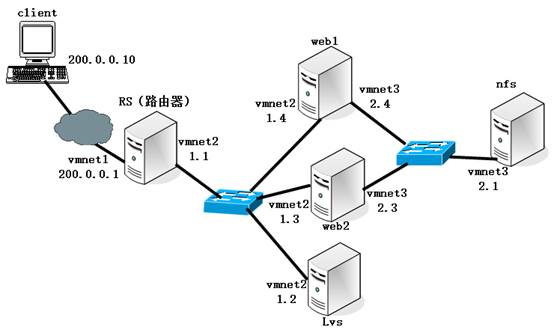
DR mode cluster. In fact, it should be the IP of the Internet. Here we simulate the phenomenon. Packet back directly from the web to the client.
Problems that may arise
1. Cluster addresses (web backpack IP is different from client requests) require vip to be established.
2. Router ARP request (need to turn off web1, web2 part of ARP response).
3. lvs turns off ICMP response (ICMP redirection problem). Both pc and router have routing optimization functions. Find a web.
Start configuring NFS without the previous document.
chkconfig NetworkManager off chkconfig iptables off cat /etc/sysconfig/selinux #This is the case with all four sets of routine business.
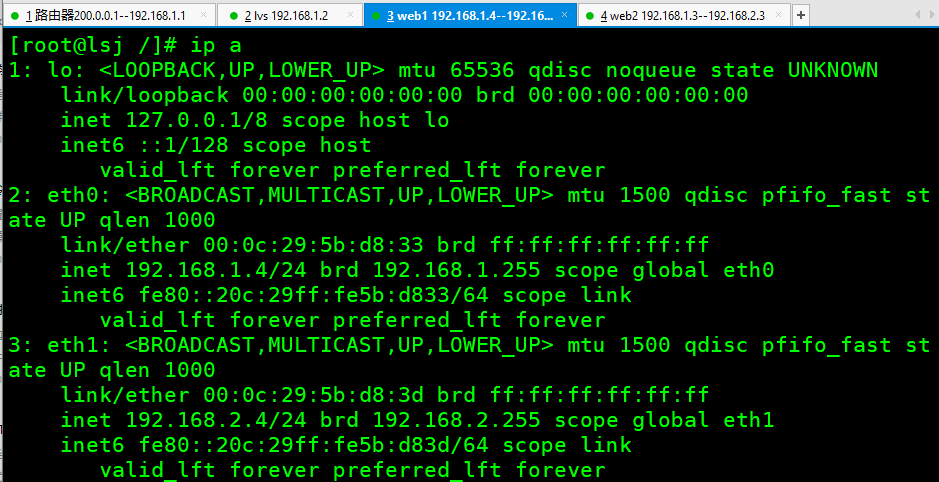
Configuring IP web1 web2 LVS requires specifying gateway 1.1
ip a #The following is the output of web1
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:5b:d8:33 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.4/24 brd 192.168.1.255 scope global eth0
inet6 fe80::20c:29ff:fe5b:d833/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:5b:d8:3d brd ff:ff:ff:ff:ff:ff
inet 192.168.2.4/24 brd 192.168.2.255 scope global eth1
inet6 fe80::20c:29ff:fe5b:d83d/64 scope link
valid_lft forever preferred_lft forever
Configure lvs
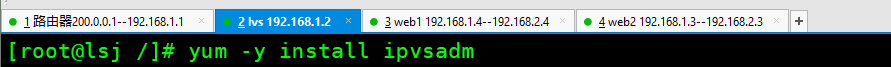
yum -y install ipvsadm
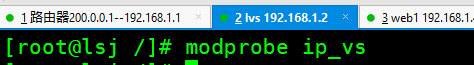
modprobe ip_vs #Enable ip_vs
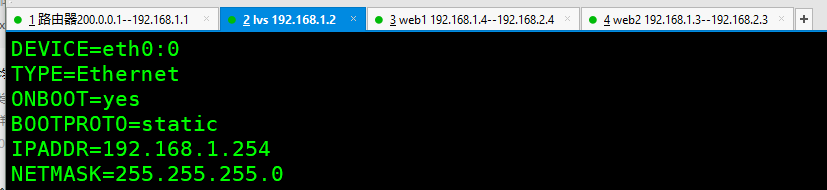
Configure virtual IP Address ( vip) cd /etc/sysconfig/network-scripts/ network-scripts]# cp ifcfg-eth0 ifcfg-eth0:0 network-scripts]# vim ifcfg-eth0:0
ip a #Output of lvs1
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:3b:69:41 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.2/24 brd 192.168.1.255 scope global eth0
inet 192.168.1.254/24 brd 192.168.1.255 scope global secondary eth0:0
inet6 fe80::20c:29ff:fe3b:6941/64 scope link
valid_lft forever preferred_lft forever
net.ipv4.ip_forward = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.eth0.send_redirects = 0 #Reorientation parameter response by turning off routing forwarding and linux kernel
sysctl -p


service ipvsadm stop ipvsadm -A -t 192.168.1.254:80 -s rr ipvsadm -a -t 192.168.1.254:80 -r 192.168.1.4:80 -g -w 1 ipvsadm -a -t 192.168.1.254:80 -r 192.168.1.3:80 -g -w 1 chkconfig ipvsadm on service ipvsadm save service ipvsadm start #Configuring load allocation strategy

web1 and web2 use the virtual interface lo:0 to host IP, which is used only as the source address for sending Web response packets. Add a routing log table to restrict access to vip data locally.
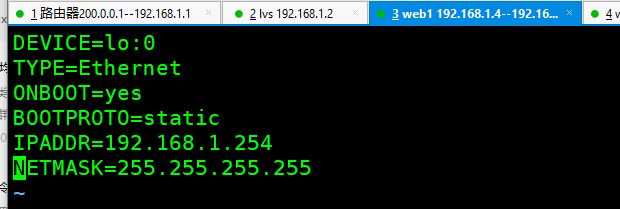
cd /etc/sysconfig/network-scripts/ network-scripts]# cp ifcfg-eth0 ifcfg-lo:0 network-scripts]# vim ifcfg-lo:0 DEVICE=lo:0 TYPE=Ethernet ONBOOT=yes BOOTPROTO=static IPADDR=192.168.1.254 NETMASK=255.255.255.255 #web1 and web2 have the same configuration #Subnet masks must have four 255
route add -host 192.168.1.254 dev lo:0 #Representatives go to 1.254 and lo:0 card is right here. cat /etc/rc.local #Add routing records, write files, boot automatically.

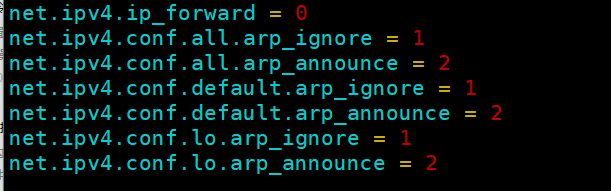
vim /etc/sysctl.conf net.ipv4.ip_forward = 0 net.ipv4.conf.all.arp_ignore = 1 net.ipv4.conf.all.arp_announce = 2 net.ipv4.conf.default.arp_ignore = 1 net.ipv4.conf.default.arp_announce = 2 net.ipv4.conf.lo.arp_ignore = 1 net.ipv4.conf.lo.arp_announce = 2 sysctl -p #Adjusting/proc ARP response parameters
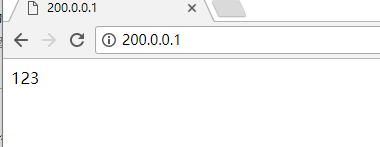
echo 123 > /var/www/html/index.html service httpd start # Establishing Web Page Test Files
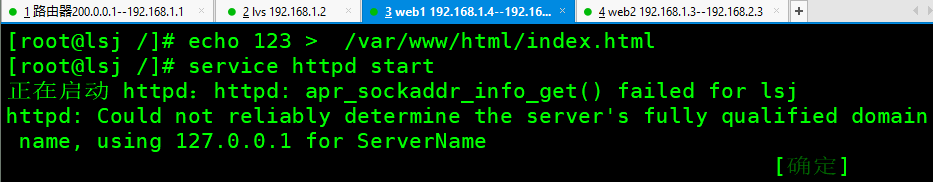
web2 has the same configuration as web1.
iptables -t nat -A PREROUTING -d 200.0.0.1 -p tcp --dport 80 -j DNAT --to 192.168.1.254:80 service iptables save chkconfig iptables on #Router Setting Firewall Rules

#Open Route Forwarding systc -p

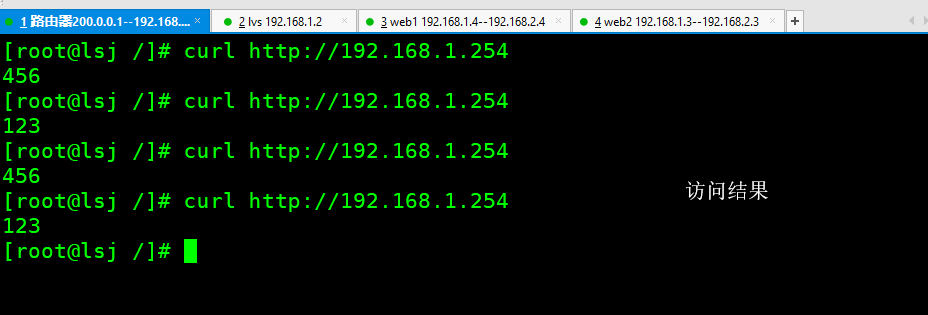
If you use client to access 200.0.0.1