from: All
selector:
matchLabels:
app: whoami
---
apiVersion: networking.x-k8s.io/v1alpha1
kind: HTTPRoute
metadata:
name: whoami-gateway-api-route
labels:
app: whoami
spec:
hostnames:
- "whoami8.coolops.cn"
rules:
- matches:
- path:
type: Prefix
value: /
forwardTo:
- serviceName: whoami
port: 80
weight: 1
last
Traefik is a powerful edge gateway, which can basically meet the needs of most scenarios. In addition, there are tools such as Mesh, which are easy to use. Interested friends can learn from the official website [14], and are also welcome to communicate.
Finally, ask for attention. If you want to see more original articles, please pay attention to our official account, "operation and development story".
If my article is helpful to you, please also like, read and forward it. Your support will encourage me to output higher quality articles. Thank you very much!
You can also set my official account as "star sign", so that when the official account is updated, you will receive the push message at the first time, so that you will not miss my update.
Official account official account of migrant workers, cloud and native workers. There are not only hard core technology dry cargo, but also our thinking and understanding of technology. Welcome to pay attention to our public number and expect to grow with you!
quote
[1] https://doc.traefik.io/traefik/ [2] https://github.com/traefik/traefik-helm-chart/blob/master/traefik/values.yaml [3] https://doc.traefik.io/traefik/providers/kubernetes-crd/ [4] https://github.com/traefik/whoami [5] https://letsencrypt.org/zh-cn/ [6] https://doc.traefik.io/traefik/https/acme/ [7] https://doc.traefik.io/traefik/https/acme/#tlschallenge [8] https://go-acme.github.io/lego/dns/alidns/ [9] https://doc.traefik.io/traefik/middlewares/http/overview/ [10] https://doc.traefik.io/traefik/routing/routers/#configuring-tcp-routers [11] https://doc.traefik.io/traefik/routing/services/#mirroring-service [12] https://doc.traefik.io/traefik/providers/kubernetes-gateway/ [13] https://gateway-api.sigs.k8s.io/ [14] https://traefik.io/