Absrtact: This paper mainly studied how to configure firewall in Linux system.
iptables command
Iptables is not exactly a firewall, the real firewall is a Netfilter running in the system kernel, and iptables is only a tool to operate netfilter. Its main function is to interact with users, get the user's requirements, and convert them into information acceptable to netfilter.
The Concept of Chain
When the client accesses the server's WEB service, the client is the starting point, and the socket (IP address and port) monitored by the WEB service is the end point. When WEB services need to respond to client requests, the IP and port that WEB services listen on becomes the starting point and the client becomes the end point.
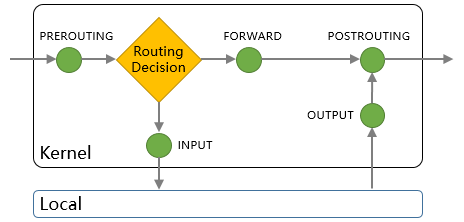
If you want the firewall to achieve the purpose of fire prevention, you need to set up checkpoints in the netfilter framework of the kernel. All incoming and outgoing messages must pass these checkpoints. After checking, they can be released only if they meet the conditions of release. If they meet the conditions of blocking, they need to be blocked. So there are INPUT checkpoints and OUTPUT checkpoints. If the destination address of the message from the client is not local, but other servers, then PREROUTING, FORWARD and POSTUROUTING will be used. These checkpoints are called chains in iptables.
Brief description: INPUT chain and OUTPUT chain are mainly used in the "host firewall", that is, the firewall for server local wake-up protection. FORWARD chain, PREROUTING chain and POSTROUTING chain are mostly used in "network firewall", such as using Linux firewall as gateway server to control security between company and Inetnet.
Detailed description of the chain:
INPUT Chain: The rules in this chain are applied when a packet (inbound) accessing the local address of the firewall is received.
OUTPUT Chain: When the firewall sends data packets (outbound) locally, the rules in this chain are applied.
FORWARD Chain: The rules in this chain are applied when receiving packets that need to be forwarded to other addresses through the firewall.
PREROUTING Chain: Apply the rules in this chain before routing a packet.
POSTROUTING Chain: After routing a packet, apply the rules in the chain.
The Concept of Table
Every message passing through this level matches all the rules in this chain. If there are qualified rules, the corresponding actions of the rules are executed. But there may be more than one rule in each chain, so a set of rules with the same function is called a table, and rules are managed through the rule table.
The default iptables rule table is:
1 filter table, filter rule table, and the kernel module is iptables_filter. 2 nat table, network address translation rule table, the core module is iptable_nat. 3 mangle table, modify the data label bit rule table, the core module is iptable_mangle. 4 raw table, tracking data rule table, and the core module is iptable_raw.
Rule table application priority: raw, mangle, nat, filter.
The application order of each rule: The filtering in the chain follows the principle of "matching is stopping". If the matching rule is not found in the whole chain, it will be processed according to the default strategy of the chain.
Packet filtration process
install
In version 7 of CentOS, the iptables tool is not installed by default, so you need to install it manually:
1 [root@localhost ~]# yum install -y iptables-services 2 ... 3 ============================================================================================================================= 4 Package Architecture Version Source Size 5 ============================================================================================================================= 6 Installing: 7 iptables-services x86_64 1.4.21-28.el7 base 52 k 8 Installed for dependency: 9 iptables x86_64 1.4.21-28.el7 base 433 k 10 ... 11 is over! 12 [root@localhost ~]#
Start up service
Start and view the iptables service using the system CTL command of the management service:
1 [root@localhost ~]# systemctl status iptables 2 ● iptables.service - IPv4 firewall with iptables 3 Loaded: loaded (/usr/lib/systemd/system/iptables.service; disabled; vendor preset: disabled) 4 Active: inactive (dead) 5 6 8 month 16 10:38:38 localhost.localdomain systemd[1]: Stopped IPv4 firewall with iptables. 7 8 month 16 10:39:29 localhost.localdomain systemd[1]: Stopped IPv4 firewall with iptables. 8 [root@localhost ~]# systemctl start iptables 9 [root@localhost ~]# systemctl status iptables 10 ● iptables.service - IPv4 firewall with iptables 11 Loaded: loaded (/usr/lib/systemd/system/iptables.service; disabled; vendor preset: disabled) 12 Active: active (exited) since Five 2019-08-16 10:41:24 CST; 2s ago 13 Process: 1582 ExecStart=/usr/libexec/iptables/iptables.init start (code=exited, status=0/SUCCESS) 14 Main PID: 1582 (code=exited, status=0/SUCCESS) 15 16 8 month 16 10:41:24 localhost.localdomain systemd[1]: Starting IPv4 firewall with iptables... 17 8 month 16 10:41:24 localhost.localdomain iptables.init[1582]: /usr/libexec/iptables/iptables.init:Row 22: /etc/init.d/func...Or catalogue 18 8 month 16 10:41:24 localhost.localdomain iptables.init[1582]: iptables: Applying firewall rules: /usr/libexec/iptables/i...To order 19 8 month 16 10:41:24 localhost.localdomain systemd[1]: Started IPv4 firewall with iptables. 20 Hint: Some lines were ellipsized, use -l to show in full. 21 [root@localhost ~]#
Basic Grammar
1 iptables [specified table] [option] [condition] - j [policy]
Specified table description
1-T Table Name: Tables used to specify operations, such as filter, nat, mangle or raw, use filter by default.
Option Description
View options:
1-L Chain Name: View the rules for specifying the chain for the specified table, and view all rules for the specified table without specifying the chain. 2-v: See the details. 3-n: Display host address and port number in digital format. 4-x: Display the exact value of the counter. 5 --line-numbers: When you look at the rules, display their number on the chain.
Options for management rules:
1-A Chain Name: Add a new rule to the end of the specified chain. 2-I Chain Name Number: Add a new rule to the specified location of the chain, default to the first. 3-R Chain Name Number: Replace the specified rule with a new rule. 4-D Chain Name Number: Delete the rule according to the rule number.
Management Chain Options:
1-N Chain Name: Create a new custom rule chain. 2-X Chain Name: Delete rules for specifying custom chains for specified tables, and delete rules for all custom chains for specified tables without specifying chains. 3-F Chain Name: Clear the rules for specifying the chain of the specified table, and empty all rules for specifying the table without specifying the chain. 4-E Original Chain Name New Chain Name: Rename Chain. 5-Z: Clear the chain and the counter of default rules in the chain. 6-P chain name policy, setting the default link policy.
Conditional description
1-s IP address: Matches the source address. Host name cannot be specified here. It must be IP. There are mainly three kinds, IP, IP/MASK and 0.0.0.0/0.0.0. Address can be reversed by adding a "!" to indicate which IP is excluded. 2-D IP Address: Match the target address, the same rule as-s. 3 --sport port number - port number: specify the source port, can not specify multiple discontinuous ports, can only specify a single port. 4 --dport port port port number - port number: specify the target port, the same rule - sport. 5-I Network Card: Data flowing from a designated network card is generally used on INPUT and PRROUTING. 6-O Network Card: Data outflow from designated network card is generally on OUTPUT and POSTTROUTING. 7-p protocol: matching protocol, where there are usually three protocols, TCP, UDP, ICMP. 8-m port number, port number: indicates that multi-port extension is enabled.
Policy Description
1 ACCEPT: Receive data packets. 2 DROP: Drop packets. 3 REJECT: When rejected, the reason for rejection is prompted. 4 REDIRECT: Redirects data packets to one port of the local or another host, usually functioning as transparent proxy or open intranet services. 5 SNAT: Source address translation. 6 DNA T: Destination address conversion. 7 MASQUERADE: IP camouflage. 8 LOG: Logging function.
Save configuration
1 [root@localhost ~]# service iptables save 2 iptables: Saving firewall rules to /etc/sysconfig/iptables:[ Sure? ] 3 [root@localhost ~]#
Use examples
View Rules:
1 [root@localhost ~]# iptables -nvL 2 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) 3 pkts bytes target prot opt in out source destination 4 584 45376 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 5 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 7 1 52 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 8 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 9 10 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) 11 pkts bytes target prot opt in out source destination 12 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 13 14 Chain OUTPUT (policy ACCEPT 4 packets, 464 bytes) 15 pkts bytes target prot opt in out source destination 16 [root@localhost ~]#
Add rules:
1 [root@localhost ~]# iptables -A INPUT -m state --state NEW -p tcp --dport 3306 -j ACCEPT 2 [root@localhost ~]# iptables -nvL 3 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) 4 pkts bytes target prot opt in out source destination 5 754 57856 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 6 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 8 1 52 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 10 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:3306 11 12 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) 13 pkts bytes target prot opt in out source destination 14 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 15 16 Chain OUTPUT (policy ACCEPT 4 packets, 592 bytes) 17 pkts bytes target prot opt in out source destination 18 [root@localhost ~]#
Delete the rule:
1 [root@localhost ~]# iptables -D INPUT 6 2 [root@localhost ~]# iptables -t filter -nvL 3 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) 4 pkts bytes target prot opt in out source destination 5 807 61588 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 6 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 8 1 52 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 9 1 229 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 10 11 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) 12 pkts bytes target prot opt in out source destination 13 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited 14 15 Chain OUTPUT (policy ACCEPT 19 packets, 2004 bytes) 16 pkts bytes target prot opt in out source destination 17 [root@localhost ~]#