Nginx Optimization Practice (process management, anti-theft chain)
Keywords:
Linux
Nginx
vim
DNS
IIS
Nginx process management instance:
[root@nginx nginx-1.12.2]# cd /usr/local/nginx/
[root@nginx nginx]# ls
client_body_temp fastcgi_temp logs sbin uwsgi_temp
conf html proxy_temp scgi_temp
[root@nginx nginx]# cd conf/
[root@nginx conf]# vim nginx.conf
//Set timeout
keepalive_timeout 65 180;
client_header_timeout 80;
client_body_timeout 80;
//After modification, press Esc to exit the insertion mode, enter: wq to save and exit
[root@nginx conf]# service nginx stop
[root@nginx conf]# service nginx start
[root@nginx conf]# ps aux | grep nginx
root 53792 0.0 0.0 20548 620 ? Ss 14:15 0:00 nginx: master process /usr/local/nginx/sbin/nginx
nginx 53794 0.0 0.0 23076 1396 ? S 14:15 0:00 nginx: worker process
root 53818 0.0 0.0 112728 972 pts/0 R+ 14:15 0:00 grep --color=auto nginx
//At this time, the status is a master process and a worker process
[root@nginx conf]#init 0
Expand the CUP in virtual machine settings as follows:
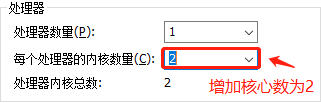
//To view the number of cpu cores:
[root@nginx ~]# cd /proc/
[root@nginx proc]# ls
1 1607 1881 2016 247 33 499 587 992 kcore softirqs
10 1613 1892 2074 2476 364 5 589 997 keys stat
100 1620 19 21 248 381 500 599 acpi key-users swaps
101 1621 1901 2119 25 391 501 6 buddyinfo kmsg sys
1010 1679 1907 2168 256 394 502 601 bus kpagecount sysrq-trigger
1011 1684 1914 22 257 396 503 604 cgroups kpageflags sysvipc
1012 17 1920 2244 258 4 504 605 cmdline loadavg timer_list
1044 1772 1934 2294 270 41 505 606 consoles locks timer_stats
11 1787 1946 23 283 42 506 608 cpuinfo mdstat tty
......Many lines are omitted here, among which there are some we need to see cpuinfo
[root@nginx proc]# cat cpuinfo
//First core:
processor : 0
vendor_id : GenuineIntel
cpu family : 6
model : 142
model name : Intel(R) Core(TM) i5-8265U CPU @ 1.60GHz
stepping : 11
microcode : 0x9a
cpu MHz : 1799.452
cache size : 6144 KB
physical id : 0
siblings : 2
core id : 0
cpu cores : 2
apicid : 0
initial apicid : 0
fpu : yes
fpu_exception : yes
cpuid level : 22
wp : yes
//Second core:
processor : 1
vendor_id : GenuineIntel
cpu family : 6
model : 142
model name : Intel(R) Core(TM) i5-8265U CPU @ 1.60GHz
stepping : 11
microcode : 0x9a
cpu MHz : 1799.452
cache size : 6144 KB
physical id : 0
siblings : 2
core id : 1
cpu cores : 2
apicid : 1
initial apicid : 1
fpu : yes
fpu_exception : yes
cpuid level : 22
wp : yes
[root@nginx proc]# cd /usr/local/nginx/conf/
[root@nginx conf]# vim nginx.conf
worker_processes 2; //Change core number 1 to 2
//Next, average the distribution
worker_cpu_affinity 01 10; //Insert this row
//After modification, press Esc to exit the insertion mode, enter: wq to save and exit
[root@nginx conf]# service nginx start
[root@nginx conf]# ps aux | grep nginx
avahi 573 0.0 0.0 30248 1788 ? Ss 14:26 0:00 avahi-daemon: running [nginx.local]
root 2759 0.0 0.0 20548 624 ? Ss 14:45 0:00 nginx: master process /usr/local/nginx/sbin/nginx
nginx 2760 0.0 0.0 23076 1400 ? S 14:45 0:00 nginx: worker process
nginx 2761 0.0 0.0 23076 1400 ? S 14:45 0:00 nginx: worker process
root 2782 0.0 0.0 112732 972 pts/0 S+ 14:45 0:00 grep --color=auto nginx
//There are two worker processes at this time
Nginx anti theft chain
Create page in win10:
<html>
<head>
<title>Happy every day</title>
</head>
<body>
<h1>this is happy web</h1>
<img src="http://www.kgc.com/lf.png"/>
</body>
</html>
Install IIS service in win10 virtual machine:
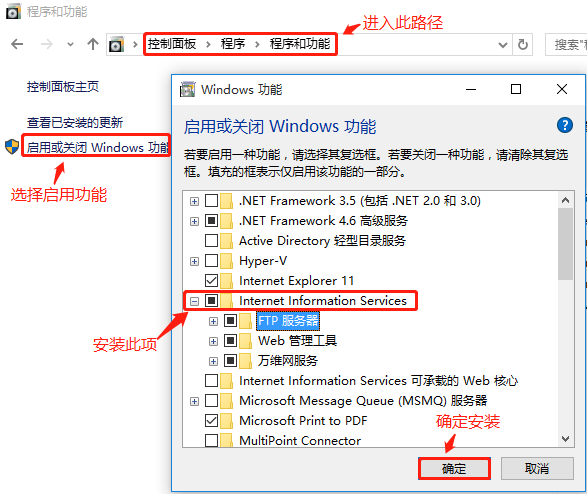
Put the written web page in the following path: C:\inetpub\wwwroot
Turn off firewall function at the same time
install DNS Services:
[root@nginx conf]# yum install bind -y
Change the DNS address of win10 and win7 to 192.168.18.136
[root@nginx conf]# vim /etc/named.conf
options {
listen-on port 53 { any; }; //Change 127 in brackets to any
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; }; //Change localhost in brackets to any
//After modification, press Esc to exit the insertion mode, enter: wq to save and exit
[root@nginx conf]# vim /etc/named.rfc1912.zones
zone "kgc.com" IN {
type master;
file "kgc.com.zone";
allow-update { none; };
};
//Add the above content, press Esc to exit the insertion mode after modification, enter: wq to save and exit
[root@nginx conf]# cd /var/named/
[root@nginx named]# cp -p named.localhost kgc.com.zone
[root@nginx named]# vim kgc.com.zone
$TTL 1D
@ IN SOA @ rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 127.0.0.1
www IN A 192.168.18.136
//After modification, press Esc to exit the insertion mode, enter: wq to save and exit
[root@nginx named]# systemctl start named
[root@nginx named]# systemctl stop firewalld.service
[root@nginx named]# setenforce 0
In win10 and win7 systems, use cmd tool to input nslookup www.kgc.com for domain name resolution, and the results are as follows:
C:\Users\zhou>nslookup www.kgc.com
//Server: UnKnown
Address: 192.168.18.136
//Name: www.kgc.com
Address: 192.168.18.136
We use win7 to visit the IP address of win10: 192.168.18.139 to get the page after stealing the chain:
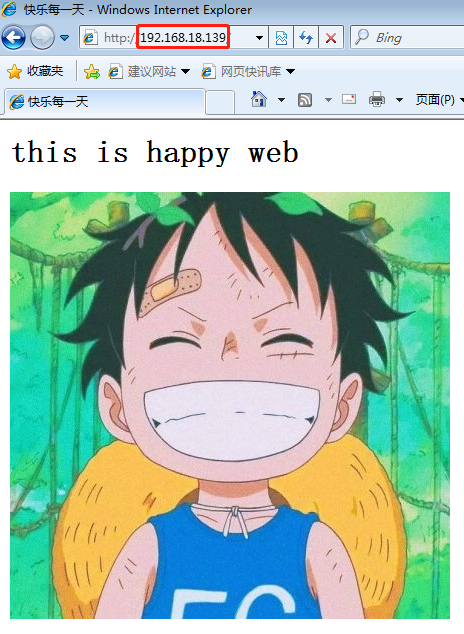
We use win7 to visit www.kgc.com and get the normal welcome interface of Nginx:
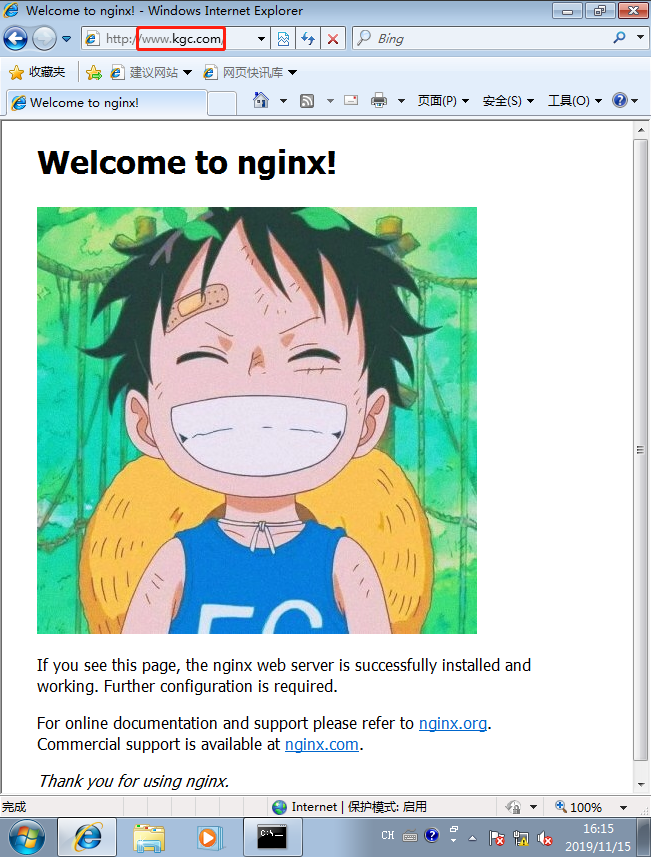
At this time to steal chain success! What we need to do next is to do anti-theft chain in Nginx!
[root@nginx named]# cd /usr/local/nginx/conf/
[root@nginx conf]# vim nginx.conf
root html;
}
//Insert the following below the line above
location ~*\.(jpg|gif|swf)$ {
valid_referers none blocked *.kgc.com kgc.com;
if ( $invalid_referer ) {
rewrite ^/ http://www.kgc.com/yy.png;
}
}
//After modification, press Esc to exit the insertion mode, enter: wq to save and exit
[root@nginx conf]# cp /aaa/yy.png /usr/local/nginx/html/
[root@nginx conf]# cd ../html/
[root@nginx html]# ls
50x.html index.html lf.jpg yy.png
[root@nginx conf]# service nginx stop
[root@nginx conf]# service nginx start
We use win7 to access the IP address of win10: 192.168.18.139. At this time, the image of the anti-theft chain will pop up:
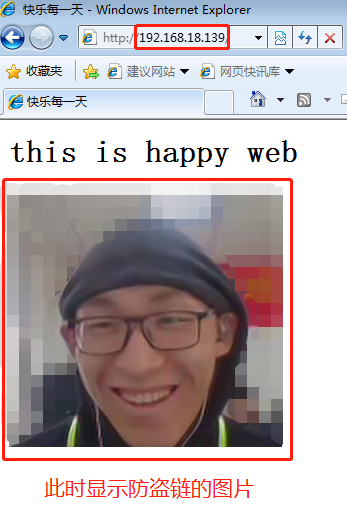
At this time, the anti-theft chain is a great success!
Posted by newcastle_unite on Fri, 15 Nov 2019 11:09:18 -0800




