introduce
The Linux kernel was originally written by Finnish Linus Torvalds as a hobby when he was studying at the University of Helsinki.
Linux is a UNIX like operating system that is free to use and spread. It is a multi-user, multi task, multi thread and multi CPU operating system based on POSIX and UNIX.
Linux can run the main UNIX tools, software, applications and network protocols. It supports 32-bit and 64 bit hardware. Linux inherits the design idea of UNIX with network as the core. It is a multi-user network operating system with stable performance.
- Linux operating system is an efficient, safe, stable, free, open source operating system with strong ability to deal with concurrency.
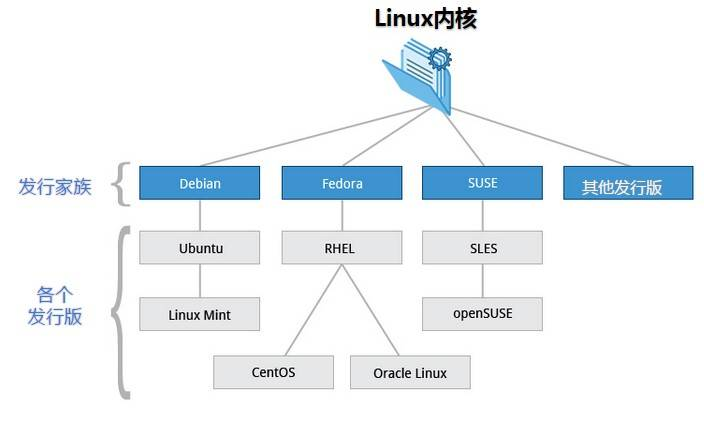
- Main distribution versions of Linux (further developed on Linux kernel): CentOS, RedHat, Ubuntu, Suse, red flag Linux (China)
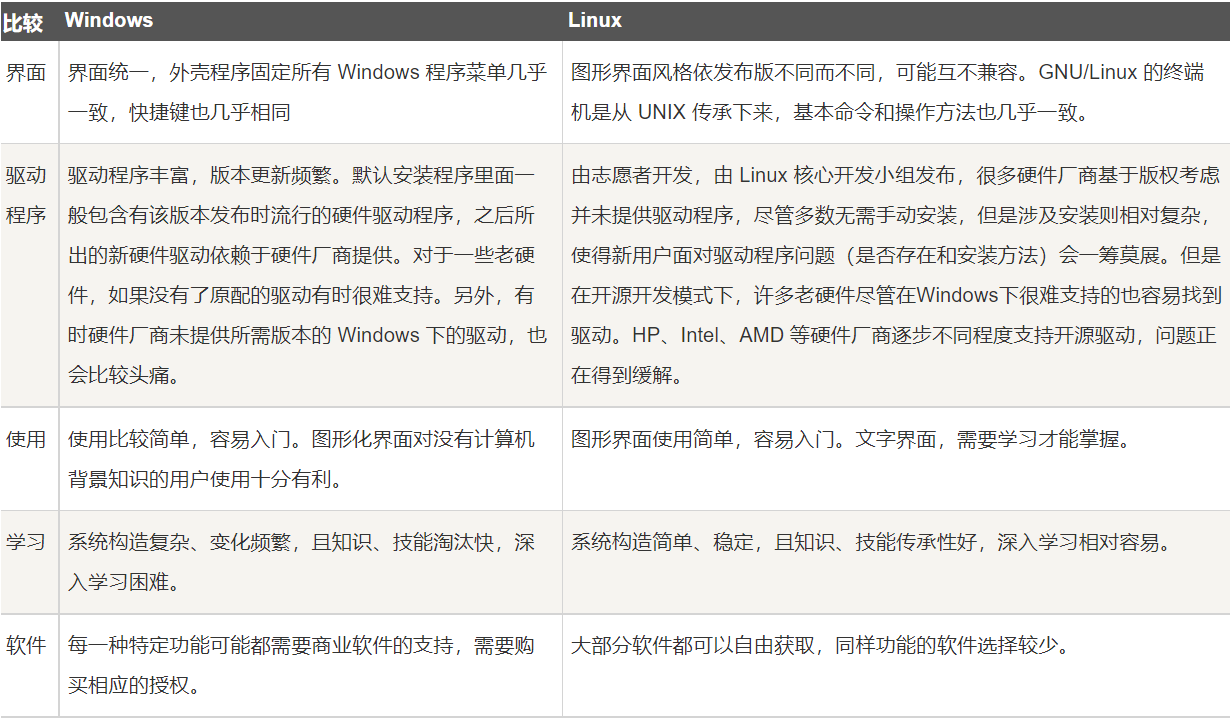
- At present, the main operating system is Windows; Android; Linux; IOS; MAC; Hongmeng
Linux Installation (VM + CentOS)
-
Boot to enter BOIS settings, and change the virtual settings to enable
-
Install VM (fool installation)
Precautions when editing virtual machine information:
CPU allocation;
Network connection analysis
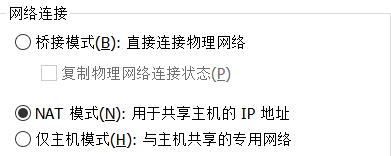
We found that there are three kinds of network connections in VM, so what do they mean
1. Bridge connection mode
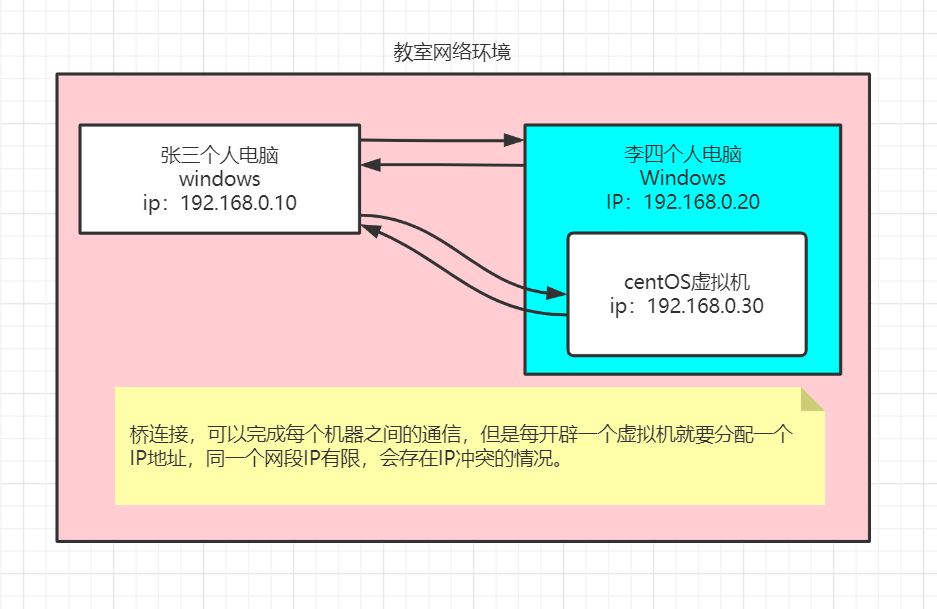
2. NAT mode
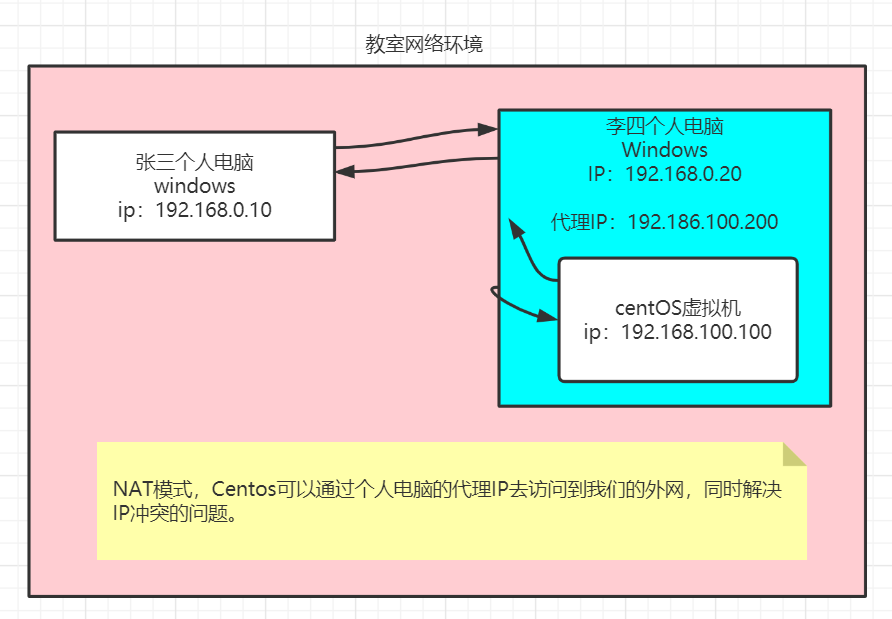
3. Host only mode: centOS system is an independent host and cannot access the external network. -
Related installation through image
Reference tutorial
Terminal use
- After installation, we will find that our system is offline
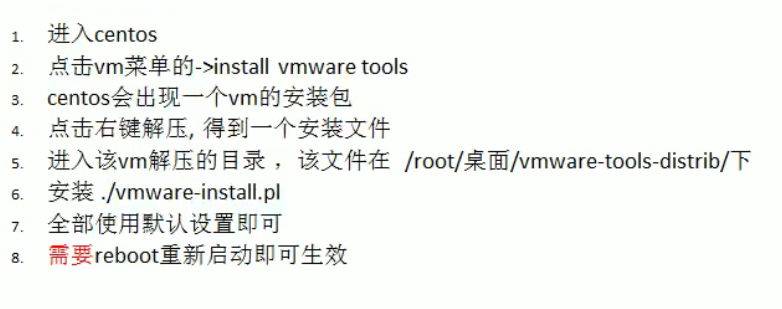
Install VMtools (you can set shared folders or copy and paste hosts and virtual machines)
Directory structure of Linux
Linux adopts a hierarchical tree directory structure, in which the top layer is "/", and other directories are established under this directory. (in the Linux world, everything is a file)
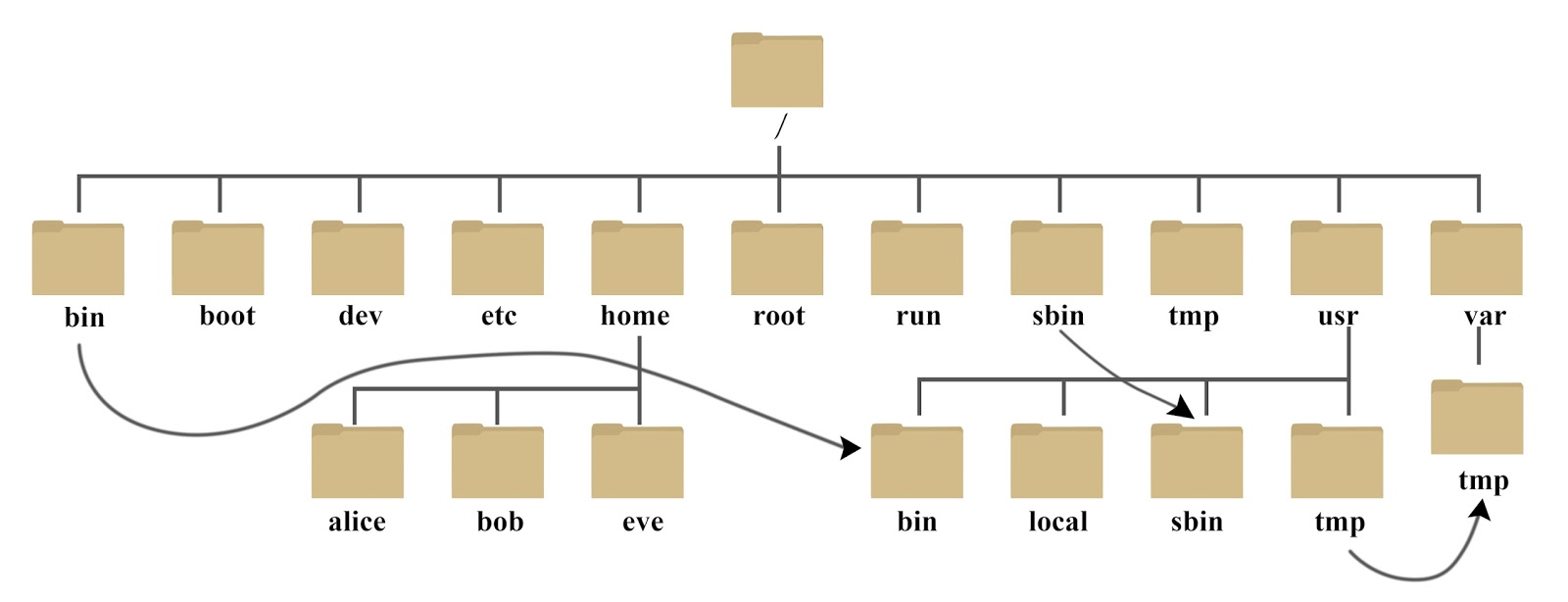
Directory structure description link
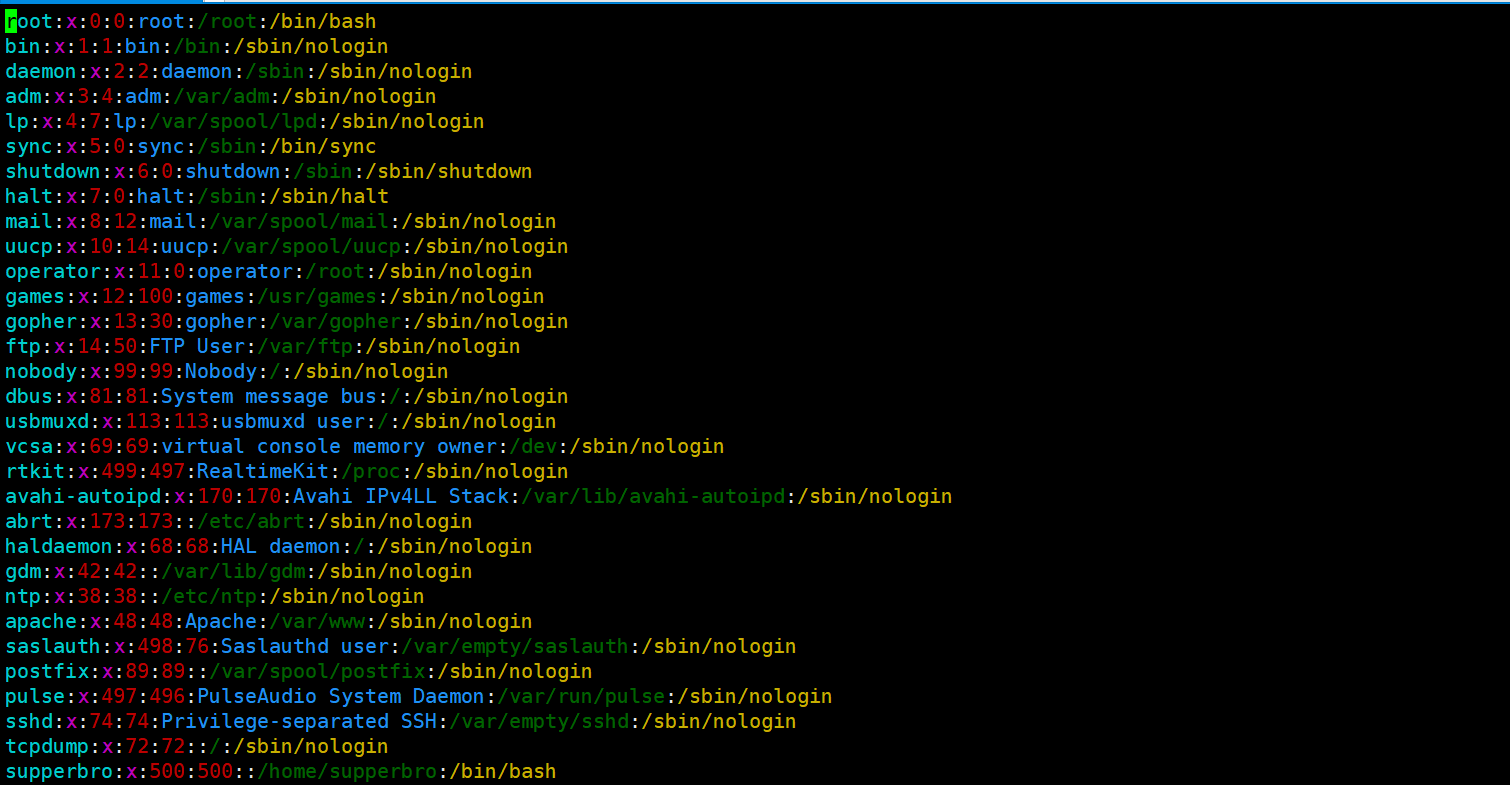
- /Bin: bin is the abbreviation of Binaries. This directory stores the most frequently used commands.
- /boot: here are some core files used when starting Linux, including some connection files and image files.
- /Dev: dev is the abbreviation of device. The external devices of Linux are stored in this directory
You access devices in the same way as you access files. - /Etc: etc is the abbreviation of etcetera (etc.), which is used to store all configuration files and subdirectories required for system management.
- /Home: the user's home directory. In Linux, each user has its own directory. Generally, the directory name is named after the user's account
- /Lib: lib is the abbreviation of library. This directory stores the most basic dynamic connection shared library of the system, which is similar to the DLL file in Windows. Almost all applications need these shared libraries.
- /lost+found: this directory is generally empty. When the system shuts down illegally, some files are stored here.
- /media: the Linux system will automatically identify some devices, such as U SB flash disk, optical drive, etc. when identified, Linux will mount the identified devices to this directory.
- /mnt: the system provides this directory to allow users to temporarily mount other file systems. We can mount the optical drive on / mnt /, and then enter this directory to view the contents of the optical drive.
- /Opt: opt is an abbreviation for optional, which is the directory where additional software is installed for the host. For example, if you install an ORACLE database, you can put it in this directory. The default is empty.
- /Proc: proc is the abbreviation of processes, / proc is a pseudo file system (i.e. virtual file system), which stores a series of special files in the current kernel running state. This directory is a virtual directory, which is the mapping of system memory. We can access this directory directly to obtain system information.
- /root: this directory is the home directory of the system administrator, also known as the super authority user.
- /sbin: s means Super User, which means Super User binaries
Here is the system management program used by the system administrator. - /selinux: this directory is unique to Redhat/CentOS. selinux is a security mechanism similar to windows firewall, but this mechanism is complex. This directory is used to store selinux related files.
- /srv: this directory stores some data to be extracted after the service is started.
- /sys: This is a big change in the Linux 2.6 kernel. A new file system sysfs in the 2.6 kernel is installed in this directory. Sysfs file system integrates the information of the following three file systems: proc file system for process information, devfs file system for device and devpts file system for pseudo terminal. The file system is a visual reflection of the kernel device tree. When a kernel object is created, the corresponding files and directories are also created in the kernel object subsystem.
- /tmp: tmp is the abbreviation of temporary. This directory is used to store some temporary files.
- /Usr: usr is the abbreviation of UNIX shared resources. It is a very important directory. Many user applications and files are placed in this directory, similar to the program files directory under windows.
- /usr/bin: application used by system users.
- /usr/sbin: a more advanced hypervisor and system daemon used by super users.
- /usr/src: the default placement directory for kernel source code.
- /var: var is the abbreviation of variable. There are expanding things stored in this directory. We are used to putting those directories that are often modified under this directory. Including various log files.
- /Run: a temporary file system that stores information since the system was started. When the system restarts, the files in this directory should be deleted or cleared. If you have a / var/run directory on your system, you should make it point to run.
remote access
In the actual development process, remote access is essential.
XShell (remote login) Xftp5 (remote upload and download)
Install XShell
XShell perfectly solves the problem of Chinese garbled code
-
Linux starts the sshd service to listen on port 22 and wait for the XShell link
-
Fool install XShell, link Linux
Installing Xftp5
- For fool installation, 22 ports are also selected for connection
- Solve garbled Code: you can modify it through the connection attribute option
vi and vim
Vim is a text editor developed from vi. Code completion, compilation, error jump and other convenient programming functions are particularly rich, which are widely used by programmers.
In short, vi is an old-fashioned word processor, but it has complete functions, but there is still room for improvement. vim can be said to be a good tool for program developers.
Even VIM's official website( http://www.vim.org )I also said that VIM is a program development tool rather than word processing software.
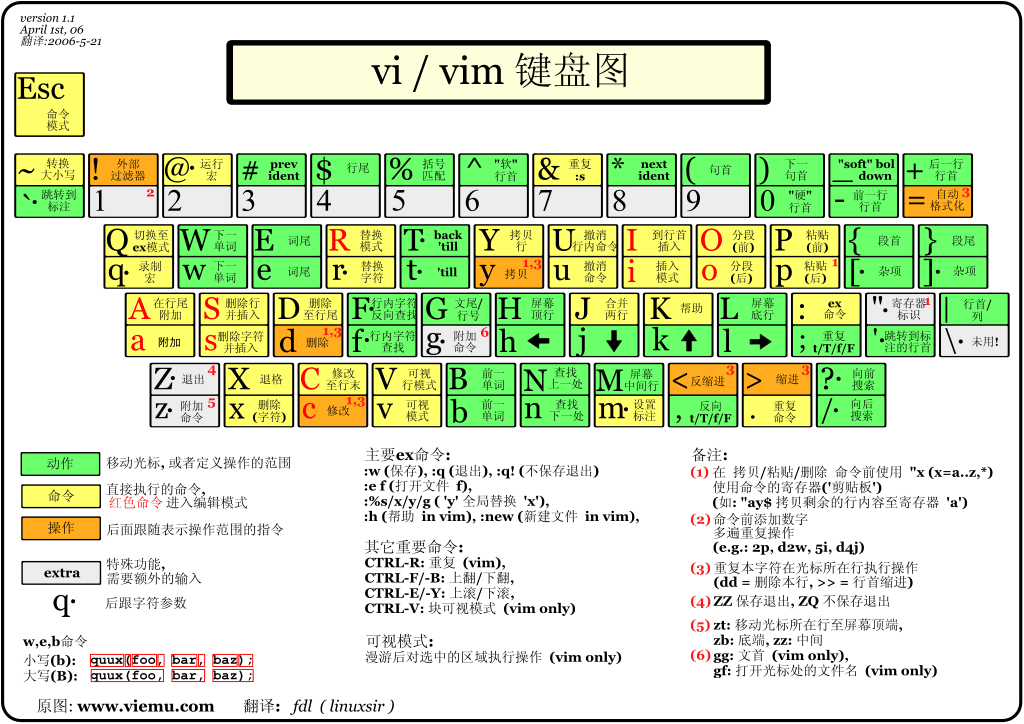
Three modes of vi/vim
-
Normal mode
As soon as the user starts vi/vim, he enters the normal mode.
In this state, the keyboard tapping action will be recognized by Vim as a command rather than an input character. For example, if we press i at this time, we will not enter a character. i is regarded as a command.
Here are some common commands:
i switch to input mode to input characters.
x deletes the character at the current cursor.
: switch to the bottom line command mode to enter the command on the bottom line.
To edit text: start Vim, enter command mode, press i, and switch to input mode. -
Edit mode / insert mode
In the command mode, press i to enter the input mode.
In input mode, the following keys can be used:
Character keys and Shift combination to enter characters
ENTER, ENTER, line feed
BACK SPACE, backspace key to delete the previous character of the cursor
DEL, delete key, delete the next character after the cursor
Direction keys to move the cursor in the text
HOME/END, move the cursor to the beginning / end of the line
Page Up/Page Down
Insert, switch the cursor to the input / replace mode, and the cursor will become a vertical line / underline
ESC, exit the input mode and switch to the command mode -
Command line mode
In the command mode, press: (English colon) to enter the bottom line command mode.
The bottom line command mode can input single or multiple character commands, and there are many available commands.
In the baseline command mode, the basic commands are (colon has been omitted):
q exit program
w save file
Press ESC to exit the bobbin thread command mode at any time.
Shortcut key details
Shutdown restart logoff
Shutdown and restart
- shutdown
shutdown -h now means shutdown immediately
shutdown -h 1 indicates that the shutdown will be performed in one minute
shutdown -r now means restart immediately - halt
When used alone, it means immediate shutdown - reboot
Restart the system - sync
Write memory data to disk.
Note: execute sync every time you restart or shut down to prevent data loss.
User login and logout
Remote login and logout
user management
Linux system is a multi-user and multi task time-sharing operating system. Any user who wants to use system resources must first apply to the system administrator for an account, and then enter the system as this account.
On the one hand, the user's account can help the system administrator track the users using the system and control their access to system resources; On the other hand, it can also help users organize files and provide security protection for users.
Each user account has a unique user name and their own password.
Users can enter the system and their home directory after entering the correct user name and password when logging in.
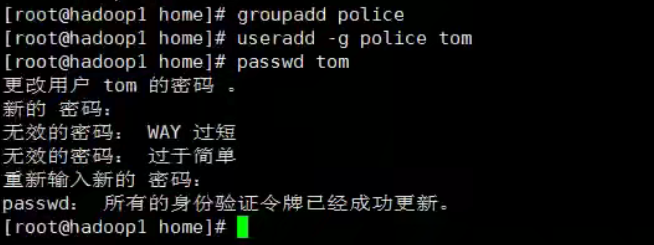
Add user
useradd Option user name option:((optional) -c comment Specify an annotative description. -d Directory specifies the user's home directory. If this directory does not exist, it will be used at the same time-m Option to create a home directory. -g User group specifies the user group to which the user belongs. -G User group. User group specifies the additional group to which the user belongs. -s Shell File specifies the user's login Shell. -u User number specifies the user number of the user, if both exist-o Option, you can reuse the identification numbers of other users. user name: Specify the login name of the new account.
Add user case
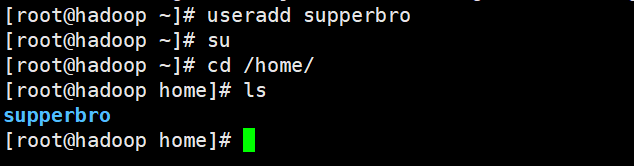
Special note: set password passwd supperbro
delete user
userdel Option user name Common options are -r,Its function is to delete the user's home directory together. Note: the user's home directory is generally not deleted in actual development.
Query user information
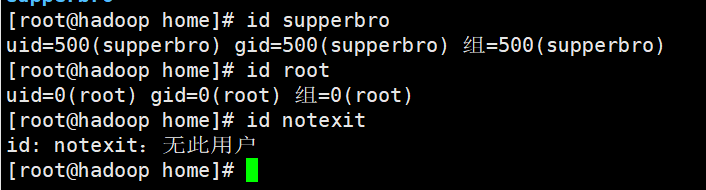
Switch users
su user name
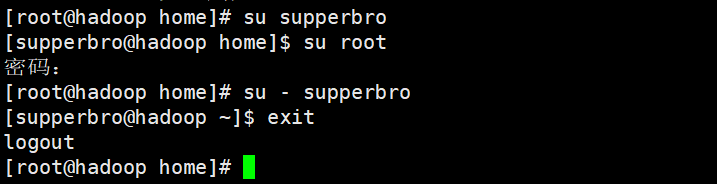
View this user
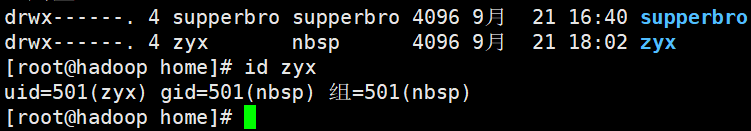
User group
Each user has a user group. The system can centrally manage all users in a user group. Different Linux systems have different regulations on user groups. For example, users under Linux belong to a user group with the same name. This user group is created at the same time when creating users.
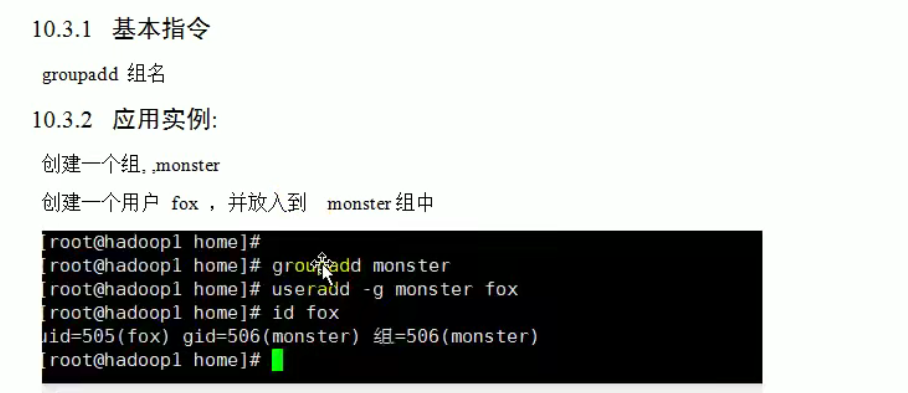
Create user group
groupadd Option user group The options available are: -g GID Specifies the group identification number for the new user group( GID). -o General and-g Options are used together to represent the name of the new user group GID You can connect with existing user groups in the system GID Same.
delete group
groupdel User group
Create a user and specify its user group
useradd -g User group user name
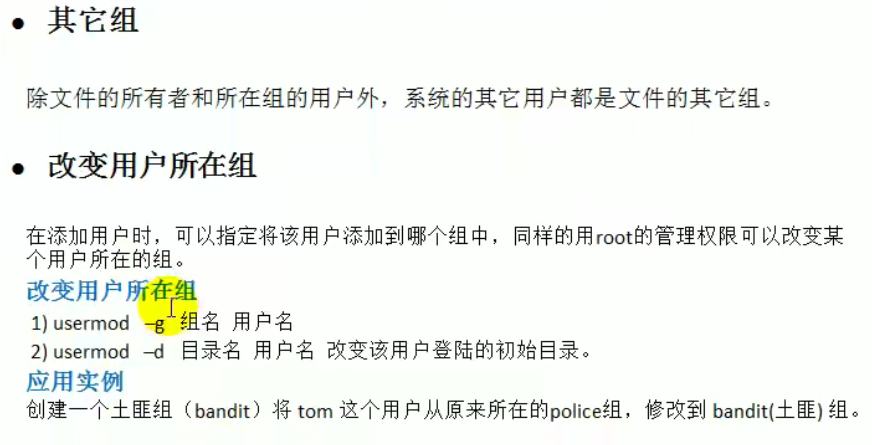
Modify user group
groupmod Option user group Common options are: -g GID Specify a new group ID for the user group. -o And-g Options are used together with the new user group GID You can connect with existing user groups in the system GID Same. -n New user group changes the name of the user group to a new name
Modify the user's group
usermod -g User group user name
System files related to user account
/The etc/passwd file is the most important file involved in user management
user name:Password:User identification number:Group identification number:Annotative description:home directory:Sign in Shell
1)"user name"Is a string representing the user account. It is usually no longer than 8 characters and consists of upper and lower case letters and/Or numbers. Login names cannot have colons(:),Because the colon is a separator here. For compatibility, it is best not to include dot characters in the login name(.),And do not use hyphens(-)Plus sign(+)Take the lead. 2)"Password "in some systems, encrypted user password words are stored. Although this field only stores the encrypted string of the user password, not clear text, but because/etc/passwd Files are readable to all users, so this is still a security risk. Therefore, many people now Linux System (e.g SVR4)All used shadow Technology to store the real encrypted user password in/etc/shadow File, and in/etc/passwd Only one special character is stored in the password field of the file, such as“ x"Or“*". 3)"User ID is an integer, which is used internally to identify users. Generally, it corresponds to the user name one by one. If the user identification numbers corresponding to several user names are the same, they will be regarded as the same user within the system, but they can have different passwords, different home directories and different logins Shell Wait. Generally, the value range of user ID is 0~65 535. 0 Super user root Identification number of, 1~99 It is reserved by the system. As a management account, the identification number of ordinary users starts from 100 Linux In the system, the limit is 500. 4)"The group ID field records the user group to which the user belongs. It corresponds to/etc/group A record in a file. 5)"The annotative description field records some personal information about the user. For example, the user's real name, telephone number, address, etc. this field has no practical use Linux The format of this field is not uniform in many systems Linux In the system, this field stores an arbitrary annotative description text for finger Output of the command. 6)"Home directory ", that is, the user's starting working directory. It is the directory where the user is located after logging in to the system. In most systems, each user's home directory is organized in the same specific directory, and the name of the user's home directory is the user's login name. Each user has read, write and execute (search) permissions on their own home directory, and the access permissions of other users to this directory are set according to the specific situation. 7)After the user logs in, it is necessary to start a process, which is responsible for transmitting the user's operation to the kernel. This process is the command interpreter or a specific program that the user runs after logging in to the system, that is Shell. Shell Are users and Linux Interface between systems. Linux of Shell There are many kinds, each with different characteristics. Commonly used are sh(Bourne Shell), csh(C Shell), ksh(Korn Shell), tcsh(TENEX/TOPS-20 type C Shell), bash(Bourne Again Shell)Wait. The system administrator can specify a user according to the system conditions and user habits Shell. If not specified Shell,Then the system uses sh Is the default login Shell,That is, the value of this field is/bin/sh. User login Shell It can also be specified as a specific program (this program is not a command interpreter). Using this feature, we can limit the user to run only the specified application. After the application runs, the user will automatically exit the system. Some Linux The system requires that only those programs registered in the system can appear in this field. 8)There is a kind of user in the system called pseudo user( pseudo users). These users are/etc/passwd There is also a record in the file, but they cannot log in because they are logged in Shell Empty. Their existence is mainly to facilitate system management and meet the requirements of corresponding system processes for file ownership. Common pseudo users are as follows: Pseudo user meaning bin Have executable user command files sys Own system files adm Own account file uucp UUCP use lp lp or lpd Subsystem usage nobody NFS use
/etc/shadow directive file
Login name:encrypted password:Last modification time:Minimum time interval:Maximum time interval:Warning time:Inactive time:Failure time:sign
"Login name"Is with/etc/passwd User account with the same login name in the file
"Password"The field stores the encrypted user password, which is 13 characters long. If it is empty, the corresponding user does not have a password and does not need a password when logging in; if it does not belong to the collection { ./0-9A-Za-z }The corresponding user cannot log in.
"Last modification time"It refers to the number of days from a certain time to the last time the user modifies the password. The time starting point may be different for different systems. For example, in SCO Linux The starting point of this time is January 1, 1970.
"Minimum time interval"It refers to the minimum number of days between two password changes.
"Maximum time interval"It refers to the maximum number of days that the password remains valid.
"Warning time"The field indicates the number of days between the system warning the user and the official expiration of the user's password.
"Inactive time"It indicates the maximum number of days that the user has no login activity but the account can remain valid.
"Failure time"The field gives an absolute number of days. If this field is used, the lifetime of the corresponding account will be given. After expiration, the account will no longer be a legal account and can no longer be used for login.
All user group information is stored in the / etc/group file
Grouping users is a means to manage users and control access rights in Linux system.
Each user belongs to a user group; there can be multiple users in a group, and a user can also belong to different groups.
When a user is a member of multiple groups at the same time, the main group to which the user belongs is recorded in the / etc/passwd file, that is, the default group to which the user belongs when logging in, while other groups are called additional groups.
When a user wants to access a file belonging to an additional group, he must first use the newgrp command to make himself a member of the group to be accessed.
All information about user groups is stored in the / etc/group file. The format of this file is also similar to that of the / etc/passwd file. Several fields are separated by colons (:). These fields are:
Group name:Password:Group identification number:List of users in the group
"Group name"Is the name of the user group, consisting of letters or numbers/etc/passwd Like the login in, the group name should not be duplicate. "Password"The field stores the password word encrypted by the user group. Generally Linux The user groups of the system do not have passwords, that is, this field is generally empty or empty*. "Group identification number"Similar to the user ID number, it is also an integer, which is used internally to identify the group. "List of users in the group"Is a list of all users belonging to this group/b],Use commas between different users(,)Separate. This user group may be the user's primary group or an additional group.
Practical instruction
Instruction level
Different command levels are specified according to different operators.
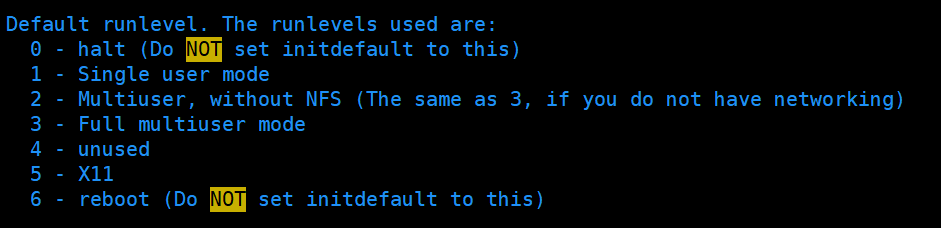
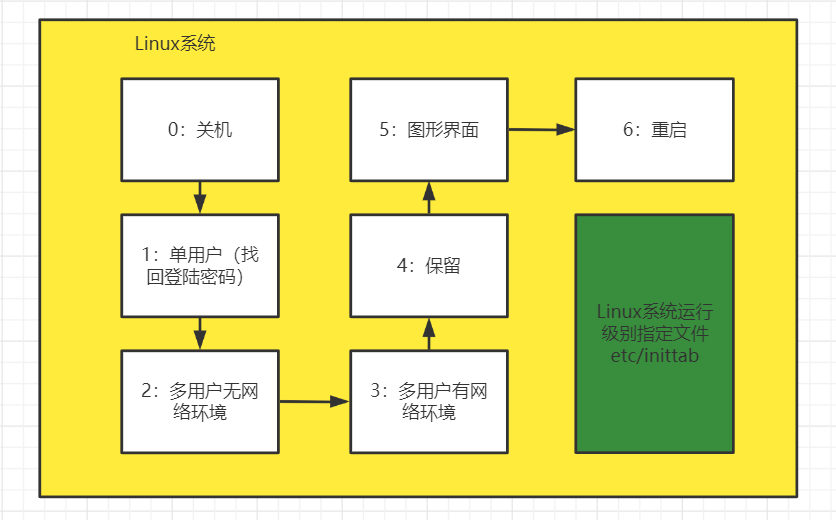
Switch level
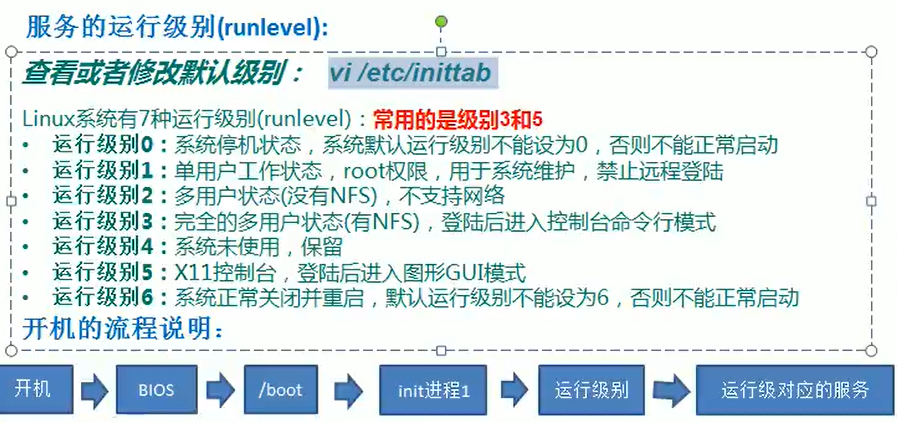
init [0123456]
interview: Linux Retrieve root Password: (remote operation is not allowed) Idea: enter the single user mode. In the single user mode, there is no need to root Password, you can get root Can be modified root password

Modifying the default instruction level of the specified file etc/inittab can also change our instruction level.

Help instruction
When we are not familiar with linux instructions, we can view the usage of instructions through help instructions.
- Get help
man [[instructions to be viewed]

2. help get instruction information
help [Instruction]
File directory class instruction
-
pwd (displays the absolute address of the current working directory)

-
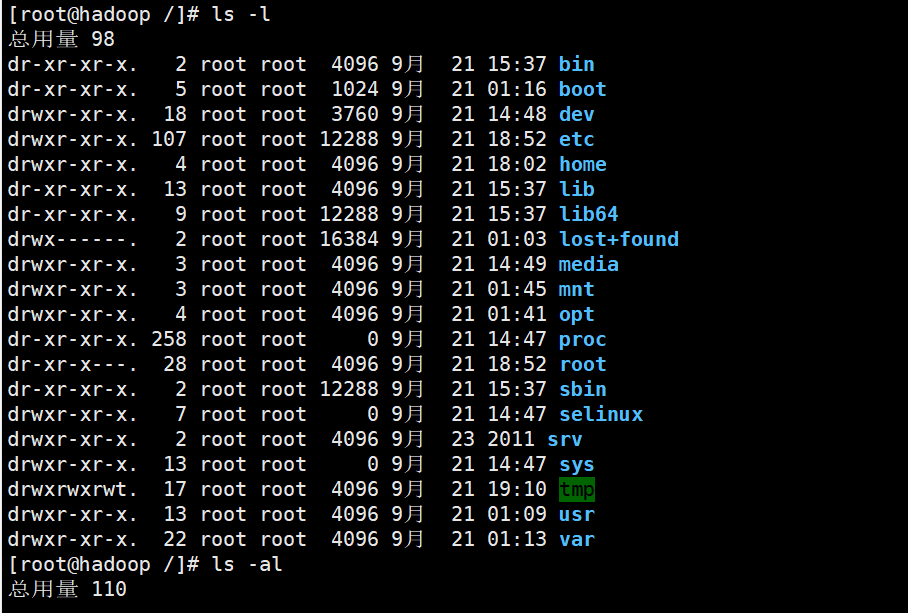
ls instruction
ls [Option] [directory or file] option -a Show hidden files -l Format display file
3. cd switching directory
cd [parameter]
cd... One level above the current directory
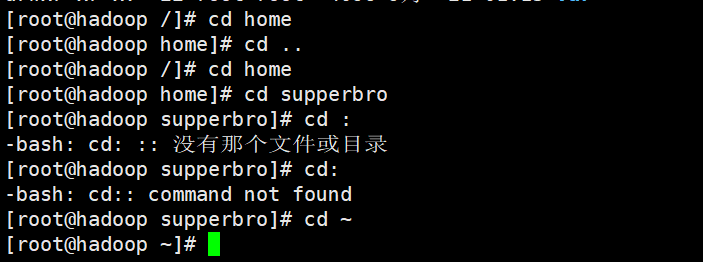
cd ~ or cd: return to the user's home directory
4. mkdir
mkdir [option] Directory to be created option -p Create multi-level directory at one time
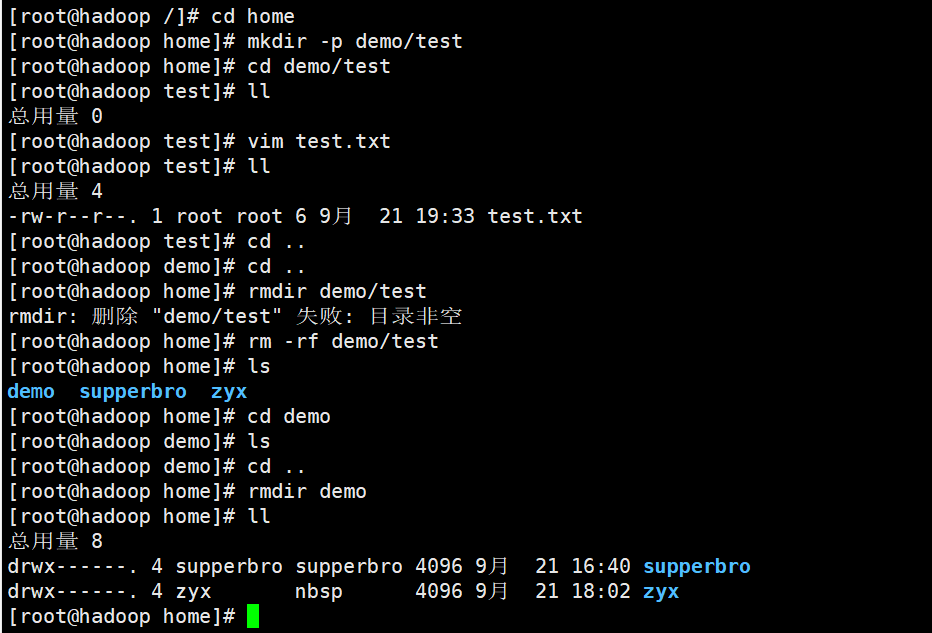
5,rmdir
rmdir [options] empty directory to be removed
Note: if the directory is not empty, it cannot be removed. You need rm -rf to remove it
6,touch
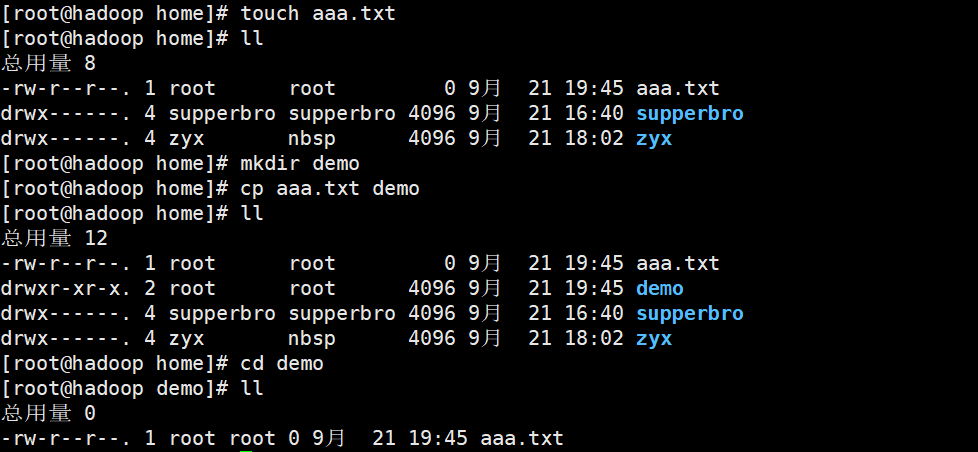
touch Files to be created Note: you can create multiple files at once
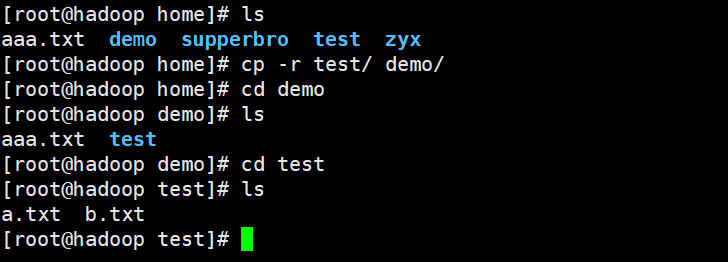
7,cp
cp [[options] source dest Options: -r Copy entire folder
8,mv
mv old new (Rename) mv /../.. /../ (Move files)
9,cat
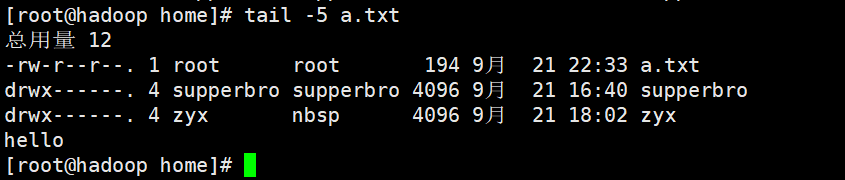
cat [Options] file (view file content, read-only) Options: -n set number
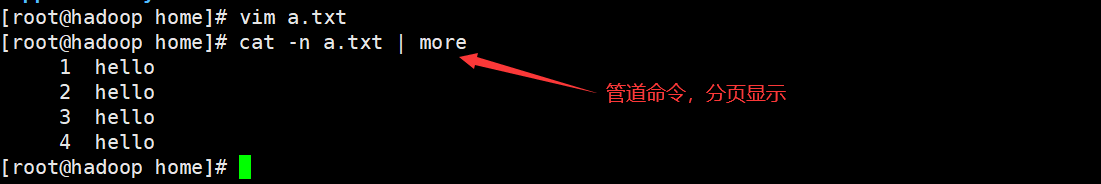
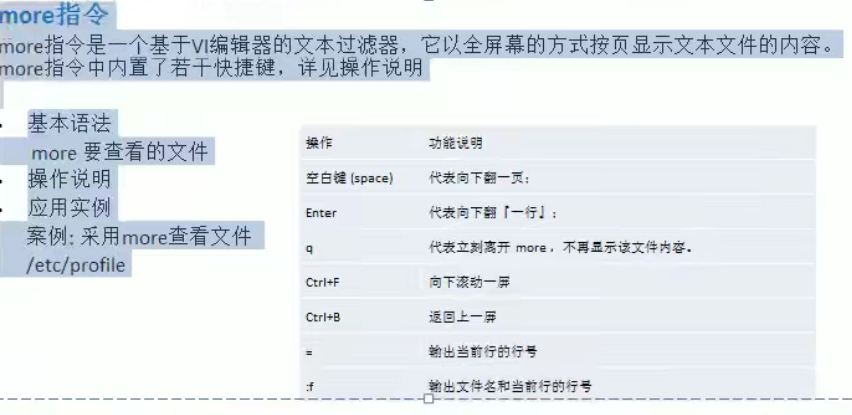
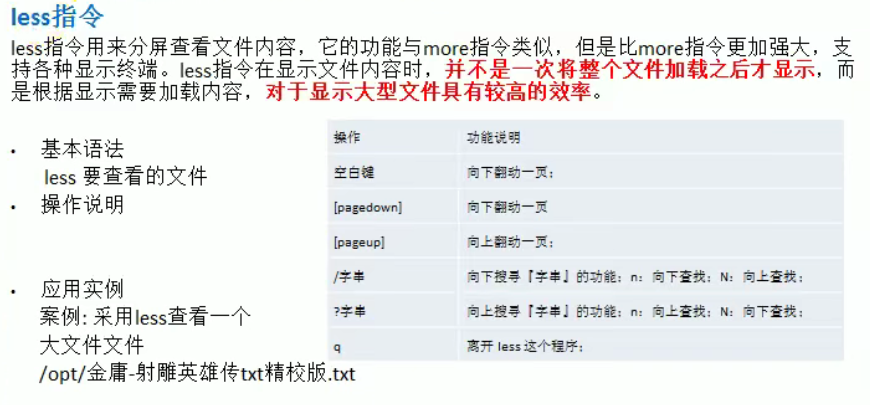
10. list instruction
11,> >>
ls -l > File (if the file exists, it will be overwritten; if it does not exist, it will be created and written)
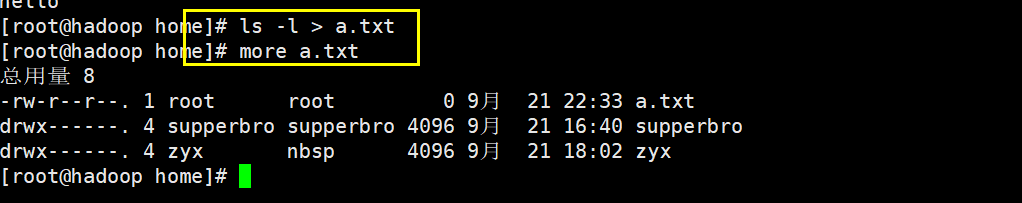
ls -al >> file(Append to end of file)
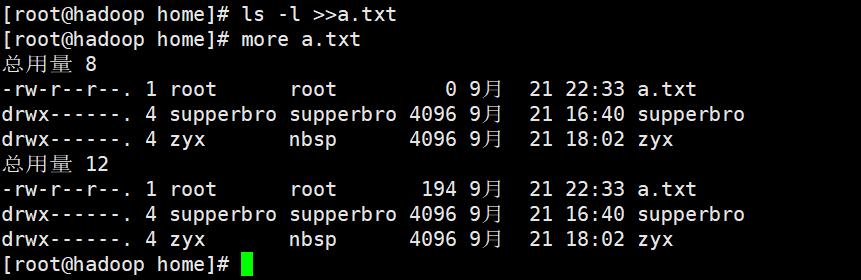
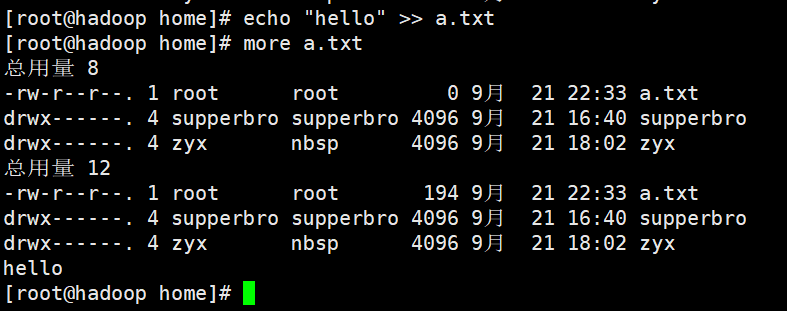
echo "" > > (append quotation marks to the end of the file)
12,echo / head / tail
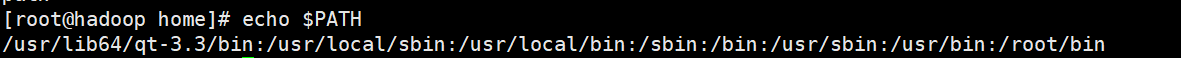
echo [Options] [text content]
For example: output the path of the current environment variable
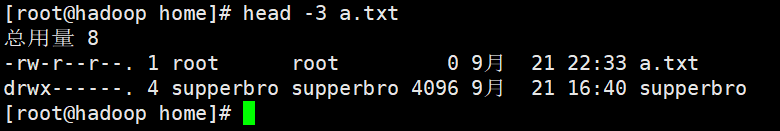
head [[options] file
head file: the default display is 10
head -n file: the first 5 lines are displayed by default
tail [[options] file
tail file (display the last 10 lines of the file)
tail -n file (display the last n lines of the file)
tail -f file (track the update of the file, monitor the file after joining, and respond to the update immediately if the file changes)
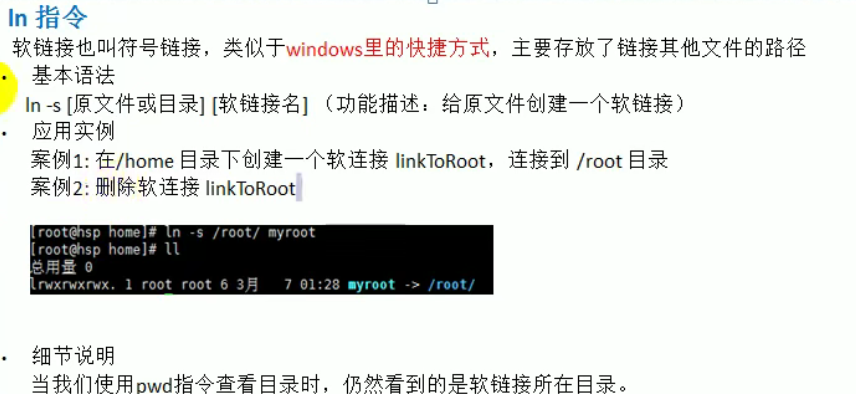
13. ln instruction
14,history
history [options] (view the instructions that have been executed on the system)
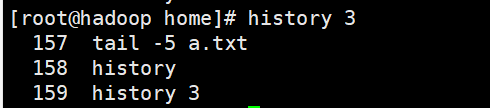
!+ Historical instruction number (executed again)
Time date class
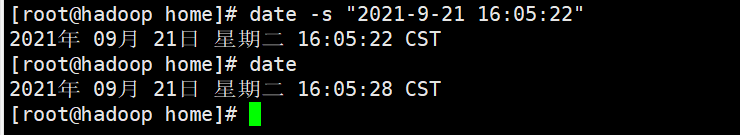
1. date instruction

date -s String (set time)
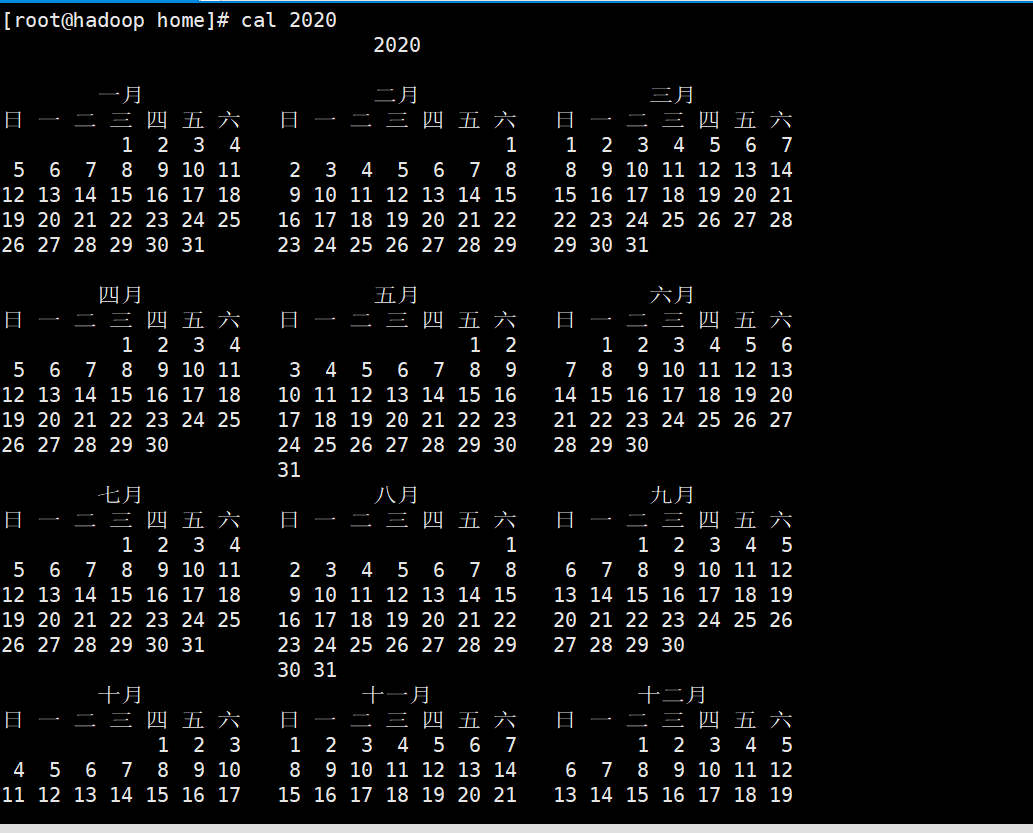
2,cal
cal [[options] (Display calendar information)
Search find class
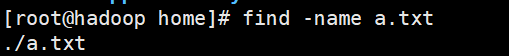
1. find instruction
The find instruction will recurse down from the specified directory once, and print the qualified instruction on the terminal.
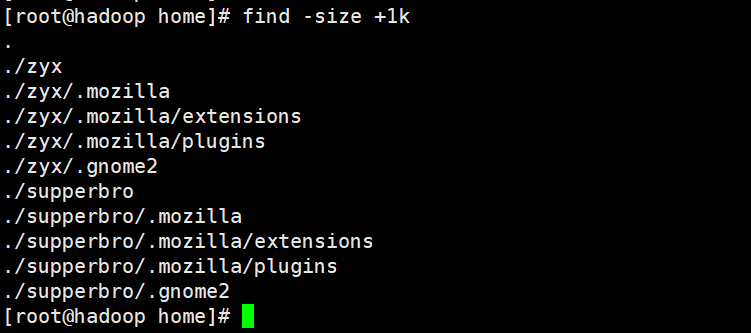
find [Search range [ options ] Option Description: -name<file name> -user<File owner> -size<file size>
Find files with file size greater than 1k
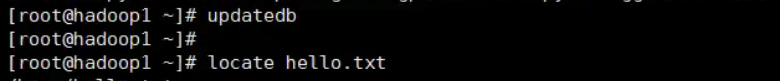
2,locate
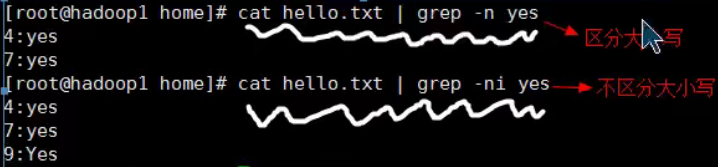
3,grep
Compression and decompression
1,gzip/gunzip

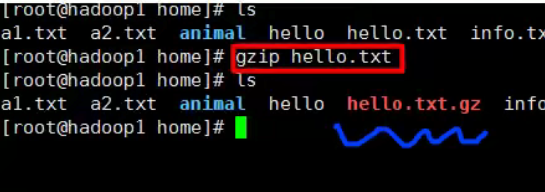
Note: after gzip compression, the original file will not be retained
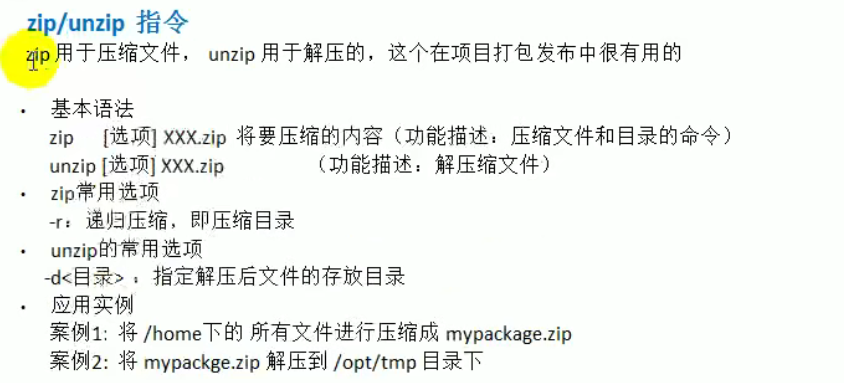
2,zip/unzip
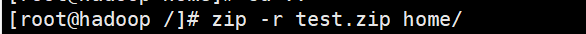
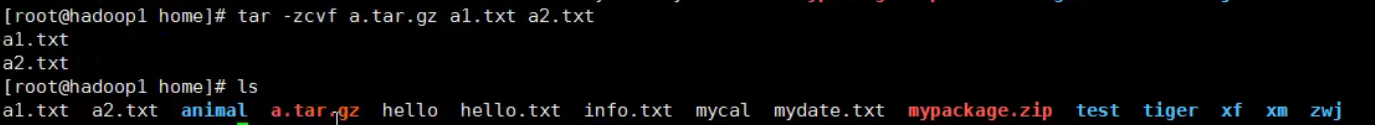
3,tar
Group management and rights management
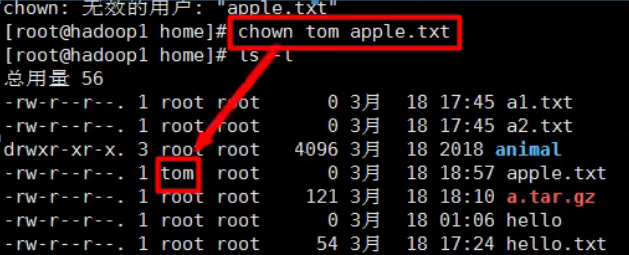
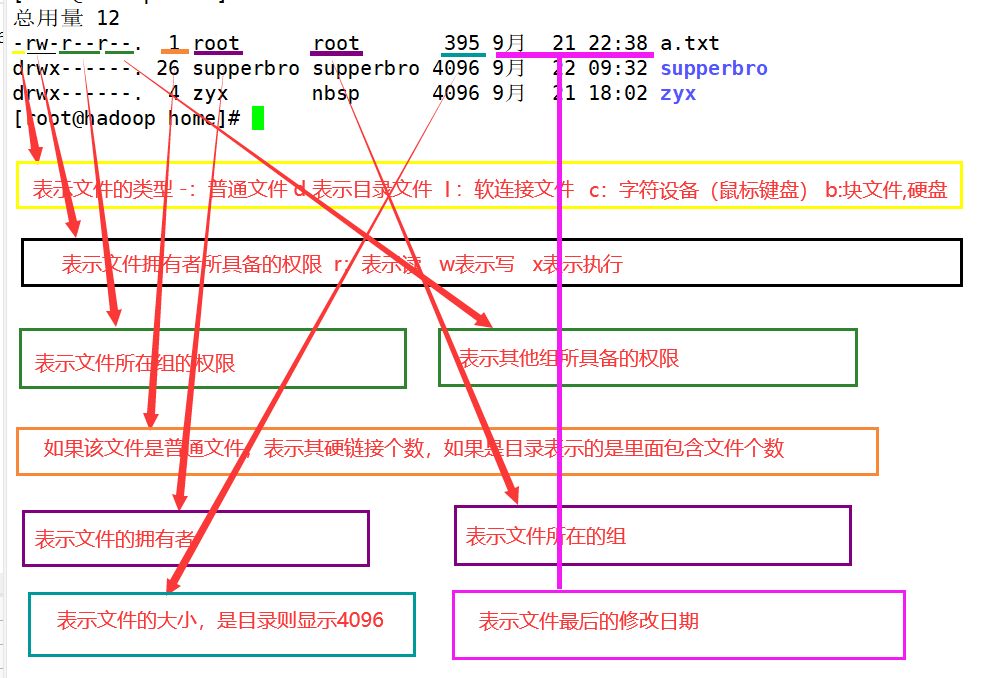
Owner of the file


Group creation
Other groups
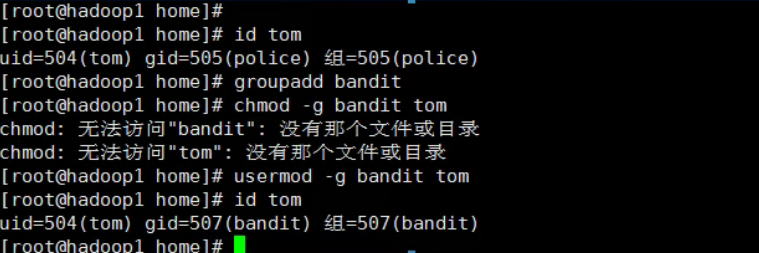
Basic introduction to permissions


Permission management - modify permission chmode
You can modify the permissions of directories or files.
- Method 1: modify the permission through + - =
u represents the owner of the file, o represents others of the file, g represents users in the same group, and a represents the sum of the first three, that is, all
chmod u=rwx, g = rwx, o=rw file name
chmod g+x file name
chmod a-r file name
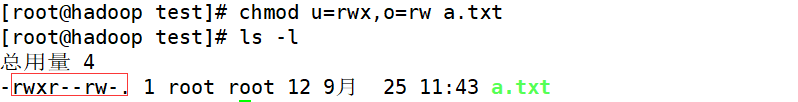
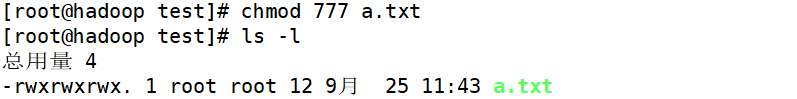
- Method 2: change authority through numbers
r=4 w=2 x=1 rwx=7
chmod u=rwx, g = rwx, o=rw file name is equivalent to chmod 776 file name
Modify file owner

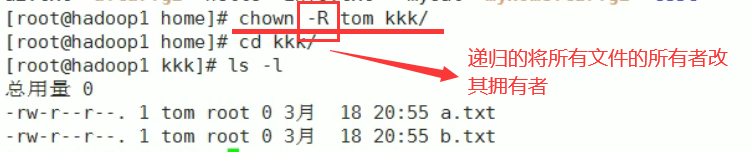
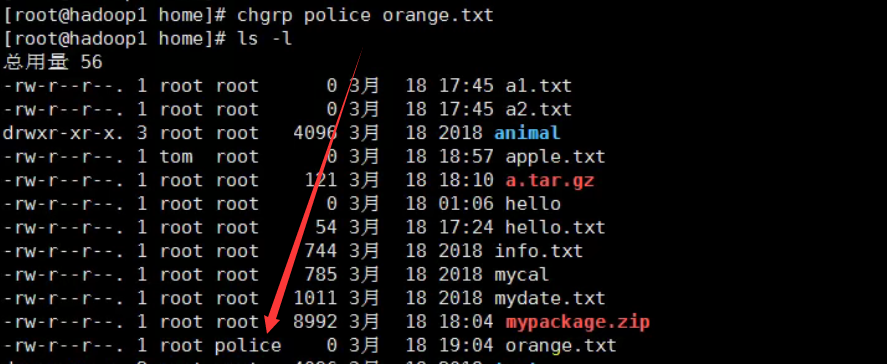
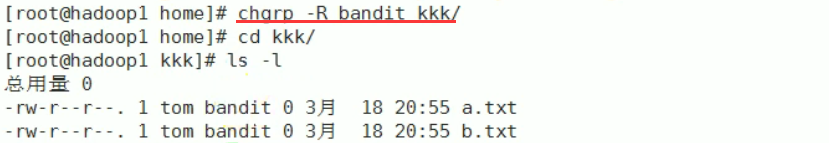
Change the file group chgrp
Scheduled task scheduling
crond task scheduling
Crond regularly executes a task or a script or code of the system; If it's just a simple task, you don't need to write a script, you just need to edit and execute it in crond.
Common options
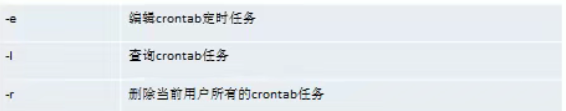
case

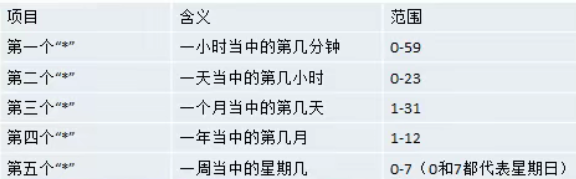
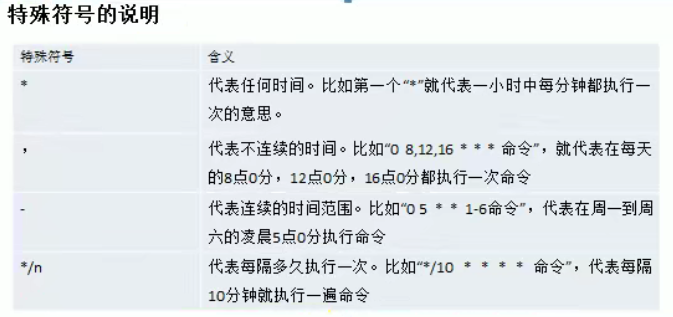

Linux disk partition, mounting

Linux partition principle
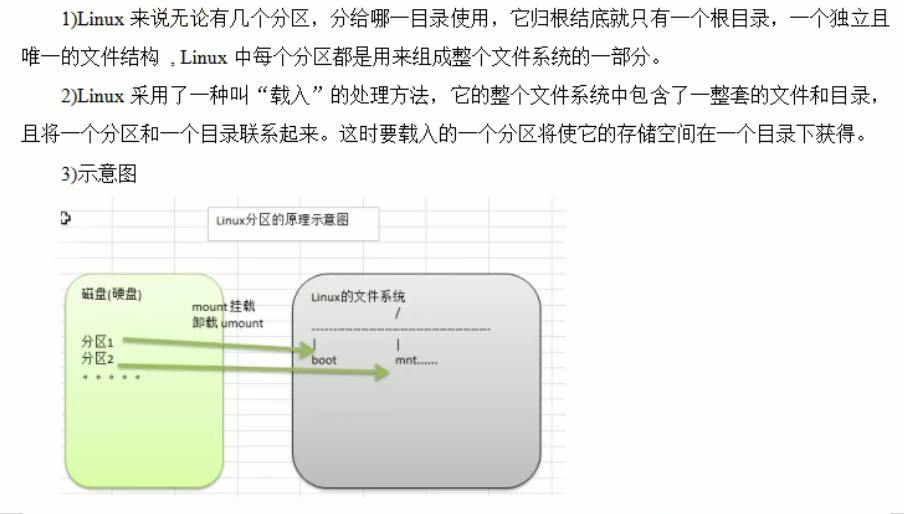
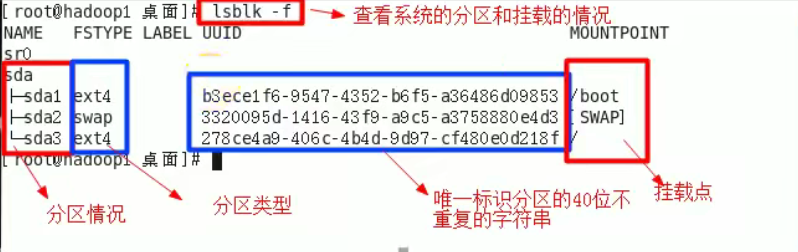
Use lsblk [options] to view the partition
-f you can view the details
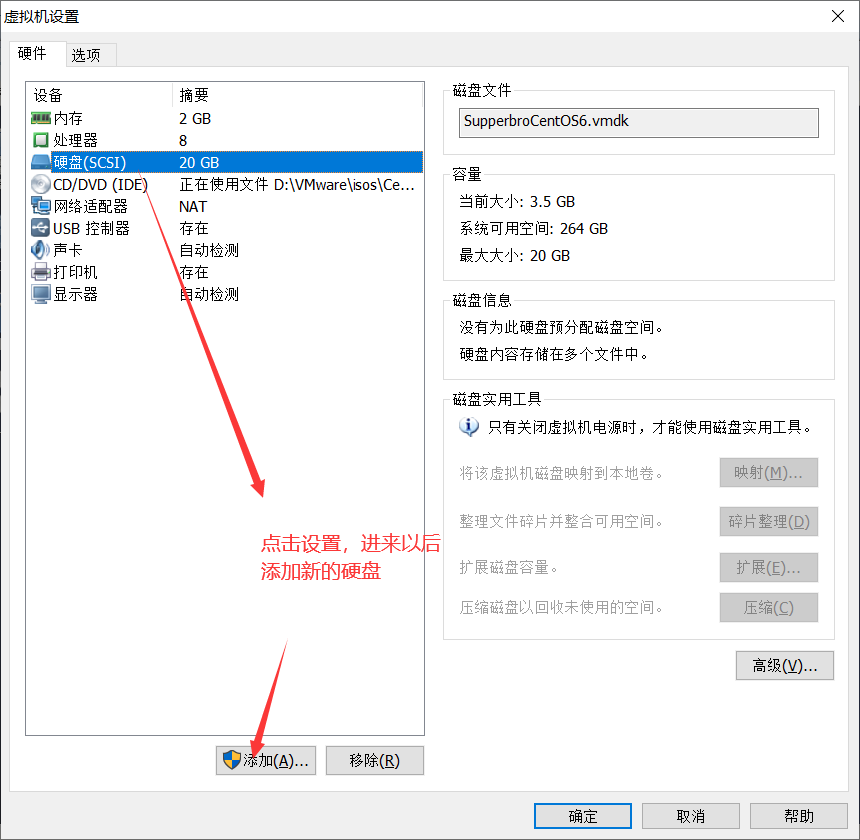
Case - adding a hard disk
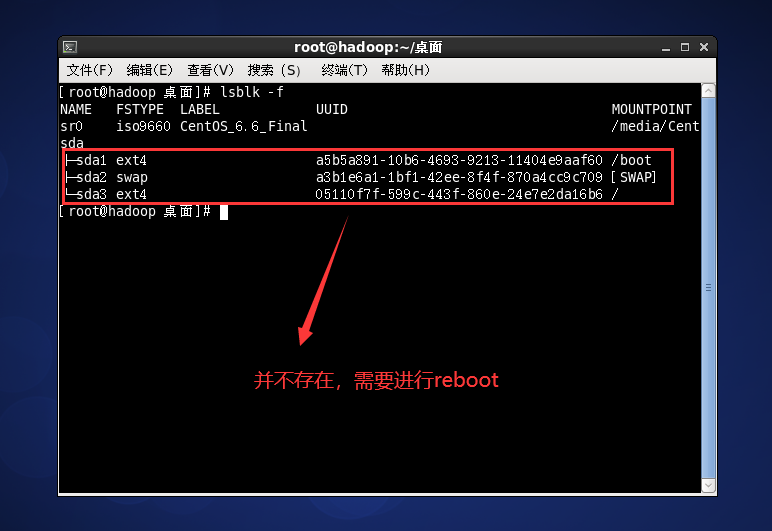
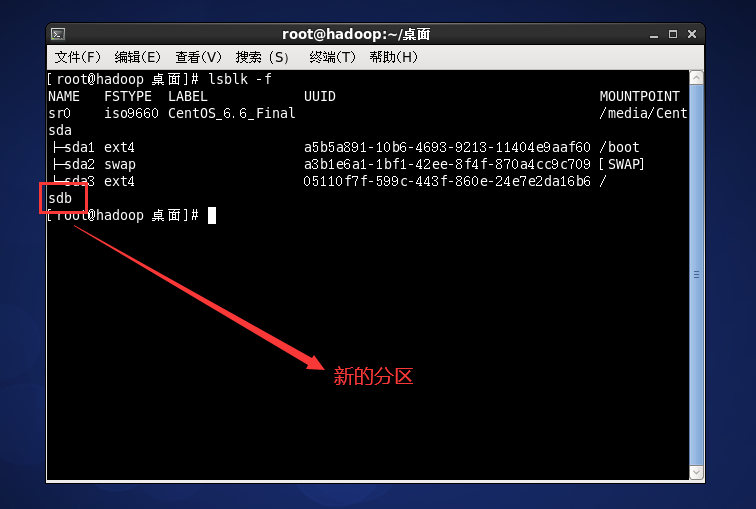
fdisk /dev/sdb for disk partition
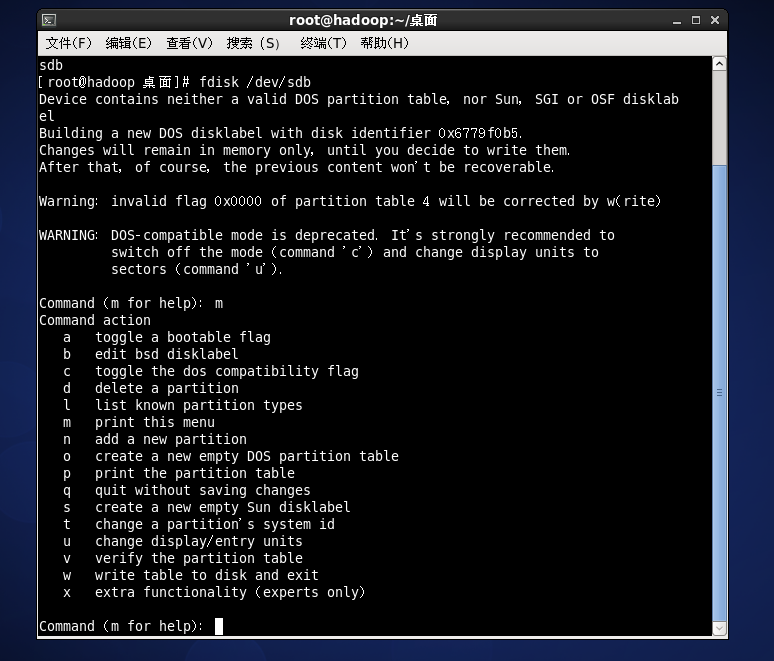
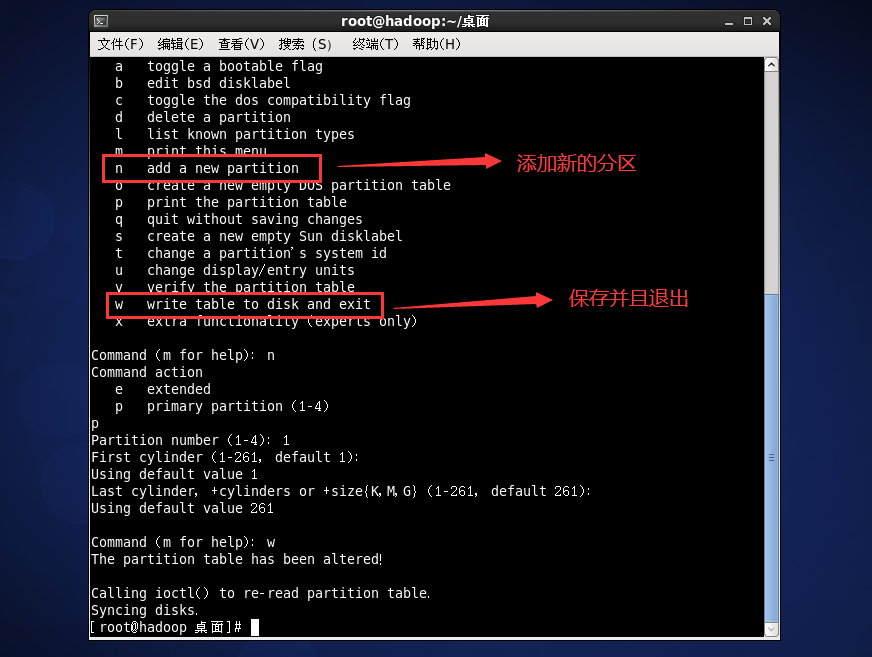
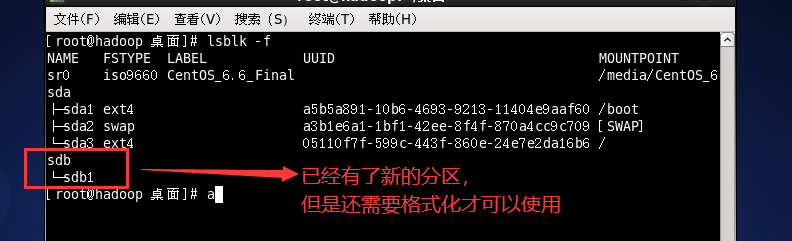
Instruction operation for formatting
mkfs -t ext4 /dev/sdb1
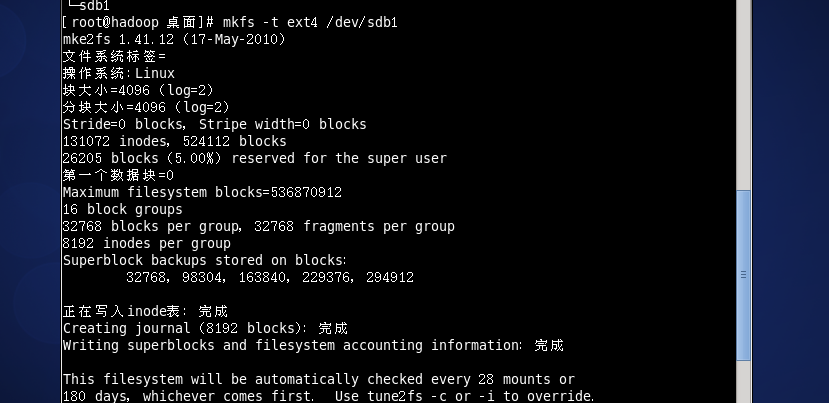
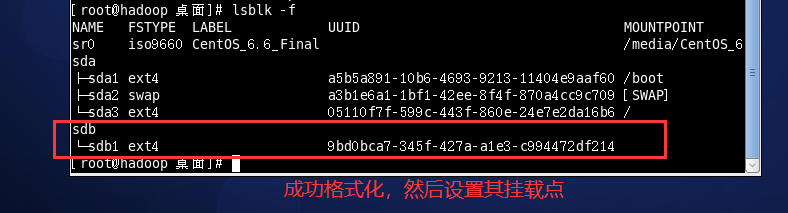
Set the mount point, for example: / home/newdisk to create the directory
mount /dev/sdb1 /home/newdisk
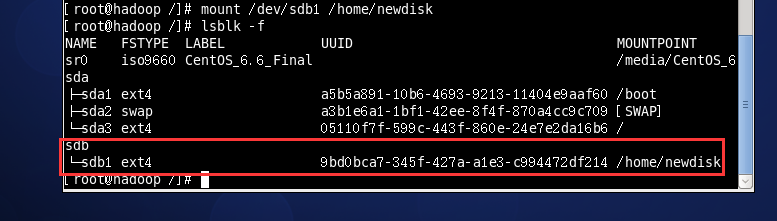
The currently set mount is temporary. You need to set automatic mount. The details of the current mount are recorded in / etc/fstab. You can change the auto mount by setting it.
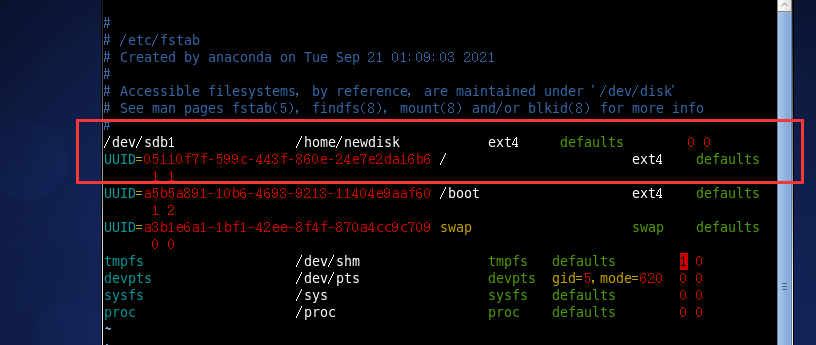
mount -a set auto mount
Disk status query
Check the overall usage of the disk; df -h instruction
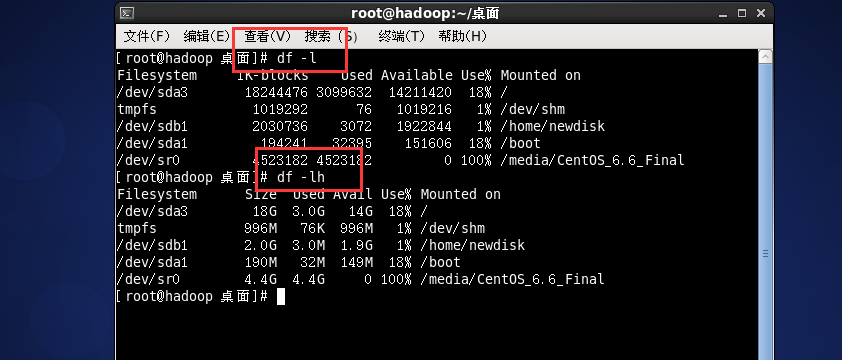
Query the disk usage of the specified directory du -h / directory
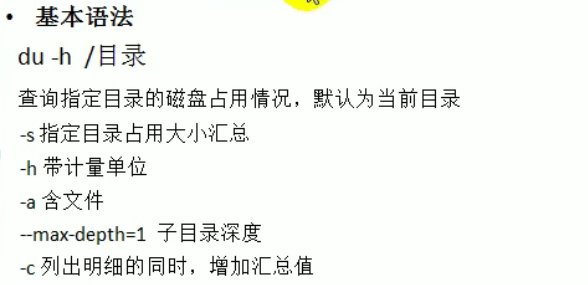
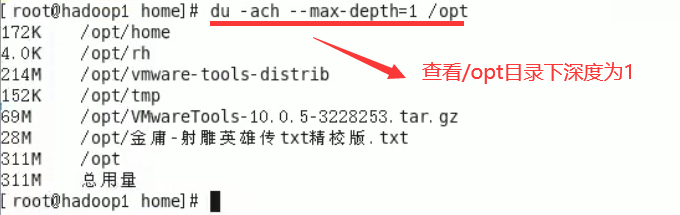
case

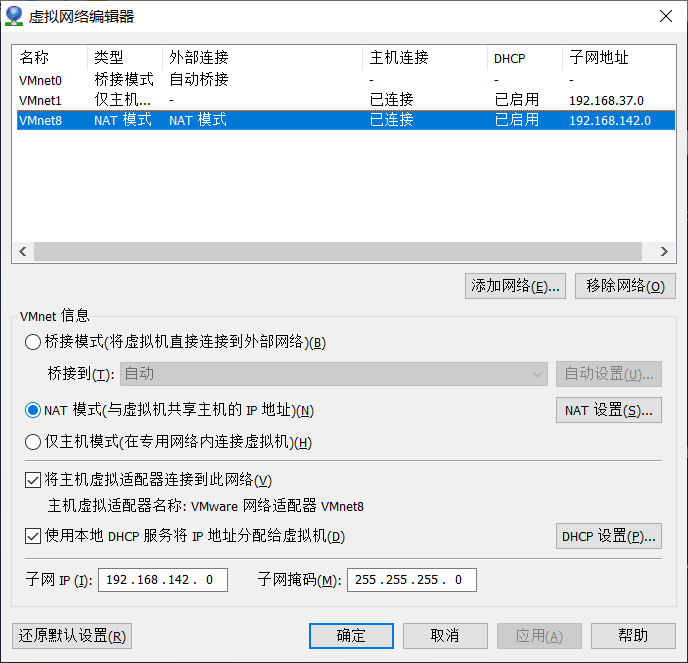
network configuration
Nat network schematic diagram
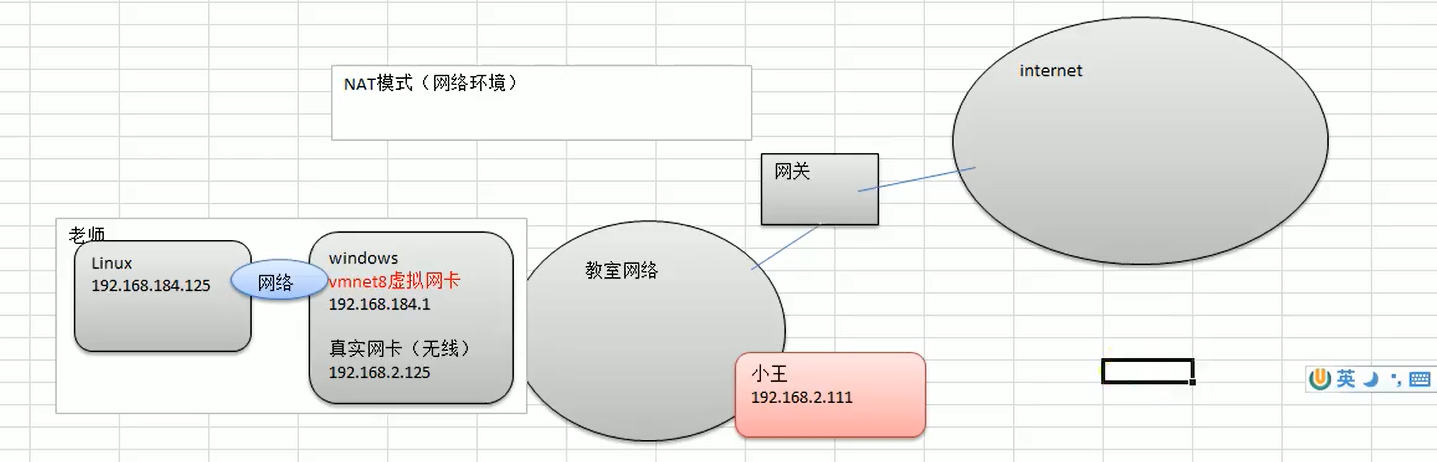
View networks and gateways
Process management
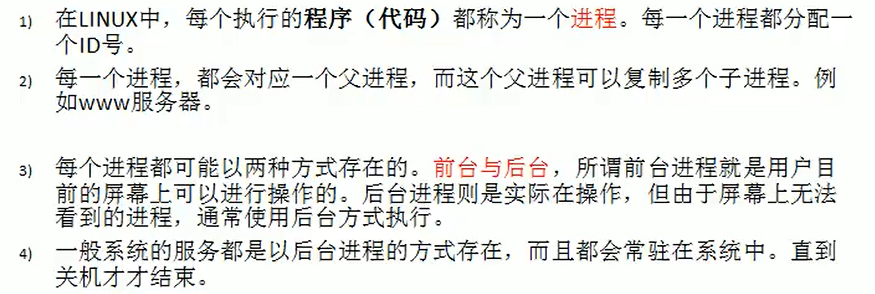
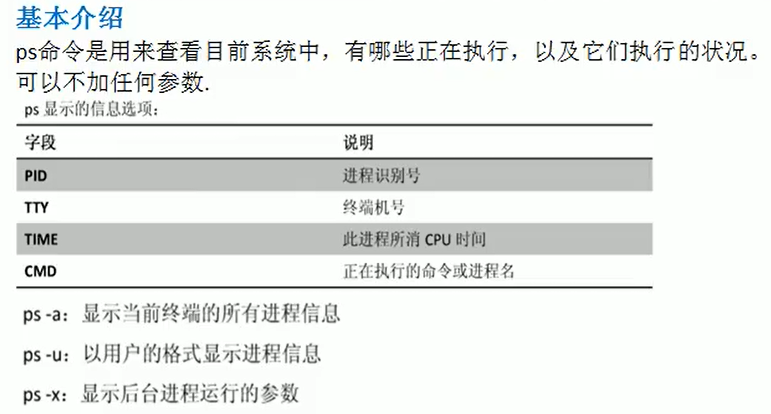
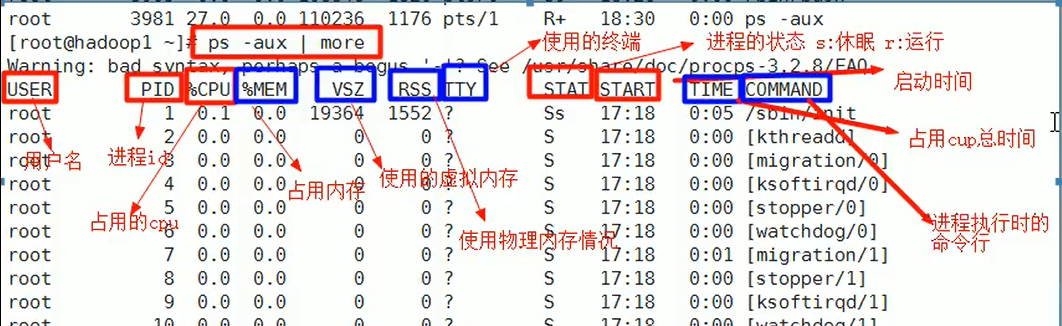
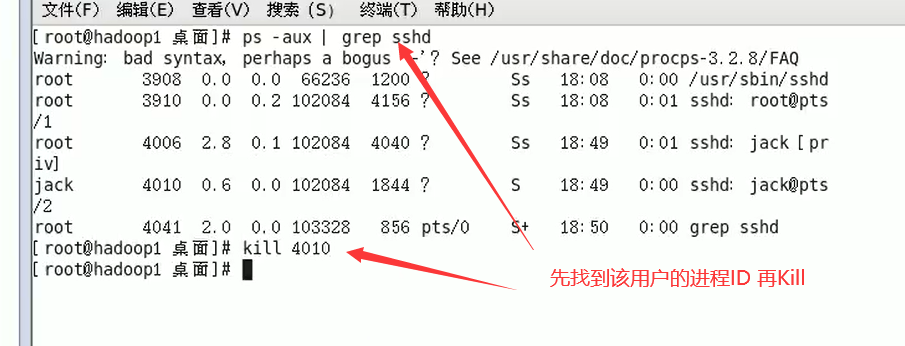
Display system process instructions ps


Terminate process kill kill

service management
Service level
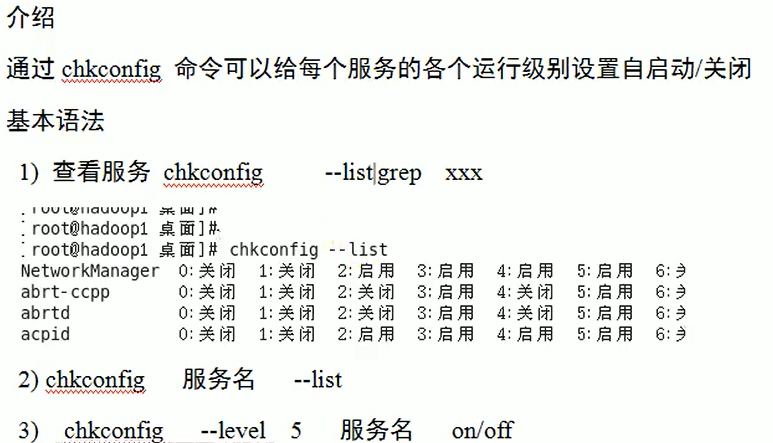
chkconfig instruction
RPM and PUM management
RPM introduction
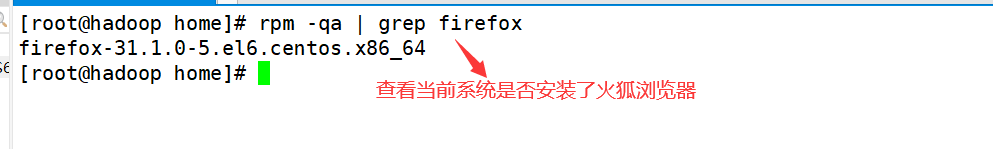
Query instruction
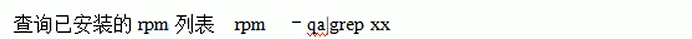

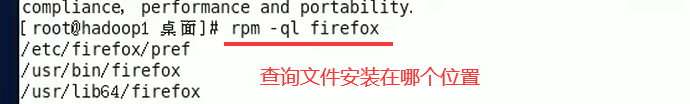
Unload instruction

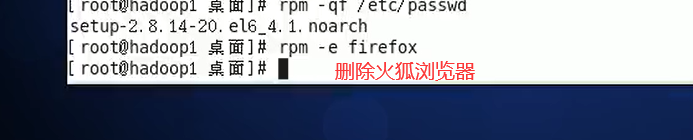
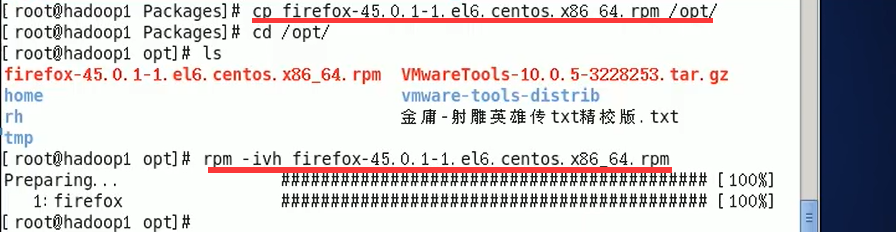
Installation instructions

yum
yum (Yellow dog Updater, Modified) is a Shell front-end package manager in Fedora, RedHat and SUSE.
Based on RPM package management, it can automatically download and install RPM packages from the specified server, automatically deal with dependencies, and install all dependent software packages at one time without tedious downloading and installation.
yum provides commands to find, install, and delete a package, a group, or even all packages. The commands are simple and easy to remember.
yum [options] [command] [package ...] options: Optional, options include-h(Help),-y(When prompted during the installation process, select all as "yes"),-q(Do not display the installation process) and so on. command: What to do. package: The package name of the installation.
yum Common commands 1. List all updatable software inventory commands: yum check-update 2. Update all software commands: yum update 3. Install only the specified software commands: yum install <package_name> 4. Update only specified software commands: yum update <package_name> 5. List all installable software commands: yum list 6. Delete package command: yum remove <package_name> 7. Find package command: yum search <keyword> 8. Clear cache command: yum clean packages: Clear the package in the cache directory yum clean headers: Clear the cache directory headers yum clean oldheaders: Clear old in cache directory headers yum clean, yum clean all (= yum clean packages; yum clean oldheaders) :Clear the software package and old in the cache directory headers